ANY.RUN’s Threat Intelligence Feeds are designed to power SOAR, SIEM, EDR/XDR, TIP, and other security systems. Our goal is simple: to fit naturally into a customer’s security ecosystem so analysts can investigate incidents faster, improve detection quality, and spend less time on repetitive tasks.
Now, IBM QRadar SIEM users can directly consolidate ANY.RUN’s Threat Intelligence Feeds to strengthen detection and triage capabilities — all from a single console.
IBM Qradar and TI Feeds Connector Effects: Visible on Metrics
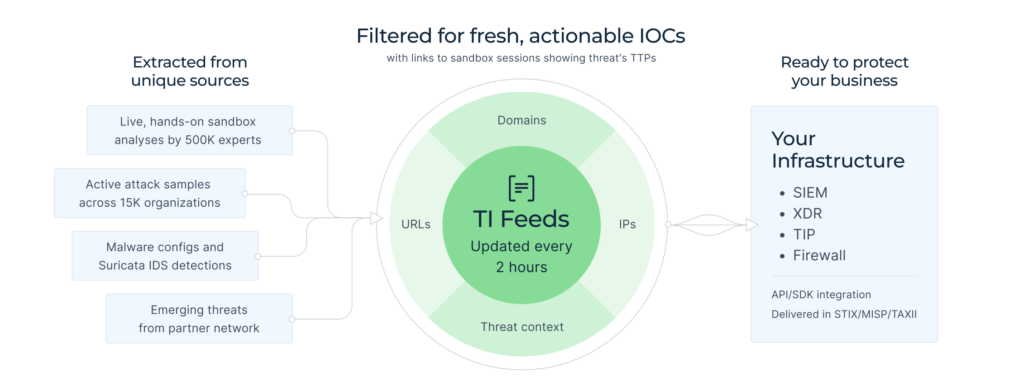
IBM QRadar SIEM is a leading Security Information and Event Management solution that centralizes visibility across IT infrastructure, enables real-time threat detection through log and flow analysis, and incorporates advanced analytics like AI and user behavior monitoring.
The integration with TI Feeds helps teams using QRadar SIEM boost their security with high-quality threat intelligence. They deliver malicious IPs, domains, URLs extracted from live sandbox analyses of the latest threats hitting 15,000+ organizations worldwide. Unlike post-incident reports that lag behind, our feeds update in real time sending active attack indicators straight to clients.
- Expanded Threat Coverage
Automatically correlate logs and events with the latest IOCs to spot the latest threats, reduce mean time to detect/respond (MTTD/MTTR), and lower analyst burnout.
- Early Threat Detection
Identify threats earlier in the kill chain to stop and mitigate attacks before they impact business operations
- Enhanced Team Productivity
Automated correlation reduces manual research time, allowing analysts to focus on investigation and response rather than IOC verification and threat hunting.
- Measurable ROI
Faster threat detection translates directly to reduced potential damage from security incidents, while improved analyst efficiency lowers operational costs.
API, SDK, and STIX/TAXII formats are supported to seamlessly bring the feeds into your existing architecture. No redesigning workflows, no extra costs.
Benefits for Security Teams
For SOC level 1-2 analysts, the IBM-ANY.RUN connection fuels:
- Automated Threat Detection: When network logs or infrastructure data collected by QRadar match ANY.RUN’s IOCs, correlation rules automatically generate high-priority alerts. This eliminates manual IOC checking and accelerates initial triage.
- Reduced Alert Fatigue: With nearly 100% malicious indicators, analysts can trust that ANY.RUN-sourced alerts represent genuine threats requiring immediate attention, improving focus and reducing investigation overhead.
Implementation: How to Connect TI Feeds to IBM QRadar SIEM
The ANY.RUN TI Feeds application is available through the IBM X-Force App Exchange marketplace, ensuring compatibility and support within IBM’s security ecosystem.
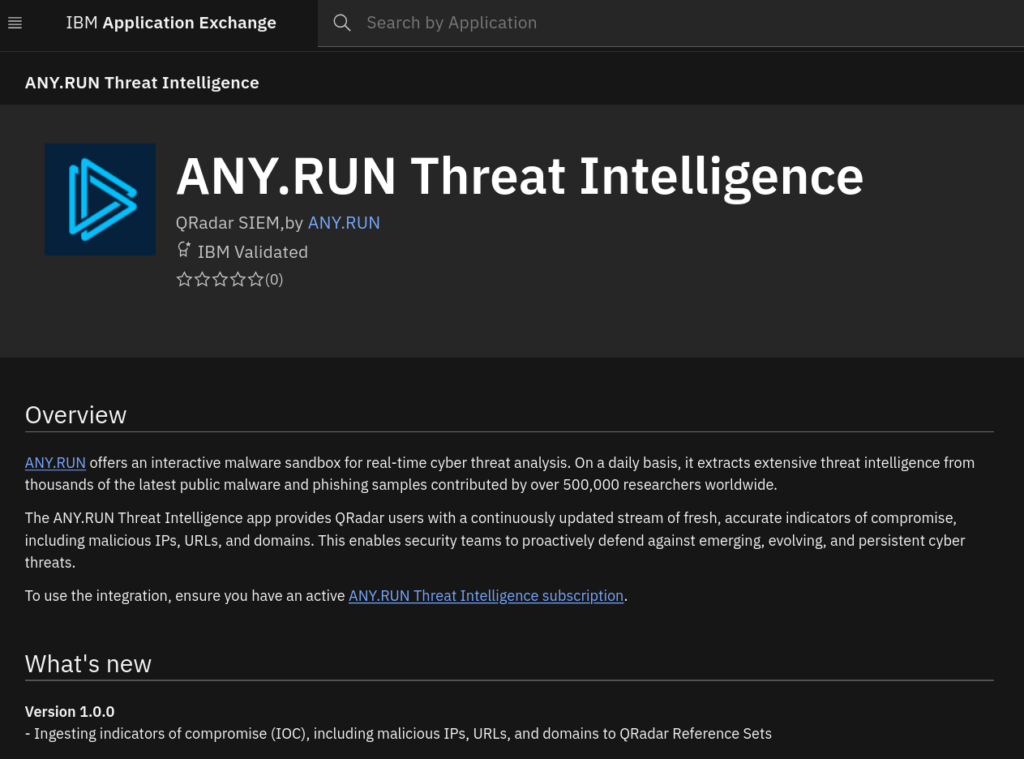
Deployment:
- Download the ANY.RUN TI application from IBM X-Force App Exchange
- Install within your existing QRadar SIEM environment
- Configure correlation rules to leverage ANY.RUN IOCs
- Begin receiving automated threat alerts based on fresh malware analysis data
Requirements:
- Valid ANY.RUN Threat Intelligence Feeds subscription (trial access available)
- IBM QRadar SIEM environment with X-Force App Exchange access
- Network connectivity for real-time feed consumption.
Use Case Scenario: Automated Threat Detection
Consider a typical enterprise environment where network traffic and infrastructure logs flow into IBM QRadar SIEM. When the ANY.RUN TI Feeds connection is active:
- Data Collection: QRadar continues normal log collection from network devices, endpoints, and security tools
- Automated Correlation: QRadar correlation rules automatically cross-reference network artifacts against ANY.RUN’s real-time IOC feeds
- Alert Generation: When a match occurs, QRadar generates a high-priority alert that the team can act on
This workflow turns reactive threat hunting into proactive threat detection, with verified threats automatically surfaced for investigation, near-zero false positives, and faster triage.
Start Transforming Your Security Operations
By combining QRadar’s proven correlation and alerting capabilities with ANY.RUN’s real-time, high-fidelity threat intelligence, organizations can achieve:
- Immediate Threat Detection: Hours instead of days or weeks for emerging threat identification
- Operational Efficiency: Reduced analyst workload through automated, high-confidence alerting
- Strategic Security Advantage: Access to threat intelligence from a global community of security professionals
- Seamless Connection: No disruption to existing security processes or infrastructure
The ANY.RUN TI application is available now through the IBM X-Force App Exchange for organizations with active ANY.RUN Threat Intelligence Feeds subscriptions.
About ANY.RUN
ANY.RUN is trusted by more than 500,000 cybersecurity professionals and 15,000+ organizations across finance, healthcare, manufacturing, and other critical industries. Our platform helps security teams investigate threats faster and with more clarity.
Speed up incident response with our Interactive Sandbox: analyze suspicious files in real time, observe behavior as it unfolds, and make faster, more informed decisions.
Strengthen detection with Threat Intelligence Lookup and TI Feeds: give your team the context they need to stay ahead of today’s most advanced threats.
Want to see it in action? Start your 14-day trial of ANY.RUN today →








0 comments