Welcome back to ANY.RUN’s monthly update series where we keep you in the loop on the progress we’ve made.
Continuing from last month, the team at ANY.RUN has been hard at work. We’ve rolled out more features, ramped up our threat detection capabilities, and added new rules.
Let’s dive into the details.
Product updates
New detection logic for IP, URL, Domain. The overhauled logic enables more robust detection of malicious IPs, URLs, and domains.
New malware config extractors and fixes
We’ve added support for several new malware and improved detection capabilities for families that were already supported.
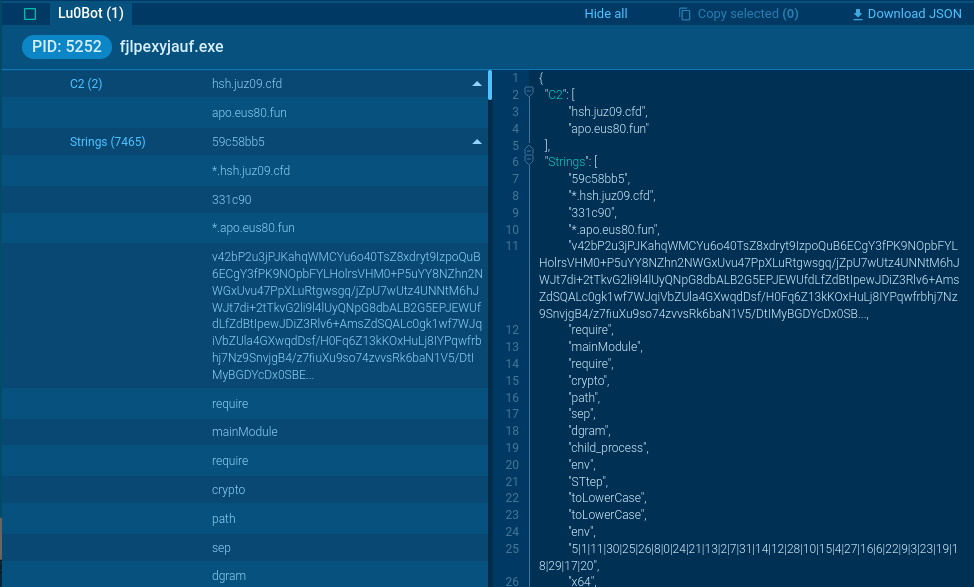
Lu0Bot support
Lu0Bot uses Node.js and heavily obfuscates its code. It starts by unpacking an SFX file, passes byte data to node input, then decrypts and executes the main JS code. Functions include string decryption using its own cipher suite like base64 and RC4, domain assembly, PC info collection, and AES-128-cbc encryption for traffic.
Strela extractor and new YARA rules
Strela is a stealer that specializes in stealing email credentials from Thunderbird and Outlook applications. The malware itself is relatively simple, but its analysis is complicated by the packer layer.

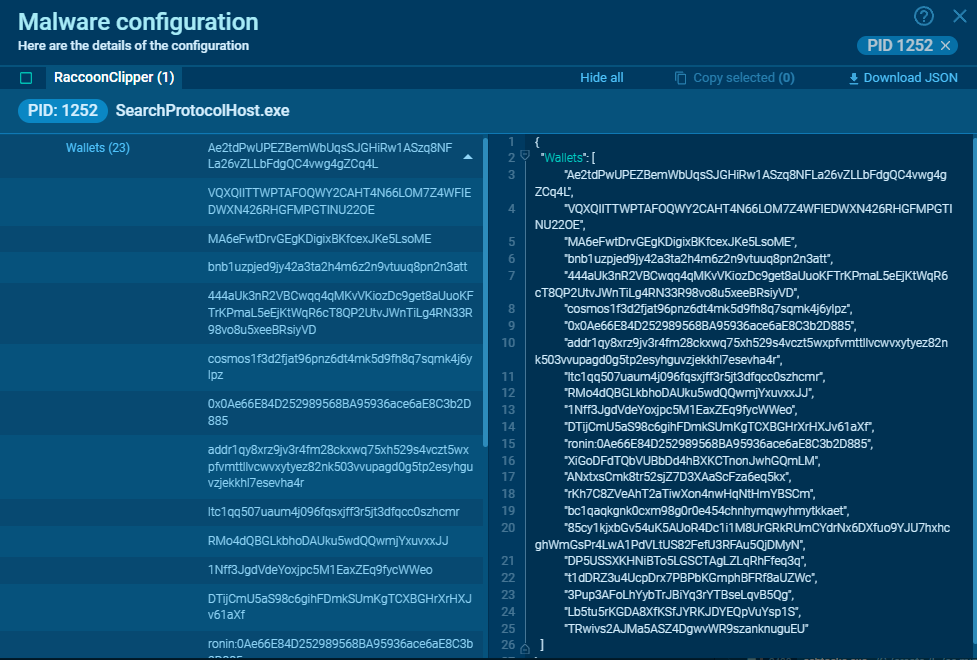
RaccoonClipper extractor and new YARA rules
RaccoonClipper is a clipper from the developers of RaccoonStealer. This malware accesses the clipboard and swaps cryptocurrency wallets of its victims with wallets belonging to the attackers.
Fixed extractor and rules for LummaStealer
We’ve updated LummaStealer rule and extractor to handle the changes implemented in the latest versions of this malware family:
- No longer includes build number in newer versions.
- Supports additional C2s, with priority given to mirror domains.
- Server response now in plain text, containing base64 encoded XOR key and JSON config.
- Operates in both stealer and bootloader modes.
- Hash included in config if mirror exists; “default” used if not.
The fix also addresses sample processing issues. In addition, config extraction is now compatible with the latest LummaID and C2 formats.
Additional updates and fixes
We’ve added a rule to detect KrakenStealer, also known as KrakenKeylogger, which is simply called Kraken. Written in .NET (VB), this malware steals browser data and account information, operates as a keylogger, takes screenshots, and lacks obfuscation. While many AV vendors incorrectly label it as SnakeKeylogger or MassKeylogger, our team made sure not to make that mistake. The malware sends data using one of the selected methods: SMTP, FTP, Telegram.
Another implemented small fix was related to AZORult. Some samples weren’t processed by the extractor; this issue is now resolved. However, samples often complete before the extractor does.
More additions include:
- Updated extractor and YARA for GO LaplasClipper variations
- Updated RaccoonStealer extractor and YARA
- Updated extractor and YARA for StealC
- Updated Remcos extractor and YARA
- Separated tags between StormKitty and AsyncRAT
- Added support for extracting configuration from new XWorm types.
Network rules
In August, we focused on network rules heavily, writing 120 new Suricata rules. Here’s some of the work that is worth highlighting:
New rules for detecting PovertyStealer activity: our rules for PovertyStealer were updated due to changes in the malware’s behavior. Check out the task on ANY.RUN for details. Big thanks to the community and g0njxa on Twitter for catching this change. Our detection updates are shared here.
August’s improvements in phishing detection. In August, we amped up our research on phishing, resulting in 51 new network rules. We analyzed extensive data sets from saved phishing sites, scavengers, and author tags. Our work in phishing detection is ongoing.
Fine-tuning file sharing policy violations. To avoid false positives, the rules related to file downloading from sharing services were calibrated. We now estimate the number of bytes received, ensuring we’re not flagging every service call.
Expanded clipper malware detection. Added rules to catch the new Raccoon Clipper Activity variant. Have a look at the sandbox task here for more details.
.lnk file rule update. If a .lnk file contains a reference to an external DLL, you’ll now get notified via our new rule: SUSPICIOUS [ANY.RUN] Windows Shortcut File containing DLL on external server. Check out the basis for this rule here.
BroExt payload and loader rules. We’ve rolled out new rules for BroExt. For payloads, we’ve flagged XORed Windows executables in Base64, with specific versions for BroExt and Oilrig. On the loader side, we’ve implemented a new rule focused on BroExt, potentially linked to Oilrig.
Rule update for Phemedrone Stealer detection. Phemedrone Stealer is now detectable via our newly implemented rule number 8000618. This enhances our ability to spot its reporting activities.
Extending coverage for Havoc C2. Our rules to detect Havoc’s modern command and control system is now extended. The new rule, BACKDOOR [ANY.RUN] Havoc (DEMON_MAGIC_VALUE), does the job. Take a look at a sample with decrypted traffic.
ICMP tunnel backdoor flagged. A backdoor using an ICMP tunnel and UDP traffic is now flagged under BACKDOOR [ANY.RUN] ShellcodeRunner. This threat previously appeared under Chinese names. More info is available here.
Monitoring Phoenix Miner activity. Phoenix Miner isn’t malware, but it’s worth noting its network activity. For this, we’ve rolled out the rule MINER [ANY.RUN] Phoenix Miner. Check it out here.
DBatLoader rule with unique detection technique. DBatLoader often uses unblocked channels like Discord and OneDrive. This August, we crafted rule number 8000634, utilizing forbidden bigrams in English, to catch 17 samples. Searches can be conducted using the rule number.
JsOutProx rule enhancements. JsOutProx is an intricate attack framework blending Javascript and .NET. We’ve updated our existing rules to catch minor variations in content and HTTP headers.
StealC rules updated. Five new rules for Win32/StealC have been rolled out. Community engagement helped refine these rules, and we’ve shared our finds here.
DarkGate loader detected. We’ve added a new rule, LOADER [ANY.RUN] DarkGate with the number 8000655, following the release of DarkGate’s new version in May 2023.
RootTeam Stealer adjustments. We updated our rules for RootTeam Stealer due to changes in its HTTP protocol data. Updates have been posted in the Emerging Threats community thread.
Mustang Panda’s PUBLOAD tool flagged. The APT group Mustang Panda updated PUBLOAD by adding an extra layer of Base64 encoding. We caught this and implemented new LOADER [ANY.RUN] PUBLOAD Activity rules.
New rule for Kraken Stealer. Kraken Stealer now has a specific rule in our repository for FTP exfiltration detection.
Casbaneiro loader variant covered. We’ve added a rule for a loader variant of Casbaneiro, the Latin American banking trojan. The new rule is LOADER [ANY.RUN] Casbaneiro sid: 8000716.
Rare stealer rule discovered via Twitter. A search on Twitter led us to a rare stealer. We’ve named the rule STEALER [ANY.RUN] StlFun and extended our thanks to crep1x on Twitter for the discovery.
Contributing to Emerging Threats Community
This month, we’ve continued submitting rules to the Emerging Threats community. Here’s the list of our main contributions:
Parallax RAT now detectable.Thanks to a Twitter tip, we identified previously elusive Parallax RAT traffic. Our new rule sid: 8000638, 8000643, 8000644 has been shared on the Emerging Threats community page and added to our repo.
Mekotio rules boosted. Mekotio, mostly active in Latin America, is now easier to catch thanks to several new rules. Find sandbox samples under the #mekotio tag. Our updates are also shared on the Emerging Threats community page.
New rule for DarkCloud stealer. We’ve pushed a proposed rule for DarkCloud stealer in the Emerging Threats community and implemented the STEALER [ANY.RUN] DarkCloud External IP Check. You can see the rule at work in this sample.
Wrapping up
Our team consistently monitors new threats to ensure that ANY.RUN’s detection capabilities remain at the forefront of the industry.
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.








0 comments