Of the 4 levels of threat intelligence (strategic, operational, tactical, and technical), technical TI is at the bottom of the pyramid — but it’s no less important than the rest.
That’s because it helps SOC teams configure the security systems that are the first line of defense against known and emerging threats.
What is Technical Threat Intelligence?
Technical Threat Intelligence focuses on indicators of immediate compromise like bad IP addresses or domains.
This data is typically machine-readable. Systems like TIP, SIEM, IDS/IPS and EDR can ingest and operationalize it, and SOC teams can then create new security rules or enrich existing ones.
All popular security solutions can read technical TI data because they use a common format for sharing threat information — STIX.
Here is an example of a technical threat intelligence data object from ANY.RUN’s TI feeds:
{
"type": "ipv4-addr",
"id": "ipv4-addr--8c851c0c-ee42-5e7e-af06-f849efc0ffb4",
"value": "194.104.136.5",
"created": "2022-04-20T15:05:54.181Z",
"modified": "2024-02-19T11:21:47.728Z",
"external_references": [
{
"source_name": "ANY.RUN task c761d29c-a02a-4666-bc34-b89c4aab5cd1",
"url": "https://app.any.run/tasks/c761d29c-a02a-4666-bc34-b89c4aab5cd1"
}
],
"labels": [
"RedLine"
]
} STIX is essentially JSON that’s been modified to better build connections between data elements likened indicators, tactics, techniques, and threat actors.
What are common use cases for technical threat intelligence?
Technical TI revolves around collecting, analyzing, and disseminating threat data, which comes from TI Feeds and malware analysis sessions.
This data includes:
- IP Addresses.
- Malicious domain names.
- File hashes.
- System events (like command lines).
Here’s how different security teams use this data:
SOC analysts can load threat intel feeds into their SIEM and IDS/IPS to identify attacks in real-time. When the systems detect a known bad IP connecting to the network, analysts can immediately block it and investigate further.
Incident responders use threat intel reports to quickly identify the root cause of a breach. For example, they can look up the specific servers a malware connects to, block those IPs in their firewalls, and scan the network for any compromised devices communicating with those addresses.
Vulnerability managers use threat intel to prioritize patching. They focus on vulnerabilities that are actively being exploited in the wild based on threat reports, rather than trying to patch everything at once. This helps them fix the most critical issues first and reduce risk more efficiently.
Where does technical TI data come from?
Technical TI data comes from threat feeds and malware analysis sessions, both manual and in sandboxes:
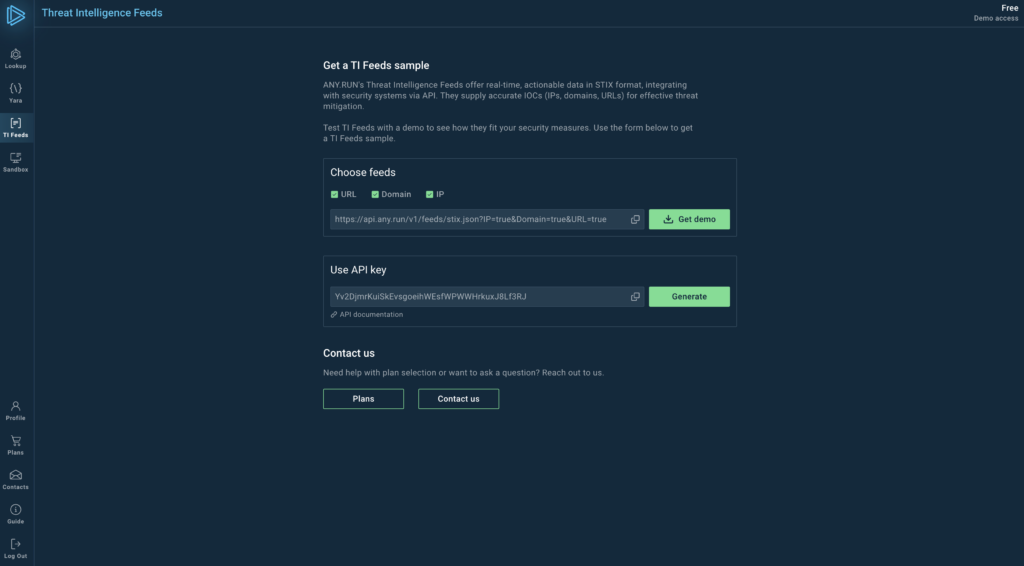
TI feeds provide a stream of real-time data about new and emerging malware from an external source and plug into SIEM and TIP systems to constantly update them with new indicators.
Sandbox analysis sessions allow analysts to place and run malware in a controlled environment, while the malware sandbox collects and records all system events related to its activity. Analysts can then access this data through reports.
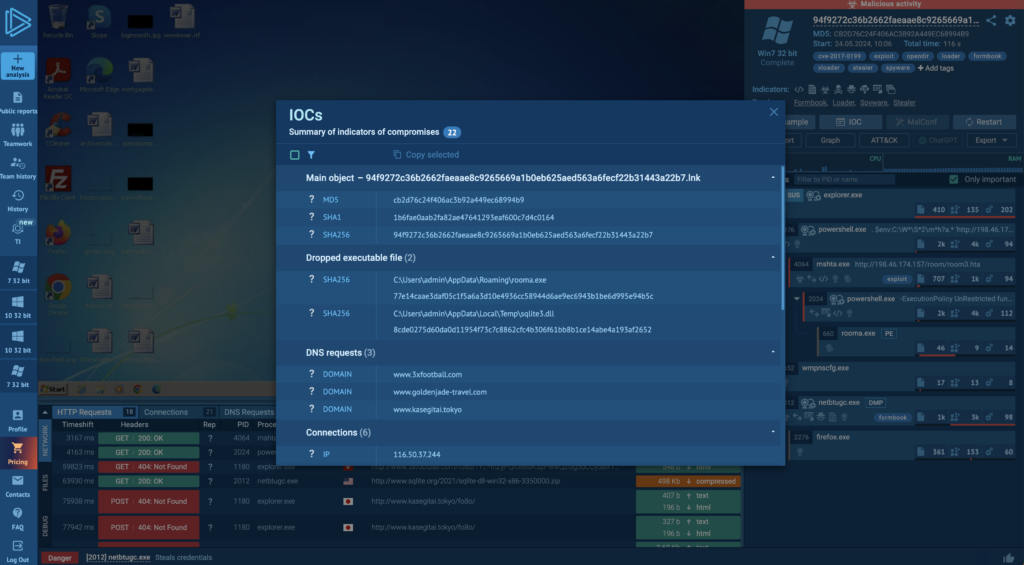
The screenshot above shows an IOC report that the ANY.RUN sandbox provides after running a malicious file. You can see what other information is available by going to this link.
Using technical TI to collect threat data
With services like TI Lookup, security teams can get a holistic understanding of the threat they’re dealing with. For example, if a security team member notices unusual DNS connections to an IP they don’t recognize, they can use ANY.RUN’s Threat Intelligence Lookup to quickly query that IP address.
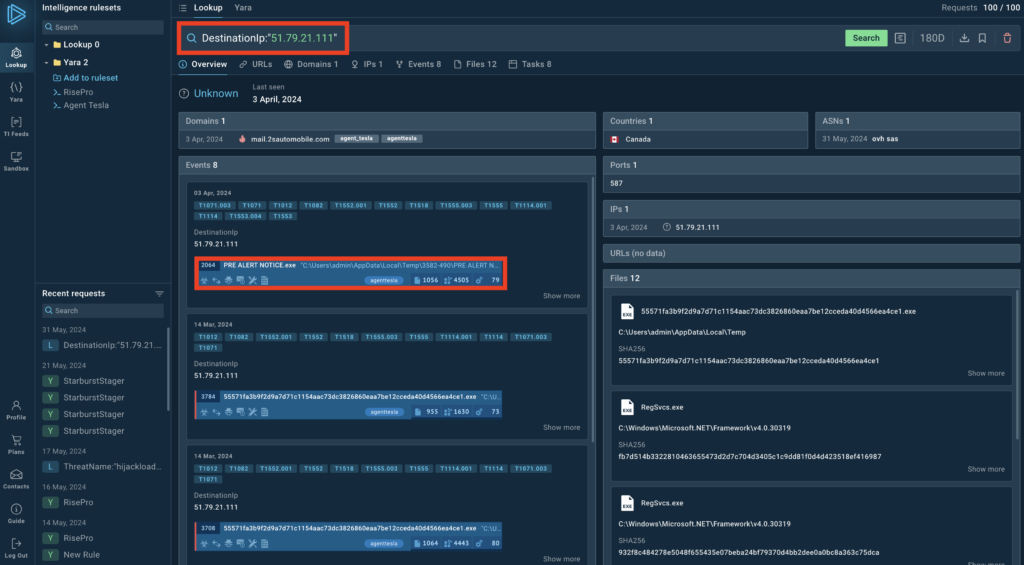
ANY.RUN will provide more related evidence, like domain names, file hashes and ports — along with tactical intelligence: associated malware families and TTPs. With that information, you can determine if this is an intrusion and take steps to contain and remediate it.
SOC teams operationalize this data to monitor system and network logs, automatically detecting and alerting entries that match known threat intelligence indicators.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Advantages of ANY.RUN
ANY.RUN helps you analyze threats faster while improving detection rates. The platform detects common malware families with YARA and Suricata rules and identifies malware behavior with signatures when detection by family is not possible.
With ANY.RUN you can:
- Detect malware in under 40s.
- Interact with samples in real time.
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior.
- Collaborate with your team
- Scale as you need.
Try the full power of ANY.RUN for free








0 comments