This is ANY.RUN’s monthly update, where we keep you posted on our progress.
In September, we introduced multiple new features aimed at improving the identification of suspicious objects. ANY.RUN now can leverage AI for enhanced detection, fortifying the capabilities of our sandbox. Additionally, our analysts have expanded the threat coverage by implementing new rules and extractors.
Product updates
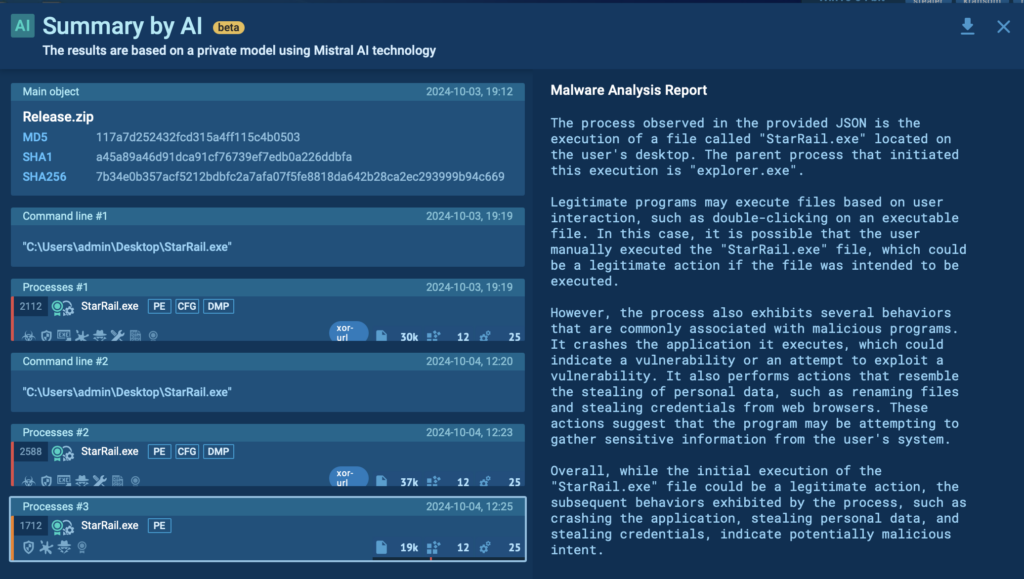
AI summaries: This major update lets you generate focused reports using AI. These reports can cover the entire task or zoom in on specific indicators like processes, command-line activities, or even triggered detection rules. This tool complements your existing behavioral and heuristic analysis methods. Learn more.
Team-based API usage quotas: Now, API quotas are set at the team level, not per team member. This lets any team member use the available quotas, making it easier for managers to monitor when you’re nearing the limit.
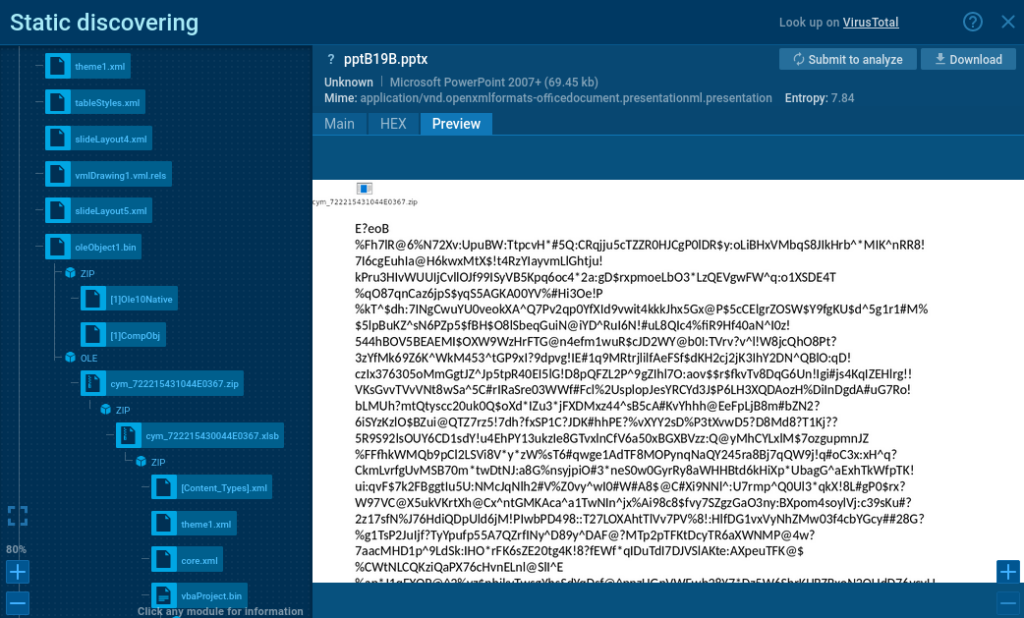
Modular Static Discovering: We’ve redesigned the architecture of the Static Discovery pop-up window to make it modular. This allows for rapid deployment of data extractors tailored to specific file types. The feature intelligently identifies which modules can best extract data, even from deeply nested structures. Initial modules available at launch are MSG/Email, Office, OneNote, PDF, LNK, and ZIP.
Default browser selection for .html file analysis: When you upload .html files into the sandbox, you can now specify which default browser should open them. This flexibility allows for more accurate testing environments that mimic real-world user behavior. It helps you identify browser-specific vulnerabilities or exploits, thus improving the quality and scope of your analysis.
Want to leverage the power of interactive analysis in the cloud?
New malware config extractors and fixes
In September, we’ve implemented detection capabilities and config extractors for new stealers and RATs:
Agniane
Agniane Stealer swipes credentials, system info, and session details from browsers, tokens, and file transfer tools, with a focus on cryptocurrency wallets. The stolen data is then shipped to C&C servers for further exploitation. Tied to the Malware-as-a-Service platform Cinoshi Project, it’s sold on various dark web forums. The operators use packers to regularly update its capabilities and evasion tactics.
Bandook
Bandook is a commercial remote access trojan (RAT) with stealer features, coded in Delphi and C++. Closed-sourced before, its variants got leaked and are now publicly downloadable, which could make it a prominent threat in the coming months.
DarkGate
DarkGate malware uses a custom base64 dictionary for string encryption, followed by a unique cipher. Beyond its stealer functions, this versatile threat may also function as a loader and keylogger.
MarsStealer
MarsStealer targets browser data, crypto wallets, and messenger sessions, pulling files from the victim’s machine. Part of a stealer family including Oski, Vidar, and Arkei, it shares a common codebase and is sold on forums alongside similar offerings like StealC and Racoon.
Analyze MarsStealer in ANY.RUN →
Stealc
The malware is coded in C and comes in two variations. The first encrypts C2 and strings using base64 and RC4, while the second uses a custom XTEA algorithm with stack obfuscation for C2 and XOR for string encryption. Both versions employ a grabber to snatch credentials from platforms like Telegram, Steam, and Chrome.
More YARA Rules
In addition, we’ve added new YARA rules (without extractors) for the following malware families:
New Network and Suricata Rules
We wrote 305 new Suricata rules, with particular attention to the Lazarus and TAG74 groups.
We’ve also updated signatures for DarkCrystal, Lumma Stealer, and Rhadamanthys. Enhancements were made in detecting encrypted payloads and file-sharing services. Additionally, we improved the detection of specific malware families, including Gh0stRAT, Amadey, Grandoreiro, Echida, DBatLoader, and Mekotio.
We shared these updates with the ET (Emerging Threats) community at the following links:
Wrapping up
This month, we’ve updated our threat intelligence and introduced additional sandbox features. These updates enable more effective malware analysis, including detailed behavioral reports and object investigation.
We’ve integrated AI to assist in this process. Our team is also monitoring emerging threats to maintain the efficacy of ANY.RUN’s detection algorithms. To support broader cybersecurity efforts, we’re sharing our detection rules with the analyst community.
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.








0 comments