Ransomware groups are becoming bolder, targeting both government and corporate entities. At ANY.RUN, our sandbox is used by over 300,000 researchers who process tens of thousands of malware submissions every day, including ransomware. In this article we’ll aim to provide insight into the Calvià city attack and share information about the threat encountered.
What happened in Calvià?
You might have heard that in Majorca, Spain, the city of Calvià, a key tourist destination, has been hit by a ransomware attack, causing significant disruption to its municipal services.
Calvià, with a population of 50,000 and an annual tourist influx of 1.6 million visitors, has faced IT outages leading to the suspension of all administrative deadlines for submissions and requests until January 31, 2024.
Although no major ransomware group has claimed responsibility for the attack, local media reports indicate the attackers demanded €10 million (about $11 million). The mayor has stated that the city will not pay the ransom.
Despite the challenge, we at ANY.RUN consistently advise against complying with cybercriminals’ demands. Doing so only encourages them to continue their harmful activities.
The city’s mayor, Juan Antonio Amengual, revealed that IT specialists are working on a forensic analysis to understand the full scope of the breach and recover affected systems.
At this point, we know that the threat Calvià municipality faced was the LoсkBit ransomware.
What is LockBit Ransomware?
LockBit is a ransomware that primarily targets Windows computers but can also encrypt files on Linux and MacOS machines. It is operated by a hacker group that promotes it as the “fastest encryption software in the world.” LockBit is a Ransomware-as-a-Service (RaaS) operation, where they sell access to their ransomware on underground forums, contributing to its widespread use — this means that it is likely the attack on Calvià wasn’t specifically carried out personally by LockBit creators, but rather by someone who bought access to a control panel from them.
What’s more, LockBit is known for maintaining a professional-looking website and even running a bug bounty program — they have very strong marketing effort for a ransomware.
Once it infiltrates a system, LockBit uses various tools to carry out its attack, including credential gathering, disabling security products, and propagating within networks. It exfiltrates data using cloud storage tools and then initiates file encryption using AES encryption with RSA keys. Like many ransomware strains, LockBit replaces the desktop wallpaper with a ransom note:
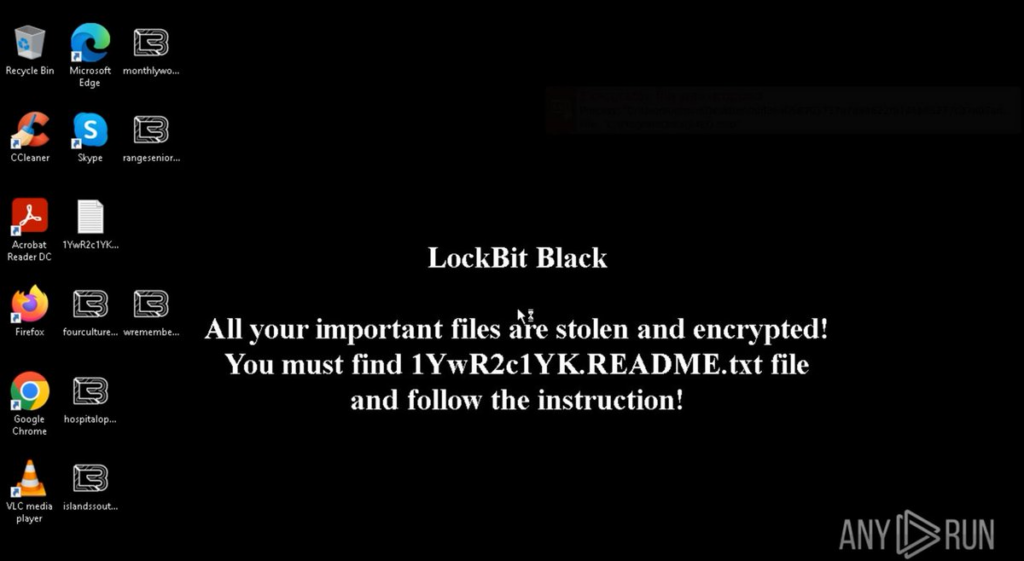
If you want to better understand how LockBit works and collect LockBit IOCs, check out this LockBit ransomware analysis in ANY.RUN.
LockBit’s popularity is spiking
Looking at ANY.RUN’s Malware Trends Tracker we can see that LockBit is currently ranked 19 as the most popular malware overall. This is high for ransomware — this type isn’t as popular as, for example, loaders or stealers.
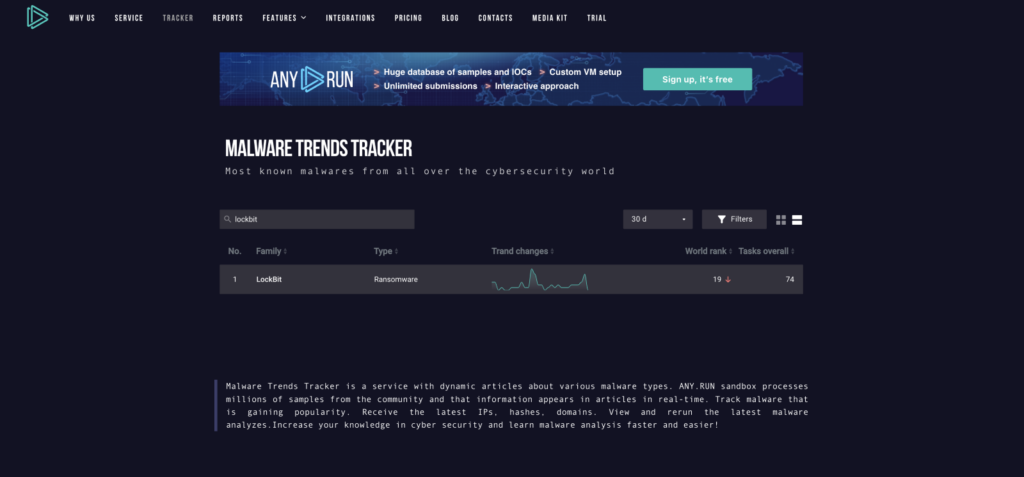
We also observe an increase in usage activity on this 30-day graph, which roughly corresponds to the Calvià attack. Additionally, we notice another recent spike. High number of detections shows that users are quite interested in Lockbit.
The Malware Trends Tracker displays the number of tasks executed in the ANY.RUN sandbox when malware, such as LockBit in this case, was detected using our detection rules and tagged. An increase in detections indicates that more researchers are encountering this threat in the wild
What’s noteworthy is that LockBit isn’t typically employed in this manner. Its primary targets are usually small to medium-sized businesses, with an average ransom demand of approximately $85,000. It’s somewhat unusual to witness this threat being deployed on such a large scale.
Does this suggest that LockBit might become more popular among APTs and be utilized in high-complexity, high-stakes ransomware attacks? Perhaps this is a trend worth monitoring.
What could have caused the attack?
While the emergency IT committee in Calvià is still investigating the incident, we cannot be certain about the exact cause of this attack. However, we can make some educated guesses based on our general knowledge of LockBit.
To get inside a system, LockBit affiliates may leverage phishing, or VPN and RDP brute force credentials as an initial access. In certain cases, LockBit exploits software vulnerabilities.
- Spearphishing: In this scenario, one of the employees of the affected system might have fallen victim to a spearphishing attack, where they unknowingly open a malicious email. This email could contain a link or attachment that, once clicked or downloaded, installs malware on their system, giving attackers access.
- Use of unpatched software: Another possible route to the infection could be the presence of unpatched software on one of the machines within the organization. The attacker could have exploited a vulnerability in this software to gain access.
It’s important to note that at this point, these are only speculations and should be taken with caution.
What can organizations do to prevent similar attacks?
Without knowing the specific details of the attack, the only recommendations we can provide at this point are general ones related to proper online hygiene, system management, and employee security training.
Not to beat a dead horse, but these basic measures can significantly enhance cybersecurity. Unfortunately, not all organizations adhere to them, which creates opportunities for cybercriminals.
Here’s what you can do to improve security:
- Employee training: conduct regular cybersecurity awareness training for employees to help them avoid phishing.
- Patch management: Keep all software and systems up-to-date with the latest security patches and updates to minimize vulnerabilities.
- Strong authentication: enforce the use of strong, unique passwords and implement multi-factor authentication wherever possible.
- Access control: Limit access to critical systems and data to only those who need it for their job roles.
- Regular backups: Regularly back up data and store it in isolation from the main network.
About ANY.RUN
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis of Windows and Linux tasks.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.






0 comments