By 2026, MSSPs will compete less on tooling and more on clarity, speed, and foresight. Security buyers want proof that their provider understands what threats matter now, how fast they can respond, and how security decisions reduce business risk.
At the center of this challenge sits threat intelligence. Not as a research output, but as an operational input shaping every security decision.
What Clients Will Demand This Year: The Five Deciding Factors
Winning deals in 2026 means excelling where others fall short. Prospects grill providers on these five areas before signing:
- Relentless Threat Blocking: They want evidence you’re stopping attacks they can’t see coming.
- Clean, Actionable Alerts: Too many false positives waste time and erode confidence.
- Blazing-Fast Incident Response: Slow containment turns small incidents into headline breaches.
- Forward-Leaning Threat Hunting: Reactive-only services feel outdated in a zero-trust world.
- Undeniable ROI Visibility: Executives need clear proof of risks blocked and value delivered.
Master these with actionable threat intelligence, and you’ll close more deals while your competitors hassle.
ANY.RUN’s Threat Intelligence Feeds contain real-time streams of malicious IPs, domains, and URLs pulled from millions of sandbox submissions, updated frequently to keep you ahead. TI Feeds are not background data. They are the operational core of detection, response, hunting, reporting, and proactive defense.

Here are the five ways to stand out by employing real-time trustworthy threat data.
1. Early awareness defines credibility
Clients rarely see the attacks you stop. They only notice the ones you miss. One successful intrusion can erase years of good service and trigger immediate vendor reassessment.
The difficulty lies in the speed of attacker adaptation. Malware changes quickly, infrastructure rotates, and indicators expire fast. Detection logic based on static or delayed intelligence struggles to keep pace.
What mature threat intelligence enables:
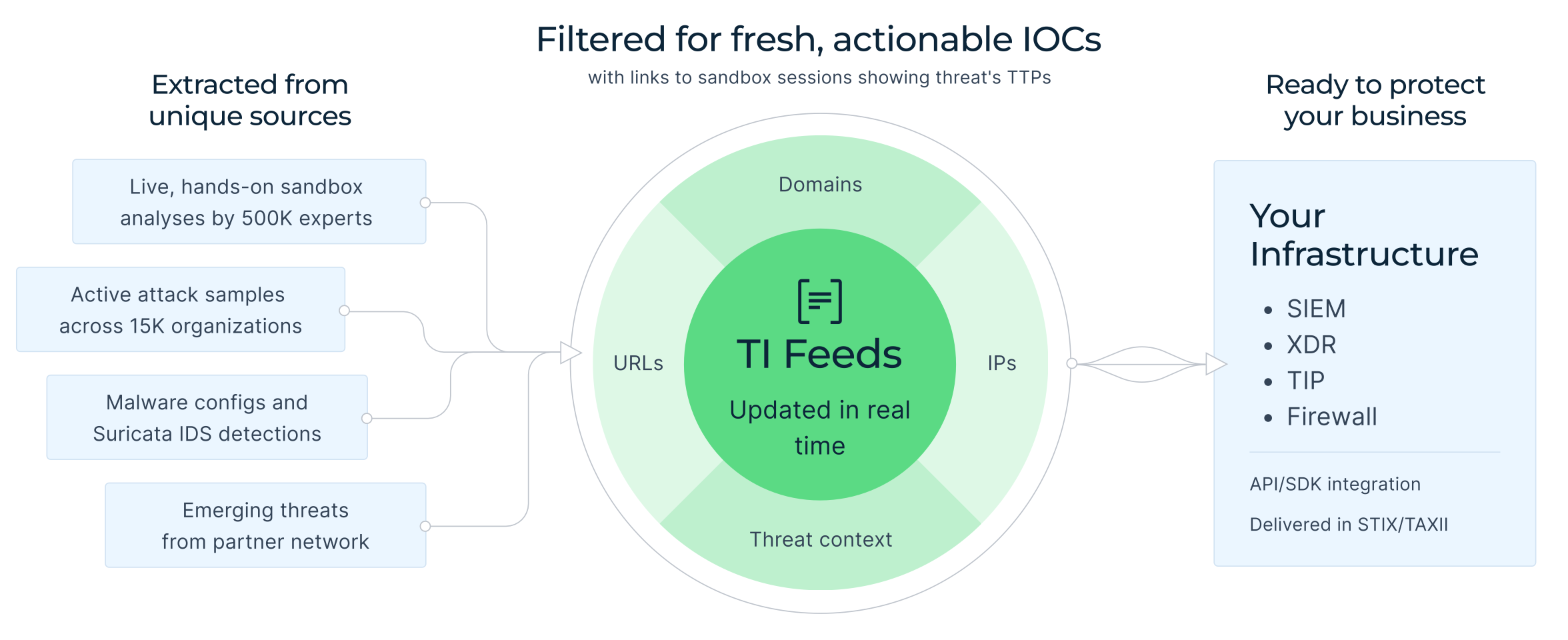
ANY.RUN’s TI Feeds deliver continuously updated indicators along with sandbox analyses documenting attacker behavior extracted from live malware execution. For MSSPs, this means:
- Detection rules that evolve as threats evolve;
- Faster identification of emerging malware families;
- Visibility into infrastructure used in active attacks;
- Reduced reliance on outdated or recycled indicators.
Instead of reacting to incidents reported elsewhere, your MSSP detects threats while competitors are still catching up. For clients, that difference is felt as safety, not statistics.
2. Response matters more than perfection
No MSSP can prevent every incident. What matters is how quickly and confidently you respond. Long investigations, unclear answers, and delayed containment create anxiety at the executive level.
Most delays come from context gaps. Analysts must validate indicators, understand attackers’ intent, and assess scope before acting. That takes time when intelligence is fragmented.
TI Feeds give response teams immediate access to:
- Fresh, validated indicators of compromise: malicious IPs, domains, and URLs continuously updated from real malware analysis by over 15K SOC teams;
- Contextual metadata including links to sandbox analysis sessions that provide additional insight into threat behavior;
- Intelligence that supports instant containment decisions;
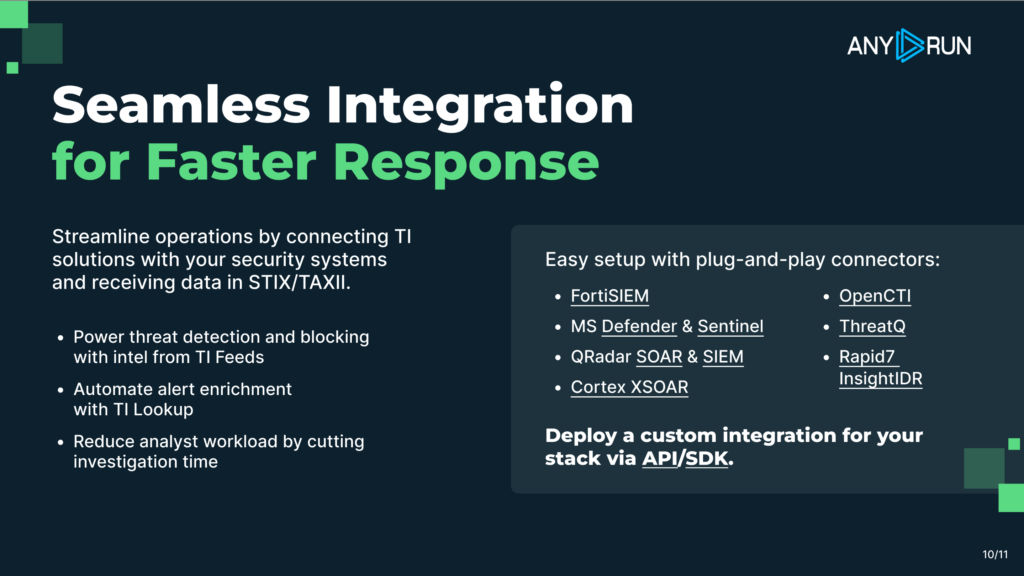
- Formats compatible with SIEMs and security platforms (STIX/TAXII) for seamless integration into existing workflows;
- API-enabled delivery so intelligence can feed automated detection and monitoring systems in real time.
This allows MSSPs to move from alert to action in minutes, not hours. Over time, clients associate your service with decisiveness and control. That perception is critical for renewal conversations.
3. Proactive security becomes expected
By 2026, clients will not ask whether you offer threat hunting. They will assume you do. The real question will be whether your hunting produces meaningful results or just internal noise.
Without fresh intelligence, hunting teams often chase weak signals or outdated hypotheses. That leads to low impact and poor client communication.
With TI Feeds, MSSPs can anchor threat hunting in reality:
- Hunt for indicators tied to active attacker campaigns;
- Correlate client telemetry with known malicious behavior;
- Continuously refine hypotheses using new feed data;
- Demonstrate findings backed by observable attacker activity.
This makes threat hunting repeatable, scalable, and easier to justify commercially.
4. Reporting shapes executive perception
Executives don’t want dashboards full of alerts. They want confidence that risk is being reduced and managed. Poor reporting creates the impression that security work is abstract or disconnected from business reality.
In many cases, churn begins not after incidents, but after months of unclear reporting.
TI Feeds allow MSSPs to report on outcomes, not effort:
- Indicators with associated threat context help explain why a detected indicator matters;
- Detection timestamps and threat labels reveal whether an indicator is recent and connected to active campaigns;
- Consistent delivery of validated, actionable IOCs allows reports to reflect real threat activity, not noise.
Reports become stories of protection delivered, not lists of events processed. This is where MSSPs justify their value in language decision-makers understand.
5. Generic defense won’t hold clients
Clients increasingly expect their security posture to evolve alongside attacker behavior. Generic controls applied uniformly across clients feel outdated and inattentive. The challenge is keeping defenses current without overwhelming analysts.
By aligning TI Feeds with each client’s risk profile, MSSPs can:
- Base decisions on high-confidence threat data, minimizing distraction from low-value or false signals;
- Use enriched contextual data to explain how specific IOCs are connected to observed or emerging threats;
- Update detection logic as campaigns evolve.
Security stops being reactive and starts feeling anticipatory. Clients feel seen, protected, and prioritized. That emotional factor matters more than most technical metrics.
Final Thought: What Clients Are Willing to Pay For
MSSPs don’t lose clients because attackers exist. They lose clients because they fail to show awareness, speed, and progress.
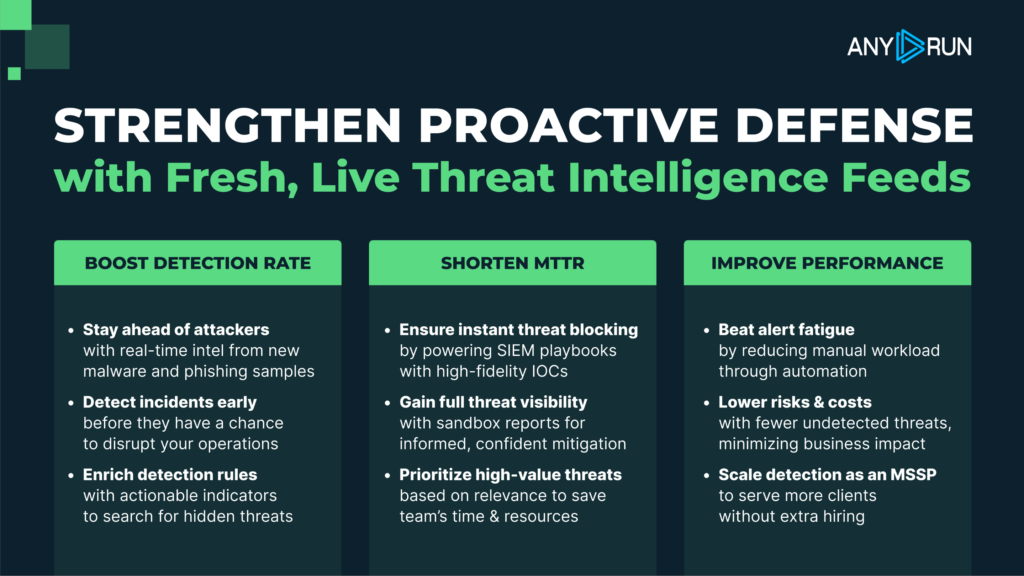
In 2026, Threat Intelligence Feeds are the foundation of competitive MSSP services. They power better detection, faster response, meaningful hunting, credible reporting, and proactive protection. The key metrics demonstrate this clearly:
- Security teams report up to a 21‑minute reduction in MTTR per case, with automation-ready feeds accelerating triage and containment actions.
- Up to 58% more threats identified after integrating TI Feeds into detection rules and playbooks.
- Streamlined intelligence lets Tier 1 teams resolve more incidents independently, reducing escalations to senior analysts by 30%.
The MSSPs that win will be those who turn intelligence into visible outcomes their clients can trust month after month.
About ANY.RUN
Trusted by over 500,000 cybersecurity professionals and 15,000+ organizations in finance, healthcare, manufacturing, and other critical industries, ANY.RUN helps security teams investigate threats faster and with greater accuracy.
Our Interactive Sandbox accelerates incident response by allowing you to analyze suspicious files in real time, watch behavior as it unfolds, and make confident, well-informed decisions.
Our Threat Intelligence Lookup and Threat Intelligence Feeds strengthen detection by providing the context your team needs to anticipate and stop today’s most advanced attacks.
Start a 2-week ANY.RUN trial →
FAQ: Threat Intelligence Feeds for MSSPs
Because attackers move faster than manual analysis can handle. TI Feeds provide a continuous stream of fresh indicators and attacker behavior that allow MSSPs to detect, respond, and adapt in near real time—something clients will increasingly expect as standard service.
Unlike static or delayed sources, TI Feeds are updated continuously and reflect indicators observed in real malware executions. This helps MSSPs detect emerging threats earlier and avoid relying on outdated indicators.
Yes. By supplying validated IOCs and associated TTPs upfront, TI Feeds remove much of the uncertainty during investigations. Response teams spend less time validating alerts and more time containing threats.
TI Feeds give hunters access to indicators and techniques tied to active campaigns, making hunting more focused and defensible. This allows MSSPs to offer threat hunting as a repeatable, intelligence-driven service rather than ad hoc investigation.
They do. TI Feeds enable MSSPs to report on real threats detected, blocked campaigns, and changes in risk exposure. This turns reports into proof of value, which is critical for client retention and contract renewals.
Absolutely. By tracking evolving attacker behavior and infrastructure, TI Feeds help MSSPs keep detection rules updated and defenses aligned with current threats—before attacks reach client environments.
TI Feeds automate intelligence delivery. Instead of analysts manually researching each alert, intelligence is continuously ingested into security tools, allowing MSSPs to protect more clients without proportional growth in headcount.








0 comments