Fresh, actionable IOCs from the latest malware attacks are now available to all security teams using the ThreatQ TIP. ANY.RUN’s Threat Intelligence Feeds integrate seamlessly with the platform, enabling SOCs and MSSPs to boost detection rates, expand threat coverage, and streamline response.
Here’s how you can benefit from it.
Real-Time Visibility of the Current Threat Landscape
As a leading Threat Intelligence Platform (TIP) widely adopted in enterprise SOCs, ThreatQ serves as a powerful indicator management solution, facilitating response.

ANY.RUN’s Threat Intelligence Feeds connector for ThreatQ provides a real-time stream of fresh, filtered, low-noise network IOC from sandbox investigations of the latest attacks by 15,000+ companies and 500,000+ analysts.
Follow a guide to implement in your SOC →
With STIX/TAXII support, TI Feeds can be made a part of SOCs’ security infrastructure without additional custom development or costs, helping them maximize the value of their existing ThreatQ setup. As a result, security teams can achieve:
- Early Detection: IOCs added to TI Feeds as soon as they emerge from live sandbox analyses, enabling proactive identification of new threats in your SOC.
- Expanded Threat Coverage: 99% unique indicators from global attacks (e.g., phishing, malware) provide visibility into threats traditional feeds miss.
- Informed Response: Each IOC comes enriched with a link to a sandbox report, showing the full attack being detonated on a live system, providing SOCs with actionable context for fast mitigation.
- Reduced Workload: Filtered for malicious alerts, cutting Tier 1 analysis time spent on false positives.
How SOC Teams Can Use TI Feeds: Case Example
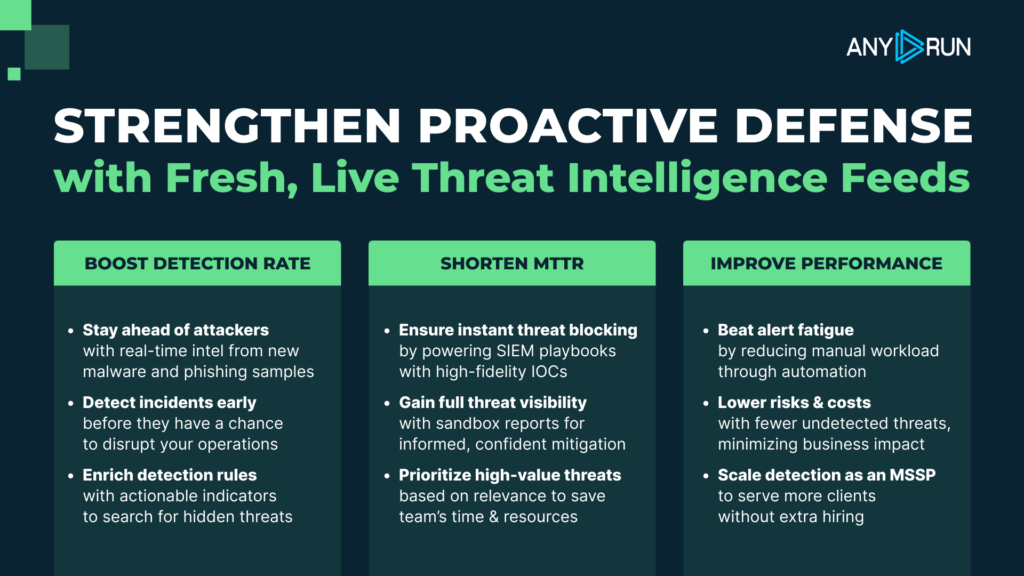
Threat Intelligence Feeds improve and simplify the core operations of security teams, delivering measurable results. Here’s a possible case for using our fresh threat intelligence to spot and contain attacks:
- Easy Setup for Fast IOC Delivery
Connect ANY.RUN’s TI Feeds to ThreatQ via STIX/TAXII in minutes. Choose hourly, daily, or custom schedules to get real-time IOCs from global incidents, keeping your SOC ahead of new threats.
- Power SOC Analysis with Actionable Data
ANY.RUN’s TI Feeds flow into ThreatQ, providing fresh IOCs to analyze alerts, investigate incidents, or enrich SIEM/EDR systems. This speeds up threat detection and strengthens your defense strategy.
- Streamline Response and Prevention
Use ANY.RUN’s IOCs in ThreatQ to automate threat blocking, isolate risks, or enhance playbooks and visualizations. SOC analysts and threat hunters can respond faster and prevent attacks, saving time and reducing breach risks.
How to Implement
The connector operates through the STIX/TAXII protocol, allowing clients to configure feed schedules within ThreatQ’s flexible options: hourly, every 6 hours, daily, bi-daily, bi-weekly, or monthly updates.
ThreatQ leverages ANY.RUN data for real-time or scheduled analysis as a malicious indicator source for alert and incident investigation. With additional connectors, organizations can optionally forward intelligence to their SIEM/EDR systems.
Workflow Capabilities
Depending on configuration settings, the system supports:
- Manual or automated response actions (isolation, blocking, escalation)
- Investigation enrichment and new rule/playbook configuration
- Advanced visualizations for analysts and threat hunters
Quick Setup Guide with 5 Easy Steps:
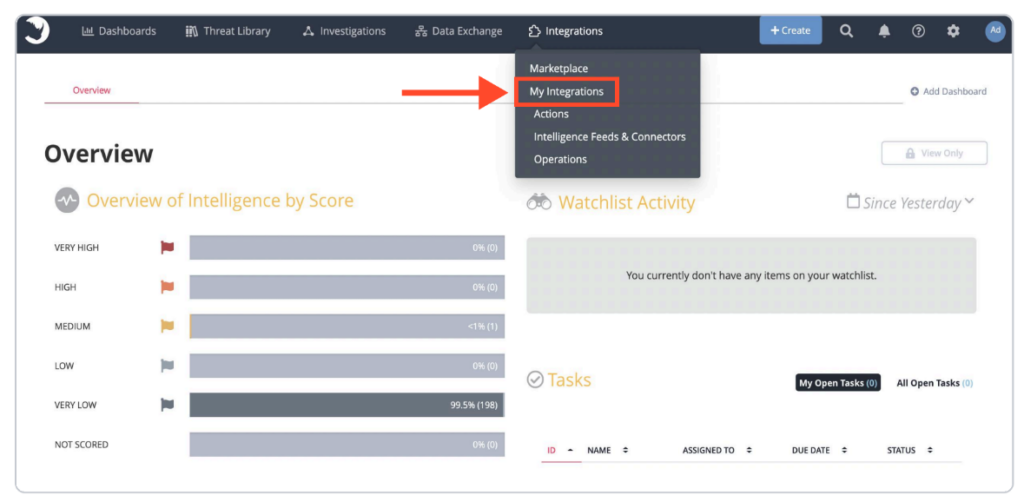
1. Open ThreatQ and click My Integrations in the Integrations tab.
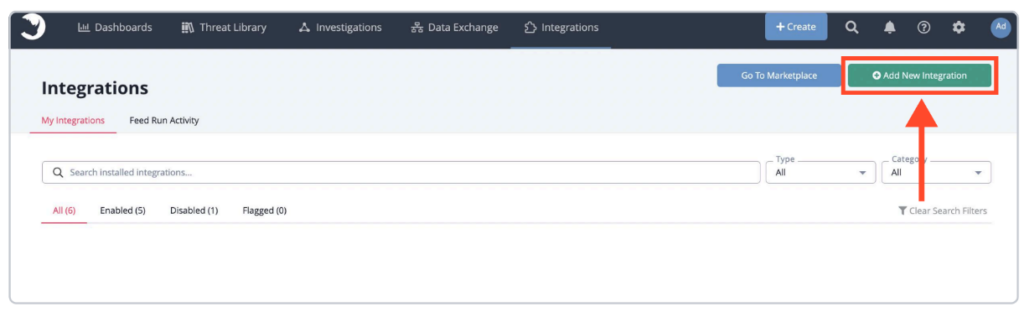
2. Click Add New Integration.
3. Configure TAXII Connection: go to the tab Add New TAXII Feed, fill out the configuration form.
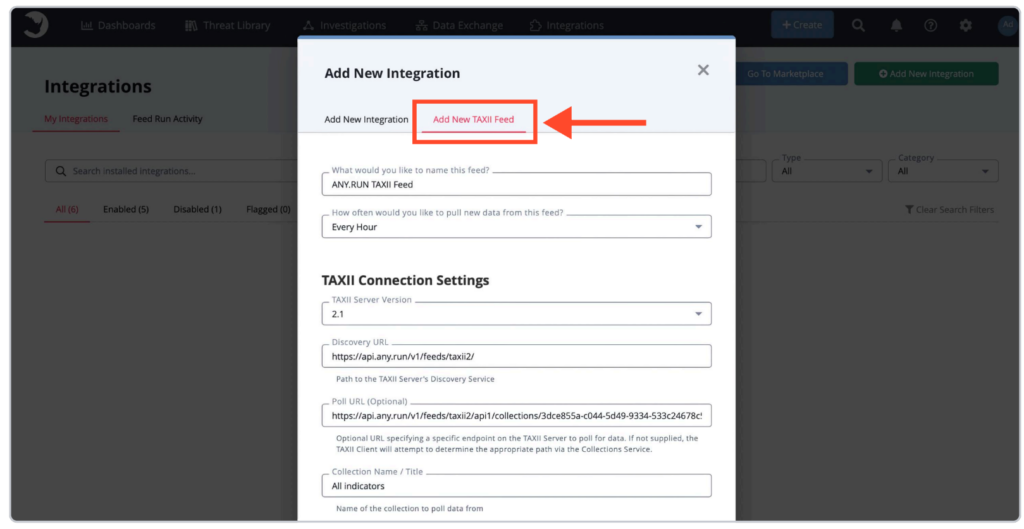
For detailed information, see ANY.RUN’s TAXII connection documentation.
4. After adding the TAXII feed, click on the settings button in the created connector card. Set switch to Enabled, and you’re all set up.
5. After finalizing the configuration, use the retrieved indicators to:
- Export them to SIEM/SOAR to automate detection and blocking of threats
- Prioritize high-risk threats to stay focused on the most critical incidents
- Combine them with data from other sources to gain full visibility into attacks
- Enrich and accelerate threat hunting and investigations with actionable intelligence
- Launch playbooks for automated response to threats.
About ANY.RUN
ANY.RUN is trusted by more than 500,000 cybersecurity professionals and 15,000+ organizations across finance, healthcare, manufacturing, and other critical industries. Our platform helps security teams investigate threats faster and with more clarity.
Speed up incident response with our Interactive Sandbox: analyze suspicious files in real time, observe behavior as it unfolds, and make faster, more informed decisions.
Strengthen detection with Threat Intelligence Lookup and TI Feeds: give your team the context they need to stay ahead of today’s most advanced threats.
Want to see it in action? Start your 14-day trial of ANY.RUN today →







0 comments