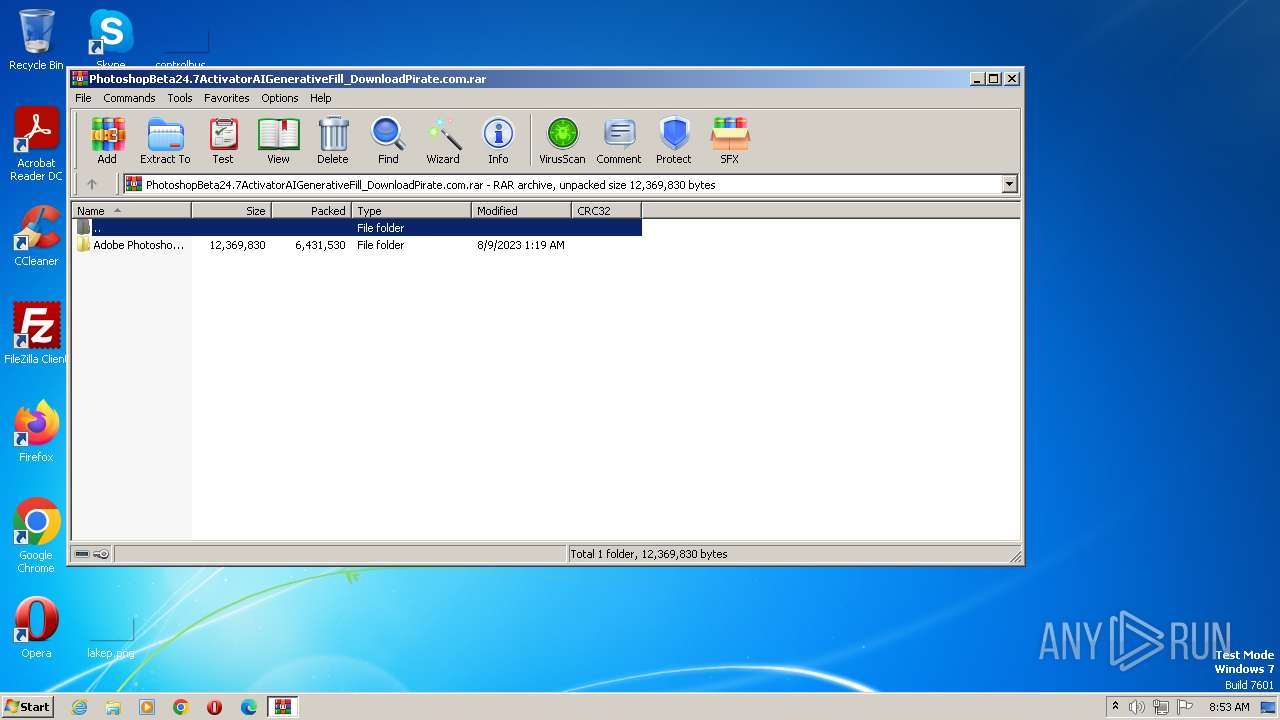
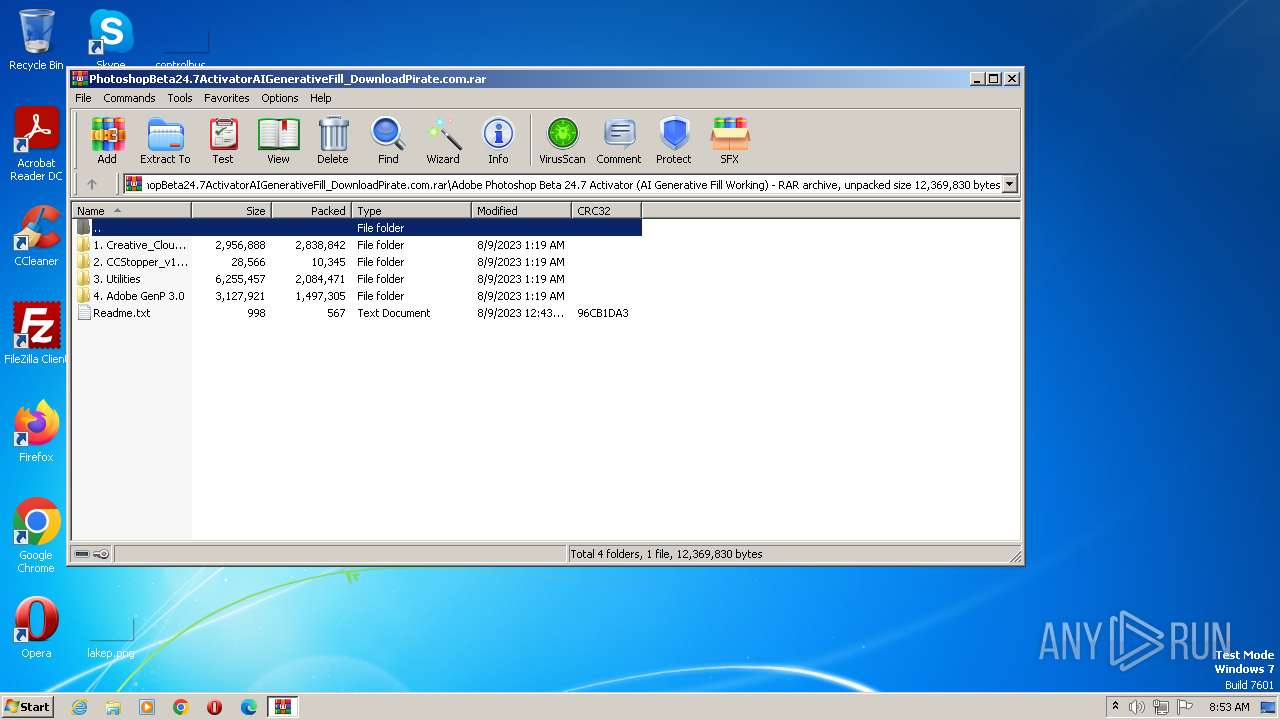
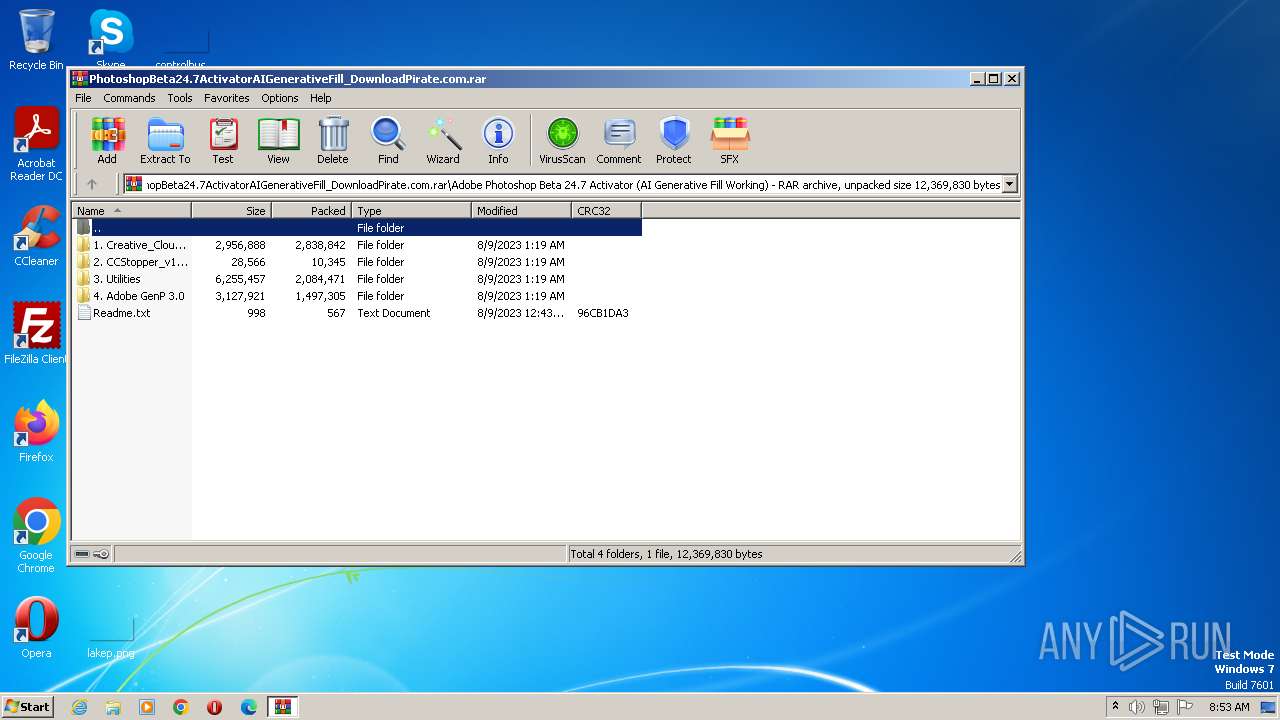
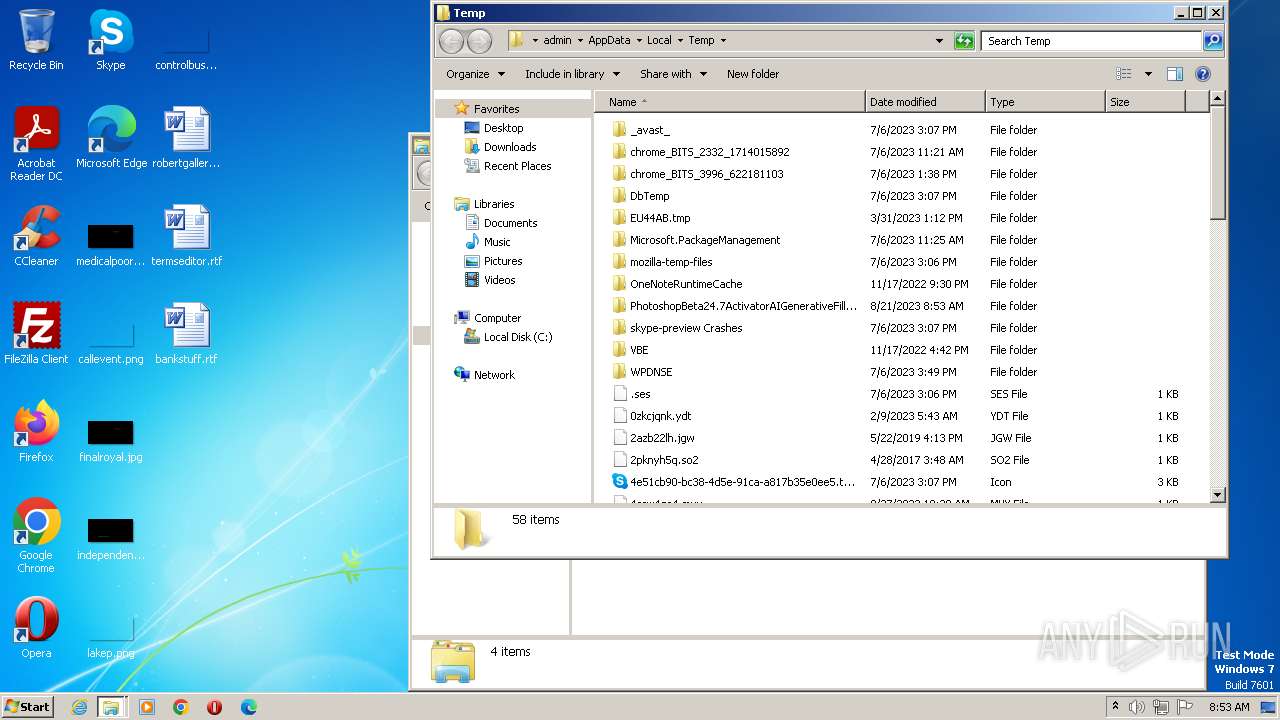
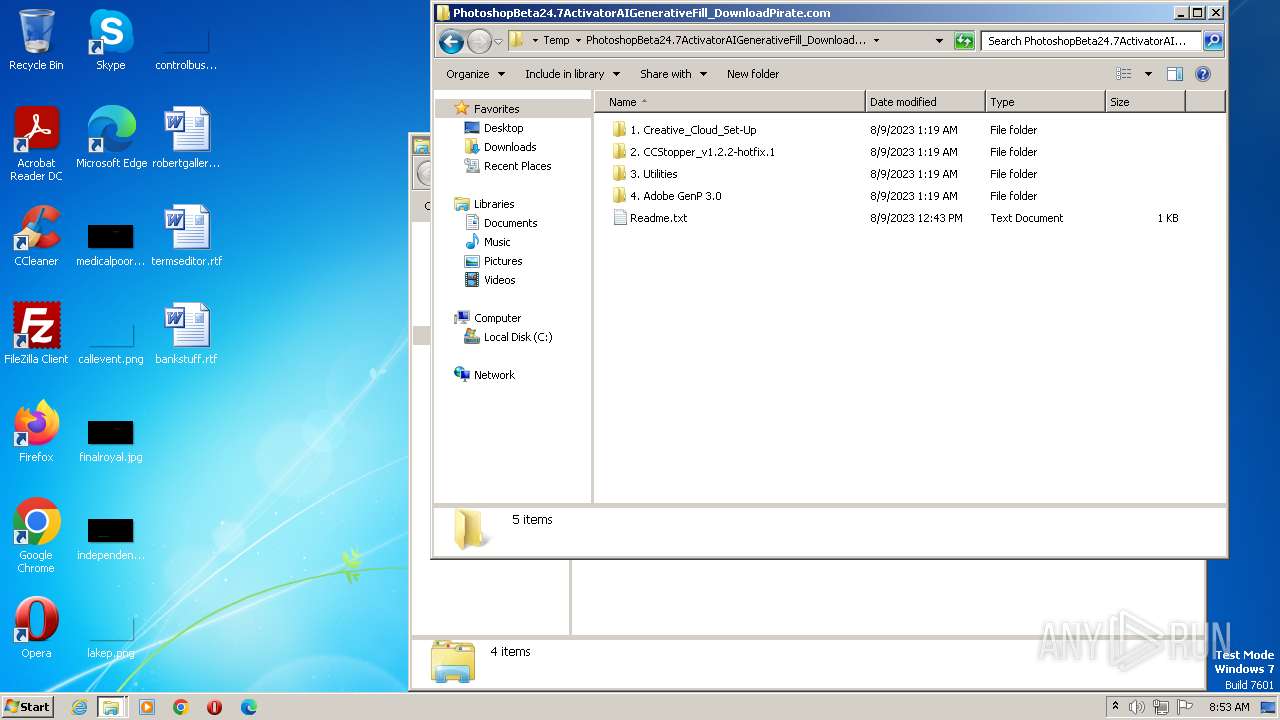
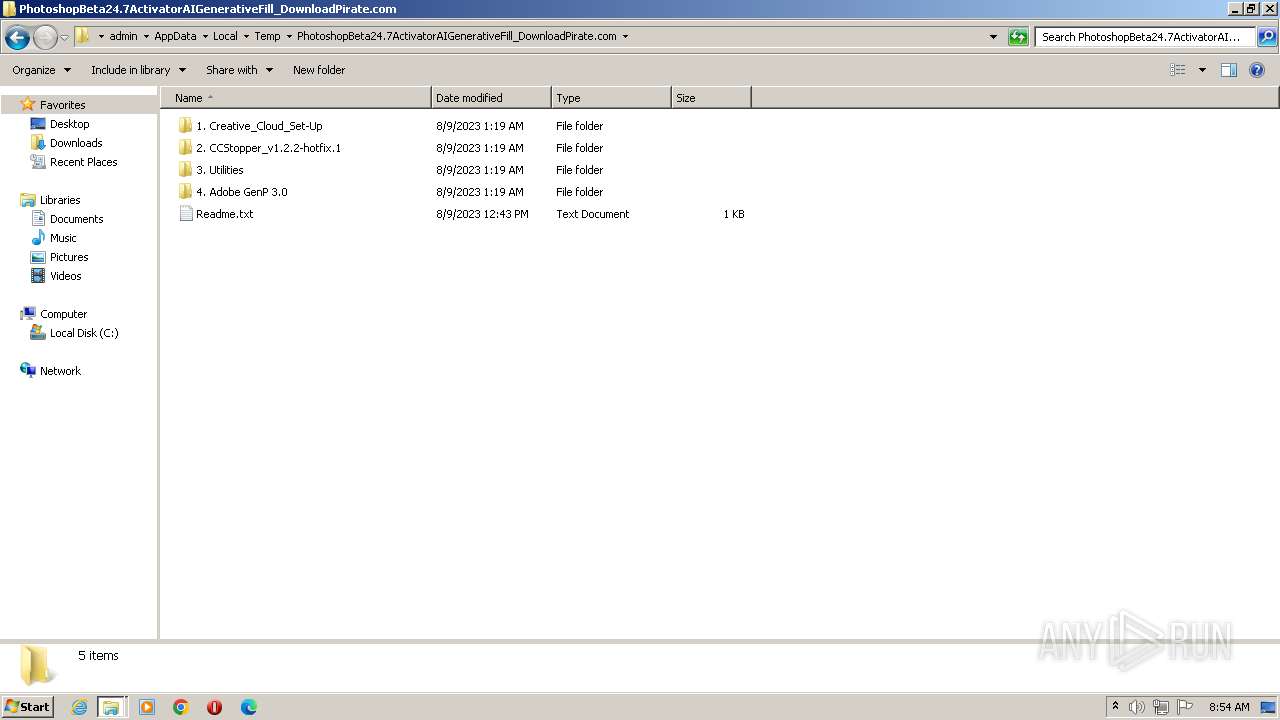
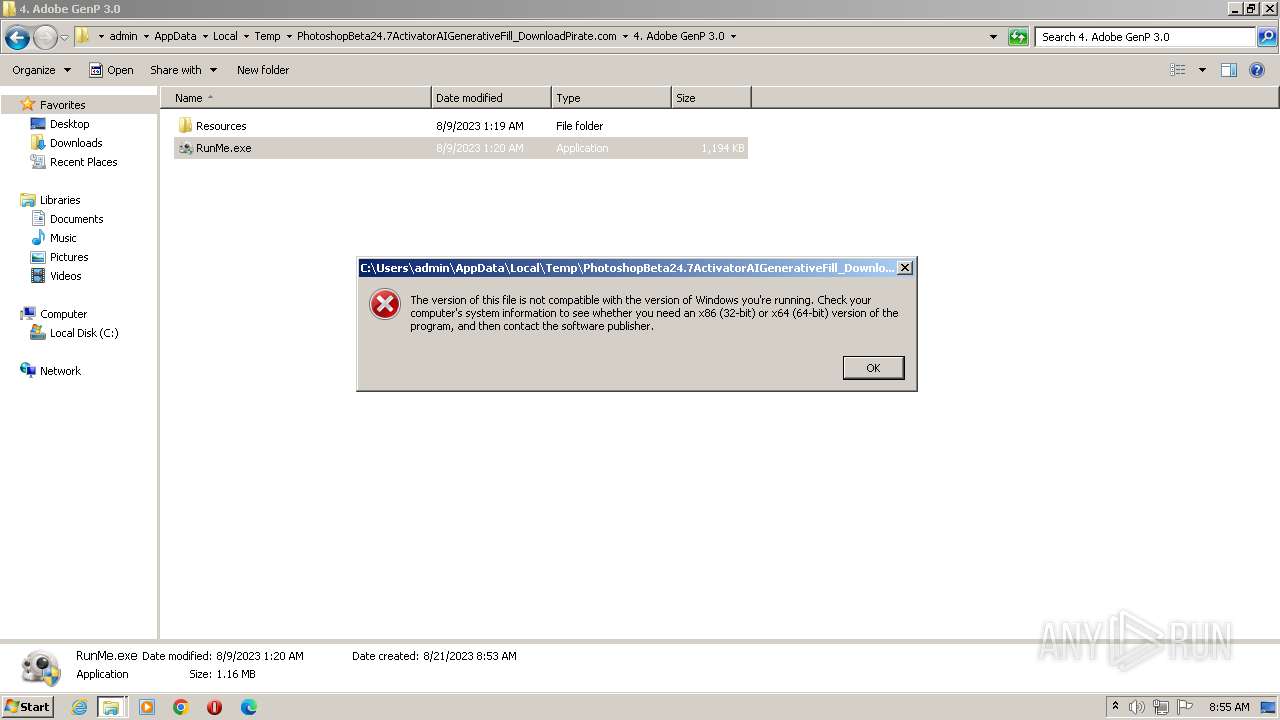
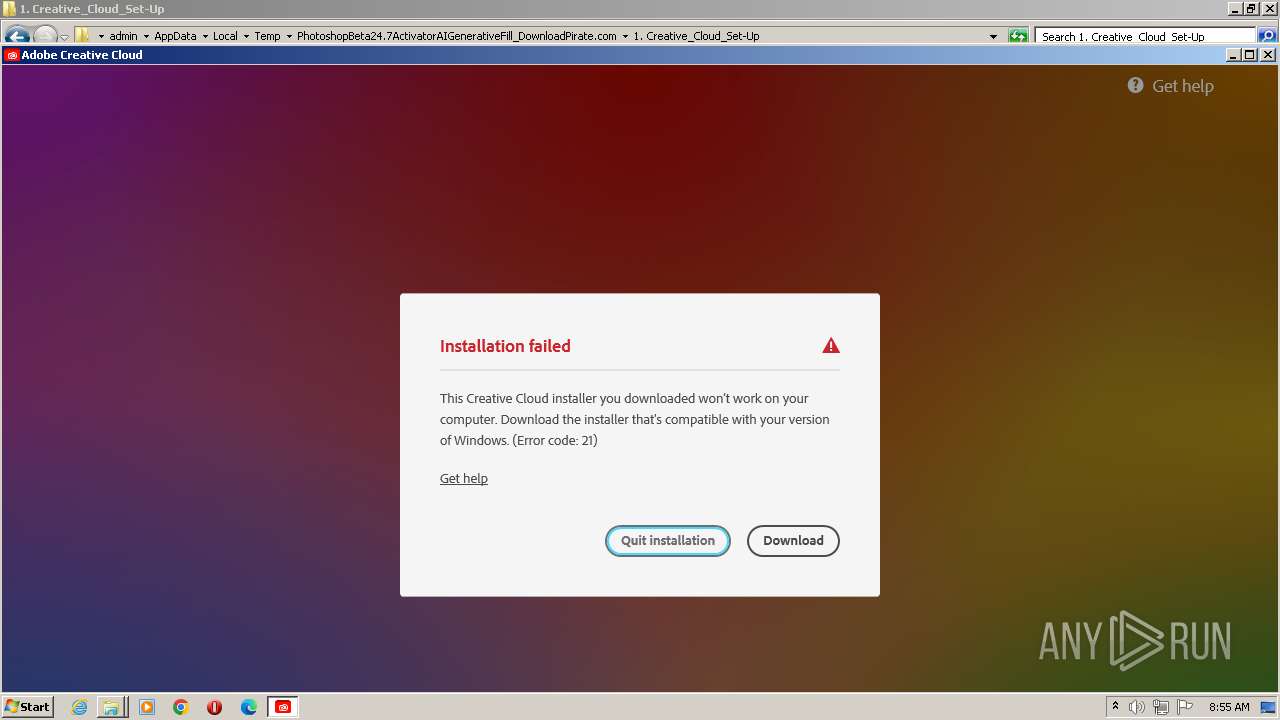
| File name: | PhotoshopBeta24.7ActivatorAIGenerativeFill_DownloadPirate.com.rar |
| Full analysis: | https://app.any.run/tasks/0ff6fa0a-db0e-4f07-9ebb-ccba1be45e6e |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | August 21, 2023, 07:52:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 98717B0D79181A089B66C2825C6D13A2 |
| SHA1: | 547E945C1002F68ABB9C8AB76226368D0B18BCF6 |
| SHA256: | FDC37AD631D8A06B8926097C9345565229F92F098CC8DA11B257689A00EBC6E2 |
| SSDEEP: | 196608:HhDX7zHdJiIsNxJ+cbfL8YjbbQ8BBy3hMm:HRXHdJBs7J/zL8efQEBIMm |
MALICIOUS
Application was dropped or rewritten from another process
- Creative_Cloud_Set-Up.exe (PID: 2080)
- Creative_Cloud_Set-Up.exe (PID: 2032)
Changes powershell execution policy (RemoteSigned)
- cmd.exe (PID: 3332)
- cmd.exe (PID: 3984)
SUSPICIOUS
Reads the Internet Settings
- Creative_Cloud_Set-Up.exe (PID: 2080)
- mshta.exe (PID: 4052)
- mshta.exe (PID: 1028)
- powershell.exe (PID: 3440)
- powershell.exe (PID: 1680)
- Creative_Cloud_Set-Up.exe (PID: 2032)
Reads Microsoft Outlook installation path
- Creative_Cloud_Set-Up.exe (PID: 2080)
- Creative_Cloud_Set-Up.exe (PID: 2032)
Reads Internet Explorer settings
- Creative_Cloud_Set-Up.exe (PID: 2080)
- Creative_Cloud_Set-Up.exe (PID: 2032)
Starts CMD.EXE for commands execution
- mshta.exe (PID: 4052)
- mshta.exe (PID: 1028)
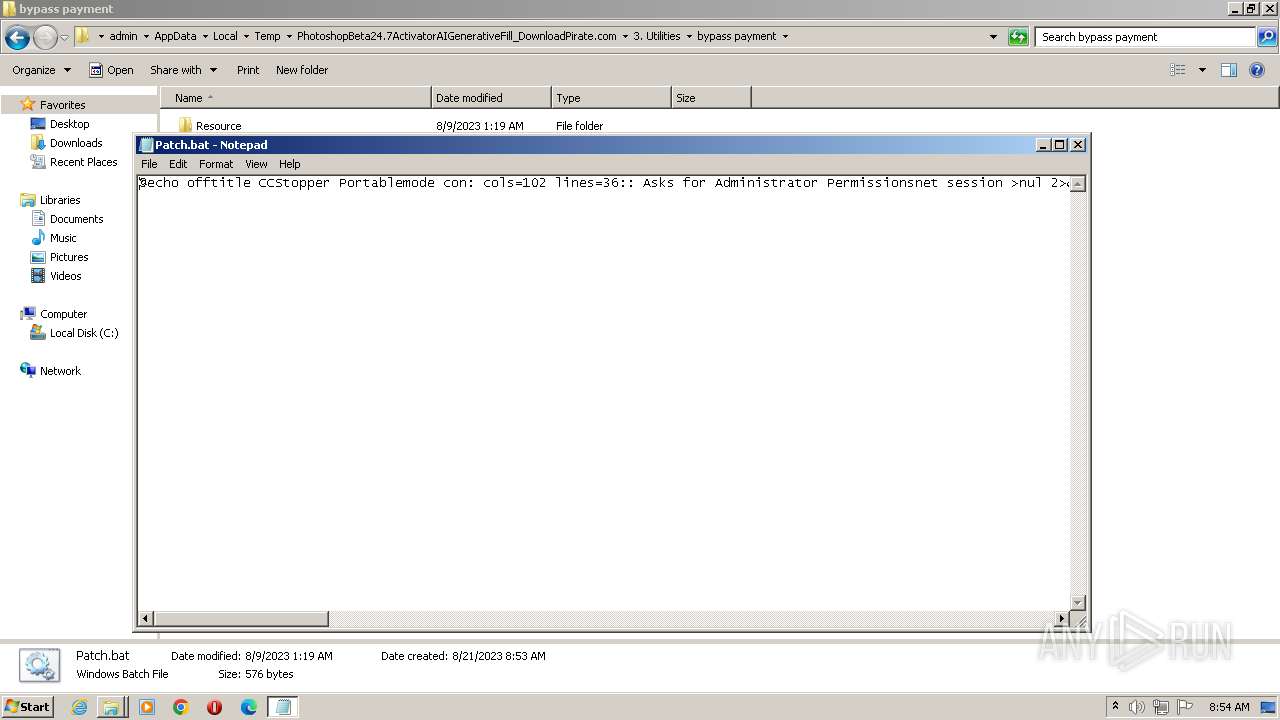
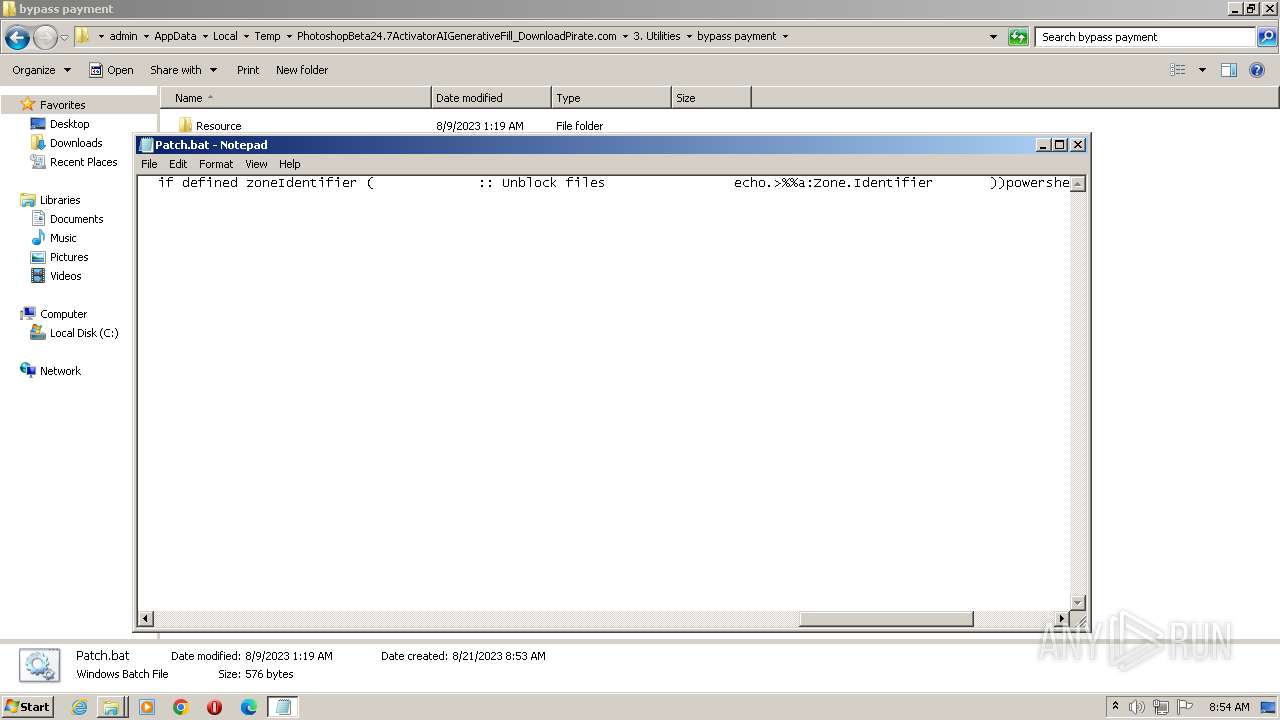
Executing commands from a ".bat" file
- mshta.exe (PID: 4052)
- mshta.exe (PID: 1028)
The process executes Powershell scripts
- cmd.exe (PID: 3332)
- cmd.exe (PID: 3984)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3332)
- cmd.exe (PID: 3984)
Powershell version downgrade attack
- powershell.exe (PID: 3440)
- powershell.exe (PID: 1680)
Reads security settings of Internet Explorer
- Creative_Cloud_Set-Up.exe (PID: 2032)
Checks Windows Trust Settings
- Creative_Cloud_Set-Up.exe (PID: 2032)
Reads settings of System Certificates
- Creative_Cloud_Set-Up.exe (PID: 2032)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3488)
Checks supported languages
- Creative_Cloud_Set-Up.exe (PID: 2080)
- mode.com (PID: 2664)
- mode.com (PID: 2684)
- mode.com (PID: 2736)
- mode.com (PID: 2740)
- Creative_Cloud_Set-Up.exe (PID: 2032)
Manual execution by a user
- explorer.exe (PID: 2384)
- Creative_Cloud_Set-Up.exe (PID: 2080)
- cmd.exe (PID: 2600)
- cmd.exe (PID: 720)
- Creative_Cloud_Set-Up.exe (PID: 2032)
- notepad.exe (PID: 3256)
Create files in a temporary directory
- Creative_Cloud_Set-Up.exe (PID: 2080)
- Creative_Cloud_Set-Up.exe (PID: 2032)
Reads CPU info
- Creative_Cloud_Set-Up.exe (PID: 2080)
- Creative_Cloud_Set-Up.exe (PID: 2032)
Reads the computer name
- Creative_Cloud_Set-Up.exe (PID: 2080)
- Creative_Cloud_Set-Up.exe (PID: 2032)
Creates files or folders in the user directory
- Creative_Cloud_Set-Up.exe (PID: 2080)
- Creative_Cloud_Set-Up.exe (PID: 2032)
Reads the machine GUID from the registry
- Creative_Cloud_Set-Up.exe (PID: 2080)
- Creative_Cloud_Set-Up.exe (PID: 2032)
Checks proxy server information
- Creative_Cloud_Set-Up.exe (PID: 2080)
- mshta.exe (PID: 4052)
- mshta.exe (PID: 1028)
- Creative_Cloud_Set-Up.exe (PID: 2032)
Process checks are UAC notifies on
- Creative_Cloud_Set-Up.exe (PID: 2080)
- Creative_Cloud_Set-Up.exe (PID: 2032)
Reads Internet Explorer settings
- mshta.exe (PID: 4052)
- mshta.exe (PID: 1028)
The process uses the downloaded file
- cmd.exe (PID: 3332)
- powershell.exe (PID: 3440)
- cmd.exe (PID: 3984)
- powershell.exe (PID: 1680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
77
Monitored processes
25
Malicious processes
10
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 720 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\PhotoshopBeta24.7ActivatorAIGenerativeFill_DownloadPirate.com\3. Utilities\bypass payment\Patch.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 980 | net session | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1028 | mshta vbscript:CreateObject("Shell.Application").ShellExecute("cmd","/c C:\Users\admin\AppData\Local\Temp\PHOTOS~1.COM\37966~1.UTI\BYPASS~1\Patch.bat ::","","runas",1)(window.close) | C:\Windows\System32\mshta.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1048 | C:\Windows\system32\net1 session | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1208 | net session | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1528 | net session | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1680 | powershell -ExecutionPolicy RemoteSigned -File .\portable.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
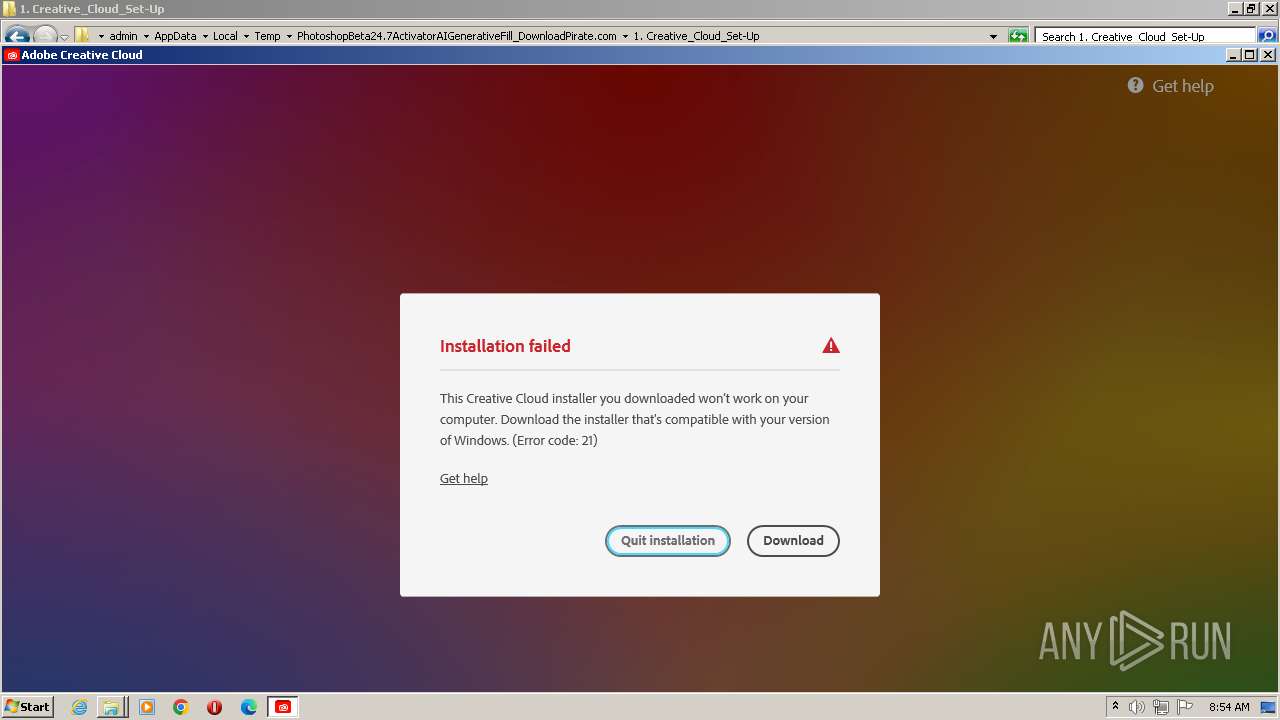
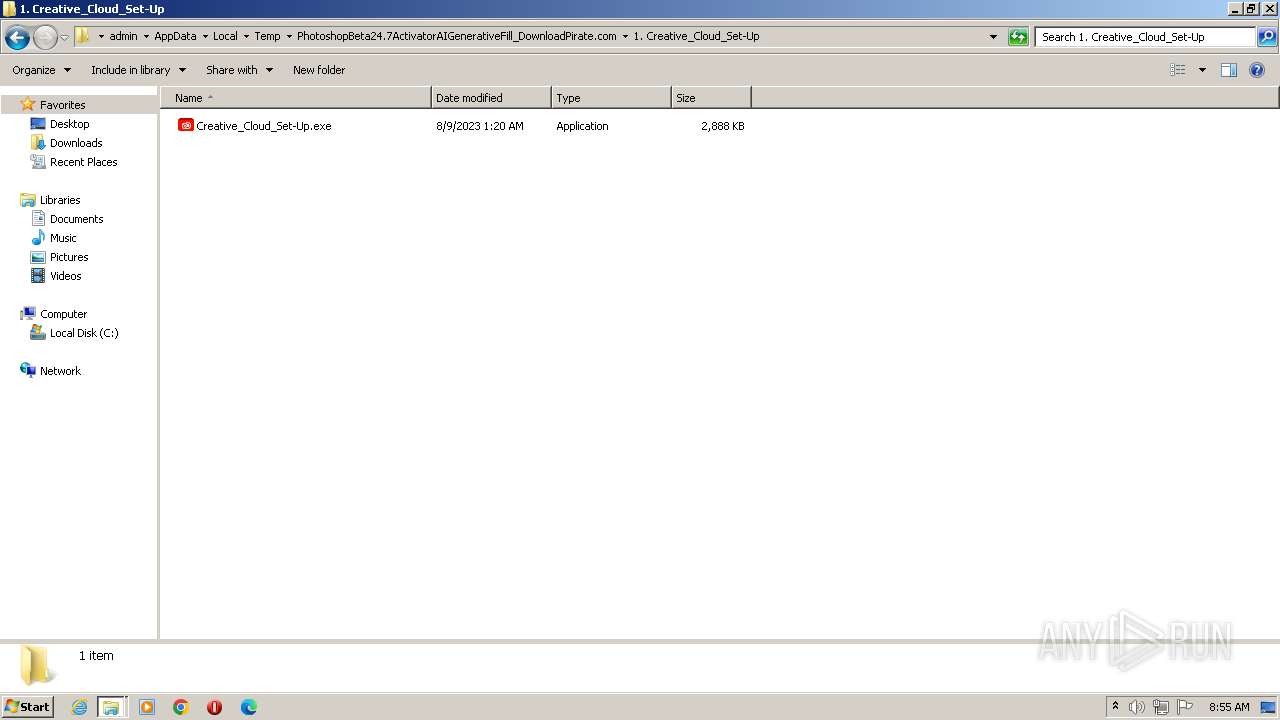
| 2032 | "C:\Users\admin\AppData\Local\Temp\PhotoshopBeta24.7ActivatorAIGenerativeFill_DownloadPirate.com\1. Creative_Cloud_Set-Up\Creative_Cloud_Set-Up.exe" | C:\Users\admin\AppData\Local\Temp\PhotoshopBeta24.7ActivatorAIGenerativeFill_DownloadPirate.com\1. Creative_Cloud_Set-Up\Creative_Cloud_Set-Up.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Inc. Integrity Level: MEDIUM Description: Adobe Installer Exit code: 0 Version: 2.11.0.30 Modules
| |||||||||||||||
| 2080 | "C:\Users\admin\AppData\Local\Temp\PhotoshopBeta24.7ActivatorAIGenerativeFill_DownloadPirate.com\1. Creative_Cloud_Set-Up\Creative_Cloud_Set-Up.exe" | C:\Users\admin\AppData\Local\Temp\PhotoshopBeta24.7ActivatorAIGenerativeFill_DownloadPirate.com\1. Creative_Cloud_Set-Up\Creative_Cloud_Set-Up.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Inc. Integrity Level: MEDIUM Description: Adobe Installer Exit code: 0 Version: 2.11.0.30 Modules
| |||||||||||||||
| 2384 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
9 391
Read events
9 163
Write events
228
Delete events
0
Modification events
| (PID) Process: | (3488) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3488) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3488) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3488) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3488) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3488) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3488) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3488) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3488) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3488) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
6
Suspicious files
25
Text files
32
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\PhotoshopBeta24.7ActivatorAIGenerativeFill_DownloadPirate.com\2. CCStopper_v1.2.2-hotfix.1\scripts\FirewallBlock.ps1 | text | |
MD5:E5A8737939EC235AA748D9172E758833 | SHA256:49320F6F67EAEA3929184F43B6143BC823C4C5042E94026EFCE6071F8AB48036 | |||
| 3488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\PhotoshopBeta24.7ActivatorAIGenerativeFill_DownloadPirate.com\2. CCStopper_v1.2.2-hotfix.1\scripts\Functions.ps1 | text | |
MD5:BF4369A88EF0580936630DDBEB9758CB | SHA256:497A25B71D74DEFCBB41E5F40627F4839208730892C732C068793E5679D1B838 | |||
| 3488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\PhotoshopBeta24.7ActivatorAIGenerativeFill_DownloadPirate.com\2. CCStopper_v1.2.2-hotfix.1\scripts\HostBlock.ps1 | text | |
MD5:838F6831A5C48880D1ABF67D8EFF0340 | SHA256:FACA2A0503B830F1FA8918362568DD4E455364F6C820B5BC430B6A5EC4311015 | |||
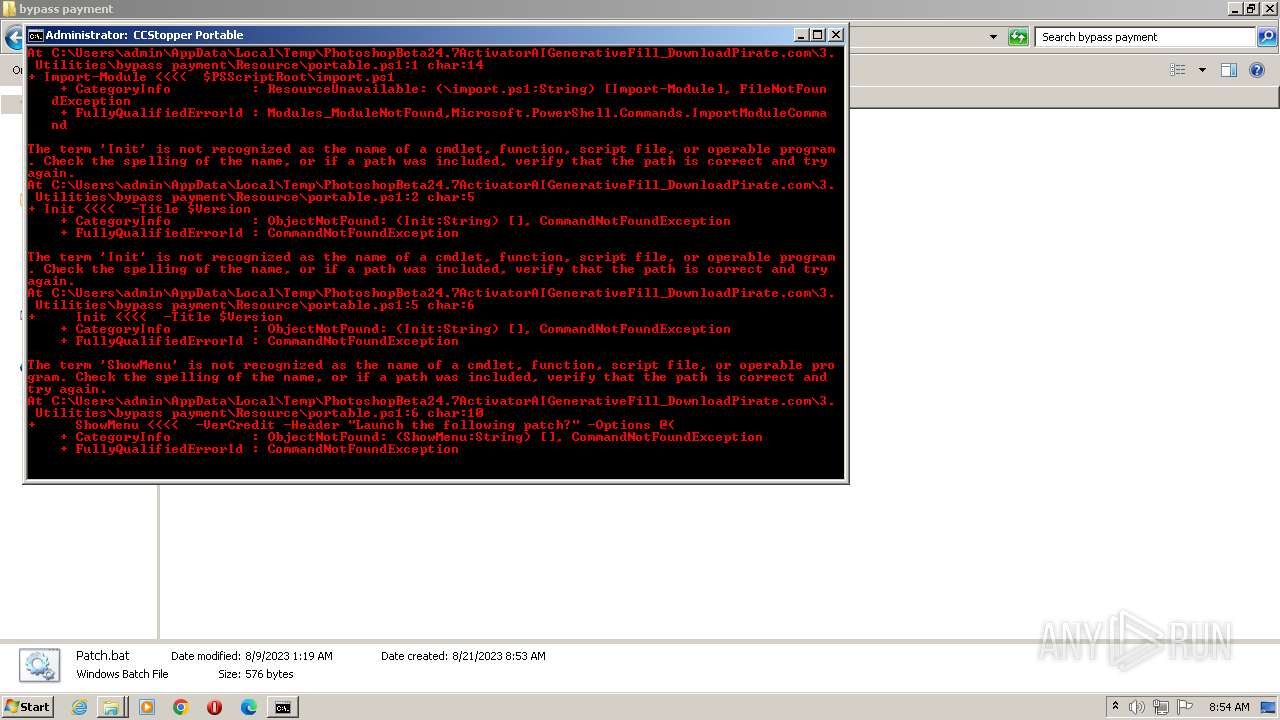
| 3488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\PhotoshopBeta24.7ActivatorAIGenerativeFill_DownloadPirate.com\3. Utilities\bypass payment\Resource\import.ps1 | text | |
MD5:DFEA6576CCC0FC7E2BAC188EF68E612A | SHA256:12E9A9B1B6F6720E4A0BCB7F8D8D5FE605AFFBD2A56BC6552A96BB29F4439F49 | |||
| 3488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\PhotoshopBeta24.7ActivatorAIGenerativeFill_DownloadPirate.com\3. Utilities\bypass payment\Resource\portable.ps1 | text | |
MD5:0ABF702B10BDDDC9B9795347B6684D20 | SHA256:9D415506811C8951D97E805E4E530D792FCC11FF3F8FB7AD2A2D157E110BAB3B | |||
| 3488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\PhotoshopBeta24.7ActivatorAIGenerativeFill_DownloadPirate.com\2. CCStopper_v1.2.2-hotfix.1\scripts\RemoveAGS.ps1 | text | |
MD5:D6531922C8057CAC8215AD38957D7297 | SHA256:E3399022827DB98D488485C8784A5B002B90B4D756ECA6C6E5BF965B8826AF96 | |||
| 3488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\PhotoshopBeta24.7ActivatorAIGenerativeFill_DownloadPirate.com\3. Utilities\bypass payment\Resource\module.ps1 | text | |
MD5:F793A64C786EB54630806118368D415A | SHA256:190FA9CAB2F8C76DE77A1EBAC3554F17671487C1A5DA134E49AEE576AC3ECB60 | |||
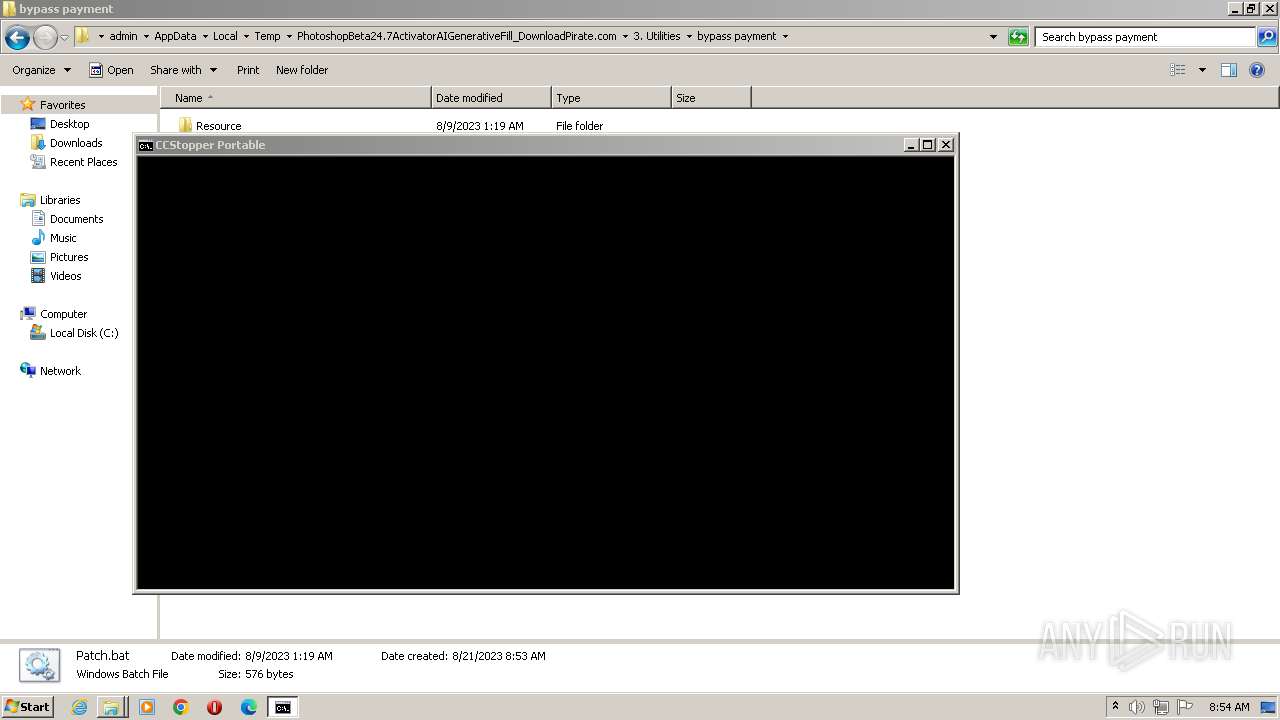
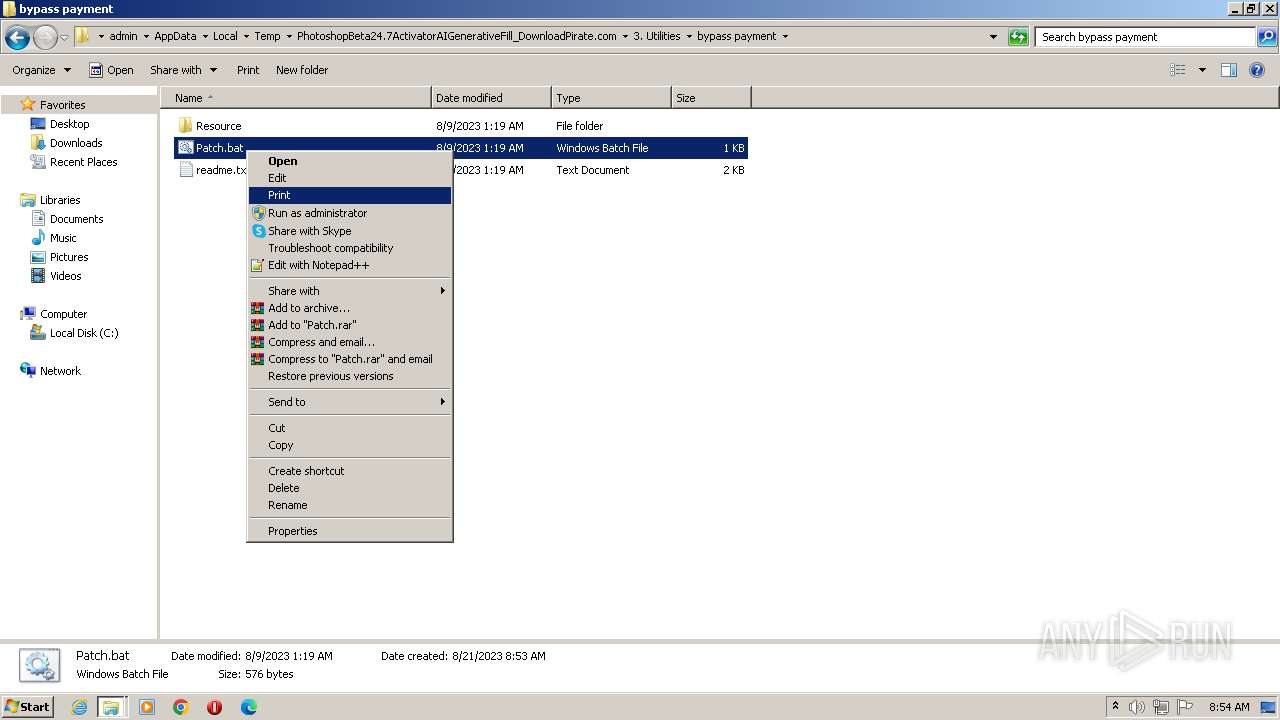
| 3488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\PhotoshopBeta24.7ActivatorAIGenerativeFill_DownloadPirate.com\3. Utilities\bypass payment\Patch.bat | text | |
MD5:17242BB383F1F5A2362A0BECD66A591D | SHA256:C574D4BA81A60BCCF241530040A3015CEBF55A3724B92B5472288FB15813C02C | |||
| 3488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\PhotoshopBeta24.7ActivatorAIGenerativeFill_DownloadPirate.com\2. CCStopper_v1.2.2-hotfix.1\scripts\StopProcesses.ps1 | text | |
MD5:3B12E6A24316FA36DEF8E05177E34049 | SHA256:2EEFD0B5DDF105B65EA581DCD9F02C6F72AD495F152B6795B3BC0B78FCACD2DA | |||
| 3488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\PhotoshopBeta24.7ActivatorAIGenerativeFill_DownloadPirate.com\3. Utilities\bypass unlicensed disablements\Resource\module.ps1 | text | |
MD5:BAACA908AF09AA68CF566A17B1B57427 | SHA256:6094A61999B63AB7081AE4B3B0359CB46633DAB7851A8270B668E4713387F15F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
15
DNS requests
11
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2032 | Creative_Cloud_Set-Up.exe | GET | 200 | 192.229.221.95:80 | http://crl3.digicert.com/DigiCertGlobalRootG2.crl | US | binary | 1.10 Kb | whitelisted |
2032 | Creative_Cloud_Set-Up.exe | GET | 200 | 178.79.242.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e74d6e88368726d2 | DE | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2080 | Creative_Cloud_Set-Up.exe | 13.32.99.117:443 | client.messaging.adobe.com | AMAZON-02 | US | suspicious |
2032 | Creative_Cloud_Set-Up.exe | 178.79.242.128:80 | ctldl.windowsupdate.com | LLNW | DE | malicious |
2032 | Creative_Cloud_Set-Up.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2080 | Creative_Cloud_Set-Up.exe | 54.74.179.44:443 | cc-api-data.adobe.io | AMAZON-02 | IE | suspicious |
2032 | Creative_Cloud_Set-Up.exe | 54.77.72.255:443 | cc-api-data.adobe.io | AMAZON-02 | IE | suspicious |
2032 | Creative_Cloud_Set-Up.exe | 178.79.242.0:80 | ctldl.windowsupdate.com | LLNW | DE | whitelisted |
2032 | Creative_Cloud_Set-Up.exe | 13.32.99.117:443 | client.messaging.adobe.com | AMAZON-02 | US | suspicious |
2032 | Creative_Cloud_Set-Up.exe | 13.32.99.32:443 | client.messaging.adobe.com | AMAZON-02 | US | suspicious |
2080 | Creative_Cloud_Set-Up.exe | 13.32.99.120:443 | client.messaging.adobe.com | AMAZON-02 | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
client.messaging.adobe.com |
| whitelisted |
cc-api-data.adobe.io |
| whitelisted |
dns.msftncsi.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Malware Command and Control Activity Detected | ET MALWARE FormBook CnC Checkin (GET) |