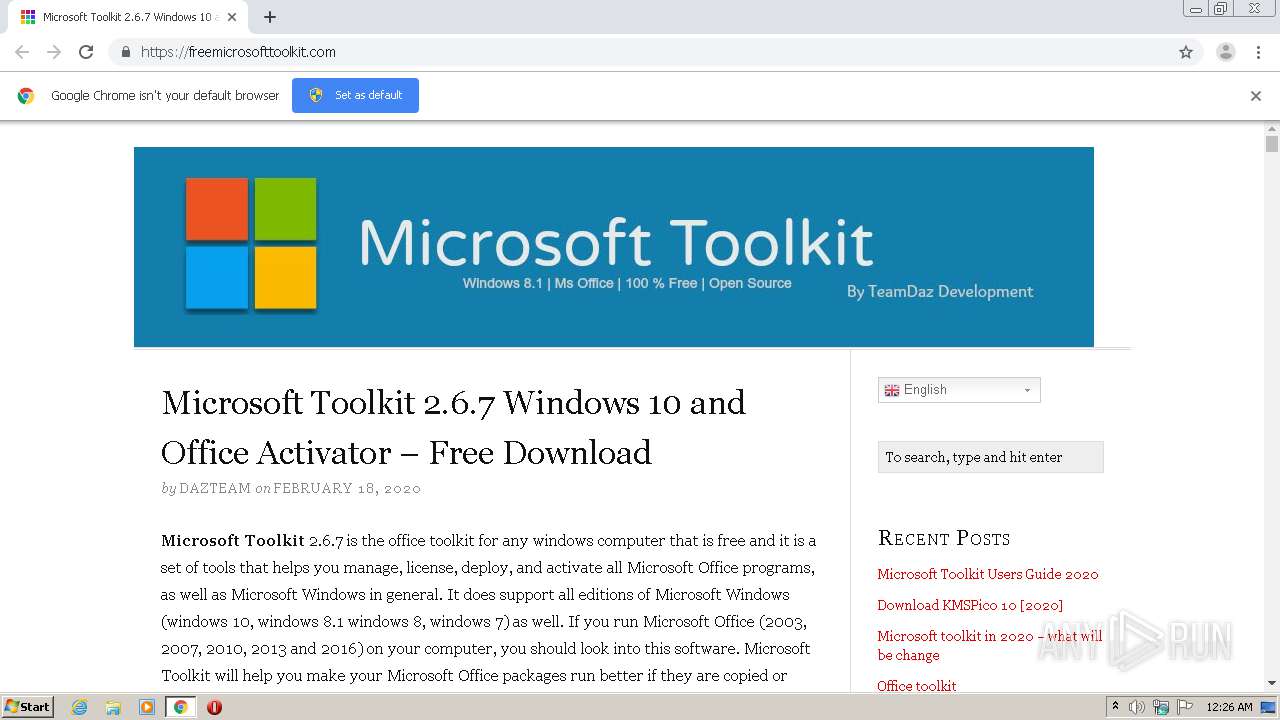
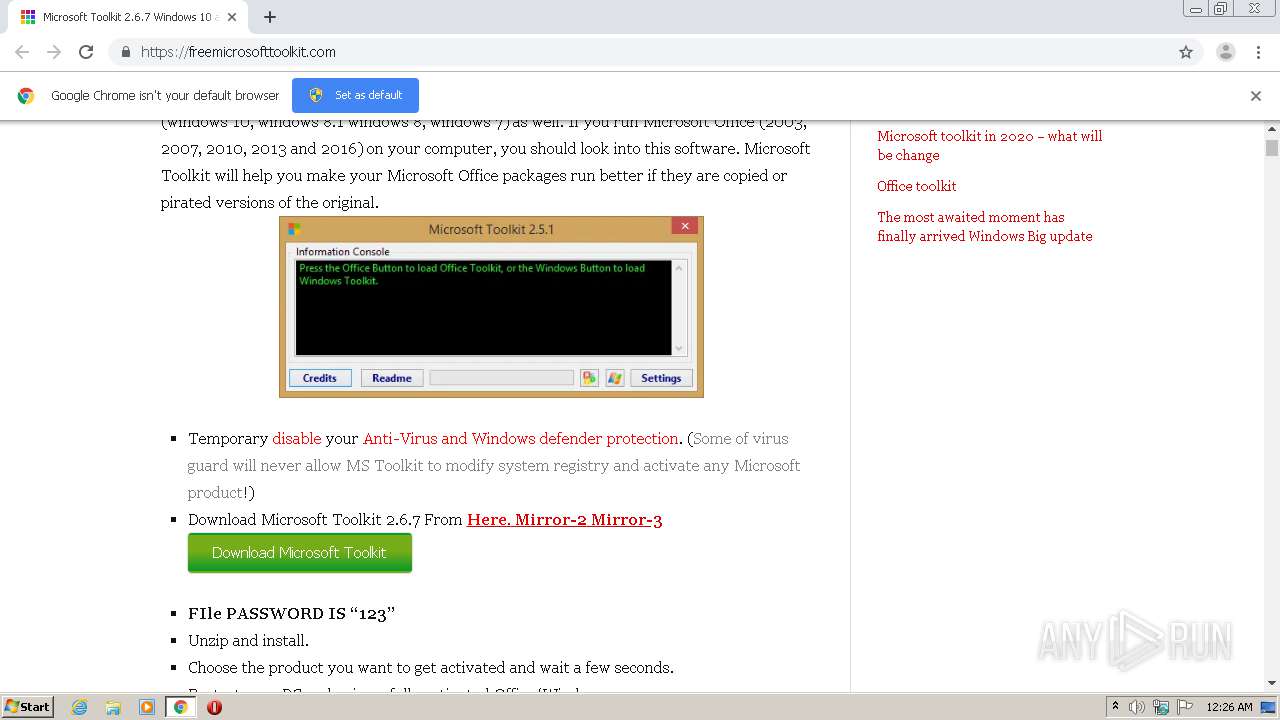
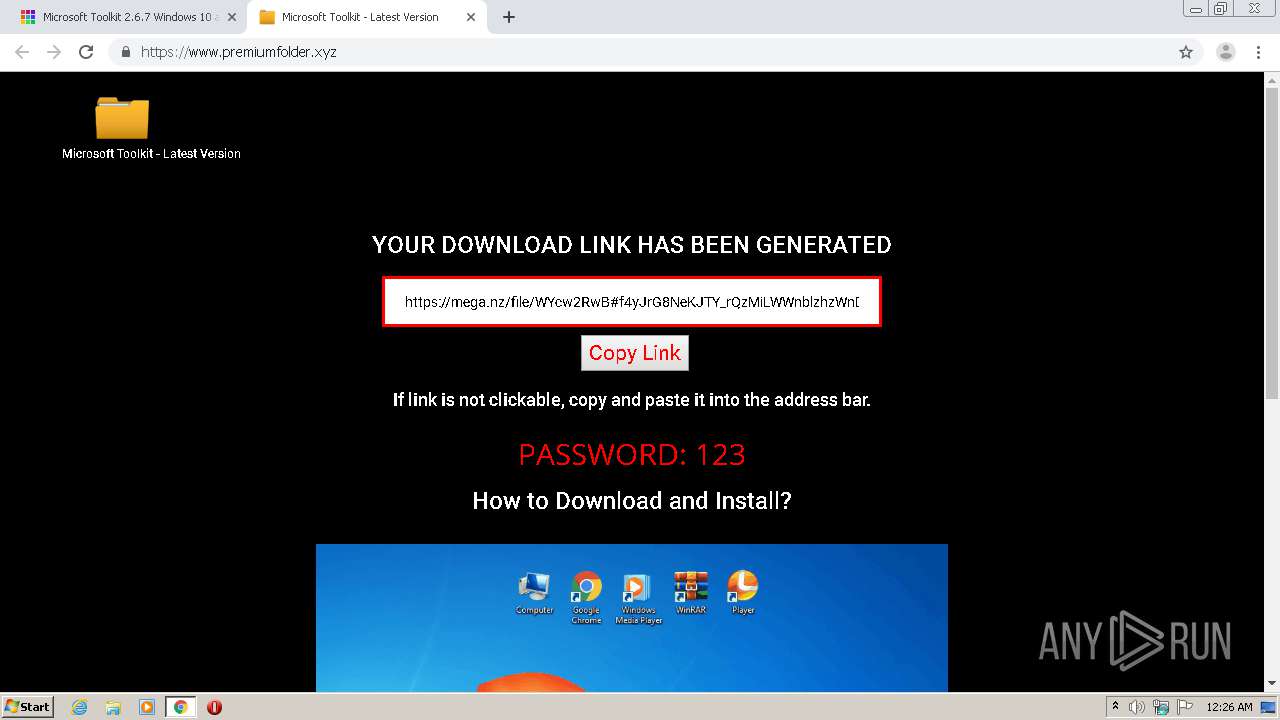
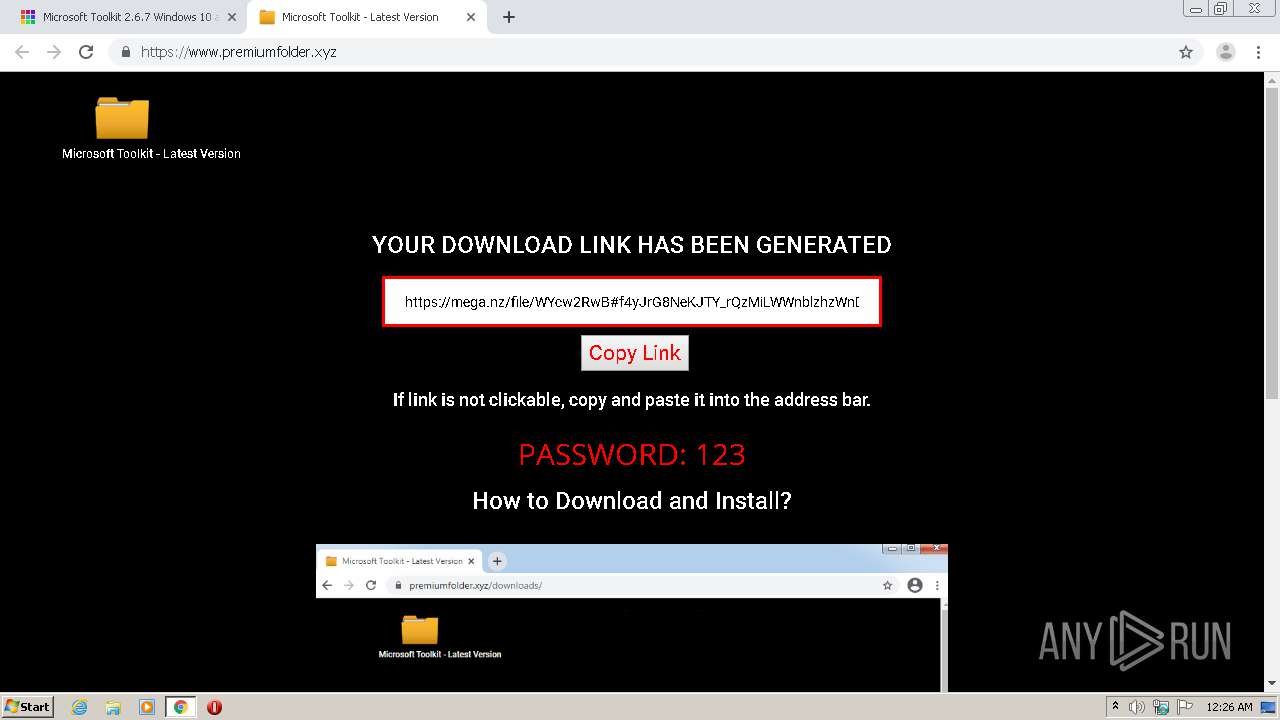
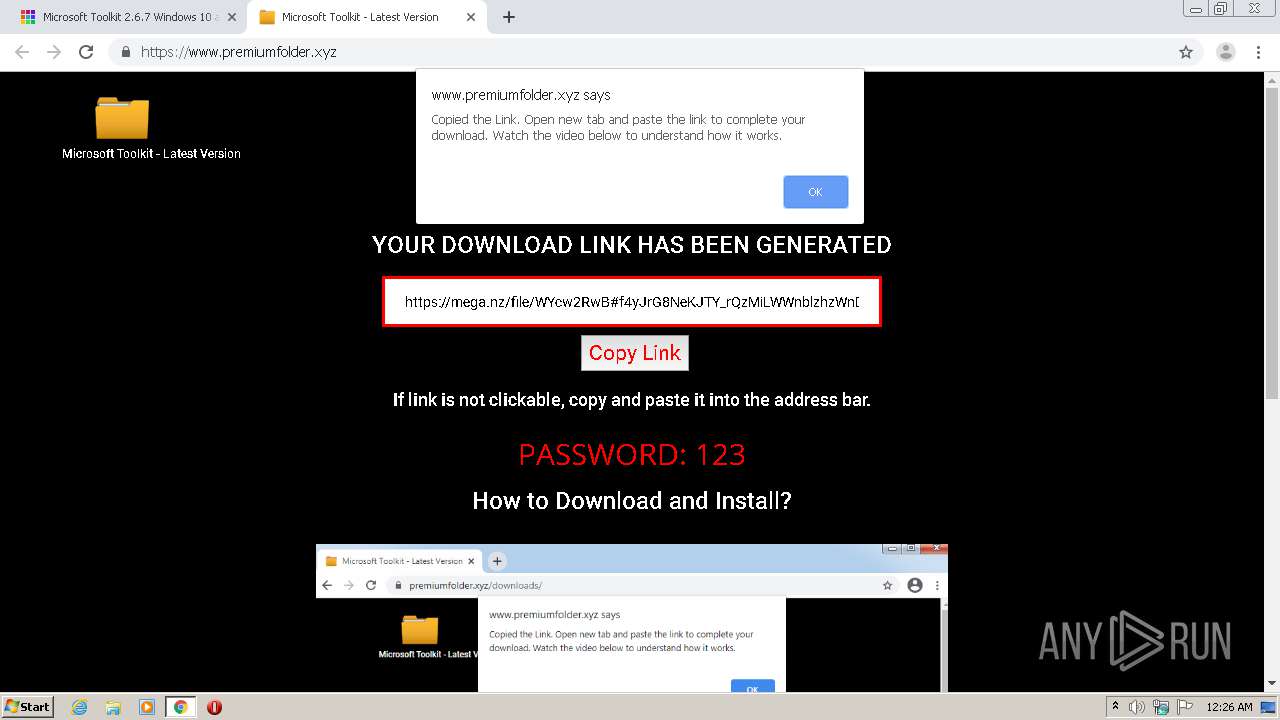
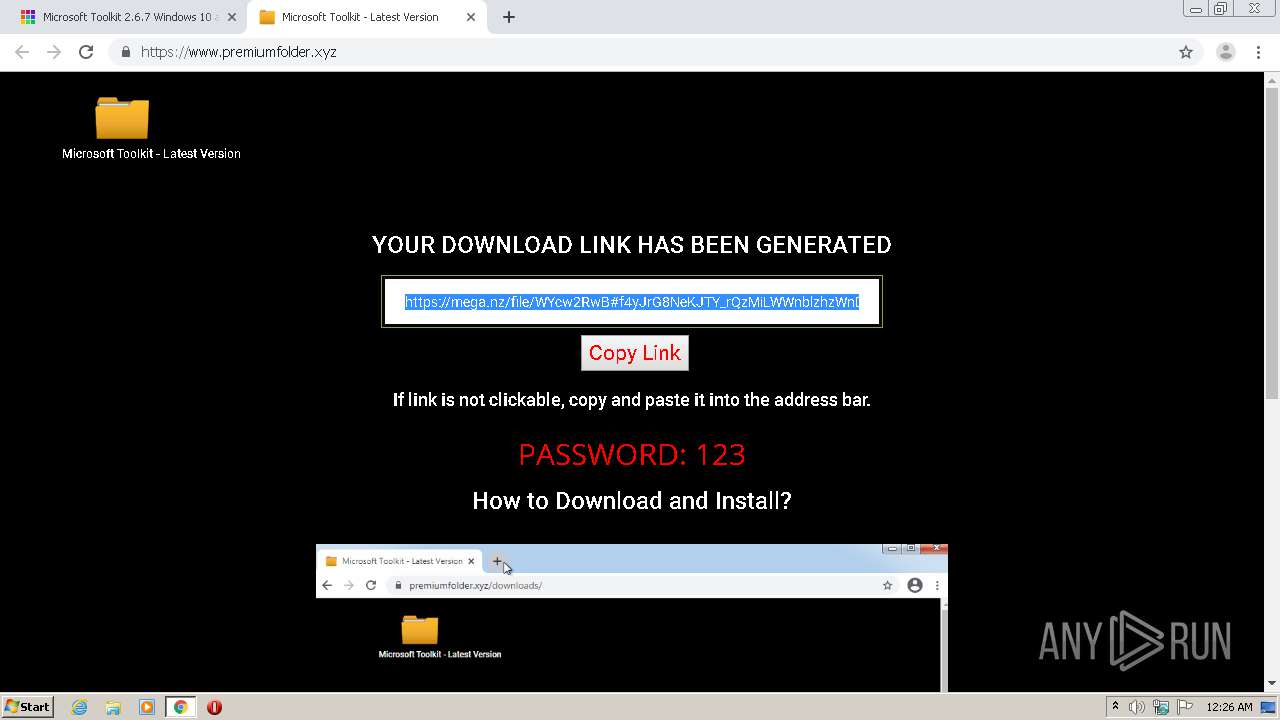
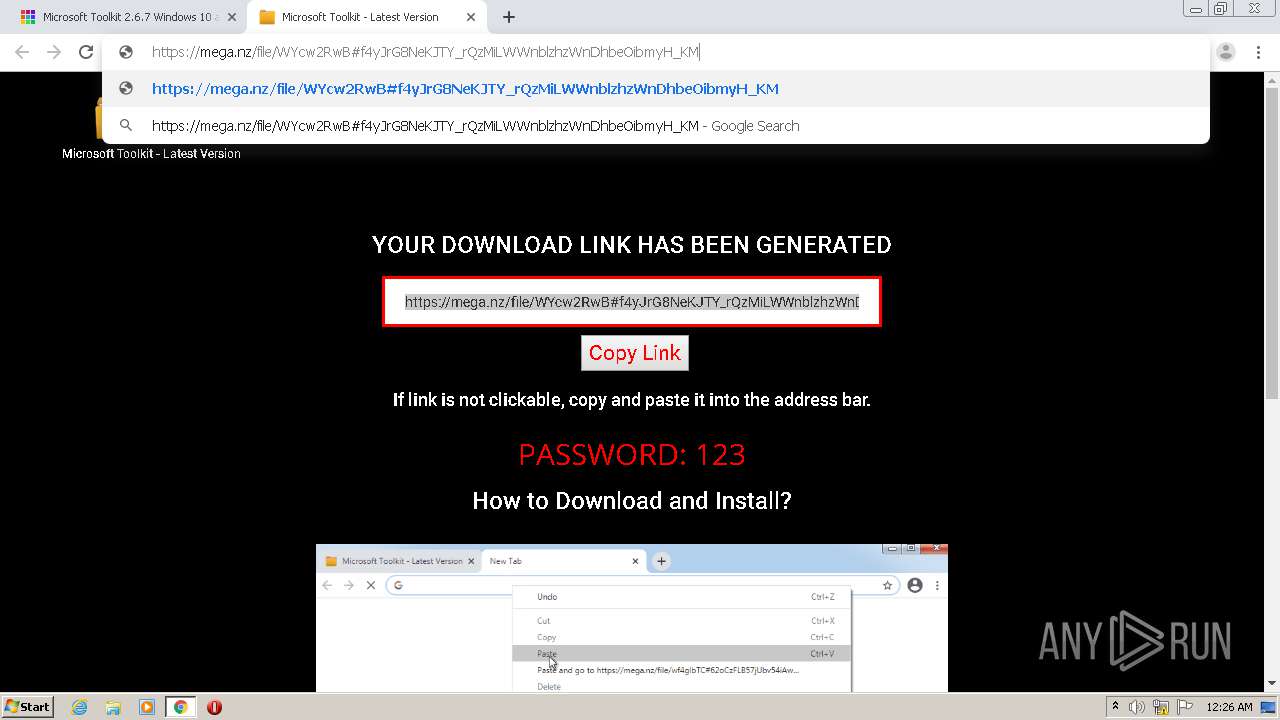
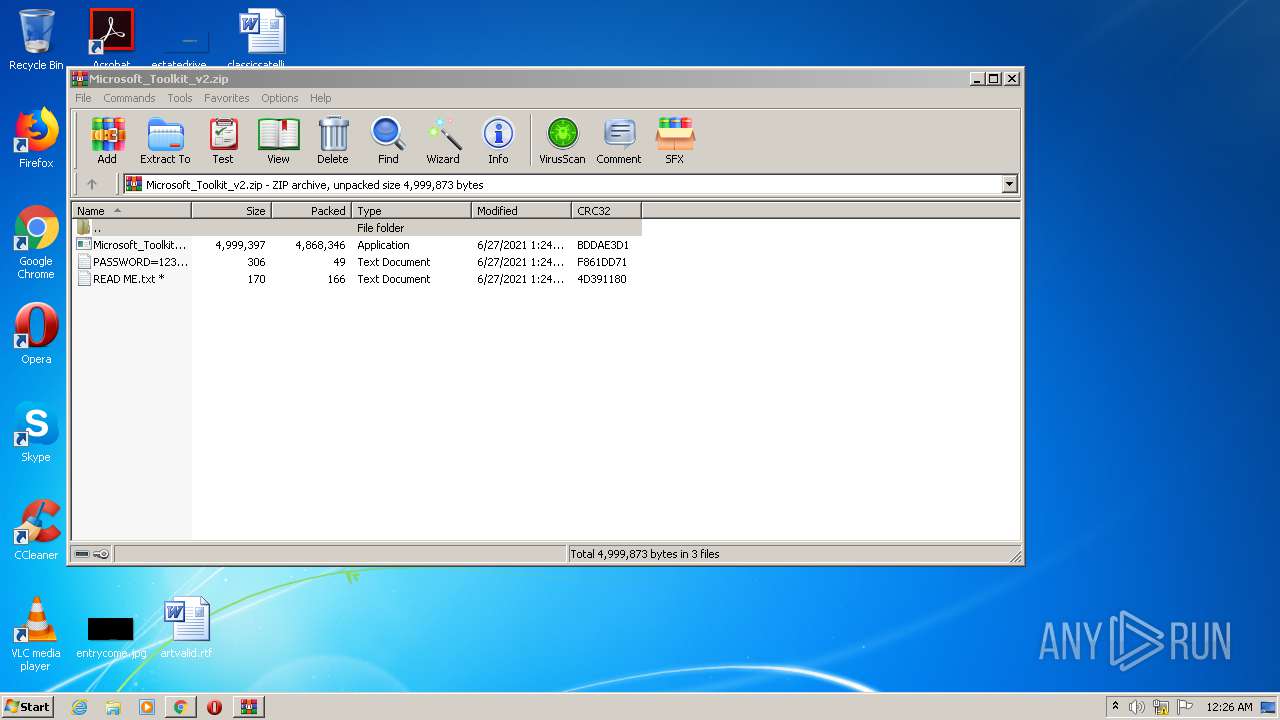
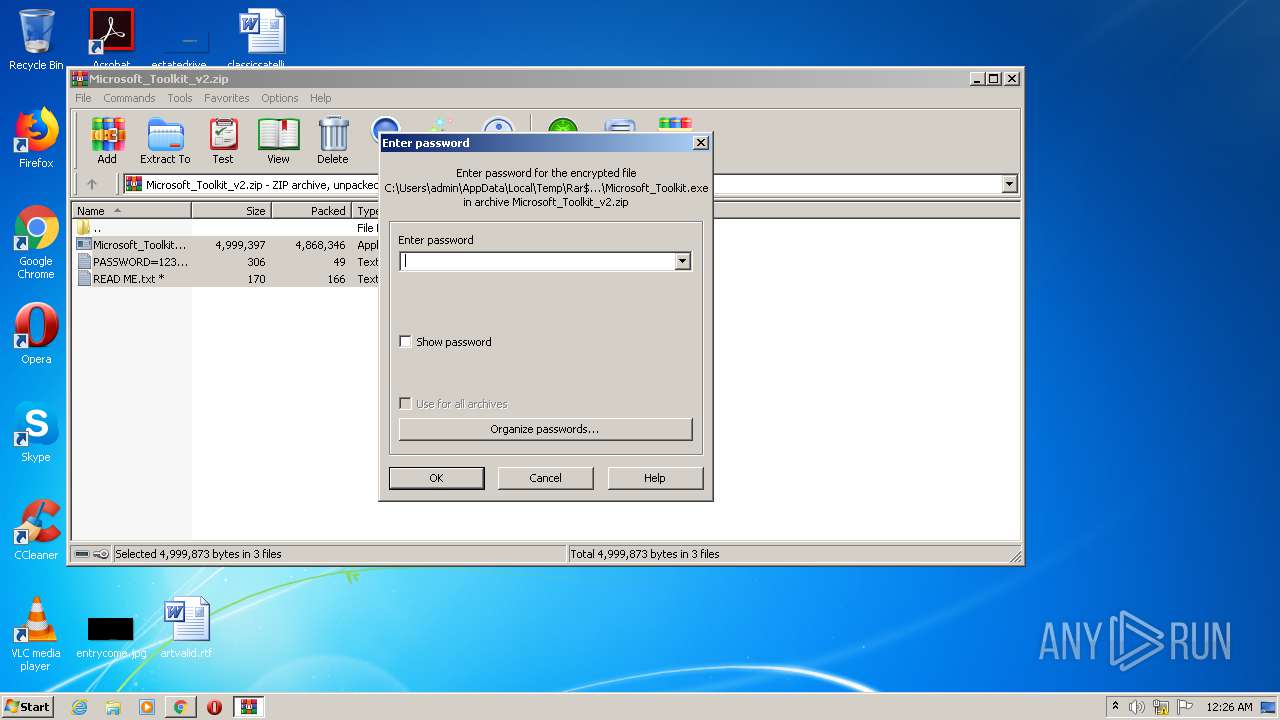
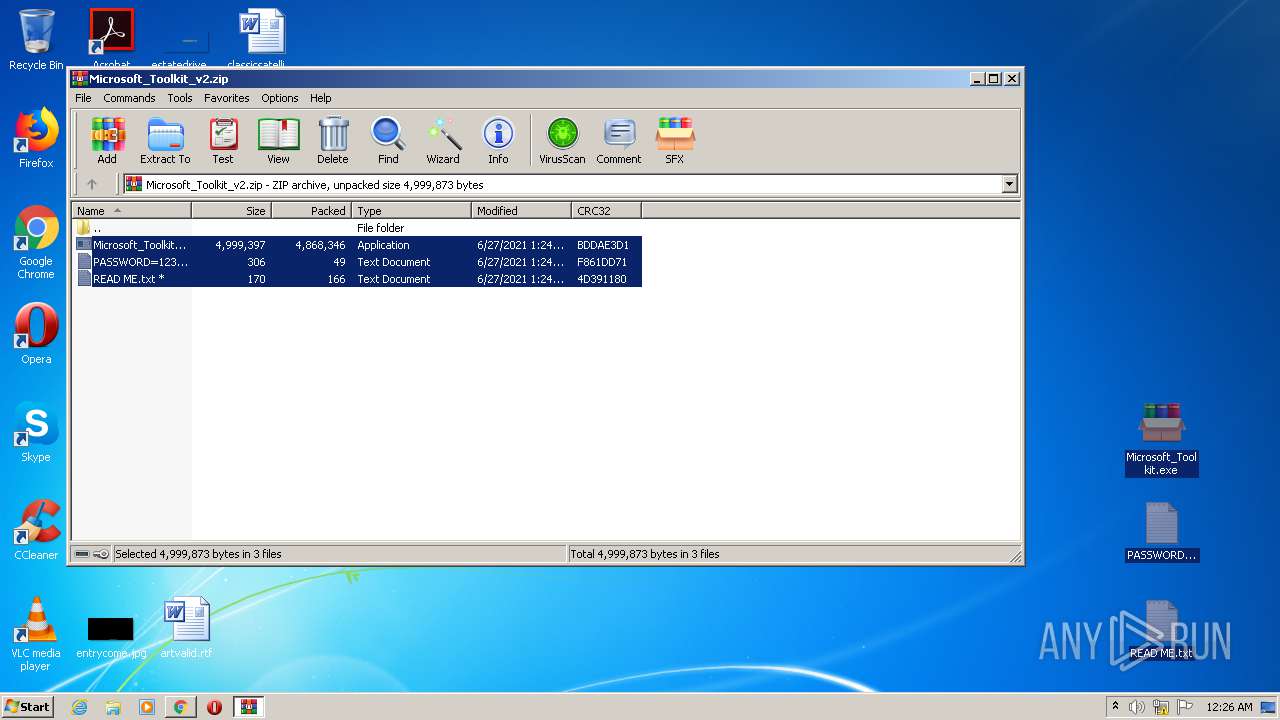
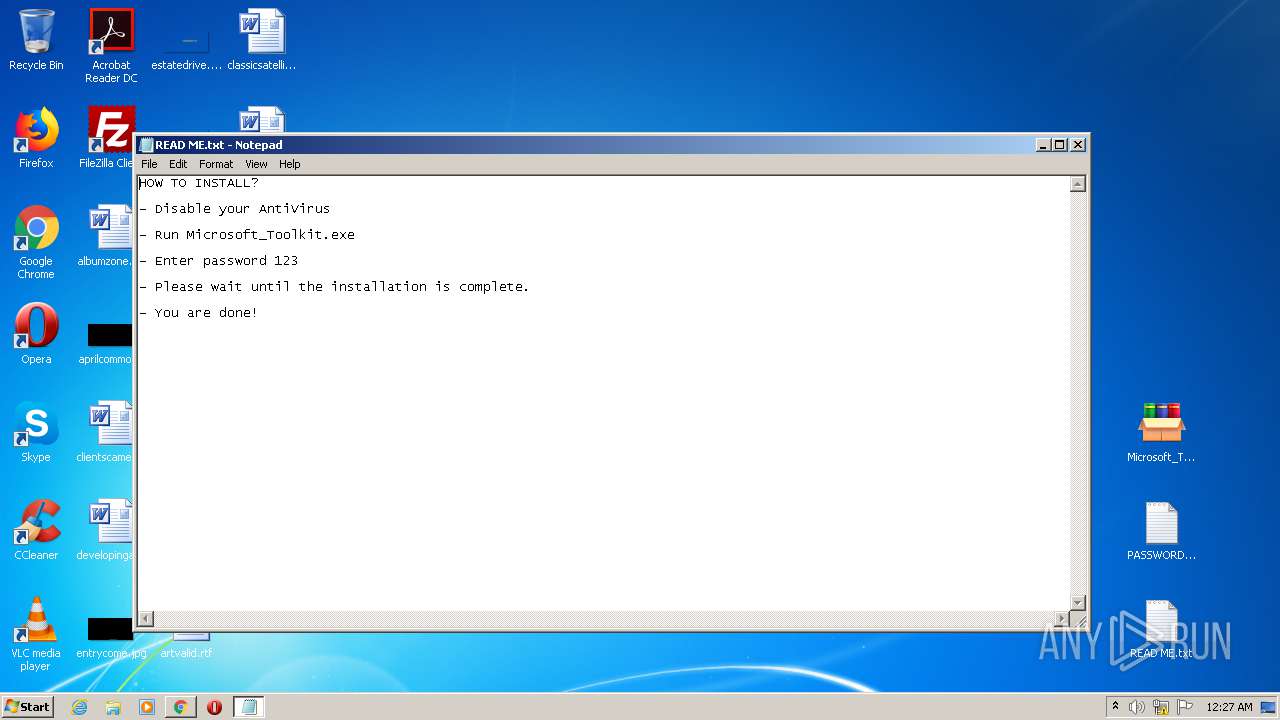
| URL: | https://freemicrosofttoolkit.com/ |
| Full analysis: | https://app.any.run/tasks/60d0f747-6bc6-45c4-8f94-7df8cf15eb0d |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | June 26, 2021, 23:25:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 8930FC6A5B59779BAAC0F706B1596960 |
| SHA1: | 9747D99DF3F633A14D59EE43C4412EE883890CA3 |
| SHA256: | FF7A0A4B474133FAE2A0E10EE92F029AAAFF12537A36373F428B0E27B868AE0F |
| SSDEEP: | 3:N88e3KKpRt:28ehpD |
MALICIOUS
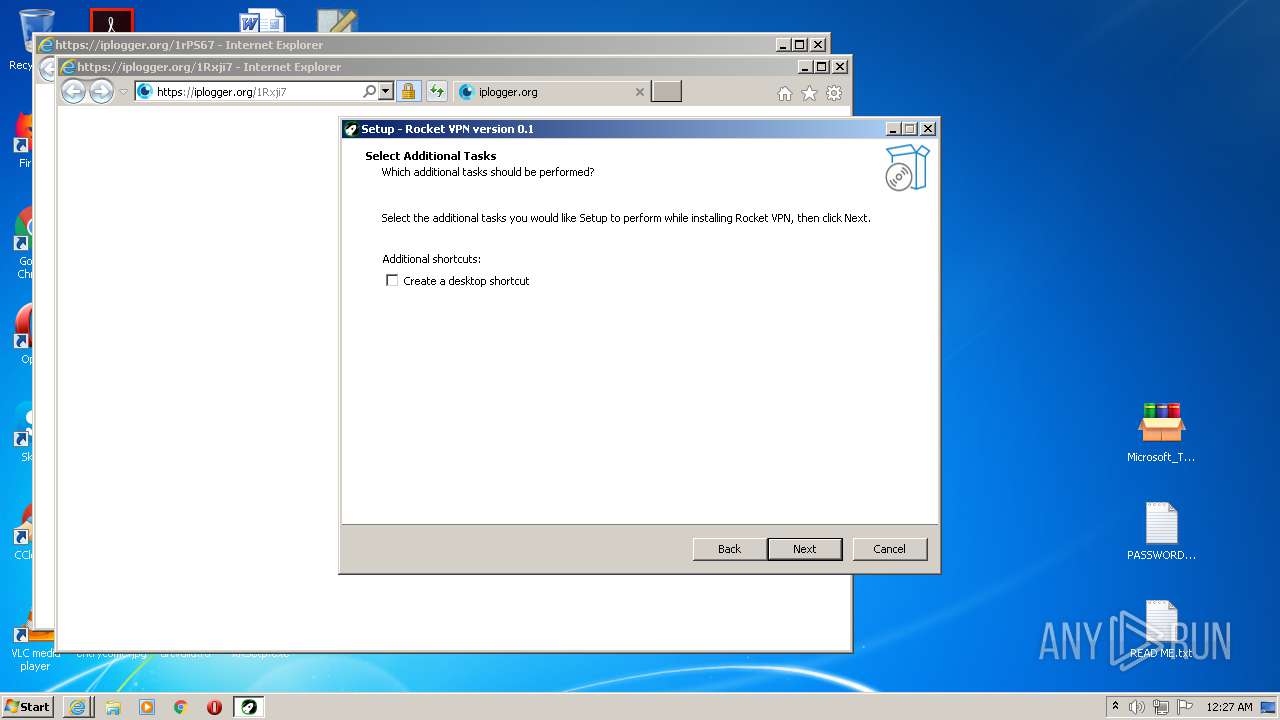
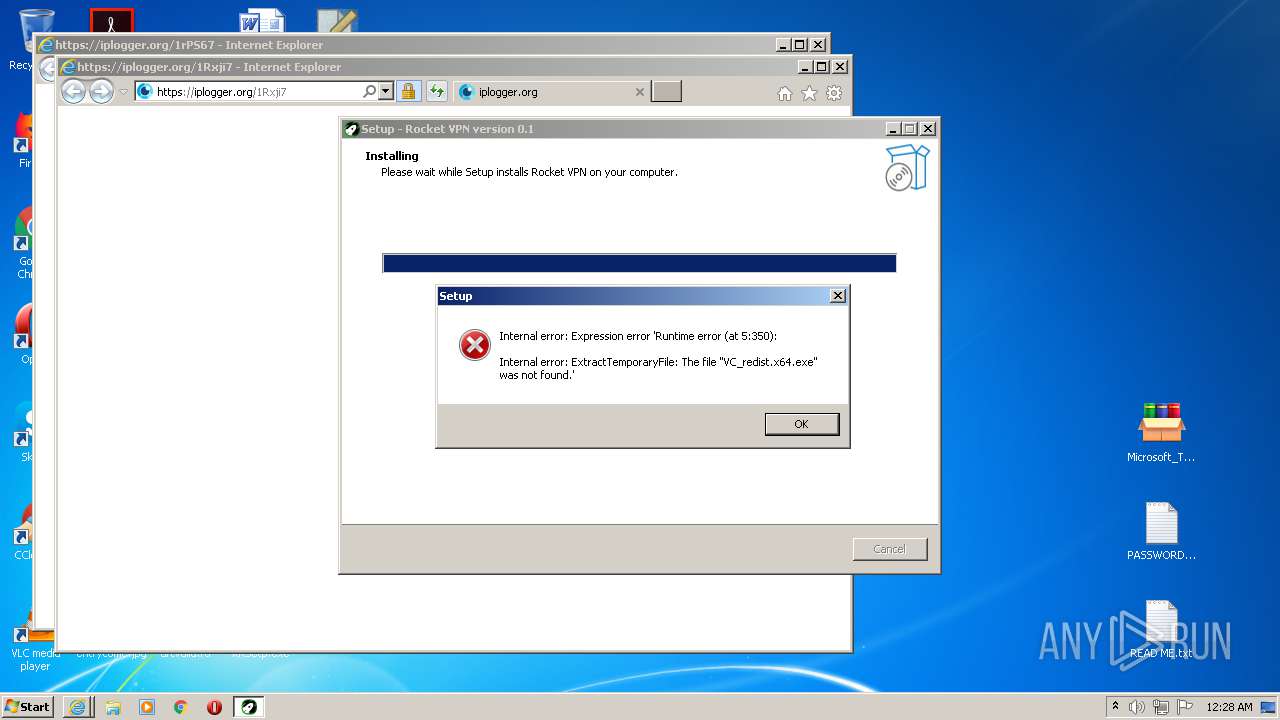
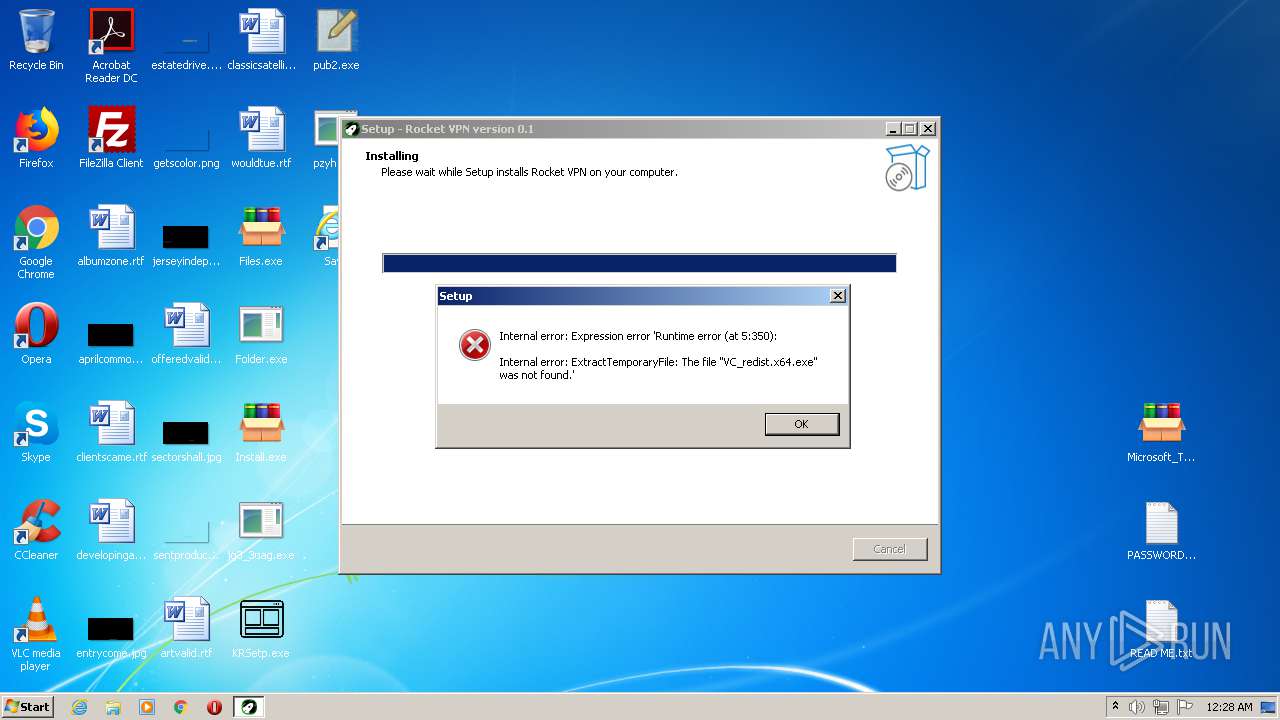
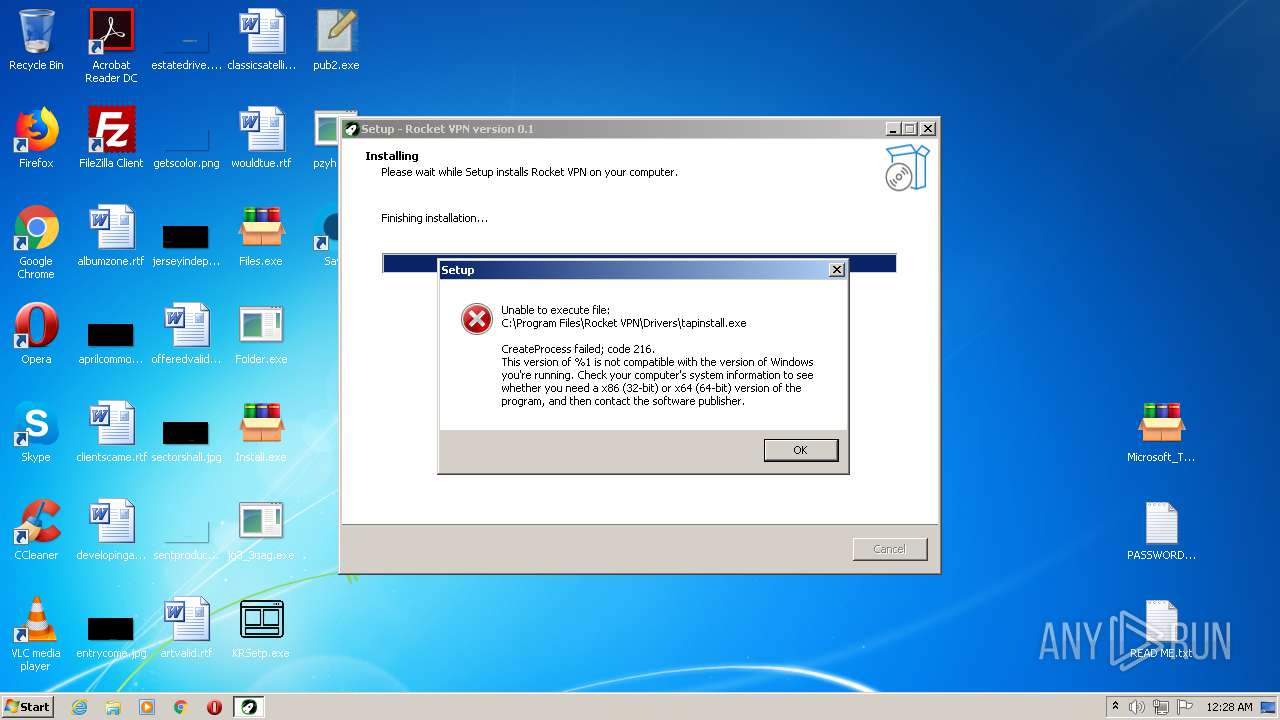
Drops executable file immediately after starts
- Microsoft_Toolkit.exe (PID: 2152)
- pzyh.exe (PID: 2284)
- Folder.exe (PID: 3596)
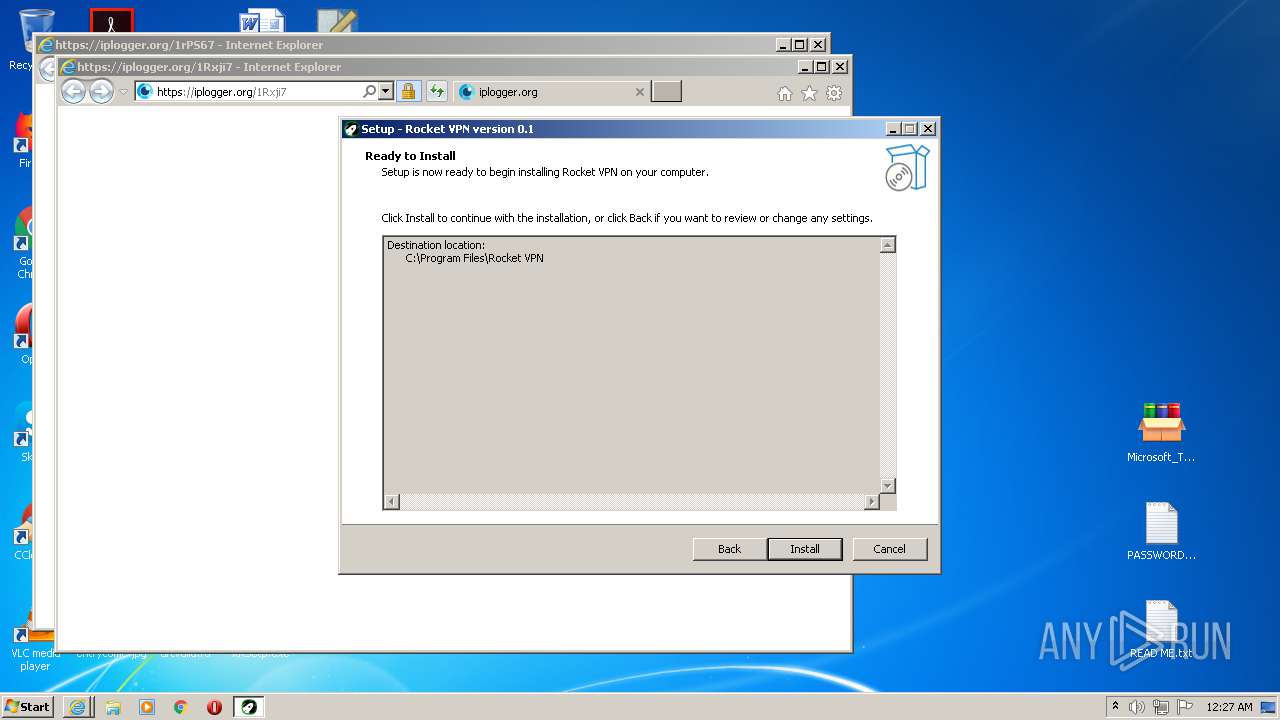
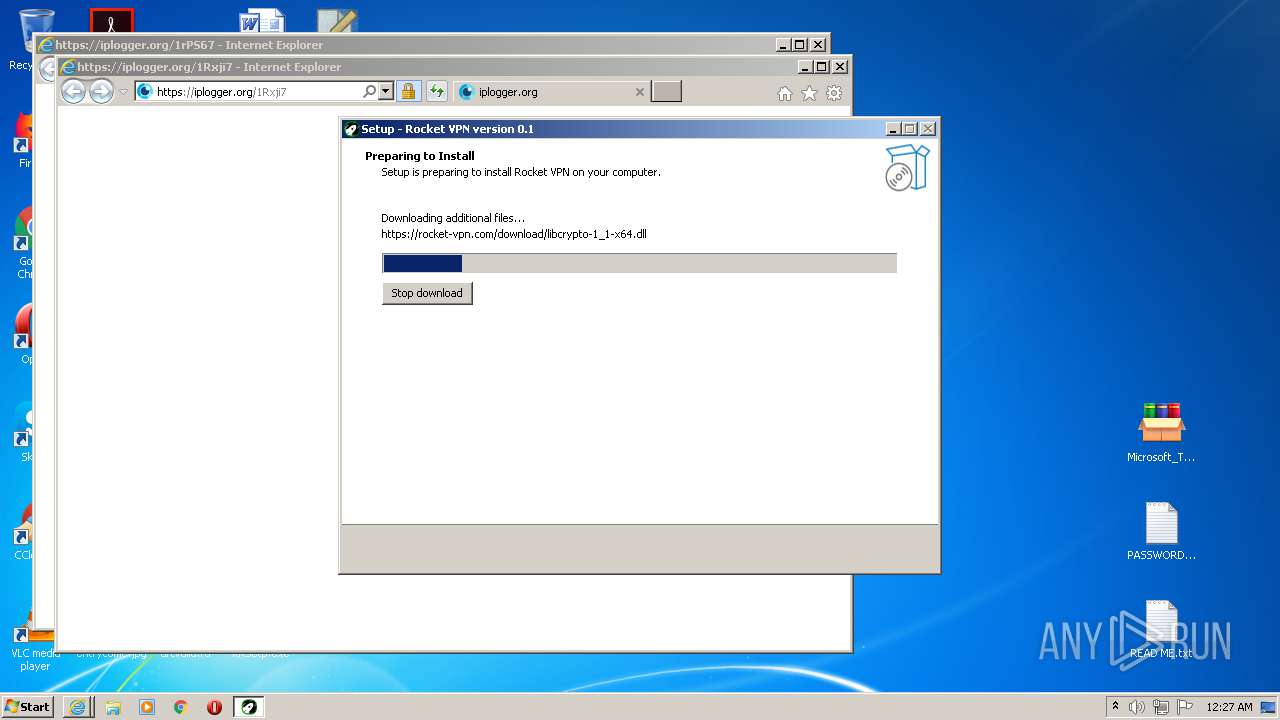
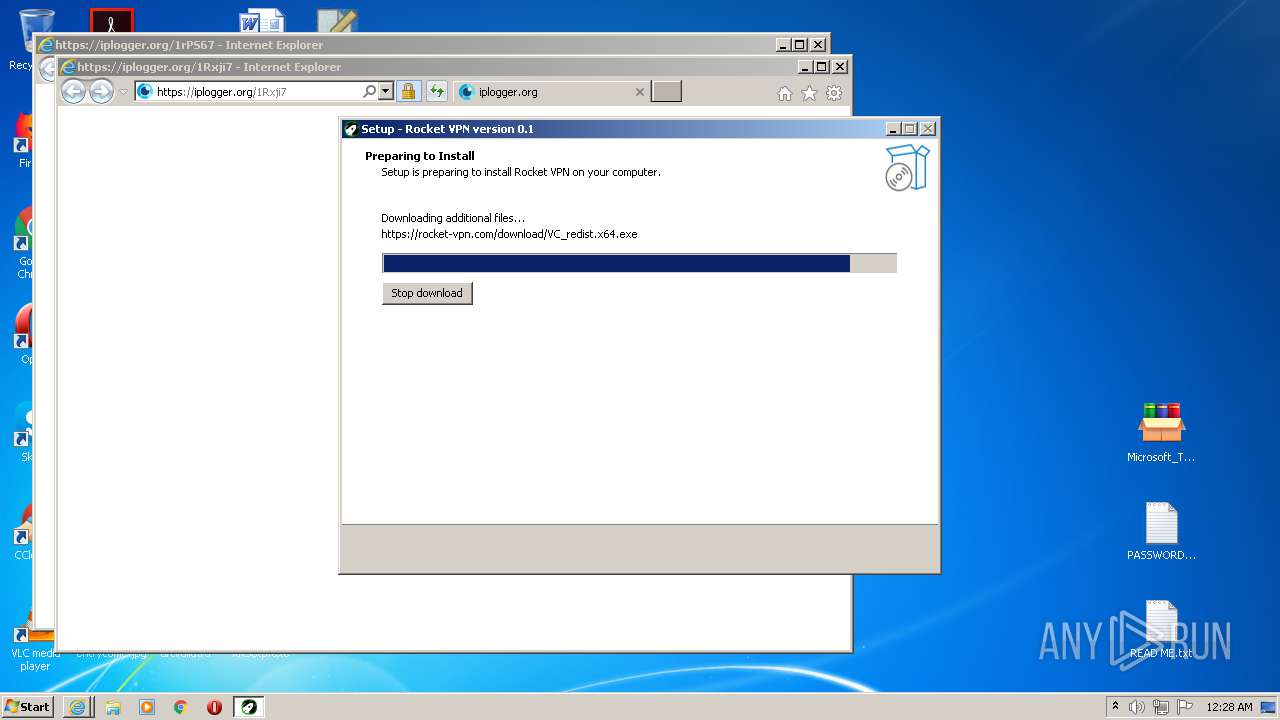
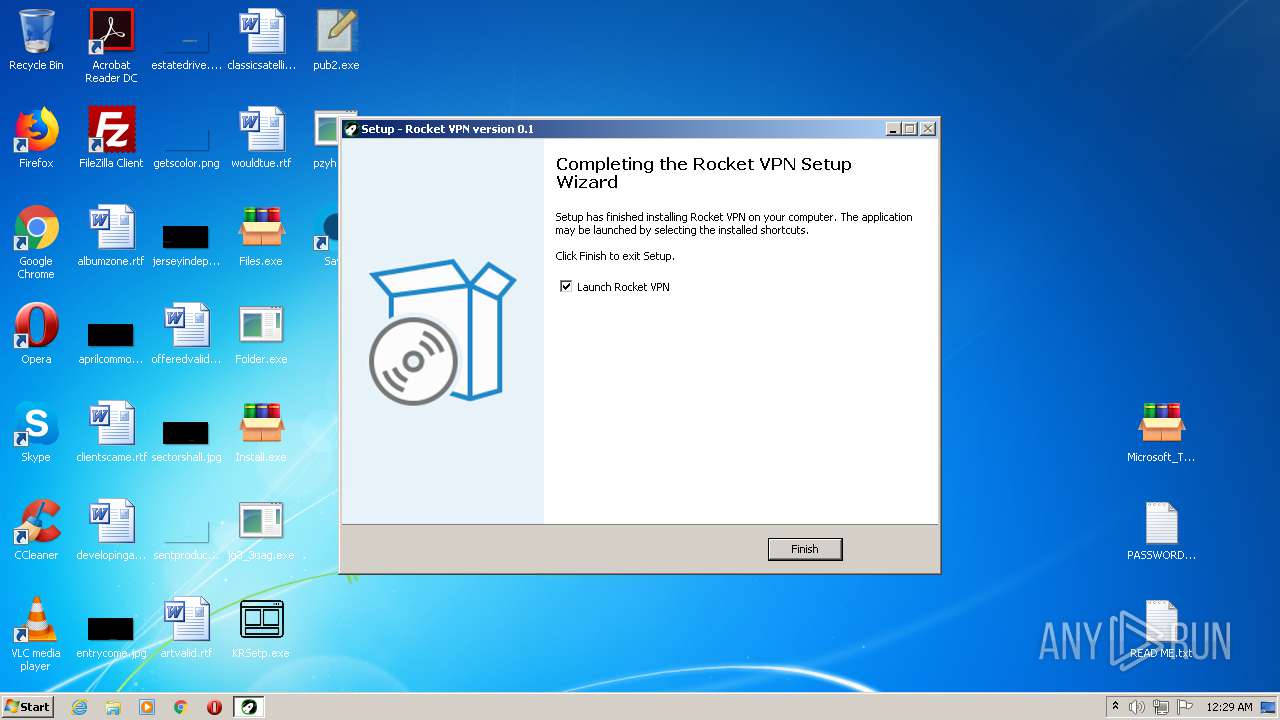
- RocketVPN.exe (PID: 3316)
- RocketVPN.exe (PID: 2764)
Application was dropped or rewritten from another process
- Files.exe (PID: 2416)
- pzyh.exe (PID: 3000)
- Microsoft_Toolkit.exe (PID: 2152)
- Install.exe (PID: 1852)
- pub2.exe (PID: 2564)
- Folder.exe (PID: 3596)
- jg3_3uag.exe (PID: 2256)
- pzyh.exe (PID: 2284)
- KRSetp.exe (PID: 3888)
- File.exe (PID: 3548)
- jfiag3g_gg.exe (PID: 3316)
- RocketVPN.exe (PID: 3316)
- 6961670.exe (PID: 2360)
- 1448142.exe (PID: 1424)
- 6717481.exe (PID: 1856)
- run.exe (PID: 2472)
- run2.exe (PID: 2116)
- jfiag3g_gg.exe (PID: 2084)
- 4850656.exe (PID: 4068)
- 4850656.exe (PID: 3092)
- RocketVPN.exe (PID: 2764)
- WinHoster.exe (PID: 2012)
- run2.exe (PID: 2112)
- run2.exe (PID: 2684)
- run2.exe (PID: 1736)
- run2.exe (PID: 3516)
- run2.exe (PID: 1768)
- run2.exe (PID: 2768)
- run2.exe (PID: 2580)
- run2.exe (PID: 1920)
- run2.exe (PID: 2808)
- run2.exe (PID: 3580)
- run2.exe (PID: 116)
- run2.exe (PID: 184)
- run2.exe (PID: 2828)
- run2.exe (PID: 2540)
- run2.exe (PID: 3184)
- run2.exe (PID: 3828)
- run2.exe (PID: 3040)
- run2.exe (PID: 2868)
- run2.exe (PID: 3700)
- run2.exe (PID: 2488)
- run2.exe (PID: 2980)
- run2.exe (PID: 1088)
- run2.exe (PID: 3164)
- run2.exe (PID: 3112)
- run2.exe (PID: 2428)
- run2.exe (PID: 2412)
- run2.exe (PID: 1468)
- run2.exe (PID: 972)
- run2.exe (PID: 2572)
- run2.exe (PID: 3476)
- run2.exe (PID: 3428)
- run2.exe (PID: 1016)
- run2.exe (PID: 1216)
- run2.exe (PID: 1248)
- run2.exe (PID: 3004)
- run2.exe (PID: 1500)
- run2.exe (PID: 2460)
- run2.exe (PID: 3844)
- run2.exe (PID: 2992)
- run2.exe (PID: 580)
- run2.exe (PID: 1332)
- run2.exe (PID: 1364)
- run2.exe (PID: 924)
- run2.exe (PID: 2532)
- run2.exe (PID: 2548)
- run2.exe (PID: 2052)
- run2.exe (PID: 3048)
- run2.exe (PID: 704)
- run2.exe (PID: 3220)
- run2.exe (PID: 2832)
- run2.exe (PID: 1932)
- run2.exe (PID: 3372)
- run2.exe (PID: 2632)
- run2.exe (PID: 3956)
- run2.exe (PID: 3140)
- run2.exe (PID: 1544)
- run2.exe (PID: 2876)
- run2.exe (PID: 3572)
- run2.exe (PID: 1392)
- run2.exe (PID: 592)
- run2.exe (PID: 3344)
- run2.exe (PID: 1020)
- run2.exe (PID: 3212)
- run2.exe (PID: 692)
- run2.exe (PID: 616)
- run2.exe (PID: 1860)
- run2.exe (PID: 632)
- run2.exe (PID: 2732)
- run2.exe (PID: 1720)
- run2.exe (PID: 3880)
- run2.exe (PID: 2624)
- run2.exe (PID: 3280)
- run2.exe (PID: 2944)
- run2.exe (PID: 3124)
- run2.exe (PID: 1488)
- run2.exe (PID: 1312)
- run2.exe (PID: 1524)
- run2.exe (PID: 3860)
- run2.exe (PID: 2100)
- run2.exe (PID: 4296)
- run2.exe (PID: 4380)
- run2.exe (PID: 4128)
- run2.exe (PID: 2716)
- run2.exe (PID: 4548)
- run2.exe (PID: 4716)
- run2.exe (PID: 4636)
- run2.exe (PID: 4800)
- run2.exe (PID: 4884)
- run2.exe (PID: 4464)
- run2.exe (PID: 4212)
- run2.exe (PID: 5308)
- run2.exe (PID: 5476)
- run2.exe (PID: 5560)
- run2.exe (PID: 5624)
- run2.exe (PID: 5732)
- run2.exe (PID: 5140)
- run2.exe (PID: 5220)
- run2.exe (PID: 4948)
- run2.exe (PID: 5052)
- run2.exe (PID: 5388)
- run2.exe (PID: 4104)
- run2.exe (PID: 6068)
- run2.exe (PID: 5960)
- run2.exe (PID: 4196)
- run2.exe (PID: 4588)
- run2.exe (PID: 4400)
- run2.exe (PID: 5812)
- run2.exe (PID: 5896)
- run2.exe (PID: 4756)
- run2.exe (PID: 4872)
- run2.exe (PID: 4976)
- run2.exe (PID: 5060)
- run2.exe (PID: 5152)
- run2.exe (PID: 4688)
- run2.exe (PID: 4284)
- run2.exe (PID: 4492)
- run2.exe (PID: 5236)
- run2.exe (PID: 5620)
- run2.exe (PID: 6028)
- run2.exe (PID: 5720)
- run2.exe (PID: 5832)
- run2.exe (PID: 5928)
- run2.exe (PID: 6128)
- run2.exe (PID: 5344)
- run2.exe (PID: 5436)
- run2.exe (PID: 5524)
- run2.exe (PID: 4396)
- run2.exe (PID: 4852)
- run2.exe (PID: 4532)
- run2.exe (PID: 4632)
- run2.exe (PID: 4764)
- run2.exe (PID: 5112)
- run2.exe (PID: 4156)
- run2.exe (PID: 4304)
- run2.exe (PID: 4992)
- run2.exe (PID: 5228)
- run2.exe (PID: 5636)
- run2.exe (PID: 5332)
- run2.exe (PID: 5552)
- run2.exe (PID: 5780)
- run2.exe (PID: 5976)
- run2.exe (PID: 5884)
- run2.exe (PID: 6112)
- run2.exe (PID: 4192)
- run2.exe (PID: 5428)
- run2.exe (PID: 4352)
- run2.exe (PID: 4564)
- run2.exe (PID: 4460)
- run2.exe (PID: 4684)
- run2.exe (PID: 4932)
- run2.exe (PID: 5096)
- run2.exe (PID: 5204)
- run2.exe (PID: 4860)
- run2.exe (PID: 5984)
- run2.exe (PID: 6092)
- run2.exe (PID: 4220)
- run2.exe (PID: 5300)
- run2.exe (PID: 5488)
- run2.exe (PID: 5608)
- run2.exe (PID: 5756)
- run2.exe (PID: 3536)
- run2.exe (PID: 4624)
- run2.exe (PID: 4904)
- run2.exe (PID: 5668)
- run2.exe (PID: 5076)
- run2.exe (PID: 5184)
- run2.exe (PID: 5324)
- run2.exe (PID: 5500)
- run2.exe (PID: 4312)
- run2.exe (PID: 4504)
- run2.exe (PID: 4136)
- run2.exe (PID: 6016)
- run2.exe (PID: 4328)
- run2.exe (PID: 4428)
- run2.exe (PID: 4576)
- run2.exe (PID: 4784)
- run2.exe (PID: 5784)
- run2.exe (PID: 5940)
- run2.exe (PID: 5232)
- run2.exe (PID: 5408)
- run2.exe (PID: 5700)
- run2.exe (PID: 5516)
- run2.exe (PID: 5844)
- run2.exe (PID: 5920)
- run2.exe (PID: 4944)
- run2.exe (PID: 5044)
- run2.exe (PID: 4276)
- run2.exe (PID: 3384)
- run2.exe (PID: 1868)
- run2.exe (PID: 4708)
- run2.exe (PID: 2636)
- run2.exe (PID: 3380)
- run2.exe (PID: 1004)
- run2.exe (PID: 6024)
- run2.exe (PID: 5864)
- run2.exe (PID: 3396)
- run2.exe (PID: 5192)
- run2.exe (PID: 5304)
- run2.exe (PID: 3260)
- run2.exe (PID: 5640)
- run2.exe (PID: 5000)
- run2.exe (PID: 5600)
- run2.exe (PID: 2688)
- run2.exe (PID: 5328)
- run2.exe (PID: 2432)
- run2.exe (PID: 3648)
- run2.exe (PID: 4480)
- run2.exe (PID: 4600)
- run2.exe (PID: 1612)
- run2.exe (PID: 4604)
- run2.exe (PID: 1556)
- run2.exe (PID: 2160)
- run2.exe (PID: 5028)
- run2.exe (PID: 5176)
- run2.exe (PID: 5892)
- run2.exe (PID: 3808)
- run2.exe (PID: 4324)
- run2.exe (PID: 5648)
- run2.exe (PID: 4544)
- run2.exe (PID: 4040)
- run2.exe (PID: 5932)
- run2.exe (PID: 5268)
- run2.exe (PID: 5424)
- run2.exe (PID: 3284)
- run2.exe (PID: 5460)
- run2.exe (PID: 4100)
- run2.exe (PID: 5704)
- run2.exe (PID: 5916)
- run2.exe (PID: 4288)
- run2.exe (PID: 4776)
- run2.exe (PID: 5004)
- run2.exe (PID: 5320)
- run2.exe (PID: 4748)
- run2.exe (PID: 2456)
- run2.exe (PID: 5768)
- run2.exe (PID: 5944)
- run2.exe (PID: 4148)
- run2.exe (PID: 4424)
- run2.exe (PID: 3652)
- run2.exe (PID: 4140)
- run2.exe (PID: 728)
- run2.exe (PID: 4984)
- run2.exe (PID: 5504)
- run2.exe (PID: 5652)
- run2.exe (PID: 6020)
- run2.exe (PID: 4540)
- run2.exe (PID: 5248)
- run2.exe (PID: 2924)
- run2.exe (PID: 4440)
- run2.exe (PID: 5664)
- run2.exe (PID: 4360)
- run2.exe (PID: 4208)
- run2.exe (PID: 4560)
- run2.exe (PID: 4116)
- run2.exe (PID: 3532)
- run2.exe (PID: 4248)
- run2.exe (PID: 2196)
- run2.exe (PID: 1992)
- run2.exe (PID: 4240)
- run2.exe (PID: 5008)
- run2.exe (PID: 4936)
- run2.exe (PID: 5472)
- run2.exe (PID: 5416)
- run2.exe (PID: 5880)
- run2.exe (PID: 2800)
- run2.exe (PID: 4280)
- run2.exe (PID: 5280)
- run2.exe (PID: 3876)
- run2.exe (PID: 5196)
- run2.exe (PID: 5904)
- run2.exe (PID: 4680)
- run2.exe (PID: 4316)
- run2.exe (PID: 5292)
- run2.exe (PID: 4676)
- run2.exe (PID: 4112)
- run2.exe (PID: 4972)
- run2.exe (PID: 1952)
- run2.exe (PID: 5824)
- run2.exe (PID: 6084)
- run2.exe (PID: 5576)
- run2.exe (PID: 2476)
- run2.exe (PID: 4272)
- run2.exe (PID: 4392)
- run2.exe (PID: 5180)
- run2.exe (PID: 4256)
- run2.exe (PID: 5484)
- run2.exe (PID: 5936)
- run2.exe (PID: 5796)
- run2.exe (PID: 4572)
- run2.exe (PID: 5680)
- run2.exe (PID: 4476)
- run2.exe (PID: 4568)
- run2.exe (PID: 5996)
- run2.exe (PID: 5908)
- run2.exe (PID: 4168)
- run2.exe (PID: 2144)
- run2.exe (PID: 4812)
- run2.exe (PID: 5512)
- run2.exe (PID: 4780)
- run2.exe (PID: 5548)
- run2.exe (PID: 5540)
- run2.exe (PID: 2588)
- run2.exe (PID: 5084)
- run2.exe (PID: 4320)
- run2.exe (PID: 5020)
- run2.exe (PID: 5532)
- run2.exe (PID: 5272)
- run2.exe (PID: 4228)
- run2.exe (PID: 4444)
- run2.exe (PID: 3400)
- run2.exe (PID: 5400)
- run2.exe (PID: 5464)
- run2.exe (PID: 2756)
- run2.exe (PID: 5208)
- run2.exe (PID: 4448)
- run2.exe (PID: 4200)
- run2.exe (PID: 6036)
- run2.exe (PID: 5444)
- run2.exe (PID: 4740)
- run2.exe (PID: 4792)
- run2.exe (PID: 6156)
- run2.exe (PID: 3460)
- run2.exe (PID: 5040)
- run2.exe (PID: 6324)
- run2.exe (PID: 6408)
- run2.exe (PID: 6492)
- run2.exe (PID: 6556)
- run2.exe (PID: 6660)
- run2.exe (PID: 6748)
- run2.exe (PID: 6232)
- run2.exe (PID: 7000)
- run2.exe (PID: 7084)
- run2.exe (PID: 7168)
- run2.exe (PID: 7336)
- run2.exe (PID: 7252)
- run2.exe (PID: 6832)
- run2.exe (PID: 6896)
- run2.exe (PID: 7844)
- run2.exe (PID: 7756)
- run2.exe (PID: 7928)
- run2.exe (PID: 7420)
- run2.exe (PID: 7504)
- run2.exe (PID: 7592)
- run2.exe (PID: 7676)
- run2.exe (PID: 6304)
- run2.exe (PID: 6488)
- run2.exe (PID: 6376)
- run2.exe (PID: 6588)
- run2.exe (PID: 6772)
- run2.exe (PID: 8008)
- run2.exe (PID: 8092)
- run2.exe (PID: 8176)
- run2.exe (PID: 6200)
- run2.exe (PID: 6672)
- run2.exe (PID: 7056)
- run2.exe (PID: 7144)
- run2.exe (PID: 7324)
- run2.exe (PID: 7232)
- run2.exe (PID: 6848)
- run2.exe (PID: 6948)
- run2.exe (PID: 7428)
- run2.exe (PID: 7700)
- run2.exe (PID: 7900)
- run2.exe (PID: 7964)
- run2.exe (PID: 8072)
- run2.exe (PID: 7528)
- run2.exe (PID: 7584)
- run2.exe (PID: 7796)
- run2.exe (PID: 6480)
- run2.exe (PID: 6584)
- run2.exe (PID: 6700)
- run2.exe (PID: 8140)
- run2.exe (PID: 5440)
- run2.exe (PID: 6300)
- run2.exe (PID: 6388)
- run2.exe (PID: 7124)
- run2.exe (PID: 7268)
- run2.exe (PID: 7416)
- run2.exe (PID: 7548)
- run2.exe (PID: 6788)
- run2.exe (PID: 6884)
- run2.exe (PID: 6980)
- run2.exe (PID: 7228)
- run2.exe (PID: 6312)
- run2.exe (PID: 8132)
- run2.exe (PID: 6208)
- run2.exe (PID: 5124)
- run2.exe (PID: 7716)
- run2.exe (PID: 7840)
- run2.exe (PID: 8048)
- run2.exe (PID: 7956)
- run2.exe (PID: 6760)
- run2.exe (PID: 7020)
- run2.exe (PID: 6904)
- run2.exe (PID: 6420)
- run2.exe (PID: 6564)
- run2.exe (PID: 6696)
- run2.exe (PID: 7656)
- run2.exe (PID: 7452)
- run2.exe (PID: 7824)
- run2.exe (PID: 7924)
- run2.exe (PID: 8024)
- run2.exe (PID: 4628)
- run2.exe (PID: 7200)
- run2.exe (PID: 7344)
- run2.exe (PID: 4416)
- run2.exe (PID: 6372)
- run2.exe (PID: 4556)
- run2.exe (PID: 3204)
- run2.exe (PID: 8128)
- run2.exe (PID: 6196)
- run2.exe (PID: 6456)
- run2.exe (PID: 6576)
- run2.exe (PID: 7448)
- run2.exe (PID: 7684)
- run2.exe (PID: 7612)
- run2.exe (PID: 4520)
- run2.exe (PID: 8016)
- run2.exe (PID: 6956)
- run2.exe (PID: 7108)
- run2.exe (PID: 5764)
- run2.exe (PID: 7364)
- run2.exe (PID: 6512)
- run2.exe (PID: 6820)
- run2.exe (PID: 4160)
- run2.exe (PID: 6244)
- run2.exe (PID: 6364)
- run2.exe (PID: 6620)
- run2.exe (PID: 6796)
- run2.exe (PID: 4584)
- run2.exe (PID: 7856)
- run2.exe (PID: 7764)
- run2.exe (PID: 7048)
- run2.exe (PID: 7196)
- run2.exe (PID: 7320)
- run2.exe (PID: 7480)
- run2.exe (PID: 8064)
- run2.exe (PID: 4900)
- run2.exe (PID: 5852)
- run2.exe (PID: 4880)
- run2.exe (PID: 7292)
- run2.exe (PID: 5364)
- run2.exe (PID: 6332)
- run2.exe (PID: 5972)
- run2.exe (PID: 6652)
- run2.exe (PID: 5376)
- run2.exe (PID: 7892)
- run2.exe (PID: 6172)
- run2.exe (PID: 6876)
- run2.exe (PID: 6516)
- run2.exe (PID: 4432)
- run2.exe (PID: 7104)
- run2.exe (PID: 5012)
- run2.exe (PID: 5148)
- run2.exe (PID: 7728)
- run2.exe (PID: 8104)
- run2.exe (PID: 7276)
- run2.exe (PID: 7408)
- run2.exe (PID: 7628)
- run2.exe (PID: 7744)
- run2.exe (PID: 5656)
- run2.exe (PID: 6252)
- run2.exe (PID: 8188)
- run2.exe (PID: 5760)
- run2.exe (PID: 6736)
- run2.exe (PID: 4412)
- run2.exe (PID: 7132)
- run2.exe (PID: 7240)
- run2.exe (PID: 7484)
- run2.exe (PID: 6444)
- run2.exe (PID: 7916)
- run2.exe (PID: 6368)
- run2.exe (PID: 7288)
- run2.exe (PID: 4452)
- run2.exe (PID: 6580)
- run2.exe (PID: 6908)
- run2.exe (PID: 8068)
- run2.exe (PID: 6272)
- run2.exe (PID: 5036)
- run2.exe (PID: 6472)
- run2.exe (PID: 4724)
- run2.exe (PID: 7136)
- run2.exe (PID: 7396)
- run2.exe (PID: 7576)
- run2.exe (PID: 7776)
- run2.exe (PID: 7792)
- run2.exe (PID: 7096)
- run2.exe (PID: 6852)
- run2.exe (PID: 6484)
- run2.exe (PID: 6164)
- run2.exe (PID: 3512)
- run2.exe (PID: 3412)
- run2.exe (PID: 5032)
- run2.exe (PID: 7616)
- run2.exe (PID: 7940)
- run2.exe (PID: 5808)
- run2.exe (PID: 6692)
- run2.exe (PID: 6616)
- run2.exe (PID: 7388)
- run2.exe (PID: 2124)
- run2.exe (PID: 5200)
- run2.exe (PID: 6996)
- run2.exe (PID: 7284)
- run2.exe (PID: 7688)
- run2.exe (PID: 7540)
- run2.exe (PID: 6288)
- run2.exe (PID: 6336)
- run2.exe (PID: 7444)
- run2.exe (PID: 7812)
- run2.exe (PID: 7352)
- run2.exe (PID: 8112)
- run2.exe (PID: 8004)
- run2.exe (PID: 7640)
- run2.exe (PID: 6428)
- run2.exe (PID: 6176)
- run2.exe (PID: 7712)
- run2.exe (PID: 4728)
- run2.exe (PID: 4712)
- run2.exe (PID: 6436)
- run2.exe (PID: 7472)
- run2.exe (PID: 6740)
- run2.exe (PID: 5676)
- run2.exe (PID: 6080)
- run2.exe (PID: 6676)
- run2.exe (PID: 7296)
- run2.exe (PID: 2172)
- run2.exe (PID: 7092)
- run2.exe (PID: 6932)
- run2.exe (PID: 6600)
- run2.exe (PID: 7672)
- run2.exe (PID: 5356)
- run2.exe (PID: 7164)
- run2.exe (PID: 6960)
- run2.exe (PID: 6248)
- run2.exe (PID: 6264)
- run2.exe (PID: 4732)
- run2.exe (PID: 6812)
- run2.exe (PID: 7544)
- run2.exe (PID: 5276)
- run2.exe (PID: 6148)
- run2.exe (PID: 7264)
- run2.exe (PID: 7204)
- run2.exe (PID: 5456)
- run2.exe (PID: 6992)
- run2.exe (PID: 7920)
- run2.exe (PID: 7988)
- run2.exe (PID: 1464)
- run2.exe (PID: 2552)
- run2.exe (PID: 2268)
- run2.exe (PID: 4232)
- run2.exe (PID: 7068)
- run2.exe (PID: 7732)
- run2.exe (PID: 6508)
- run2.exe (PID: 7372)
- run2.exe (PID: 7772)
- run2.exe (PID: 7724)
- run2.exe (PID: 5252)
- run2.exe (PID: 1644)
- run2.exe (PID: 7648)
- run2.exe (PID: 7768)
- run2.exe (PID: 8032)
- run2.exe (PID: 8156)
- run2.exe (PID: 7980)
- run2.exe (PID: 2180)
- run2.exe (PID: 7248)
- run2.exe (PID: 6724)
- run2.exe (PID: 7312)
- run2.exe (PID: 6432)
- run2.exe (PID: 3436)
- run2.exe (PID: 7076)
- run2.exe (PID: 6340)
- run2.exe (PID: 3136)
- run2.exe (PID: 7380)
- run2.exe (PID: 7788)
- run2.exe (PID: 6384)
- run2.exe (PID: 7660)
- run2.exe (PID: 8284)
- run2.exe (PID: 7140)
- run2.exe (PID: 8392)
- run2.exe (PID: 8496)
- run2.exe (PID: 8080)
- run2.exe (PID: 7872)
- run2.exe (PID: 5688)
- run2.exe (PID: 2364)
- run2.exe (PID: 6856)
- run2.exe (PID: 3912)
- run2.exe (PID: 6536)
- run2.exe (PID: 9336)
- run2.exe (PID: 9172)
- run2.exe (PID: 9256)
- run2.exe (PID: 9504)
- run2.exe (PID: 9420)
- run2.exe (PID: 9840)
- run2.exe (PID: 9756)
- run2.exe (PID: 8584)
- run2.exe (PID: 8664)
- run2.exe (PID: 8840)
- run2.exe (PID: 8748)
- run2.exe (PID: 8916)
- run2.exe (PID: 9000)
- run2.exe (PID: 9088)
- run2.exe (PID: 9588)
- run2.exe (PID: 9672)
- run2.exe (PID: 8212)
- run2.exe (PID: 9016)
- run2.exe (PID: 8632)
- run2.exe (PID: 8720)
- run2.exe (PID: 8836)
- run2.exe (PID: 8944)
- run2.exe (PID: 9104)
- run2.exe (PID: 9924)
- run2.exe (PID: 10008)
- run2.exe (PID: 10176)
- run2.exe (PID: 10092)
- run2.exe (PID: 8280)
- run2.exe (PID: 8376)
- run2.exe (PID: 8476)
- run2.exe (PID: 8572)
- run2.exe (PID: 9784)
- run2.exe (PID: 9860)
- run2.exe (PID: 9956)
- run2.exe (PID: 10068)
- run2.exe (PID: 8372)
- run2.exe (PID: 8208)
- run2.exe (PID: 6548)
- run2.exe (PID: 8492)
- run2.exe (PID: 8608)
- run2.exe (PID: 9184)
- run2.exe (PID: 9316)
- run2.exe (PID: 7948)
- run2.exe (PID: 9484)
- run2.exe (PID: 9576)
- run2.exe (PID: 9644)
- run2.exe (PID: 10160)
- run2.exe (PID: 9404)
- run2.exe (PID: 9296)
- run2.exe (PID: 9724)
- run2.exe (PID: 9516)
- run2.exe (PID: 9620)
- run2.exe (PID: 7624)
- run2.exe (PID: 10004)
- run2.exe (PID: 9920)
- run2.exe (PID: 10132)
- run2.exe (PID: 8660)
- run2.exe (PID: 8764)
- run2.exe (PID: 8904)
- run2.exe (PID: 9012)
- run2.exe (PID: 9108)
- run2.exe (PID: 9200)
- run2.exe (PID: 7600)
- run2.exe (PID: 8912)
- run2.exe (PID: 8028)
- run2.exe (PID: 9360)
- run2.exe (PID: 9476)
- run2.exe (PID: 9596)
- run2.exe (PID: 9688)
- run2.exe (PID: 10208)
- run2.exe (PID: 7748)
- run2.exe (PID: 8360)
- run2.exe (PID: 8480)
- run2.exe (PID: 8564)
- run2.exe (PID: 8700)
- run2.exe (PID: 8804)
- run2.exe (PID: 9236)
- run2.exe (PID: 8744)
- run2.exe (PID: 5684)
- run2.exe (PID: 8996)
- run2.exe (PID: 8820)
- run2.exe (PID: 6404)
- run2.exe (PID: 9180)
- run2.exe (PID: 9364)
- run2.exe (PID: 9564)
- run2.exe (PID: 9804)
- run2.exe (PID: 9912)
- run2.exe (PID: 10040)
- run2.exe (PID: 6972)
- run2.exe (PID: 8252)
- run2.exe (PID: 8352)
- run2.exe (PID: 8448)
- run2.exe (PID: 10204)
- run2.exe (PID: 8464)
- run2.exe (PID: 8860)
- run2.exe (PID: 7016)
- run2.exe (PID: 8676)
- run2.exe (PID: 9068)
- run2.exe (PID: 6628)
- run2.exe (PID: 7460)
- run2.exe (PID: 9480)
- run2.exe (PID: 9732)
- run2.exe (PID: 9828)
- run2.exe (PID: 9988)
- run2.exe (PID: 2888)
- run2.exe (PID: 8304)
- run2.exe (PID: 8172)
- run2.exe (PID: 8780)
- run2.exe (PID: 9248)
- run2.exe (PID: 8956)
- run2.exe (PID: 7804)
- run2.exe (PID: 9388)
- run2.exe (PID: 9552)
- run2.exe (PID: 9460)
- run2.exe (PID: 4796)
- run2.exe (PID: 9704)
- run2.exe (PID: 7992)
- run2.exe (PID: 10116)
- run2.exe (PID: 8228)
- run2.exe (PID: 6260)
- run2.exe (PID: 5800)
- run2.exe (PID: 8540)
- run2.exe (PID: 8768)
- run2.exe (PID: 6216)
- run2.exe (PID: 9116)
- run2.exe (PID: 9532)
- run2.exe (PID: 8536)
- run2.exe (PID: 6888)
- run2.exe (PID: 9628)
- run2.exe (PID: 9764)
- run2.exe (PID: 9856)
- run2.exe (PID: 9976)
- run2.exe (PID: 10220)
- run2.exe (PID: 6976)
- run2.exe (PID: 8440)
- run2.exe (PID: 3924)
- run2.exe (PID: 7112)
- run2.exe (PID: 9168)
- run2.exe (PID: 9952)
- run2.exe (PID: 9560)
- run2.exe (PID: 8260)
- run2.exe (PID: 10020)
- run2.exe (PID: 8460)
- run2.exe (PID: 7100)
- run2.exe (PID: 10140)
- run2.exe (PID: 8696)
- run2.exe (PID: 8436)
- run2.exe (PID: 2796)
- run2.exe (PID: 8796)
- run2.exe (PID: 9048)
- run2.exe (PID: 9440)
- run2.exe (PID: 9992)
- run2.exe (PID: 9848)
- run2.exe (PID: 8620)
- run2.exe (PID: 8472)
- run2.exe (PID: 8828)
- run2.exe (PID: 5100)
- run2.exe (PID: 9380)
- run2.exe (PID: 9528)
- run2.exe (PID: 8624)
- run2.exe (PID: 8852)
- run2.exe (PID: 9064)
- run2.exe (PID: 9372)
- run2.exe (PID: 8692)
- run2.exe (PID: 8428)
- run2.exe (PID: 8060)
- run2.exe (PID: 2392)
- run2.exe (PID: 9268)
- run2.exe (PID: 7580)
- run2.exe (PID: 7832)
- run2.exe (PID: 9656)
- run2.exe (PID: 10184)
- run2.exe (PID: 6224)
- run2.exe (PID: 8568)
- run2.exe (PID: 9368)
- run2.exe (PID: 7608)
- run2.exe (PID: 8296)
- run2.exe (PID: 10120)
- run2.exe (PID: 8316)
- run2.exe (PID: 8528)
- run2.exe (PID: 9036)
- run2.exe (PID: 8232)
- run2.exe (PID: 8976)
- run2.exe (PID: 9852)
- run2.exe (PID: 2844)
- run2.exe (PID: 7536)
- run2.exe (PID: 8000)
- run2.exe (PID: 9376)
- run2.exe (PID: 9040)
- run2.exe (PID: 9220)
- run2.exe (PID: 9692)
- run2.exe (PID: 9444)
- run2.exe (PID: 9792)
- run2.exe (PID: 9900)
- run2.exe (PID: 8580)
- run2.exe (PID: 8892)
- run2.exe (PID: 3576)
- run2.exe (PID: 10188)
- run2.exe (PID: 8688)
- run2.exe (PID: 9640)
- run2.exe (PID: 9408)
- run2.exe (PID: 9624)
- run2.exe (PID: 8368)
- run2.exe (PID: 8740)
- run2.exe (PID: 9752)
- run2.exe (PID: 9456)
- run2.exe (PID: 7952)
- run2.exe (PID: 8644)
- run2.exe (PID: 9100)
- run2.exe (PID: 6612)
- run2.exe (PID: 9652)
- run2.exe (PID: 556)
- run2.exe (PID: 4124)
- run2.exe (PID: 9252)
- run2.exe (PID: 4968)
- run2.exe (PID: 10164)
- run2.exe (PID: 2720)
- run2.exe (PID: 7868)
- run2.exe (PID: 9680)
- run2.exe (PID: 7160)
- run2.exe (PID: 9876)
- run2.exe (PID: 8488)
- run2.exe (PID: 9204)
- run2.exe (PID: 9556)
- run2.exe (PID: 8884)
- run2.exe (PID: 8636)
- run2.exe (PID: 9800)
- run2.exe (PID: 10152)
- run2.exe (PID: 8424)
- run2.exe (PID: 9700)
- run2.exe (PID: 8552)
- run2.exe (PID: 4916)
- run2.exe (PID: 9324)
- run2.exe (PID: 9280)
- run2.exe (PID: 10156)
- run2.exe (PID: 8100)
- run2.exe (PID: 8344)
- run2.exe (PID: 6792)
- run2.exe (PID: 9312)
- run2.exe (PID: 8236)
- run2.exe (PID: 10024)
- run2.exe (PID: 9568)
- run2.exe (PID: 8656)
- run2.exe (PID: 9820)
- run2.exe (PID: 9024)
- run2.exe (PID: 7604)
- run2.exe (PID: 9208)
- run2.exe (PID: 10444)
- run2.exe (PID: 8684)
- run2.exe (PID: 9748)
- run2.exe (PID: 9412)
- run2.exe (PID: 10276)
- run2.exe (PID: 10360)
- run2.exe (PID: 10524)
- run2.exe (PID: 10608)
- run2.exe (PID: 10696)
- run2.exe (PID: 5136)
- run2.exe (PID: 8900)
- run2.exe (PID: 3188)
- run2.exe (PID: 9232)
- run2.exe (PID: 11120)
- run2.exe (PID: 11284)
- run2.exe (PID: 11368)
- run2.exe (PID: 11856)
- run2.exe (PID: 11452)
- run2.exe (PID: 11512)
- run2.exe (PID: 11708)
- run2.exe (PID: 11796)
- run2.exe (PID: 11932)
- run2.exe (PID: 10784)
- run2.exe (PID: 10864)
- run2.exe (PID: 10948)
- run2.exe (PID: 11032)
- run2.exe (PID: 11204)
- run2.exe (PID: 11624)
- run2.exe (PID: 10420)
- run2.exe (PID: 10516)
- run2.exe (PID: 11576)
- run2.exe (PID: 10684)
- run2.exe (PID: 10792)
- run2.exe (PID: 10892)
- run2.exe (PID: 10992)
- run2.exe (PID: 11280)
- run2.exe (PID: 11168)
- run2.exe (PID: 11380)
- run2.exe (PID: 11480)
- run2.exe (PID: 12044)
- run2.exe (PID: 12128)
- run2.exe (PID: 12212)
- run2.exe (PID: 9520)
- run2.exe (PID: 10320)
- run2.exe (PID: 10616)
- run2.exe (PID: 11080)
- run2.exe (PID: 12052)
- run2.exe (PID: 11968)
- run2.exe (PID: 12152)
- run2.exe (PID: 12224)
- run2.exe (PID: 10256)
- run2.exe (PID: 10372)
- run2.exe (PID: 10492)
- run2.exe (PID: 9492)
- run2.exe (PID: 10680)
- run2.exe (PID: 11216)
- run2.exe (PID: 10880)
- run2.exe (PID: 11004)
- run2.exe (PID: 11084)
- run2.exe (PID: 11676)
- run2.exe (PID: 11760)
- run2.exe (PID: 11864)
- run2.exe (PID: 10776)
- run2.exe (PID: 12116)
- run2.exe (PID: 11680)
- run2.exe (PID: 11912)
- run2.exe (PID: 12028)
- run2.exe (PID: 7960)
- run2.exe (PID: 12276)
- run2.exe (PID: 10392)
- run2.exe (PID: 10708)
- run2.exe (PID: 9896)
- run2.exe (PID: 10804)
- run2.exe (PID: 10908)
- run2.exe (PID: 11332)
- run2.exe (PID: 11340)
- run2.exe (PID: 11484)
- run2.exe (PID: 11604)
- run2.exe (PID: 11804)
- run2.exe (PID: 10504)
- run2.exe (PID: 6352)
- run2.exe (PID: 11444)
- run2.exe (PID: 11748)
- run2.exe (PID: 11896)
- run2.exe (PID: 11824)
- run2.exe (PID: 12060)
- run2.exe (PID: 9768)
- run2.exe (PID: 10588)
- run2.exe (PID: 10460)
- run2.exe (PID: 8556)
- run2.exe (PID: 11136)
- run2.exe (PID: 11304)
- run2.exe (PID: 11360)
- run2.exe (PID: 11588)
- run2.exe (PID: 10316)
- run2.exe (PID: 10752)
- run2.exe (PID: 11336)
- run2.exe (PID: 11476)
- run2.exe (PID: 11652)
- run2.exe (PID: 8960)
- run2.exe (PID: 8308)
- run2.exe (PID: 11140)
- run2.exe (PID: 11260)
Changes the autorun value in the registry
- pzyh.exe (PID: 2284)
- 1448142.exe (PID: 1424)
Loads dropped or rewritten executable
- chrome.exe (PID: 3856)
- iexplore.exe (PID: 2312)
- svchost.exe (PID: 3508)
- SearchProtocolHost.exe (PID: 1368)
- chrome.exe (PID: 1784)
- jg3_3uag.exe (PID: 2256)
- pzyh.exe (PID: 3000)
- chrome.exe (PID: 3480)
- chrome.exe (PID: 2996)
- jfiag3g_gg.exe (PID: 3316)
- pub2.exe (PID: 2564)
- chrome.exe (PID: 2900)
- NOTEPAD.EXE (PID: 2748)
- AUDIODG.EXE (PID: 3100)
- chrome.exe (PID: 2948)
- consent.exe (PID: 3528)
- chrome.exe (PID: 3360)
- DllHost.exe (PID: 2596)
- conhost.exe (PID: 3864)
- Folder.exe (PID: 3596)
- pzyh.exe (PID: 2284)
- chrome.exe (PID: 676)
- SearchFilterHost.exe (PID: 2300)
- wmiprvse.exe (PID: 2592)
- KRSetp.exe (PID: 3888)
- Install.exe (PID: 1852)
- DllHost.exe (PID: 2776)
- WerFault.exe (PID: 3288)
- File.exe (PID: 3548)
- chrome.exe (PID: 3180)
- chrome.exe (PID: 1692)
- DllHost.exe (PID: 3252)
- chrome.exe (PID: 2396)
- Microsoft_Toolkit.exe (PID: 2152)
- iexplore.exe (PID: 3020)
- chrome.exe (PID: 556)
- Files.exe (PID: 2416)
- chrome.exe (PID: 3452)
- wmiprvse.exe (PID: 2384)
- WinRAR.exe (PID: 2192)
- chrome.exe (PID: 1896)
- chrome.exe (PID: 3608)
- WerFault.exe (PID: 3612)
- DllHost.exe (PID: 3676)
- 6961670.exe (PID: 2360)
- consent.exe (PID: 3804)
- 6717481.exe (PID: 1856)
- 1448142.exe (PID: 1424)
- RocketVPN.exe (PID: 3316)
- consent.exe (PID: 3848)
- 4850656.exe (PID: 3092)
- conhost.exe (PID: 584)
- run.exe (PID: 2472)
- run2.exe (PID: 2116)
- jfiag3g_gg.exe (PID: 2084)
- DllHost.exe (PID: 308)
- iexplore.exe (PID: 2248)
- DllHost.exe (PID: 2220)
- RocketVPN.exe (PID: 2764)
- rUNdlL32.eXe (PID: 3324)
- WinHoster.exe (PID: 2012)
- 4850656.exe (PID: 4068)
- SearchProtocolHost.exe (PID: 3984)
- svchost.exe (PID: 3088)
- wmiprvse.exe (PID: 1108)
- run2.exe (PID: 1736)
- run2.exe (PID: 1920)
- run2.exe (PID: 3516)
- run2.exe (PID: 1768)
- run2.exe (PID: 2684)
- run2.exe (PID: 2112)
- run2.exe (PID: 2580)
- run2.exe (PID: 3184)
- run2.exe (PID: 3040)
- run2.exe (PID: 3828)
- run2.exe (PID: 3580)
- run2.exe (PID: 2808)
- run2.exe (PID: 2768)
- run2.exe (PID: 2540)
- run2.exe (PID: 2828)
- run2.exe (PID: 2488)
- run2.exe (PID: 3700)
- run2.exe (PID: 2868)
- run2.exe (PID: 184)
- run2.exe (PID: 116)
- run2.exe (PID: 2980)
- run2.exe (PID: 1088)
- run2.exe (PID: 3112)
- run2.exe (PID: 2428)
- run2.exe (PID: 2412)
- run2.exe (PID: 1016)
- run2.exe (PID: 3164)
- run2.exe (PID: 3476)
- run2.exe (PID: 3428)
- run2.exe (PID: 1468)
- run2.exe (PID: 3004)
- run2.exe (PID: 2572)
- run2.exe (PID: 1500)
- run2.exe (PID: 1216)
- run2.exe (PID: 2460)
- run2.exe (PID: 3844)
- run2.exe (PID: 972)
- run2.exe (PID: 2052)
- run2.exe (PID: 1248)
- run2.exe (PID: 2532)
- run2.exe (PID: 3048)
- run2.exe (PID: 580)
- run2.exe (PID: 2548)
- run2.exe (PID: 1332)
- run2.exe (PID: 924)
- run2.exe (PID: 3220)
- run2.exe (PID: 1364)
- run2.exe (PID: 704)
- run2.exe (PID: 3140)
- run2.exe (PID: 1544)
- run2.exe (PID: 2832)
- run2.exe (PID: 2632)
- run2.exe (PID: 2992)
- run2.exe (PID: 3572)
- run2.exe (PID: 1860)
- run2.exe (PID: 1392)
- run2.exe (PID: 1932)
- run2.exe (PID: 592)
- run2.exe (PID: 3372)
- run2.exe (PID: 3956)
- run2.exe (PID: 692)
- run2.exe (PID: 2876)
- run2.exe (PID: 3344)
- run2.exe (PID: 616)
- run2.exe (PID: 2624)
- run2.exe (PID: 632)
- run2.exe (PID: 3880)
- run2.exe (PID: 1720)
- run2.exe (PID: 3212)
- run2.exe (PID: 1020)
- run2.exe (PID: 3124)
- run2.exe (PID: 1524)
- run2.exe (PID: 1312)
- run2.exe (PID: 2732)
- run2.exe (PID: 3860)
- run2.exe (PID: 2716)
- run2.exe (PID: 3280)
- run2.exe (PID: 1488)
- run2.exe (PID: 2944)
- run2.exe (PID: 2100)
- run2.exe (PID: 4212)
- run2.exe (PID: 4380)
- run2.exe (PID: 4296)
- run2.exe (PID: 4464)
- run2.exe (PID: 4128)
- run2.exe (PID: 4716)
- run2.exe (PID: 4800)
- run2.exe (PID: 4636)
- run2.exe (PID: 4548)
- run2.exe (PID: 4884)
- run2.exe (PID: 4948)
- run2.exe (PID: 5052)
- run2.exe (PID: 5388)
- run2.exe (PID: 5308)
- run2.exe (PID: 5220)
- run2.exe (PID: 5476)
- run2.exe (PID: 5140)
- run2.exe (PID: 4104)
- run2.exe (PID: 5812)
- run2.exe (PID: 5624)
- run2.exe (PID: 5732)
- run2.exe (PID: 4196)
- run2.exe (PID: 5896)
- run2.exe (PID: 5960)
- run2.exe (PID: 6068)
- run2.exe (PID: 5560)
- run2.exe (PID: 4492)
- run2.exe (PID: 4588)
- run2.exe (PID: 4284)
- run2.exe (PID: 4688)
- run2.exe (PID: 4872)
- run2.exe (PID: 4756)
- run2.exe (PID: 5060)
- run2.exe (PID: 4976)
- run2.exe (PID: 5152)
- run2.exe (PID: 4400)
- run2.exe (PID: 5236)
- run2.exe (PID: 5524)
- run2.exe (PID: 5436)
- run2.exe (PID: 5344)
- run2.exe (PID: 5620)
- run2.exe (PID: 5720)
- run2.exe (PID: 5832)
- run2.exe (PID: 6028)
- run2.exe (PID: 5928)
- run2.exe (PID: 6128)
- run2.exe (PID: 4156)
- run2.exe (PID: 4304)
- run2.exe (PID: 4764)
- run2.exe (PID: 4396)
- run2.exe (PID: 4632)
- run2.exe (PID: 4852)
- run2.exe (PID: 4532)
- run2.exe (PID: 5780)
- run2.exe (PID: 5428)
- run2.exe (PID: 5332)
- run2.exe (PID: 5636)
- run2.exe (PID: 5552)
- run2.exe (PID: 6112)
- run2.exe (PID: 5228)
- run2.exe (PID: 5112)
- run2.exe (PID: 4992)
- run2.exe (PID: 5976)
- run2.exe (PID: 4352)
- run2.exe (PID: 4460)
- run2.exe (PID: 4564)
- run2.exe (PID: 4860)
- run2.exe (PID: 4932)
- run2.exe (PID: 4684)
- run2.exe (PID: 4192)
- run2.exe (PID: 5884)
- run2.exe (PID: 5488)
- run2.exe (PID: 5096)
- run2.exe (PID: 5300)
- run2.exe (PID: 5204)
- run2.exe (PID: 5984)
- run2.exe (PID: 5756)
- run2.exe (PID: 3536)
- run2.exe (PID: 5608)
- run2.exe (PID: 4624)
- run2.exe (PID: 4904)
- run2.exe (PID: 4504)
- run2.exe (PID: 5324)
- run2.exe (PID: 5184)
- run2.exe (PID: 5076)
- run2.exe (PID: 4312)
- run2.exe (PID: 6092)
- run2.exe (PID: 4220)
- run2.exe (PID: 5668)
- run2.exe (PID: 5500)
- run2.exe (PID: 6016)
- run2.exe (PID: 4136)
- run2.exe (PID: 4576)
- run2.exe (PID: 5784)
- run2.exe (PID: 5940)
- run2.exe (PID: 5408)
- run2.exe (PID: 4944)
- run2.exe (PID: 5232)
- run2.exe (PID: 5920)
- run2.exe (PID: 4428)
- run2.exe (PID: 4328)
- run2.exe (PID: 4784)
- run2.exe (PID: 5044)
- run2.exe (PID: 3380)
- run2.exe (PID: 1004)
- run2.exe (PID: 4276)
- run2.exe (PID: 4708)
- run2.exe (PID: 5700)
- run2.exe (PID: 5844)
- run2.exe (PID: 5516)
- run2.exe (PID: 3384)
- run2.exe (PID: 1868)
- run2.exe (PID: 3260)
- run2.exe (PID: 5640)
- run2.exe (PID: 6024)
- run2.exe (PID: 5864)
- run2.exe (PID: 2636)
- run2.exe (PID: 5304)
- run2.exe (PID: 5192)
- run2.exe (PID: 1612)
- run2.exe (PID: 4600)
- run2.exe (PID: 3648)
- run2.exe (PID: 3396)
- run2.exe (PID: 4480)
- run2.exe (PID: 5600)
- run2.exe (PID: 5892)
- run2.exe (PID: 2432)
- run2.exe (PID: 3808)
- run2.exe (PID: 2160)
- run2.exe (PID: 5328)
- run2.exe (PID: 2688)
- run2.exe (PID: 5000)
- run2.exe (PID: 4324)
- run2.exe (PID: 5176)
- run2.exe (PID: 5648)
- run2.exe (PID: 5268)
- run2.exe (PID: 5424)
- run2.exe (PID: 4544)
- run2.exe (PID: 5028)
- run2.exe (PID: 4604)
- run2.exe (PID: 1556)
- run2.exe (PID: 5320)
- run2.exe (PID: 4040)
- run2.exe (PID: 3284)
- run2.exe (PID: 5932)
- run2.exe (PID: 4776)
- run2.exe (PID: 5460)
- run2.exe (PID: 5004)
- run2.exe (PID: 3652)
- run2.exe (PID: 4140)
- run2.exe (PID: 4748)
- run2.exe (PID: 4424)
- run2.exe (PID: 2456)
- run2.exe (PID: 5944)
- run2.exe (PID: 4288)
- run2.exe (PID: 4100)
- run2.exe (PID: 5916)
- run2.exe (PID: 5704)
- run2.exe (PID: 5652)
- run2.exe (PID: 5504)
- run2.exe (PID: 4984)
- run2.exe (PID: 5248)
- run2.exe (PID: 5768)
- run2.exe (PID: 4540)
- run2.exe (PID: 4148)
- run2.exe (PID: 728)
- run2.exe (PID: 4116)
- run2.exe (PID: 2924)
- run2.exe (PID: 3532)
- run2.exe (PID: 4360)
- run2.exe (PID: 4208)
- run2.exe (PID: 6020)
- run2.exe (PID: 4560)
- run2.exe (PID: 5472)
- run2.exe (PID: 4936)
- run2.exe (PID: 5416)
- run2.exe (PID: 4248)
- run2.exe (PID: 1992)
- run2.exe (PID: 2800)
- run2.exe (PID: 2196)
- run2.exe (PID: 5880)
- run2.exe (PID: 5664)
- run2.exe (PID: 4440)
- run2.exe (PID: 4280)
- run2.exe (PID: 4676)
- run2.exe (PID: 3876)
- run2.exe (PID: 5008)
- run2.exe (PID: 5280)
- run2.exe (PID: 5196)
- run2.exe (PID: 5904)
- run2.exe (PID: 4240)
- run2.exe (PID: 4112)
- run2.exe (PID: 5576)
- run2.exe (PID: 2476)
- run2.exe (PID: 4972)
- run2.exe (PID: 4316)
- run2.exe (PID: 4680)
- run2.exe (PID: 5292)
- run2.exe (PID: 4272)
- run2.exe (PID: 6084)
- run2.exe (PID: 5180)
- run2.exe (PID: 5796)
- run2.exe (PID: 5824)
- run2.exe (PID: 5936)
- run2.exe (PID: 1952)
- run2.exe (PID: 4572)
- run2.exe (PID: 5996)
- run2.exe (PID: 4568)
- run2.exe (PID: 2144)
- run2.exe (PID: 5680)
- run2.exe (PID: 5484)
- run2.exe (PID: 4392)
- run2.exe (PID: 4256)
- run2.exe (PID: 4812)
- run2.exe (PID: 4476)
- run2.exe (PID: 4168)
- run2.exe (PID: 5548)
- run2.exe (PID: 5512)
- run2.exe (PID: 5084)
- run2.exe (PID: 4320)
- run2.exe (PID: 5908)
- run2.exe (PID: 2588)
- run2.exe (PID: 4780)
- run2.exe (PID: 5400)
- run2.exe (PID: 5540)
- run2.exe (PID: 5272)
- run2.exe (PID: 5532)
- run2.exe (PID: 5020)
- run2.exe (PID: 5464)
- run2.exe (PID: 2756)
- run2.exe (PID: 3400)
- run2.exe (PID: 6036)
- run2.exe (PID: 4200)
- run2.exe (PID: 4448)
- run2.exe (PID: 3460)
- run2.exe (PID: 4228)
- run2.exe (PID: 4444)
- run2.exe (PID: 5208)
- run2.exe (PID: 5040)
- run2.exe (PID: 6324)
- run2.exe (PID: 6408)
- run2.exe (PID: 6156)
- run2.exe (PID: 6232)
- run2.exe (PID: 5444)
- run2.exe (PID: 4740)
- run2.exe (PID: 4792)
- run2.exe (PID: 7168)
- run2.exe (PID: 7084)
- run2.exe (PID: 6896)
- run2.exe (PID: 6556)
- run2.exe (PID: 6748)
- run2.exe (PID: 6492)
- run2.exe (PID: 6660)
- run2.exe (PID: 6832)
- run2.exe (PID: 7000)
- run2.exe (PID: 7504)
- run2.exe (PID: 7420)
- run2.exe (PID: 7756)
- run2.exe (PID: 7844)
- run2.exe (PID: 7928)
- run2.exe (PID: 7676)
- run2.exe (PID: 7592)
- run2.exe (PID: 7336)
- run2.exe (PID: 7252)
- run2.exe (PID: 6200)
- run2.exe (PID: 8092)
- run2.exe (PID: 6304)
- run2.exe (PID: 8008)
- run2.exe (PID: 6588)
- run2.exe (PID: 8176)
- run2.exe (PID: 6772)
- run2.exe (PID: 6848)
- run2.exe (PID: 7056)
- run2.exe (PID: 6948)
- run2.exe (PID: 7144)
- run2.exe (PID: 6672)
- run2.exe (PID: 6488)
- run2.exe (PID: 6376)
- run2.exe (PID: 7584)
- run2.exe (PID: 7528)
- run2.exe (PID: 7796)
- run2.exe (PID: 8072)
- run2.exe (PID: 7428)
- run2.exe (PID: 7324)
- run2.exe (PID: 7232)
- run2.exe (PID: 7700)
- run2.exe (PID: 6300)
- run2.exe (PID: 8140)
- run2.exe (PID: 6480)
- run2.exe (PID: 6584)
- run2.exe (PID: 6388)
- run2.exe (PID: 7900)
- run2.exe (PID: 7964)
- run2.exe (PID: 5440)
- run2.exe (PID: 6884)
- run2.exe (PID: 6980)
- run2.exe (PID: 7268)
- run2.exe (PID: 7228)
- run2.exe (PID: 6700)
- run2.exe (PID: 6788)
- run2.exe (PID: 7124)
- run2.exe (PID: 7956)
- run2.exe (PID: 5124)
- run2.exe (PID: 7840)
- run2.exe (PID: 7716)
- run2.exe (PID: 7548)
- run2.exe (PID: 7416)
- run2.exe (PID: 6696)
- run2.exe (PID: 6420)
- run2.exe (PID: 6564)
- run2.exe (PID: 6904)
- run2.exe (PID: 8132)
- run2.exe (PID: 6208)
- run2.exe (PID: 6312)
- run2.exe (PID: 8048)
- run2.exe (PID: 7020)
- run2.exe (PID: 7344)
- run2.exe (PID: 7452)
- run2.exe (PID: 7824)
- run2.exe (PID: 4416)
- run2.exe (PID: 7656)
- run2.exe (PID: 6760)
- run2.exe (PID: 4628)
- run2.exe (PID: 7200)
- run2.exe (PID: 7924)
- run2.exe (PID: 8128)
- run2.exe (PID: 6372)
- run2.exe (PID: 6456)
- run2.exe (PID: 4556)
- run2.exe (PID: 6576)
- run2.exe (PID: 6196)
- run2.exe (PID: 8024)
- run2.exe (PID: 7364)
- run2.exe (PID: 6956)
- run2.exe (PID: 5764)
- run2.exe (PID: 7448)
- run2.exe (PID: 3204)
- run2.exe (PID: 7108)
- run2.exe (PID: 4520)
- run2.exe (PID: 6512)
- run2.exe (PID: 6620)
- run2.exe (PID: 6244)
- run2.exe (PID: 6364)
- run2.exe (PID: 7684)
- run2.exe (PID: 7612)
- run2.exe (PID: 8016)
- run2.exe (PID: 4160)
- run2.exe (PID: 4584)
- run2.exe (PID: 7196)
- run2.exe (PID: 6820)
- run2.exe (PID: 7320)
- run2.exe (PID: 7480)
- run2.exe (PID: 7764)
- run2.exe (PID: 6796)
- run2.exe (PID: 7048)
- run2.exe (PID: 8064)
- run2.exe (PID: 6652)
- run2.exe (PID: 6332)
- run2.exe (PID: 5364)
- run2.exe (PID: 5852)
- run2.exe (PID: 5972)
- run2.exe (PID: 7856)
- run2.exe (PID: 5012)
- run2.exe (PID: 4900)
- run2.exe (PID: 7292)
- run2.exe (PID: 4880)
Changes settings of System certificates
- pzyh.exe (PID: 2284)
- 6961670.exe (PID: 2360)
- RocketVPN.tmp (PID: 3992)
Runs injected code in another process
- svchost.exe (PID: 880)
- rUNdlL32.eXe (PID: 3324)
Application was injected by another process
- svchost.exe (PID: 3088)
- svchost.exe (PID: 880)
Connects to CnC server
- pzyh.exe (PID: 2284)
REDLINE was detected
- 6717481.exe (PID: 1856)
Stealing of credential data
- 6717481.exe (PID: 1856)
- run.exe (PID: 2472)
Steals credentials from Web Browsers
- 6717481.exe (PID: 1856)
- run.exe (PID: 2472)
- 6961670.exe (PID: 2360)
- svchost.exe (PID: 3088)
Actions looks like stealing of personal data
- 6717481.exe (PID: 1856)
- run.exe (PID: 2472)
- 6961670.exe (PID: 2360)
- svchost.exe (PID: 3088)
VIDAR was detected
- run.exe (PID: 2472)
SUSPICIOUS
Executable content was dropped or overwritten
- Files.exe (PID: 2416)
- Folder.exe (PID: 3596)
- Microsoft_Toolkit.exe (PID: 2152)
- Install.exe (PID: 1852)
- pzyh.exe (PID: 2284)
- pub2.exe (PID: 2564)
- RocketVPN.exe (PID: 3316)
- KRSetp.exe (PID: 3888)
- 1448142.exe (PID: 1424)
- File.exe (PID: 3548)
- 6961670.exe (PID: 2360)
- RocketVPN.exe (PID: 2764)
- run.exe (PID: 2472)
- RocketVPN.tmp (PID: 3992)
Drops a file with a compile date too recent
- Microsoft_Toolkit.exe (PID: 2152)
- Files.exe (PID: 2416)
- Folder.exe (PID: 3596)
- Install.exe (PID: 1852)
- pzyh.exe (PID: 2284)
- RocketVPN.exe (PID: 3316)
- KRSetp.exe (PID: 3888)
- 1448142.exe (PID: 1424)
- File.exe (PID: 3548)
- RocketVPN.exe (PID: 2764)
- RocketVPN.tmp (PID: 3992)
Drops a file that was compiled in debug mode
- Microsoft_Toolkit.exe (PID: 2152)
- pzyh.exe (PID: 2284)
- pub2.exe (PID: 2564)
- File.exe (PID: 3548)
- 6961670.exe (PID: 2360)
- run.exe (PID: 2472)
- RocketVPN.tmp (PID: 3992)
Executed via COM
- iexplore.exe (PID: 2312)
Application launched itself
- pzyh.exe (PID: 3000)
- 4850656.exe (PID: 3092)
- run2.exe (PID: 2116)
Reads the cookies of Google Chrome
- jfiag3g_gg.exe (PID: 3316)
- run.exe (PID: 2472)
- 6961670.exe (PID: 2360)
- 6717481.exe (PID: 1856)
- svchost.exe (PID: 3088)
Checks for external IP
- pzyh.exe (PID: 2284)
- svchost.exe (PID: 3088)
Creates files in the user directory
- KRSetp.exe (PID: 3888)
- 1448142.exe (PID: 1424)
- svchost.exe (PID: 3088)
Adds / modifies Windows certificates
- pzyh.exe (PID: 2284)
- 6961670.exe (PID: 2360)
- RocketVPN.tmp (PID: 3992)
Drops a file with too old compile date
- KRSetp.exe (PID: 3888)
Reads the Windows organization settings
- RocketVPN.tmp (PID: 3992)
Creates files in the program directory
- 6961670.exe (PID: 2360)
- run.exe (PID: 2472)
Starts itself from another location
- 1448142.exe (PID: 1424)
Uses RUNDLL32.EXE to load library
- Folder.exe (PID: 3596)
Reads Windows owner or organization settings
- RocketVPN.tmp (PID: 3992)
Searches for installed software
- RocketVPN.tmp (PID: 3992)
- run.exe (PID: 2472)
- 6717481.exe (PID: 1856)
- 6961670.exe (PID: 2360)
Reads Environment values
- 6717481.exe (PID: 1856)
Low-level read access rights to disk partition
- svchost.exe (PID: 3088)
Reads the cookies of Mozilla Firefox
- 6717481.exe (PID: 1856)
- run.exe (PID: 2472)
- 6961670.exe (PID: 2360)
- svchost.exe (PID: 3088)
INFO
Application launched itself
- chrome.exe (PID: 676)
- iexplore.exe (PID: 2312)
Reads the hosts file
- chrome.exe (PID: 676)
- chrome.exe (PID: 3856)
Manual execution by user
- Microsoft_Toolkit.exe (PID: 2152)
- NOTEPAD.EXE (PID: 2748)
Changes internet zones settings
- iexplore.exe (PID: 2312)
Loads dropped or rewritten executable
- RocketVPN.tmp (PID: 3132)
- RocketVPN.tmp (PID: 3992)
Application was dropped or rewritten from another process
- RocketVPN.tmp (PID: 3132)
- RocketVPN.tmp (PID: 3992)
Reads settings of System Certificates
- iexplore.exe (PID: 3020)
- KRSetp.exe (PID: 3888)
- iexplore.exe (PID: 2248)
- iexplore.exe (PID: 2312)
Dropped object may contain Bitcoin addresses
- KRSetp.exe (PID: 3888)
Creates files in the user directory
- iexplore.exe (PID: 3020)
Reads internet explorer settings
- iexplore.exe (PID: 2248)
- iexplore.exe (PID: 3020)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
1 036
Monitored processes
1 005
Malicious processes
461
Suspicious processes
13
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | C:\Users\Public\run2.exe | C:\Users\Public\run2.exe | — | run2.exe | |||||||||||
User: admin Company: CRFML Corporation. Integrity Level: MEDIUM Description: Fish Delegates Exit code: 0 Version: 18.578.803.851 Modules
| |||||||||||||||
| 184 | C:\Users\Public\run2.exe | C:\Users\Public\run2.exe | — | run2.exe | |||||||||||
User: admin Company: CRFML Corporation. Integrity Level: MEDIUM Description: Fish Delegates Exit code: 0 Version: 18.578.803.851 Modules
| |||||||||||||||
| 308 | C:\Windows\system32\DllHost.exe /Processid:{E10F6C3A-F1AE-4ADC-AA9D-2FE65525666E} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 556 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=996,2513750469053627109,8342221524222317460,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=6382836279422913104 --mojo-platform-channel-handle=3640 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 556 | C:\Users\Public\run2.exe | C:\Users\Public\run2.exe | — | run2.exe | |||||||||||
User: admin Company: CRFML Corporation. Integrity Level: MEDIUM Description: Fish Delegates Exit code: 0 Version: 18.578.803.851 Modules
| |||||||||||||||
| 580 | C:\Users\Public\run2.exe | C:\Users\Public\run2.exe | — | run2.exe | |||||||||||
User: admin Company: CRFML Corporation. Integrity Level: MEDIUM Description: Fish Delegates Exit code: 0 Version: 18.578.803.851 Modules
| |||||||||||||||
| 584 | \??\C:\Windows\system32\conhost.exe "-183231972214118444879589243361847035351846698759106565233512872354551871531122" | C:\Windows\system32\conhost.exe | — | csrss.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 592 | C:\Users\Public\run2.exe | C:\Users\Public\run2.exe | — | run2.exe | |||||||||||
User: admin Company: CRFML Corporation. Integrity Level: MEDIUM Description: Fish Delegates Exit code: 0 Version: 18.578.803.851 Modules
| |||||||||||||||
| 616 | C:\Users\Public\run2.exe | C:\Users\Public\run2.exe | — | run2.exe | |||||||||||
User: admin Company: CRFML Corporation. Integrity Level: MEDIUM Description: Fish Delegates Exit code: 0 Version: 18.578.803.851 Modules
| |||||||||||||||
| 632 | C:\Users\Public\run2.exe | C:\Users\Public\run2.exe | — | run2.exe | |||||||||||
User: admin Company: CRFML Corporation. Integrity Level: MEDIUM Description: Fish Delegates Exit code: 0 Version: 18.578.803.851 Modules
| |||||||||||||||
Total events
7 433
Read events
6 805
Write events
624
Delete events
4
Modification events
| (PID) Process: | (676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1896) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 676-13269223536944000 |
Value: 259 | |||
| (PID) Process: | (676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3252-13245750958665039 |
Value: 0 | |||
| (PID) Process: | (676) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
45
Suspicious files
89
Text files
131
Unknown types
40
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-60D7B771-2A4.pma | — | |
MD5:— | SHA256:— | |||
| 676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\099e3917-155e-4a0b-8958-34b769e6ee30.tmp | — | |
MD5:— | SHA256:— | |||
| 676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\CURRENT | — | |
MD5:— | SHA256:— | |||
| 676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF18a0cf.TMP | text | |
MD5:— | SHA256:— | |||
| 676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF18a311.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
74
DNS requests
49
Threats
64
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2284 | pzyh.exe | GET | — | 88.218.92.148:80 | http://uehge4g6gh.2ihsfa.com/api/fbtime | ES | — | — | malicious |
3856 | chrome.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAx5qUSwjBGVIJJhX%2BJrHYM%3D | US | der | 471 b | whitelisted |
3020 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
3020 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
2284 | pzyh.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | text | 296 b | malicious |
3020 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
3548 | File.exe | GET | 200 | 92.53.96.150:80 | http://newja.webtm.ru/james2.zip | RU | compressed | 1006 Kb | whitelisted |
3020 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEGmjTouN%2FW5s3CDseaiw7qE%3D | US | der | 471 b | whitelisted |
3020 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEGmjTouN%2FW5s3CDseaiw7qE%3D | US | der | 471 b | whitelisted |
3020 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3856 | chrome.exe | 172.67.157.161:443 | freemicrosofttoolkit.com | — | US | suspicious |
3856 | chrome.exe | 142.250.186.77:443 | accounts.google.com | Google Inc. | US | suspicious |
3856 | chrome.exe | 142.250.181.234:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3856 | chrome.exe | 192.0.77.2:443 | i2.wp.com | Automattic, Inc | US | suspicious |
3856 | chrome.exe | 142.250.185.195:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3856 | chrome.exe | 192.0.73.2:443 | secure.gravatar.com | Automattic, Inc | US | whitelisted |
3856 | chrome.exe | 142.250.186.74:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3856 | chrome.exe | 192.0.77.32:443 | s0.wp.com | Automattic, Inc | US | suspicious |
3856 | chrome.exe | 192.0.76.3:443 | stats.wp.com | Automattic, Inc | US | suspicious |
3856 | chrome.exe | 142.250.185.174:443 | translate.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
freemicrosofttoolkit.com |
| suspicious |
accounts.google.com |
| shared |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
i2.wp.com |
| whitelisted |
i1.wp.com |
| whitelisted |
s0.wp.com |
| whitelisted |
s.w.org |
| whitelisted |
secure.gravatar.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2284 | pzyh.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
2284 | pzyh.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
3548 | File.exe | Potential Corporate Privacy Violation | ET POLICY Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
3548 | File.exe | A Network Trojan was detected | ET INFO AutoIt User-Agent Downloading ZIP |
1856 | 6717481.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
2472 | run.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host DLL Request |
2472 | run.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .dll file with no User-Agent |
2472 | run.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2472 | run.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host DLL Request |
2472 | run.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .dll file with no User-Agent |
25 ETPRO signatures available at the full report