Both interactive and automated sandboxes play a role in an organization’s defense strategy, yet they function differently.
Understanding their differences, applications, and how they complement each other is vital for making informed decisions on integrating these tools into your security infrastructure.
The role of malware sandboxes in cybersecurity
At the core, malware sandboxes utilize virtualization and emulation techniques to mimic real operating systems and hardware environments. When a suspicious file enters the sandbox, it’s executed in this controlled space, which closely resembles a regular host environment to the malware. This deception is key, as many sophisticated malware types are designed to detect and evade sandbox analysis.
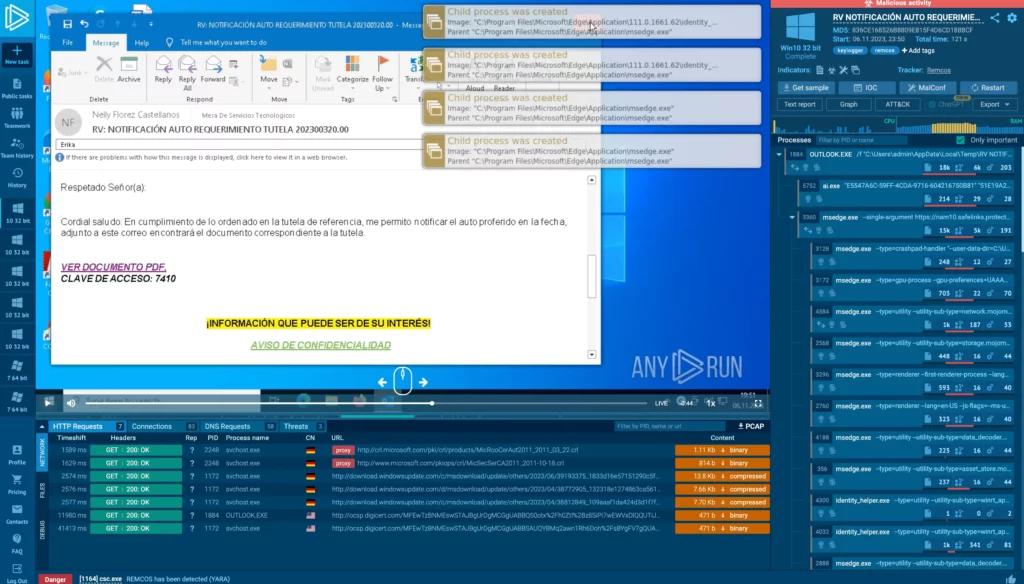
The sandbox monitors the file’s interactions with the virtualized system, including API calls, system function utilization, and network traffic, to detect malicious patterns. Some sandboxes also employ behavioral heuristics, analyzing the intention of commands and code execution paths.
Benefits and uses of malware sandboxes
The benefits and uses of both interactive and automated malware sandboxes extend across several aspects of cybersecurity:
- Threat Analysis: Sandboxes are critical for reverse-engineering malware. Analysts can dissect how malware operates: its payloads, communication mechanisms, and persistence techniques. This deep dive into the malware’s anatomy informs the development of more effective countermeasures.
- Malware Research: Researchers utilize sandboxes to study malware evolution and tactics. This research can lead to insights about threat actor methodologies, contributing to strategic threat intelligence.
- Incident Response: During a suspected breach, sandboxes play a pivotal role in incident response, allowing for quick, safe analysis of the threat, thereby accelerating the response time and reducing the potential impact of an attack.
How interactive malware sandboxes work
Interactive sandboxes are built for detailed investigation, allowing analysts to dissect code, modify the execution environment, and adjust malware behavior. This is crucial for tackling APTs or zero-day exploits that require a nuanced approach.
Typical use case for an interactive sandbox
Consider a recent phishing campaign hiding malware in a password-protected archive, with instructions for recipients to unpack it using a provided password. Using an interactive sandbox, an analyst can mimic these steps and change network or system settings to study the malware’s actions and mechanisms.
Benefits of interactive malware sandboxes
Interactive sandboxes give analysts the ability to deeply analyze malware. They offer hands-on tools to directly manipulate and observe suspicious code, unlike automated sandboxes that run with minimal intervention.
Here’s a breakdown of how an interactive sandbox operates:
- VM interactivity: Analysts interact with the malware within a VM, executing commands and tweaking system settings to provoke and observe malware actions that may only occur with user interaction or system changes.
- Environment manipulation: An interactive sandbox allows for the modification of the execution environment. Analysts can alter registry values, change network configurations while working with a sample, or mimic different operating systems to see how the malware reacts, which is particularly useful in analyzing malware that looks for specific conditions before executing its payload.
- Network Interaction: By simulating network services or replicating traffic patterns, analysts can trick the malware into activating its network-based behavior. This allows them to track C2 communications, understand data exfiltration methods, and even identify other compromised systems.
- Task relaunch with different configurations: Analysts can adjust VM configurations and quickly relaunch tasks to see how different environments affect malware behavior.
These techniques enable analysts to extract additional IOCs from complex malware samples. Examples include banking trojans that only trigger when a user accesses a certain website or malware with kill switches activated by specific file names or registry keys.
How automated malware sandboxes work
Automated sandboxes lack control over emulation flow, as they’re built for rapid, high-volume analysis with little human input. They utilize set parameters to replicate target environments, assessing a multitude of samples to swiftly determine if a file is malicious.
Typical use case for an automated sandbox
Imagine an organization that gets hundreds of suspect email attachments each day. An automated sandbox can handle these en masse, applying behavioral analysis and signature detection to separate harmless files from malicious ones. This effectively prioritizes threats for deeper scrutiny.
Choosing the right tool for the job
Both interactive and automated sandboxes have their place in a robust security posture:
Use interactive sandboxes when:
- You need to collect IOCs from a complex malware sample fast.
- You need control over the execution environment.
- Your analysis requires custom interaction with the malware.
- You want to observe malware behavior in specific scenarios.
- Detailed logging and step-through execution are necessary.
Use automated sandboxes when:
- Speed is critical, and you’re handling high volumes of potential threats.
- You’re prioritizing breadth over depth in your initial analysis.
- You require a quick determination of benign vs. malicious files.
Wrapping up: interactive and automated sandboxes are best used together
Using both automated and interactive sandboxes is beneficial. Automated sandboxes efficiently process large volumes of data, identifying potential threats. Analysts can then examine these flagged items in interactive sandboxes for detailed analysis.
Moreover, integrating sandbox findings with other security solutions, like SIEM systems, is crucial. IOCs detected in sandbox environments should be incorporated into SIEMs to refine real-time surveillance and alert precision.
About ANY.RUN
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.










0 comments