Although Linux is often regarded, and indeed is, less susceptible to attacks than Windows — partly because it’s not as widespread, it is not immune to malware. In fact, certain types of malware, such as DDoS botnets, are more prevalent on Linux systems than on Windows systems.
It’s no secret that Linux servers are widely deployed in enterprise environments. This attracts hackers who seek a higher return on their investment. As a result, Linux malware saw a 50% increase in 2022 — a historical record.
Why it’s important to analyze Linux malware
So, how do you protect your organization against Linux threats? The answer is complex and a bit beyond the scope of this article. But a big part of hardening your security posture is to analyze the malware samples you encounter.
It’s crucial to understand how they behave on a system. This way you will be able to collect IOCs they leave behind, and accordingly set up WAF, SIEM, or SOAR systems.
Let’s analyze four such cases together in ANY.RUN:
1. Analyzing Mirai, Botnet on Linux
Mirai is a type of malware that transforms network-connected Linux devices into remotely controlled bots, often referred to as “zombies.” These compromised devices are then used to carry out Distributed Denial of Service attacks. This means that after a Mirai infection, your servers could become sources of DDoS traffic.
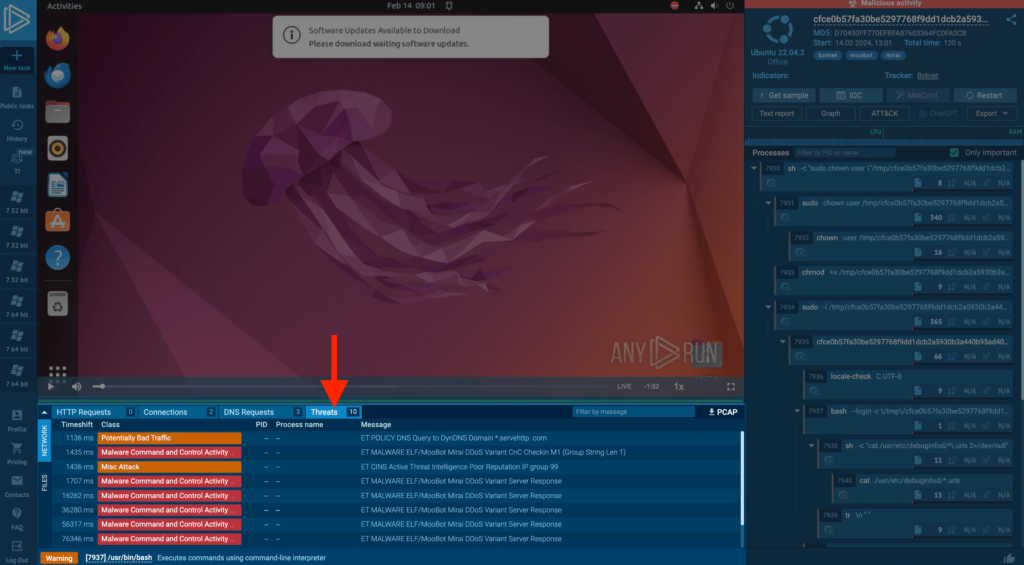
In the example, we can observe the botnet’s actions in an ANY.RUN task by visiting the threats tab.
(Read how ANY.RUN helps analyze network threats)
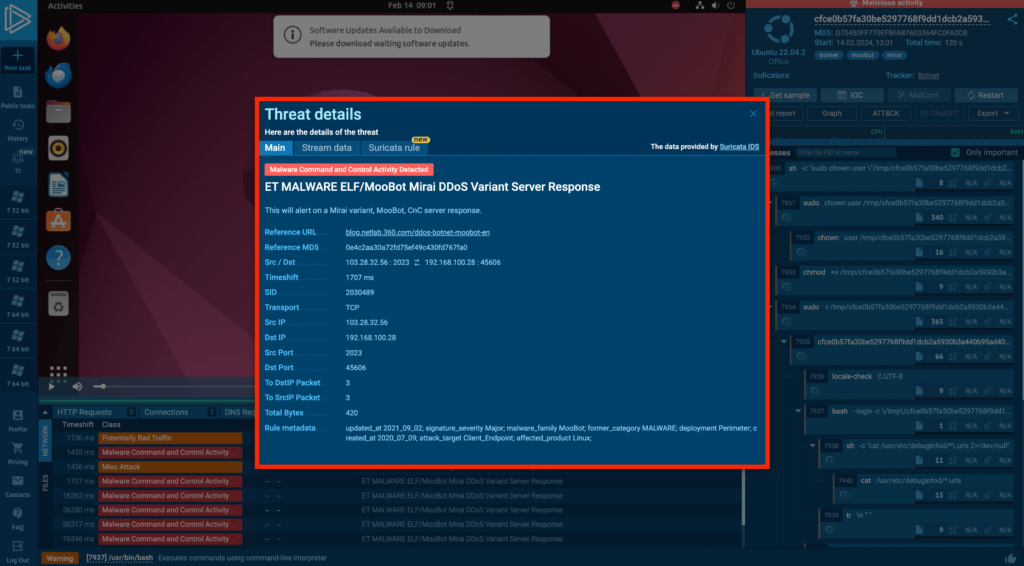
Because Mirai is active on the network, we can analyze which Suricata rules were triggered and examine them in the Threats tab.
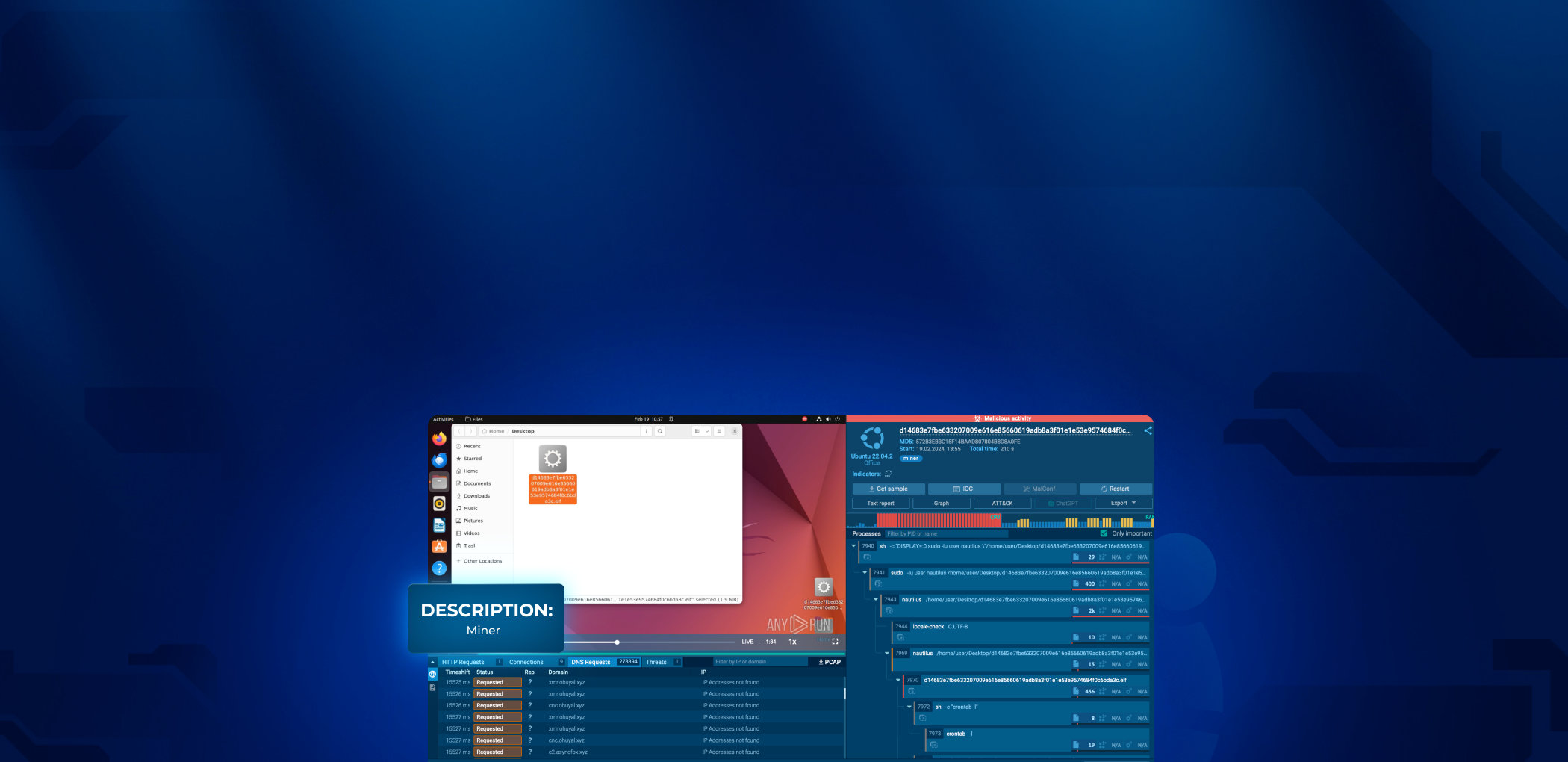
2. Analyzing Linux Miners
The next example is a miner — a type of parasitic malware that uses the system resources of infected host to mine cryptocurrency. It leads to degraded performance and unresponsiveness of infected machines.
(Read more about crypto-mining malware.)
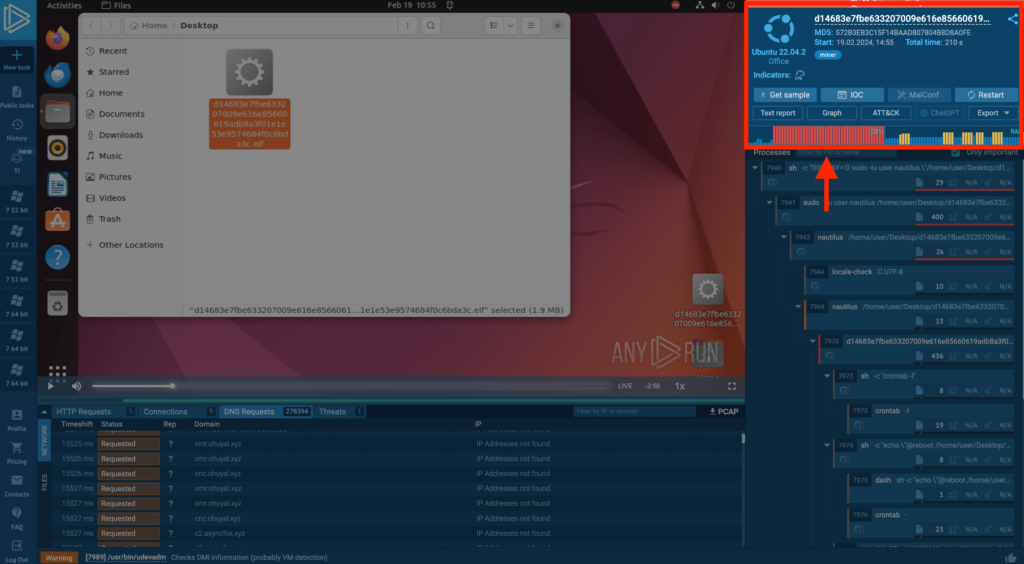
In this example, ANY.RUN initially detected the threat through network activity. Abnormal resource consumption is further proof of mining — Immediately after the malware launched, the CPU reached maximum capacity, and RAM usage spiked at the same time.
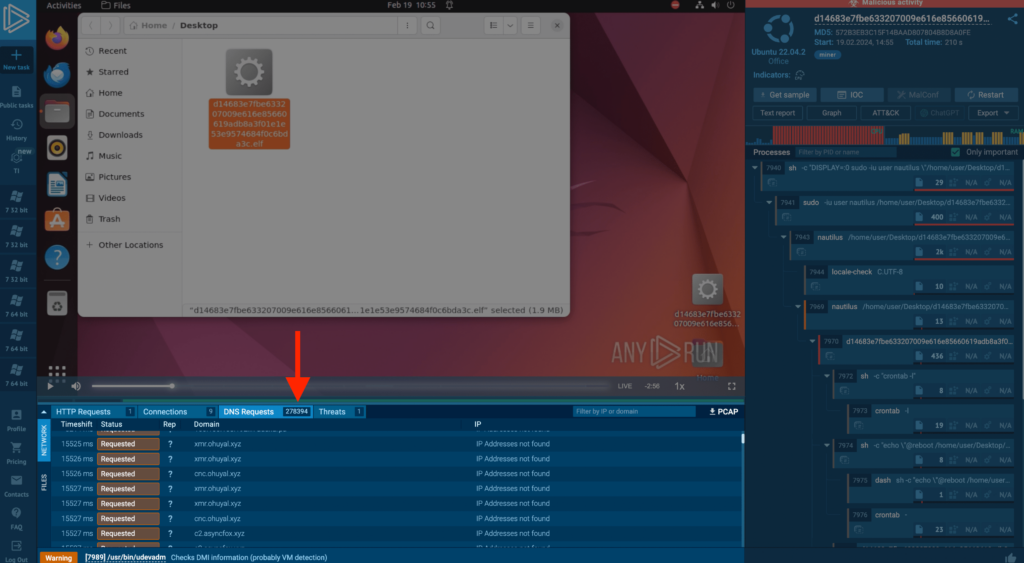
ANY.RUN also clearly shows abnormal network behavior; the miner sent almost 300,000 DNS requests to generated domain names in less than 4 minutes.
And in this task, we’re also examining a miner, but a key point to highlight is the signatures:
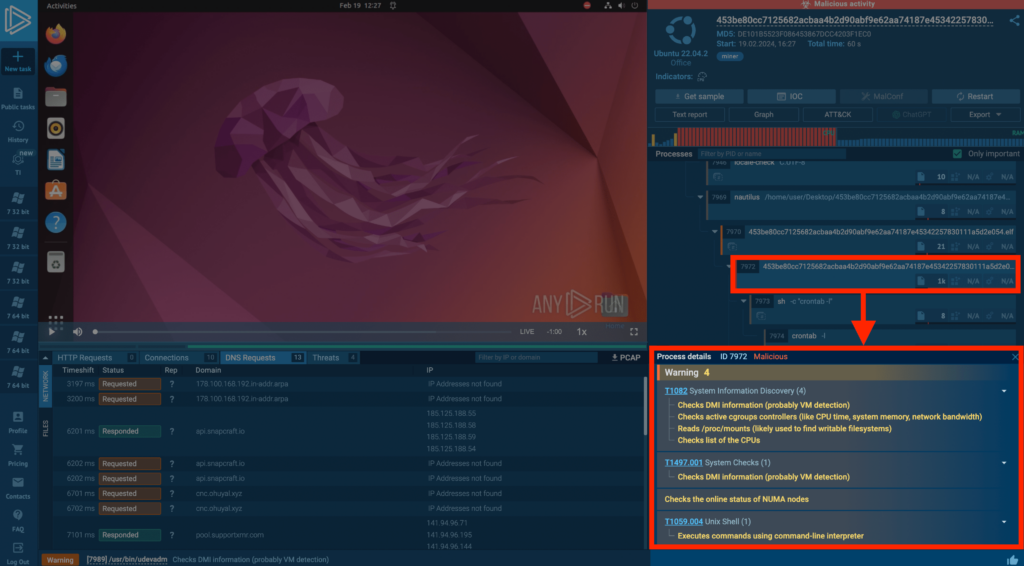
The titles of these signatures provide insight into what occurred. By clicking on one, you receive a detailed explanation of the conditions that triggered the signature. This way, we can better understand the network behavior of the sample.
For example, we can see that the malware checks active group controllers and the list of CPUs. This is a tactic advanced miners use to gather system data and configure themselves to run covertly in the system, ensuring they don’t overuse resources.
3. Analyzing DDoS on Linux
In this example, we observe a compromised Linux system executing a DDoS attack: within just one minute, the malware attempts to establish connections over 15,000 times.
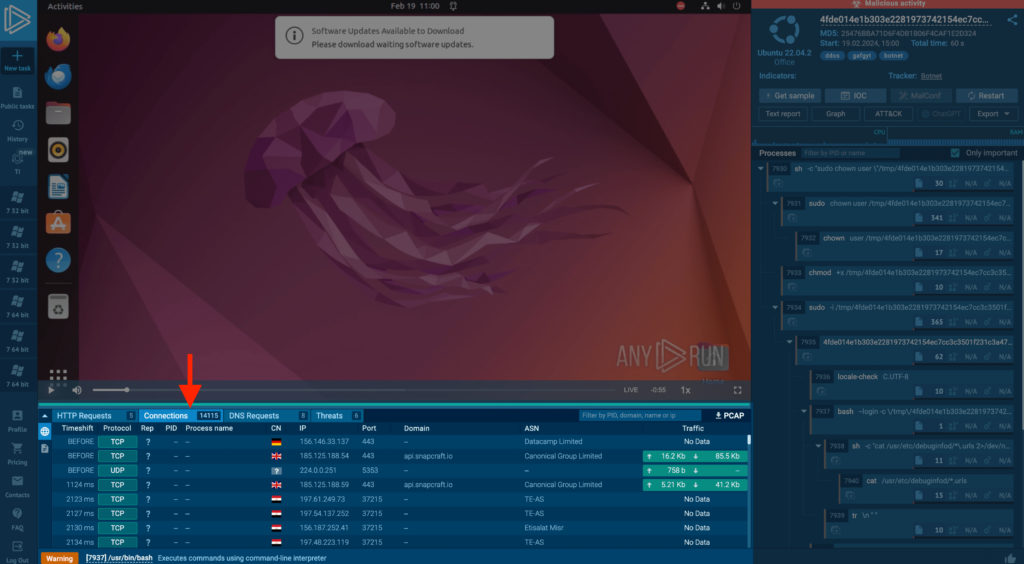
Catching a DDoS attack originating from your servers can result in severe consequences: it could lead to reputational damage, and even regulatory repercussions, especially if the attack targets critical infrastructure or helps hackers to execute a data breach by smoke screening.
Conclusion
Let’s recap the main points:
- Linux is not immune to malware: Despite its reputation for security, Linux systems can fall prey to various types of malware.
- It is important to analyze the latest malware samples: Analyzing malware samples is crucial for understanding their behavior, collecting IOCs, and configuring security systems like WAF, SIEM, and SOAR systems against emerging threats.
- Case studies in ANY.RUN: In the article, we looked how ANY.RUN helps analyze and better understand behavior of malware, using miners and DDoS botnets as an example — of course, you can also just as well analyze other threats such as ransomware, RATs and stealers.
About ANY.RUN
ANY.RUN is a developer of cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams, as well as Threat Intelligence Feeds and Threat Intelligence Lookup. Every day, 400,000 professionals use our platform to investigate incidents and streamline threat analysis.







0 comments