ANY.RUN proudly presents Threat Intelligence Reports: investigative reports on cyber threats and attacks focused on delivering actionable insights to security professionals and decision makers.
Manually composed by our experienced analysts, the Reports provide data for threat monitoring and detection, incident mitigation and response, R&D, education, strategic planning and compliance.
These detailed attack overviews are based on comprehensive research of cyber threats, including malware, ransomware, phishing campaigns, and other malicious activities. APTs and cybercriminal groups are under special scrutiny as one of the most critical and persistent hazards to organizations and individuals.
How to Get TI Reports
TI Lookup’s paid customers get access to detailed reports with comprehensive intelligence data. For a wider audience, summaries on actors and threats are available. Some reports are also fully available for free.
Reach the reports in 3 easy steps:
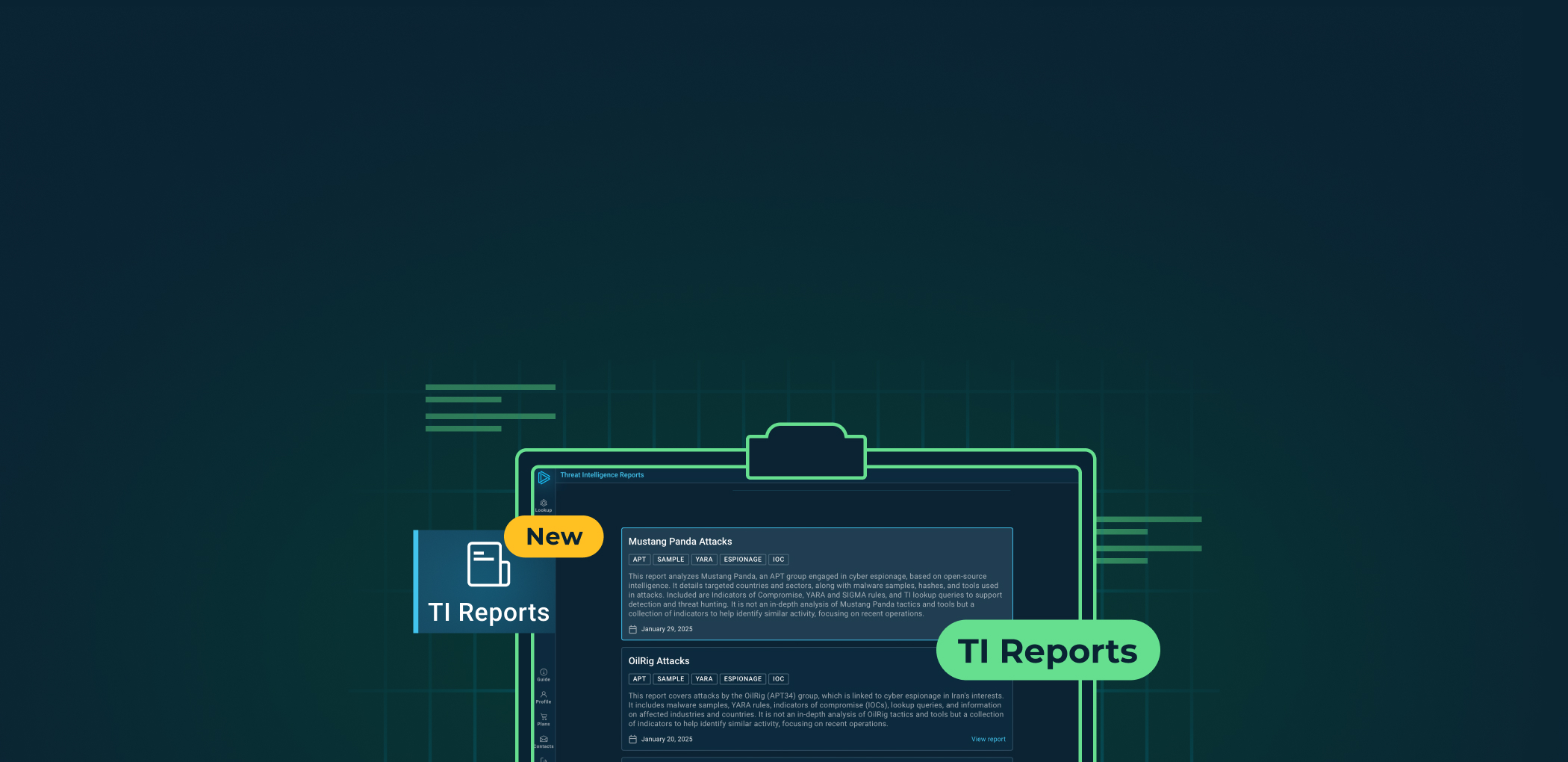
1. Visit TI Lookup’s main page at intelligence.any.run.
2. Navigate to TI Reports via the icon on the left.
3. Click on a report of your choice in the feed.
View sample report on APT41 Attacks
As a fresh report is added, the “New” badge will emerge on the “TI Reports” icon.
Data Behind TI Reports
TI Reports are founded on fresh real-world data about new and ongoing threats, handpicked and processed by ANY.RUN analysts. Our Interactive Sandbox, among other sources, provides us with a constantly filling community-powered collection of malware sample analyses.
Each report lets researchers dive deeper into any indicator or artifact with pre-created TI Lookup search queries to discover more relevant data.
Info You Can Find in TI Reports
Each report begins with the actor or vehicle overview and continues with its basic description: aims, origins, first-seens, targeted industries and countries. The description helps to grasp the scale and context of a threat, letting you understand its relevance to specific industries.
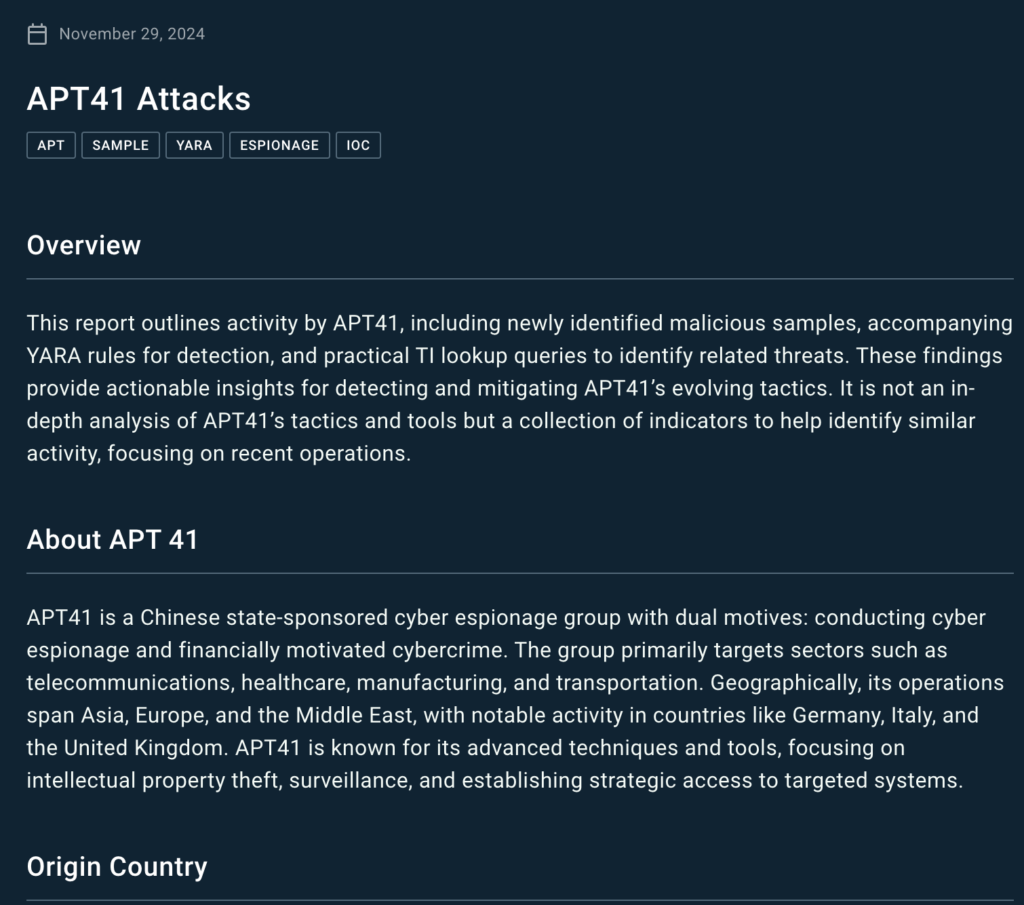
A list of TTPs used by the attackers contains their tactics, techniques and procedures which are methods and tools that adversaries engage and combine in their campaigns. TTPs are followed by a collection of indicators — of compromise (IOCs), of behavior (IOBs) and of attack (IOAs) — associated with the threat or the group.
TTPs and indicators are essential for setting up proactive cyber defense and are listed along with links to sandbox sessions showing them in action.
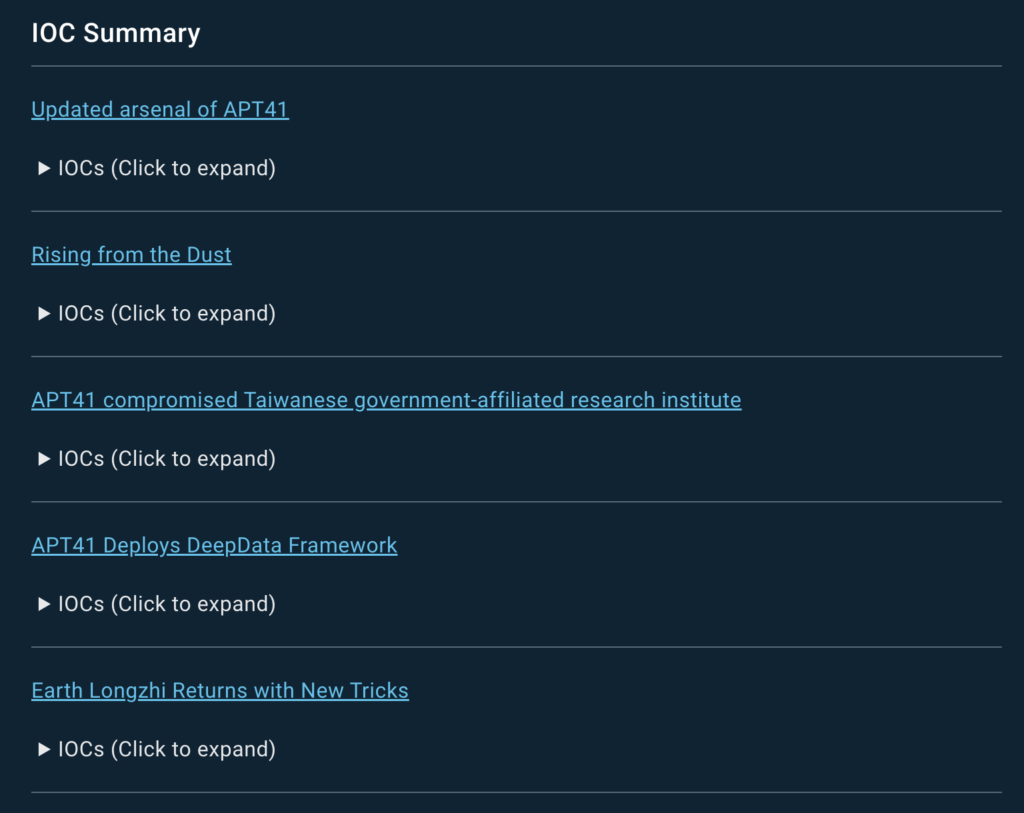
Last but not least, YARA and SIGMA rules are included for tuning the detection systems.
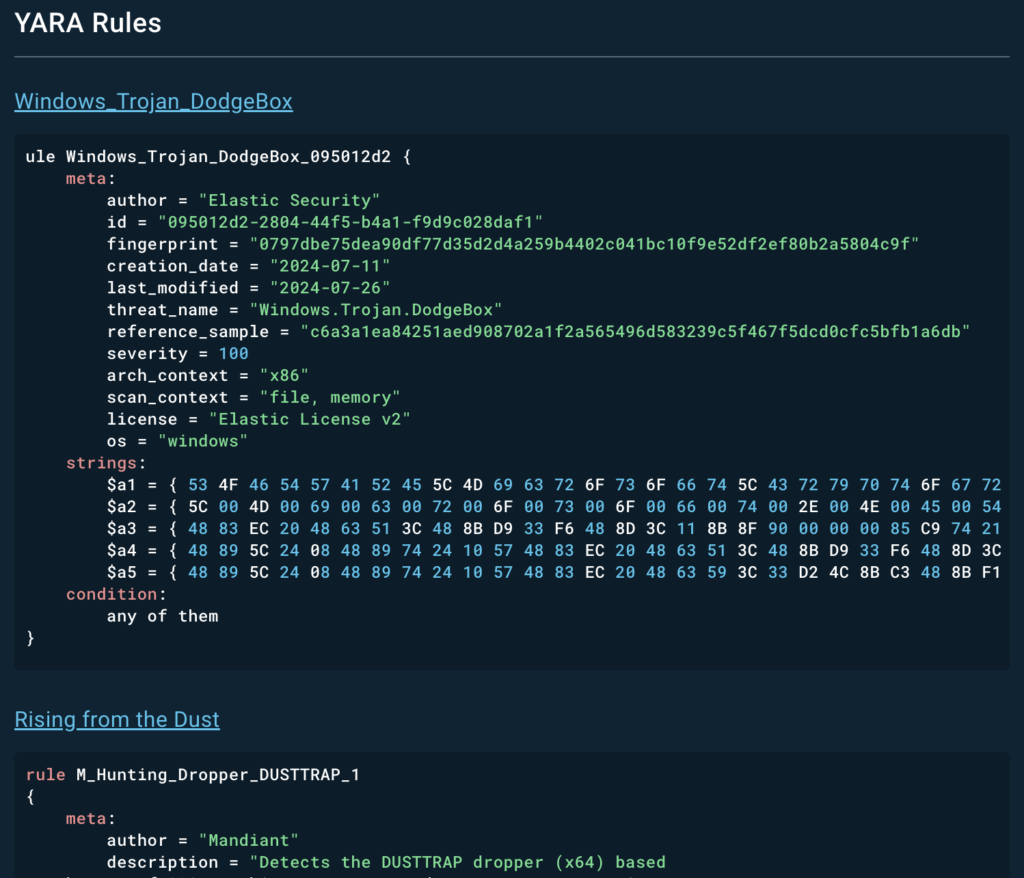
References and links for wider research are integrated into report text, and more are added as an appendix.

Learn to Track Emerging Cyber Threats
Check out expert guide to collecting intelligence on emerging threats with TI Lookup
Benefits for SOC Teams
For security analysts and SOC teams, Threat Intelligence Reports are to fuel the critical measures in building and supporting a robust cyber security infrastructure:
- Enhanced Threat Detection: gather IOCs, IOBs, IOAs, and TTPs to tune monitoring and detection for SIEMs and firewalls; compose new rules and fine-tune existing ones.
- Incident Response: use reports to understand the scope, impact, and nature of threats for reducing response time.
- Proactive Defense: block known threats preemptively and prepare mitigations for similar attacks.
- Threat Hunting: watch TTPs to look for similar behaviors that might indicate an attack before it unfolds.
- Research and Development: add the Reports’ data to your sources for studying new or evolving malware.
Benefits for Businesses
For organization stakeholders and decision makers, TI Reports are a valuable resource for fulfilling security-related business goals and objectives:
- Risk Assessment: understand the risk landscape better, see how threats might impact business operations, grasp risks specific to your industry or organization.
- Strategic Decision Making: allocate security resources based on threat intelligence, align your budget with actual risks.
- Strategic Planning: develop cybersecurity strategies and policies to protect business assets.
- Compliance and Reporting: use Reports to signal due diligence in cybersecurity practices, your adequacy in threat monitoring and response.
- Communication and IR: accommodate Reports to explain the state of cybersecurity to non-technical stakeholders, to illustrate why certain investments or actions are necessary.
- Reputation Management: manage the narrative around how the incident was handled in case it happens.
- Insurance and Legal: strengthen your position for insurance purposes or in legal scenarios with access to comprehensive threat intelligence: it can be beneficial in proving due diligence or in understanding the extent of a security incident.
Conclusion
Threat Intelligence Reports, as unique pieces of research crafted by ANY.RUN’s threat analysts with proactive approach to cyber attacks in mind, can assist both security teams in their everyday routine, and management in their strategic planning.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.







0 comments