We’re excited to announce that ANY.RUN added Linux support. Now, malware analysts, SOC and DFIR team members can analyze not only Windows malware but also Linux-based samples in a secure, interactive cloud environment — with the advantages of ANY.RUN.
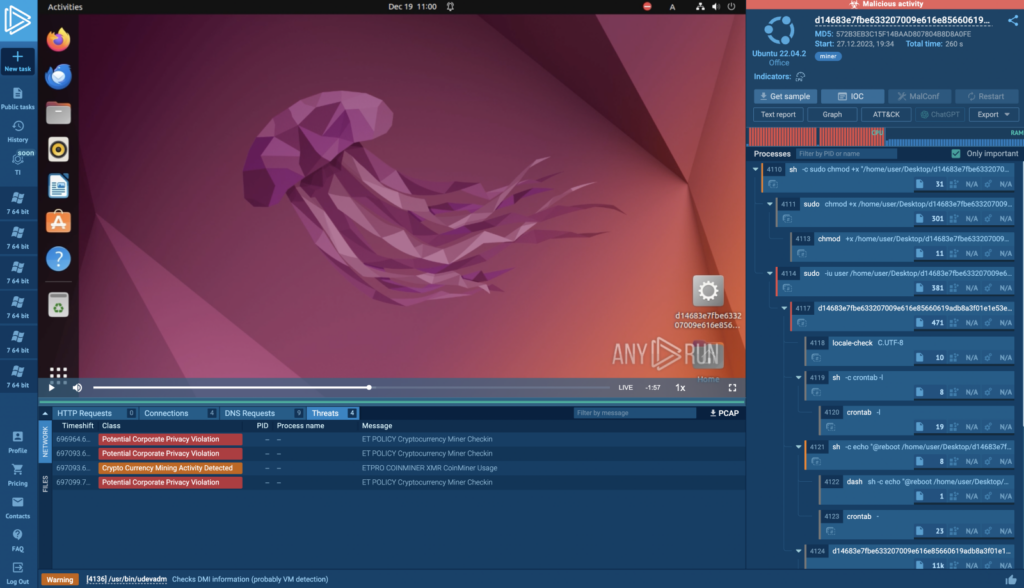
How to launch Linux tasks in ANY.RUN
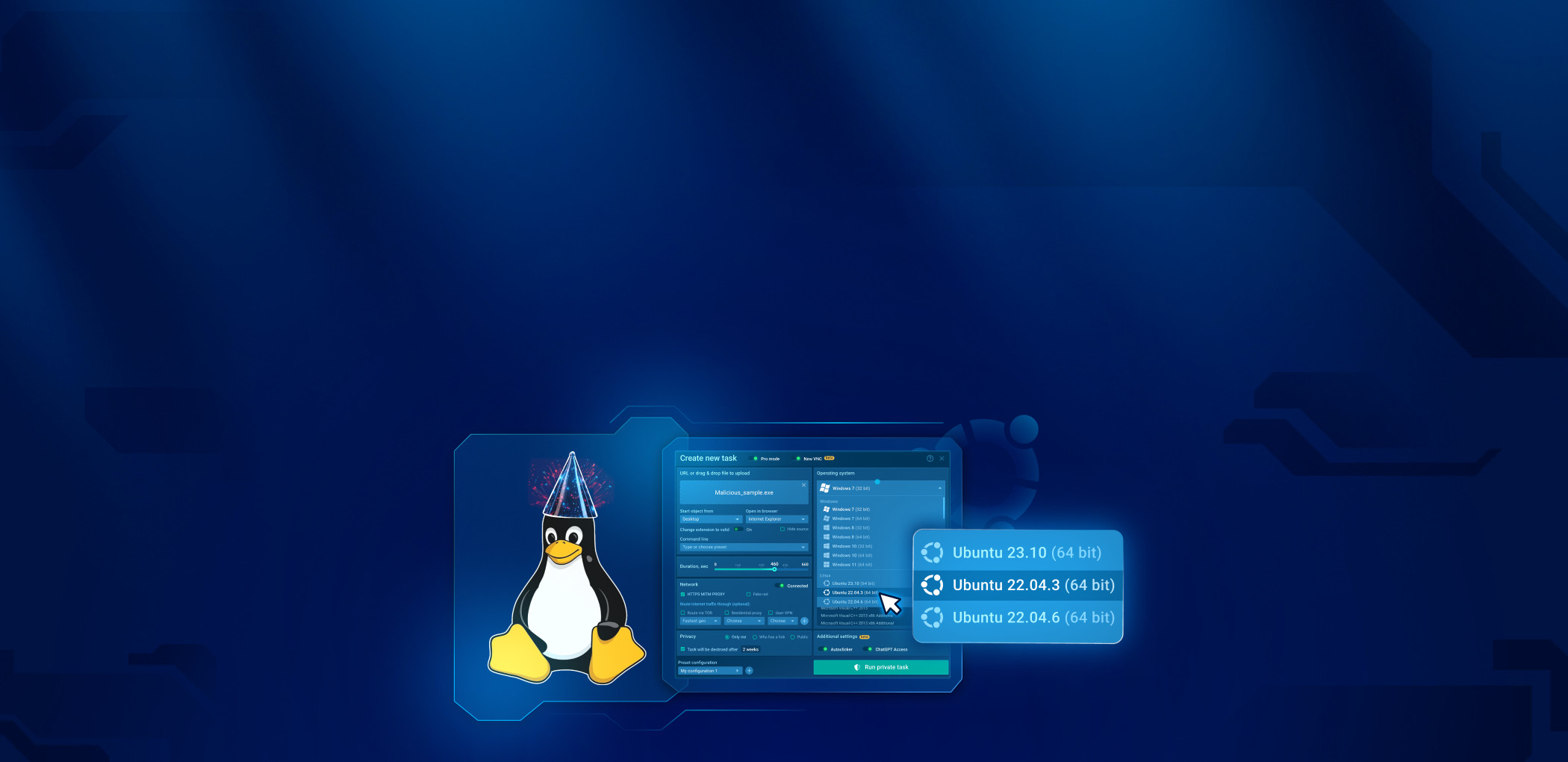
When creating a new task, you will now see Linux as an option in the Operating system drop-down. Select it, and the sandbox will run Linux VM for you. At launch, Ubuntu 22.04.2 is supported.
For simple navigation we marked Linux samples with an Ubuntu logo — it will make it easy to determine which tasks are Windows-based and which are Linux-based in the sidebar quick menu and in the team’s homepage menu.
Why Linux malware analysis is important
Linux malware analysis is important because Linux is an attractive target for hackers, and Linux malware is sophisticated.
Many organizations use Linux for their IT infrastructure, which means there are a lot of files to analyze on Linux systems.
IBM researchers note that Linux malware is on the rise. There’s been a 40% increase in Linux-related malware families in 2020. Compromising Linux-based cloud computing platforms could grant attackers access to vast resources, which makes the OS an attractive target.
Bringing advantages of ANY.RUN to Linux malware analysis
For the first time, we’re bringing the power of ANY.RUN’s interactive analysis to Linux. ANY.RUN already helps analysts from junior to senior levels accelerate threat analysis with Windows samples, while spending fewer resources and providing faster training for entry-level analysis and reverse engineers.
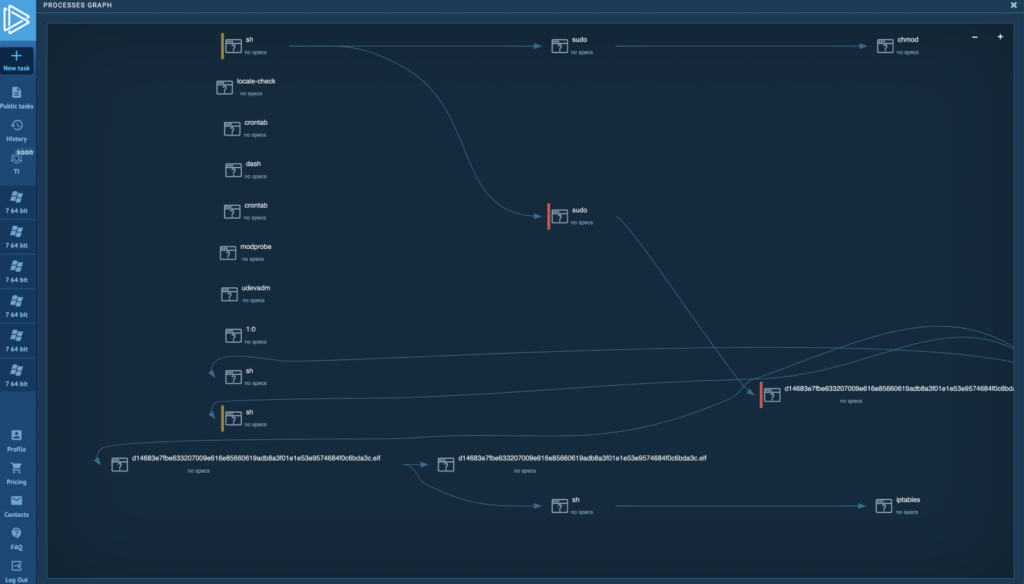
ANY.RUN’s built around the concept of interactive analysis — it lets an analyst detect hidden threats faster by changing the vector of analysis even when dealing with zero days. For the first time, it is available for Linux. Our service shows suspicious activity to the analyst in real time, making sure no important details go unnoticed. When the task is completed, users get a series of clear reports, making sure that every analyst has all necessary data and IOCs for further research or incident response.
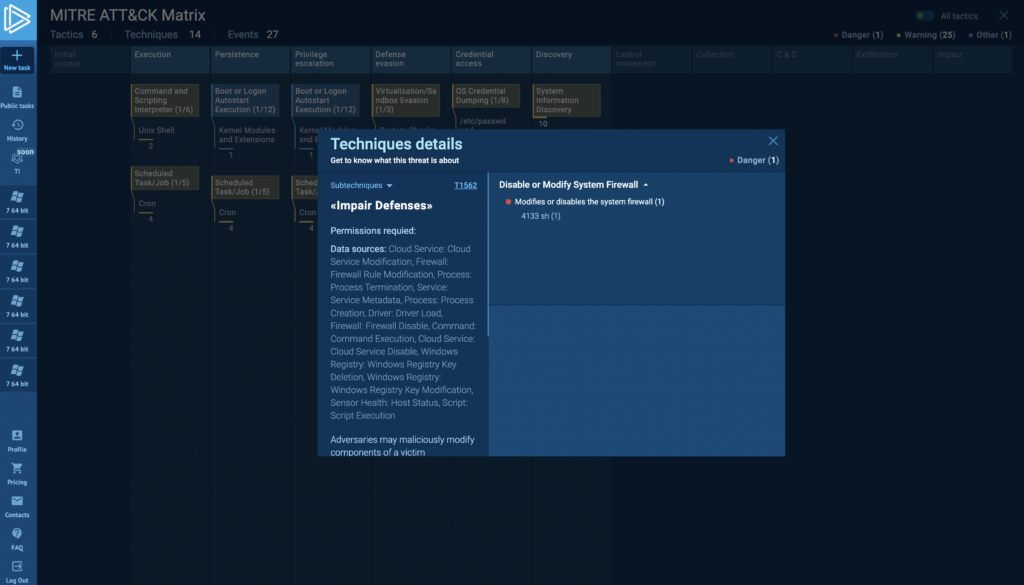
For example, ANY.RUN has a MITRE Matrix report which makes it easy to align suspicious behaviors that the sandbox recorded in a Linux task with TTPs — this is a quick way to understand the type of family or threat you are dealing with.
ANY.RUN advantages for Linux malware analysis
Linux as an operating system inherently has stronger security than Windows. This means that many malware families capable of exploiting Linux vulnerabilities are sophisticated, which makes them difficult to detect.
Not all security specialists are reverse engineers capable of quickly identifying functionality and extracting necessary IOCs of sophisticated Linux malware. ANY.RUN addresses this by providing information from the analysis in real-time. Analysts immediately understand the results, allowing them to proceed efficiently without context switching.
Using the ANY.RUN Linux environment also reduces company expenses with a cost-effective solution, eliminating the need for custom infrastructure. Our Linux VMs are already set up and configured to collect IOCs, saving our users weeks of DevOps time of set-up infrastructure.
ANY.RUN can be used independently as a self-sufficient research platform, or in combination with SIEM/SOAR.
About ANY.RUN
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis of Windows and Linux tasks.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.







0 comments