Malware often uses custom mutexes. We’ve released an update that allows you to search for these mutexes in TI Lookup and add them to your IOCs.
What’s more, the tasks in the search results make it easier to distinguish between malicious and legitimate mutexes, which can significantly speed up your threat investigations.
Let’s explore this new functionality with an example to better understand how it works.
Example: DCRat
To find mutexes used by DCRat, you can use this query in ANY.RUN:
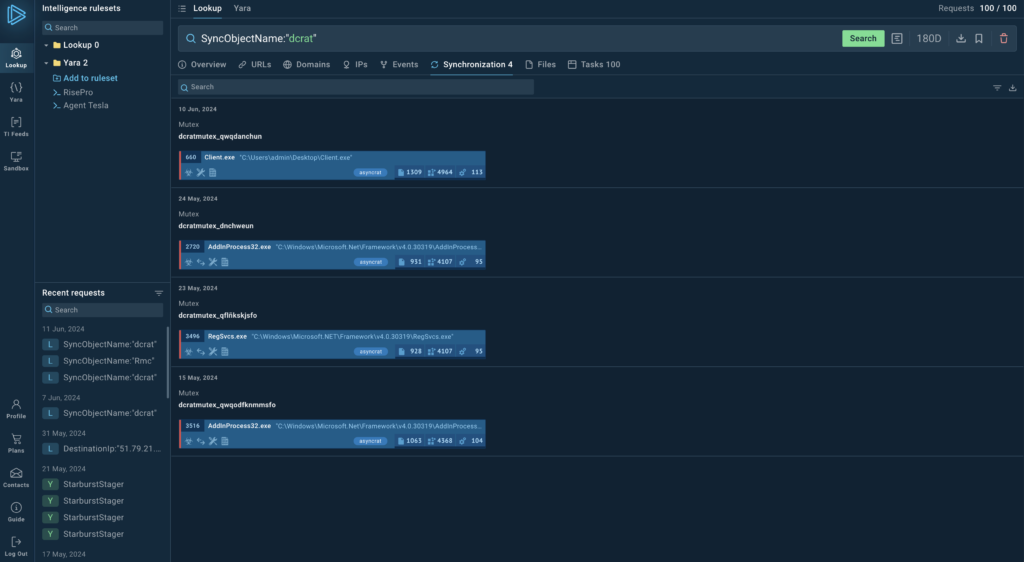
Go to the ‘Synchronizations’ tab to isolate the list of mutexes.
ANY.RUN’s TI Lookup makes it easy to go from an overview of search results to a deeper investigation of a malware sample.
We can switch to the Tasks tab to see a list of analysis sessions where that sample was recorded.
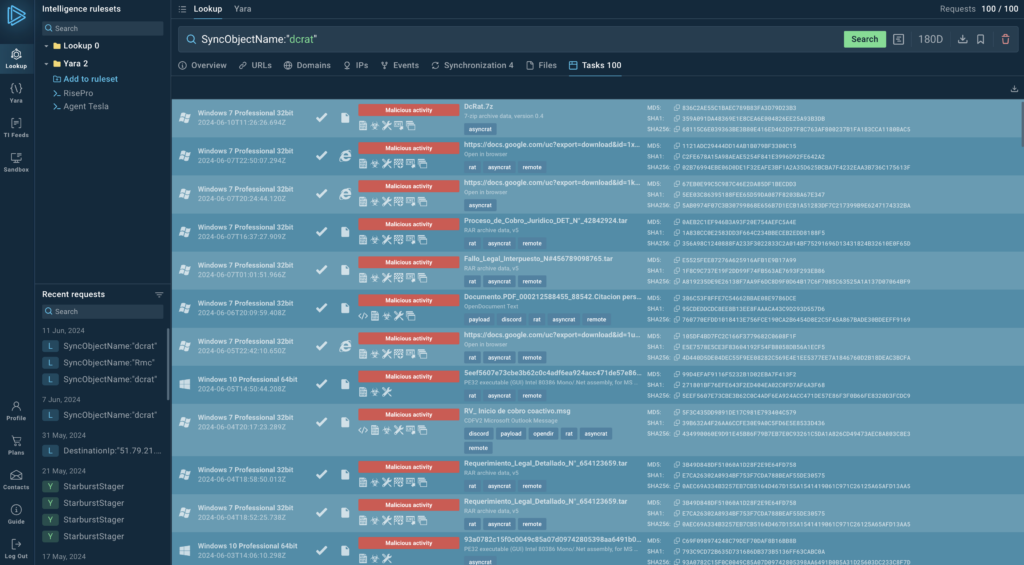
But the result shows lots of AsyncRAT instances. What’s going on?
That’s because DCRat and AsyncRAT share a lot of the same codebase, which can trick antivirus software and malware sandboxes into confusing them with each other.
We will identify DCRat by doing a little bit of research in the sandbox:
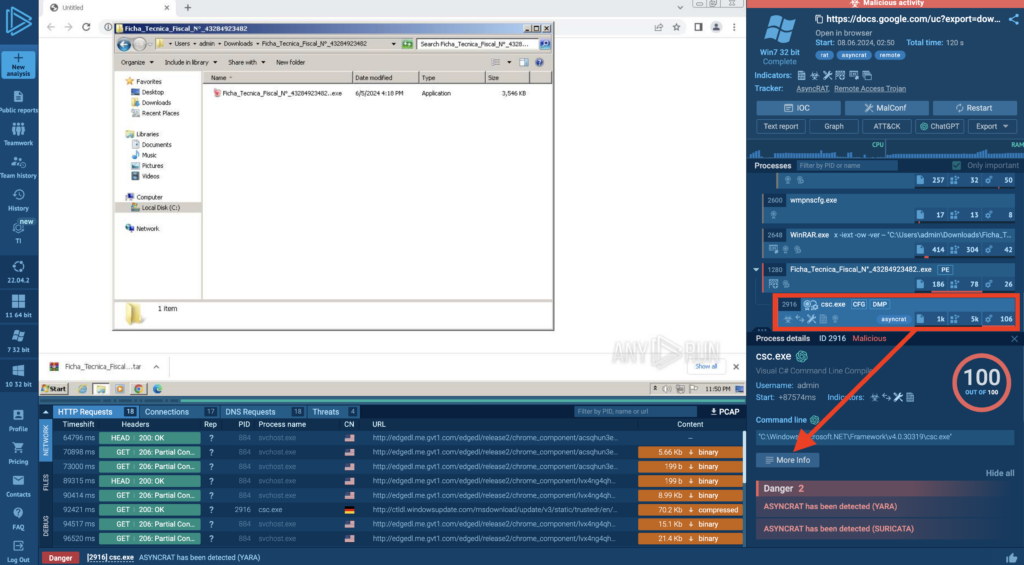
Open one of the analysis sessions from the resuts, and then go to Advanced process details, as shown above.
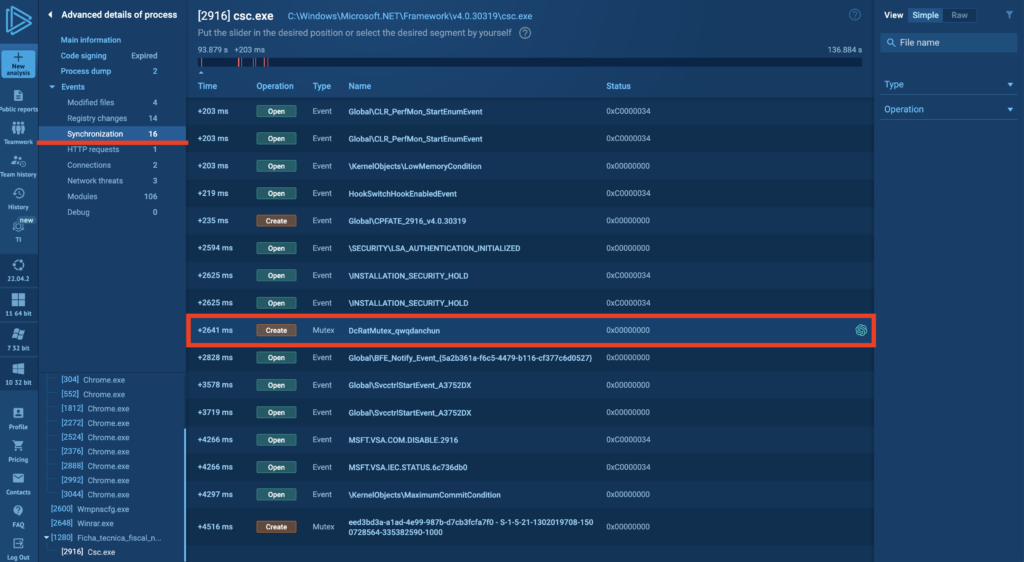
One way we can identify DCRat is to look at the PBKDF2 salt value using a tool like dnSpy, check the decrypted configuration where the mutex contains something like DCstringRatMutexqwqdan3chun, or analyze the X509Certificate.
More examples
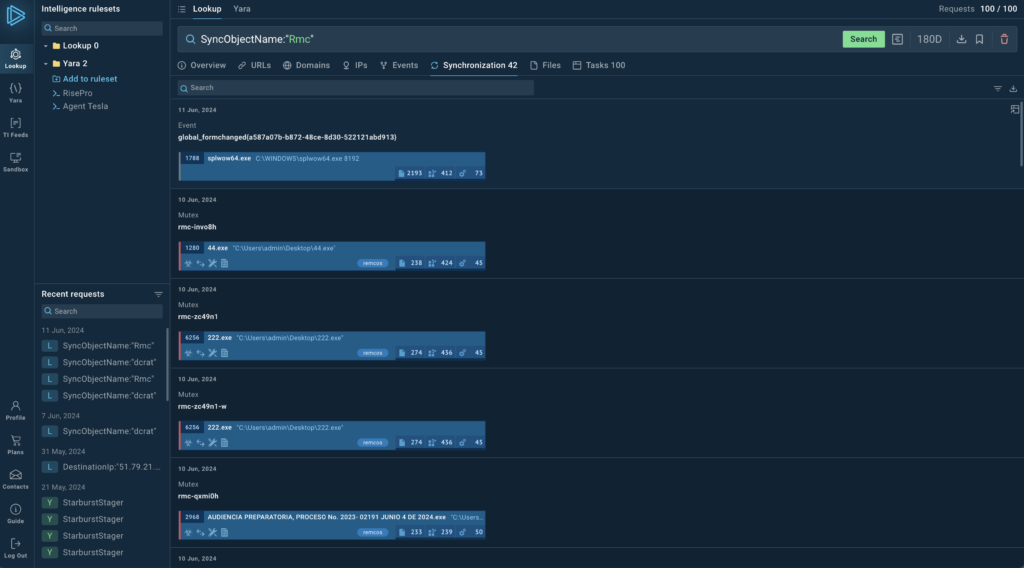
We can find mutexes used by Remcos with this query:
And here are the results of running that search in the TI Lookup:
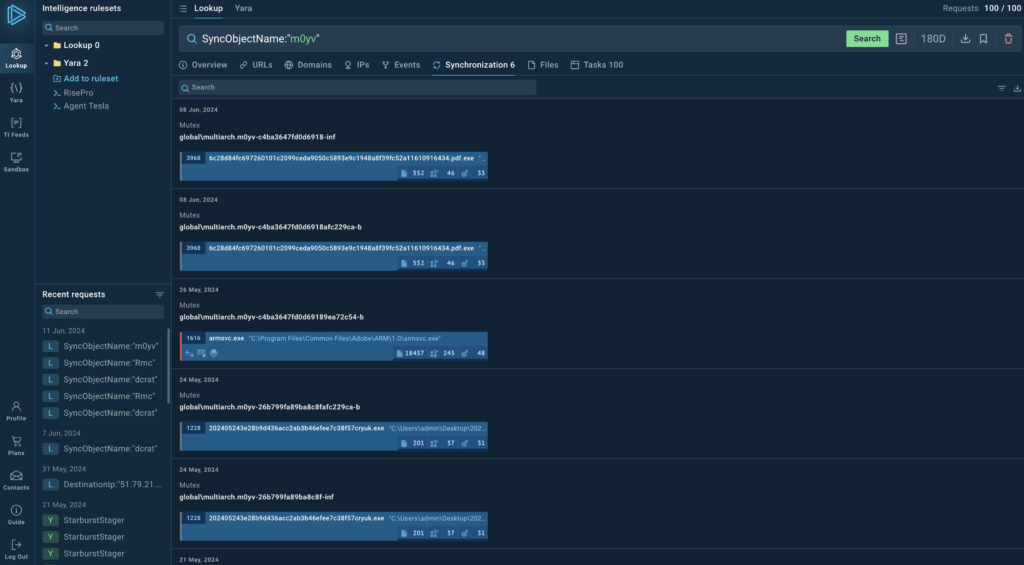
To find DarkGate mutexes, we can use this query:
And the screenshot below shows the search result:
What are mutexes and why should you investigate them?
Mutexes (short for mutual exclusion objects) are kernel objects that allow only one process or thread at a time to access a shared resource or critical section of code.
Malware often uses custom mutexes to ensure that only a single instance is running and to communicate between components.
Mutexes can tell you how a piece of malware interacts with the system, help you identify the specific threat family, or you can use them as IOCs to detect malware.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Advantages of ANY.RUN
ANY.RUN helps you analyze threats faster while improving detection rates. The platform detects common malware families with YARA and Suricata rules and identifies malware behavior with signatures when detection by family is not possible.
With ANY.RUN you can:
- Detect malware in under 40s.
- Interact with samples in real time.
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior.
- Collaborate with your team
- Scale as you need.
Try the full power of ANY.RUN for free








0 comments