Malware analysis is complex.
The tools we use rely on an array of detection methods — heuristic analysis, behavior-based detection, signature matching, machine learning algorithms, and more. ANY.RUN already uses all of these methods, and each helps us deliver in-depth data about a program’s intent. But ultimately, it is up to the analyst to decide whether a sample is malicious or benign.
Today, we’re excited to introduce a new AI-driven detection method to ANY.RUN. Powered by OpenAI’s ChatGPT, our new feature will give you another approach to judge if a file is malicious, helping you to save time, optimize resources, and focus on key areas of your work.
ChatGPT helps you judge if a file is harmful or not
Over 300,000 users already rely on ANY.RUN to detect and analyze malicious files. So, what does AI-driven detection bring to your malware analysis workflow?
Here’s what you can expect when using the new AI-detection in ANY.RUN:
- Expanded data: all our tasks now include a ChatGPT sandbox-analysis section, which starts with a verdict — is the sample malicious, suspicious, or benign? For maximum clarity, the section will include a detailed explanation of how the conclusion was made, what makes the code malicious, and how indicators were used.
- Detailed AI-driven analysis of processes, connections, and rules: beyond the global task overview, you can focus on specific elements. Mark the processes, rules, or other elements you’re interested in, and we’ll generate a separate report just about these objects.
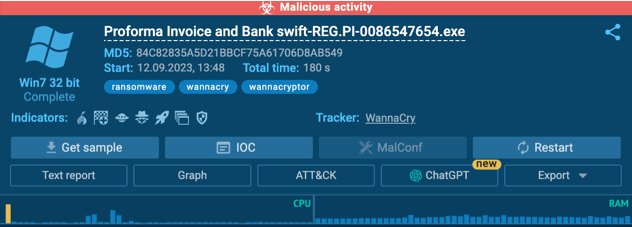
How to you use new ChatGPT malware analysis feature
An AI-driven review will appear in all reports automatically. But beyond that, you’ll find the ChatGPT icon next to important elements, such as processes, rules, and connections. Click on it, and we will include a separate AI-generated explanation about that element. We use our own prompts, so all the answers follow the same structure — this way, they’re easy to read and understand across samples.
These queries are securely saved, ensuring that you can easily refer to past inquiries for future reference. Being able to access this information aids in streamlining your search process and promotes a more efficient use of time. By utilizing this feature, you can avoid having to recreate searches that have already been conducted, saving you both time and effort. You can choose which elements to analyze with the sandbox GPT analysis feature.
In scenarios with many processes or events, ANY.RUN AI prioritizes those with the highest score or those considered suspicious, helping you focus your attention where needed most. But you can also tell it what you want to analyze:
- Process trees: AI will assess the process tree of your system as a whole or individual processes you select, pinpoint suspicious activities, and provide you with a summary.
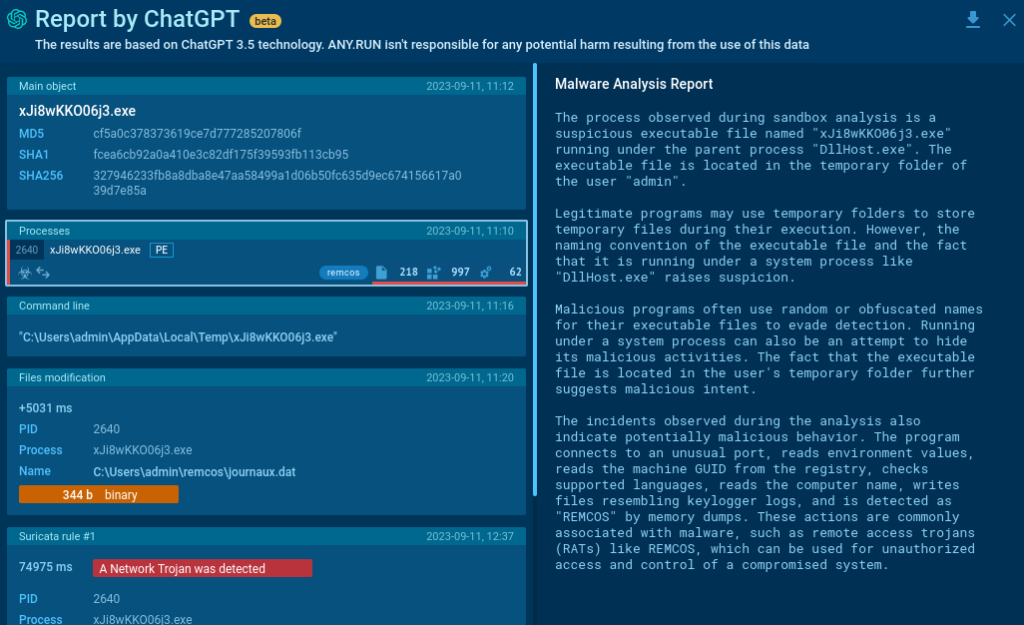
- Command Line: It will scan the command line data, generating a report highlighting potential malicious activity indicators.
- Suricata rule triggers: AI evaluates triggered Suricata rules, offering a concise explanation of what this could mean for your security.
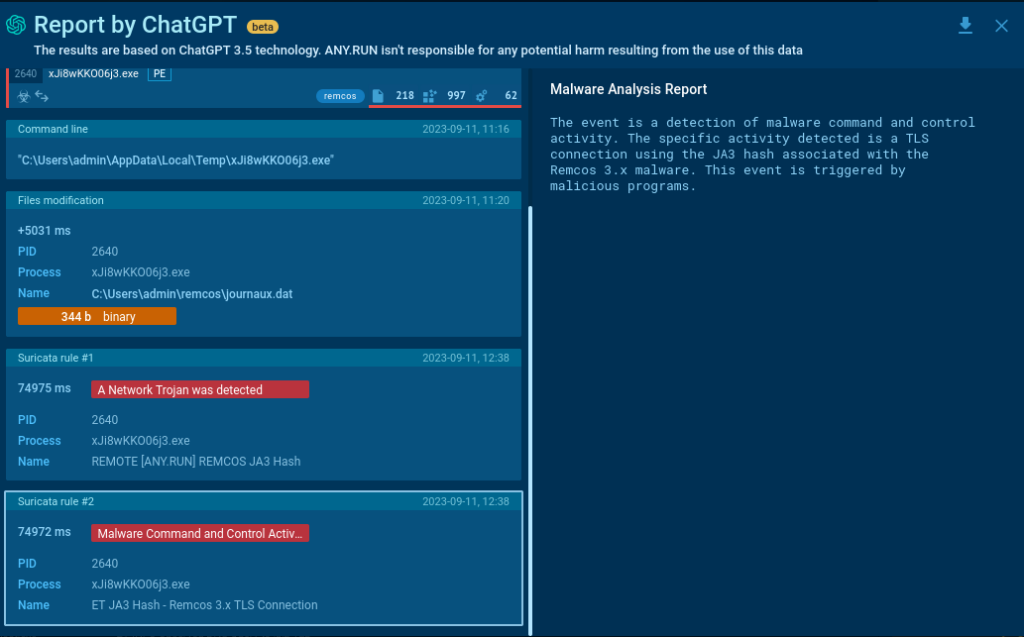
- HTTP connections: AI reviews HTTP connection data, providing a detailed summary outlining potential threats.
- Registry: Identify unusual changes or activities in the registry and spot potentially harmful actions with AI.
- Mutex: Apply Chat GPT malware analysis to examine the Mutex objects in your system and detect usage pattern anomalies.
Our new AI tool augments the other detection methods used in the sandbox to give you a new perspective of the file you’re working with.
The more analysis methods we have, the clearer the verdict
When using a sandbox ChatGPT can offer a way to break down complex data and concepts, providing clear, actionable summaries that not only identify threats but help you understand them. All so you can save time, optimize resources, and focus on key areas of your work — such as incident investigation, research, or threat response. We plan to update ChatGPTpowered sandbox capabilities in the coming months.
Get started with ANY.RUN today →
4 comments






IYH hello can you use this any dot run ChatGPT capabilities to analyze:
Configuration Files – ChatGPT could examine configuration files for servers, applications, networks etc. to flag any suspicious or abnormal settings.
Log Files – It could rapidly scan lengthy log files to highlight events of interest like errors, warnings or potential attacks for further investigation.
Memory Dumps – By querying specific processes, modules, artifacts in a memory dump, ChatGPT may detect signs of compromise missed by other tools.
Document Files – For documents like Word, PDF etc. it could potentially detect anomalies in metadata, hidden content or unusual file behaviors.
Compressed Files – ChatGPT could provide insight into the structure and likely contents of zip, rar, tar files without fully extracting them.
Source Code – It may be helpful for auditing codebases to check for vulnerabilities, weaknesses, poor practices or odd functionality.
Disk Images – When analyzing disk/partition images, ChatGPT could expedite the search for indicators across large amounts of unstructured data.
Hello! The integration of ChatGPT with ANY.RUN is designed to serve as a tool to improve your understanding of sandbox analyses, including those of documents and compressed files. Its main purpose is to offer additional insights into various elements such as processes, command lines, Suricata rule triggers, HTTP connections, registry, Mutex objects, etc.
this is great! i always wanted to see some chatgpt-related stuff used in malware analysis
Thank you! Check out chatgpt use cases, hope they’ll come in handy: https://any.run/cybersecurity-blog/chatgpt-for-analysts/