Welcome to the April 2023 edition of our monthly malware analysis digest.
ANY.RUN’s aim is to keep you up-to-date with the latest cybersecurity events and emerging threats that have surfaced over the past month. So let’s dive into the key highlights and developments in the world of malware and cybersecurity that occurred in April 2023.
1. GuLoader Resurfaces in Fake Shipping Notification Emails
GuLoader, a notorious downloader used in email-based malware campaigns since 2019, has reemerged in the wild. In the past, it has disguised itself as various attachments, including a health e-book sent from the World Health Organization. GuLoader is primarily used to deliver payloads for different campaigns, including data stealers, trojans, and other forms of malware. Its design allows it to evade network detection and bypass sandbox technology.
In a recent incident, a bogus shipping notification email written in Italian was identified as containing GuLoader. Unlike previous instances, GuLoader was not hidden inside a ZIP file. instead, it was found in an .ISO file disguised as a fake .JPG file with a double extension — an old trick that still proves effective.
2. RedEyes Threat Group Distributes RokRAT via LNK Files
The RedEyes threat group (also known as APT37 or ScarCruft) has been distributing the RokRAT malware through LNK files. Confirmed file names so far are:
- 230407Infosheet.lnk
- April 29th 2023 Seminar.lnk
- 2023 Personal Evaluation.hwp.lnk
- NK Diplomat Dispatch Selection and Diplomatic Offices.lnk
- NK Diplomacy Policy Decision Process.lnk
The LNK files contain PowerShell commands that perform malicious behavior alongside a normal file. The PowerShell command executed through cmd.exe reads the LNK file, saves, and executes it in the Temp folder, appearing as a normal PDF before carrying out malicious behavior.
3. ‘Decoy Dog’ Malware Toolkit Targets Enterprises
Researchers from Infoblox discovered a new enterprise-targeting malware toolkit named ‘Decoy Dog’ by analyzing over 70 billion DNS records daily for signs of abnormal or suspicious activity.
Decoy Dog helps threat actors evade detection through strategic domain aging and DNS query dribbling. The toolkit’s DNS fingerprint is unique and rare among the 370 million active domains on the internet. The investigation led to the discovery of several command and control (C2) domains linked to the same operation.
Decoy Dog deploys the Pupy RAT, a modular open-source post-exploitation toolkit popular among state-sponsored threat actors.
4. QBot Changes Tactic and Threatens Business Networks with New Phishing Campaign
Qbot, an infostealer-turned-dropper malware, is now being distributed through a phishing campaign that uses PDFs and Windows Script Files (WSF). QBot’s presence in company systems can be disastrous, as it’s used by operators of ransomware-as-a-service (RaaS) offerings.
The attack starts with a reply-chain phishing email in various languages, targeting businesses worldwide. When a user opens the attached PDF and clicks the “open” button, a ZIP file containing the WSF script is downloaded. The heavily obfuscated script triggers a PowerShell that downloads the QBot DLL from a list of hardcoded URLs, which is then executed.
According to ANY.RUN public submissions, QBot ranked among the top 10 malware families in April 2023, indicating a high likelihood for organizations to encounter this threat in the wild.
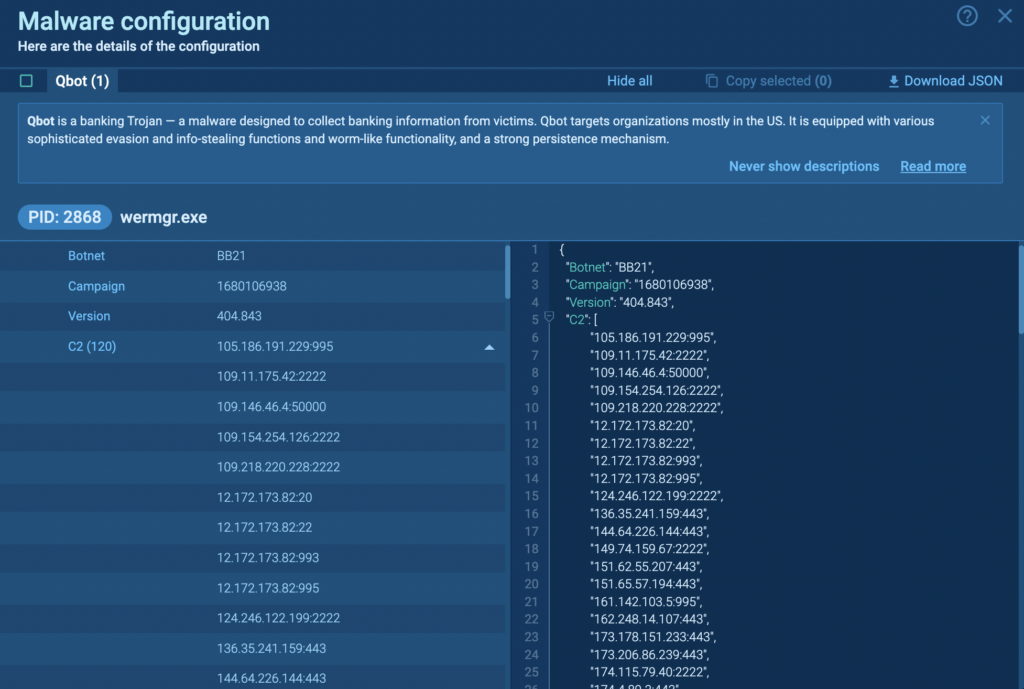
ANY.RUN’s cloud-based interactive sandbox can swiftly analyze QBot, streamlining your workflow and providing vital information — like malware configuration details — in under a minute.
Here are the indicators of compromise identified during the analysis of a recent QBot sample:
| SHA256 | 4a579d7776ea76dc53cf2718e602e4f52661a5caf46dd61b3e6fd4fca1e29ff1 |
| SHA1 | 7a7806f2b5f1ed4f5ca834bc33173af790b5c704 |
| MD5 | 8876d4836d456c2c657c905b33c612e0 |
5. Zaraza Bot Credential-Stealer Targets 38 Web Browsers, Sold on Telegram
A new credential-stealing malware called Zaraza bot is being offered for sale on Telegram and uses the messaging service as a command-and-control (C2) platform.
The malware targets 38 different web browsers, including Google Chrome, Microsoft Edge, and Opera, and can capture screenshots of the active window. It is currently unclear how the malware is propagated, but information stealers have previously used methods such as malvertising and social engineering.
6. Play Ransomware Gang Develops Custom Shadow Volume Copy Data-Theft Tool
The Play ransomware group has created two custom tools, Grixba and VSS Copying Tool, to enhance the effectiveness of their cyberattacks.
The new .NET tools allow attackers to enumerate users and computers in compromised networks, gather information about security, backup, and remote administration software, and copy files from the Volume Shadow Copy Service (VSS) to bypass locked files.
Grixba is a network-scanning and information-stealing tool used to enumerate users and computers in a domain, while VSS Copying Tool interacts with VSS via API calls, allowing Play ransomware to steal files from existing shadow volume copies even when those files are in use by applications.
7. Active Zero-Day Vulnerability Exploit Released for GoAnywhere MFT Administrator Consoles
An exploit code has been made public for an actively targeted zero-day vulnerability affecting internet-exposed GoAnywhere MFT admin consoles.
Developed by Fortra (previously HelpSystems), GoAnywhere MFT is a web-based managed file transfer solution that assists organizations in securely transferring files and maintaining audit logs for accessed shared files.
Florian Hauser, a security researcher from Code White, released technical information and a proof-of-concept exploit code for unauthenticated remote code execution on susceptible GoAnywhere MFT servers. According to a Shodan scan, nearly 1,000 GoAnywhere instances are exposed online, with over 140 on ports 8000 and 8001, which are associated with the vulnerable admin console.
8. Former Conti Members and FIN7 Developers Collaborate to Launch New Domino Malware
Ex-members of the Conti ransomware group have joined forces with FIN7 threat actors to launch a new malware family called ‘Domino’ in attacks targeting corporate networks.
The Domino malware family is comprised of two components: the ‘Domino Backdoor’ and the ‘Domino Loader,’ which injects an info-stealing malware DLL into another process. IBM’s Security Intelligence researchers have been monitoring ex-Conti and TrickBot members using the new malware in attacks since February 2023. A recent IBM report links the development of the Domino malware to the FIN7 hacking group, a cybercriminal organization connected to various malware and the BlackBasta and DarkSide ransomware operations.
9. LockBit Ransomware Encryptors Now Target Mac Devices
The LockBit ransomware gang has developed encryptors targeting Mac devices for the first time, making them the first major ransomware operation to specifically target macOS.
The new ransomware encryptors discovered in a ZIP archive contained most of the available LockBit encryptors. Previously, LockBit encryptors were designed for Windows, Linux, and VMware ESXi server attacks. The newly discovered archive also contains encryptors for macOS, ARM, FreeBSD, MIPS, and SPARC CPUs. It is likely that the current encryptors are test builds, not yet ready for deployment in actual attacks against macOS devices.
10. Fastest Ransomware Encryptor Yet: New Rorschach Ransomware Discovered
Researchers have discovered a new ransomware strain named Rorschach, which appears to be the fastest encryptor to date.
The malware was found following a cyberattack on a US-based company and is reported to have “technically unique features.” Rorschach was deployed using the DLL side-loading technique via a signed component in Cortex XDR, a product from Palo Alto Networks. The ransomware creates a Group Policy when executed on a Windows Domain Controller to propagate to other hosts on the domain.
Notably, Rorschach’s encryption scheme blends the curve25519 and eSTREAM cipher hc-128 algorithms and follows the intermittent encryption trend, meaning it only encrypts files partially, increasing its processing speed. In a test with 220,000 files on a 6-core CPU machine, Rorschach encrypted the data in 4.5 minutes, while LockBit v3.0, previously considered the fastest ransomware, took 7 minutes.
ANY.RUN April News
April marked our 7th anniversary, which we commemorated with exclusive deals and promotions for both our free and business users. These included extra months when purchasing select plans and temporary access to PRO features for free users, such as setting up cloud sandboxes with Windows 10 and 11 operating systems.
We also introduced a guides and tutorials hub, compiling helpful articles from our blog into a single, convenient location. Be sure to visit the hub for insights on effectively utilizing our cloud sandbox.
Additionally, we delved into the encryption and decryption methods employed by PrivateLoader and provided an overview of the most prevalent malware types and families used by threat actors in Q1 2023.








0 comments