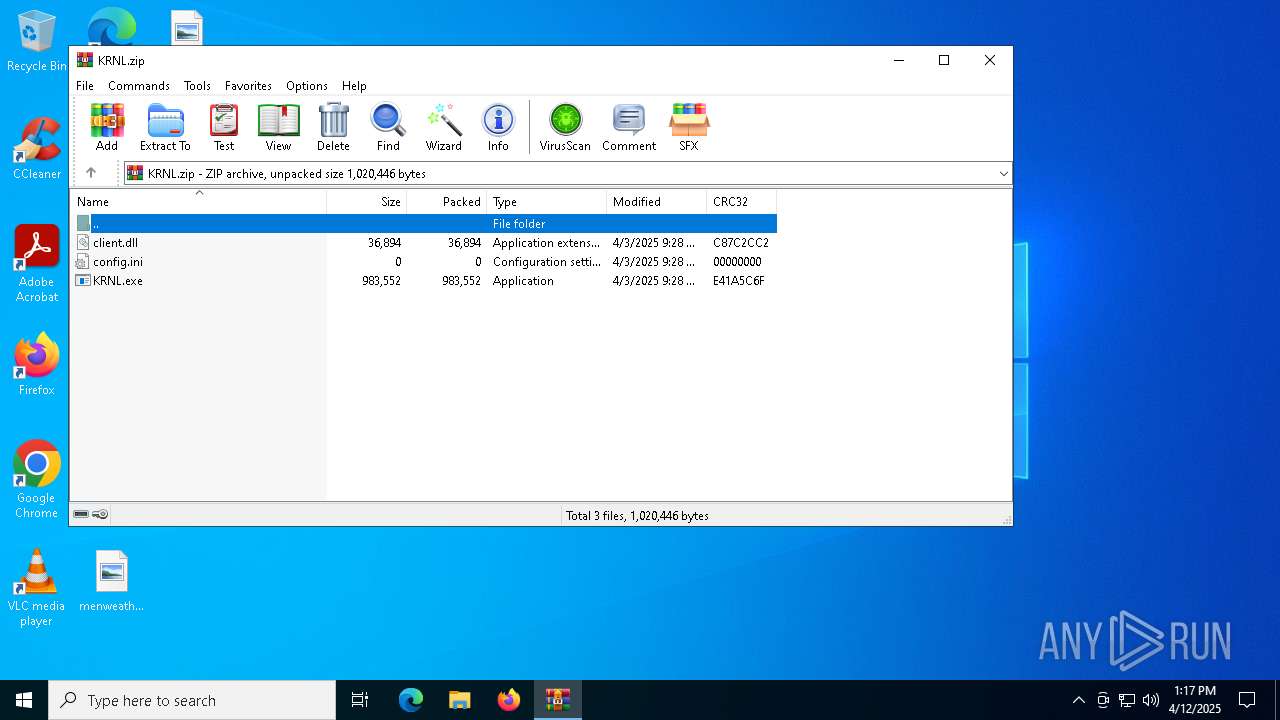
| File name: | KRNL.zip |
| Full analysis: | https://app.any.run/tasks/d70c01b8-8c05-46a4-9550-a206846cc086 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | April 12, 2025, 13:17:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 2D667E20FFCE65F33ADC38ED4AE19944 |
| SHA1: | 5A908A19ED3762947E24BD08BDB9C03127239E4C |
| SHA256: | FEA6F4165BED389421598BF2CFAED3E31976F6EF119C21DF17E73956B8A7C4C4 |
| SSDEEP: | 49152:D7NRL7gjR7qNOK2RXvNviSNchJ9RHiLpJ5PboXOxOM7Zqf+SC37o77hsuATR9m1N:FRL7gJqNOK2RXvNviSNchJ9RHiT5PboX |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2236)
Stealers network behavior
- svchost.exe (PID: 2196)
Connects to the CnC server
- svchost.exe (PID: 2196)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
SUSPICIOUS
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2196)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 2236)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2236)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 2236)
INFO
Reads the computer name
- MSBuild.exe (PID: 6048)
- MpCmdRun.exe (PID: 2096)
Reads the machine GUID from the registry
- MSBuild.exe (PID: 6048)
Checks supported languages
- MSBuild.exe (PID: 6048)
- KRNL.exe (PID: 5956)
- MpCmdRun.exe (PID: 2096)
Reads the software policy settings
- MSBuild.exe (PID: 6048)
- slui.exe (PID: 864)
Manual execution by a user
- KRNL.exe (PID: 5956)
Create files in a temporary directory
- MpCmdRun.exe (PID: 2096)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2236)
Checks proxy server information
- slui.exe (PID: 864)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:04:03 21:28:24 |
| ZipCRC: | 0xc87c2cc2 |
| ZipCompressedSize: | 36894 |
| ZipUncompressedSize: | 36894 |
| ZipFileName: | client.dll |
Total processes
129
Monitored processes
11
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 864 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2096 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR2236.28506" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\KRNL.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3884 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4988 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR2236.28506\Rar$Scan97576.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5408 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | — | KRNL.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 5956 | "C:\Users\admin\Desktop\KRNL.exe" | C:\Users\admin\Desktop\KRNL.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6028 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | — | KRNL.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 6048 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | KRNL.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
Total events
8 240
Read events
8 229
Write events
11
Delete events
0
Modification events
| (PID) Process: | (2236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\KRNL.zip | |||
| (PID) Process: | (2236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
| (PID) Process: | (2236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 0 | |||
Executable files
1
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2236 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR2236.28506\KRNL.zip\KRNL.exe | executable | |
MD5:92C11D2892CC8901077AFC2DEEAC4593 | SHA256:031E9AAEAF348EC4A0F5F8733A0925AA04D6640CA2441A63DD3C2C2BE26F21FD | |||
| 2096 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | binary | |
MD5:48DB8ECA027C99F01213EB2324736DD2 | SHA256:8371CDFB505DA5B3A138C9E501E6770F3774F62096CB8EE6BAAEBA93AB0B2D9C | |||
| 2236 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR2236.28506\Rar$Scan97576.bat | text | |
MD5:35049DB87C06E7D511C955D1D4CB3850 | SHA256:86937D6A05770694AD110F06C81C6CF8642A673CAD3ED936FFDE167C9C590F60 | |||
| 2236 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR2236.28506\KRNL.zip\client.dll | text | |
MD5:702348A3919A13F056AB52A8085C5B5B | SHA256:8C5F289D8817F1FF725DCCA44B93A0A9BEBDBB933750EBE81E91C33C561C875C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
23
DNS requests
14
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.197.130.99:443 | https://steamcommunity.com/profiles/76561199822375128 | unknown | html | 25.6 Kb | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | GET | 200 | 23.197.130.99:443 | https://steamcommunity.com/profiles/76561199822375128 | unknown | html | 25.6 Kb | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6048 | MSBuild.exe | 23.197.130.99:443 | steamcommunity.com | Akamai International B.V. | US | whitelisted |
5868 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
864 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
rlxspoty.run |
| malicious |
jrxsafer.top |
| malicious |
krxspint.digital |
| malicious |
rhxhube.run |
| malicious |
grxeasyw.digital |
| malicious |
advennture.top |
| malicious |
targett.top |
| unknown |
xrfxcaseq.live |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | A Network Trojan was detected | STEALER [ANY.RUN] Domain has been identified as part of Lumma Stealer's infrastructure (rhxhube .run) |
2196 | svchost.exe | A Network Trojan was detected | STEALER [ANY.RUN] Domain has been identified as part of Lumma Stealer's infrastructure (krxspint .digital) |
2196 | svchost.exe | A Network Trojan was detected | STEALER [ANY.RUN] Domain has been identified as part of Lumma Stealer's infrastructure (jrxsafer .top) |
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (rhxhube .run) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (krxspint .digital) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (jrxsafer .top) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (rlxspoty .run) |
2196 | svchost.exe | A Network Trojan was detected | STEALER [ANY.RUN] Domain has been identified as part of Lumma Stealer's infrastructure (xrfxcaseq .live) |
2196 | svchost.exe | A Network Trojan was detected | STEALER [ANY.RUN] Domain has been identified as part of Lumma Stealer's infrastructure (advennture .top) |