How many real threats hide behind the noise your SOC faces every day?
When hundreds of alerts demand attention at once, even the best analysts start to lose focus. The nonstop pressure to react to everything drains energy, clouds judgment, and opens the door to real risk.
Teams using ANY.RUN have already flipped that script:
- 90% of attacks become visible within 60 seconds, giving analysts instant context instead of endless guesswork.
- 94% of users report faster triage, cutting time spent on false positives and low-value alerts.
- 95% of SOC teams speed up investigations, easing the overload that leads to burnout.
Ready to see how to get there? This action plan lays out the steps CISOs can take to turn alert fatigue into lasting focus.
Step 1: Replace Guesswork with Real-Time Visibility
Alert fatigue often begins with uncertainty. Analysts spend hours dissecting fragmented data, trying to connect the dots between partial logs and incomplete alerts. When they can’t see the full story, every alert feels critical, and fatigue takes over.
Real-time behavioral visibility changes everything. With ANY.RUN’s Interactive Sandbox, your team watches the attack unfold in a safe environment. From the first process execution to registry changes and data exfiltration attempts, every move is mapped in real time.
That level of context replaces guesswork with confidence.
Check recent attack fully exposed in real-time
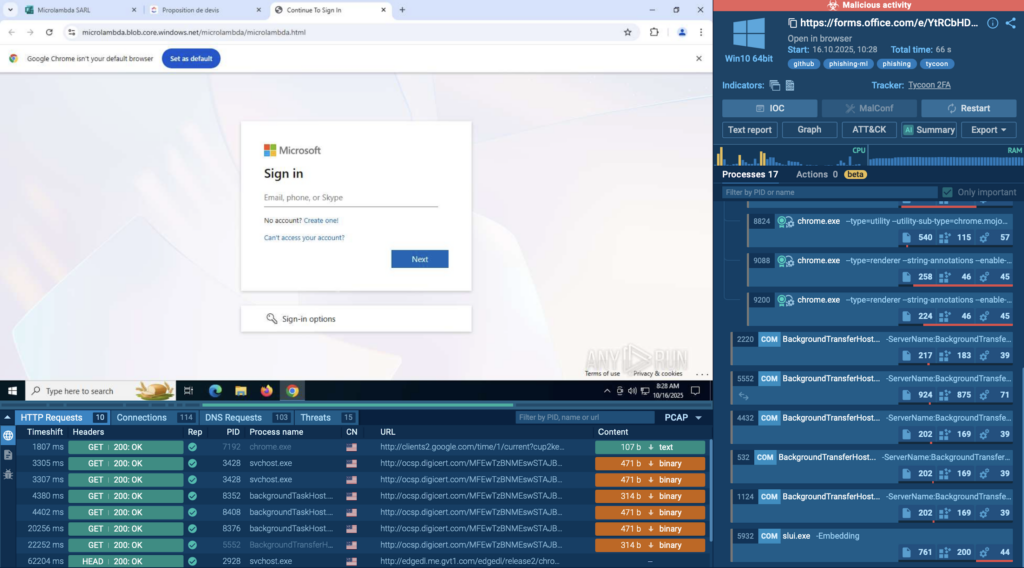
In the following example, analysts used the sandbox to expose a phishing attack that abused ClickUp to deliver a fake Microsoft 365 login page, uncovering the full chain in seconds.
With ANY.RUN’s real-time visibility, team achieve:
- 3× higher efficiency in daily operations
- 15 sec median MTTD
- Fewer false positives and missed threats
- Faster response and a calmer, more focused SOC
Step 2: Automate the Routine, Protect Human Focus
Even the strongest SOCs lose precious hours to repetitive work, copying IOCs, exporting reports, updating tickets. None of these tasks strengthen defense; they just drain energy and attention. Over time, that’s how alert fatigue turns into burnout.
But not every task can or should be automated. Many modern threats still require human-like interaction to be revealed: clicking a phishing link, solving a CAPTCHA, or scanning a QR code that hides a malicious redirect. Traditional tools stop short there.
That’s where automated interactivity changes everything.
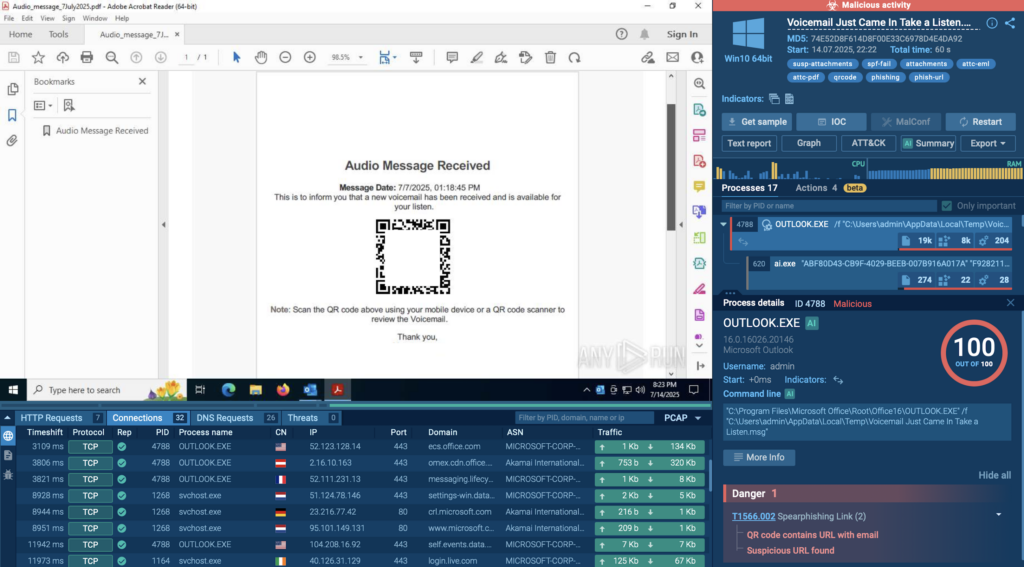
With ANY.RUN’s sandbox, analysts get the best of both worlds; automation that behaves like a human when automated interactivity is enabled. It clicks through phishing pages, solves CAPTCHAs, follows redirects, and even scans QR codes that hide malicious links. All of this happens automatically, revealing threats most tools would miss. And when deeper insight is needed, analysts can jump in at any point to interact directly.
Outcome of automation and interactivity:
- Hidden threats revealed that traditional tools can’t detect
- Faster investigations with less manual work
- Lower analyst fatigue through balanced automation
- Human control preserved for high-priority incidents
This combination helps analysts uncover complex threats in less time and enables Tier 1 teams to resolve more cases independently.
According to recent data among ANY.RUN’s users:
- 20% lower workload for Tier 1 analysts
- 30% fewer escalations from Tier 1 to Tier 2
Step 3: Integrate Live Threat Intelligence to Cut Through the Noise
Even the best SOCs struggle to stay focused when analysts waste hours chasing outdated data; verifying expired domains, checking inactive IOCs, or switching between disconnected tools just to confirm what’s real.

You can easily solve this with the help of live, connected intelligence.
ANY.RUN’s Threat Intelligence Feeds pull verified indicators from 15,000 organizations and 600,000 analysts worldwide, all sourced from real-time sandbox investigations. This means your team acts on current data, active phishing kits, live redirect chains, and real attacker infrastructure, not last month’s reports.

When this intelligence is integrated into your SOC tools, analysts no longer need to jump between platforms or second-guess stale alerts. Every IOC is backed by behavioral evidence and traceable to a live analysis.
With this setup, your team can:
- Validate alerts instantly using verified, real-time data
- Eliminate repetitive checks for outdated or inactive indicators
- Trace every IOC back to its full attack chain
- Make faster, evidence-based decisions without leaving their workflow
As a result, businesses achieve stronger detection, less context-switching, and sharper focus across all SOC operations.
Step 4: Create a Unified Response Workflow
Even the most advanced SOCs lose efficiency when investigations and follow-ups aren’t coordinated. Without clear ownership and visibility into who’s handling what, tasks overlap, progress stalls, and important findings slip through the cracks.
With ANY.RUN’s teamwork features, CISOs and SOC leads can manage investigations within a single workspace: assigning tasks, tracking analyst progress, and keeping every case organized.
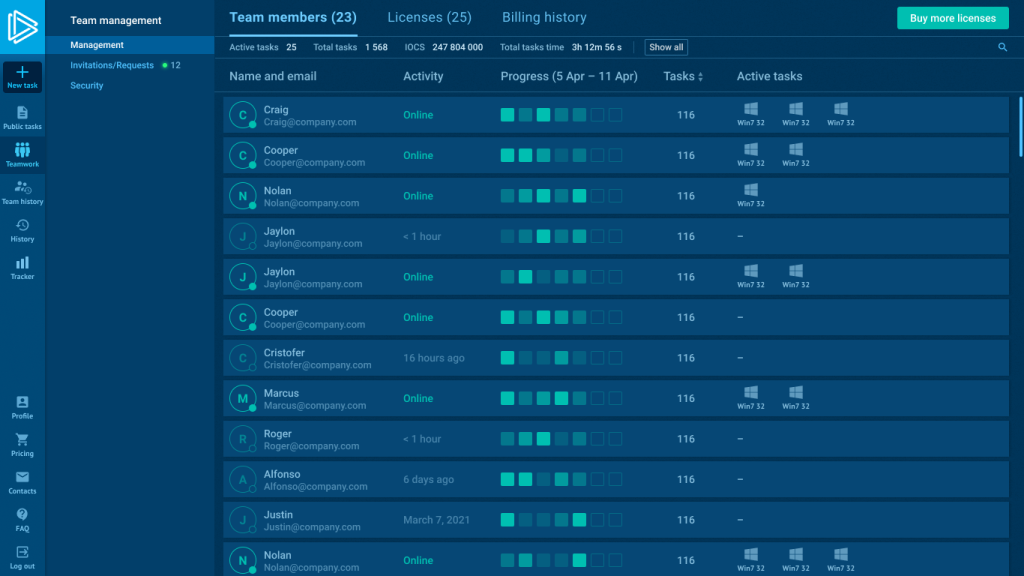
Each analysis also generates a structured, shareable report, so findings are easy to review, reuse, or hand off across shifts.
This unified workflow keeps everyone aligned, from initial detection to final response, while ensuring accountability and consistency across the SOC.
With a unified response workflow, you can ensure:
- Clear task ownership and visibility into investigation progress
- Structured, shareable reports for faster knowledge transfer
- Stronger coordination between analysts and response leads
- Higher overall efficiency with no duplicated effort
Time to Give Your Team a Break from the Noise
Alert fatigue is a sign of systems that demand too much and explain too little.
By giving your analysts real-time visibility, automation that understands context, and intelligence they can trust, you give them what they need most: focus.
When the noise quiets down, your team moves with intent; faster investigations, sharper decisions, and actions backed by real context instead of guesswork.
Talk to ANY.RUN experts to see how your SOC can leave alert fatigue behind.
About ANY.RUN
Built for modern SOC operations, ANY.RUN helps teams detect, analyze, and respond to threats in real time. Its Interactive Sandbox reveals full attack behavior, from process execution to network activity, giving analysts the clarity they need to act with confidence.
Compatible with Windows, Linux, and Android, the cloud-based sandbox provides deep behavioral visibility with no setup required. Integrated Threat Intelligence Lookup and TI Feeds deliver continuously updated, automation-ready IOCs that strengthen every layer of detection.








0 comments