Welcome to the March 2023 edition of our monthly malware analysis news report. We’ve compiled some of the most significant security events and emerging threats that took place over the past month to keep you informed and help you stay one step ahead of cybercriminals.
Let’s dive into some of the key highlights and developments in the world of malware and cybersecurity.
1. Outlook Vulnerability (CVE-2023-23397) and Mitigation Steps
A new Microsoft Office Outlook vulnerability, CVE-2023-23397, has been identified.
This vulnerability enables threat actors to steal user account credentials, including the NTLM hash value, upon receiving an email and triggering a notification. Attackers can exploit this information for internal propagation and further system compromise.
Users can mitigate the vulnerability by disabling the ‘Reminder’ feature in MS Outlook. However, caution is advised as the vulnerability can still be triggered if the sound is played by checking ‘Play this sound’ on a malicious email.
2. LummaC2 Infostealer Disguised as Illegal Cracks
A new infostealer called LummaC2 is being distributed disguised as illegal cracks and keygens.
Similar to other malware such as CryptBot, RedLine, and Vidar, it has been available for purchase on the dark web since early this year. LummaC2 uses obfuscation techniques and anti-sandbox measures to evade detection and hinder analysis. It targets browser data, browser extensions, cryptocurrency wallet programs, system information, email clients, and other applications for theft.
The distribution method involves users searching for a crack or serial key for popular software, leading them to a malicious website. After clicking the download button, users are redirected several times before reaching the malware distribution page. The malware is then downloaded in a compressed format, either through the threat actor’s server or services like MediaFire or MEGA.
3. New IcedID Variants Focus on Malware Delivery Instead of Bank Fraud
Recent IcedID malware variants have shifted focus from online banking fraud to installing further malware on compromised systems.
Proofpoint has identified two new IcedID loader variants, “Lite” and “Forked,” which deliver the IcedID bot with a narrower feature set.
By removing unneeded functions, these variants become stealthier and leaner, helping threat actors evade detection. The “Lite” variant appeared in November 2022, while the “Forked” version emerged in February 2023. Proofpoint predicts the use of new IcedID variants will likely grow, with more variants possibly emerging later in 2023.
4. CatB: a new Ransomware Strain Discovered
CatB is a new ransomware family with unique characteristics, including performing basic evasion checks before executing its loader component to avoid running in an analysis environment like a sandbox.
Once the checks are passed, the payload containing the ransomware is executed via a DLL Side-Loading attack using a trusted Windows service.
CatB searches for user-specific files to encrypt, but unlike other ransomware families, it prepends the ransom note to each encrypted file instead of dropping it in separate files in various locations. The malware uses anti-VM techniques to hide its behavior from analysis environments, making it more challenging for security researchers to study its operations.
Emotet malware is now targeting US taxpayers by impersonating W-9 tax forms allegedly sent by the Internal Revenue Service and companies taxpayers work with.
5. Emotet Malware Targets US Taxpayers with Fake W-9 Forms
This notorious malware infection is distributed through phishing emails, which in the past contained Microsoft Word and Excel documents with malicious macros. However, with Microsoft now blocking macros by default, Emotet has switched to using Microsoft OneNote files with embedded scripts to install the malware.
Once installed, Emotet steals victims’ emails for future reply-chain attacks, sends spam emails, and installs other malware that grants initial access to threat actors, such as ransomware gangs.
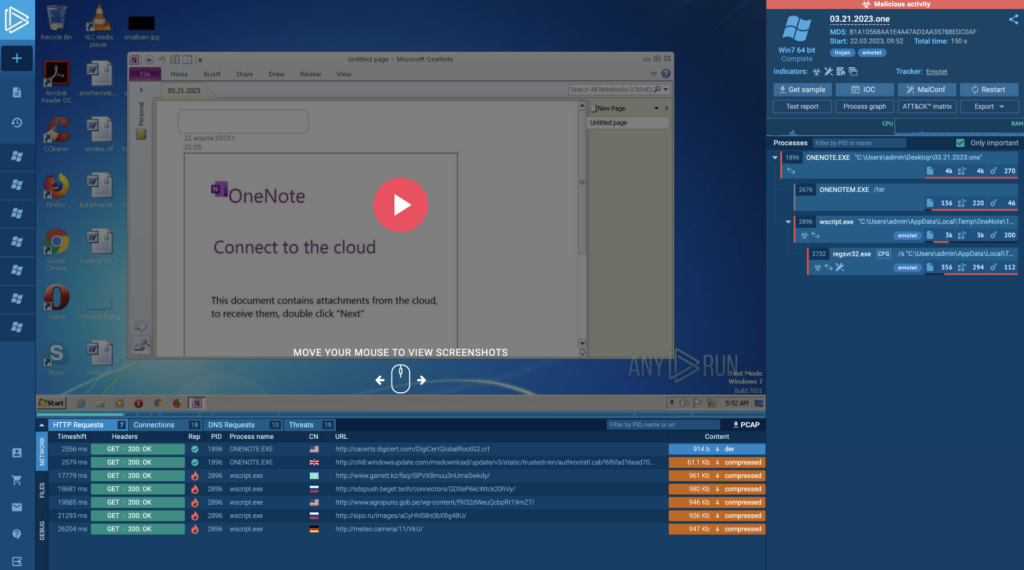
Emotet — which holds a spot in the top 5 of most popular malware families (according to our monthly submissions data at the time of writing) — can evade discovery by waiting for user interaction to start executing. This tactic means that its detection in an automated sandbox is not guaranteed.
We successfully activated the malware and gathered the following:
Indicators of Compromise (IOCs)
| SHA256 | e173ecebfd5b01766dd8184250d5f2d442507b9b097e4ced319c246b78550d85 |
| SHA1 | dd6ba6ae1680e4245f5ecc22ee12a18b9e16db2d |
| MD5 | b1a10568aa1e4a47ad2aa35788edc0af |
Domains
| sipo.ru |
| sdspush.beget.tech |
| www.agropuno.gob.pe |
| www.gomespontes.com.br |
| meteo.camera |
| www.garrett.kz |
| penshorn.org |
IP
| 186.202.153.5 |
| 209.126.85.32 |
| 187.63.160.88 |
Feel free to explore more DNS and HTTP requests and connections on the linked analysis page above. Alternatively, visit our public submissions page for more Emotet analyses.
In our recent analysis in ANY.RUN, a researcher detonated the malware by interacting with a OneNote document and dismissing a few system warnings. So, no matter what system you use, ensure that it also allows for interactivity or employs alternative methods for detecting user-triggered malware.
Try ANY.RUN for Enterprises
Combat new threats together – ANALYZE MALWARE IN A TEAM
6. New ‘HinataBot’ Botnet Could Launch Massive 3.3 Tbps DDoS Attacks
A new botnet named HinataBot has been discovered targeting Realtek SDK, Huawei routers, and Hadoop YARN servers to recruit devices for massive DDoS (distributed denial of service) attacks.
Researchers at Akamai discovered the botnet at the beginning of 2023 and believe it is based on Mirai, a notorious malware strain. HinataBot is under active development and has shown functional improvements and anti-analysis additions.
The botnet can potentially perform powerful DDoS attacks using HTTP and UDP floods. With 10,000 nodes, the attack data volume could reach 3.3 Tbps for UDP floods and generate 20,400,000 requests per second for HTTP floods. As HinataBot’s development remains active, more potent versions may soon appear in the wild.
7. CASPER Attack Steals Data Using Air-Gapped Computer’s Internal Speaker
CASPER is a new covert channel attack that can steal data from air-gapped computers using their internal speakers.
It transmits high-frequency audio inaudible to humans, up to 1.5 meters away, to a nearby smartphone or laptop microphone. Malware must first be installed on the target, and the maximum reliable transmission bit rate is 20 bits/s. To defend against CASPER, remove internal speakers from mission-critical computers or implement a high-pass filter to block ultrasound transmissions.
8. Kimsuky Group Distributes Malware via Fake Profile Template on GitHub
A malicious Word file distributed by the Kimsuky Group, disguised as a profile template was found in the wild.
The password-protected file, named ‘[Attachment] Profile Template.doc,’ contains a malicious VBA macro. When activated, it connects to a C2 server via PowerShell, downloading and executing additional scripts.
The malware collects information saved on browsers, similar to the one found in a previously discovered Malicious Word Document. However, unlike the previous version, which used FTP to leak user credentials, this altered script uses the GitHub API to transmit the information to a specific repository. The Red Eyes threat group (also known as APT37 or ScarCruft) has recently been found using GitHub as their malware distribution site as well.
Users are advised to exercise caution as these scripts continue to evolve.
ANY.RUN March news
March proved to be an eventful month for ANY.RUN, and if you haven’t had a chance to catch up on our latest news, now is the perfect time before we jump headfirst into April!
We shared a comprehensive analysis of LimeRat, explored the potential impact of AI on the development of super malware, and discussed how ANY.RUN assists large security teams in staying coordinated daily, and reported on our participation at GISEC 2022 in Dubai.
- How Threat Intelligence Helps Protect Financial Organizations from Business Risk
- Release Notes: Workflow Improvements, MISP Integration & 2,000+ New Detections
- Enterprise Phishing: How Attackers Abuse Trusted Microsoft & Google Platforms
- SOC & Business Success with ANY.RUN: Real-World Results & Cases
1 comments













Thanks, for the awesome post ?