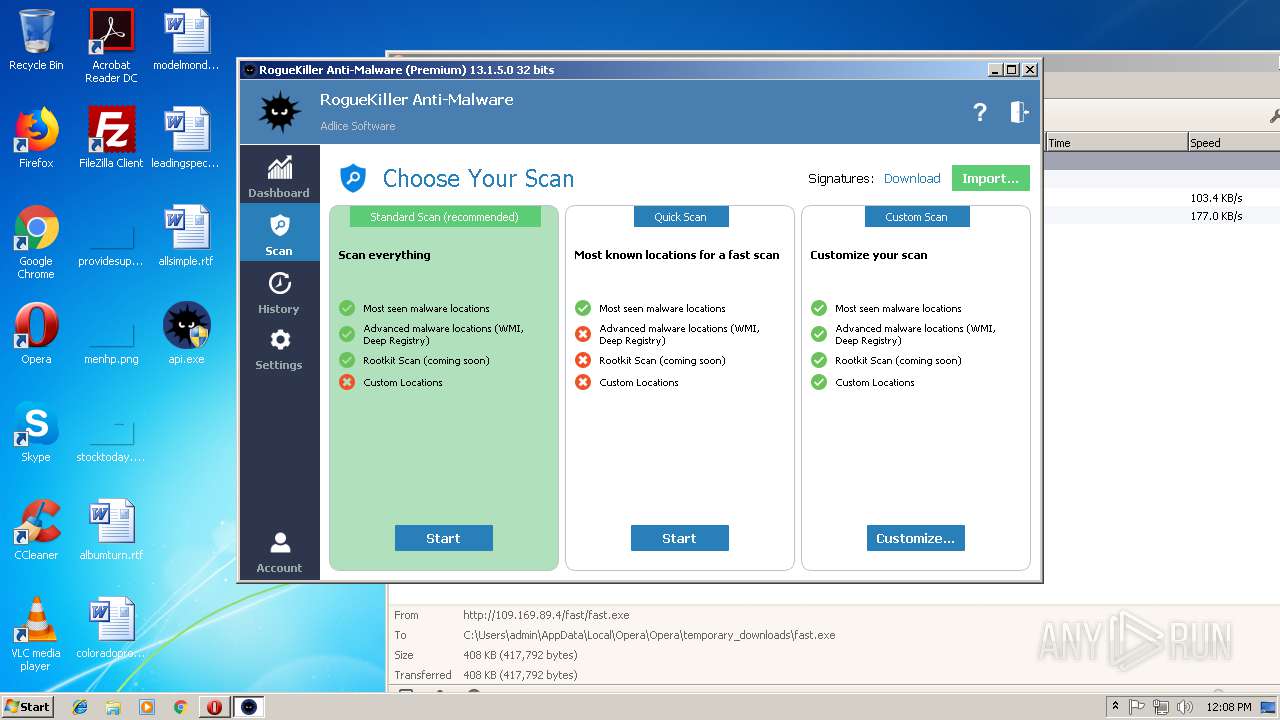
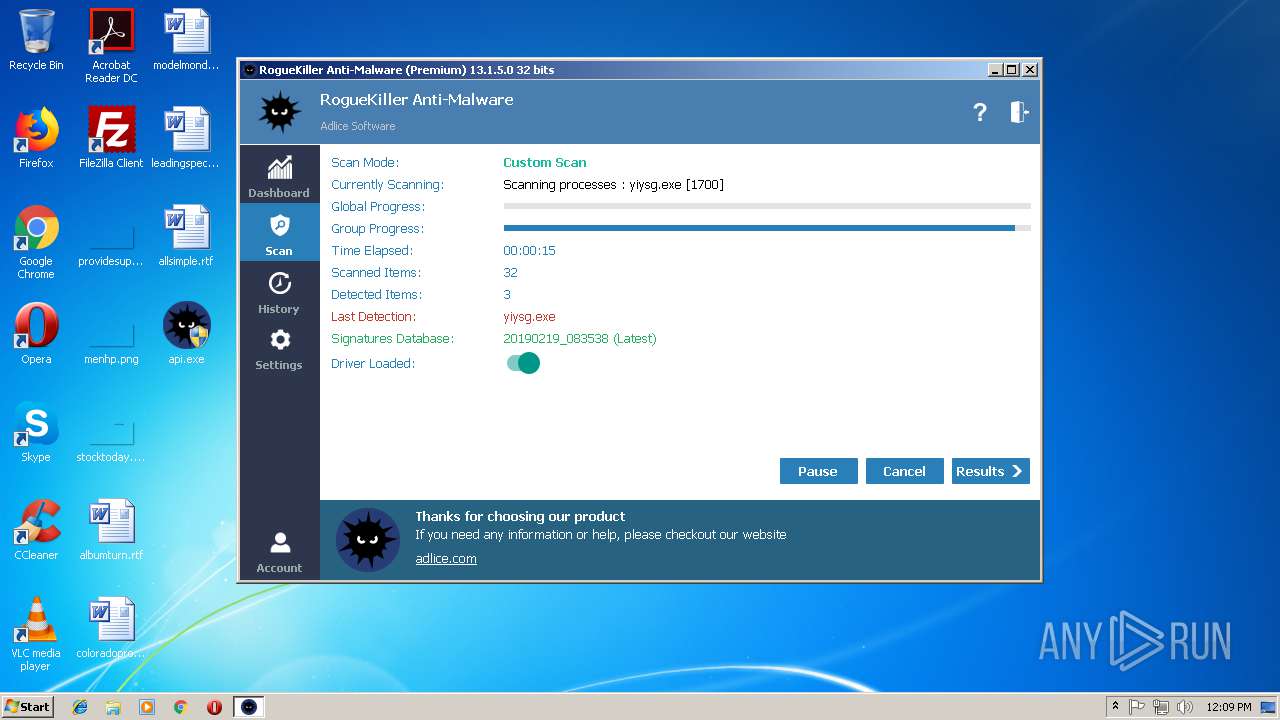
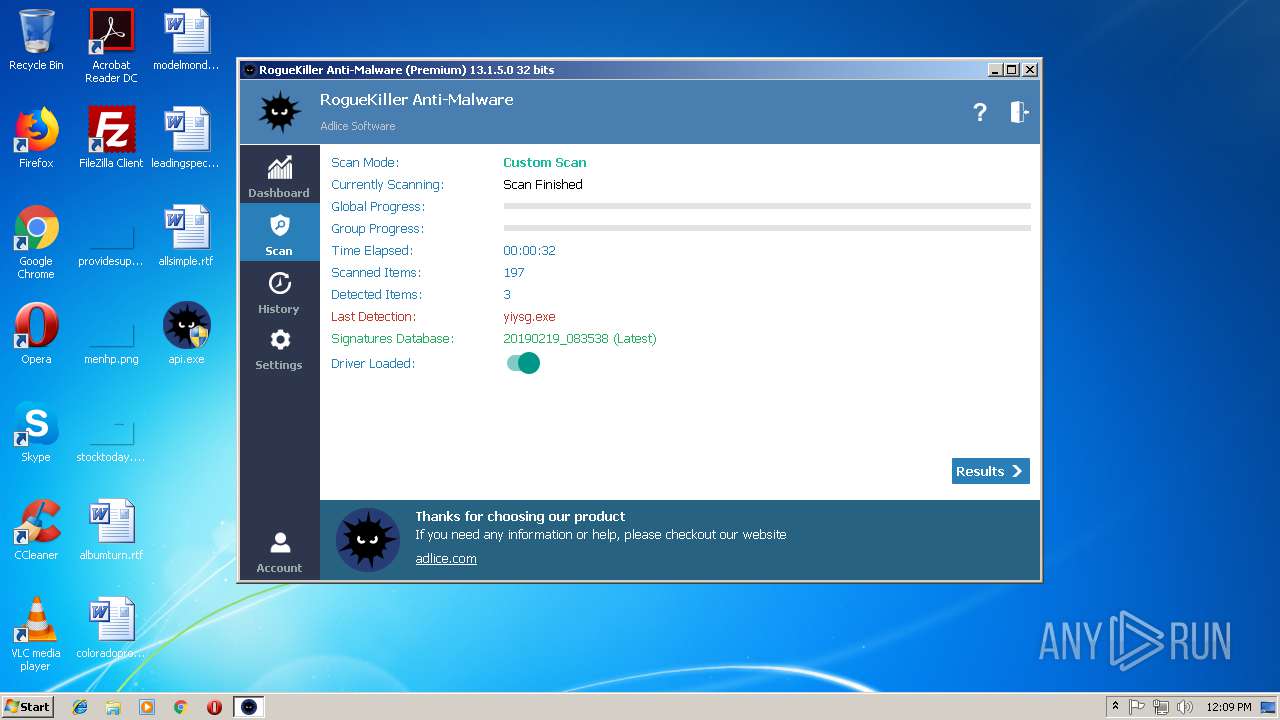
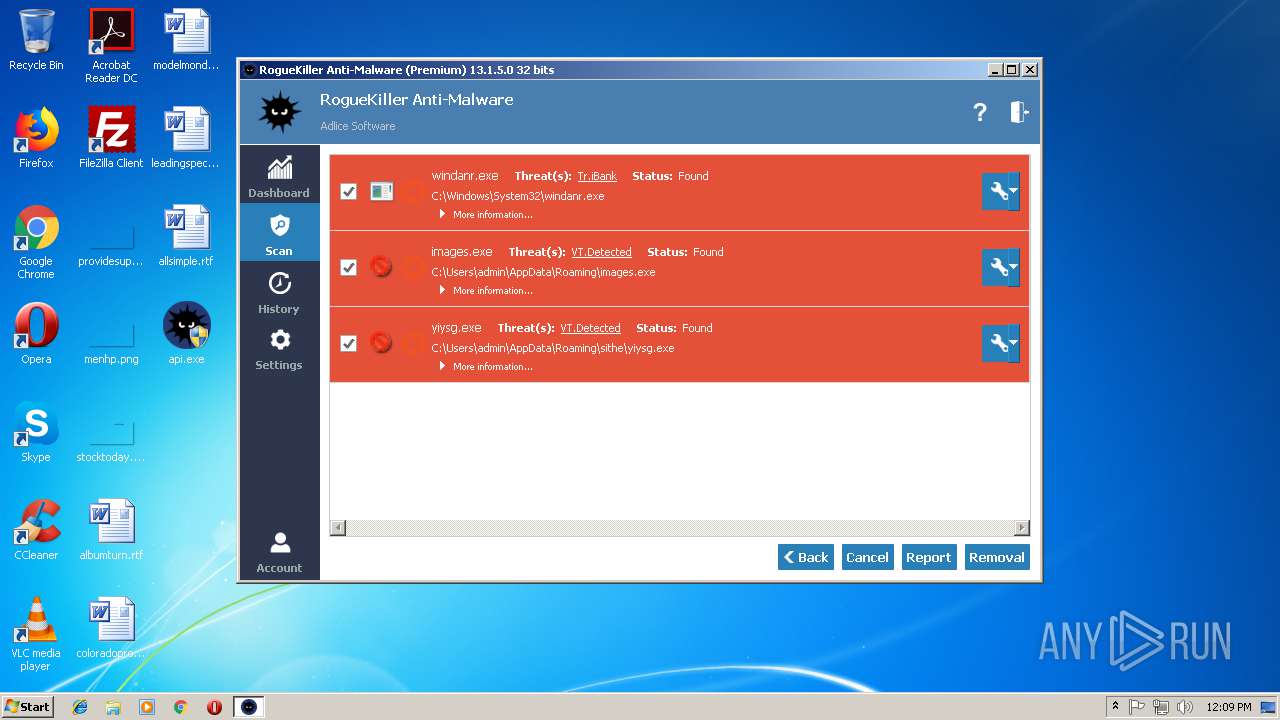
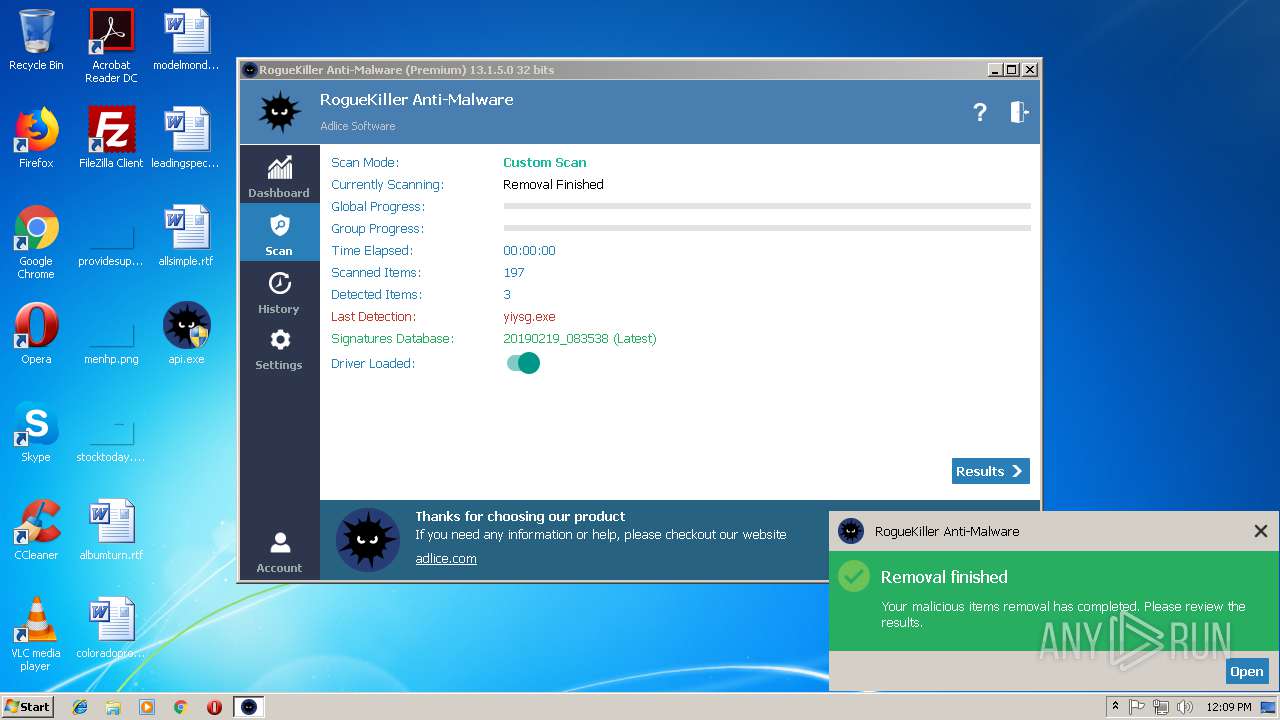
| File name: | api |
| Full analysis: | https://app.any.run/tasks/9b5d32dd-b6db-48d7-9d6f-179ae11cdbc8 |
| Verdict: | Malicious activity |
| Threats: | WarZone RAT is a remote access trojan, which is written in C++ and offered as a malware-as-a-service. It packs a wide range of capabilities, from stealing victims’ files and passwords to capturing desktop activities. WarZone RAT is primarily distributed via phishing emails and receives regular updates from its C2. |
| Analysis date: | February 19, 2019, 12:04:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 6609998C66B9B6DF12F31010EB814436 |
| SHA1: | 328DB637D2D5EE552B9EBF509443E93741B538B7 |
| SHA256: | FDE2C7E81D55D3037062BA6940792C1012F3B837880ECFBCEAE61A7DD4D6517F |
| SSDEEP: | 393216:a7A4NqkGYO1Khx4qCwEz2HrGu0OJsv6tWKFdu9CFWE12L8uk:+hNtOYhx4qClqHrGS2L8R |
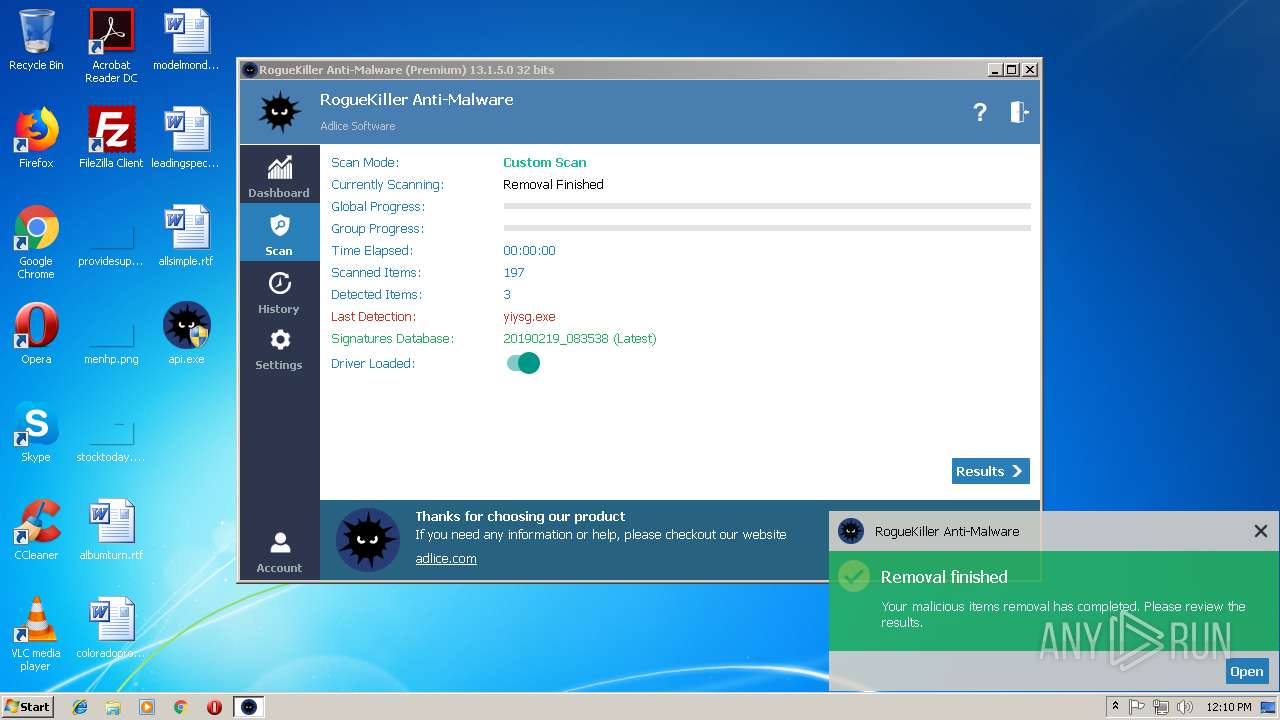
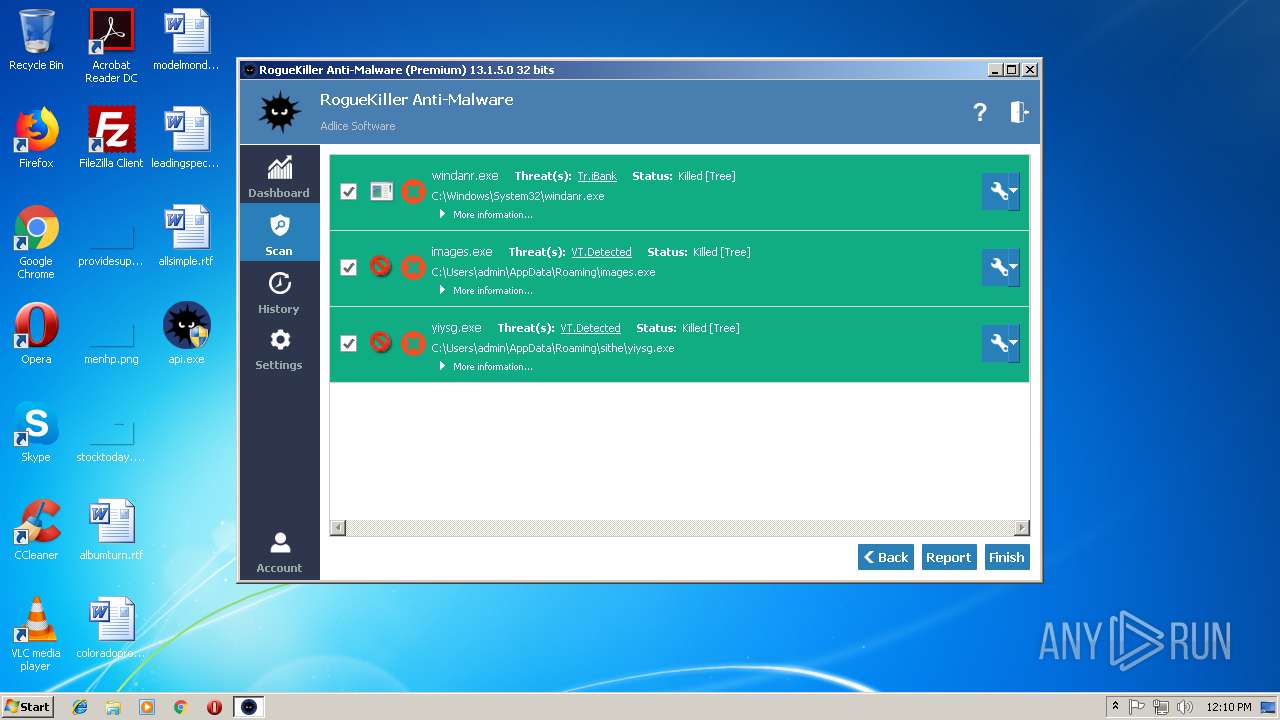
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:02:18 08:36:38+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 16304640 |
| InitializedDataSize: | 10856960 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xce35c4 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 13.1.5.0 |
| ProductVersionNumber: | 13.1.5.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
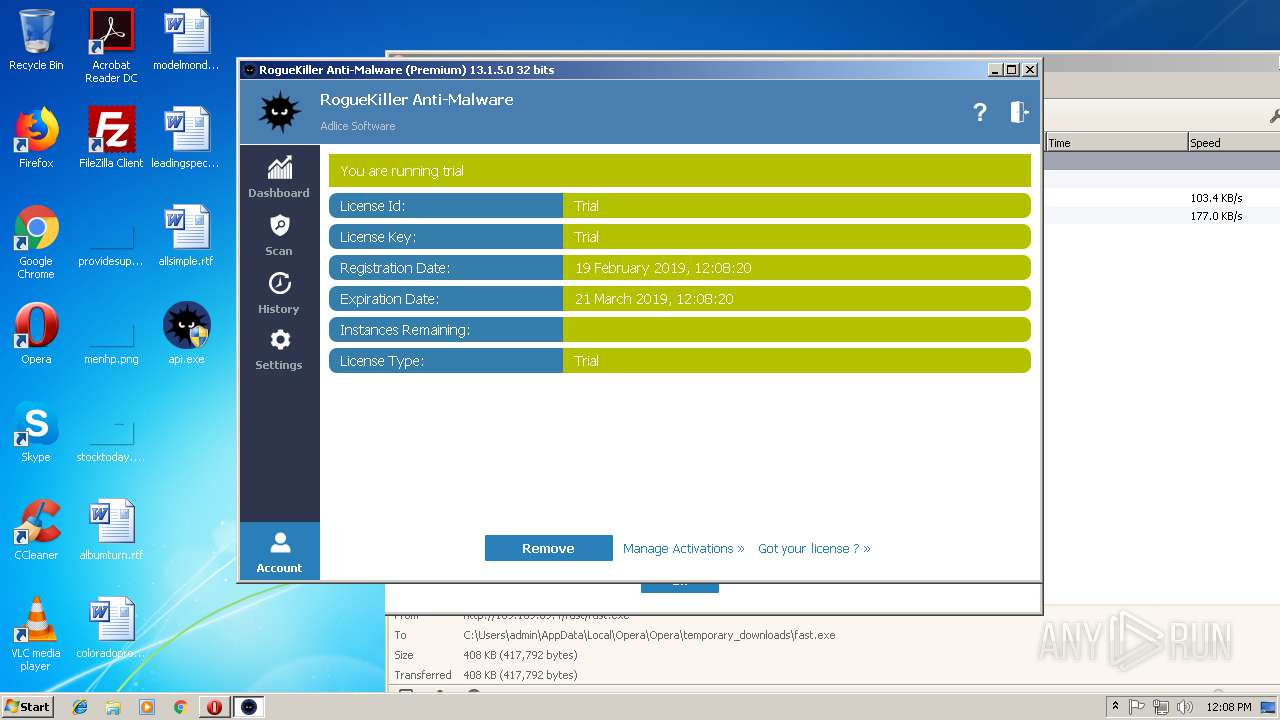
| CompanyName: | Adlice Software |
| FileDescription: | Anti-Malware Scan and Removal |
| FileVersion: | 13.1.5.0 |
| InternalName: | RogueKiller Anti-Malware |
| LegalCopyright: | Copyright Adlice Software(C) 2018 |
| LegalTrademarks1: | Adlice Software |
| LegalTrademarks2: | Adlice Software |
| OriginalFileName: | RogueKiller Anti-Malware |
| ProductName: | RogueKiller Anti-Malware |
| ProductVersion: | 13.1.5.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 18-Feb-2019 07:36:38 |
| Detected languages: |
|
| Debug artifacts: |
|
| CompanyName: | Adlice Software |
| FileDescription: | Anti-Malware Scan and Removal |
| FileVersion: | 13.1.5.0 |
| InternalName: | RogueKiller Anti-Malware |
| LegalCopyright: | Copyright Adlice Software(C) 2018 |
| LegalTrademarks1: | Adlice Software |
| LegalTrademarks2: | Adlice Software |
| OriginalFilename: | RogueKiller Anti-Malware |
| ProductName: | RogueKiller Anti-Malware |
| ProductVersion: | 13.1.5.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000150 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 9 |
| Time date stamp: | 18-Feb-2019 07:36:38 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00F8C9DE | 0x00F8CA00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.60151 |
.rdata | 0x00F8E000 | 0x004A8B82 | 0x004A8C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.29987 |
.data | 0x01437000 | 0x0004B2A0 | 0x0002C000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.76392 |
.tls | 0x01483000 | 0x0000000D | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.0203931 |
.qtmetadL\x02 | 0x01484000 | 0x0000024C | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 3.15593 |
.gfids | 0x01485000 | 0x000007CC | 0x00000800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.1122 |
_RDATA | 0x01486000 | 0x00000124 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.51793 |
.rsrc | 0x01487000 | 0x004C01C8 | 0x004C0200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.8823 |
.reloc | 0x01948000 | 0x000A5614 | 0x000A5800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.64787 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.21878 | 667 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 3.08492 | 296 | UNKNOWN | English - United States | RT_ICON |
3 | 4.32673 | 3752 | UNKNOWN | English - United States | RT_ICON |
4 | 4.69 | 2216 | UNKNOWN | English - United States | RT_ICON |
5 | 4.96085 | 1384 | UNKNOWN | English - United States | RT_ICON |
6 | 7.96471 | 21897 | UNKNOWN | English - United States | RT_ICON |
7 | 3.53747 | 16936 | UNKNOWN | English - United States | RT_ICON |
8 | 3.87766 | 9640 | UNKNOWN | English - United States | RT_ICON |
9 | 4.07378 | 6760 | UNKNOWN | English - United States | RT_ICON |
10 | 4.36584 | 4264 | UNKNOWN | English - United States | RT_ICON |
Imports
ADVAPI32.dll |
CRYPT32.dll |
GDI32.dll |
IMM32.dll |
IPHLPAPI.DLL |
KERNEL32.dll |
MPR.dll |
OLEAUT32.dll |
OPENGL32.dll |
PSAPI.DLL |
Total processes
0
Monitored processes
0
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
124
TCP/UDP connections
255
DNS requests
86
Threats
59
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
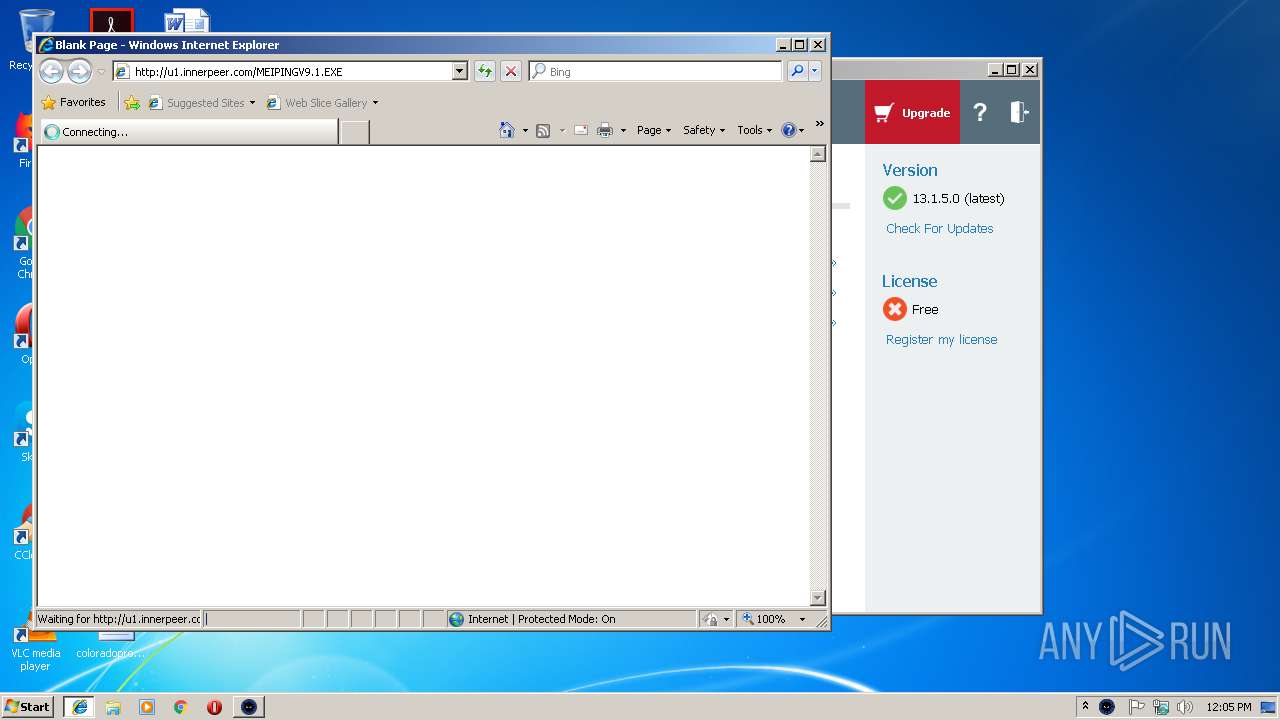
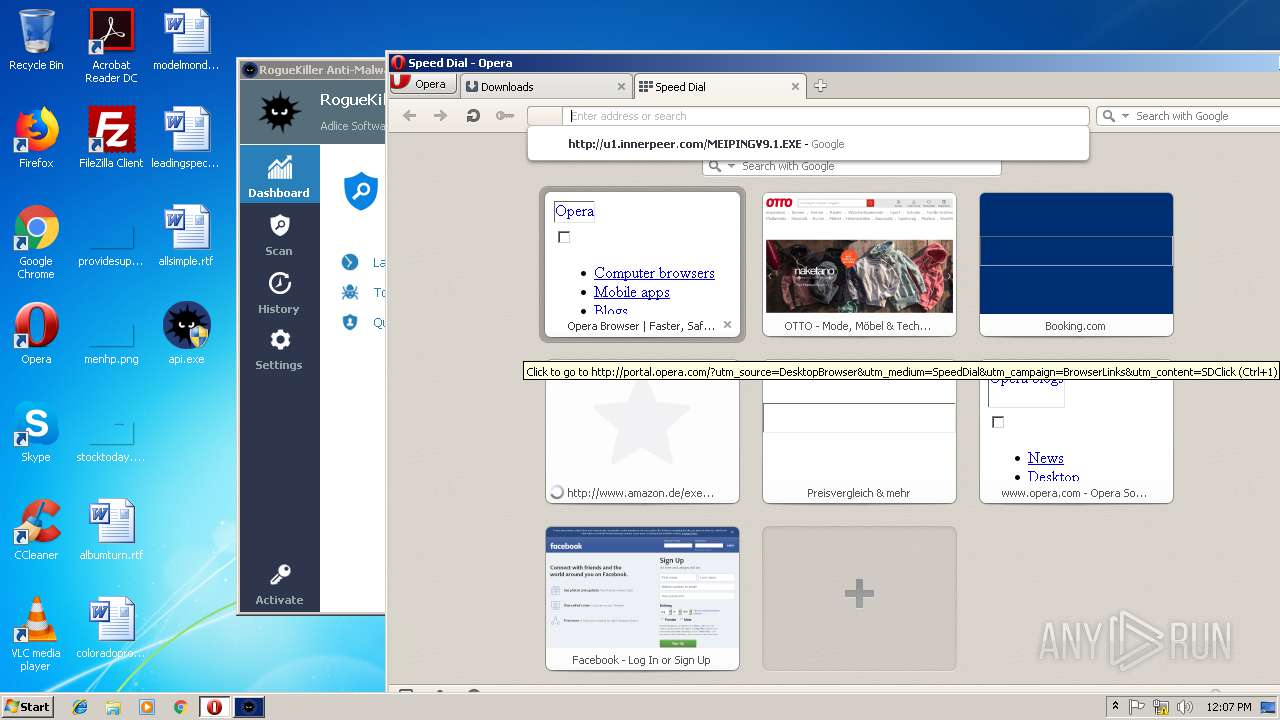
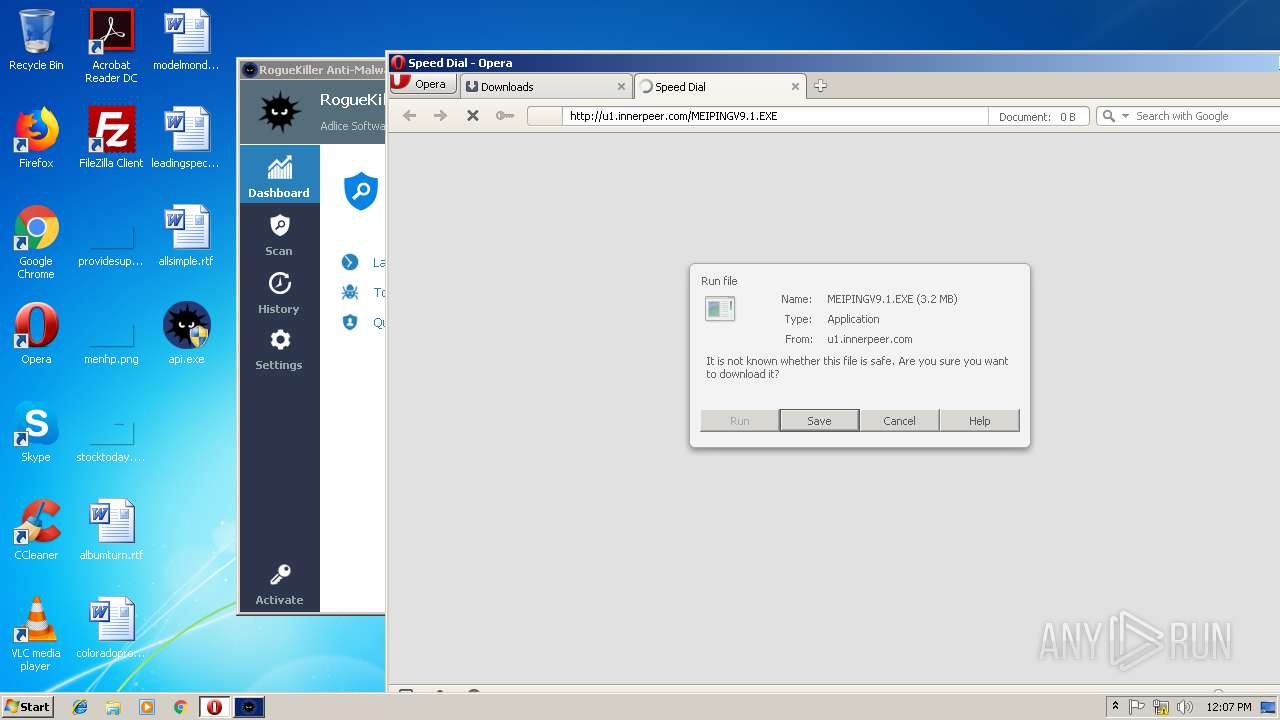
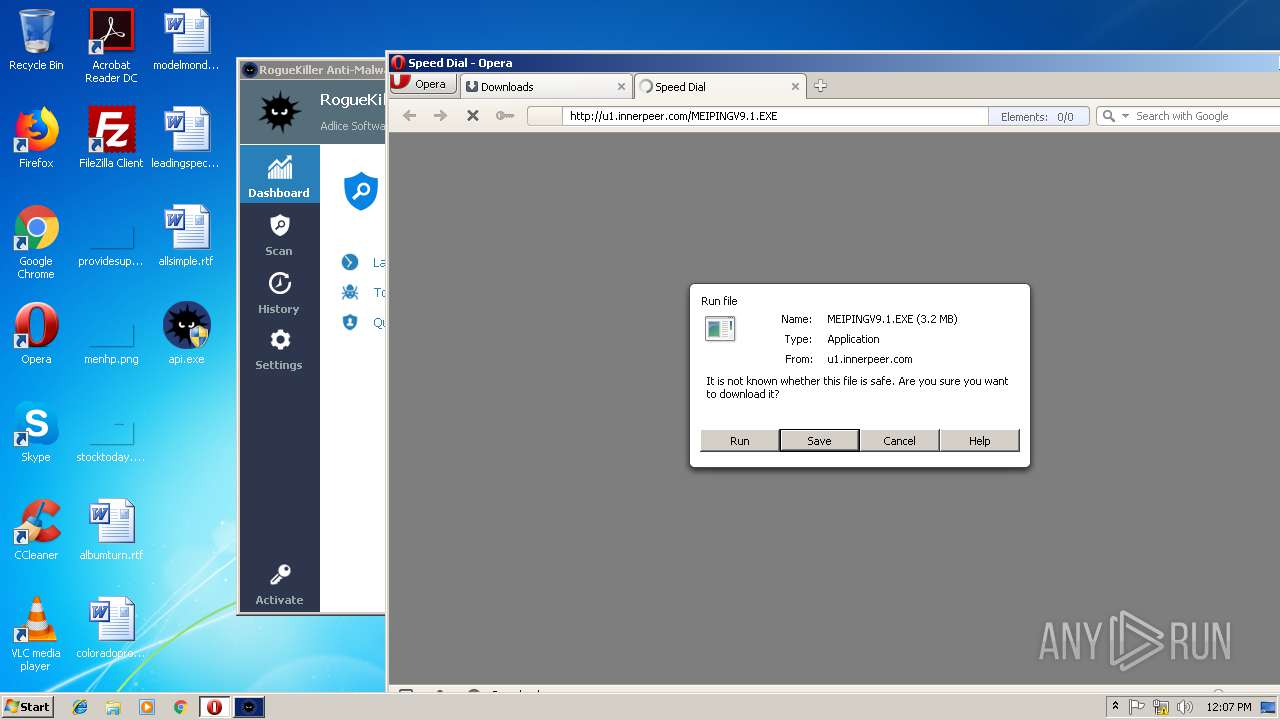
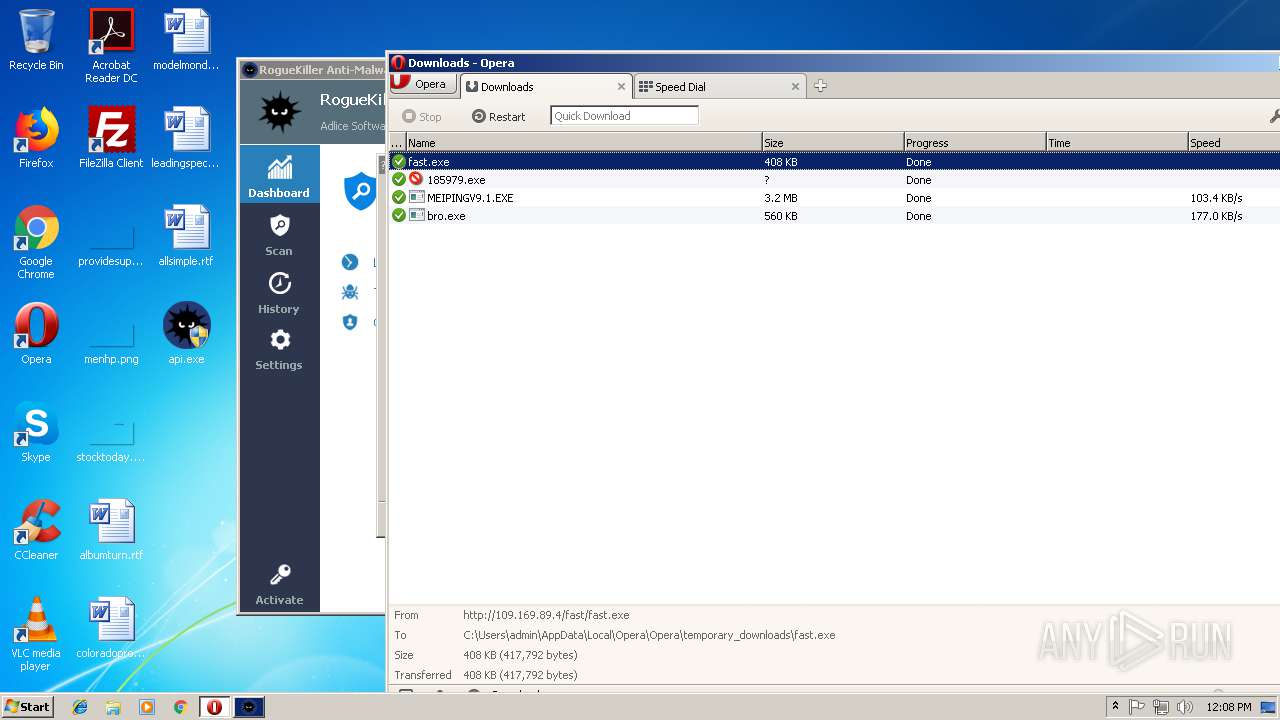
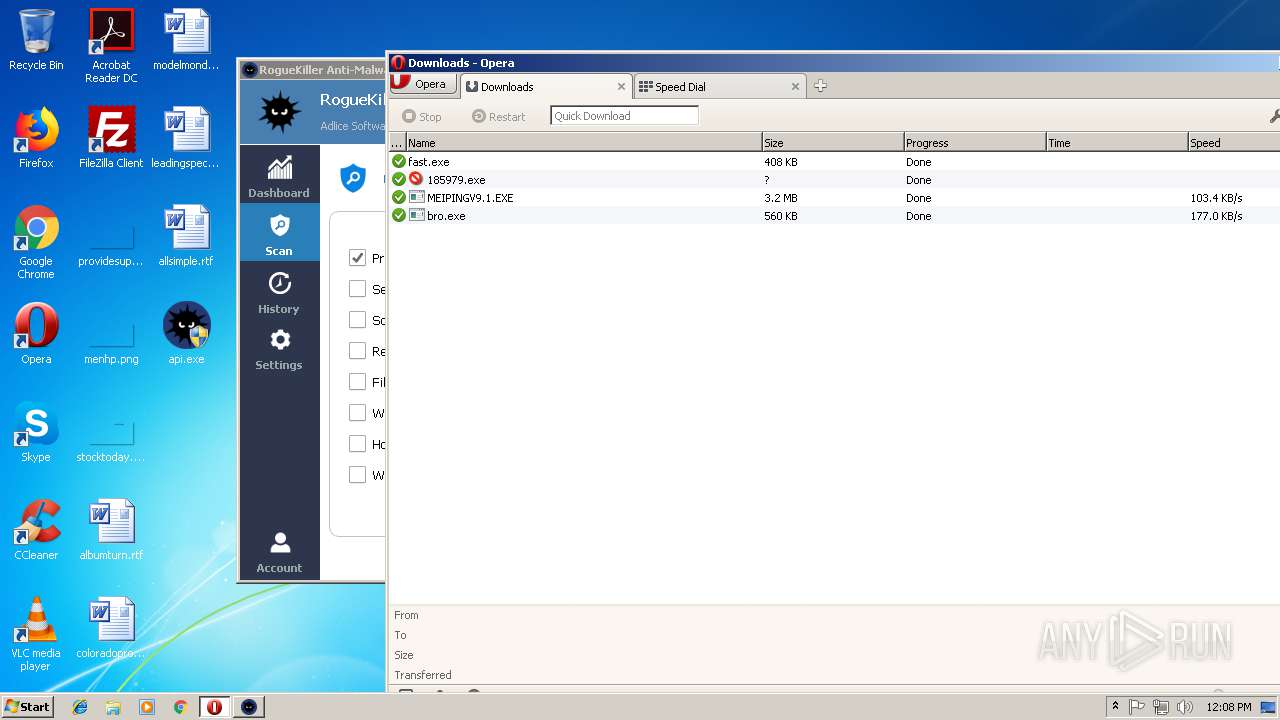
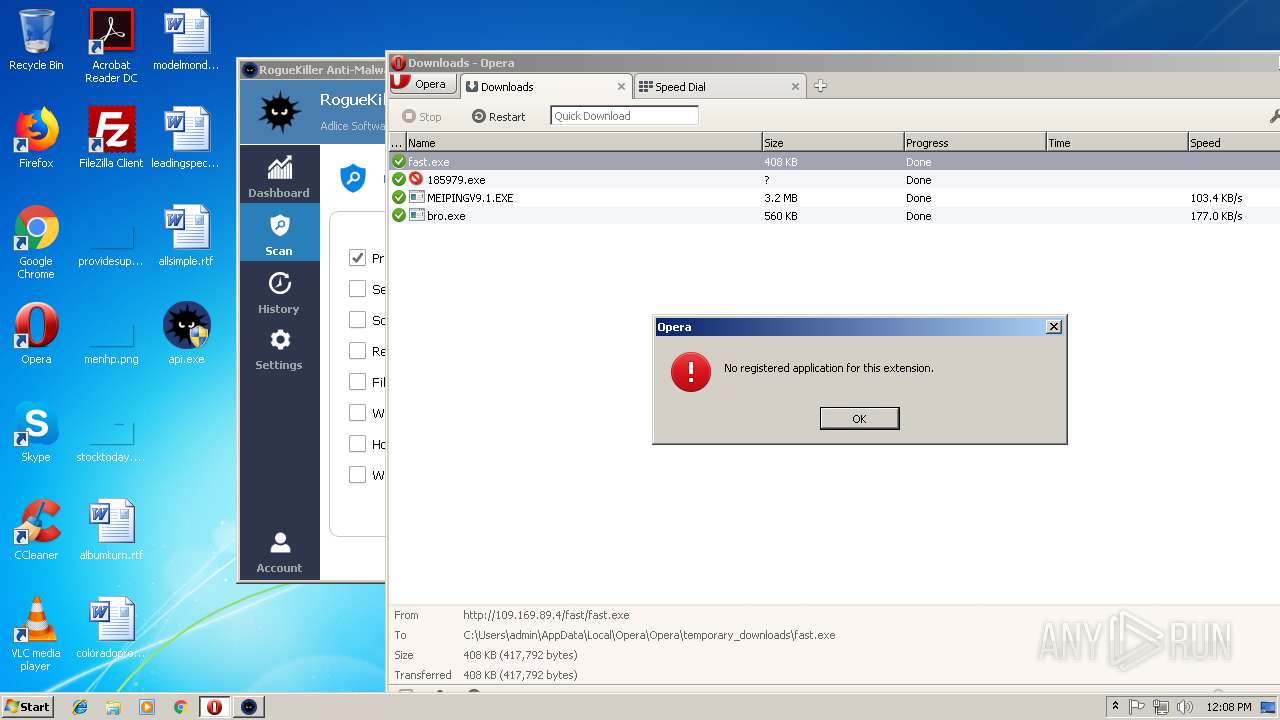
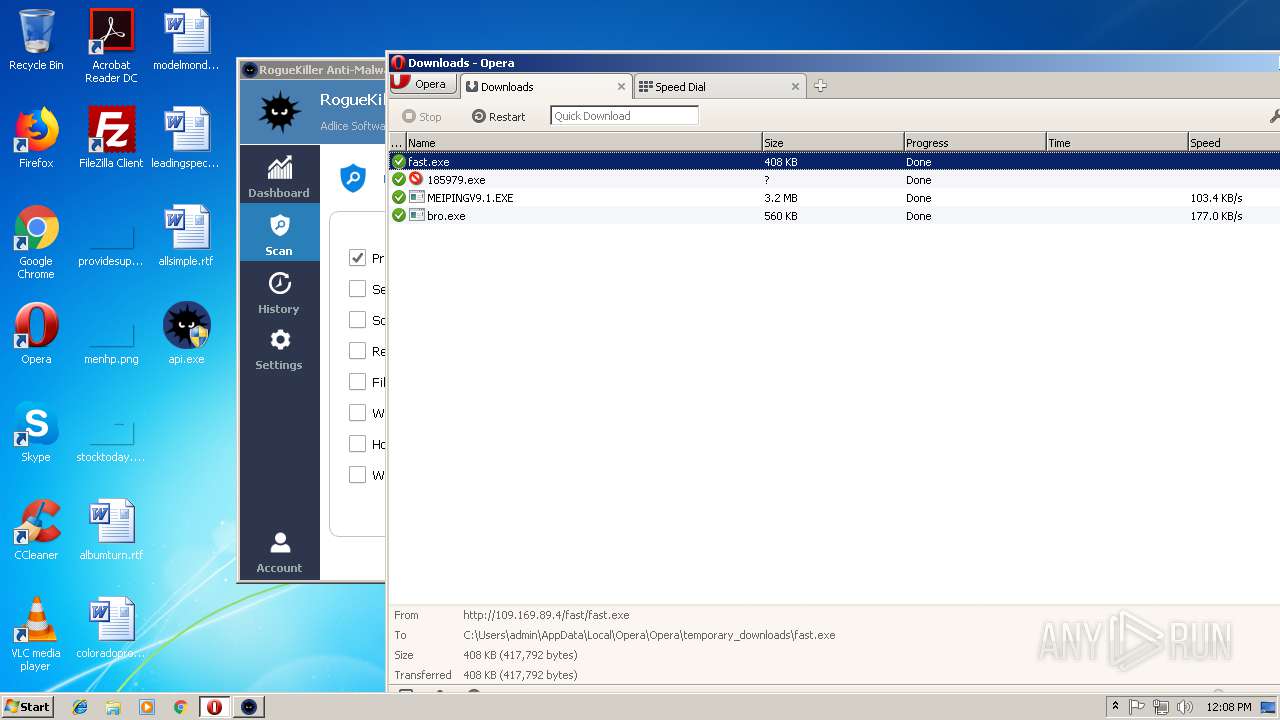
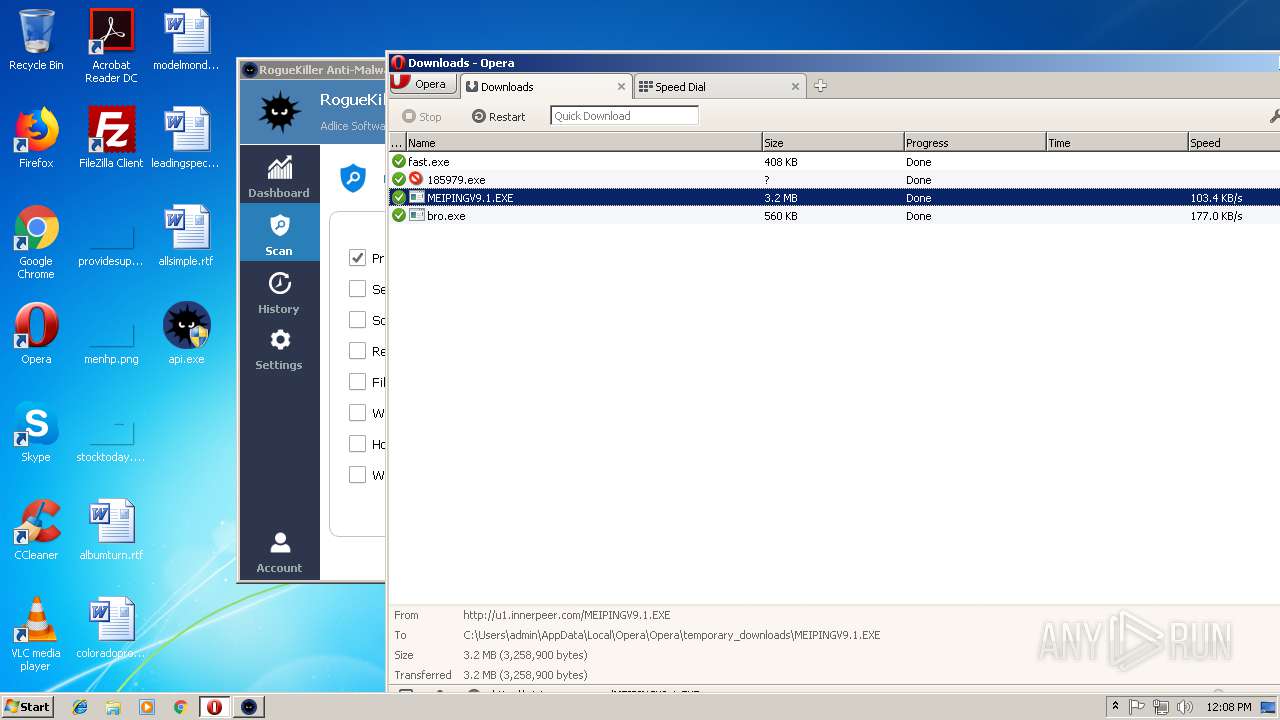
— | — | GET | — | 122.226.188.14:80 | http://u1.innerpeer.com/MEIPINGV9.1.EXE | CN | — | — | suspicious |
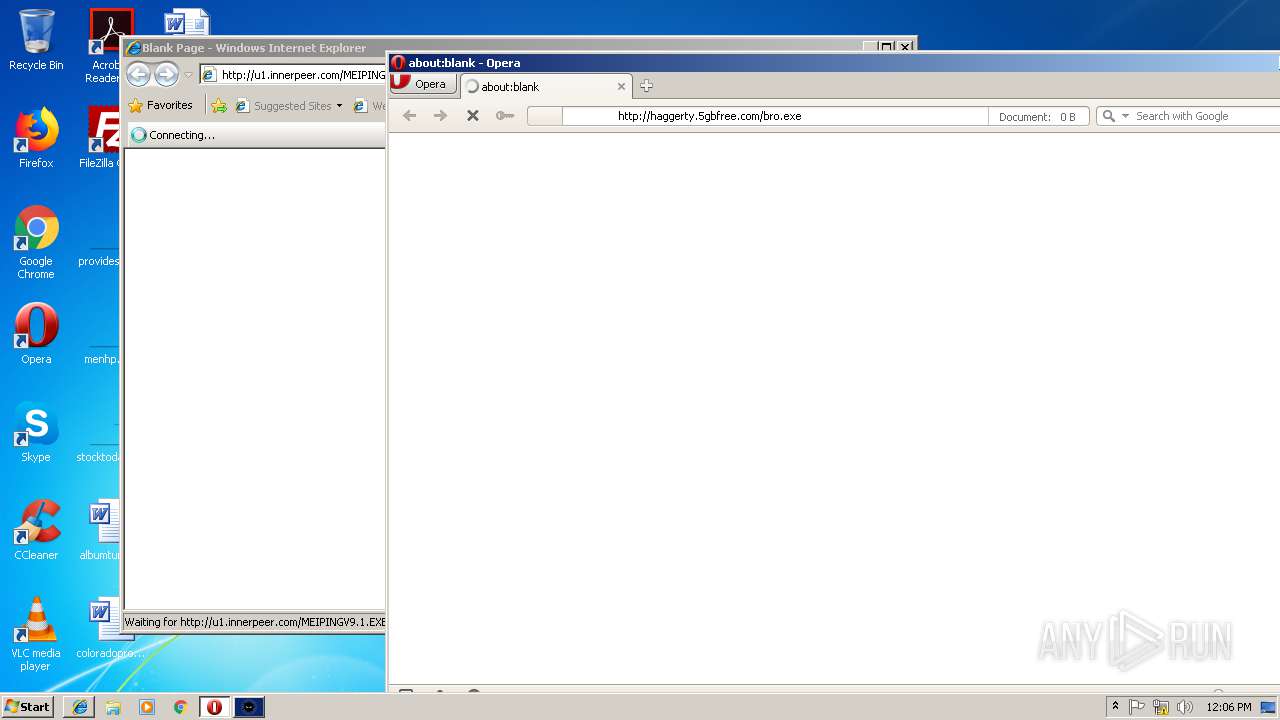
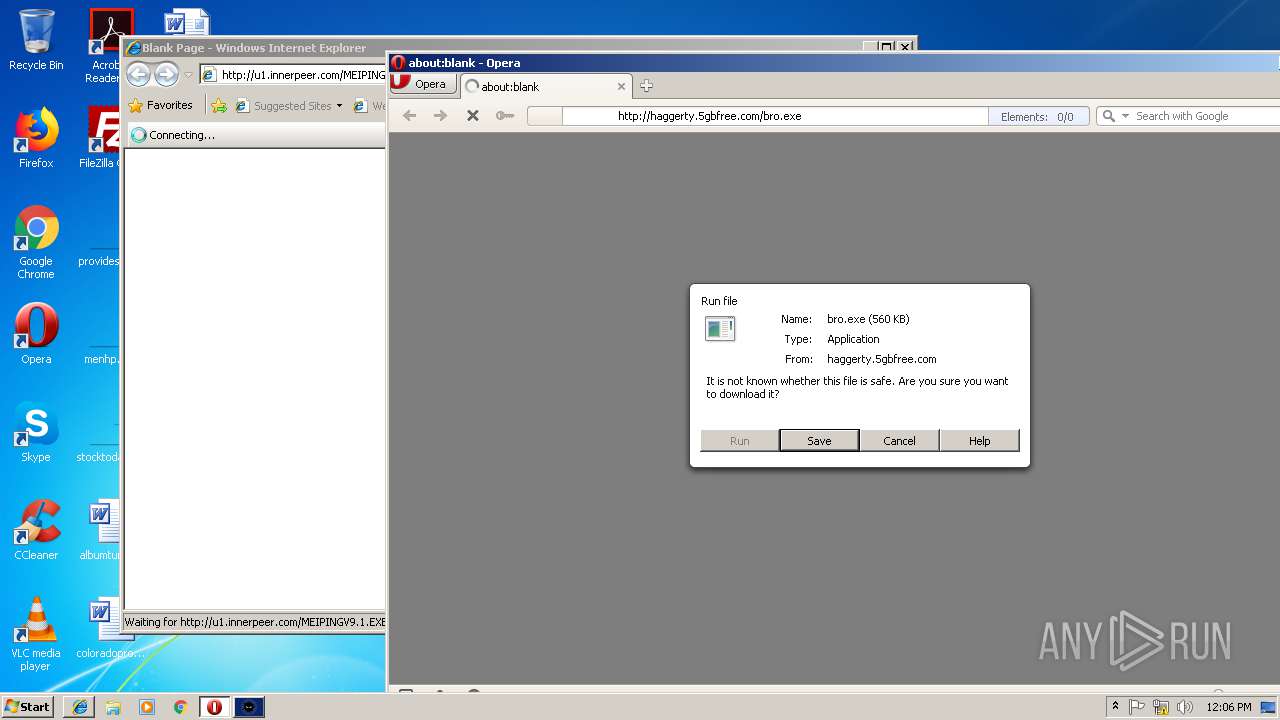
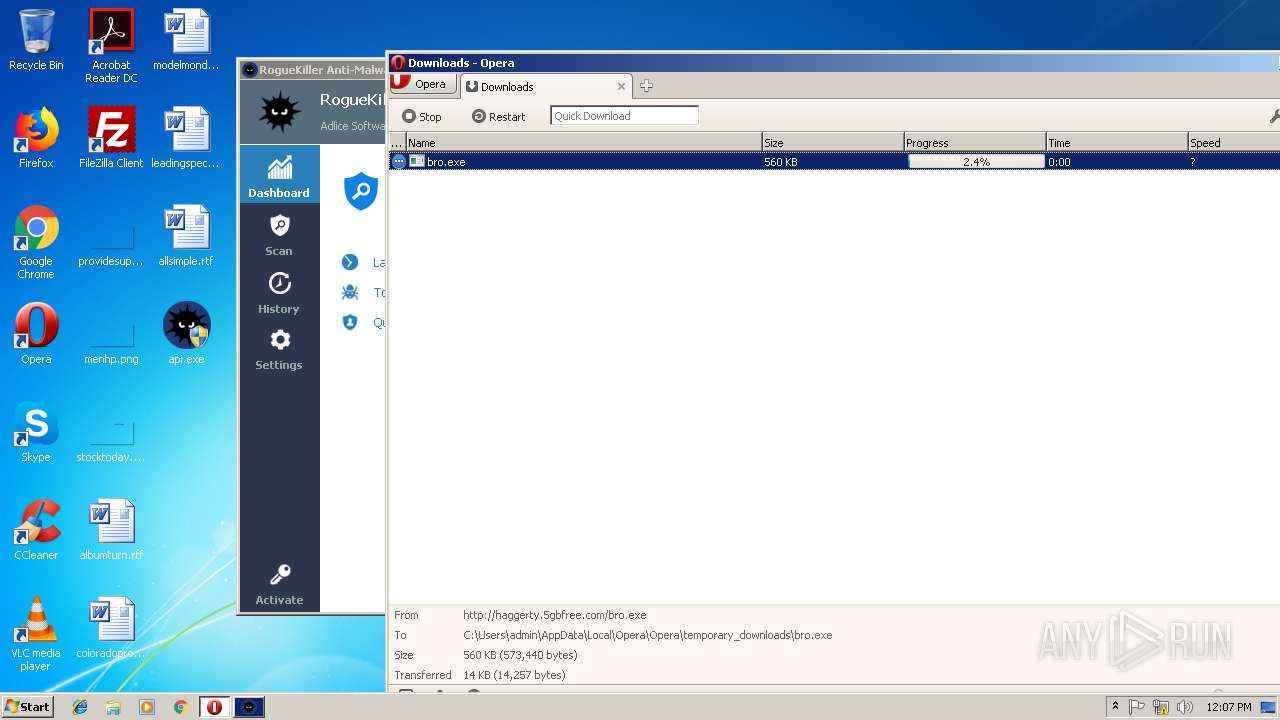
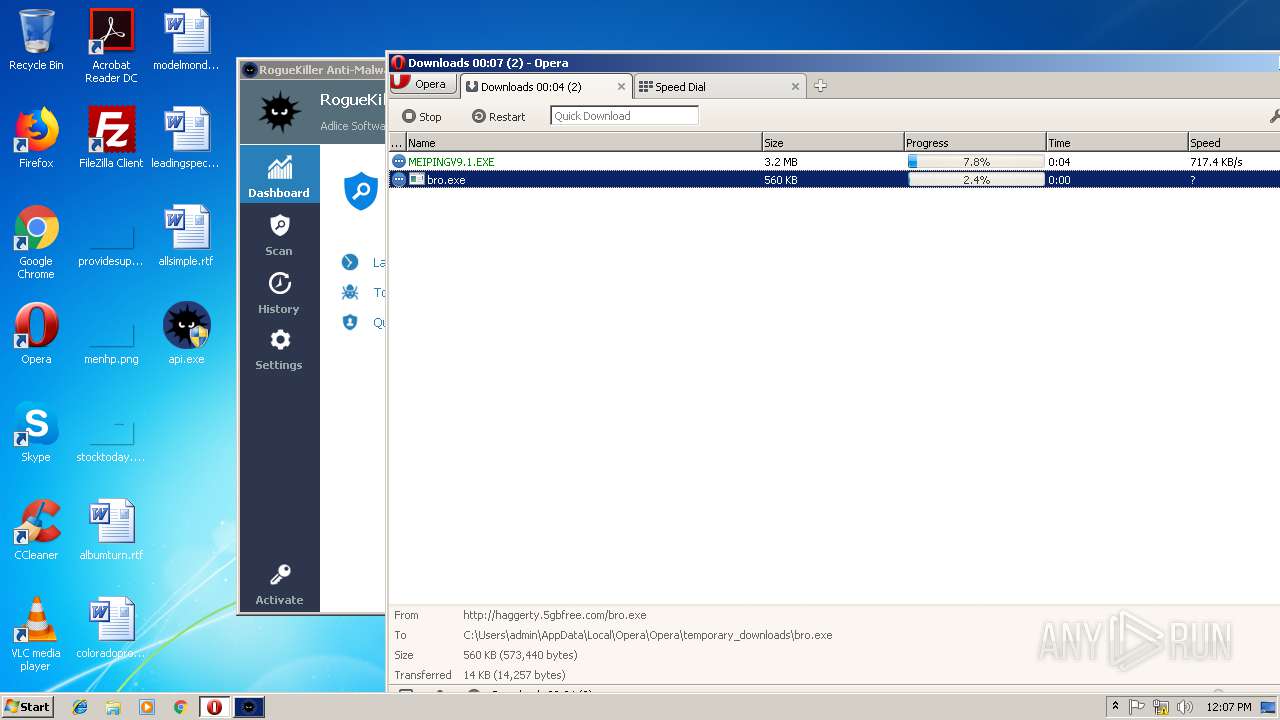
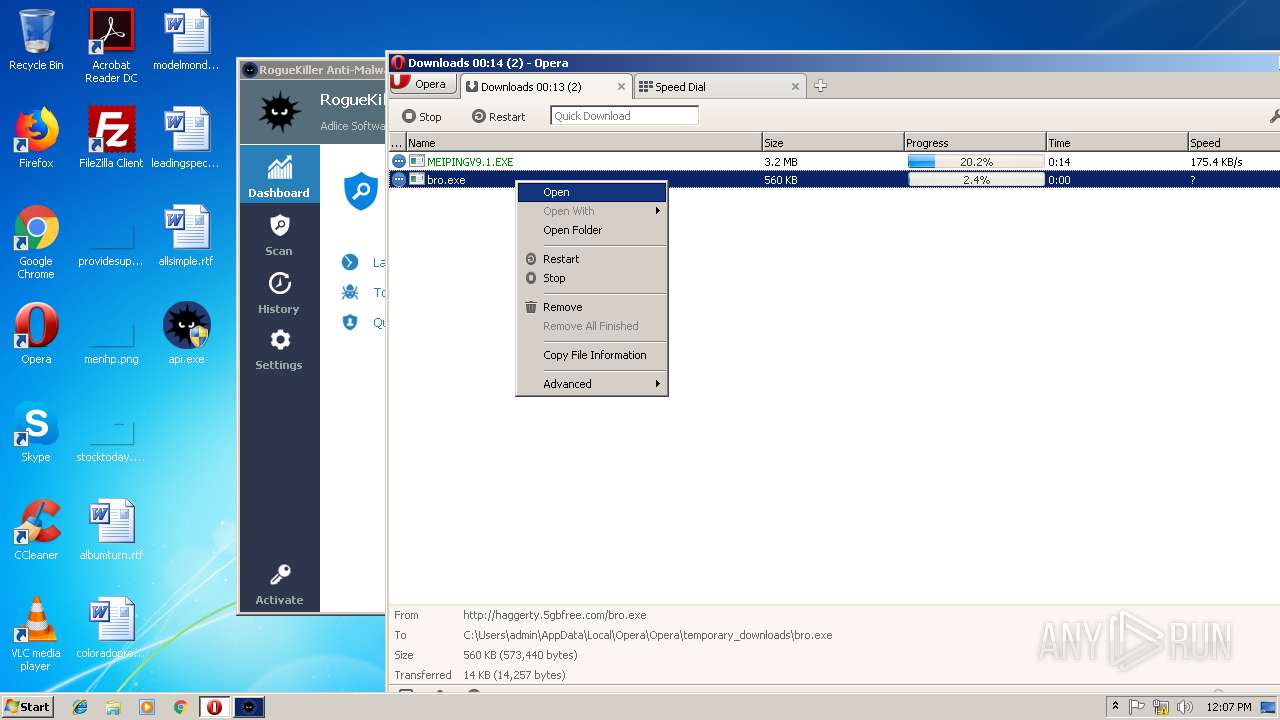
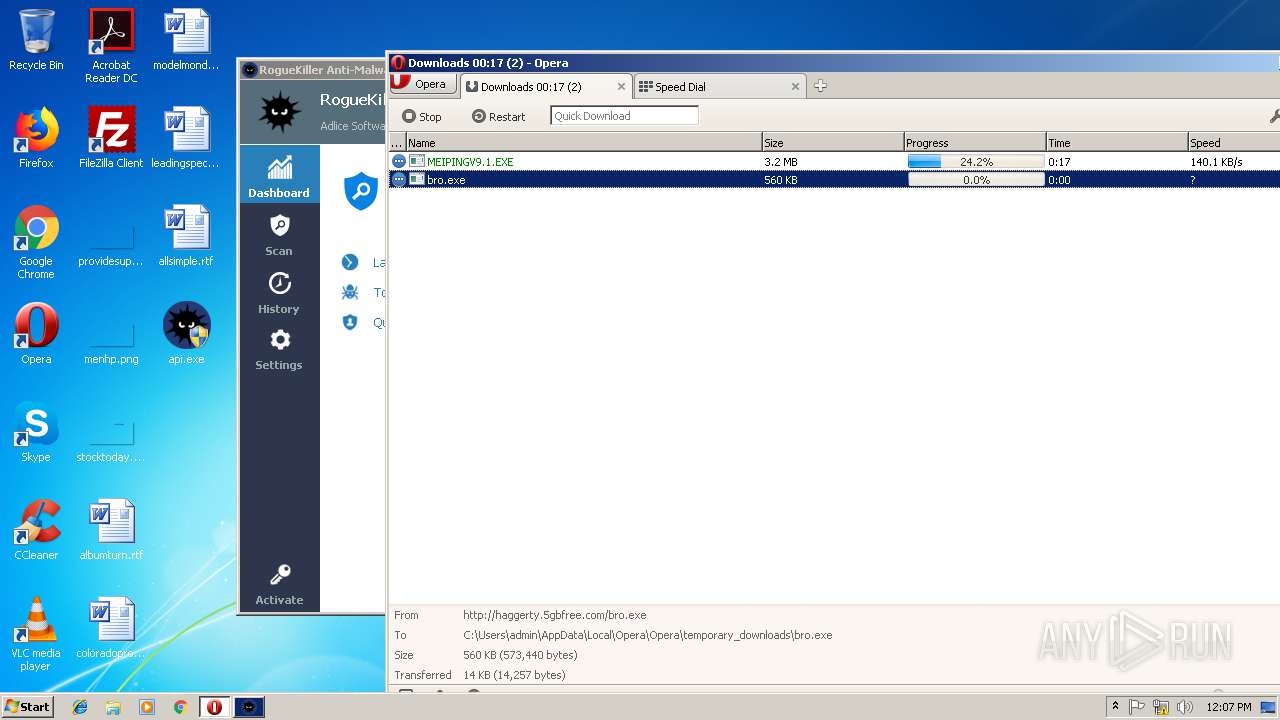
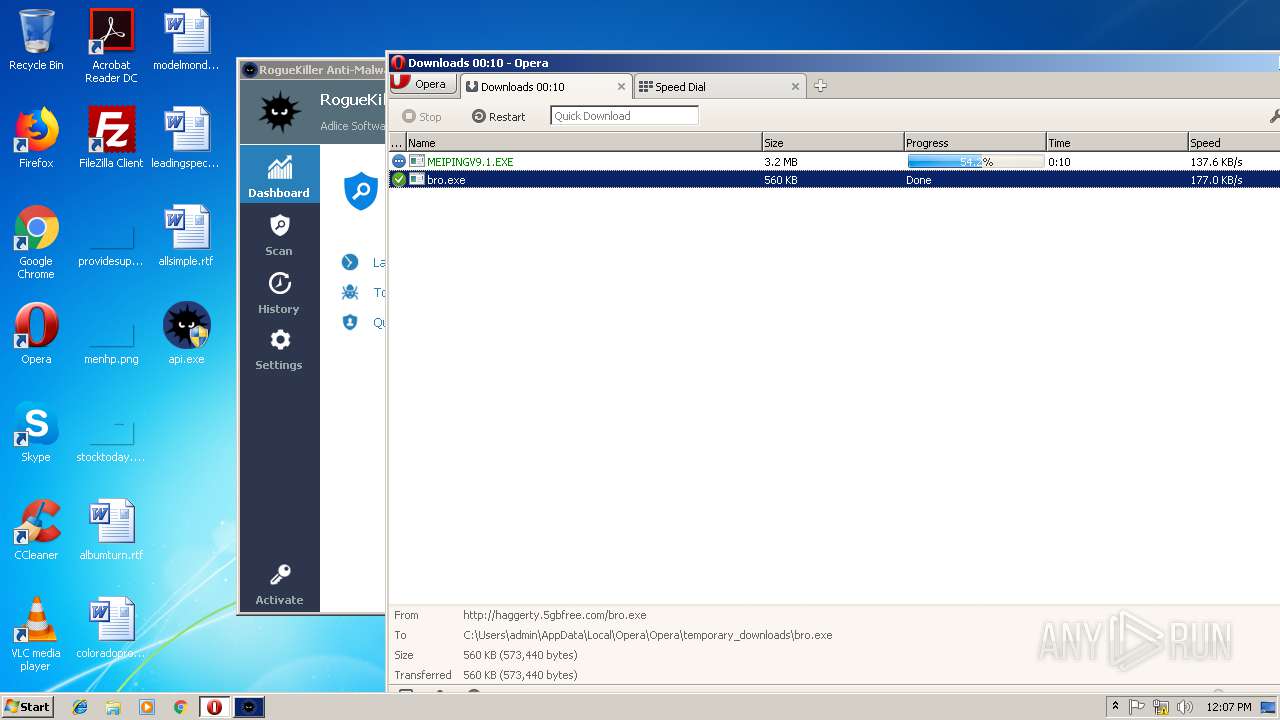
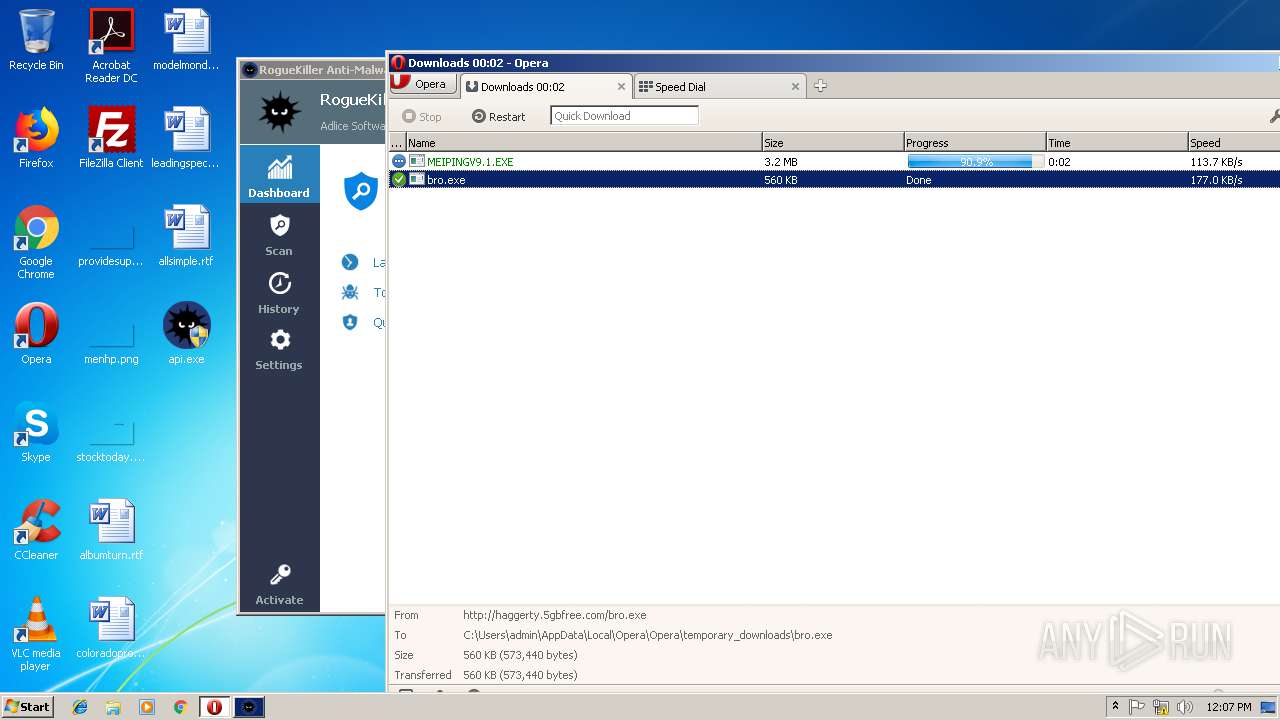
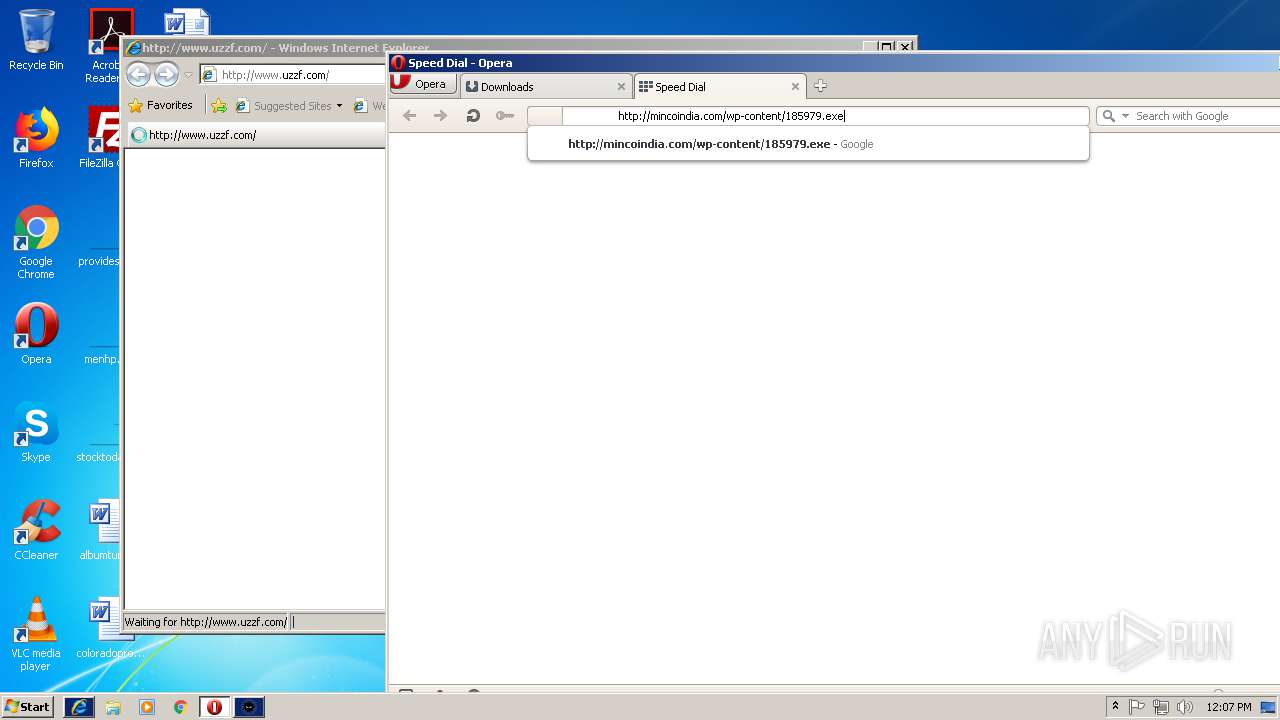
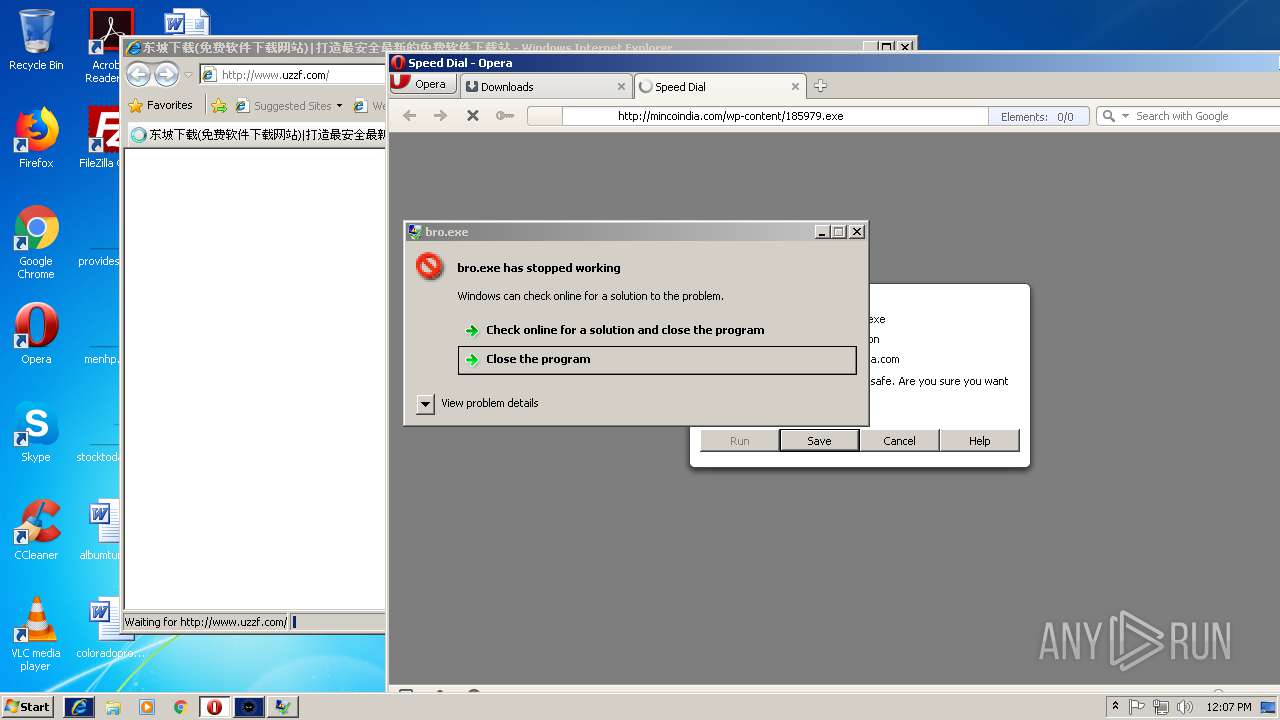
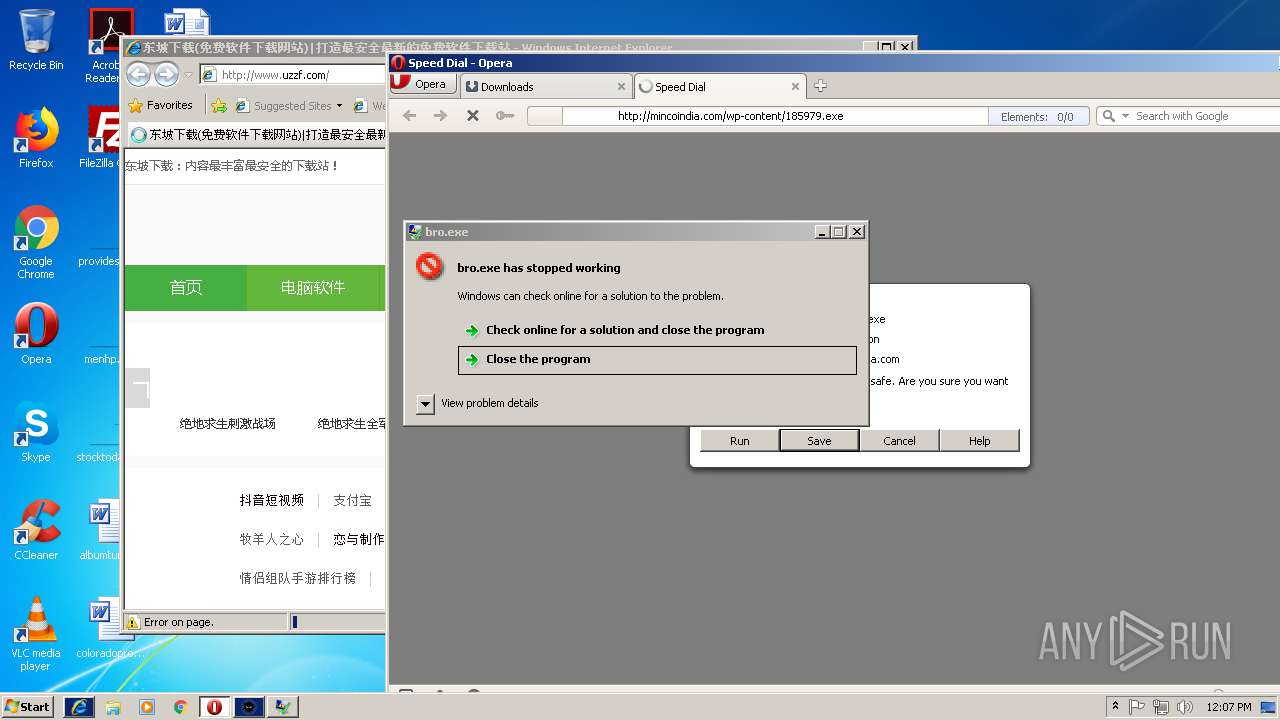
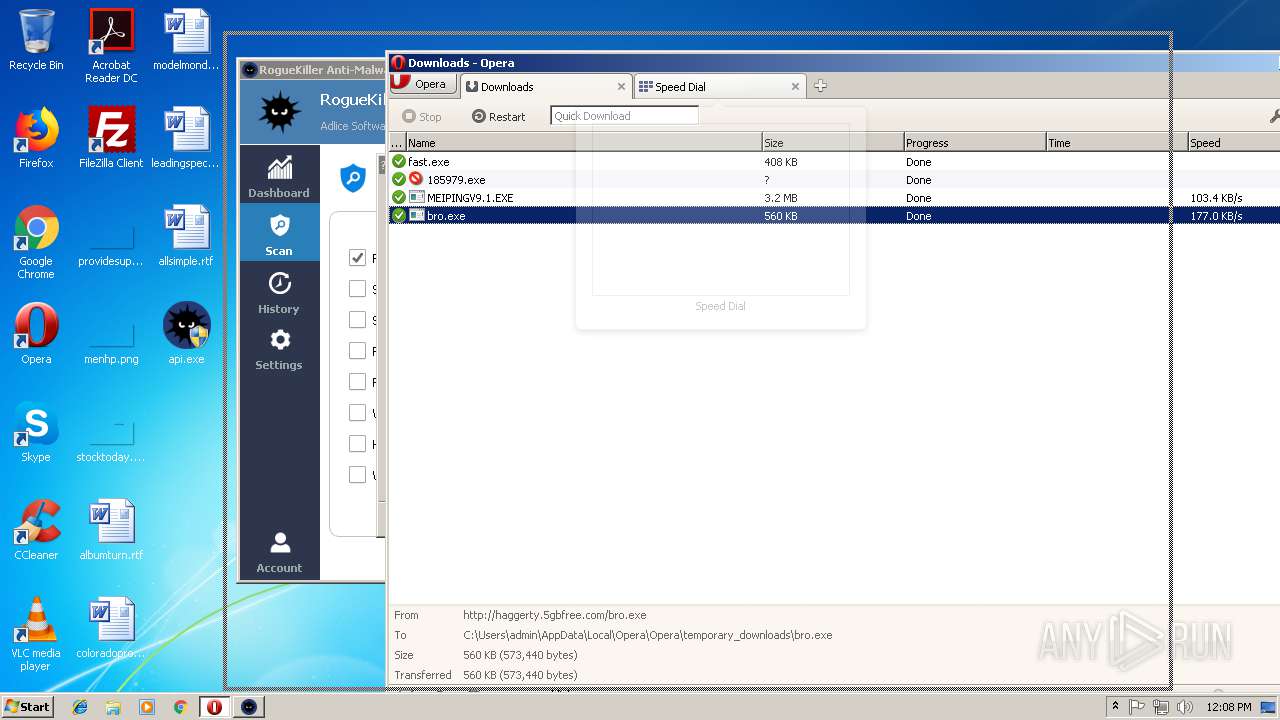
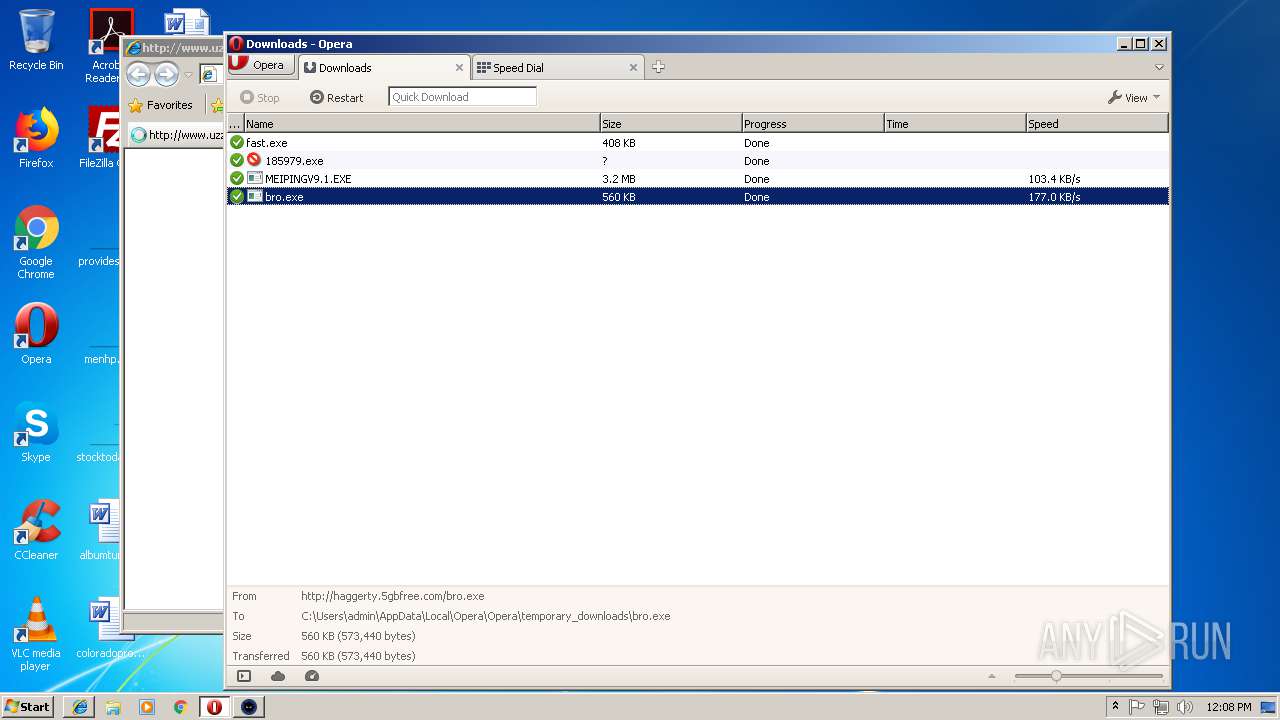
— | — | GET | — | 209.90.88.138:80 | http://haggerty.5gbfree.com/bro.exe | US | — | — | malicious |
— | — | GET | 302 | 185.26.182.109:80 | http://redir.opera.com/speeddials/amazon/ | unknown | — | — | whitelisted |
— | — | GET | 302 | 185.26.182.109:80 | http://redir.opera.com/speeddials/amazon/ | unknown | — | — | whitelisted |
— | — | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAOXQPQlVpLtFek%2BmcpabOk%3D | US | der | 471 b | whitelisted |
— | — | GET | 200 | 66.225.197.197:80 | http://crl4.digicert.com/DigiCertGlobalRootG2.crl | US | der | 517 b | whitelisted |
— | — | GET | 200 | 122.226.188.14:80 | http://u1.innerpeer.com/MEIPINGV9.1.EXE | CN | executable | 3.11 Mb | suspicious |
— | — | GET | 200 | 209.90.88.138:80 | http://haggerty.5gbfree.com/bro.exe | US | executable | 560 Kb | malicious |
— | — | GET | 200 | 13.32.222.248:80 | http://crl.rootca1.amazontrust.com/rootca1.crl | US | der | 439 b | whitelisted |
— | — | GET | 301 | 13.32.159.158:80 | http://www.amazon.com/exec/obidos/redirect-home/opera-20 | US | html | 183 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 178.33.106.117:443 | download.adlice.com | OVH SAS | FR | suspicious |
— | — | 104.27.165.26:443 | adlice.com | Cloudflare Inc | US | shared |
— | — | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
— | — | 104.27.164.26:443 | adlice.com | Cloudflare Inc | US | shared |
— | — | 122.226.188.14:80 | u1.innerpeer.com | No.31,Jin-rong Street | CN | suspicious |
— | — | 82.145.215.40:443 | certs.opera.com | Opera Software AS | — | whitelisted |
— | — | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
— | — | 13.32.159.158:443 | www.amazon.com | Amazon.com, Inc. | US | unknown |
— | — | 13.32.141.62:443 | images-na.ssl-images-amazon.com | Amazon.com, Inc. | US | unknown |
— | — | 13.32.222.241:80 | s.ss2.us | Amazon.com, Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download.adlice.com |
| whitelisted |
adlice.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.adlice.com |
| whitelisted |
u1.innerpeer.com |
| suspicious |
certs.opera.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
haggerty.5gbfree.com |
| malicious |
sitecheck2.opera.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile |
— | — | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
— | — | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
— | — | Potentially Bad Traffic | ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile |
— | — | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
— | — | A Network Trojan was detected | MALWARE [PTsecurity] RAT.Win32.AveMaria |
— | — | A Network Trojan was detected | MALWARE [PTsecurity] RAT.Win32.AveMaria |
— | — | A Network Trojan was detected | ET TROJAN EXE Download Request To Wordpress Folder Likely Malicious |
— | — | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
— | — | A Network Trojan was detected | ET INFO Executable Download from dotted-quad Host |
31 ETPRO signatures available at the full report