ANY.RUN is glad to surprise you with new service changes! Our focus is to make your analysis fast and easy. That’s why we carefully designed the logic of several windows and the MITRE ATT&CK Matriх. In this release, we’d like to introduce some helpful changes.
Update overview:
- MITRE ATT&CK Matrix’s redesigned logic
- Considered groups with sub-techniques
- Improved “Techniques details” window
- Service usability improvements
The MITRE ATT&CK Matrix
Analysis in ANY.RUN has become more structural, intuitive, and convenient. Here are some changes that we’ve done to achieve it:
- A clear view of the techniques groups.
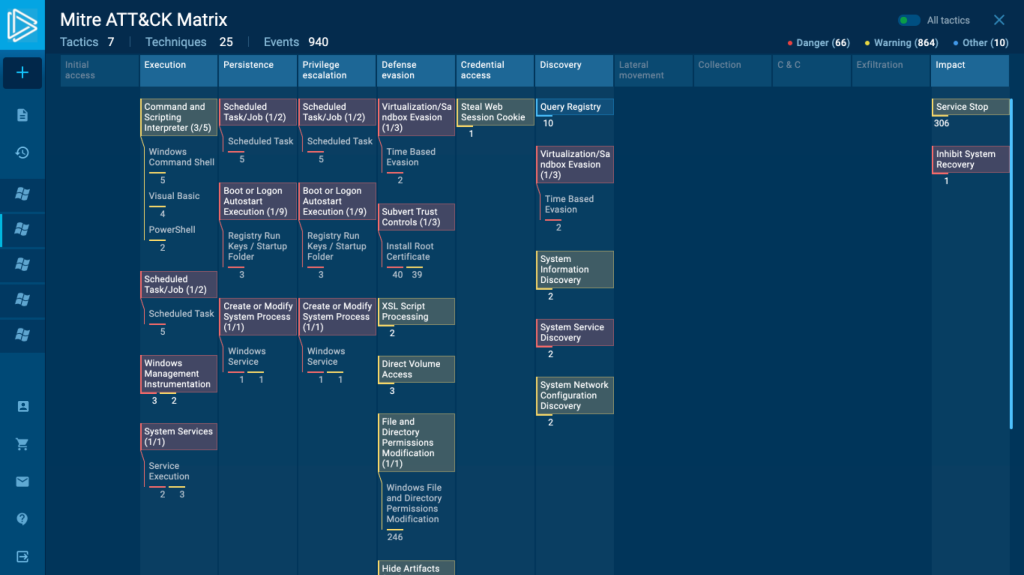
The MITRE ATT&CK Matrix is constantly growing and expanding. Many new techniques appeared both in the large and small scope. That’s why the ones that cover more specific and narrow activities have become sub-techniques.
For example, there were 3 tactics: spearphishing attachment, spearphishing via service, and spearphishing link. All of them are about common but specific actions that cybercriminals can take. And now they are turned into sub-techniques and united under the Phishing technique.
If your task has identified the activity that concerns any of the techniques, you will see the whole group with sub-techniques and how many of them are malicious.
This clear demonstration allows you to understand immediately where and what is happening in the task. Just open the matrix, and your analysis has already started. It’s that simple.
- Fast estimation.
When you open the matrix, the first thing that helps you analyze the threat is information at the top:
- Tactics
- Techniques
- Events.
The number in these categories gives you a complete picture of the way malware acts. At the very start, you already know what to expect from it, how big it is, and others.
- Event filter.
Now there are 3 filters of events: Danger, Warning, Other. Choose any of them to see the events you want to analyze. If you are only interested in malicious ones, use the Danger filter. Need to have a look at suspicious activities? Turn off Danger and Other, the Warning filter will show you exactly what you want.
- Color indication
All the technique groups have a color indication. If one of the sub-techniques includes malicious activity, then the whole group is in the Danger category, with red color. Yellow stands for Warning, suspicious behavior. And blue corresponds to Other. This kind of data sorting speeds up the time of your analysis.
Don’t forget that you can research all MITRE ATT&CK Matrix if you switch to All tactics. It also has groups and if you click on them, the list of sub-techniques will expand.
The detected techniques of your sample will be highlighted there as well.
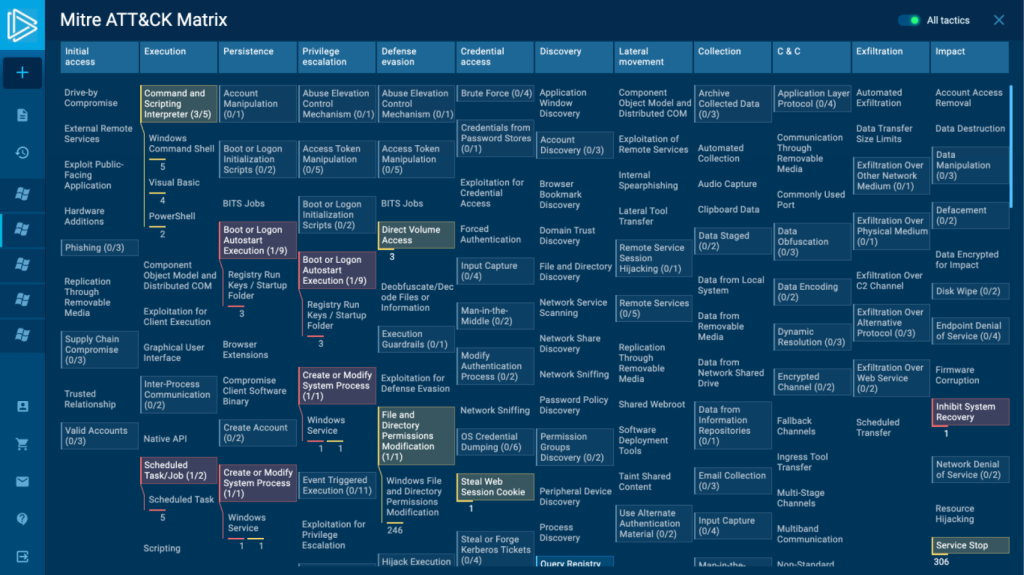
All these changes can simplify your work. Any analyst gets information about the investigated sample right away, just looking at the header and groups’ matrix.
Techniques details
The “Techniques details” window has acquired a new look. Besides that, there are some updates.
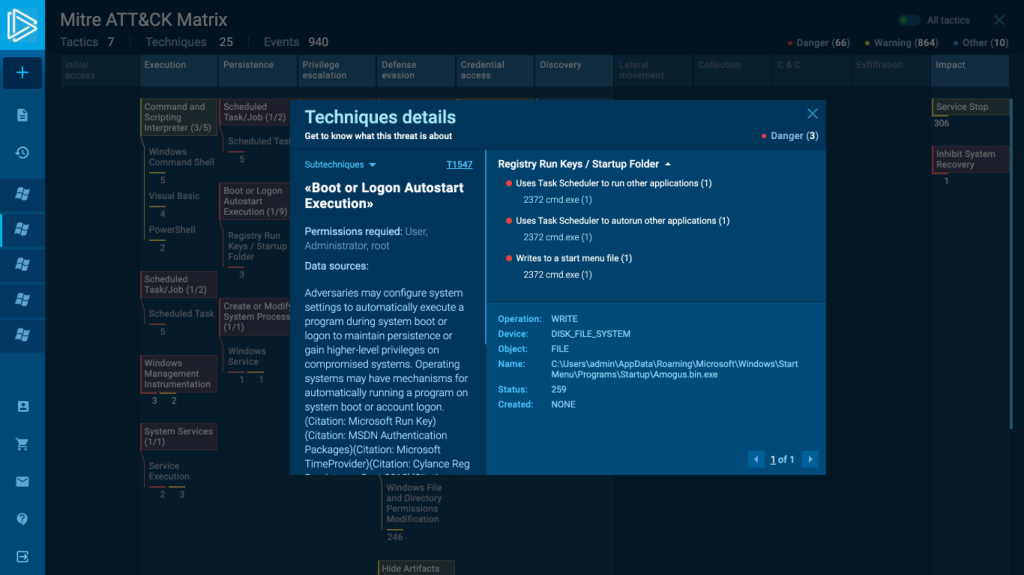
- First of all, you can see what type of activity this window is about – Danger, Warning, Other as the filter system works here. So you can switch between them as well.
- Go through all detected techniques in the task without closing the window. If you click on sub-techniques, you can switch between them. Don’t waste your time leaving this window and looking for the next technique to open. Work here and see them all in one place.
- Furthermore, we have additional information here besides the basic technique description.
“Permission required” and “Data Source” are at the very top for you. Techniques may ask for different permission in the operating system for execution. For example, administration, system, or user permission is necessary to run a task.
If you need to find where the task execution can be detected, here is the “Data Source” information. This window has all details that are important for your research, and you don’t have to look for it somewhere else.
- Events are also grouped here and under each of them, you can see processes. If a group or a process repeats, there will be an exact number of them. This new approach helps to organize information and see not a long list of processes but helpful data.
- Expand and collapse lists of processes. Also, choose the area of groups or process details and resize the needed one to see more data.
The ID of all sub-techniques has also changed, so keep it in mind during your investigations.
Please remember that you can find and research fresh samples in Public submissions using newly added techniques in the MITRE ATT&CK Matrix.
That’s all for today, so it’s time to go and check out these changes by yourself! Feel free to write comments down below or share your feedback on our social networks. ANY.RUN team is committed to giving you the best experience in the service, so your opinion is very important for us. And check back here for future updates!








0 comments