Do you struggle to connect the dots between multiple artifacts linked to the same incident because your threat intelligence solution doesn’t support combined searches? ANY.RUN’s Threat Intelligence Lookup fixes this problem for you. The service’s advanced search capabilities let you craft complex queries featuring more than one indicator at the same time. Let us show you how.
What is TI Lookup?
For those who are new to TI Lookup, it is ANY.RUN’s threat intelligence portal designed to help security analysts and researchers contextualize and enrich indicators of compromise (IOCs). It serves as a solution for gathering, analyzing, and understanding emerging and persistent cyber threats.
TI Lookup runs on the information extracted from the ANY.RUN sandbox’s public database of millions of interactive analysis sessions (tasks), launched by users from all over the world. Thanks to this integration, you get to search for contextual information across over 30 different fields, including destination IP addresses, file hashes, as well as command lines, MITRE ATT&CK TTPs, and Suricata rule class.
On top of receiving valuable context information, you also get to explore the sandbox sessions where IOCs of your interest were found. Thus, you can study the entire execution process of the malware (network and registry activity, processes, etc.), collect a comprehensive threat report, and even rerun the analysis in a different analysis environment to extract more insights.
Types of searches in TI Lookup
Before diving into combined requests, here are other types of searches you can conduct on Threat Intelligence Lookup:
- Single IOC: You can perform a search using a single IOC, examples of which include URLs, MD5, SHA1, SHA256 hashes, IP addresses, and domain names. By searching for a single IOC, you can quickly identify whether it is associated with any known malicious activity.
- Logged Event Fields: When investigating a potential cyber threat, you can target specific fields within logged events to narrow down your search. These fields can include command lines, registry paths and values, as well as process and module names.
- Wildcard Queries: To broaden or limit the scope of your search, you can use wildcard characters. These characters include the asterisk (*), caret (^), and dollar sign ($). Wildcard queries are particularly useful when dealing with limited or incomplete threat information. For example, if you only have a partial hash or URL, you can use a wildcard character to search for all possible matches.
- Detection Details: You can also search using MITRE techniques and detection names, including Suricata class, message, and Suricata ID. This information can help you identify specific types of threats and the techniques used by attackers.
How does combined search work?
Combined searches enable you to identify multiple instances of Indicators of Compromise (IOCs) or events occurring together within the same analytical session. This means that when you have several artifacts from the same incident, you can group them together and submit them for a combined search using Threat Intelligence Lookup. This approach not only accelerates your investigation but also leads to a more precise identification of the threat you are dealing with.
Examples of combined search requests
1. IP address and Destination Port
Suppose you need to investigate an alert about a suspicious connection involving some machines on your network attempting to connect to IP address 193.233.132[.]62 on port 50500. To determine quickly whether this poses a risk, you can combine these indicators into a single query using Threat Intelligence Lookup.
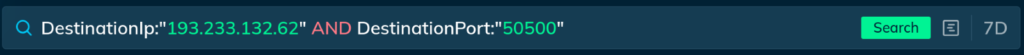
By constructing a request as shown in the image above and setting the search period to seven days, you will receive the following results:
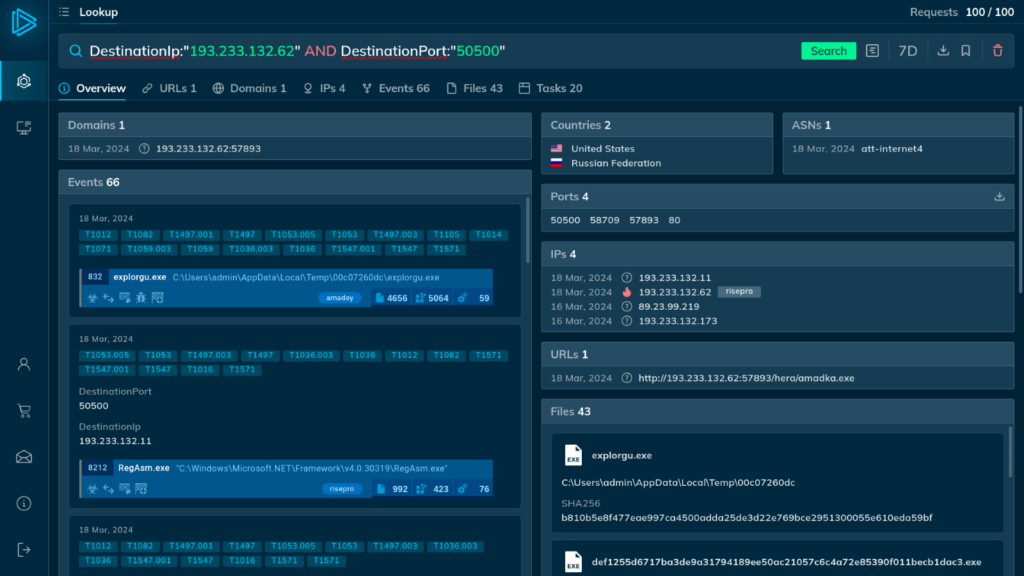
TI Lookup returns extensive contextual information, including events, IPs, files, and tasks.
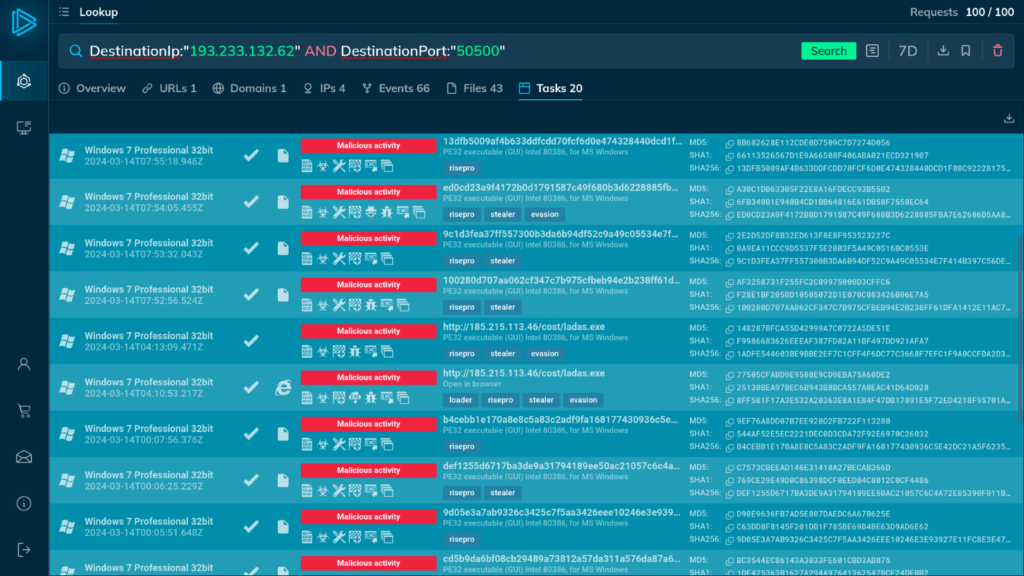
The results show that these indicators are associated with the RisePro malware. The service provides additional context about the threat and access to tasks that detail the infection process.
2. Domain Name and URL
Telegram bots have become a popular tool for attackers to automate and control malicious activities, such as command and control (C2) communication and data exfiltration. Criminals leverage Telegram API to create bots that blend in with legitimate traffic.
To find the latest reports related to Telegram bots, we can use a query that searches for all instances of the domain “api.telegram[.]org” and the “/bot” path in a URL appearing in the same analysis session.
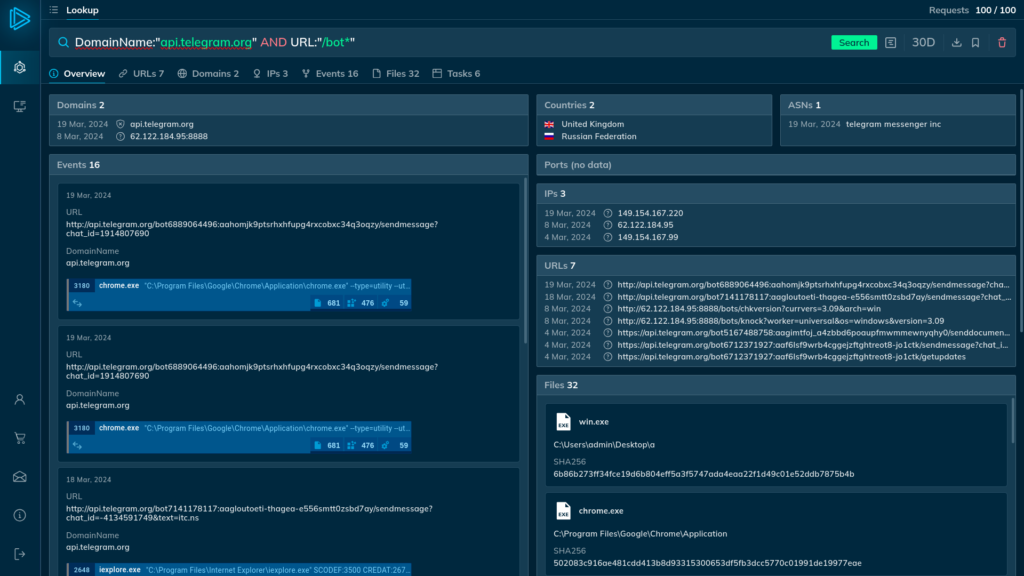
The results reveal plenty of valuable information, including URLs, files, events, IPs, and, most importantly, tasks related to the indicators mentioned in the request.
3. URL and Threat Name
Combined searches can help identify threats that use evasion techniques to avoid detection by sandbox environments. One such technique is checking if the environment uses hosting.
Attackers may employ this technique in phishing attacks to determine if their malicious URLs are being analyzed in a sandbox, allowing them to evade detection and extend the lifespan of their campaigns. ANY.RUN users can counter this evasion attempt by employing a residential proxy.
To find the latest instances of samples using this evasion technique, we can use the following request:
URL:"?fields=hosting$" AND ThreatName:"phishing" 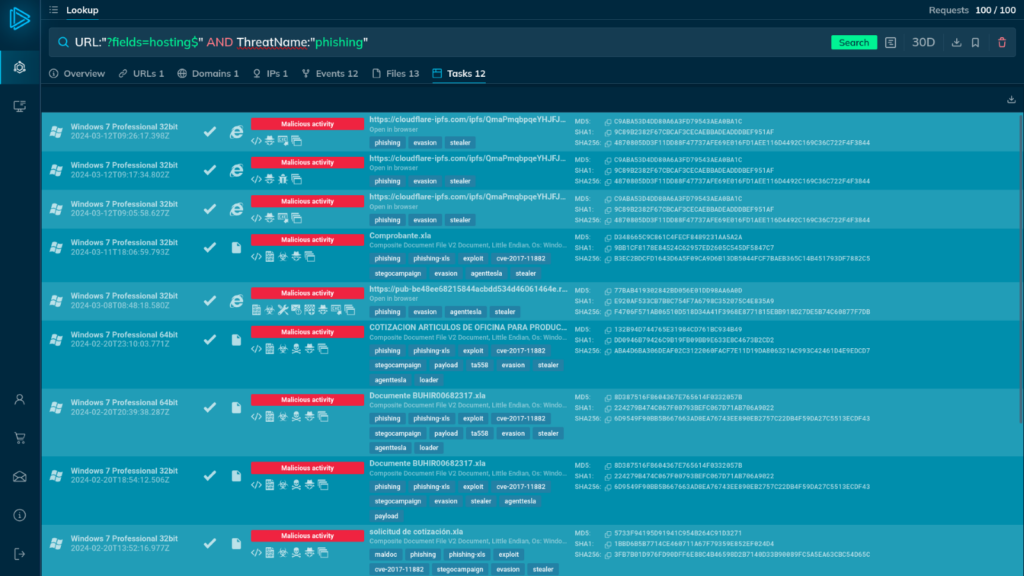
The search yields 12 tasks, each of which has been tagged as “phishing.”
Get a Demo of Threat Intelligence Lookup
Request a personalized demo of TI Lookup for your team and learn how it can benefit your threat investigations.
About ANY.RUN
ANY.RUN is a trusted partner for more than 400,000 cybersecurity professionals around the world. Our interactive sandbox simplifies malware analysis of threats targeting both Windows and Linux systems, providing analysts with an advanced tool for investigations. Our threat intelligence products, Lookup and Feeds, offer refined indicators of compromise and context that lets users detect threats and respond to incidents faster.
Advantages of ANY.RUN
ANY.RUN offers numerous advantages for businesses looking to improve their threat analysis capabilities, including:
- Rapid malware detection: ANY.RUN can detect malware and identify many malware families using YARA and Suricata rules within approximately 40 seconds of uploading a file.
- Interactive analysis: ANY.RUN’s interactive capability allows you to engage with the virtual machine directly through your browser, serving as a convenient tool for uncovering the inner workings of sophisticated malware all in the comfort of your browser.
- Cost-effective solution: ANY.RUN’s cloud-based nature eliminates the need for setup or maintenance by your DevOps team, making it a cost-effective solution for businesses.
- Intuitive interface: ANY.RUN’s user-friendly interface helps onboard new security team members by enabling even junior SOC analysts to quickly learn how to analyze malware and extract indicators of compromise (IOCs).
- Comprehensive analysis: ANY.RUN provides a detailed analysis of malware behavior, including network traffic, system calls, and file system changes, allowing security teams to gain a deeper understanding of the threat they are facing.
- Scalability: ANY.RUN’s cloud infrastructure enables businesses to scale their threat analysis capabilities as needed, providing flexibility and adaptability to changing business needs.
- Collaboration: ANY.RUN allows security teams to collaborate and share analysis results, improving communication and streamlining the threat analysis process.
- Integration: ANY.RUN integrates with popular security tools, such as SIEM systems and threat intelligence platforms, enabling businesses to incorporate ANY.RUN’s analysis capabilities into their existing security infrastructure.
Try ANY.RUN and see how it can help your security team.








0 comments