Hey, cybersecurity enthusiasts!
February brought major enhancements to ANY.RUN, improving threat intelligence, detection capabilities, and overall user experience.
With the launch of Threat Intelligence Reports, security professionals now have access to detailed, expert-driven analyses of cyber threats, malware, and APT activities.
We also introduced a redesigned website, making navigation more intuitive and structured.
On the detection side, we significantly improved our threat-hunting capabilities, adding 314 new Suricata rules, refining behavior signatures, and expanding our YARA rule database. These updates strengthen real-time threat visibility and detection accuracy, helping analysts respond faster to emerging cyber threats.
Let’s take a closer look at February’s updates and how they enhance your malware-hunting workflow.
Product Updates
Threat Intelligence Reports
In February, ANY.RUN introduced Threat Intelligence Reports in TI Lookup: detailed research on cyber threats, providing security professionals and decision-makers with actionable insights.
Curated by our experts, these reports support threat monitoring, incident response, R&D, and strategic planning, covering malware, ransomware, phishing campaigns, and APTs.
Built on real-world threat data, sources include our Interactive Sandbox, TI Lookup, and community-driven malware analyses.
View sample report on APT41 Attacks
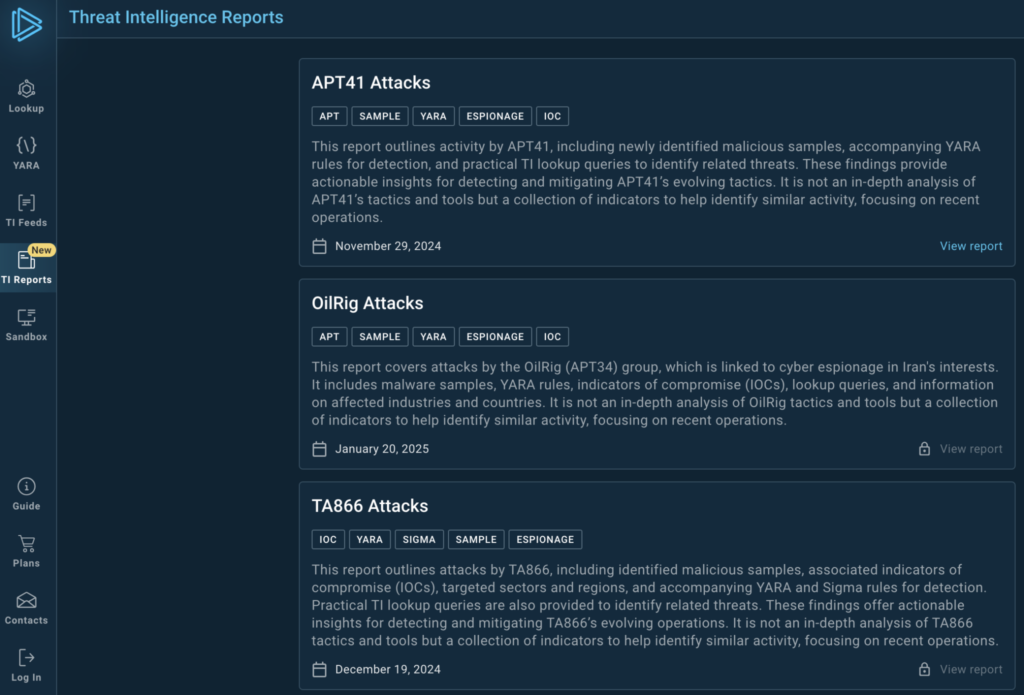
How to access TI Reports
Paid TI Lookup users get full reports, while summaries and select reports are available for free.
- Go to intelligence.any.run.
- Click the TI Reports icon on the left.
- Select a report from the feed.
New reports are marked with a “New” badge for quick access.
What’s inside TI Reports?
Each report provides a detailed threat overview, covering key aspects such as:
- Threat actor or malware profile: Origins, objectives, targeted industries, and regions.
- TTPs: Methods used by attackers, helping in detection and mitigation.
- IOCs, IOBs, IOAs: Critical data for identifying threats in your environment.
- YARA and SIGMA rules: Ready-to-use detection rules for security systems.
- Sandbox analysis links: Direct access to real-world threat samples in action.
- Additional references: Supporting research and external resources for deeper insights.
New Website Design: A More User-Friendly Experience
In February, we introduced a redesigned ANY.RUN website, making it more intuitive, structured, and easier to navigate. The new design makes sure that all essential cybersecurity resources and solutions are now better organized and easily accessible.
Whether you’re exploring threat intelligence, running sandbox analyses, or researching cybersecurity insights, the updated layout enhances usability for both security experts and new users.
Threat Coverage Updates
Suricata Rules
In February, we added 314 new Suricata rules, strengthening our network-based threat detection. Notable updates include:
- A Booking.com phishing rule, designed to detect fraudulent activity targeting users.
- A rule for Australia Gov phishing attempts, though it covers only partial cases due to dynamic URL changes and regional access restrictions.
New Behavior Signatures
This month, we expanded behavior-based detection, adding new mutex findings, threat detections, and suspicious activity signatures. These updates improve the ability to track malware persistence mechanisms and evasive techniques in real-time.
New Malware & Threat Detections
Suspicious Activities & Evasion Techniques
- Disabling Windows security features:
- Firewall
- SmartScreen
- Task Manager
- Command Prompt
- Remote Desktop Access
Additional Mutex Detections
- Darkside, Crytox, Xtreme, Funlocker, Redlocker, Roblox, Aida64, Smartsteamemu, Processlasso, Cactus, Phobos
- Nitrogen (mutex & detection)
- Various software-related mutex detections, including COYOTE mutex, Proxifier, Wireshark, Java, Adguardvpn, Cheatengine, Opera, Electron Js, Adobeinstaller, Hotbar, Quickdriverupdater, And Pcappstore
New YARA Rule Updates
In February, we expanded our YARA rule database, enhancing malware detection and classification. The latest rules target a variety of stealers, RATs, ransomware, and loaders, improving detection accuracy for emerging threats.
- Spearal
- Veaty
- Clipog
- Cerbfyne
- Funklocker
- Redlocker
- Cloudscout
- MillenniumRAT
- JasonRAT
- Meduza
- CelestialRAT
- RansomHub
- Xorist
- Hellcat
- HKBot
- MiyaRAT
- Zhong
- DarkTrack

Sandbox for Businesses
Discover all features of the Enterprise plan designed for businesses and large security teams.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.








0 comments