Security systems assign generic threat labels to files that appear malicious but don’t exactly match any known threat. Let’s discuss why and when this happens.
When antivirus, SIEM, or SOAR products scan files for signs of malware, they use several methods, including signature-based detection. This approach involves comparing the hash of the file being checked against a database of known malware threats, like ANY.RUN’s Threat Intelligence.
When an antivirus detects a file, whose signature exactly matches the signature of a known malware, it typically labels the file with the specific name of that malware, such as “Trojan:Win32/Emotet”, though specific label depends on the provider.
What exactly is Win32:Malware-gen?
“Win32:Malware-gen” indicates a generic threat that targets Windows 32bit operating system. Generic threats are files that appear suspicious to antivurs products, but don’t match any known threat.
Since antiviruses use a variety of methods to detect malware, they can assign the Win32:Malware-gen label to files under several circumstances. Here’s a list of cases when suspicious files might receive this label:
Closely matching signature-based detection
Malware authors frequently release updates to their software. These new variants might have minor modifications in their code that change their signatures just enough to not exactly match the known signatures in antivirus databases. In such cases, if the antivirus detects that the file closely resembles known malware but doesn’t match precisely, it may use a generic classification to indicate a general threat.
Results of heuristic analysis
Heuristic analysis involves examining the behavior of files to identify suspicious actions commonly associated with malware: modifying system files, installing unauthorized software, or attempting to hide presence on the system. If a file exhibits such behaviors, it can be classified as “Win32:Malware-gen,” even if it doesn’t match any known malware signature.
File attributes and metadata
Attributes like the file’s origin, modification dates, and whether a file has a digital signature from a trusted source can influence its assessment. Files lacking transparency about their origin or exhibiting irregularities in their metadata might receive “Win32:Malware-gen” classification.
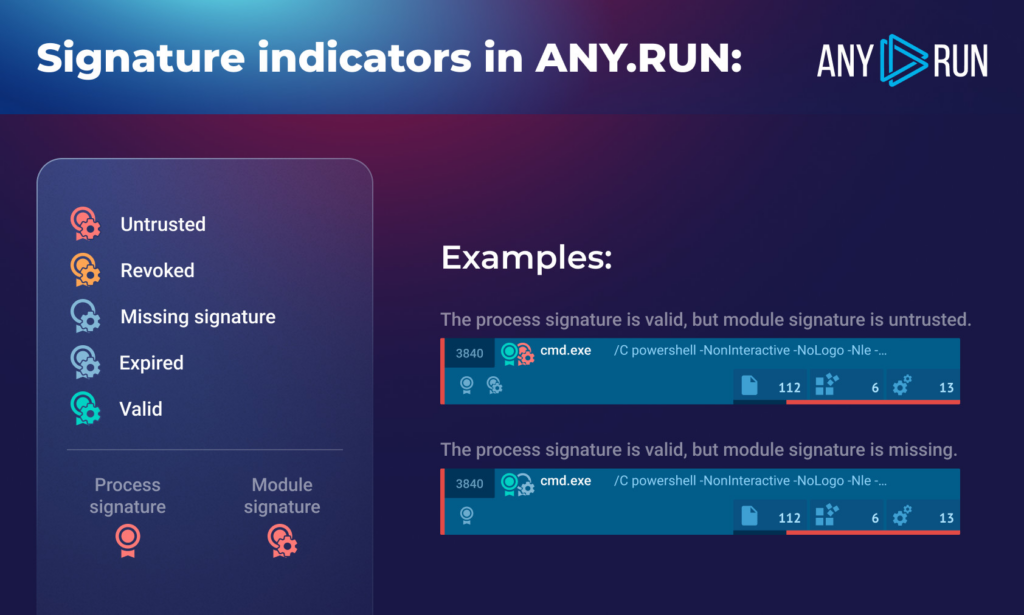
For example, in ANY.RUN, you can easily see tampered, expired or missing signatures both for files and modules. Signature icons inside of the process tree is one of many tools our interactive sandbox gives analysts and malware researchers to identify malicious files and executables.
Context and behavior in the system
Unauthorized network connections or modifying registry entries without user consent are examples of suspicious behavior. The antivirus software assesses the file’s behavior within the ecosystem of the user’s computer, looking for patterns that typically indicate malicious intent. When found, such files might get the “Win32:Malware-gen” label.
What software uses the Win32:Malware-gen label and what other labels exist?
“Win32:Malware-gen” is associated with Avast and AVG products (the latter merged with Avast in 2016). Other programs may use slightly different naming conventions for similar generic tags. Here are a few examples:
- Symantec (Norton): Uses names like “Trojan.Gen.2” or “Suspicious.Insight”. The “Gen” suffix indicates a generic detection of a trojan, while “Suspicious.Insight” is based on their reputation-based insight system.
- McAfee: Labels such threats with names like “Artemis!” followed by a unique identification string.
- Kaspersky: Utilizes labels such as “HEUR:Trojan.Win32.Generic”.
- Microsoft Defender: Microsoft’s integrated antivirus solution might classify generic malware under names like “Trojan:Win32/Dynamer!ac” or use terms like “SoftwareBundler:Win32/Prepscram”.
- Malwarebytes: Labels potential threats with “Malware.Generic,” followed by a series of numbers.
Verdict system in ANY.RUN
ANY.RUN interactive malware sandbox is not an antivirus, rather, it’s software used to better understand behavior of malware by running and observing it in realistic environments. We use a verdict system with No threats detected, suspicious and malicious classifications, instead of generic labels. That’s because our sandbox allows for very detailed behavioral analysis, and we can accurately pinpoint malicious actions.
When our interactive sandbox is able to identify a specific family, either from memory dumps, signatures, Yara rules or behavioral patterns, the threat also receives a family classification tag.
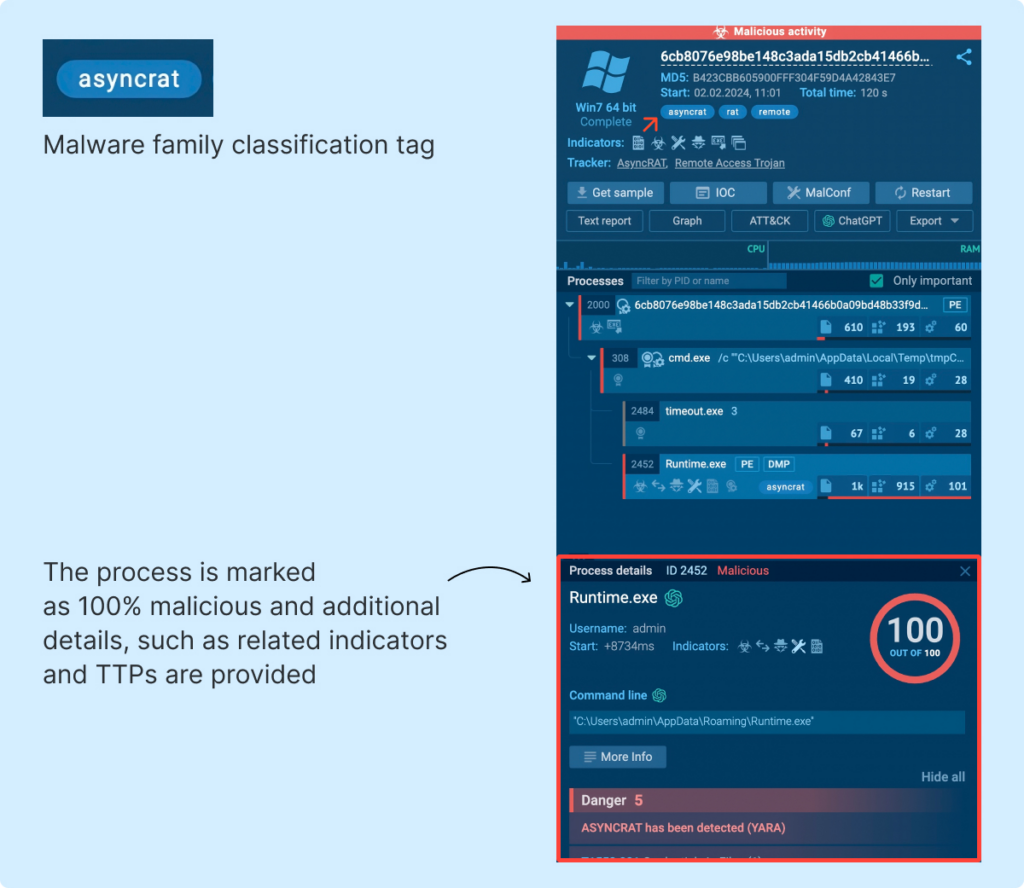
For example, this ANY.RUN task received a 100% malicious score, and AsyncRAT was identified from a memory dump.
Wrapping up
In conclusion, “Win32:Malware-gen” is a generic label used by antivirus programs to identify files that seem suspicious but don’t exactly match any known malware signatures.
- Generic threats are identified using multiple analysis techniques: files are tagged as “Win32:Malware-gen” when they closely resemble but do not exactly match known malware signatures, when heuristic analysis shows suspicious behavior, or according to metadata like missing or expired file or module signatures, as well as in other scenarios.
- There are many generic labels, and these depend on the security system provider: “Win32:Malware-gen” is associated with Avast and AVG products, but other systems have similar tags.
- There are not generic labels in ANY.RUN: Our interactive sandbox doesn’t rely solely on generic labels but uses a more detailed behavioral analysis to identify malicious actions, allowing for more specific threat identification.
About ANY.RUN
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.








0 comments