| URL: | https://www.gomlab.com/en/gomplayer-media-player |
| Full analysis: | https://app.any.run/tasks/3fca026c-755a-4568-9369-8f0182ad6bc4 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | August 07, 2024, 18:55:04 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 0B1118BC6CB821037DDA889591AF8619 |
| SHA1: | 7B7A6625D8A3EC98C720C1AD07F0A1E677717572 |
| SHA256: | FF82E0143C561C5EE738F2973D066D45F8EAE52C59DC963CA0CCE8E879ED5915 |
| SSDEEP: | 3:N8DSLeOA+CKIVJ1bx/n:2OLeOA+Je1 |
MALICIOUS
Drops the executable file immediately after the start
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
- ofyuumpg.exe (PID: 4024)
- UnifiedStub-installer.exe (PID: 7092)
- rsEngineSvc.exe (PID: 5284)
- nsxA08B.tmp (PID: 9068)
- nsoB193.tmp (PID: 9120)
- avast_free_antivirus_setup_online_x64.exe (PID: 8656)
- AvastBrowserUpdateSetup.exe (PID: 1128)
- AvastBrowserUpdate.exe (PID: 8972)
- Instup.exe (PID: 1500)
Scans artifacts that could help determine the target
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
Actions looks like stealing of personal data
- UnifiedStub-installer.exe (PID: 7092)
- rsEngineSvc.exe (PID: 5284)
- nsxA08B.tmp (PID: 9068)
- rsVPNSvc.exe (PID: 7088)
- rsDNSSvc.exe (PID: 2032)
Changes the autorun value in the registry
- rundll32.exe (PID: 5028)
- instup.exe (PID: 9532)
- rundll32.exe (PID: 6008)
Steals credentials from Web Browsers
- nsxA08B.tmp (PID: 9068)
SUSPICIOUS
Reads security settings of Internet Explorer
- cookie_exporter.exe (PID: 7668)
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
- UnifiedStub-installer.exe (PID: 7092)
- rsWSC.exe (PID: 7912)
- rsEngineSvc.exe (PID: 5500)
- rsEDRSvc.exe (PID: 7880)
- rsEngineSvc.exe (PID: 5284)
- GOM.exe (PID: 8792)
- GrLauncher.exe (PID: 8912)
- GOM.exe (PID: 9212)
- nsxA08B.tmp (PID: 9068)
- rsVPNSvc.exe (PID: 9056)
- AvastBrowserUpdate.exe (PID: 8972)
- rsDNSSvc.exe (PID: 3832)
Executable content was dropped or overwritten
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
- ofyuumpg.exe (PID: 4024)
- UnifiedStub-installer.exe (PID: 7092)
- rsEngineSvc.exe (PID: 5284)
- nsxA08B.tmp (PID: 9068)
- avast_free_antivirus_setup_online_x64.exe (PID: 8656)
- AvastBrowserUpdateSetup.exe (PID: 1128)
- nsoB193.tmp (PID: 9120)
- AvastBrowserUpdate.exe (PID: 8972)
- Instup.exe (PID: 1500)
The process creates files with name similar to system file names
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
- UnifiedStub-installer.exe (PID: 7092)
Malware-specific behavior (creating "System.dll" in Temp)
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
Checks Windows Trust Settings
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
- UnifiedStub-installer.exe (PID: 7092)
- rsWSC.exe (PID: 7912)
- rsEngineSvc.exe (PID: 5500)
- rsEDRSvc.exe (PID: 7880)
- rsWSC.exe (PID: 8152)
- rsEDRSvc.exe (PID: 7096)
- GrLauncher.exe (PID: 8912)
- rsEngineSvc.exe (PID: 5284)
- nsxA08B.tmp (PID: 9068)
- rsVPNSvc.exe (PID: 9056)
- rsDNSSvc.exe (PID: 3832)
Searches for installed software
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
- UnifiedStub-installer.exe (PID: 7092)
- nsxA08B.tmp (PID: 9068)
- rsVPNSvc.exe (PID: 7088)
Reads Microsoft Outlook installation path
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
Reads Internet Explorer settings
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
Process requests binary or script from the Internet
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
Process drops legitimate windows executable
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
- ofyuumpg.exe (PID: 4024)
- UnifiedStub-installer.exe (PID: 7092)
- rsEngineSvc.exe (PID: 5284)
Creates/Modifies COM task schedule object
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
- AvastBrowserUpdateComRegisterShell64.exe (PID: 8780)
- AvastBrowserUpdate.exe (PID: 8884)
- AvastBrowserUpdateComRegisterShell64.exe (PID: 9180)
- AvastBrowserUpdateComRegisterShell64.exe (PID: 2472)
- AvastBrowserUpdate.exe (PID: 8972)
Creates a software uninstall entry
- UnifiedStub-installer.exe (PID: 7092)
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
Executes as Windows Service
- rsSyncSvc.exe (PID: 6168)
- rsWSC.exe (PID: 8152)
- rsClientSvc.exe (PID: 2608)
- rsEngineSvc.exe (PID: 5284)
- rsEDRSvc.exe (PID: 7096)
- WmiApSrv.exe (PID: 6164)
- rsVPNClientSvc.exe (PID: 8872)
- rsVPNSvc.exe (PID: 7088)
- AvastBrowserUpdate.exe (PID: 6156)
- WmiApSrv.exe (PID: 8768)
- rsDNSClientSvc.exe (PID: 9752)
- rsDNSResolver.exe (PID: 5400)
- rsDNSSvc.exe (PID: 2032)
- WmiApSrv.exe (PID: 5344)
Drops 7-zip archiver for unpacking
- UnifiedStub-installer.exe (PID: 7092)
Drops a system driver (possible attempt to evade defenses)
- UnifiedStub-installer.exe (PID: 7092)
The process drops C-runtime libraries
- UnifiedStub-installer.exe (PID: 7092)
Adds/modifies Windows certificates
- UnifiedStub-installer.exe (PID: 7092)
- rsWSC.exe (PID: 7912)
- rsEngineSvc.exe (PID: 5284)
Creates files in the driver directory
- UnifiedStub-installer.exe (PID: 7092)
Uses RUNDLL32.EXE to load library
- UnifiedStub-installer.exe (PID: 7092)
Uses WEVTUTIL.EXE to install publishers and event logs from the manifest
- UnifiedStub-installer.exe (PID: 7092)
Creates or modifies Windows services
- UnifiedStub-installer.exe (PID: 7092)
- rundll32.exe (PID: 5028)
Dropped object may contain URLs of mainers pools
- rsEngineSvc.exe (PID: 5284)
Reads the BIOS version
- rsEDRSvc.exe (PID: 7096)
- rsEngineSvc.exe (PID: 5284)
- nsxA08B.tmp (PID: 9068)
Reads the date of Windows installation
- rsEDRSvc.exe (PID: 7096)
- rsEngineSvc.exe (PID: 5284)
- AvastBrowserUpdate.exe (PID: 8972)
Process checks is Powershell's Script Block Logging on
- rsEDRSvc.exe (PID: 7096)
The process checks if it is being run in the virtual environment
- rsEngineSvc.exe (PID: 5284)
- rsVPNSvc.exe (PID: 7088)
- rsDNSSvc.exe (PID: 2032)
Application launched itself
- rsAppUI.exe (PID: 7072)
- rsAppUI.exe (PID: 1656)
- rsAppUI.exe (PID: 4880)
Changes Internet Explorer settings (feature browser emulation)
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
Starts application with an unusual extension
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
The process verifies whether the antivirus software is installed
- nsxA08B.tmp (PID: 9068)
- AvastBrowserUpdate.exe (PID: 8960)
- AvastBrowserUpdate.exe (PID: 8884)
- AvastBrowserUpdate.exe (PID: 8972)
- AvastBrowserUpdateComRegisterShell64.exe (PID: 8780)
- AvastBrowserUpdateComRegisterShell64.exe (PID: 9180)
- rsEngineSvc.exe (PID: 5284)
- AvastBrowserUpdateComRegisterShell64.exe (PID: 2472)
- AvastBrowserUpdate.exe (PID: 8864)
- AvastBrowserUpdate.exe (PID: 6156)
- AvastBrowserUpdate.exe (PID: 4784)
- rsVPNSvc.exe (PID: 7088)
- instup.exe (PID: 9532)
- runonce.exe (PID: 3904)
- rsDNSSvc.exe (PID: 2032)
Checks for external IP
- nsoB193.tmp (PID: 9120)
Disables SEHOP
- AvastBrowserUpdate.exe (PID: 8972)
Starts itself from another location
- AvastBrowserUpdate.exe (PID: 8972)
- Instup.exe (PID: 1500)
Process checks presence of unattended files
- instup.exe (PID: 9532)
Potential Corporate Privacy Violation
- AvastBrowserUpdate.exe (PID: 6156)
Starts CMD.EXE for commands execution
- rsDNSSvc.exe (PID: 2032)
Process uses IPCONFIG to clear DNS cache
- cmd.exe (PID: 3784)
- cmd.exe (PID: 8712)
INFO
Application launched itself
- msedge.exe (PID: 6488)
Checks supported languages
- identity_helper.exe (PID: 7524)
- cookie_exporter.exe (PID: 7668)
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
- KillGom.exe (PID: 6220)
- ofyuumpg.exe (PID: 4024)
- UnifiedStub-installer.exe (PID: 7092)
- KillGom.exe (PID: 7716)
- rsSyncSvc.exe (PID: 6168)
- rsSyncSvc.exe (PID: 644)
- rsWSC.exe (PID: 7912)
- rsWSC.exe (PID: 8152)
- rsClientSvc.exe (PID: 7064)
- rsEngineSvc.exe (PID: 5500)
- rsClientSvc.exe (PID: 2608)
- rsEngineSvc.exe (PID: 5284)
- rsEDRSvc.exe (PID: 7880)
- rsHelper.exe (PID: 2064)
- rsEDRSvc.exe (PID: 7096)
- EPP.exe (PID: 4760)
- rsAppUI.exe (PID: 7072)
- rsAppUI.exe (PID: 6192)
- rsAppUI.exe (PID: 3068)
- rsAppUI.exe (PID: 7228)
- rsAppUI.exe (PID: 8516)
- rsLitmus.A.exe (PID: 8608)
- GOM.exe (PID: 8724)
- GOM.exe (PID: 8792)
- GrLauncher.exe (PID: 8912)
- nsxA08B.tmp (PID: 9068)
- nsoB193.tmp (PID: 9120)
- GOM.exe (PID: 9212)
- avast_free_antivirus_setup_online_x64.exe (PID: 8656)
- AvastBrowserUpdateSetup.exe (PID: 1128)
- Instup.exe (PID: 1500)
- AvastBrowserUpdate.exe (PID: 8972)
- AvastBrowserUpdate.exe (PID: 8960)
- rsVPNClientSvc.exe (PID: 8872)
- AvastBrowserUpdate.exe (PID: 8884)
- rsVPNSvc.exe (PID: 9056)
- AvastBrowserUpdateComRegisterShell64.exe (PID: 8780)
- rsVPNClientSvc.exe (PID: 8912)
- AvastBrowserUpdateComRegisterShell64.exe (PID: 2472)
- AvastBrowserUpdateComRegisterShell64.exe (PID: 9180)
- AvastBrowserUpdate.exe (PID: 8864)
- AvastBrowserUpdate.exe (PID: 6156)
- rsVPNSvc.exe (PID: 7088)
- AvastBrowserUpdate.exe (PID: 4784)
- rsAppUI.exe (PID: 1656)
- VPN.exe (PID: 9180)
- rsAppUI.exe (PID: 8408)
- rsAppUI.exe (PID: 8916)
- rsAppUI.exe (PID: 8744)
- rsAppUI.exe (PID: 9452)
- instup.exe (PID: 9532)
- sbr.exe (PID: 9808)
- rsDNSClientSvc.exe (PID: 7740)
- rsDNSResolver.exe (PID: 9692)
- rsDNSClientSvc.exe (PID: 9752)
- rsDNSResolver.exe (PID: 7744)
- rsDNSResolver.exe (PID: 5400)
- rsDNSSvc.exe (PID: 3832)
- rsDNSSvc.exe (PID: 2032)
- rsAppUI.exe (PID: 4880)
- DNS.exe (PID: 10064)
- rsAppUI.exe (PID: 7904)
- rsAppUI.exe (PID: 7860)
- rsAppUI.exe (PID: 9108)
Reads Environment values
- identity_helper.exe (PID: 7524)
- cookie_exporter.exe (PID: 7668)
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
- UnifiedStub-installer.exe (PID: 7092)
- rsEngineSvc.exe (PID: 5284)
- rsEDRSvc.exe (PID: 7096)
- rsAppUI.exe (PID: 7072)
- nsxA08B.tmp (PID: 9068)
- Instup.exe (PID: 1500)
- rsVPNSvc.exe (PID: 7088)
- rsAppUI.exe (PID: 1656)
- instup.exe (PID: 9532)
- rsDNSSvc.exe (PID: 2032)
- rsAppUI.exe (PID: 4880)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6488)
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
Reads the computer name
- identity_helper.exe (PID: 7524)
- cookie_exporter.exe (PID: 7668)
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
- UnifiedStub-installer.exe (PID: 7092)
- rsSyncSvc.exe (PID: 6168)
- rsSyncSvc.exe (PID: 644)
- rsWSC.exe (PID: 7912)
- rsWSC.exe (PID: 8152)
- rsClientSvc.exe (PID: 7064)
- rsClientSvc.exe (PID: 2608)
- rsEngineSvc.exe (PID: 5500)
- rsEngineSvc.exe (PID: 5284)
- rsEDRSvc.exe (PID: 7880)
- rsEDRSvc.exe (PID: 7096)
- rsHelper.exe (PID: 2064)
- rsAppUI.exe (PID: 6192)
- rsAppUI.exe (PID: 3068)
- rsAppUI.exe (PID: 7072)
- GOM.exe (PID: 8724)
- GOM.exe (PID: 8792)
- GrLauncher.exe (PID: 8912)
- nsxA08B.tmp (PID: 9068)
- nsoB193.tmp (PID: 9120)
- GOM.exe (PID: 9212)
- avast_free_antivirus_setup_online_x64.exe (PID: 8656)
- Instup.exe (PID: 1500)
- AvastBrowserUpdate.exe (PID: 8972)
- rsVPNClientSvc.exe (PID: 8912)
- rsVPNSvc.exe (PID: 9056)
- AvastBrowserUpdate.exe (PID: 8884)
- AvastBrowserUpdate.exe (PID: 8960)
- rsVPNClientSvc.exe (PID: 8872)
- AvastBrowserUpdate.exe (PID: 4784)
- AvastBrowserUpdate.exe (PID: 8864)
- AvastBrowserUpdate.exe (PID: 6156)
- rsVPNSvc.exe (PID: 7088)
- rsAppUI.exe (PID: 1656)
- rsAppUI.exe (PID: 8408)
- rsAppUI.exe (PID: 8916)
- instup.exe (PID: 9532)
- rsDNSClientSvc.exe (PID: 9752)
- rsDNSResolver.exe (PID: 7744)
- rsDNSResolver.exe (PID: 5400)
- rsDNSClientSvc.exe (PID: 7740)
- rsDNSSvc.exe (PID: 2032)
- rsDNSSvc.exe (PID: 3832)
- rsAppUI.exe (PID: 4880)
- rsAppUI.exe (PID: 9108)
- rsAppUI.exe (PID: 7904)
Checks proxy server information
- cookie_exporter.exe (PID: 7668)
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
- UnifiedStub-installer.exe (PID: 7092)
- rsWSC.exe (PID: 7912)
- rsAppUI.exe (PID: 7072)
- GOM.exe (PID: 8792)
- GrLauncher.exe (PID: 8912)
- GOM.exe (PID: 9212)
- nsxA08B.tmp (PID: 9068)
- avast_free_antivirus_setup_online_x64.exe (PID: 8656)
- Instup.exe (PID: 1500)
- AvastBrowserUpdate.exe (PID: 4784)
- rsAppUI.exe (PID: 1656)
- instup.exe (PID: 9532)
- rsAppUI.exe (PID: 4880)
Executable content was dropped or overwritten
- msedge.exe (PID: 6488)
- msedge.exe (PID: 6720)
Drops the executable file immediately after the start
- msedge.exe (PID: 6488)
- msedge.exe (PID: 6720)
The process uses the downloaded file
- msedge.exe (PID: 7584)
- msedge.exe (PID: 6488)
Create files in a temporary directory
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
- ofyuumpg.exe (PID: 4024)
- UnifiedStub-installer.exe (PID: 7092)
- rsAppUI.exe (PID: 7072)
- GrLauncher.exe (PID: 8912)
- nsxA08B.tmp (PID: 9068)
- AvastBrowserUpdate.exe (PID: 6156)
- rsAppUI.exe (PID: 1656)
- rsAppUI.exe (PID: 4880)
Creates files or folders in the user directory
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
- UnifiedStub-installer.exe (PID: 7092)
- rsWSC.exe (PID: 7912)
- rsEngineSvc.exe (PID: 5284)
- rsAppUI.exe (PID: 7072)
- GOM.exe (PID: 8792)
- rsAppUI.exe (PID: 3068)
- GrLauncher.exe (PID: 8912)
- nsxA08B.tmp (PID: 9068)
- rsVPNSvc.exe (PID: 7088)
- rsAppUI.exe (PID: 1656)
- rsAppUI.exe (PID: 8916)
- rsAppUI.exe (PID: 4880)
- rsDNSSvc.exe (PID: 2032)
- rsAppUI.exe (PID: 9108)
Reads the software policy settings
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
- UnifiedStub-installer.exe (PID: 7092)
- rsWSC.exe (PID: 7912)
- rsEngineSvc.exe (PID: 5500)
- rsEngineSvc.exe (PID: 5284)
- rsEDRSvc.exe (PID: 7880)
- rsWSC.exe (PID: 8152)
- rsEDRSvc.exe (PID: 7096)
- GrLauncher.exe (PID: 8912)
- nsoB193.tmp (PID: 9120)
- nsxA08B.tmp (PID: 9068)
- avast_free_antivirus_setup_online_x64.exe (PID: 8656)
- Instup.exe (PID: 1500)
- rsVPNSvc.exe (PID: 9056)
- AvastBrowserUpdate.exe (PID: 4784)
- AvastBrowserUpdate.exe (PID: 6156)
- rsVPNSvc.exe (PID: 7088)
- instup.exe (PID: 9532)
- rsDNSSvc.exe (PID: 3832)
- rsDNSSvc.exe (PID: 2032)
Reads the machine GUID from the registry
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
- UnifiedStub-installer.exe (PID: 7092)
- rsWSC.exe (PID: 7912)
- rsWSC.exe (PID: 8152)
- rsEngineSvc.exe (PID: 5500)
- rsEngineSvc.exe (PID: 5284)
- rsEDRSvc.exe (PID: 7096)
- rsHelper.exe (PID: 2064)
- rsEDRSvc.exe (PID: 7880)
- rsAppUI.exe (PID: 7072)
- GOM.exe (PID: 8724)
- GOM.exe (PID: 8792)
- GrLauncher.exe (PID: 8912)
- nsoB193.tmp (PID: 9120)
- nsxA08B.tmp (PID: 9068)
- GOM.exe (PID: 9212)
- avast_free_antivirus_setup_online_x64.exe (PID: 8656)
- Instup.exe (PID: 1500)
- rsVPNSvc.exe (PID: 9056)
- AvastBrowserUpdate.exe (PID: 8972)
- rsVPNSvc.exe (PID: 7088)
- AvastBrowserUpdate.exe (PID: 6156)
- rsAppUI.exe (PID: 1656)
- instup.exe (PID: 9532)
- rsDNSSvc.exe (PID: 3832)
- rsDNSSvc.exe (PID: 2032)
- rsAppUI.exe (PID: 4880)
Disables trace logs
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
- UnifiedStub-installer.exe (PID: 7092)
- rsEngineSvc.exe (PID: 5284)
- rsEDRSvc.exe (PID: 7096)
- rsVPNSvc.exe (PID: 7088)
- rsDNSSvc.exe (PID: 2032)
Process checks Internet Explorer phishing filters
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
Creates files in the program directory
- GOMPLAYERGLOBALSETUP_CHROME.EXE (PID: 1884)
- UnifiedStub-installer.exe (PID: 7092)
- rsWSC.exe (PID: 7912)
- rsEngineSvc.exe (PID: 5500)
- rsEngineSvc.exe (PID: 5284)
- rsEDRSvc.exe (PID: 7880)
- rsEDRSvc.exe (PID: 7096)
- GrLauncher.exe (PID: 8912)
- avast_free_antivirus_setup_online_x64.exe (PID: 8656)
- AvastBrowserUpdateSetup.exe (PID: 1128)
- Instup.exe (PID: 1500)
- AvastBrowserUpdate.exe (PID: 8972)
- rsVPNSvc.exe (PID: 9056)
- AvastBrowserUpdate.exe (PID: 6156)
- rsVPNSvc.exe (PID: 7088)
- instup.exe (PID: 9532)
- rsDNSResolver.exe (PID: 5400)
- rsDNSResolver.exe (PID: 7744)
- rsDNSSvc.exe (PID: 3832)
- rsDNSSvc.exe (PID: 2032)
.NET Reactor protector has been detected
- UnifiedStub-installer.exe (PID: 7092)
- rsWSC.exe (PID: 8152)
- rsEngineSvc.exe (PID: 5284)
- rsEDRSvc.exe (PID: 7096)
- rsHelper.exe (PID: 2064)
Reads the time zone
- runonce.exe (PID: 7376)
- rsEngineSvc.exe (PID: 5284)
- rsEDRSvc.exe (PID: 7096)
- rsVPNSvc.exe (PID: 7088)
- runonce.exe (PID: 3904)
- rsDNSSvc.exe (PID: 2032)
Reads security settings of Internet Explorer
- runonce.exe (PID: 7376)
- runonce.exe (PID: 3904)
Reads product name
- rsEDRSvc.exe (PID: 7096)
- rsEngineSvc.exe (PID: 5284)
- rsAppUI.exe (PID: 7072)
- rsAppUI.exe (PID: 1656)
- rsAppUI.exe (PID: 4880)
Reads CPU info
- rsEDRSvc.exe (PID: 7096)
- rsEngineSvc.exe (PID: 5284)
- avast_free_antivirus_setup_online_x64.exe (PID: 8656)
- Instup.exe (PID: 1500)
- rsVPNSvc.exe (PID: 7088)
- instup.exe (PID: 9532)
- rsDNSSvc.exe (PID: 2032)
Process checks computer location settings
- rsAppUI.exe (PID: 7228)
- rsAppUI.exe (PID: 7072)
- rsAppUI.exe (PID: 8516)
- nsxA08B.tmp (PID: 9068)
- AvastBrowserUpdate.exe (PID: 8972)
- rsVPNSvc.exe (PID: 7088)
- rsAppUI.exe (PID: 1656)
- rsAppUI.exe (PID: 8744)
- rsAppUI.exe (PID: 9452)
- rsAppUI.exe (PID: 4880)
- rsAppUI.exe (PID: 7860)
Dropped object may contain TOR URL's
- Instup.exe (PID: 1500)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
299
Monitored processes
156
Malicious processes
25
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 644 | "C:\Program Files\ReasonLabs\Common\rsSyncSvc.exe" -i -bn:ReasonLabs -pn:EPP -lpn:rav_antivirus -url:https://update.reasonsecurity.com/v2/live -dt:10 | C:\Program Files\ReasonLabs\Common\rsSyncSvc.exe | — | UnifiedStub-installer.exe | |||||||||||
User: admin Company: Reason Software Company Inc. Integrity Level: HIGH Description: Reason Security Synchronize Service Exit code: 0 Version: 1.8.5.0 Modules
| |||||||||||||||
| 736 | ipconfig /flushdns | C:\Windows\System32\ipconfig.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: IP Configuration Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6756 --field-trial-handle=2368,i,7712857698882973906,16764532404281187830,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1044 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=7240 --field-trial-handle=2368,i,7712857698882973906,16764532404281187830,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1044 | "C:\Windows\System32\grpconv.exe" -o | C:\Windows\System32\grpconv.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | AvastBrowserUpdateSetup.exe /silent /install "bundlename=Avast Secure Browser&appguid={A8504530-742B-42BC-895D-2BAD6406F698}&appname=Avast Secure Browser&needsadmin=true&lang=en-US&brand=6226&installargs=--no-create-user-shortcuts --make-chrome-default --force-default-win10 --auto-import-data%3Dmsedge --import-cookies --auto-launch-chrome" | C:\Users\admin\AppData\Local\Temp\nsyB0E0.tmp\AvastBrowserUpdateSetup.exe | nsxA08B.tmp | ||||||||||||
User: admin Company: Gen Digital Inc. Integrity Level: HIGH Description: Avast Browser Setup Version: 1.8.1697.6 Modules
| |||||||||||||||
| 1164 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=7236 --field-trial-handle=2368,i,7712857698882973906,16764532404281187830,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1500 | "C:\WINDOWS\Temp\asw.19009d3c4cdbf67f\instup.exe" /sfx:lite /sfxstorage:C:\WINDOWS\Temp\asw.19009d3c4cdbf67f /edition:1 /prod:ais /stub_context:7cbeb3c5-6af5-4699-8f35-1d0c2ef76bb2:9931880 /guid:80155fcd-a25d-4f3a-8580-aa83e733d50c /ga_clientid:77952b77-73b7-4006-ae85-9f33c927240f /silent /cookie:mmm_gom_ppi_003_434_m /ga_clientid:77952b77-73b7-4006-ae85-9f33c927240f /edat_dir:C:\WINDOWS\Temp\asw.589414bddc6c4aa6 /geo:DE | C:\Windows\Temp\asw.19009d3c4cdbf67f\Instup.exe | avast_free_antivirus_setup_online_x64.exe | ||||||||||||
User: admin Company: Gen Digital Inc. Integrity Level: HIGH Description: Avast Antivirus Installer Version: 24.7.9311.0 Modules
| |||||||||||||||
| 1656 | "C:\Program Files\ReasonLabs\Common\Client\v1.4.2\rsAppUI.exe" "c:\program files\reasonlabs\VPN\ui\app.asar" --engine-path="c:\program files\reasonlabs\VPN" --minimized --focused --first-run | C:\Program Files\ReasonLabs\Common\Client\v1.4.2\rsAppUI.exe | — | VPN.exe | |||||||||||
User: admin Company: Reason Cybersecurity Ltd. Integrity Level: MEDIUM Description: ReasonLabs Application Version: 1.4.2 Modules
| |||||||||||||||
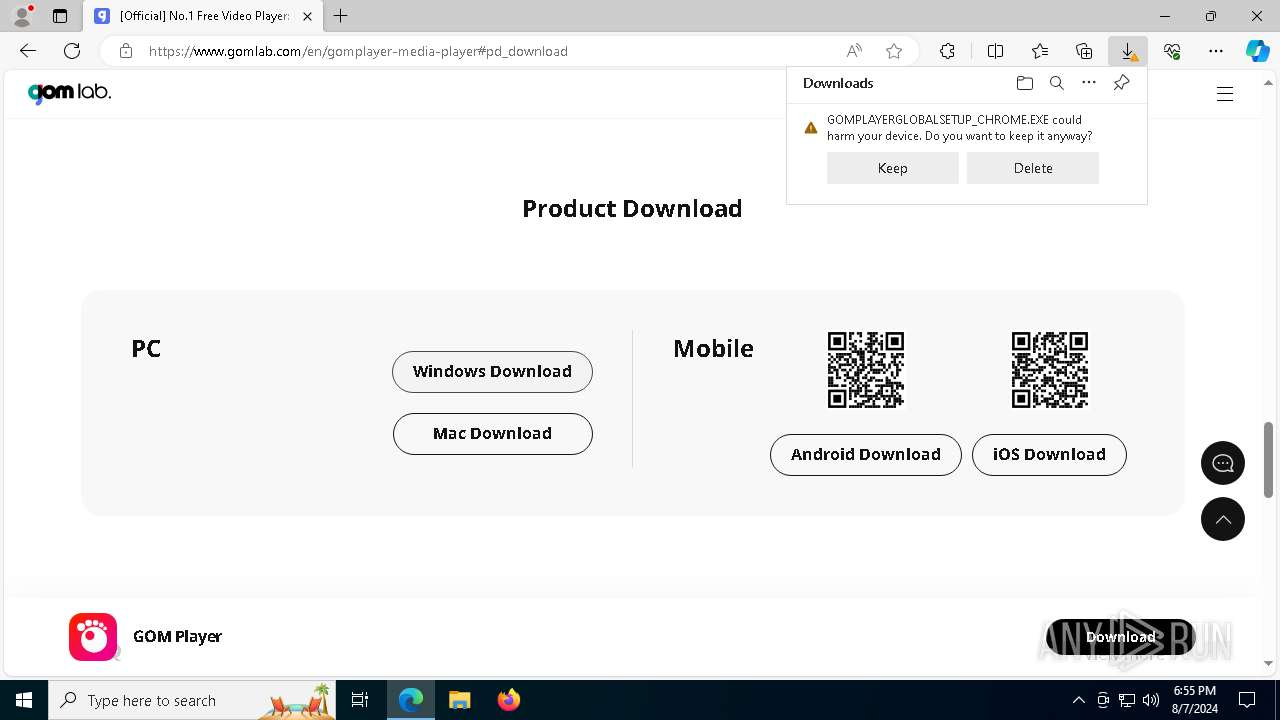
| 1884 | "C:\Users\admin\Downloads\GOMPLAYERGLOBALSETUP_CHROME.EXE" | C:\Users\admin\Downloads\GOMPLAYERGLOBALSETUP_CHROME.EXE | msedge.exe | ||||||||||||
User: admin Company: GOM & Company Integrity Level: HIGH Description: GOMPlayerGlobal Setup File Exit code: 0 Version: 2.3 Modules
| |||||||||||||||
Total events
280 777
Read events
273 414
Write events
7 074
Delete events
289
Modification events
| (PID) Process: | (6304) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkLowPart |
Value: 0 | |||
| (PID) Process: | (6304) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkHighPart |
Value: 0 | |||
| (PID) Process: | (6304) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 0 | |||
| (PID) Process: | (6304) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 0 | |||
| (PID) Process: | (6304) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (6304) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31123707 | |||
| (PID) Process: | (6304) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6304) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6304) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6304) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
Executable files
1 130
Suspicious files
695
Text files
1 862
Unknown types
60
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6488 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RFe5fa0.TMP | — | |
MD5:— | SHA256:— | |||
| 6488 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6488 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RFe5fa0.TMP | — | |
MD5:— | SHA256:— | |||
| 6488 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RFe5fa0.TMP | — | |
MD5:— | SHA256:— | |||
| 6488 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6488 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6488 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RFe5fb0.TMP | — | |
MD5:— | SHA256:— | |||
| 6488 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6488 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RFe5fcf.TMP | — | |
MD5:— | SHA256:— | |||
| 6488 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
132
TCP/UDP connections
404
DNS requests
357
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5900 | svchost.exe | HEAD | 200 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a8381623-5b08-479e-aab0-f1075e82bccf?P1=1723620898&P2=404&P3=2&P4=aiMOgy3ow95RTpFrt0xp8pPZXQHBk%2fLBehxmkO0lNN032eC6LtGIyTXADajBVs7b269CEfLicxVWFaVR2OWAwg%3d%3d | unknown | — | — | whitelisted |
1884 | GOMPLAYERGLOBALSETUP_CHROME.EXE | GET | 200 | 18.66.112.55:80 | http://playinfo.gomlab.com/setup_v2/index.gom?setup=player&name=GOMPLAYERGLOBALSETUP_CHROME&bit=32&lang=esp&version=2.3.99.5369&checkdate=202407311637 | unknown | — | — | whitelisted |
5976 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5500 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5900 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a8381623-5b08-479e-aab0-f1075e82bccf?P1=1723620898&P2=404&P3=2&P4=aiMOgy3ow95RTpFrt0xp8pPZXQHBk%2fLBehxmkO0lNN032eC6LtGIyTXADajBVs7b269CEfLicxVWFaVR2OWAwg%3d%3d | unknown | — | — | whitelisted |
7248 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5900 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a8381623-5b08-479e-aab0-f1075e82bccf?P1=1723620898&P2=404&P3=2&P4=aiMOgy3ow95RTpFrt0xp8pPZXQHBk%2fLBehxmkO0lNN032eC6LtGIyTXADajBVs7b269CEfLicxVWFaVR2OWAwg%3d%3d | unknown | — | — | whitelisted |
1884 | GOMPLAYERGLOBALSETUP_CHROME.EXE | GET | 200 | 104.18.21.226:80 | http://ocsp2.globalsign.com/rootr3/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCDQHuXyId%2FGI71DM6hVc%3D | unknown | — | — | whitelisted |
1884 | GOMPLAYERGLOBALSETUP_CHROME.EXE | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/gsrsaovsslca2018/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBRrcGT%2BanRD3C1tW3nsrKeuXC7DPwQU%2BO9%2F8s14Z6jeb48kjYjxhwMCs%2BsCDGBgMk5H71UZNVzK2Q%3D%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1120 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1884 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6720 | msedge.exe | 52.123.242.232:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | CH | unknown |
6488 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6720 | msedge.exe | 52.85.65.73:443 | www.gomlab.com | AMAZON-02 | US | unknown |
6720 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6720 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.gomlab.com |
| unknown |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
www.bing.com |
| whitelisted |
wsa.mig-log.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1884 | GOMPLAYERGLOBALSETUP_CHROME.EXE | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2256 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
9120 | nsoB193.tmp | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
6156 | AvastBrowserUpdate.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
Process | Message |
|---|---|
rsEngineSvc.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\ReasonLabs\EPP\x64\SQLite.Interop.dll"...
|
rsEDRSvc.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\ReasonLabs\EDR\x64\SQLite.Interop.dll"...
|
nsxA08B.tmp | 2024-08-07T18:58:50 [libnsis] {0000236c:00002370} <2:Info> (893f00f663353e48\src\jsis-plugins\plugins\Plugin.cpp:82) JSIS Plugin logging enabled
|
nsxA08B.tmp | 2024-08-07T18:58:50 [libnsis] {0000236c:00002370} <1:Debug> (91aa05bf654a77ad\src\sbplugins\windows\RCData.cpp:62) Throwing exception 0x00000400000715
|
nsxA08B.tmp | 2024-08-07T18:58:50 [libnsis] {0000236c:00002370} <4:Error> (893f00f663353e48\src\jsis-plugins\plugins\UtilitiesPlugin\TagData.cpp:85) 0x00000400000715 91aa05bf654a77ad\src\sbplugins\windows\RCData.cpp:62
|
nsxA08B.tmp | 2024-08-07T18:58:51 [libnsis] {0000236c:00002370} <1:Debug> (6641f181bd7f7928\src\acu\database\Sqlite.cpp:38) Oepn Sqlite DB C:\Users\admin\AppData\Local\Temp\nsyB0E0.tmp\CR.History.tmp
|
nsxA08B.tmp | 2024-08-07T18:58:51 [libnsis] {0000236c:00002370} <1:Debug> (6641f181bd7f7928\src\acu\database\Sqlite.cpp:75) Execute Sqlite query SELECT ((visits.visit_time/1000000)-11644473600) /60 /60 / 24 AS vtime FROM 'visits' WHERE vtime >= 19912 AND vtime <= 19943 GROUP BY vtime
|
nsxA08B.tmp | 2024-08-07T18:58:51 [libnsis] {0000236c:00002370} <1:Debug> (6641f181bd7f7928\src\acu\database\Sqlite.cpp:38) Oepn Sqlite DB C:\Users\admin\AppData\Local\Temp\nsyB0E0.tmp\CR.History.tmp
|
nsxA08B.tmp | 2024-08-07T18:58:51 [libnsis] {0000236c:00002370} <1:Debug> (6641f181bd7f7928\src\acu\database\Sqlite.cpp:75) Execute Sqlite query SELECT ((visits.visit_time/1000000)-11644473600) /60 /60 / 24 AS vtime FROM 'visits' WHERE vtime >= 19912 AND vtime <= 19943 GROUP BY vtime
|
nsxA08B.tmp | 2024-08-07T18:58:51 [libnsis] {0000236c:00002370} <1:Debug> (6641f181bd7f7928\src\acu\database\Sqlite.cpp:38) Oepn Sqlite DB C:\Users\admin\AppData\Local\Temp\nsyB0E0.tmp\FF.places.tmp
|