In ANY.RUN, we have proprietary mechanisms in place to keep malware from realizing it’s in a sandbox. We’re rolling out another feature to mask sandbox activity — Residential proxy (RP). Now, you’ll be able to allocate a home users’ IP address to your VMs, effectively erasing any traces that can hint at a sandbox environment from your network traffic.
Here’s what it means in practice:
- Understand malware behavior better: because malware won’t detect sandbox or data center’s IP, it will behave normally, allowing for accurate analysis.
- Bypass geo-restrictions: emulate local users to analyze region-specific threats.
- Investigate C2 traffic without giving yourself away: your connection will mimic an infected user.
Residential proxy’s greatest power is in analysis of geo-targeted attacks — especially when dealing with phishing. In some phishing campaigns, users are rerouted to different pages based on their geographic location. And some attacks analyze if the traffic is coming from a hosting to detect sandboxes. But with our new feature, you can effectively sidestep these detection attempts.
Here’s how it all works in practice.
Avoid anti-analysis techniques
In our initial analysis of this Xworm sample, we ran into a challenge. The sample is designed to detect traffic from a host and stops executing if it detects a sandbox environment. It sends a request to ip-api[.]com, checking for the ‘hosting’ parameter. If the returned response is ‘true’, execution is aborted.
Here’s how the network stream looks like without Residential proxy:
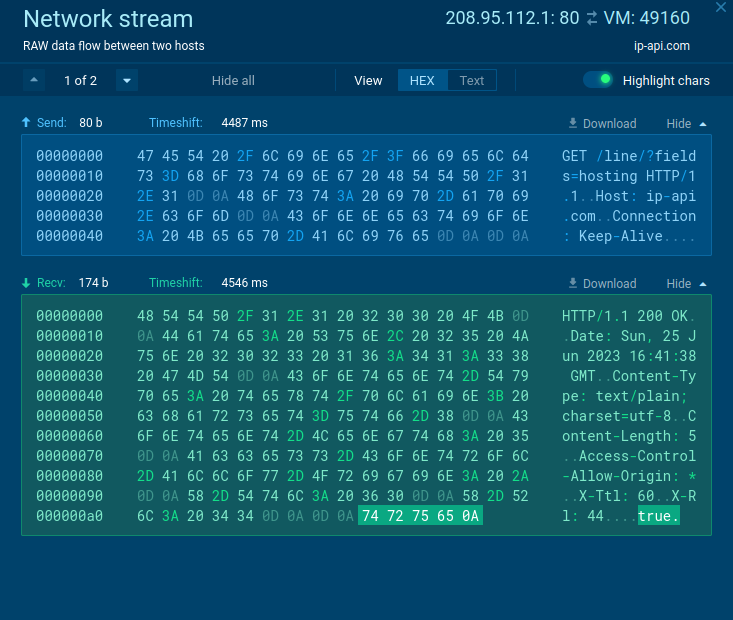
Typically, malware employs this strategy to evade sandboxes, assuming that regular user traffic wouldn’t originate from a hosting service.
We can evade detection by activating the Residential proxy and re-running the task:
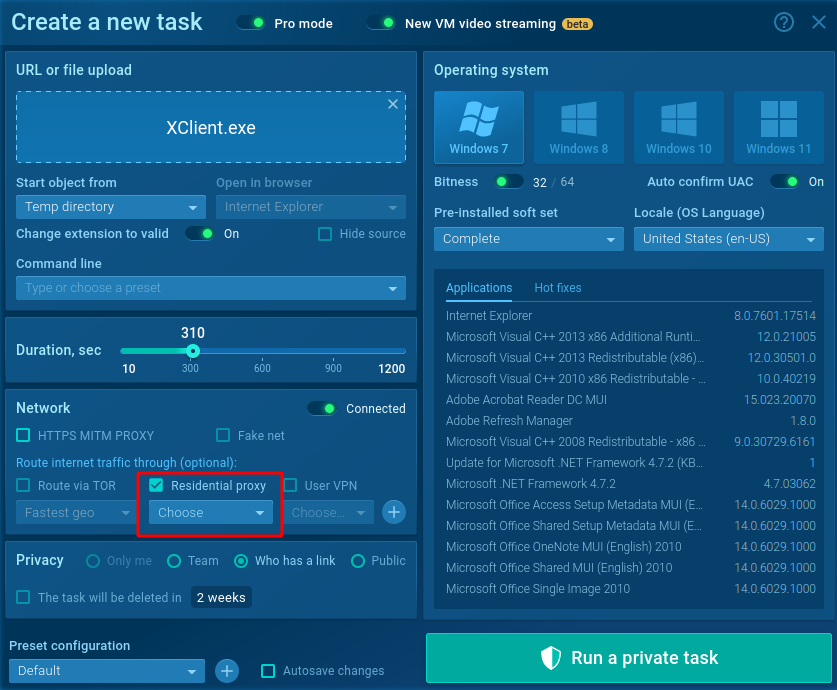
To do so, simply check the Residential proxy checkbox during your environment configuration. Then, choose the geolocation of your IP.
This time around, ip-api[.]com responds with a ‘false’ when queried if the traffic originates from a hosting site. As a result, the sample executes fully. This evasion worked because the Residential proxy masked the hosting origin of the traffic.
Analyze geo-targeting phishing websites more accurately
Now, you can also use the Residential proxy to analyze geo-targeted phishing campaigns faster and better. Some phishing websites target users from a particular country, verifying their origin before displaying the page. If the users — or analysts — aren’t from the target country, they’re left staring at a blank screen.
Here’s an example of a suspicious website that targets users from Italy. Noticing that its domain name was registered 2 weeks ago at the time of analysis, we decided to investigate further. But first, we analyzed it without selecting a proxy.
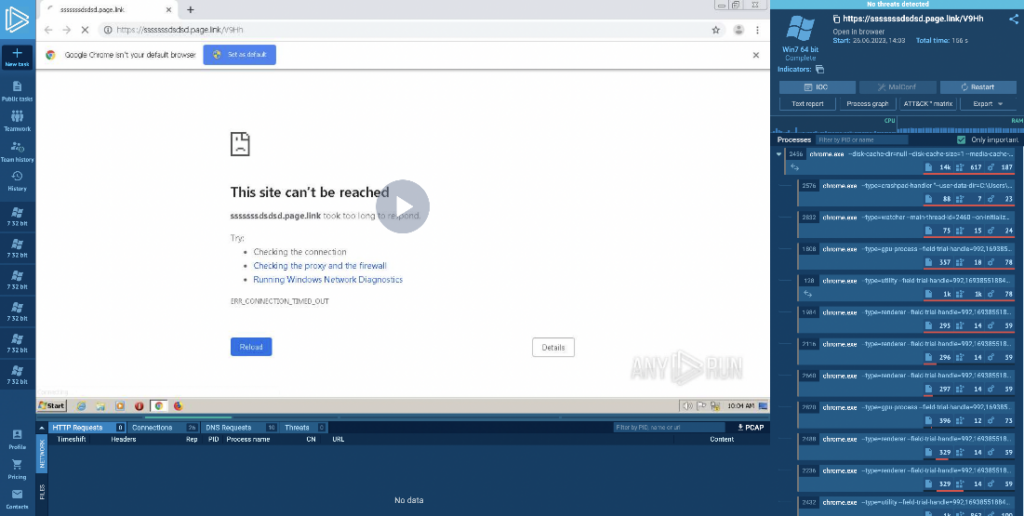
Predictably, the webpage hasn’t loaded. But we can fix this by setting the proxy to Italy and re-launching the task. Here’s the same website with proxy set to Italy:
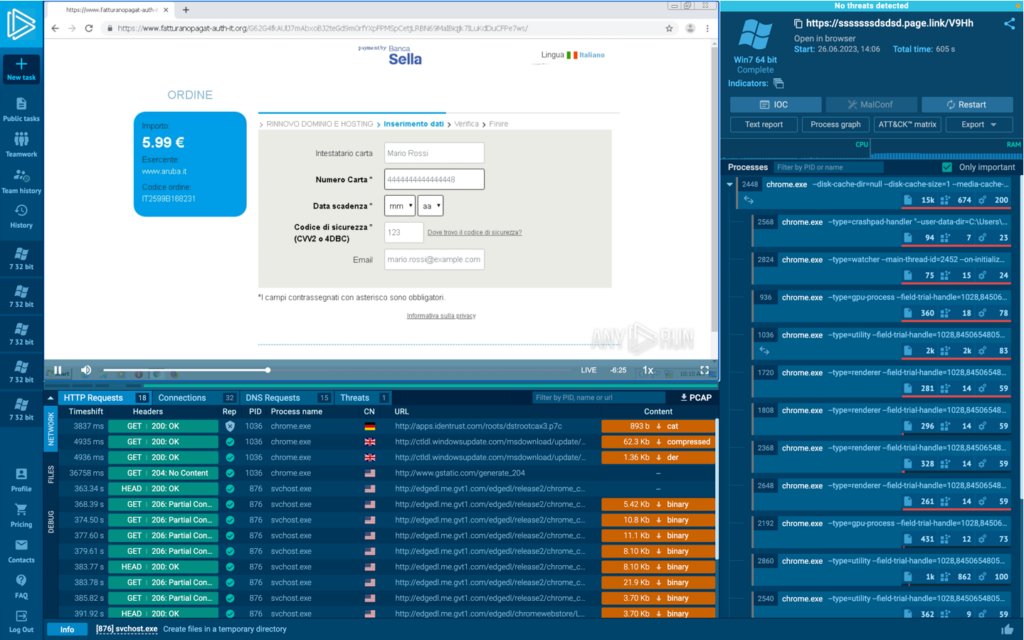
That’s better!
That’s how the Residential proxy improves our ability to analyze malicious and potentially harmful samples and websites. It gives analysts the tools they need to extract maximum information from each analysis.
Apply for 14 days free trial of ANY.RUN to test this feature.








0 comments