Every piece of malware leaves traces behind. Sometimes it’s a string buried deep in the code. Other times it’s a mutex, a registry key, or a network pattern. The key is knowing what to look for.
That’s exactly what malware signatures are for. They describe these recurring elements, unique strings, behaviors, or structural patterns, that can be used to reliably identify known threats.
Security teams use these signatures to detect and flag malicious activity; sometimes before the malware even has a chance to do damage.
In this article, we’ll break down what malware signatures are, the different types you’ll encounter, and how tools like YARA and Suricata help turn small clues into confident decisions.
What Is a Malware Signature?
A malware signature is a unique indicator tied to a specific piece of malicious software. It could be a text string, a file hash, a mutex, or even a sequence of behaviors. Security tools use these signatures to recognize and flag known threats, kind of like matching fingerprints at a crime scene.
The goal is simple: spot malware based on something that consistently shows up across samples from the same family or campaign. Once identified, these signatures become part of detection rules used by antivirus engines, sandboxes, and intrusion detection systems.
How Are Malware Signatures Created?
Malware signatures are usually crafted by security researchers and automated detection systems after analyzing how a threat behaves or what it contains.
When a new malware sample is discovered, analysts break it down, looking at code, memory behavior, registry changes, network traffic, and other markers. If they notice something unique or consistently present across samples, like a specific mutex name, string, or packet structure, that becomes a potential signature.
Depending on the tool or platform, these signatures might take different forms;
- Static signatures are based on strings, byte sequences, or file hashes.
- Behavioral signatures are based on what the malware does, like creating certain processes or modifying the registry.
- Custom rules, like YARA or Suricata, allow analysts to define more complex patterns based on real-world observations.
Main Types of Malware Signatures
Not all malware looks or behaves the same, and the same goes for how we detect it. Over time, security teams have developed different types of signatures to match different kinds of threats.
Here are the most common ones:
Static Signatures
These are the most traditional and widely used. Static signatures match fixed elements inside a file, like strings, byte sequences, or hashes, without needing to run the malware.
Key traits:
- Match based on file content (strings, hex patterns, hashes)
- Fast and efficient for known threats
- Can be bypassed through obfuscation or slight code changes
- Commonly used in antivirus software
Heuristic Signatures
Heuristic signatures look beyond exact matches. They evaluate the structure or logic of a file to identify suspicious patterns that may indicate malware, even if the sample is new or modified.
Key traits:
- Detect threats based on suspicious code structures
- Useful for catching variants or zero-day malware
- May generate false positives if too broad
- Often found in email filters, AVs, and static analyzers
Behavioral Signatures
Rather than scanning a file, these signatures monitor what it does when executed. If it behaves like malware, e.g., injecting code or modifying the registry, it gets flagged.
Key traits:
- Trigger on real-time actions and behaviors
- Great for catching fileless or evasive malware
- Requires sandboxing or endpoint monitoring
- Common in EDRs, sandboxes, and dynamic analysis tools

Learn to analyze cyber threats
See a detailed guide to using ANY.RUN’s Interactive Sandbox for malware and phishing analysis
How Detection Tools Use Signatures: YARA and Suricata
Once malware signatures are defined, they need to be used effectively, and that’s where tools like YARA and Suricata come in. Each serves a unique purpose: one focuses on files and memory, the other on network traffic. Together, they cover a wide range of threats and detection angles.
YARA Signatures: Matching Patterns in Files and Processes
YARA is a rule-based detection tool that helps analysts identify malware by describing textual or binary patterns. It’s especially powerful for hunting threats across memory dumps, unpacked payloads, or large malware datasets.
YARA helps security teams quickly identify threats by matching known patterns in files, processes, or memory. It automates what would otherwise be a slow, manual process, making detection faster, more accurate, and more scalable.
Its real strength lies in customization. Teams can write tailored rules to catch specific malware strains or adapt to new threats as they emerge. When combined with ANY.RUN’s interactive sandbox, YARA also reveals how they behave, giving organizations the insight they need to act fast and prevent damage.
Key benefits of YARA in a security workflow:
- Speeds up detection and reduces manual effort
- Detects both known and emerging malware families
- Cuts down false positives with precise rules
- Boosts efficiency across security teams
- Helps contain threats early and minimize risk
Real-World Example: Matching the Mutex Pattern
YARA rule example pulled from ANY.RUN sandbox analysis
Let’s look at an example of YARA rule used in ANY.RUN’s sandbox:
$s6 = “Local\\SM0:%d:%d:%hs” wide
This string is part of a rule designed to detect mutexes created by certain malware families.
To see this signature in action, check out this ANY.RUN analysis session.
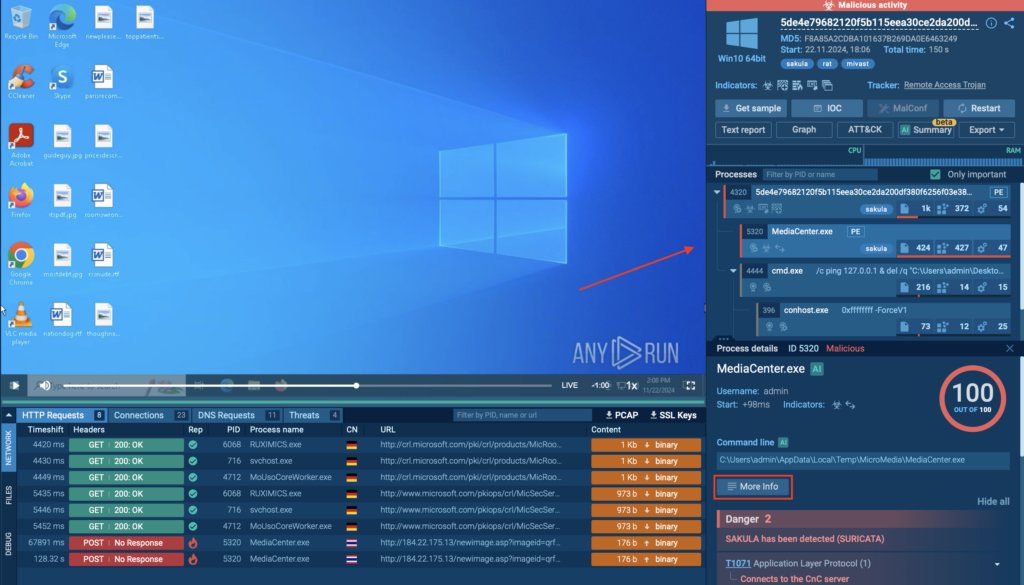
Navigate to the MediaCenter.exe process → More Info → Synchronization tab.
There, you’ll find the mutex: Local\SM0:5320:168:WilStaging_02
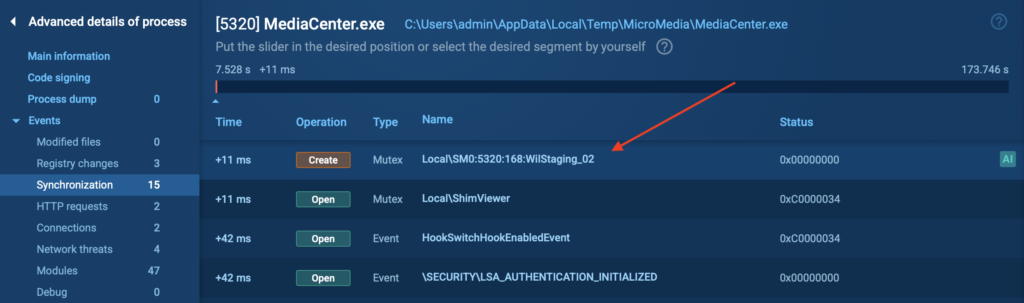
This mutex exactly matches the YARA signature pattern. The use of placeholders like %d and %hs allows the rule to flexibly detect variations of this format across different samples.
- %d matches any sequence of digits (0–9)
- %hs matches a short string or hexadecimal value, typically 2 bytes
This is a great example of how YARA rules aren’t just powerful, they’re also adaptable to the real-world quirks of evolving malware behavior.
Suricata Signatures: Detecting Malicious Behavior in Network Traffic
While YARA focuses on identifying malware based on what it is, Suricata helps detect malware based on what it does across the network. It’s an advanced intrusion detection system (IDS) that monitors real-time traffic and flags suspicious behavior using both signature- and anomaly-based techniques.
ANY.RUN integrates Suricata to enhance threat visibility at the network level, allowing analysts to catch threats as they try to communicate with command-and-control servers, exfiltrate data, or spread laterally. Suricata signatures give security teams immediate context; what’s happening, where, and why it matters.
Key benefits of Suricata in a security workflow:
- Detects malicious traffic and C2 communication in real time
- Complements file-based detection with network-layer visibility
- Helps attribute threats to specific malware families
- Speeds up incident response with actionable alerts
- Empowers teams with visibility into protocol activity across multiple layers
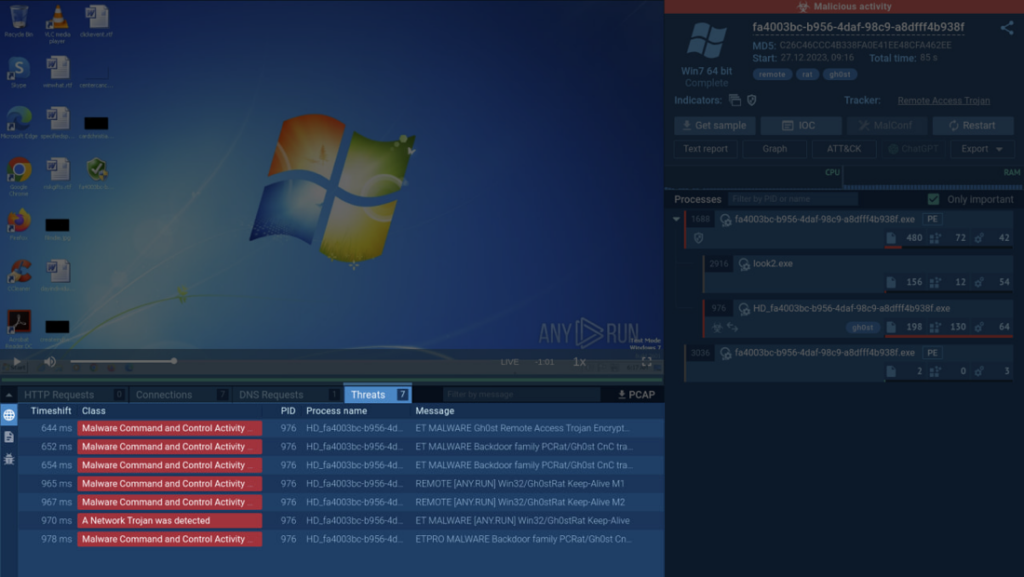
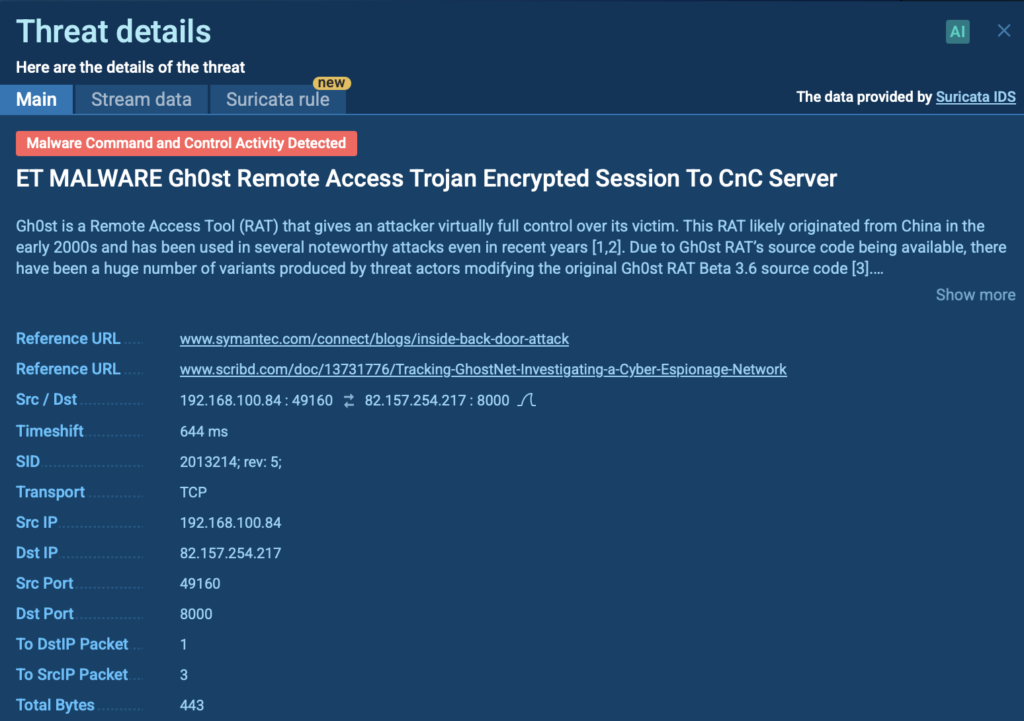
In ANY.RUN, Suricata rules are applied automatically during sandbox analysis. Let’s take a look at a real-world detection involving Gh0st Remote Access Trojan (RAT).
View analysis session with Gh0st RAT
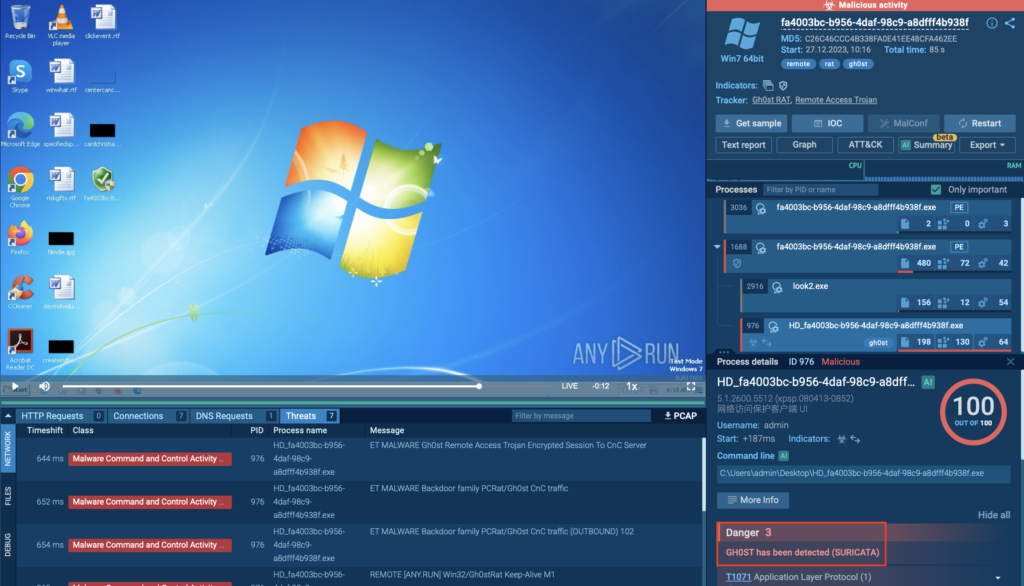
After execution, the sample initiates suspicious encrypted traffic. Suricata instantly detects it and flags the connection as Gh0st RAT activity.
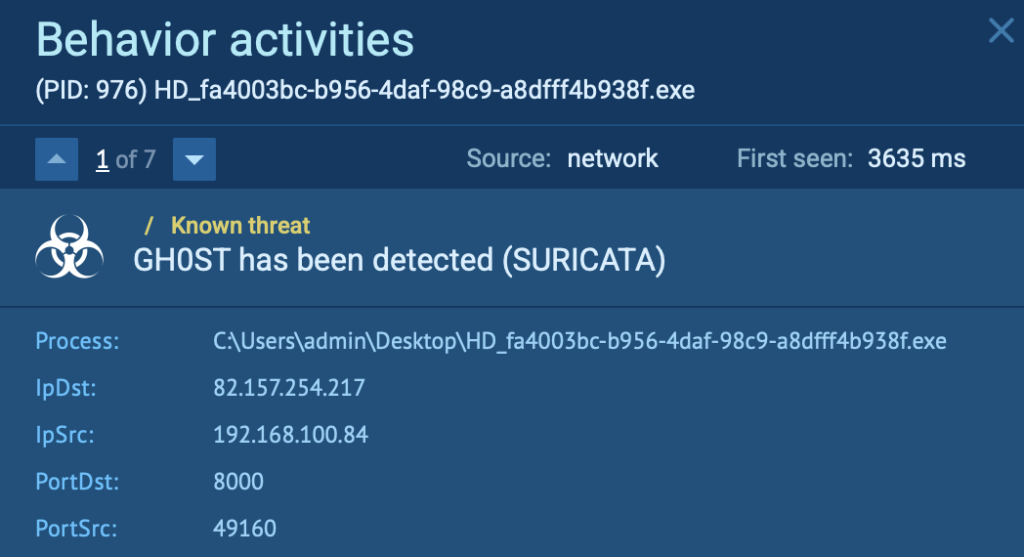
How it works:
- Suricata inspects packets across protocols (HTTP, TCP, UDP, etc.)
- It matches patterns defined in the ET (Emerging Threats) rule sets
- Once a match is found, it provides detailed metadata: source/destination IPs, ports, signature ID, and threat name
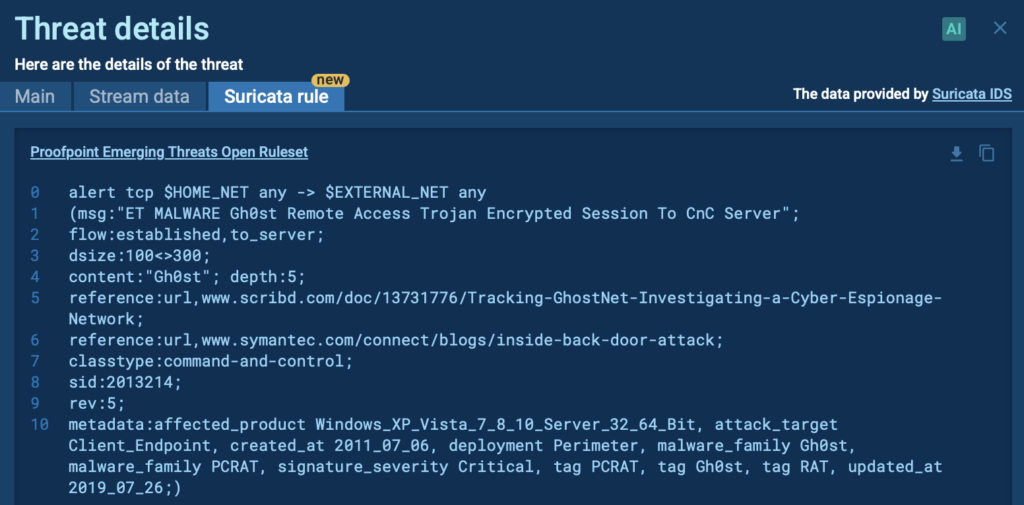
By switching to the Suricata rule tab, you’ll be able to inspect it more thoroughly.
Making the Most of Malware Signatures in ANY.RUN
Malware signatures can do a lot on their own but when they’re used in the right environment, they become even more useful.
Inside ANY.RUN’s sandbox, YARA and Suricata work together to give you the full picture. You can see what a file is doing locally, spot mutexes, registry changes, and other signs of malicious behavior, then switch to the network layer to catch things like encrypted C2 traffic or data exfiltration. Both angles are covered, without having to jump between tools.
Instead of switching between tools, analysts get everything in one place; interactive, real-time, and backed by constantly updated signature sets. This gives less time digging and more time acting.
If your goal is to reduce investigation time, improve detection accuracy, and truly understand how malware behaves, ANY.RUN puts those capabilities right at your fingertips.
About ANY.RUN
ANY.RUN is used by over 500,000 cybersecurity professionals and 15,000+ companies across finance, manufacturing, healthcare, and other industries. Its Interactive Sandbox offers fast threat analysis for Windows, Linux, and Android, aiding malware and phishing investigations. Threat Intelligence Lookup and TI Feeds enhance cyber attack knowledge and detection.








0 comments