New types of malware come around every day. As security researchers, we work on the frontier of the war against malicious programs. We keep the networks and computers of other people safe by analyzing malware samples. In most cases, this entails deliberately downloading and launching malicious samples either on our own virtual environment or machines.
While coming into close contact with malware is necessary for our line of work, it also puts us at a greater risk of a mistake. And such a mistake can have grave consequences. If a sophisticated malicious program gets unleashed into the network due to our misdoing, the aftermath can be disastrous.
While a lot has been said about typical security measures for web browsing or generally working with an internet connection, we would like to talk about security specifically for cybersecurity analysts.
Safety is a Top Importance for Security Researchers
Today, Cybersecurity professionals are in high demand. A study by Burning Glass revealed that the number of job postings in our field grew by 94% in six years as of 2019. This is compared to the mere 30% growth in the general IT industry.
Unfortunately, there is a sinister reason. Jobs in cybersecurity become more sought after an indirect relationship with cybercriminal activity, which is also on the rise.
In these dangerous times, more and more young professionals enter the industry in the hopes of making a career. And while their goal is very reasonable, it is important to understand that inexperience may open the door for dangerous situations.
That’s why, today more than ever, safety is becoming extremely important. With that in mind, let’s talk about some standard security tools that every researcher should be familiar with before engaging in malware analysis:
Safety Tools that you should know about
1. NIDS/NIPS
Network Intrusion Detection Systems or NIDS are similar to anti-virus software. Depending on how they analyze traffic, they are divided into subcategories.
Signature-based NIDS searches the network for specific signatures and signs of malicious programs. Signatures are basically user-specified patterns that are associated with a hacking activity.
Heuristic, also called behavioral NIDS work by comparing all incoming network traffic and packets using a pre-configured standard, that is considered normal for a particular network.
Anomaly-based are arguably the most technically complex. These systems actively analyze incoming traffic and use artificial intelligence to dynamically change filters and rules. However, they have a potential downside of being overly cautious. They are commonly known for flagging normal traffic as malicious, requiring manual interventions.
Last but not least, Heuristic systems rely on public databases to compare incoming traffic against known records of malicious activity. Some experts believe this type of system to be the most robust. However, they are also some of the hardest to set up and require careful configuration to avoid lots of false-positive results.
Depending on a particular NIDS type, the system can simply warn the user about suspicious activity, or update network traffic automatically to prevent an attack. NIDS that warn the user is called Intrusion Detection Systems or IDS, while those that prevent attacks are called Intrusion Prevention Systems or IPS.
2. HIDS/HIPS
Host-based Intrusion Detection systems or HIDS for short, can detect file changes and examine network traffic. These systems continually analyze the network to find behavior patterns, usually associated with malware. They also track file parameters like file size, date of last changes, or control sum can, which can reveal if something fishy is going on.
HIDS systems are designed to warn the user about suspicious activity, while HIPS can take preventive measures automatically when they detect an attack. Just like NIDS, HIDS can be signature-or behavioral-based.
These systems are useful against many attack types. In particular HIPS can:
- Prevent privilege escalation attacks.
- Stop the download of Trojans, backdoors, and rootkits.
- Automatically restrict access to email contacts and stop worms from spreading.
- Stop the malware from making changes to the registry, user accounts, or files.
3. Firewalls
A firewall is a protective filter that separates a secure network from the outside world. For example, firewalls isolate corporate networks or private machines from the public Internet. They filter incoming as well as outgoing traffic and can catch instances of private data escaping the system or restrict incoming malicious connections.
Firewalls can protect against keyloggers, Trojans, backdoors, and worms that use vulnerabilities in each host to spread across a network. After making sure that vulnerable services are not running, check that your firewall does not allow connections. Just like HIPS does, a lot of modern firewalls perform at least some degree of packet filtering and discard packets that match a specific signature.
Firewalls come in two categories. Hardware firewalls are typically built into servers and routers. They filter traffic and protect against incoming malicious connections. Software firewalls, on the other hand, can be used to detect instances of malware sending out data from your machine.
4. Sandboxes
A sandbox is an isolated environment within an operating system. Any application that runs in the sandbox can not affect processes or software that exists outside of the environment. Thus, sandboxes limit the damage that malware can inflict on an operating system. In fact, many operating systems have such restriction systems built-in by default.
Researchers can use sandboxes for mass testing of all files that employees bring into a closed network. However, they are the best used for investigating unknown files or programs that you think can be malicious, or for looking into malware behavior.
To conclude this segment. Each of the systems that we listed above has its pros and cons. That’s why we advise using them together as a security set. Each tool copes better with a specialized task.
ANY.RUN’s cases
Regardless of the number and quality of automatic security systems, you will always have suspicious files making it through and skipping the firewalls. For example, a new malware type or an updated version of older malware can have new evasion techniques or a new behavior that will be missed by automatic tools. In addition, malware can penetrate the network and infect workstations by using social engineering. Researchers should examine files like this, and the best way to do that is by using sandboxes.
Let’s talk about sandbox analysis in more detail, since our company specializes in it.
ANY.RUN allows users to upload potential malware samples into an interactive sandbox. Researchers can examine them online and quickly analyze the results. ANY.RUN can significantly cut equipment costs and make many traditional malware research tools optional.
The defining feature of ANY.RUN is that the service displays all results in real-time. Process creation, potentially suspicious files or URLs, registry activity, network requests, and much more are displayed to the user just as it happens.
Researchers can catch any suspicious activity immediately, without having to wait for the final report.
According to our statistics, ANY.RUN analysts work with an average of 1,550 malware samples every month. It’s safe to say that we’ve accumulated a lot of useful experience with workplace security that we can share with the community.
Let’s take a look at how you can use ANY.RUN to safely analyze malware samples:
Using Cloud Services and Virtual Machines
Today, malware researchers have a wide malware analysis toolset ranging from static analysis with disassembly to dynamic analysis with debuggers. We have covered types of malware analysis in a separate article in detail. Make sure to read it if you would like to learn more about this topic.
We are not going to dive into this field in a lot of detail here since it requires some specific knowledge. However, we would like to arm new researchers with a set of techniques that allow conducting a quick analysis of an unknown file.
Let’s presume that you encountered a file that you think can be malicious. Unfortunately, antiviruses can’t detect it. What should you do?
As malware is spreading more widely and threat actors are starting to utilize evasion technologies like polymorphism, classic signature scanners can no longer effectively detect new threats. This is where we need a malware sandbox.
Usually, setting up a sandbox requires a lot of effort, time, and equipment. In fact, debugging and making sure everything runs as it can take up to several days or even weeks. We rarely have this much time on our hands, in fact, it’s probably enough time for malware actors to issue a whole new strain or update their program.
This is where ANY.RUN interactive sandbox can be of great help.
Since ANY.RUN is a cloud service, you can safely run suspicious files from any device anywhere in the world without having to worry about the danger of infecting your network. ANY.RUN can analyze many types of malicious files on Windows as well as any suspicious web links.
Let’s consider a few examples:
Analyzing Phishing Websites
Phishing is an online fraud that aims to access the private information of the victim. Usually, the attacker sends out email spam to impersonate a company, such as a bank. An email usually contains a link to a fake webpage that tries to trick the user into giving their real login credentials or other sensitive information.
With ANY.RUN, you can simply and safely analyze any suspicious link and see what happens, as if you clicked on it. ANY.RUN lets you select several browsers before starting a task to see if the behavior changes. We recommend selecting the most popular browsers like Google Chrome.
To analyze a potential phishing website, simply go to the service homepage and create a new task.
A dialogue window will pop up. You can insert a URL here, or go to the advanced options to configure simulation settings.
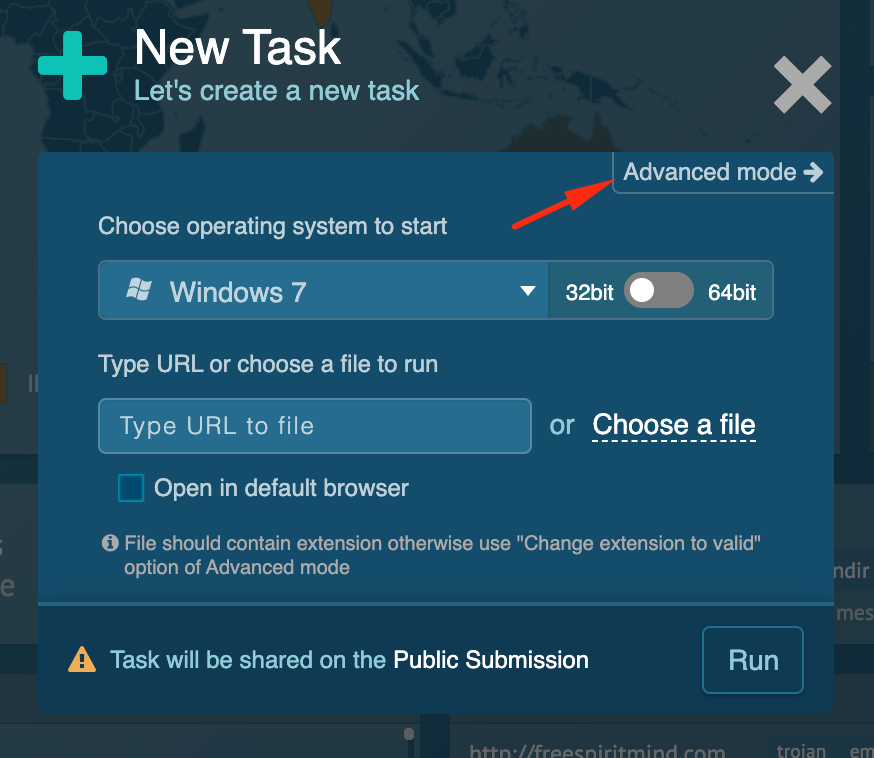
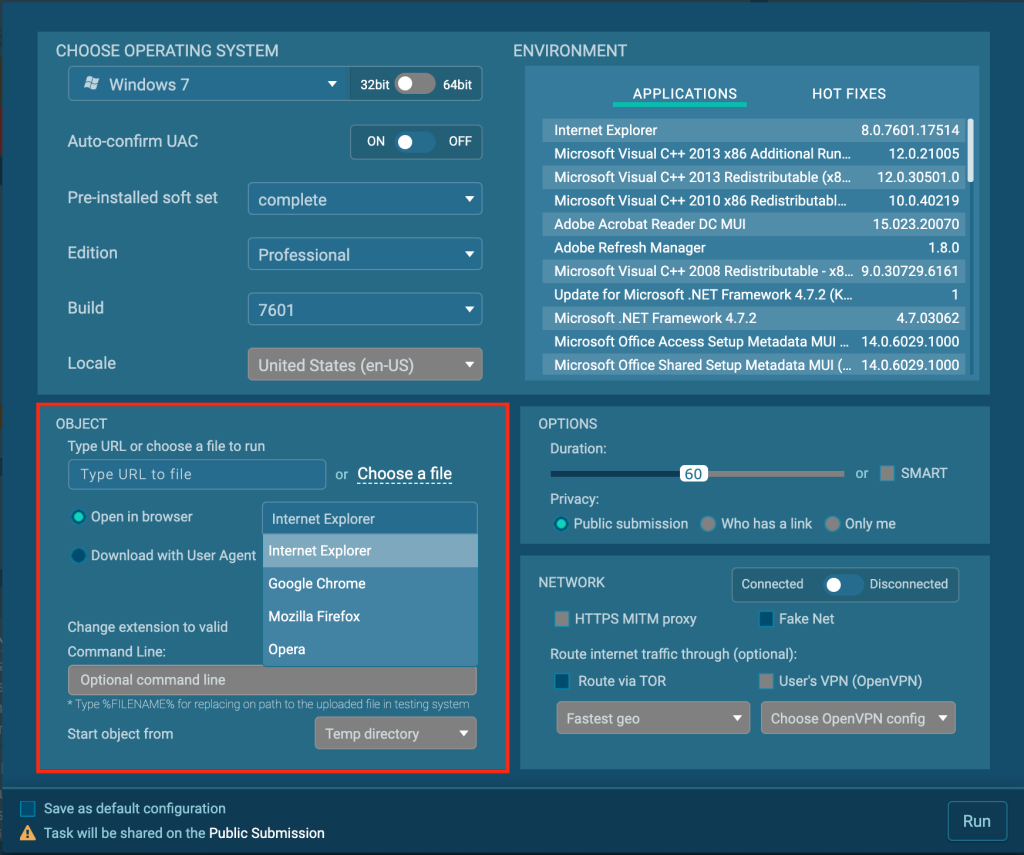
Use the object window and select the “open in browser” option. From here you can configure which browser will be used by the system.
Using Public tasks and reports.
ANY.RUN is one of the industry leaders when it comes to the number of user submissions to a public malware database. You can find many different samples or already conducted analyzes in our database, using a convenient search.
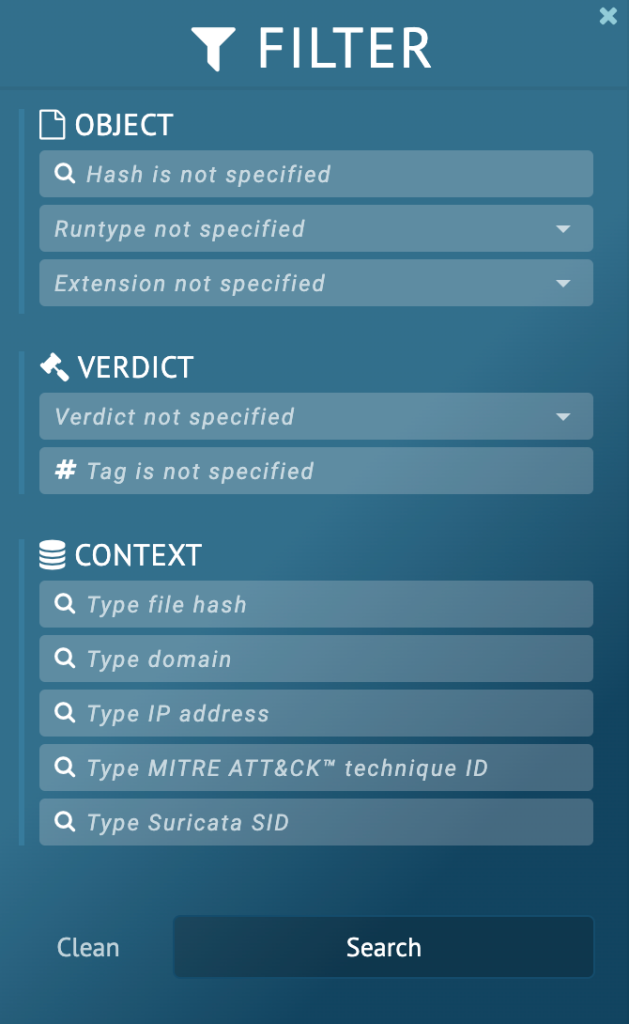
- Research by object properties like malware names, hashes, file run types or file extensions.
- Fill in verdict, specifications, and tags to find malware by behavior.
- Or explore by domain, IP, and even by MITRE ATT&CK technique ID
Want to make a retrospective analysis to find similar malware?
If you want to start analysis and you have any of the data mentioned above, search our reports database first. It’s quite likely that somebody else has already investigated the same sample and you can study their results and save time and effort.
In fact, ANY.RUN database includes around 2,000,000 tasks, presenting researchers with a lot of invaluable information.
Checking Spam Emails
One of the most popular malware distribution methods is mail spam. These emails usually contain text links or hide URLs behind banners and buttons. Often, they also contain attached malicious files. Links may point to a hacked website directly or use a series of redirects. Thus, if you want to copy the final URL to your clipboard, you must first click on the link and go through the redirect process yourself. Not the best idea.
Some email providers like Gmail give the option to download emails as a file. You can upload these files to ANY.RUN and our service will open the email with all the content and links preserved. From there, you can use the online sandbox to interact with the contents without exposing yourself to danger.
To open an email in ANY.RUN, select the “Choose a file” option from the New task window.
Keeping the Work Private
And last but not least, when working with sensitive data, it is extremely important to think about privacy.
ANY.RUN has 3 privacy levels:
- Public — the result of your analysis will be available to everyone as a report.
- By link — you can share a link and only people who receive it will be able to access your report.
- Full privacy – you will be the only user who can access the report.
You can configure the Privacy setting in the task launch window.
Last but not least, a few words about patches
Most software providers suggest installing every single patch and better yet allow your computer to update programs automatically. On the surface, this seems like a reasonable thing to do, however, in reality, it is not.
Patches are designed to improve software and fix bugs. While most of the time they do just that, they often introduce new bugs, glitches, or even vulnerabilities. On top of that, some patches maybe not suitable for your OS version, or they can mess with the work of other programs on your machine or your network.
Thus, it is important to understand that patches are not a cure-all, as software marketing teams are trying to make us believe. Patches can be a great thing, but they also can bring their own problems. What you certainly don’t want, is to have those problems introduced into your system without even knowing about them. Many system admins, and particularly those working at Microsoft have already stepped on this rake, so we can learn from their mistake.
So, do update software regularly, but make sure to test every patch before you install it on important machines. If you can’t test the patch, make sure that you can cancel its installation. What’s more, cloud storage is getting cheaper every day and you can configure automatic backup and data synchronization between your PC and your account. Also, do not forget about additional local backups. Your data is valuable, keep it safe.
Conclusion
To protect yourself against malware you first need to understand malware. Unfortunately, we can’t possibly cover protection against all malware types in any single article. Today, new strains are created almost daily, thus, it is arguably more important to understand basic security concepts as a whole. Here, we have covered some of the most important topics of malware security for researchers.
Don’t forget to regularly visit our malware trends tracker to see which strains are gaining popularity in real-time, re-run interesting tasks, collect IOCs, and remember that knowledge is power! Stay safe!








0 comments