Editor’s note: The current article was originally published on May 13, 2021, and updated on January 26, 2024.
Today we face a growing number of cyberattacks. Analysts can use the intrusion detection system to identify, minimize, and stop threats. In this post, we cover one of the industry’s leading IDS, along with a use case, so you can have a full picture of how ANY.RUN identifies malware.
Intrusion Detection System
IDS is security software that checks the network for suspicious behavior. If something unusual happens, it sends a warning message about it. Moreover, the system allows being aware of possible malicious activities.
Two popular types of IDS:
- NIDS – Network Intrusion Detection System
It includes the analysis of traffic, both in and out of the network. The system monitors if there are any malicious activities. NIDS’s goal is to detect and alert about it.
2. HIDS – Host Intrusion Detection System
It monitors any differences in the file set in the system. If there are any changes, it gives an alert message.
We should also mention the subsets of IDS:
- Signature-based
This system tries to find instances of familiar threats. Once a verdict of a file is set, then goes the analysis of special characteristics and as a result, appears a signature that belongs to that very attack. These types of systems compare the pattern with an existing database of signatures. This is how the type of threat is detected. Please note that constant updates and expansion of the library are necessary.
- Anomaly-based
This subset monitors the network’s traffic for any suspicious behavior. First of all, it creates a normal model of the system’s activity. Then it compares it with other existing models to find anomalies. That’s the way to identify attacks for this type.

Suricata IDS
Now that we know what IDS stands for, let’s talk about ANY.RUN‘s choice of the system. The platform uses the Suricata ruleset from different providers such as Proofpoint (Emerging Threats).
Suricata is NIDS based on the signature and anomaly approaches. It utilizes externally developed rule sets to monitor network traffic in real-time and provides alerts to the system administrator when suspicious events occur. It helps to reveal the known threats, policy violations, and malicious behavior faster by using patterns. One of Suricata’s benefits is that it acquires smart and elaborate processing architecture.
A signature consists of the following:
- Action
- Header
- Rule-options
The IDS collects data at the application layer. Suricata is able to monitor protocol activity at high levels: SMB, FTP, and HTTP and low levels: UDP, TLS, TCP, and ICMP. Furthermore, with this IDS analysts can extract files and investigate them by themselves.
Determining the type of threat or a malware family using the Suricata rules much simplifies and speeds up the workflow of a cybersecurity professional during file analysis. Signatures from the Open Sandbox’s rulesets are available for the Community plan’s users. And with a Hunter subscription, you get access to more accurate and fresh Pro sets.
Suricata use case
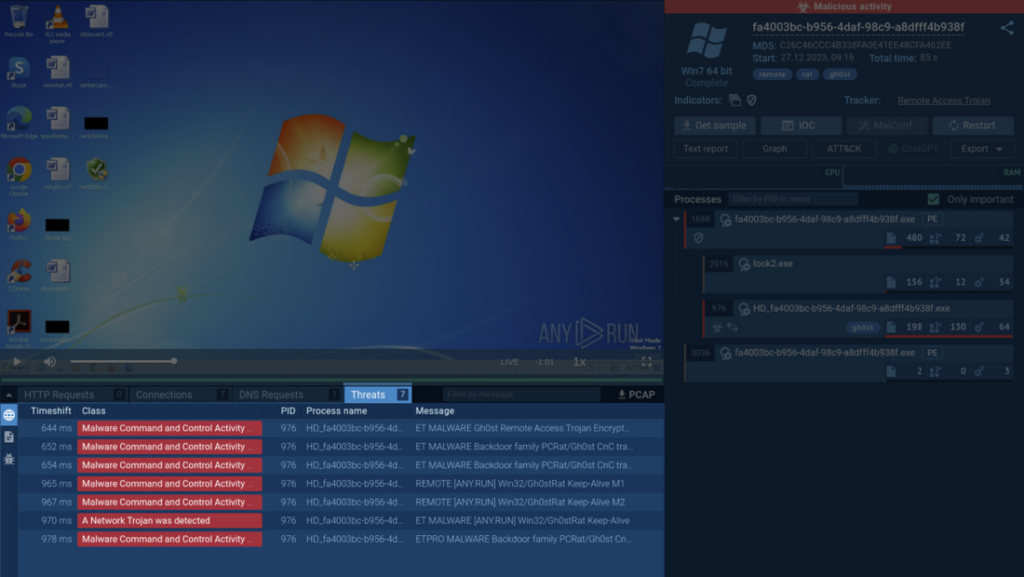
In ANY.RUN, the Threats section lists all instances of malicious network activity detected by Suricata rules. Let’s have a look at an example.
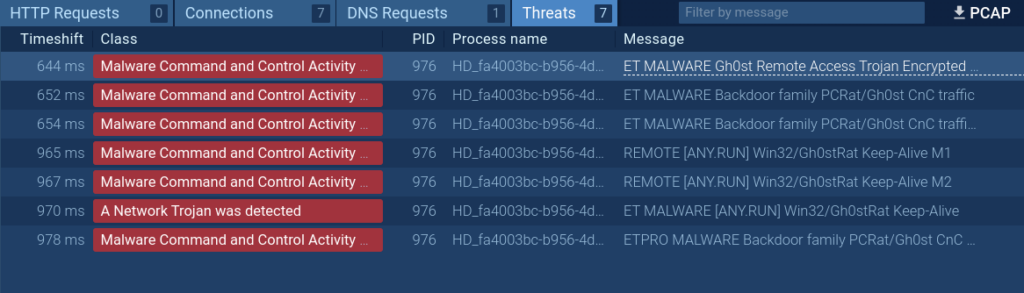
This analyzed sample establishes a connection, immediately triggering a Suricata rule that confirms the presence of the Gh0st malware engaging in encrypted communication with its command-and-control server. By clicking on the corresponding threat on the list, you’ll get to see more information on it.
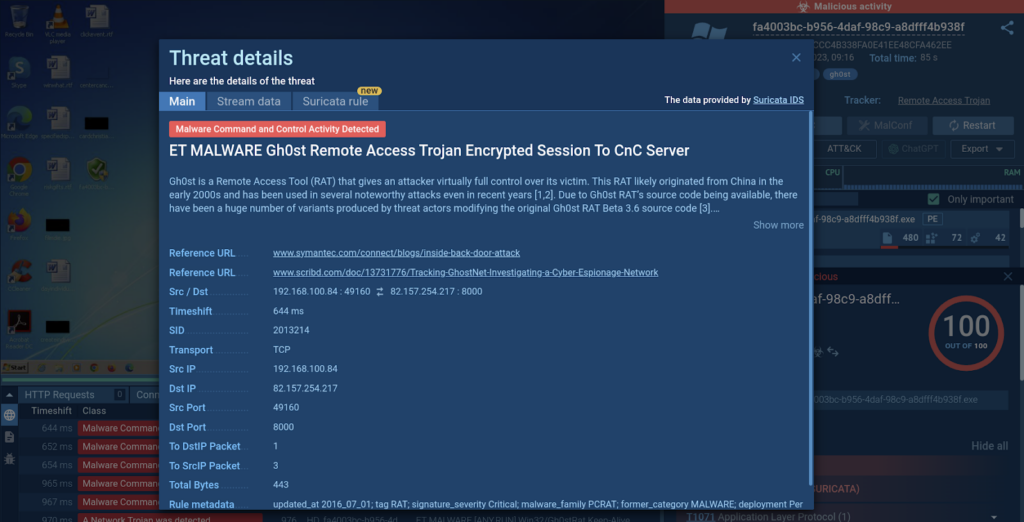
The Threat details window provides an overview of the malware detected and features links to external sources where you can learn more about the malware and its behavior. Here, you can also find information on the source and destination IP addresses, ports, and the transport protocol.

Learn to analyze cyber threats
See a detailed guide to using ANY.RUN’s Interactive Sandbox for malware and phishing analysis
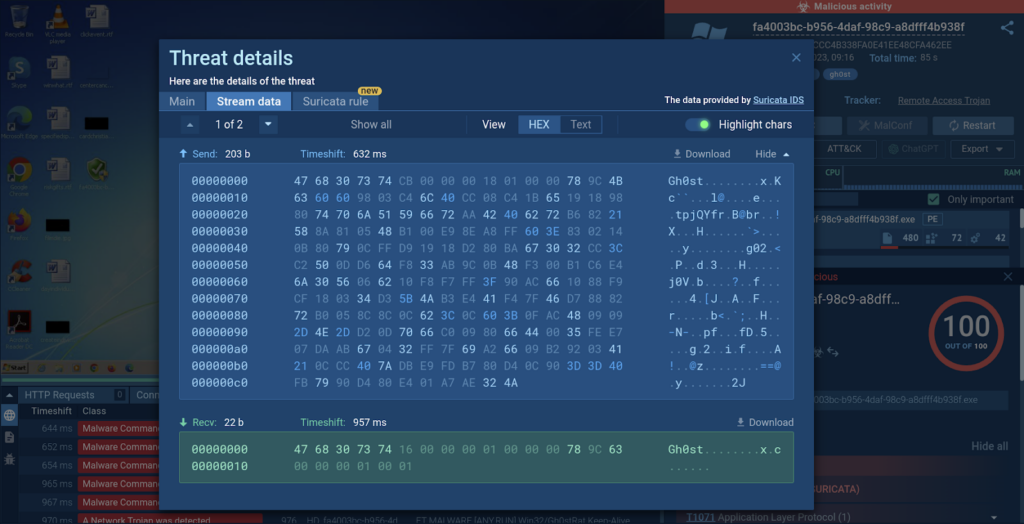
By switching to the Stream data tab, you’ll be able to inspect the captured packets.
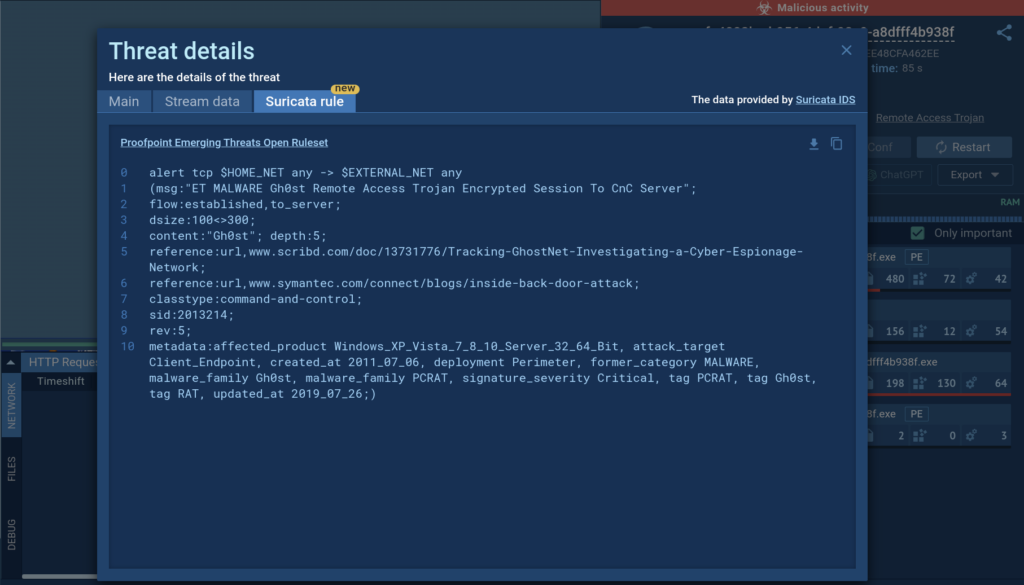
Hunter and Enterprise plan subscribers have exclusive access to the Suricata rule tab that contains the signature details used for threat identification. This enables users to observe how ET Open rulesets correlate with network activities.
Conclusion
IDS software offers real-time threat detection and network packet analysis to identify hosts and devices. Suricata, a popular IDS tool, is effectively integrated with ANY.RUN for rapid malware identification.
Try all features of ANY.RUN by requesting a 14-day free demo →








0 comments