Welcome to ANY.RUN’s monthly update series, where we share what the team has been working on this past month.
Last month, in March, we’ve added PowerShell support to our Script Tracer, released browser extensions for Chrome and Edge that allow select enterprise customers to launch tasks directly from their browser’s top panel, integrated with multiple security vendors including OpenCTI, and expanded our threat coverage with new YARA and Suricata rules.
Let’s cover these updates one-by-one.
New features
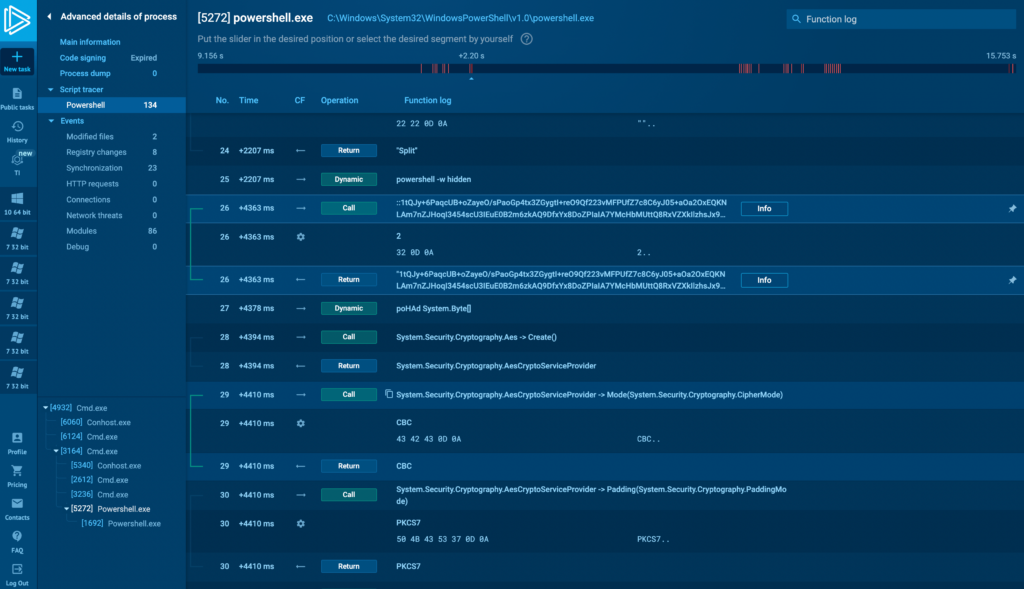
PowerShell tracer
Now, in addition to JScript, VB Script, VBA, and Macro 4.0, Script Tracer also supports PowerShell.
PowerShell is used by various malicious actors and APTs, including popular ones like TrickBot and REvil, for persistence, lateral movement, and payload execution. Trace PowerShell execution step by step to analyze and mitigate these — and other similar — threats.
ANY.RUN browser extensions
ANY.RUN extensions are now available for both Chrome and Edge browsers. Here’s how they work. For instance, if you encounter a suspicious webpage or are checking a link from a potential phishing email, you can simply open the extension and launch a task while remaining on that page, rather than navigating to the service separately.
This not only saves you time but is also more convenient. You can view the task results directly within the extension or navigate to the completed task on ANY.RUN for a detailed study.
Extensions are currently available for Hunter and Enterprise plans’ users.
New integrations
We’ve integrated with multiple vendors to seamlessly incorporate ANY.RUN into your existing ecosystem of security products. Our latest integrations include:
- OpenCTI
- D3 Security
- Threat Quotient
- Threat Quotient
- Blink
- TheHive
Read about our integration with OpenCTI.
New signatures
In March, we added 63 new malware signatures. Here are a few examples:
We’ve also added a YARA rule for Anatova ransomware, updated configuration extractor for Eternity stealer, and fixed detection and config extraction for Amadey. We’ve also updated the Suricata prompt for ChatGPT to include more Suricata fields. This has made the AI analysis more useful.
New network rules
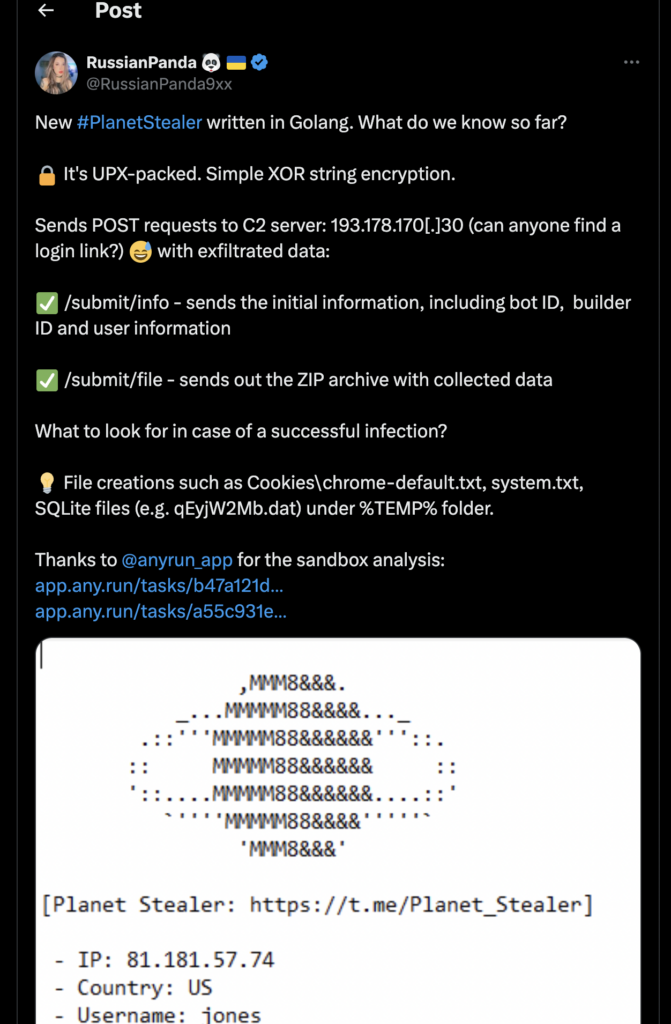
- PlanetStealer: Recently, our team of analysts has discovered a new malware called PlanetStealer. We’ve now added Suricata rules to detect it, which you can see in this task in ANY.RUN. We’ve also shared these detection rules with the Emerging Threats (ET) open source community.
- DARP: Our team has discovered a new Java-based malware loader that we’ve named DARP, short for DownloadAndRunPacket which is one of the classes it uses. You can find network signatures designed to detect this malware in this ANY.RUN task
- AsukaStealer: We’ve published an in-depth analysis of this malware on our blog, which you can read here. Additionally, we’ve added new rules to our sandbox environment that can detect this stealer’s network traffic signatures.
- DarkGate: We have implemented a new rule to detect the latest version of the DarkGate malware. The rule, called LOADER [ANY.RUN] DarkGate Stager, is designed to identify the malware’s loader component.
We’ve also developed a set of network rules to identify suspicious activity patterns. These rules are based on a research article that we’ll publish on our blog soon. But for now, we’ll keep the details under wraps, although these rule names are spoilers enough:
- POLICY [ANY.RUN] Retrieves Properties of a Lnk file via WebDAV
- POLICY [ANY.RUN] A suspicious Lnk file was downloaded containing a command shell launch (cmd.exe)
- POLICY [ANY.RUN] A suspicious Lnk file was downloaded causing the exe file to be executed
- POLICY [ANY.RUN] A suspicious Lnk file leading to a WebDAV resource was downloaded
- POLICY [ANY.RUN] Possible NTLM Hash leak over SMB (NTLMSSP_AUTH)
Last but not least, we’ve made phishing detection more accurate with new behavioral Suricata rules that aren’t tied to specific domains. This ANY.RUN task shows the improvement well in action.
About ANY.RUN
ANY.RUN’s flagship product is an interactive malware sandbox that helps security teams efficiently analyze malware.
Every day, a community of 400,000 analysts and 3000 corporate clients use our cloud-based platform to analyze Windows and Linux threats.
Key advantages of ANY.RUN for businesses:
- Interactive analysis: Analysts can “play with the sample” in a VM to learn more about its behavior.
- Fast and easy configuration. Launch VMs with different configurations in a matter of seconds.
- Fast detection: Detects malware within roughly 40 seconds of uploading a file.
- Cloud-based solution eliminates setup and maintenance costs.
- Intuitive interface: Enables even junior SOC analysts to conduct malware analysis.
Learn how ANY.RUN can benefit you or your security team. Schedule a free demo with one of our sales representatives, and we’ll walk you through real-world examples.








0 comments