At ANY.RUN, our analysts work constantly to identify new threats and create detection rules. But with over 6000 new malware released every month, it is a battle we can only win together. Thankfully, our community members often spot new samples and send them to us for further analysis. And you can help too!
Want to help us make ANY.RUN detection better?
Think you have found a new malware sample or version? If yes, we’d be really thankful if you could send us that suspicious file, or link as well as any notes you believe are important.
To make this easy, we’ve set up a new email address for you to send those samples:
SEND US NEW SAMPLES
newvirus@any.run
Your Submissions Help Make a Difference
Take a recent incident where a user shared an interesting sample with us.
This turned out to be a stealer — it gathered system information, browser history, and captured screenshots. All the harvested data was then sent back to its Command and Control (C2) server.
We decided to analyze the sample and quickly identified it as Blackguard. Interestingly, it self-declared its name and version in the Information.txt file, which also held various details about the compromised system.
Based on this insight, we developed new YARA rules to identify the Blackguard family in future analyses. We also created a malware config extractor.
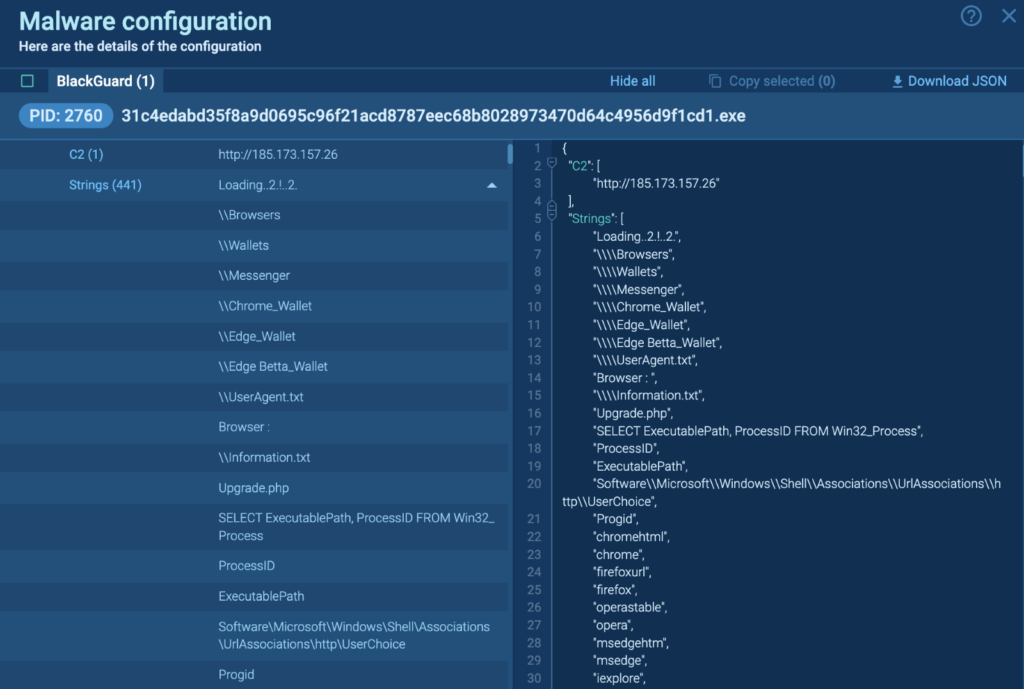
This means that even if Blackguard doesn’t fully execute in upcoming tasks — for instance, if its C2 is down during the analysis — ANY.RUN users will always have comprehensive details about this family. The config data will reveal key facts, such as the C2’s IP address, and specify which directories the malware targets for information theft.
Thank you for your help. Every little bit counts in the fight against cybercrime!








0 comments