Crafting a comprehensive malware or threat intelligence report can be challenging. It requires a mix of technical and journalistic writing skills to effectively convey the information.
The good news is that there are tools available to help automate parts of the reporting malware process, making it a bit easier.
What is a malware analysis report?
Malware analysis reports contain useful information about the threat — it’s the artifact that you get as output from malware analysis.
They’re primarily consumed by analysts, SOC and DFIR teams, and, to a lesser extent. executives. They help readers understand the threat, assess its impact, and make informed decisions.
A good report contains a mix of strategic and technical information: from what the malware is, who operates it, and whom it targets, to in-depth descriptions of malware functions, payloads, mutexes, and processes.
What is the difference between threat intelligence and malware analysis reports?
These two types of reports are sometimes confused, but in reality there are different types of security writing.
Though threat intelligence and malware analysis reports can overlap, at their core, they serve different purposes. TI reports are more strategic, and malware reports are more immediate.
Here’s how they compare:
| Malware analysis report | Threat intelligence report |
|---|---|
| Focuses on a specific sample or family | Focuses on threat actors, campaigns, and trends |
| Provides detailed technical analysis | Provides a high-level overview |
| Targets a technical audience | Targets a wide audience |
| Relies primarily on hands-on analysis | Aggregates information from multiple sources |
We’ll focus more on malware analysis reports, as we at ANY.RUN primarily provide analysis and tactical intelligence solutions.
What information should you include in a malware analysis report?
A malware analysis report should provide a bird’s eye view of the malware sample, then detail its characteristics, behavior, and impact.
Include information like:
- Technical details: File properties, hashes, encryption, obfuscation techniques
- Behavioral analysis: Network activity, persistence, data exfiltration, lateral movement
- IOCs: File paths, registry keys, URLs, IP addresses, domain names
- Attribution: Possible threat actors, similar malware, related campaigns
- Mitigation: Recommendations for removal, patching, security controls, incident response
In our information-saturated age, merely including data in a report is not enough to capture readers’ attention.
The key is to structure the information in a way that puts the most relevant insights at the front.
Below, we’ve put together 3 tips for how to structure eye-catching, yet informative malware analysis reports:
1. Grab attention with informative heading
A well-crafted headline will help pique the curiosity and attention of the reader, whether they’re an executive or a senior analyst.
Ideally, the headline should give a glimpse of the article’s content and establish its relevance. A good headline is borderline clickbait, but it walks the line between informative and clickbaity.
Here is an example of well-crafted headline from real report by Microsoft security:
- Threat actor leverages coin miner techniques to stay under the radar — here’s how to spot them
While this example is from threat intelligence reports, we can still draw relevant lessons and apply them to malware analysis reports.
Here’s why this headline works:
It explains what’s happening: From the heading alone, we know that miner techniques are being used to evade detection.
It promises value: The headline teases that by reading the report we’ll learn how to detect threats that use miner techniques.
2. Use the inverted pyramid structure
The inverted pyramid concept comes from journalism, but it also has its place in technical writing. In essence, it’s a way of grabbing the reader’s attention by placing the most crunchy, nutritious details at the top and supporting information at the bottom.
In the context of a malware analysis report, an inverted pyramid might look something like this:
| Report section | Content |
|---|---|
| Executive summary | The who, the why and the what |
| Malware overview | TTPs, what the threat can do |
| Technical analysis | IOCs and behavior breakdown |
| Impact assessment | Infection consequences |
| Recommendations | Step-by-step prevention and remediation guides |
| Appendices | Supporting materials, linked sample, references |
By structuring the report in this way, you allow readers to get the point of the report without reading the entire document.
This is particularly useful for decision makers who may not be necessarily concerned with technical intelligence.
3. Take advantage of automation
The modern malware analysis process includes a great deal of automation eliminates the need to write reports entirely from scratch, saving a ton of time.
For instance, with ANY.RUN, you can generate comprehensive threat reports about the samples you analyze with just a click of a button. Here’s how:
Open this analysis session to follow along.
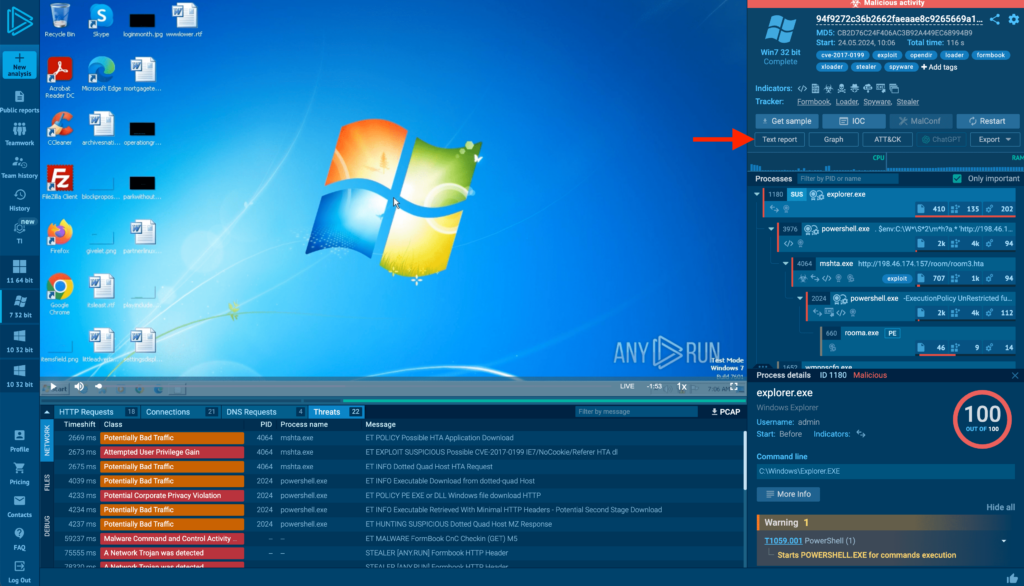
After completing an analysis session in ANY.RUN, simply click the Text report button, indicated by the red arrow above.
The service will then automatically generate a comprehensive malware analysis report with the following sections:
- General information.
- Behavior activities (TTPs).
- Malware configuration (if extracted).
- Static information (TRiD and EXIF)
- Video and screenshots of the VM from the analysis session.
- Processes (list and chart)
- Detailed process information.
- Registry activity.
- Files activity.
- Network activity (connections, DNS requests and Suricata detections).
- Debug output strings.
Before sharing the report, you can streamline it by unchecking the sections you don’t need:
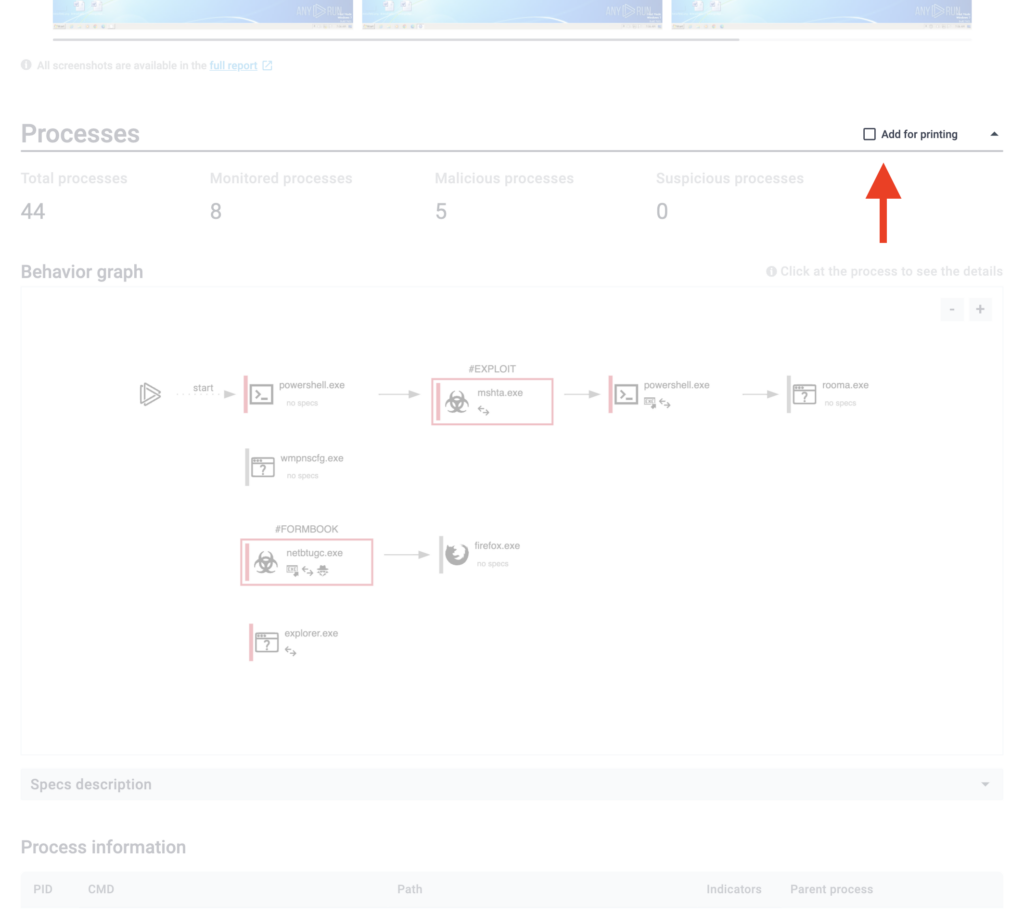
For example, if you plan to print the report, you can remove graphical sections, like the process graph and VM screenshots.
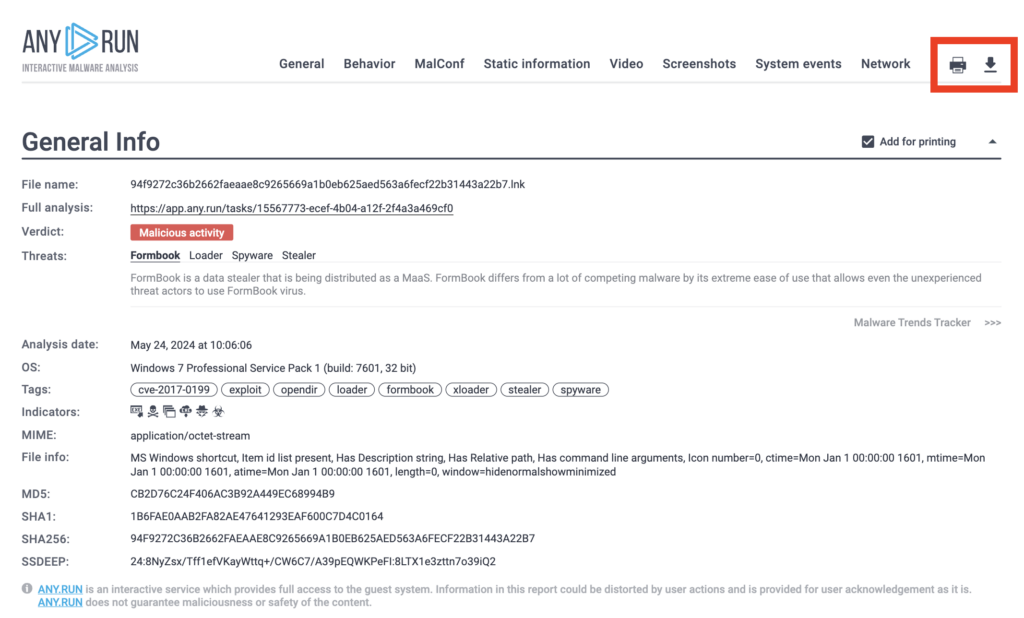
You have three options for sharing the report:
- Copy the URL and share the link directly.
- Download the report as an HTML file.
- Print it out.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Advantages of ANY.RUN
ANY.RUN helps you analyze threats faster while improving detection rates. The platform detects common malware families with YARA and Suricata rules and identifies malware behavior with signatures when detection by family is not possible.
With ANY.RUN you can:
- Detect malware in under 40s.
- Interact with samples in real time.
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior.
- Collaborate with your team
- Scale as you need.
Try the full power of ANY.RUN for free







0 comments