November was a packed month for detection coverage. We rolled out new behavioral insights, broadened our visibility across multiple threat families, and strengthened rulesets at every layer. On top of that, our analysts uncovered and documented a new phishing wave targeting Italian organizations through malicious PDF attachments, now fully mapped in a dedicated TI report.
Let’s walk through the full set of improvements we delivered this month.
Threat Intelligence Reports
In November, we published several new TI Reports covering threats that are currently targeting companies around the world. The four of them are open to everyone:
- RoningLoader, HoldingHands, Snowlight: APT-Q-27 loader chain, stealthy RAT, and Linux VShell dropper enabling cross-platform compromise of enterprise and server environments.
- PDFChampions, Efimer, BTMOB: Malvertising-based browser hijacker, Tor-hosted cryptocurrency stealer, and Android MaaS trojan abusing Accessibility to drain banking, fintech, and wallet applications.
- Monkey, Phoenix, NonEuclid: AI-generated Linux ransomware, espionage-focused backdoor, and dual-use RAT–ransomware illustrating convergence of state-aligned techniques and financially motivated crimeware.
- Valkyrie, Sfuzuan, Sorvepotel: Windows stealer MaaS, adaptable backdoor, and WhatsApp-propagating campaign weaponizing social trust and messaging channels for large-scale infection.
We also wrote an extensive report exclusively for the TI Lookup Premium subscribers. It goes in-depth on a phishing campaign aimed specifically at Italian organizations across transportation, tourism, telecom, IT, and government sectors. The activity relies on PDF attachments disguised as official documents, each redirecting victims to counterfeit Microsoft login pages built to harvest corporate credentials.
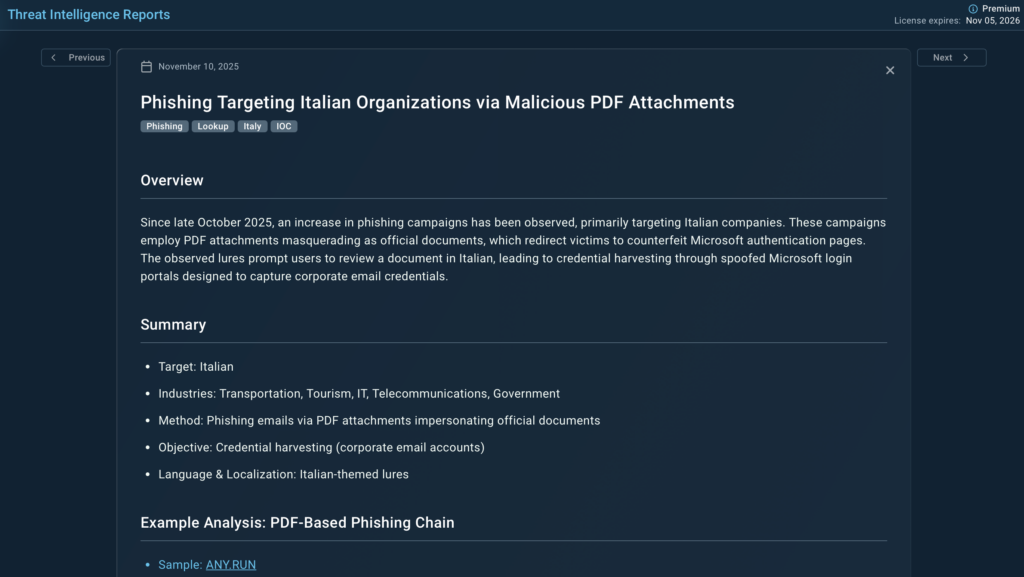
The report outlines:
- A consistent lure pattern using Italian-language prompts inviting recipients to “review” or “sign” a document
- PDF filenames following a shared template: Allegato_Ufficiale_<variable>.pdf
- Brand impersonation, including well-known Italian companies, to raise credibility
- Redirect chains leveraging both compromised domains and attacker-controlled infrastructure (e.g., phebeschool.org, mircosotfonilne.ru, vorn.revolucionww.com)
- Browser fingerprinting behavior tied to data collection on victim systems
- Email templates localized in Italian, with urgent subject lines pushing immediate action
We also included ready-to-use TI Lookup queries so analysts can surface related samples quickly, track the filename cluster, and follow the network infrastructure across recent public analysis sessions.
Behavior Signatures
In November, we expanded the malicious behavior coverage of ANY.RUN’s Interactive Sandbox with 52 new signatures across ransomware families, loaders, post-exploitation tools, and suspicious PowerShell activity. These additions help analysts surface malicious behavior earlier, reduce repeated checks, and speed up root-cause discovery.
Here are the latest signatures added:
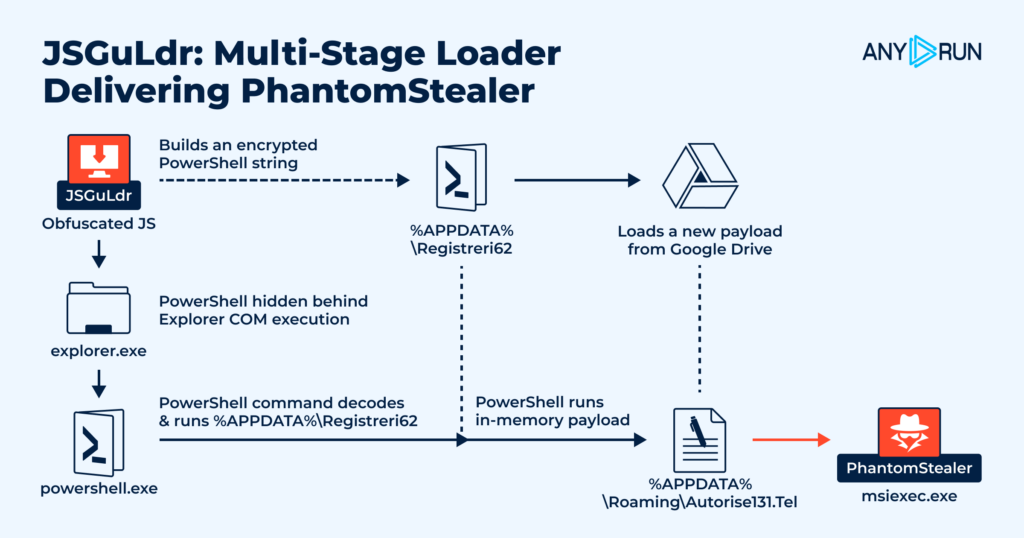
YARA Rules
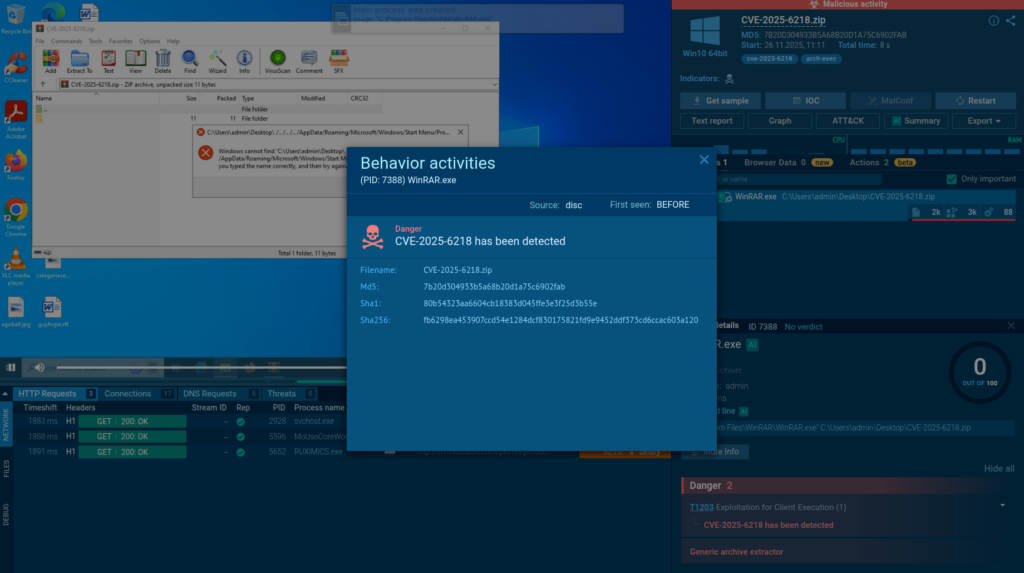
We added 9 YARA rules in November to improve early detection of ransomware, RAT families, and network-proxy tooling. These rules help analysts flag suspicious samples even before execution, making triage faster and more reliable.
Suricata Rules
In November, we added 2,184 new Suricata rules, strengthening network-level detection for RAT traffic, stealer activity, and modern phishing techniques. These additions expand coverage for TLS fingerprinting and browser-based deception tactics.
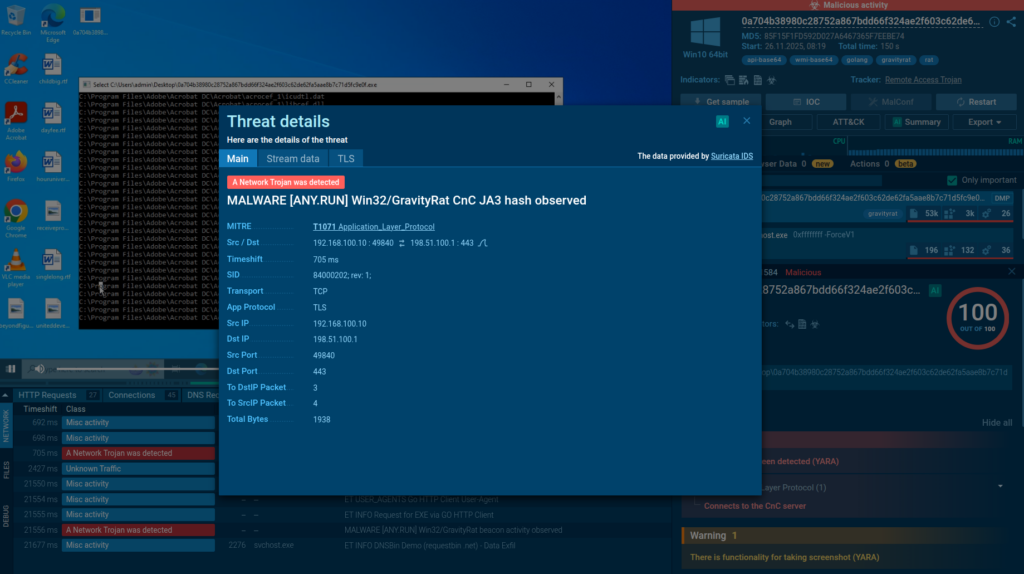
- GravityRAT JA3 (sid:84000202): Identifies GravityRAT network activity by previously unlisted JA3 TLS fingerprint.
- SalatStealer JA3 (sid:84000205): Identifies SalatStealer network activity by previously unlisted JA3 TLS fingerprint.
- Browser-in-the-Browser phishing attack (sid:85005418): Detects a phishing technique that simulates new browser window with legitimate domain within the actual browser window.
About ANY.RUN
ANY.RUN, a leading provider of interactive malware analysis and threat intelligence solutions, is used by more than 500,000 analysts across 15,000 organizations worldwide. The service helps teams investigate threats in real time, follow full execution chains, and surface critical behavior within seconds.
Analysts can detonate samples, interact with them as they run, and immediately pivot into network traces, file system changes, registry activity, and memory artifacts. With continuously updated detection coverage, including new behavioralsignatures, YARA rules, Suricata rules, and TI insights, teams get faster answers and clearer visibility with less manual effort.
Whether you’re running day-to-day investigations, handling escalations, or tracking emerging campaigns, ANY.RUN gives SOC teams, DFIR analysts, MSSPs, and researchers a practical way to reduce uncertainty and make decisions with confidence.







0 comments