ANY.RUN is the first interactive online malware analysis sandbox. The service detects, analyzes, and monitors cybersecurity threats. And it includes various types of accounts for the needs of different users. We hope you are one of these users that chose ANY.RUN for their work. And are you trying to make up your mind about what subscription to begin with?
Today we are starting the series of articles that will help you out. ANY.RUN provides 4 plans for your needs. This time we would like to tell you about the community account, its features, and use cases. The plan provides a diverse stack of functionalities that lets you do a full-fledged malware investigation.
A use case
The best way to see all features at work is to start the analysis. Why don’t we examine one of the samples? Let’s do it!
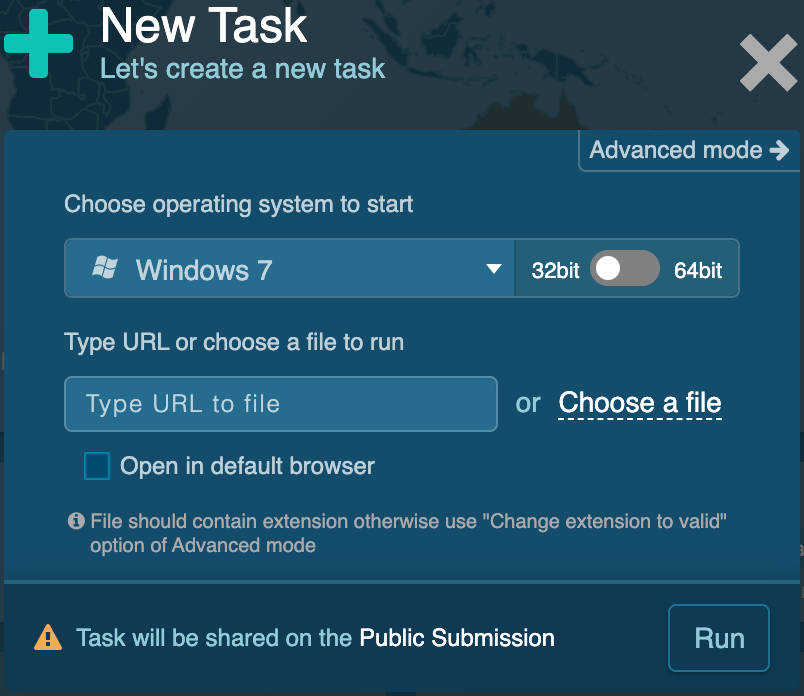
The first step is to create a new task. Windows 7, the 32-bit rate is available by default. This operating system is one of the most popular ones and that is the reason why it is available for the Community plan’s users.
Then you can choose the file to upload. Remember, you can input up to 16 Mb per file. We should note that there is hardly any malware of this size in the wild. If you want to submit a URL address to a file just either type or paste it in the input field. Our service offers you to pick one of the most used browsers to open your link. Advanced malicious programs act differently on various browsers. And, the latest version of them might be crucial for investigations. So, URL analysis in different browsers will come in handy. By checking the “Open in default browser” box, the URL address opens on the Internet Explorer browser.
And we’re ready to run the task! Furthermore, if you have more suspicious files for analysis, don’t worry, you get a chance to launch an unlimited number of public analyses! Upload as many files as you need! But note, please, that your task will be shared publicly with the Community plan.
Give the machine a few moments to load and here we go! Now we can monitor the file behavior in the environment.
To observe this task use the following link:
https://app.any.run/tasks/5d684aa5-f184-475d-bc94-b2a9308ddb53/
The duration of the analysis is set to 60 seconds, also there is a possibility to add up to 4 minutes. This time is enough to explore the suspicious file and interact with the virtual machine. ANY.RUN’s interactive access is a real game changer! Just imagine that you’re working with an attacked computer, but completely safe. Drag a mouse, tap keys, reboot the system, open files, input data— do whatever you want to research the file.
You get access to the operating system just only a few seconds after starting. There is no need to wait for the end of the analysis — get the first results in real-time.
Let’s execute the word document into the Windows 7 environment in the virtual machine. We can see how the file is loading. And on the right, all processes are structured logically in the process tree.
To finish the task, click the “Stop” button in the Up-right corner.
As you can see in the “Process details”, a biohazard sign has appeared. It means that the Qbot malware was detected by local signatures — created file and command-line argument of the cmd.exe process. To get more info, check Advanced details.
And now it’s time to dive into analysis with all collected information. In the “Connections” section, you see 1 successful response which downloaded the main payload — Qbot trojan itself. Clicking on any of them in the Headers column to research “Request details”. Copy the necessary data, if you will.
In the “Threats” sector, we get quite a bunch of results listed. If you are interested in a particular one, filter by message. The Class column gives you the whole idea of what was hiding from you. Click on any of them to uncover the “Threat details”.
It’s time to get acquainted with “File modifications”. And collect Process details.
To find out what signatures identified malware, click on the process with the biohazard sign, and detected malware tag. In our case, click on “QBOT was detected” and you can see all signatures through which it was detected. In this example, it’s the created file and arguments of the command line cmd.exe. Get more information in “More info” in this process.
The reports and necessary information can be exported in PDF, JSON, HTML, and PCAP format. Moreover, you get additional details in the info block. For example, the process behavior graph gives you extra data such as a file’s type, the malware family, the direction of injection, etc. Pick a process to bring up the process details. To find out about the process of an attack, use the Mitre ATT&CK matrix. The whole logic is shown here from the initial access to the impact. Moreover, you can research all the used tactics.
This is the way you finish the analysis! Threats are detected and processes are researched. And we are definitely not leaving empty-handed — all significant material with us, such as detailed reports, a process graph, etc. Of course, it was not an elaborate investigation as the one you get on other plans. However, the essential results you get anyway.
Besides the analyses, you get an opportunity to research the enormous ANY.RUN database of the public submissions. What a great source to learn and improve as a cybersecurity specialist!
Conclusion
The Community plan can be a discovery for you. You can perform analysis for free, isn’t it an advantage? But If you want to go deeper, check out other plans for expanded functionalities, more opportunities, and even more comprehensive reports. Sounds interesting? Stay tuned to learn more about other plans in our next articles. You can also find information about all plans and their description here.
And don’t forget that you can find more examples of how to use the Community plan in the video below. Go ahead and watch it!
5 comments








I’m no sure where you’re getting your information, but good topic. I needs to spend some time learning much more or understanding more.
Thanks for fantastic information I was looking for this information for my mission.
Thank you, do you have any questions concerning our plans? We’d love to help.
Thanks for wonderful info I was looking for this information for my mission.
Just want to say your article is as astounding. The clearness in your post is simply great and i can assume you are an expert on this subject.
Fine with your permission let me to grab your RSS
feed to keep updated with forthcoming post. Thanks a million and please carry on the rewarding work.
Excellent read, I just passed this onto a colleague who was doing a little research on that.