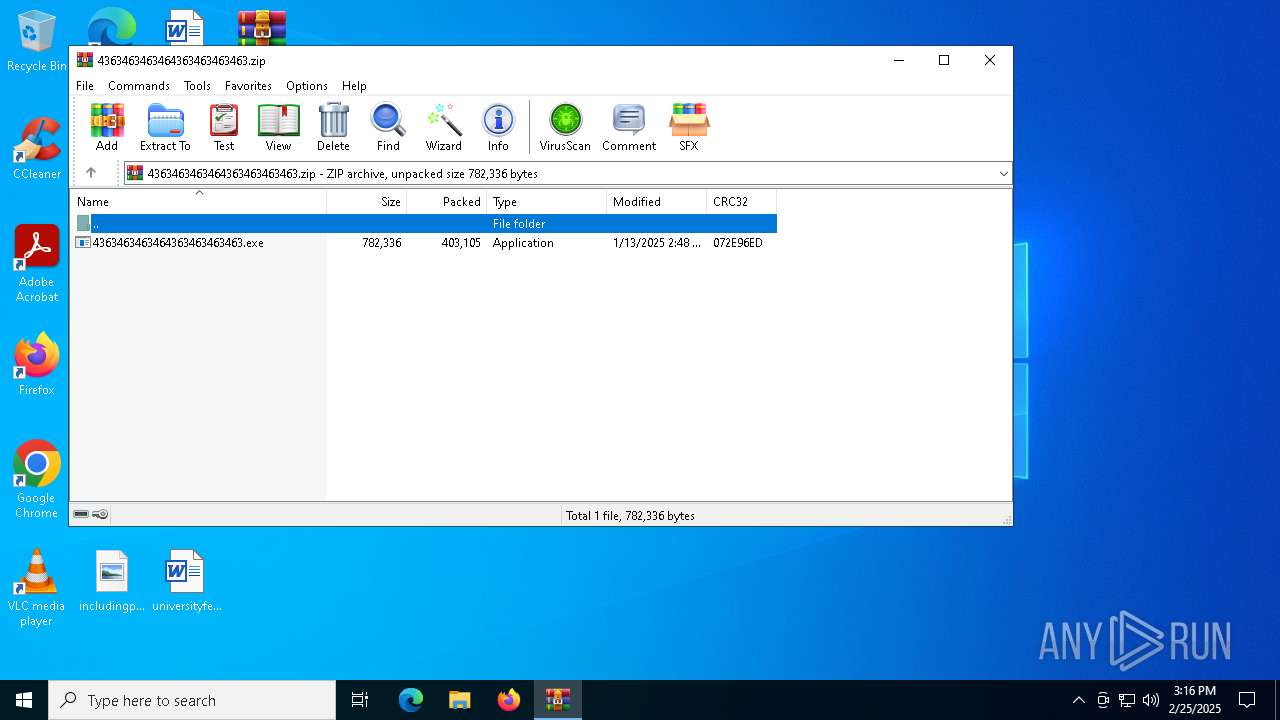
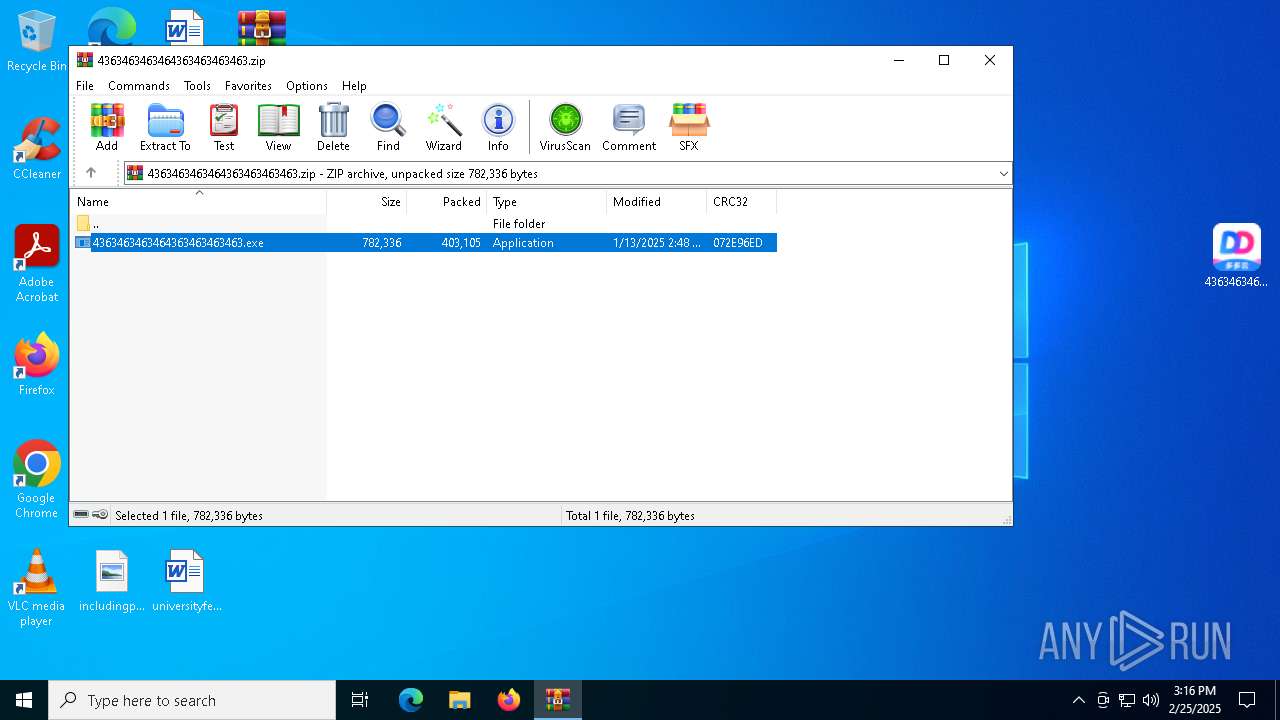
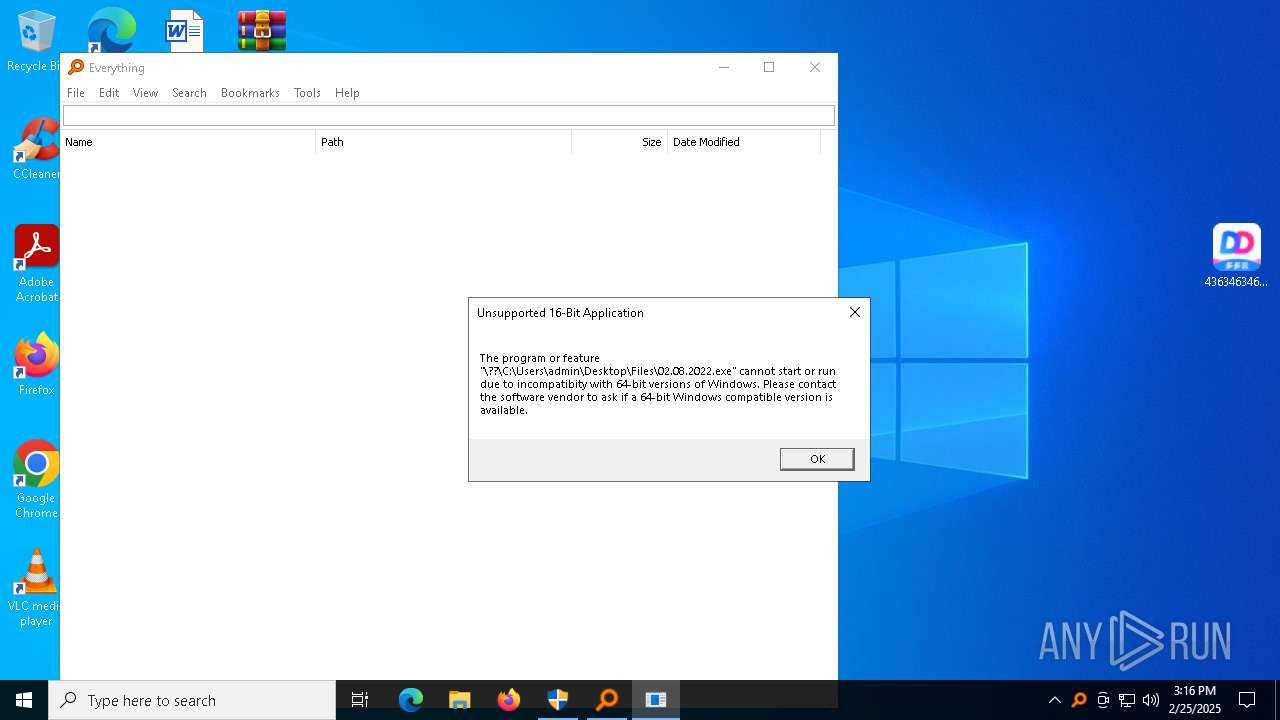
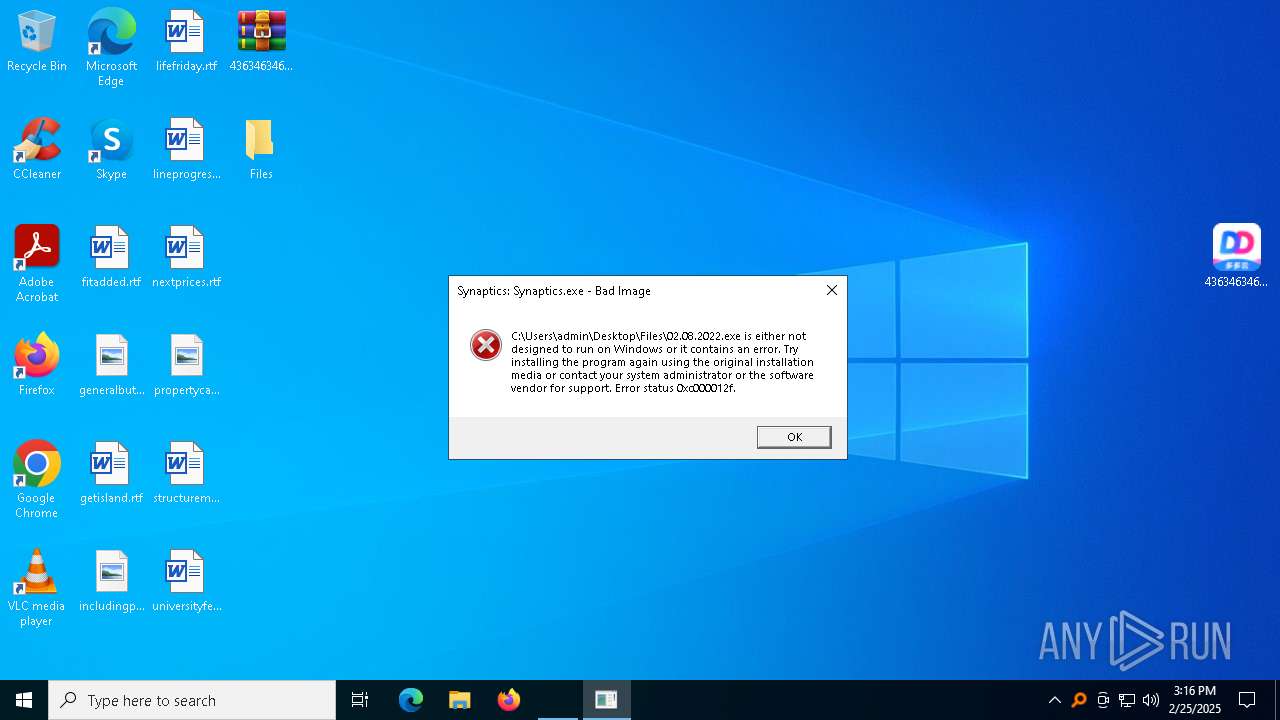
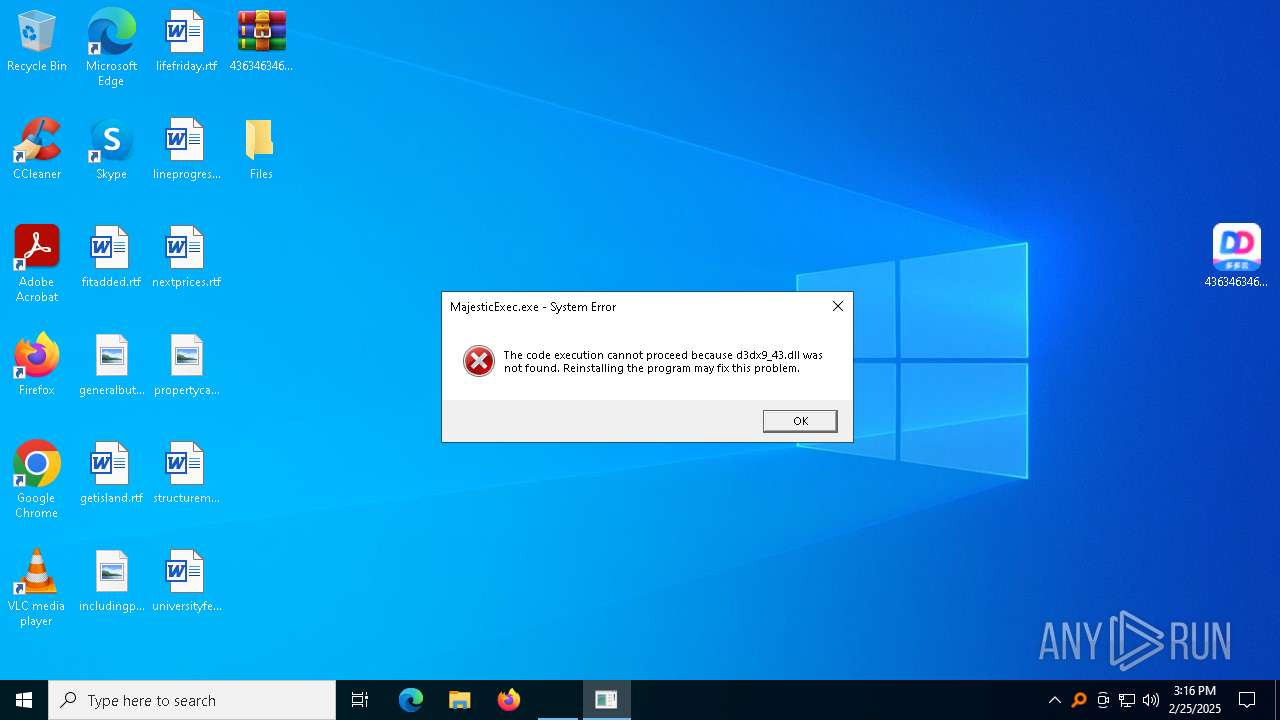
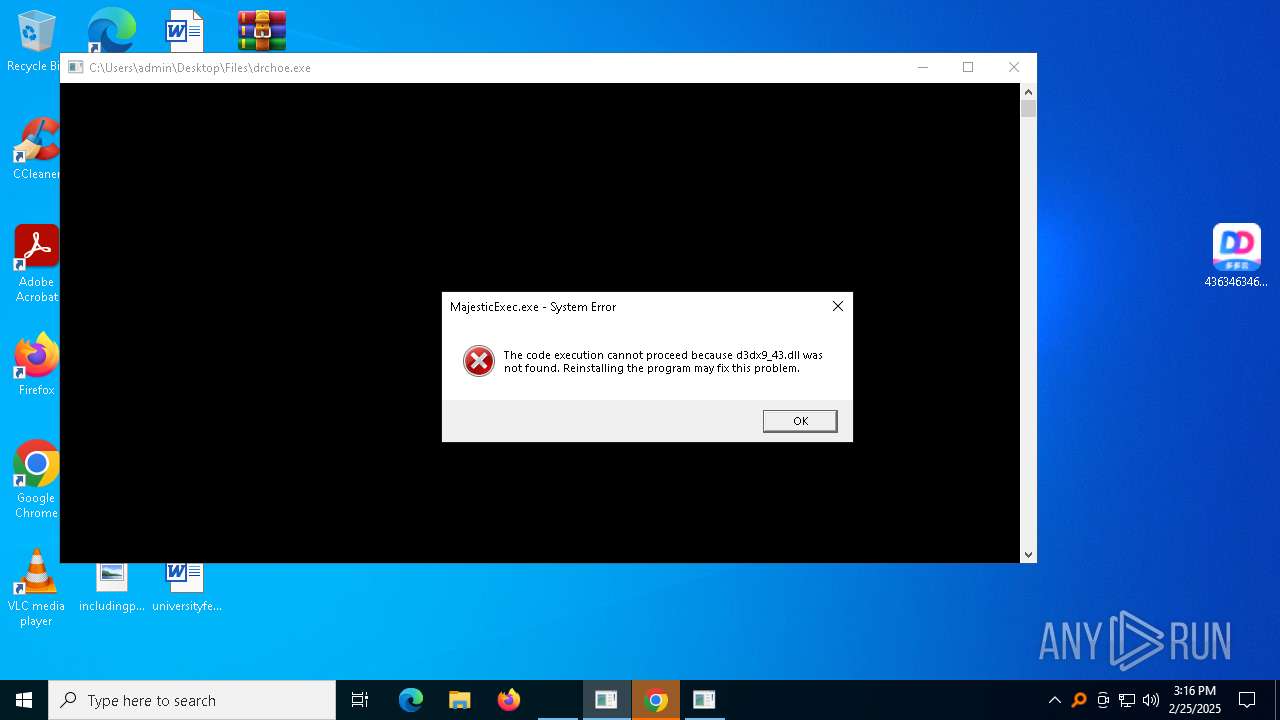
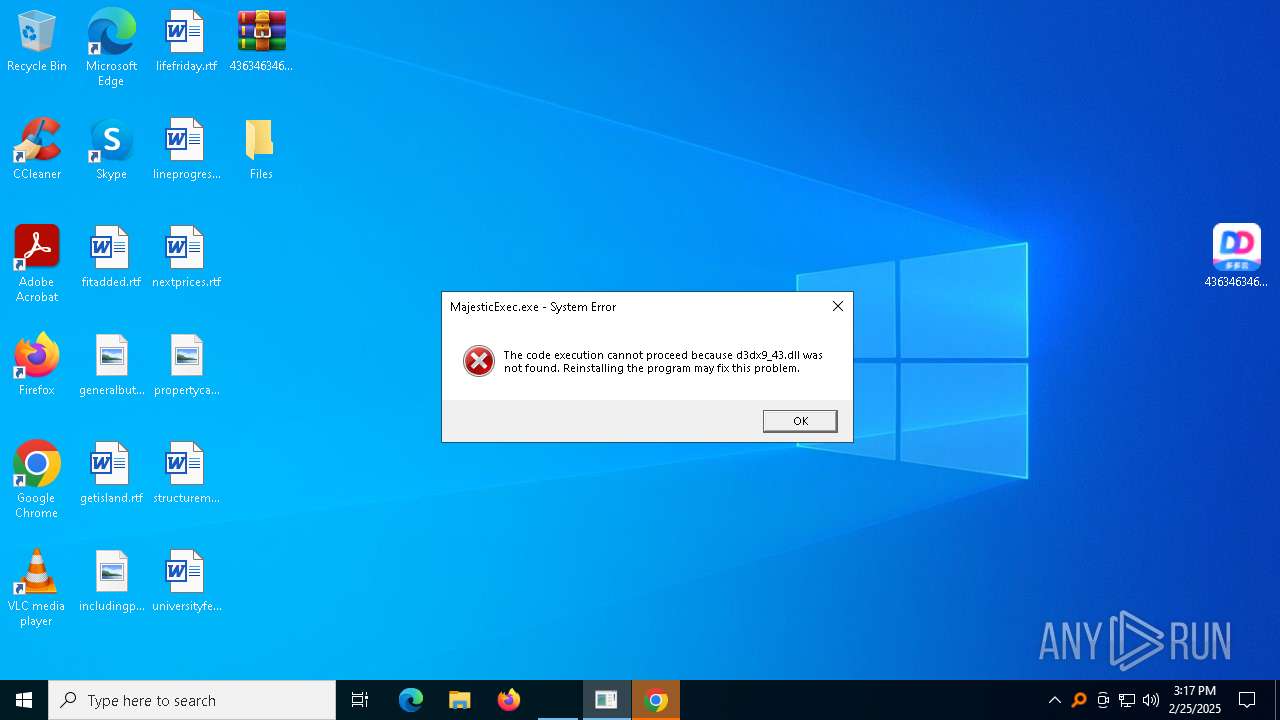
| File name: | 4363463463464363463463463.zip |
| Full analysis: | https://app.any.run/tasks/ca9aff22-8d6e-4a03-85a8-21cf103bb882 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | February 25, 2025, 15:15:55 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | C223234ED4E0BC5325C0B09744F06B6D |
| SHA1: | ECFDD884EE353CEB205BE8729EB683AECA5CCE2E |
| SHA256: | FDA46BAACB7DCD211250FE29AAA2B1B17657961675B4D8C6415A0C3D004D00A6 |
| SSDEEP: | 12288:bnUmkv+JURdK9g4Dem8nPvb+9FovfK289mOXzLcqxNOJlYb6:bnUmI+JURdig4Dem8nPD+9Foq79mOXzU |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6420)
XRED mutex has been found
- 4363463463464363463463463.exe (PID: 7124)
- Synaptics.exe (PID: 5000)
Changes the autorun value in the registry
- 4363463463464363463463463.exe (PID: 7124)
- rapes.exe (PID: 5096)
- explorer.exe (PID: 9936)
GENERIC has been found (auto)
- ._cache_4363463463464363463463463.exe (PID: 6392)
- BitLockerToGo.exe (PID: 8688)
- TH5VZLUXU8YMPLO7BGZOWA5.exe (PID: 9804)
- BitLockerToGo.exe (PID: 11192)
- 1780920692.exe (PID: 7704)
LUMMA has been found (auto)
- ._cache_4363463463464363463463463.exe (PID: 6392)
- ._cache_4363463463464363463463463.exe (PID: 6392)
METERPRETER has been detected (SURICATA)
- ._cache_4363463463464363463463463.exe (PID: 6392)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2192)
- Yg1HwMX.exe (PID: 5872)
- MegVlau.exe (PID: 7144)
- HzSVdBl.exe (PID: 7224)
- HMqdrvG.exe (PID: 8532)
- cfc53e19dd.exe (PID: 3988)
- bb20675cd6.exe (PID: 8180)
- 34647a8c61.exe (PID: 10220)
- HMqdrvG.exe (PID: 2388)
- 8NsQP4U.exe (PID: 7852)
- HzSVdBl.exe (PID: 5788)
Connects to the CnC server
- svchost.exe (PID: 2192)
- Fz7SAggvHD.exe (PID: 7472)
- sysnldcvmr.exe (PID: 7820)
- TH5VZLUXU8YMPLO7BGZOWA5.exe (PID: 9804)
- SearchUII.exe (PID: 8104)
AMADEY mutex has been found
- random.exe (PID: 5572)
- rapes.exe (PID: 5096)
- rapes.exe (PID: 5004)
- rapes.exe (PID: 9440)
- 8O1O21E9HCK5E6L2K.exe (PID: 9748)
- rapes.exe (PID: 12188)
Actions looks like stealing of personal data
- 1.exe (PID: 6820)
- k360.exe (PID: 6536)
- Yg1HwMX.exe (PID: 5872)
- MegVlau.exe (PID: 7144)
- main1.exe (PID: 6396)
- chrome.exe (PID: 7328)
- HzSVdBl.exe (PID: 7224)
- msedge.exe (PID: 8664)
AMADEY has been detected (SURICATA)
- rapes.exe (PID: 5096)
STEALER has been found (auto)
- ._cache_4363463463464363463463463.exe (PID: 6392)
- ._cache_4363463463464363463463463.exe (PID: 6392)
VIDAR mutex has been found
- Stealer.exe (PID: 6096)
Starts CMD.EXE for self-deleting
- Stealer.exe (PID: 6096)
StealC has been detected
- vtoroy.exe (PID: 5268)
- TH5VZLUXU8YMPLO7BGZOWA5.exe (PID: 9804)
Steals credentials from Web Browsers
- Stealer.exe (PID: 6096)
- Yg1HwMX.exe (PID: 5872)
- main1.exe (PID: 6396)
- MegVlau.exe (PID: 7144)
- HzSVdBl.exe (PID: 7224)
Executing a file with an untrusted certificate
- MegVlau.exe (PID: 648)
- MegVlau.exe (PID: 6364)
- MegVlau.exe (PID: 7144)
- jIZ93PY.exe (PID: 7564)
- crypted_UClient.exe (PID: 11464)
- f86nrrc6.exe (PID: 5872)
- UClient.exe (PID: 10348)
LUMMA mutex has been found
- Yg1HwMX.exe (PID: 5872)
- MegVlau.exe (PID: 7144)
- HzSVdBl.exe (PID: 7224)
- HMqdrvG.exe (PID: 8532)
- cfc53e19dd.exe (PID: 3988)
- bb20675cd6.exe (PID: 8180)
- 34647a8c61.exe (PID: 10220)
HAUSBOMBER has been detected (YARA)
- ._cache_4363463463464363463463463.exe (PID: 6392)
ASYNCRAT has been found (auto)
- ._cache_4363463463464363463463463.exe (PID: 6392)
- ddosziller.exe (PID: 9864)
Adds extension to the Windows Defender exclusion list
- Miner.exe (PID: 4872)
- whrbuflqwhah.exe (PID: 6068)
- powershell.exe (PID: 7236)
- cmd.exe (PID: 11004)
DCRAT has been detected (YARA)
- ._cache_4363463463464363463463463.exe (PID: 6392)
QUASARRAT has been found (auto)
- example_win32_dx11.exe (PID: 7148)
- RuntimeBroker.exe (PID: 5856)
- Java.exe (PID: 836)
Adds path to the Windows Defender exclusion list
- taskhost.exe (PID: 5256)
- loader.exe (PID: 9800)
Changes powershell execution policy (Bypass)
- taskhost.exe (PID: 5256)
Bypass execution policy to execute commands
- powershell.exe (PID: 7556)
- powershell.exe (PID: 8692)
Uninstalls Malicious Software Removal Tool (MRT)
- cmd.exe (PID: 7260)
- cmd.exe (PID: 8660)
Application was injected by another process
- winlogon.exe (PID: 684)
- lsass.exe (PID: 760)
- svchost.exe (PID: 320)
- dwm.exe (PID: 912)
- svchost.exe (PID: 1260)
- svchost.exe (PID: 1424)
- svchost.exe (PID: 1500)
- svchost.exe (PID: 1364)
- svchost.exe (PID: 1564)
- svchost.exe (PID: 1452)
- svchost.exe (PID: 1908)
- svchost.exe (PID: 1784)
- svchost.exe (PID: 1660)
- svchost.exe (PID: 1972)
- svchost.exe (PID: 1880)
- svchost.exe (PID: 1768)
- svchost.exe (PID: 1776)
- svchost.exe (PID: 2192)
- svchost.exe (PID: 2064)
- svchost.exe (PID: 1980)
- svchost.exe (PID: 1276)
- svchost.exe (PID: 1068)
- svchost.exe (PID: 1268)
- svchost.exe (PID: 1316)
- svchost.exe (PID: 2340)
- svchost.exe (PID: 2364)
- svchost.exe (PID: 2272)
- svchost.exe (PID: 2372)
- svchost.exe (PID: 2500)
- spoolsv.exe (PID: 2652)
- svchost.exe (PID: 2852)
- svchost.exe (PID: 2748)
- svchost.exe (PID: 2816)
- svchost.exe (PID: 2920)
- svchost.exe (PID: 2892)
- svchost.exe (PID: 2944)
- OfficeClickToRun.exe (PID: 2884)
- svchost.exe (PID: 3016)
- svchost.exe (PID: 2288)
- svchost.exe (PID: 2360)
- svchost.exe (PID: 2256)
- svchost.exe (PID: 3704)
- svchost.exe (PID: 3600)
- svchost.exe (PID: 3824)
- dasHost.exe (PID: 3896)
- svchost.exe (PID: 4176)
- svchost.exe (PID: 4000)
- sihost.exe (PID: 1712)
- svchost.exe (PID: 2952)
- svchost.exe (PID: 4436)
- svchost.exe (PID: 4168)
- svchost.exe (PID: 3668)
- explorer.exe (PID: 4488)
- ctfmon.exe (PID: 4268)
- svchost.exe (PID: 4696)
- svchost.exe (PID: 2660)
- svchost.exe (PID: 3592)
- svchost.exe (PID: 3164)
- svchost.exe (PID: 3160)
- RuntimeBroker.exe (PID: 4676)
- svchost.exe (PID: 3976)
- dllhost.exe (PID: 5904)
- ApplicationFrameHost.exe (PID: 6108)
- svchost.exe (PID: 1340)
- svchost.exe (PID: 812)
- UserOOBEBroker.exe (PID: 3004)
- svchost.exe (PID: 4456)
- svchost.exe (PID: 4200)
- svchost.exe (PID: 3056)
- svchost.exe (PID: 1764)
- dllhost.exe (PID: 1816)
- uhssvc.exe (PID: 2908)
- RuntimeBroker.exe (PID: 4960)
- dllhost.exe (PID: 5164)
- RuntimeBroker.exe (PID: 5820)
- MoUsoCoreWorker.exe (PID: 4712)
- svchost.exe (PID: 4596)
- RuntimeBroker.exe (PID: 6908)
- WmiPrvSE.exe (PID: 2728)
- svchost.exe (PID: 2132)
- WmiPrvSE.exe (PID: 6872)
- svchost.exe (PID: 1176)
- svchost.exe (PID: 376)
- svchost.exe (PID: 4188)
- svchost.exe (PID: 3628)
- RuntimeBroker.exe (PID: 8472)
- svchost.exe (PID: 8160)
- svchost.exe (PID: 7944)
- audiodg.exe (PID: 5712)
- WerFault.exe (PID: 6708)
- TrustedInstaller.exe (PID: 9964)
- svchost.exe (PID: 10736)
- WmiPrvSE.exe (PID: 14252)
Runs injected code in another process
- dialer.exe (PID: 5780)
- dialer.exe (PID: 8632)
- powershell.exe (PID: 7236)
DARKCRYSTAL has been detected (SURICATA)
- Fz7SAggvHD.exe (PID: 7472)
Adds process to the Windows Defender exclusion list
- taskhost.exe (PID: 5256)
XWORM has been detected (SURICATA)
- cvrMRi04XB.exe (PID: 7420)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2192)
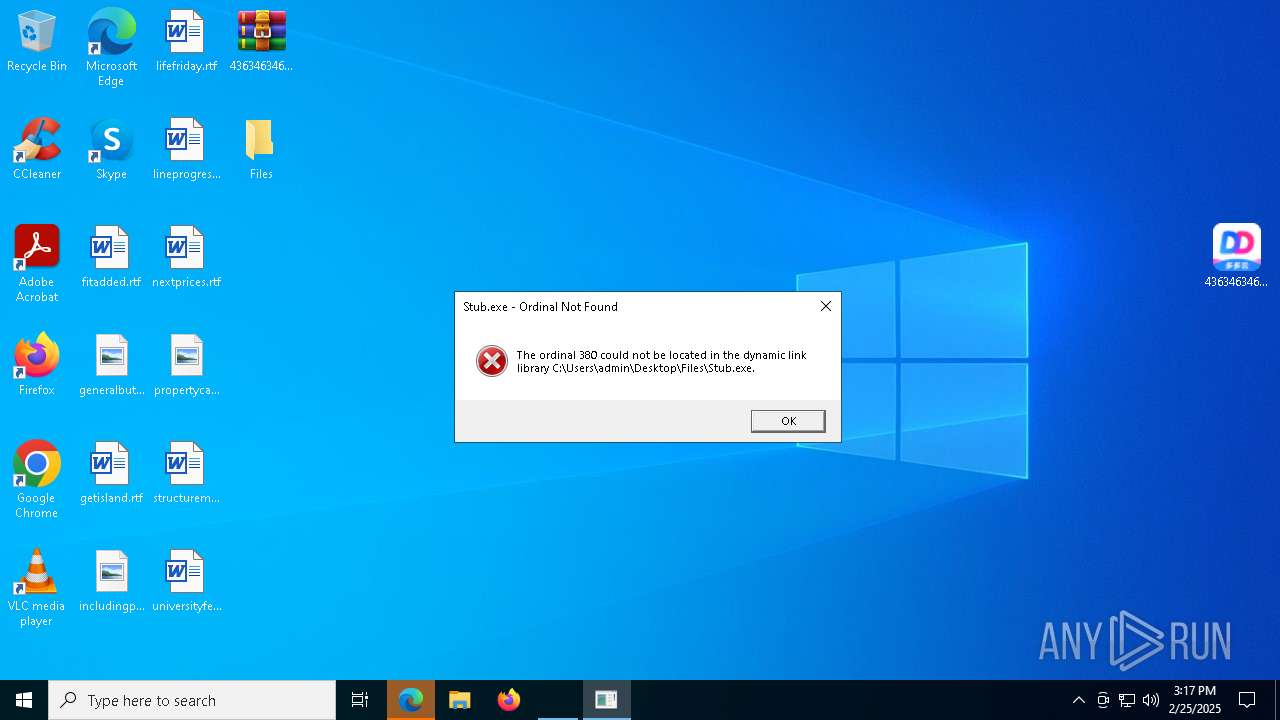
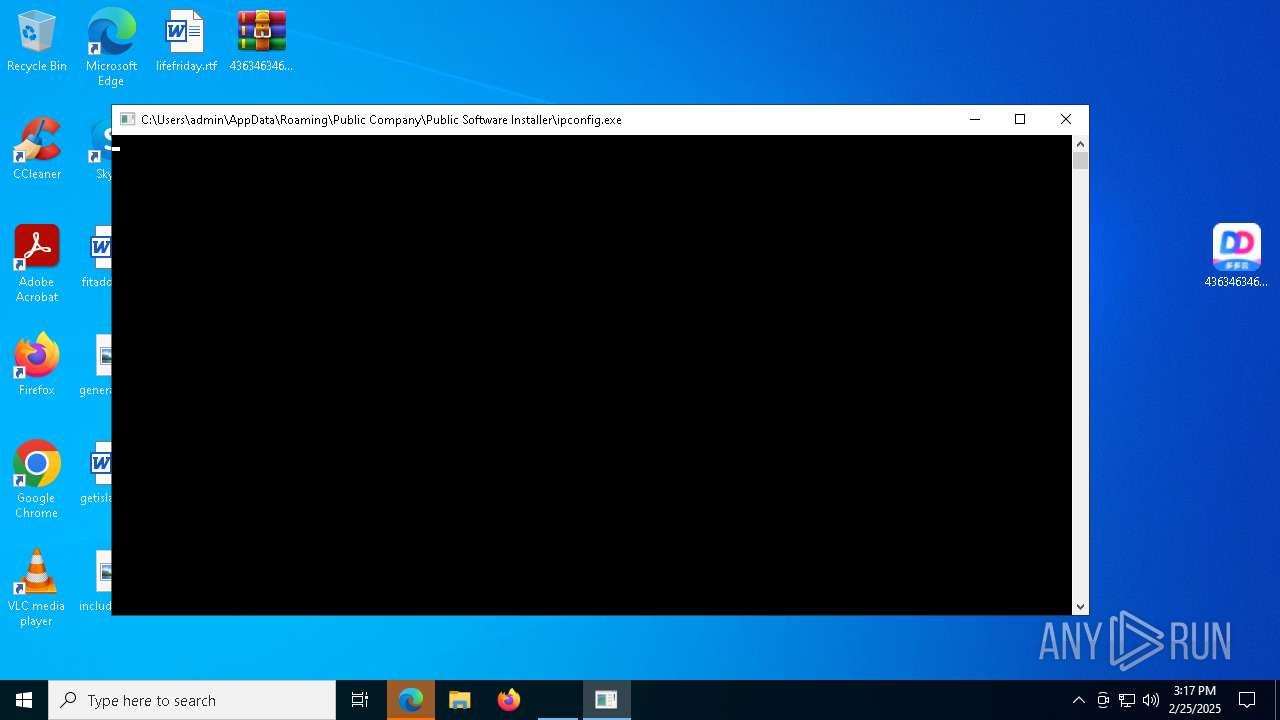
The DLL Hijacking
- ipconfig.exe (PID: 6788)
AMADEY has been detected (YARA)
- rapes.exe (PID: 5096)
Uses Task Scheduler to autorun other applications
- RuntimeBroker.exe (PID: 5856)
- RuntimeBroker.exe (PID: 9288)
- discordupdate.exe (PID: 9672)
- msinfo32.exe (PID: 9992)
- Java.exe (PID: 836)
- java.exe (PID: 9340)
- cmd.exe (PID: 9076)
- seksiak.exe (PID: 7240)
- JUSCHED.EXE (PID: 9864)
- msinfo32.exe (PID: 9672)
- jusched.exe (PID: 8876)
- java.exe (PID: 7672)
- seksiak.exe (PID: 9440)
- msinfo32.exe (PID: 10852)
- java.exe (PID: 7076)
- seksiak.exe (PID: 10680)
- msinfo32.exe (PID: 11568)
- seksiak.exe (PID: 8660)
- java.exe (PID: 11204)
- msinfo32.exe (PID: 12280)
- seksiak.exe (PID: 11308)
- java.exe (PID: 11792)
- msinfo32.exe (PID: 11756)
- seksiak.exe (PID: 10732)
- java.exe (PID: 11576)
- msinfo32.exe (PID: 6900)
- java.exe (PID: 1852)
- seksiak.exe (PID: 12216)
QUASAR has been found (auto)
- discordupdate.exe (PID: 9672)
RHADAMANTHYS has been found (auto)
- ._cache_4363463463464363463463463.exe (PID: 6392)
Possible tool for stealing has been detected
- explorer.exe (PID: 4488)
- firefox.exe (PID: 9440)
- 9593da7e83.exe (PID: 9460)
- firefox.exe (PID: 5588)
ASYNCRAT has been detected (MUTEX)
- ddosziller.exe (PID: 9864)
- tesst.exe (PID: 10020)
RHADAMANTHYS mutex has been found
- zeropersca.exe (PID: 6892)
- fontdrvhost.exe (PID: 2736)
- Loader.exe (PID: 9924)
- dialer.exe (PID: 8496)
PHORPIEX mutex has been found
- twztl.exe (PID: 7744)
- sysnldcvmr.exe (PID: 7820)
- t1.exe (PID: 7824)
XWORM has been detected
- XClient.exe (PID: 9880)
PHORPIEX has been detected (SURICATA)
- sysnldcvmr.exe (PID: 7820)
RAT has been found (auto)
- ._cache_4363463463464363463463463.exe (PID: 6392)
GCLEANER has been detected (SURICATA)
- BitLockerToGo.exe (PID: 8688)
- BitLockerToGo.exe (PID: 11192)
STEALC has been detected (SURICATA)
- TH5VZLUXU8YMPLO7BGZOWA5.exe (PID: 9804)
NJRAT mutex has been found
- sela.exe (PID: 9552)
Run PowerShell with an invisible window
- powershell.exe (PID: 11180)
- powershell.exe (PID: 7236)
RUSTYSTEALER has been found (auto)
- crypted_UClient.exe (PID: 11464)
Uses Task Scheduler to run other applications
- crypted_UClient.exe (PID: 11464)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 7236)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 7236)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 7236)
NJRAT has been detected (SURICATA)
- SearchUII.exe (PID: 8104)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 7236)
OMANI has been detected
- powershell.exe (PID: 7236)
Starts NET.EXE for service management
- net.exe (PID: 13988)
- cmd.exe (PID: 12640)
Changes Controlled Folder Access settings
- powershell.exe (PID: 6792)
Changes antivirus protection settings for downloading files from the Internet (IOAVProtection)
- powershell.exe (PID: 6792)
Changes settings for protection against network attacks (IPS)
- powershell.exe (PID: 6792)
Changes settings for sending potential threat samples to Microsoft servers
- powershell.exe (PID: 6792)
Changes settings for reporting to Microsoft Active Protection Service (MAPS)
- powershell.exe (PID: 6792)
Changes settings for real-time protection
- powershell.exe (PID: 6792)
Changes settings for checking scripts for malicious actions
- powershell.exe (PID: 6792)
UMBRALSTEALER has been detected (SURICATA)
- loader.exe (PID: 9800)
QUASAR has been detected (SURICATA)
- powershell.exe (PID: 7236)
DANABOT has been detected (SURICATA)
- ipconfig.exe (PID: 6788)
SUSPICIOUS
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 7124)
- ._cache_4363463463464363463463463.exe (PID: 6392)
- random.exe (PID: 5572)
- Build.exe (PID: 6232)
- rapes.exe (PID: 5096)
- Test2.exe (PID: 4624)
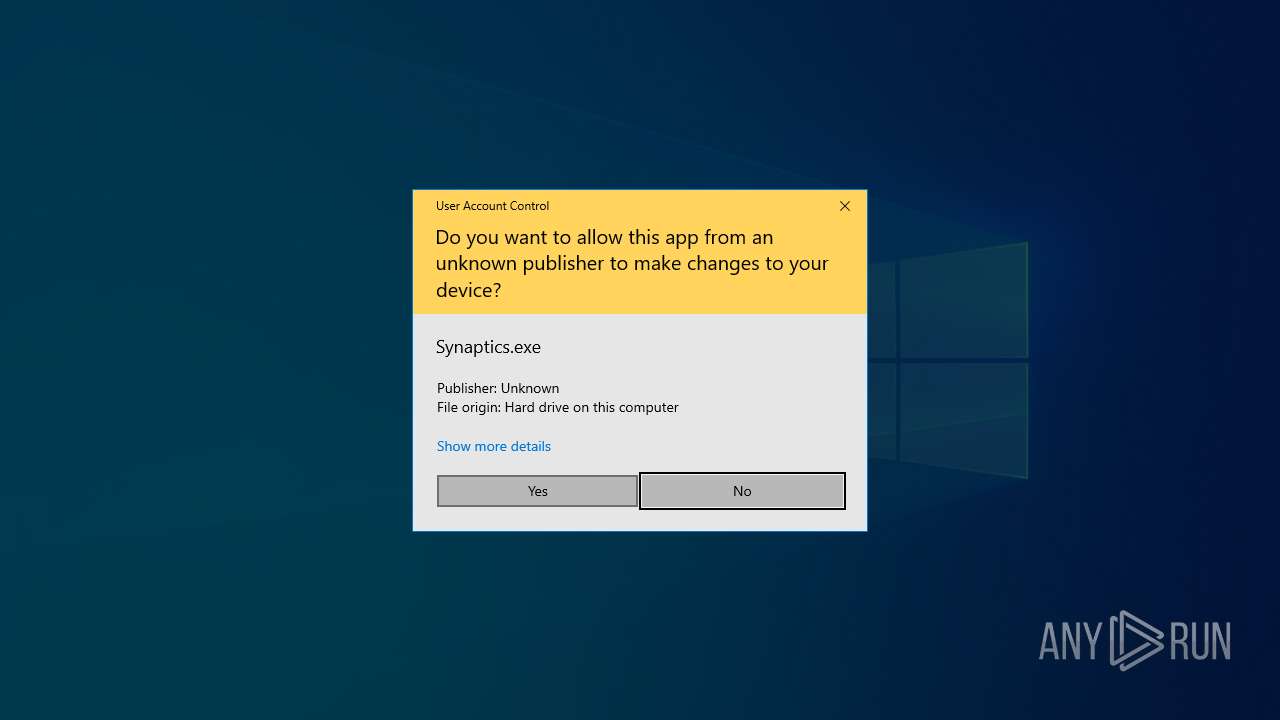
- Synaptics.exe (PID: 5000)
- main1.exe (PID: 6540)
- example_win32_dx11.exe (PID: 7148)
- JhOTKwS.exe (PID: 6032)
- drchoe.exe (PID: 8020)
- Fz7SAggvHD.exe (PID: 7472)
- Miner.exe (PID: 4872)
- whrbuflqwhah.exe (PID: 6068)
- RuntimeBroker.exe (PID: 5856)
- discordupdate.exe (PID: 9672)
- Java.exe (PID: 836)
- ddosziller.exe (PID: 9864)
- twztl.exe (PID: 7744)
- CritScript.exe (PID: 2160)
- 3544436.exe (PID: 10016)
- JUSCHED.EXE (PID: 9864)
- crypteda.exe (PID: 2060)
- XClient.exe (PID: 9880)
- bb20675cd6.exe (PID: 8180)
- explorer.exe (PID: 9936)
- xyaw4fkp.exe (PID: 8844)
- BitLockerToGo.exe (PID: 8688)
- TH5VZLUXU8YMPLO7BGZOWA5.exe (PID: 9804)
- crypted_UClient.exe (PID: 11464)
- BitLockerToGo.exe (PID: 11192)
- 1780920692.exe (PID: 7704)
- 260079166.exe (PID: 11664)
- powershell.exe (PID: 7236)
- jf.exe (PID: 10708)
- svchost.exe (PID: 1340)
- loader.exe (PID: 9800)
- svchosi.exe (PID: 1572)
- App.exe (PID: 10528)
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 7124)
- ._cache_4363463463464363463463463.exe (PID: 6392)
- random.exe (PID: 5572)
- Build.exe (PID: 6232)
- Stealer.exe (PID: 6096)
- Client.exe (PID: 1864)
- Synaptics.exe (PID: 5000)
- taskhost.exe (PID: 5256)
- rapes.exe (PID: 5096)
- Client.exe (PID: 3864)
- 3e3ev3.exe (PID: 9752)
- msinfo32.exe (PID: 9992)
- CritScript.exe (PID: 2160)
- seksiak.exe (PID: 9440)
- Client.exe (PID: 10532)
- java.exe (PID: 7076)
- java.exe (PID: 11576)
- svchoxb.exe (PID: 11476)
Potential Corporate Privacy Violation
- ._cache_4363463463464363463463463.exe (PID: 6392)
- rapes.exe (PID: 5096)
- svchost.exe (PID: 2192)
- main1.exe (PID: 6396)
- bb20675cd6.exe (PID: 8180)
- TH5VZLUXU8YMPLO7BGZOWA5.exe (PID: 9804)
- BitLockerToGo.exe (PID: 8688)
- BitLockerToGo.exe (PID: 11192)
- 1780920692.exe (PID: 7704)
- svchosi.exe (PID: 1572)
Connects to unusual port
- ._cache_4363463463464363463463463.exe (PID: 6392)
- Steanings.exe (PID: 6240)
- system404.exe (PID: 5604)
- cvrMRi04XB.exe (PID: 7420)
- MSBuild.exe (PID: 6160)
- dialer.exe (PID: 8556)
- 25072023.exe (PID: 8520)
- RuntimeBroker.exe (PID: 9288)
- MSBuild.exe (PID: 10224)
- RA4sWoTxlD.exe (PID: 8800)
- fontdrvhost.exe (PID: 2736)
- Client-built.exe (PID: 6800)
- jusched.exe (PID: 8876)
- CFZgWblawj.exe (PID: 8596)
- XClient.exe (PID: 9880)
- dialer.exe (PID: 8496)
- svchost.exe (PID: 9900)
- sela.exe (PID: 9552)
- sysnldcvmr.exe (PID: 7820)
- 5KNCHALAH.exe (PID: 10568)
- SearchUII.exe (PID: 8104)
- crypted_UClient.exe (PID: 11464)
- jf.exe (PID: 10708)
- svchosi.exe (PID: 1572)
- powershell.exe (PID: 7236)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2192)
- rapes.exe (PID: 5096)
- Yg1HwMX.exe (PID: 5872)
- MegVlau.exe (PID: 7144)
- HzSVdBl.exe (PID: 7224)
- cvrMRi04XB.exe (PID: 7420)
- HMqdrvG.exe (PID: 8532)
- cfc53e19dd.exe (PID: 3988)
- bb20675cd6.exe (PID: 8180)
- sysnldcvmr.exe (PID: 7820)
- 34647a8c61.exe (PID: 10220)
- TH5VZLUXU8YMPLO7BGZOWA5.exe (PID: 9804)
- HMqdrvG.exe (PID: 2388)
- 8NsQP4U.exe (PID: 7852)
- HzSVdBl.exe (PID: 5788)
- SearchUII.exe (PID: 8104)
- powershell.exe (PID: 7236)
- ipconfig.exe (PID: 6788)
Process requests binary or script from the Internet
- ._cache_4363463463464363463463463.exe (PID: 6392)
- rapes.exe (PID: 5096)
- bb20675cd6.exe (PID: 8180)
- TH5VZLUXU8YMPLO7BGZOWA5.exe (PID: 9804)
- 1780920692.exe (PID: 7704)
- svchosi.exe (PID: 1572)
Connects to the server without a host name
- ._cache_4363463463464363463463463.exe (PID: 6392)
- rapes.exe (PID: 5096)
- Fz7SAggvHD.exe (PID: 7472)
- sysnldcvmr.exe (PID: 7820)
- bb20675cd6.exe (PID: 8180)
- BitLockerToGo.exe (PID: 8688)
- TH5VZLUXU8YMPLO7BGZOWA5.exe (PID: 9804)
- BitLockerToGo.exe (PID: 11192)
- 1780920692.exe (PID: 7704)
Starts itself from another location
- random.exe (PID: 5572)
- Test2.exe (PID: 4624)
- example_win32_dx11.exe (PID: 7148)
- RuntimeBroker.exe (PID: 5856)
- discordupdate.exe (PID: 9672)
- Java.exe (PID: 836)
- twztl.exe (PID: 7744)
- JUSCHED.EXE (PID: 9864)
Reads the date of Windows installation
- Build.exe (PID: 6232)
- Client.exe (PID: 1864)
- taskhost.exe (PID: 5256)
- Client.exe (PID: 2120)
- Client.exe (PID: 7300)
- svchost.exe (PID: 1668)
- svchost.exe (PID: 10172)
- seksiak.exe (PID: 7240)
- seksiak.exe (PID: 9440)
- msinfo32.exe (PID: 10852)
- 0iMSdYX.exe (PID: 8480)
- svchost.exe (PID: 12184)
- Client.exe (PID: 11424)
- msinfo32.exe (PID: 11756)
BASE64 encoded PowerShell command has been detected
- Build.exe (PID: 6232)
Starts POWERSHELL.EXE for commands execution
- Build.exe (PID: 6232)
- Miner.exe (PID: 4872)
- taskhost.exe (PID: 5256)
- whrbuflqwhah.exe (PID: 6068)
- cmd.exe (PID: 11540)
- cmd.exe (PID: 11764)
- loader.exe (PID: 9800)
- cmd.exe (PID: 11004)
Base64-obfuscated command line is found
- Build.exe (PID: 6232)
Checks Windows Trust Settings
- Stealer.exe (PID: 6096)
- msiexec.exe (PID: 8628)
- rapes.exe (PID: 5096)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6004)
- cmd.exe (PID: 9568)
Starts CMD.EXE for commands execution
- Stealer.exe (PID: 6096)
- Client.exe (PID: 1864)
- svchost.exe (PID: 6004)
- Miner.exe (PID: 4872)
- Client.exe (PID: 2120)
- svchost.exe (PID: 9000)
- svchost.exe (PID: 7384)
- whrbuflqwhah.exe (PID: 6068)
- Client.exe (PID: 7300)
- svchost.exe (PID: 6760)
- Client.exe (PID: 3864)
- svchost.exe (PID: 1668)
- Client.exe (PID: 9732)
- msinfo32.exe (PID: 9992)
- svchost.exe (PID: 10172)
- java.exe (PID: 9340)
- ddosziller.exe (PID: 9864)
- seksiak.exe (PID: 7240)
- svchost.exe (PID: 8908)
- Client.exe (PID: 5460)
- msinfo32.exe (PID: 9672)
- Pichon.exe (PID: 2156)
- java.exe (PID: 7672)
- seksiak.exe (PID: 9440)
- Client.exe (PID: 10532)
- svchost.exe (PID: 10756)
- msinfo32.exe (PID: 10852)
- seksiak.exe (PID: 10680)
- java.exe (PID: 7076)
- Client.exe (PID: 12072)
- svchost.exe (PID: 11932)
- msinfo32.exe (PID: 11568)
- seksiak.exe (PID: 8660)
- java.exe (PID: 11204)
- Client.exe (PID: 11404)
- svchost.exe (PID: 12184)
- 0iMSdYX.exe (PID: 8480)
- msinfo32.exe (PID: 12280)
- seksiak.exe (PID: 11308)
- java.exe (PID: 11792)
- powershell.exe (PID: 11180)
- Client.exe (PID: 11424)
- svchost.exe (PID: 11704)
- msinfo32.exe (PID: 11756)
- cmd.exe (PID: 11764)
- seksiak.exe (PID: 10732)
- java.exe (PID: 11576)
- hell9o.exe (PID: 11448)
- powershell.exe (PID: 7236)
- 1605733096.exe (PID: 2324)
- jf.exe (PID: 10708)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- Stealer.exe (PID: 6096)
- main1.exe (PID: 6396)
Windows Defender mutex has been found
- vtoroy.exe (PID: 5268)
- TH5VZLUXU8YMPLO7BGZOWA5.exe (PID: 9804)
Searches for installed software
- Stealer.exe (PID: 6096)
- Yg1HwMX.exe (PID: 5872)
- MegVlau.exe (PID: 7144)
- HzSVdBl.exe (PID: 7224)
- ipconfig.exe (PID: 6788)
Adds/modifies Windows certificates
- lsass.exe (PID: 760)
The process creates files with name similar to system file names
- ._cache_4363463463464363463463463.exe (PID: 6392)
- example_win32_dx11.exe (PID: 7148)
Application launched itself
- MegVlau.exe (PID: 648)
- kp8dnpa9.exe (PID: 440)
- main1.exe (PID: 6540)
- JhOTKwS.exe (PID: 1572)
- chrome.exe (PID: 7328)
- HzSVdBl.exe (PID: 8108)
- msedge.exe (PID: 8664)
- HMqdrvG.exe (PID: 4604)
- golden.exe (PID: 9700)
- TPB-1.exe (PID: 11016)
- f5634328d7.exe (PID: 10644)
- HMqdrvG.exe (PID: 7432)
- 8NsQP4U.exe (PID: 12268)
- HzSVdBl.exe (PID: 11580)
- cmd.exe (PID: 11764)
- App.exe (PID: 10528)
Executes application which crashes
- MegVlau.exe (PID: 648)
- kp8dnpa9.exe (PID: 440)
- JhOTKwS.exe (PID: 1572)
- HzSVdBl.exe (PID: 8108)
- HMqdrvG.exe (PID: 4604)
- 3e3ev3.exe (PID: 9752)
- f5634328d7.exe (PID: 10644)
- TPB-1.exe (PID: 11016)
- HMqdrvG.exe (PID: 7432)
- 8NsQP4U.exe (PID: 12268)
- HzSVdBl.exe (PID: 11580)
- loader.exe (PID: 9800)
Process drops legitimate windows executable
- main1.exe (PID: 6540)
- msiexec.exe (PID: 8628)
- TH5VZLUXU8YMPLO7BGZOWA5.exe (PID: 9804)
- ._cache_4363463463464363463463463.exe (PID: 6392)
- App.exe (PID: 10528)
Process drops python dynamic module
- main1.exe (PID: 6540)
- App.exe (PID: 10528)
The process drops C-runtime libraries
- main1.exe (PID: 6540)
- TH5VZLUXU8YMPLO7BGZOWA5.exe (PID: 9804)
- App.exe (PID: 10528)
Script adds exclusion extension to Windows Defender
- Miner.exe (PID: 4872)
- whrbuflqwhah.exe (PID: 6068)
- cmd.exe (PID: 11004)
Script adds exclusion path to Windows Defender
- Miner.exe (PID: 4872)
- taskhost.exe (PID: 5256)
- whrbuflqwhah.exe (PID: 6068)
- loader.exe (PID: 9800)
Manipulates environment variables
- powershell.exe (PID: 5720)
- powershell.exe (PID: 6204)
Executing commands from a ".bat" file
- Client.exe (PID: 1864)
- svchost.exe (PID: 6004)
- Client.exe (PID: 2120)
- svchost.exe (PID: 9000)
- svchost.exe (PID: 7384)
- Client.exe (PID: 7300)
- svchost.exe (PID: 6760)
- Client.exe (PID: 3864)
- svchost.exe (PID: 1668)
- Client.exe (PID: 9732)
- msinfo32.exe (PID: 9992)
- svchost.exe (PID: 10172)
- ddosziller.exe (PID: 9864)
- java.exe (PID: 9340)
- seksiak.exe (PID: 7240)
- Client.exe (PID: 5460)
- svchost.exe (PID: 8908)
- msinfo32.exe (PID: 9672)
- Pichon.exe (PID: 2156)
- java.exe (PID: 7672)
- seksiak.exe (PID: 9440)
- Client.exe (PID: 10532)
- msinfo32.exe (PID: 10852)
- svchost.exe (PID: 10756)
- seksiak.exe (PID: 10680)
- java.exe (PID: 7076)
- Client.exe (PID: 12072)
- msinfo32.exe (PID: 11568)
- svchost.exe (PID: 11932)
- seksiak.exe (PID: 8660)
- java.exe (PID: 11204)
- Client.exe (PID: 11404)
- 0iMSdYX.exe (PID: 8480)
- msinfo32.exe (PID: 12280)
- svchost.exe (PID: 12184)
- seksiak.exe (PID: 11308)
- java.exe (PID: 11792)
- powershell.exe (PID: 11180)
- Client.exe (PID: 11424)
- svchost.exe (PID: 11704)
- msinfo32.exe (PID: 11756)
- cmd.exe (PID: 11764)
- seksiak.exe (PID: 10732)
- java.exe (PID: 11576)
- jf.exe (PID: 10708)
Loads Python modules
- main1.exe (PID: 6396)
Uses TASKKILL.EXE to kill Browsers
- main1.exe (PID: 6396)
- 9593da7e83.exe (PID: 9460)
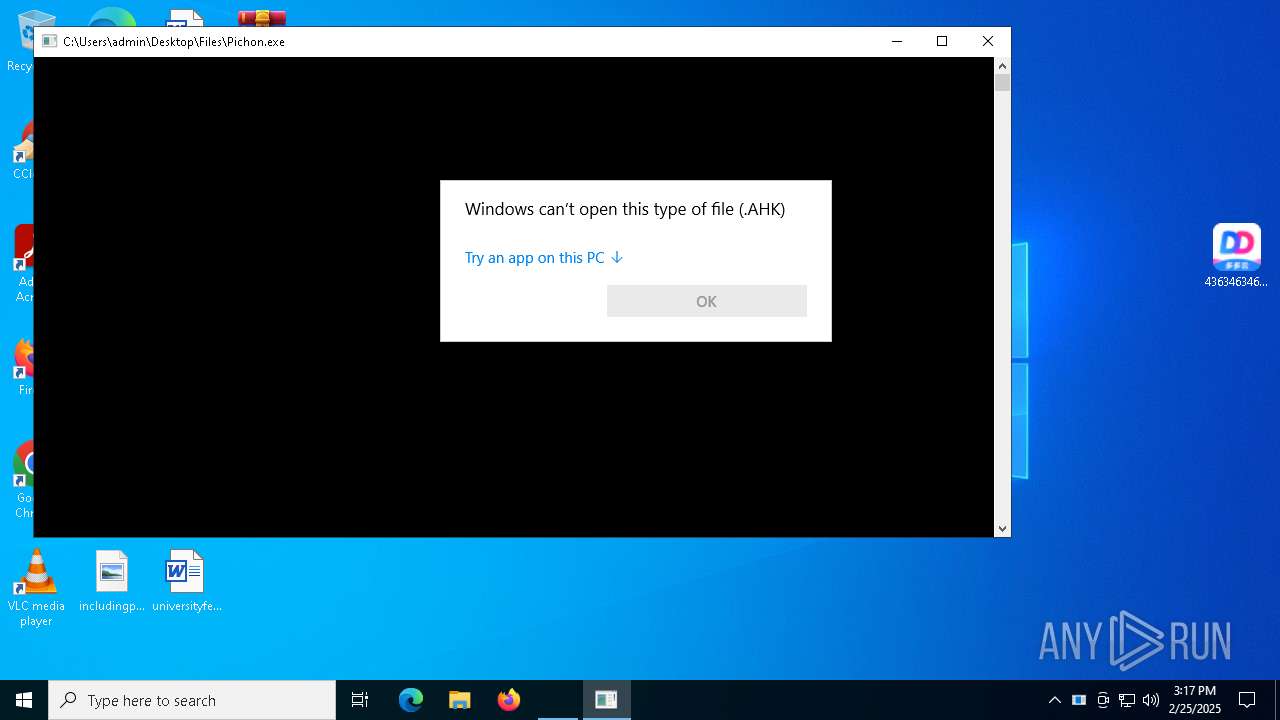
Starts application with an unusual extension
- cmd.exe (PID: 5432)
- cmd.exe (PID: 7336)
- cmd.exe (PID: 7644)
- cmd.exe (PID: 7968)
- cmd.exe (PID: 9040)
- cmd.exe (PID: 8112)
- cmd.exe (PID: 8664)
- cmd.exe (PID: 6884)
- cmd.exe (PID: 8820)
- cmd.exe (PID: 10212)
- cmd.exe (PID: 10000)
- cmd.exe (PID: 9144)
- cmd.exe (PID: 3172)
- cmd.exe (PID: 5496)
- cmd.exe (PID: 10072)
- cmd.exe (PID: 8352)
- cmd.exe (PID: 6720)
- cmd.exe (PID: 7656)
- cmd.exe (PID: 6936)
- cmd.exe (PID: 11116)
- cmd.exe (PID: 9948)
- cmd.exe (PID: 12044)
- cmd.exe (PID: 10884)
- cmd.exe (PID: 12136)
- cmd.exe (PID: 10680)
- cmd.exe (PID: 11676)
- cmd.exe (PID: 11412)
- cmd.exe (PID: 9328)
- cmd.exe (PID: 10500)
- cmd.exe (PID: 11108)
- cmd.exe (PID: 11208)
- cmd.exe (PID: 11844)
- cmd.exe (PID: 11692)
- cmd.exe (PID: 11616)
- cmd.exe (PID: 10464)
- cmd.exe (PID: 11432)
- cmd.exe (PID: 11472)
- cmd.exe (PID: 11764)
- cmd.exe (PID: 11136)
- cmd.exe (PID: 11888)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 5432)
- cmd.exe (PID: 7336)
- cmd.exe (PID: 7644)
- cmd.exe (PID: 9040)
- cmd.exe (PID: 7968)
- cmd.exe (PID: 8112)
- cmd.exe (PID: 8664)
- cmd.exe (PID: 8820)
- cmd.exe (PID: 6884)
- cmd.exe (PID: 10212)
- cmd.exe (PID: 10000)
- cmd.exe (PID: 9144)
- cmd.exe (PID: 3172)
- cmd.exe (PID: 5496)
- cmd.exe (PID: 10072)
- cmd.exe (PID: 8352)
- cmd.exe (PID: 6720)
- cmd.exe (PID: 7656)
- cmd.exe (PID: 6936)
- cmd.exe (PID: 11116)
- cmd.exe (PID: 10884)
- cmd.exe (PID: 12044)
- cmd.exe (PID: 9948)
- cmd.exe (PID: 12136)
- cmd.exe (PID: 10680)
- cmd.exe (PID: 11676)
- cmd.exe (PID: 11412)
- cmd.exe (PID: 9328)
- cmd.exe (PID: 11108)
- cmd.exe (PID: 10500)
- cmd.exe (PID: 11208)
- cmd.exe (PID: 11844)
- cmd.exe (PID: 11692)
- cmd.exe (PID: 11616)
- cmd.exe (PID: 10464)
- cmd.exe (PID: 11432)
- cmd.exe (PID: 11472)
- cmd.exe (PID: 11136)
- cmd.exe (PID: 11888)
- cmd.exe (PID: 12640)
Checks for external IP
- svchost.exe (PID: 2192)
- taskhost.exe (PID: 5256)
- main1.exe (PID: 6396)
- svchost.exe (PID: 9900)
- aspnet_compiler.exe (PID: 11632)
- loader.exe (PID: 9800)
Stops a currently running service
- sc.exe (PID: 4972)
- sc.exe (PID: 4468)
- sc.exe (PID: 7208)
- sc.exe (PID: 5028)
- sc.exe (PID: 7120)
- sc.exe (PID: 2212)
- sc.exe (PID: 8920)
- sc.exe (PID: 7920)
- sc.exe (PID: 8168)
- sc.exe (PID: 7664)
- sc.exe (PID: 8532)
Starts SC.EXE for service management
- Miner.exe (PID: 4872)
- whrbuflqwhah.exe (PID: 6068)
- cmd.exe (PID: 5392)
- 2657926259.exe (PID: 4520)
The process executes via Task Scheduler
- rapes.exe (PID: 5004)
- rapes.exe (PID: 9440)
- UClient.exe (PID: 10348)
- rapes.exe (PID: 12188)
- rapes.exe (PID: 14200)
Windows service management via SC.EXE
- sc.exe (PID: 2088)
- sc.exe (PID: 6804)
- sc.exe (PID: 4512)
- sc.exe (PID: 8068)
Process uninstalls Windows update
- wusa.exe (PID: 5564)
- wusa.exe (PID: 3976)
Creates a new Windows service
- sc.exe (PID: 7524)
Executes as Windows Service
- whrbuflqwhah.exe (PID: 6068)
Script adds exclusion process to Windows Defender
- taskhost.exe (PID: 5256)
The executable file from the user directory is run by the CMD process
- Client.exe (PID: 2120)
- svchost.exe (PID: 9000)
- svchost.exe (PID: 7384)
- Client.exe (PID: 7300)
- svchost.exe (PID: 6760)
- Client.exe (PID: 3864)
- svchost.exe (PID: 1668)
- Client.exe (PID: 9732)
- svchost.exe (PID: 10172)
- tesst.exe (PID: 10020)
- Client.exe (PID: 5460)
- svchost.exe (PID: 8908)
- java.exe (PID: 7672)
- Client.exe (PID: 10532)
- svchost.exe (PID: 10756)
- java.exe (PID: 7076)
- Client.exe (PID: 12072)
- svchost.exe (PID: 11932)
- java.exe (PID: 11204)
- Client.exe (PID: 11404)
- svchost.exe (PID: 12184)
- java.exe (PID: 11792)
- Client.exe (PID: 11424)
- svchost.exe (PID: 11704)
- java.exe (PID: 11576)
- svchost.exe (PID: 12192)
- Client.exe (PID: 11812)
- java.exe (PID: 1852)
The process checks if it is being run in the virtual environment
- tn8cdkzn.exe (PID: 5888)
Drops a system driver (possible attempt to evade defenses)
- whrbuflqwhah.exe (PID: 6068)
- powershell.exe (PID: 7236)
Crypto Currency Mining Activity Detected
- svchost.exe (PID: 2192)
There is functionality for taking screenshot (YARA)
- 1.exe (PID: 6820)
- rapes.exe (PID: 5096)
There is functionality for enable RDP (YARA)
- rapes.exe (PID: 5096)
Loads DLL from Mozilla Firefox
- Fz7SAggvHD.exe (PID: 7472)
Uses TASKKILL.EXE to kill process
- 9593da7e83.exe (PID: 9460)
Uses WMIC.EXE to obtain physical disk drive information
- cmd.exe (PID: 7560)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7560)
- powershell.exe (PID: 12236)
Reads the BIOS version
- fa0dcb4547.exe (PID: 4428)
- f86nrrc6.exe (PID: 5872)
The process drops Mozilla's DLL files
- TH5VZLUXU8YMPLO7BGZOWA5.exe (PID: 9804)
Starts process via Powershell
- powershell.exe (PID: 11180)
Returns all items found within a container (POWERSHELL)
- powershell.exe (PID: 12236)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 11764)
Uses NETSH.EXE to add a firewall rule or allowed programs
- SearchUII.exe (PID: 8104)
Starts a Microsoft application from unusual location
- hell9o.exe (PID: 11448)
- jf.exe (PID: 10708)
Executing commands from ".cmd" file
- hell9o.exe (PID: 11448)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2676)
- cmd.exe (PID: 5392)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7236)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 6384)
Uses ATTRIB.EXE to modify file attributes
- loader.exe (PID: 9800)
Uses WMIC.EXE to obtain Windows Installer data
- loader.exe (PID: 9800)
The process connected to a server suspected of theft
- WindowsFormsApp32.exe (PID: 9944)
Script disables Windows Defender's real-time protection
- loader.exe (PID: 9800)
Script disables Windows Defender's IPS
- loader.exe (PID: 9800)
Uses WMIC.EXE to obtain operating system information
- loader.exe (PID: 9800)
INFO
Reads security settings of Internet Explorer
- RuntimeBroker.exe (PID: 6908)
- explorer.exe (PID: 4488)
- WmiPrvSE.exe (PID: 2728)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6420)
- msiexec.exe (PID: 8628)
- firefox.exe (PID: 10088)
Creates files in the program directory
- MoUsoCoreWorker.exe (PID: 4712)
- 4363463463464363463463463.exe (PID: 7124)
- svchost.exe (PID: 2132)
- Synaptics.exe (PID: 5000)
- Yg1HwMX.exe (PID: 5872)
- MegVlau.exe (PID: 7144)
- HzSVdBl.exe (PID: 7224)
- Miner.exe (PID: 4872)
The sample compiled with turkish language support
- WinRAR.exe (PID: 6420)
- explorer.exe (PID: 4488)
- 4363463463464363463463463.exe (PID: 7124)
- Synaptics.exe (PID: 5000)
- msiexec.exe (PID: 8628)
- explorer.exe (PID: 9936)
- 260079166.exe (PID: 11664)
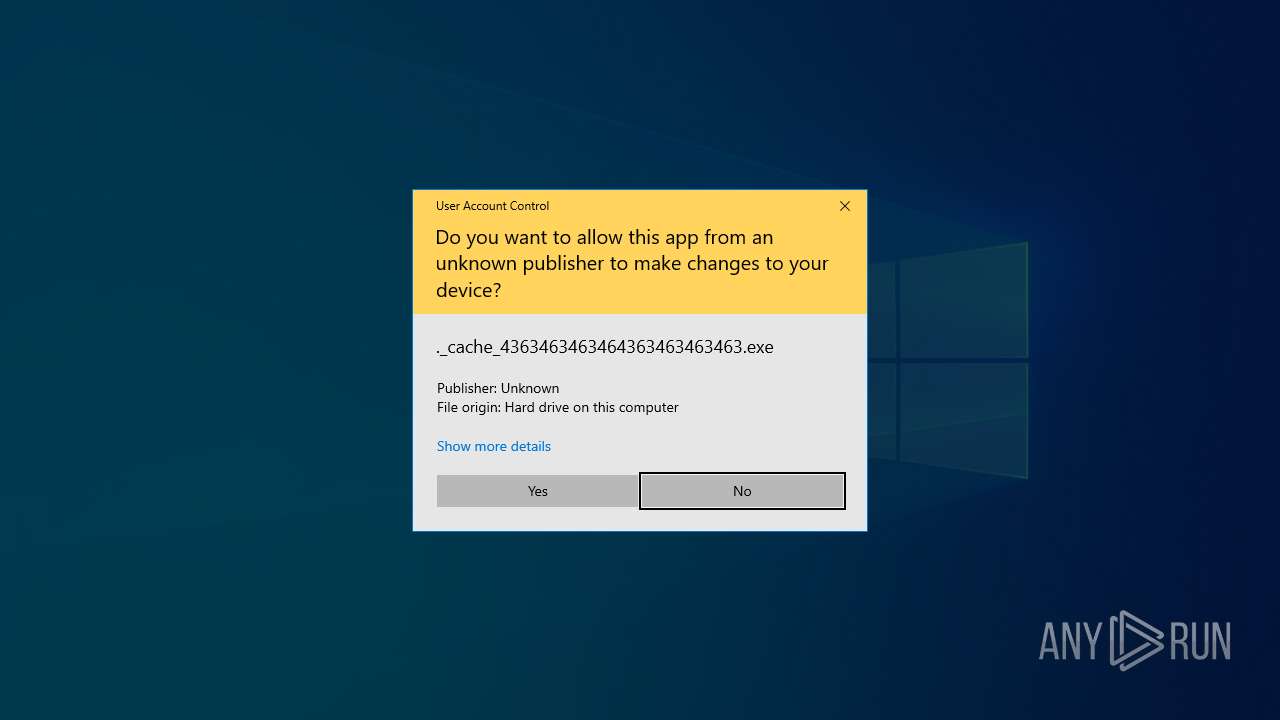
Manual execution by a user
- 4363463463464363463463463.exe (PID: 7124)
- msedge.exe (PID: 7140)
- firefox.exe (PID: 9440)
- firefox.exe (PID: 5588)
- msedge.exe (PID: 7932)
Reads the computer name
- 4363463463464363463463463.exe (PID: 7124)
- ._cache_4363463463464363463463463.exe (PID: 6392)
- 1.exe (PID: 6820)
- lummetc.exe (PID: 5392)
- random.exe (PID: 5572)
- rapes.exe (PID: 5096)
- meta.exe (PID: 5256)
- MSBuild.exe (PID: 1200)
- k360.exe (PID: 6536)
- Stealer.exe (PID: 6096)
- Test2.exe (PID: 4624)
- vtoroy.exe (PID: 5268)
- Synaptics.exe (PID: 5000)
- Yg1HwMX.exe (PID: 5872)
- MegVlau.exe (PID: 648)
- Runtime%20Broker.exe (PID: 2756)
- kp8dnpa9.exe (PID: 6136)
- example_win32_dx11.exe (PID: 7148)
- JhOTKwS.exe (PID: 1572)
- svchost.exe (PID: 9000)
- msiexec.exe (PID: 8628)
- Client-built.exe (PID: 6800)
- Java.exe (PID: 836)
- seksiak.exe (PID: 7240)
- tesst.exe (PID: 10020)
- 34647a8c61.exe (PID: 10220)
- TH5VZLUXU8YMPLO7BGZOWA5.exe (PID: 9804)
- BitLockerToGo.exe (PID: 8688)
- svchost.exe (PID: 10756)
- seksiak.exe (PID: 10680)
- Client.exe (PID: 12072)
- SearchUII.exe (PID: 8104)
- java.exe (PID: 11204)
- seksiak.exe (PID: 11308)
- seksiak.exe (PID: 10732)
- Client.exe (PID: 11812)
- java.exe (PID: 1852)
Checks supported languages
- 4363463463464363463463463.exe (PID: 7124)
- ._cache_4363463463464363463463463.exe (PID: 6392)
- 1.exe (PID: 6820)
- lummetc.exe (PID: 5392)
- random.exe (PID: 5572)
- MSBuild.exe (PID: 1200)
- meta.exe (PID: 5256)
- k360.exe (PID: 6536)
- Steanings.exe (PID: 6240)
- kp8dnpa9.exe (PID: 440)
- Build.exe (PID: 6232)
- Stealer.exe (PID: 6096)
- Test2.exe (PID: 4624)
- Synaptics.exe (PID: 5000)
- vtoroy.exe (PID: 5268)
- Yg1HwMX.exe (PID: 5872)
- main1.exe (PID: 6540)
- MegVlau.exe (PID: 648)
- Client.exe (PID: 1864)
- Runtime%20Broker.exe (PID: 2756)
- kp8dnpa9.exe (PID: 6136)
- example_win32_dx11.exe (PID: 7148)
- JhOTKwS.exe (PID: 1572)
- chcp.com (PID: 1576)
- JhOTKwS.exe (PID: 6032)
- chrome.exe (PID: 7328)
- taskhost.exe (PID: 5256)
- HzSVdBl.exe (PID: 8108)
- MSBuild.exe (PID: 6160)
- Client.exe (PID: 2120)
- msiexec.exe (PID: 8628)
- rapes.exe (PID: 5096)
- Client.exe (PID: 7300)
- HMqdrvG.exe (PID: 4604)
- Client.exe (PID: 3864)
- chcp.com (PID: 8464)
- cfc53e19dd.exe (PID: 3988)
- svchost.exe (PID: 1668)
- RuntimeBroker.exe (PID: 5856)
- 3e3ev3.exe (PID: 9752)
- ddosziller.exe (PID: 9864)
- svchost.exe (PID: 10172)
- Java.exe (PID: 836)
- 9580ad453f.exe (PID: 9428)
- sysnldcvmr.exe (PID: 7820)
- seksiak.exe (PID: 7240)
- chcp.com (PID: 10076)
- JUSCHED.EXE (PID: 9864)
- tesst.exe (PID: 10020)
- crypteda.exe (PID: 2060)
- RA4sWoTxlD.exe (PID: 8800)
- CFZgWblawj.exe (PID: 8596)
- sela.exe (PID: 9552)
- chcp.com (PID: 8216)
- seksiak.exe (PID: 9440)
- CryptoWall.exe (PID: 8600)
- fa0dcb4547.exe (PID: 4428)
- Client.exe (PID: 10532)
- BitLockerToGo.exe (PID: 8688)
- TPB-1.exe (PID: 11016)
- svchost.exe (PID: 10756)
- java.exe (PID: 7076)
- msinfo32.exe (PID: 10852)
- seksiak.exe (PID: 10680)
- chcp.com (PID: 11420)
- crypted_UClient.exe (PID: 11464)
- msinfo32.exe (PID: 11568)
- HzSVdBl.exe (PID: 11580)
- SearchUII.exe (PID: 8104)
- svchost.exe (PID: 12184)
- 0iMSdYX.exe (PID: 8480)
- chcp.com (PID: 10840)
- Client.exe (PID: 11424)
- seksiak.exe (PID: 10732)
- msinfo32.exe (PID: 11756)
- more.com (PID: 9680)
- svchost.exe (PID: 12192)
- LinkedinTuVanDat.exe (PID: 7656)
- hell9o.exe (PID: 11448)
- msinfo32.exe (PID: 6900)
- seksiak.exe (PID: 12216)
- WindowsFormsApp32.exe (PID: 9944)
- java.exe (PID: 1852)
- 1605733096.exe (PID: 2324)
- svchosi.exe (PID: 1572)
- 1050320064.exe (PID: 14144)
- 189819635.exe (PID: 6792)
- App.exe (PID: 11564)
- rapes.exe (PID: 14200)
Reads the machine GUID from the registry
- ._cache_4363463463464363463463463.exe (PID: 6392)
- MSBuild.exe (PID: 1200)
- Build.exe (PID: 6232)
- Steanings.exe (PID: 6240)
- Test2.exe (PID: 4624)
- Stealer.exe (PID: 6096)
- Client.exe (PID: 1864)
- example_win32_dx11.exe (PID: 7148)
- taskhost.exe (PID: 5256)
- svchost.exe (PID: 6004)
- MSBuild.exe (PID: 6160)
- Client.exe (PID: 2120)
- svchost.exe (PID: 9000)
- msiexec.exe (PID: 8628)
- svchost.exe (PID: 6760)
- Client.exe (PID: 3864)
- RuntimeBroker.exe (PID: 5856)
- DiskUtility.exe (PID: 9356)
- Client.exe (PID: 9732)
- 25072023.exe (PID: 8520)
- msinfo32.exe (PID: 9992)
- discordupdate.exe (PID: 9672)
- Client-built.exe (PID: 6800)
- seksiak.exe (PID: 7240)
- Client.exe (PID: 5460)
- msinfo32.exe (PID: 9672)
- CFZgWblawj.exe (PID: 8596)
- tesst.exe (PID: 10020)
- seksiak.exe (PID: 9440)
- 5KNCHALAH.exe (PID: 10568)
- java.exe (PID: 7076)
- Client.exe (PID: 12072)
- msinfo32.exe (PID: 11568)
- seksiak.exe (PID: 8660)
- sysnldcvmr.exe (PID: 7820)
- seksiak.exe (PID: 11308)
- rapes.exe (PID: 5096)
- xyaw4fkp.exe (PID: 8844)
- SearchUII.exe (PID: 8104)
- svchost.exe (PID: 12192)
- java.exe (PID: 1852)
- seksiak.exe (PID: 12216)
- ipconfig.exe (PID: 6788)
- App.exe (PID: 11564)
Reads the software policy settings
- ._cache_4363463463464363463463463.exe (PID: 6392)
- lummetc.exe (PID: 5392)
- lsass.exe (PID: 760)
- Stealer.exe (PID: 6096)
- Yg1HwMX.exe (PID: 5872)
- MegVlau.exe (PID: 7144)
- HzSVdBl.exe (PID: 7224)
- Synaptics.exe (PID: 5000)
- TPB-1.exe (PID: 11212)
- 8NsQP4U.exe (PID: 7852)
- WerFault.exe (PID: 10172)
- HzSVdBl.exe (PID: 5788)
- rapes.exe (PID: 5096)
- WindowsFormsApp32.exe (PID: 9944)
Disables trace logs
- ._cache_4363463463464363463463463.exe (PID: 6392)
- cvrMRi04XB.exe (PID: 7420)
- DiskUtility.exe (PID: 9356)
- WindowsFormsApp32.exe (PID: 9944)
- powershell.exe (PID: 7236)
Checks proxy server information
- ._cache_4363463463464363463463463.exe (PID: 6392)
- rapes.exe (PID: 5096)
- Stealer.exe (PID: 6096)
- taskhost.exe (PID: 5256)
- WerFault.exe (PID: 4160)
- cvrMRi04XB.exe (PID: 7420)
- main1.exe (PID: 6396)
- q1wnx5ir.exe (PID: 8984)
- Synaptics.exe (PID: 5000)
- WerFault.exe (PID: 7756)
- WerFault.exe (PID: 10172)
- 1780920692.exe (PID: 7704)
- svchoxb.exe (PID: 11476)
The sample compiled with english language support
- ._cache_4363463463464363463463463.exe (PID: 6392)
- main1.exe (PID: 6540)
- msiexec.exe (PID: 8628)
- rapes.exe (PID: 5096)
- TH5VZLUXU8YMPLO7BGZOWA5.exe (PID: 9804)
- crypted_UClient.exe (PID: 11464)
- Synaptics.exe (PID: 5000)
- App.exe (PID: 10528)
- svchosi.exe (PID: 1572)
Process checks computer location settings
- 4363463463464363463463463.exe (PID: 7124)
- ._cache_4363463463464363463463463.exe (PID: 6392)
- random.exe (PID: 5572)
- Build.exe (PID: 6232)
- Stealer.exe (PID: 6096)
- Client.exe (PID: 1864)
- JhOTKwS.exe (PID: 6032)
- taskhost.exe (PID: 5256)
- Client.exe (PID: 2120)
- rapes.exe (PID: 5096)
- Client.exe (PID: 7300)
- svchost.exe (PID: 1668)
- svchost.exe (PID: 10172)
- seksiak.exe (PID: 7240)
- seksiak.exe (PID: 9440)
- msinfo32.exe (PID: 10852)
- 0iMSdYX.exe (PID: 8480)
- svchost.exe (PID: 12184)
- Client.exe (PID: 11424)
- msinfo32.exe (PID: 11756)
Creates files or folders in the user directory
- lsass.exe (PID: 760)
- rapes.exe (PID: 5096)
- Build.exe (PID: 6232)
- Stealer.exe (PID: 6096)
- Test2.exe (PID: 4624)
- example_win32_dx11.exe (PID: 7148)
- JhOTKwS.exe (PID: 6032)
- chrome.exe (PID: 7328)
- drchoe.exe (PID: 8020)
- WerFault.exe (PID: 7148)
- WerFault.exe (PID: 4160)
- WerFault.exe (PID: 4428)
- msedge.exe (PID: 8664)
- explorer.exe (PID: 4488)
Reads the time zone
- WmiPrvSE.exe (PID: 2728)
Create files in a temporary directory
- random.exe (PID: 5572)
- Build.exe (PID: 6232)
- Synaptics.exe (PID: 5000)
- main1.exe (PID: 6540)
- rapes.exe (PID: 5096)
- Client.exe (PID: 1864)
- main1.exe (PID: 6396)
- svchost.exe (PID: 6004)
- chrome.exe (PID: 7328)
- svchost.exe (PID: 9000)
Compiled with Borland Delphi (YARA)
- RuntimeBroker.exe (PID: 6908)
- ._cache_4363463463464363463463463.exe (PID: 6392)
- conhost.exe (PID: 1472)
- 1.exe (PID: 6820)
- rapes.exe (PID: 5096)
- MSBuild.exe (PID: 1200)
- conhost.exe (PID: 3288)
The sample compiled with german language support
- rapes.exe (PID: 5096)
- msiexec.exe (PID: 8628)
Reads Environment values
- Test2.exe (PID: 4624)
- Client.exe (PID: 1864)
- example_win32_dx11.exe (PID: 7148)
- svchost.exe (PID: 9000)
- cvrMRi04XB.exe (PID: 7420)
- Client.exe (PID: 3864)
- msinfo32.exe (PID: 9992)
- JUSCHED.EXE (PID: 9864)
- java.exe (PID: 7672)
- java.exe (PID: 7076)
- java.exe (PID: 11204)
- seksiak.exe (PID: 11308)
- Client.exe (PID: 11424)
- seksiak.exe (PID: 10732)
- msinfo32.exe (PID: 11756)
- msinfo32.exe (PID: 6900)
- loader.exe (PID: 9800)
- java.exe (PID: 1852)
Reads CPU info
- Stealer.exe (PID: 6096)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 2424)
- powershell.exe (PID: 5720)
- powershell.exe (PID: 7556)
- powershell.exe (PID: 8692)
- powershell.exe (PID: 6204)
- powershell.exe (PID: 10908)
Changes the display of characters in the console
- cmd.exe (PID: 5432)
- cmd.exe (PID: 7336)
- cmd.exe (PID: 7644)
- cmd.exe (PID: 9040)
- cmd.exe (PID: 7968)
- cmd.exe (PID: 8664)
- cmd.exe (PID: 8112)
- cmd.exe (PID: 6884)
- cmd.exe (PID: 8820)
- cmd.exe (PID: 10212)
- cmd.exe (PID: 9144)
- cmd.exe (PID: 10000)
- cmd.exe (PID: 3172)
- cmd.exe (PID: 5496)
- cmd.exe (PID: 10072)
- cmd.exe (PID: 8352)
- cmd.exe (PID: 6720)
- cmd.exe (PID: 7656)
- cmd.exe (PID: 6936)
- cmd.exe (PID: 11116)
- cmd.exe (PID: 9948)
- cmd.exe (PID: 10884)
- cmd.exe (PID: 12044)
- cmd.exe (PID: 12136)
- cmd.exe (PID: 10680)
- cmd.exe (PID: 11676)
- cmd.exe (PID: 11412)
- cmd.exe (PID: 9328)
- cmd.exe (PID: 11108)
- cmd.exe (PID: 10500)
- cmd.exe (PID: 11208)
- cmd.exe (PID: 11844)
- cmd.exe (PID: 11692)
- cmd.exe (PID: 11616)
- cmd.exe (PID: 10464)
- cmd.exe (PID: 11432)
- cmd.exe (PID: 11472)
- cmd.exe (PID: 11888)
- cmd.exe (PID: 11136)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2424)
- powershell.exe (PID: 5720)
- powershell.exe (PID: 7556)
- powershell.exe (PID: 8692)
- powershell.exe (PID: 6204)
- powershell.exe (PID: 7236)
- powershell.exe (PID: 10908)
- powershell.exe (PID: 6532)
Reads Windows Product ID
- WmiPrvSE.exe (PID: 2728)
Application launched itself
- msedge.exe (PID: 7140)
- firefox.exe (PID: 9440)
- firefox.exe (PID: 10088)
- firefox.exe (PID: 5588)
- chrome.exe (PID: 10936)
- msedge.exe (PID: 11524)
The sample compiled with arabic language support
- msiexec.exe (PID: 8628)
The sample compiled with spanish language support
- msiexec.exe (PID: 8628)
The sample compiled with japanese language support
- whrbuflqwhah.exe (PID: 6068)
- msiexec.exe (PID: 8628)
The sample compiled with french language support
- msiexec.exe (PID: 8628)
The sample compiled with Indonesian language support
- msiexec.exe (PID: 8628)
The sample compiled with Italian language support
- msiexec.exe (PID: 8628)
The sample compiled with korean language support
- msiexec.exe (PID: 8628)
The sample compiled with polish language support
- msiexec.exe (PID: 8628)
The sample compiled with swedish language support
- msiexec.exe (PID: 8628)
The sample compiled with slovak language support
- msiexec.exe (PID: 8628)
The sample compiled with chinese language support
- msiexec.exe (PID: 8628)
- ._cache_4363463463464363463463463.exe (PID: 6392)
- jf.exe (PID: 10708)
- svchosi.exe (PID: 1572)
The sample compiled with russian language support
- msiexec.exe (PID: 8628)
- ._cache_4363463463464363463463463.exe (PID: 6392)
The sample compiled with portuguese language support
- msiexec.exe (PID: 8628)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- WmiPrvSE.exe (PID: 2728)
.NET Reactor protector has been detected
- MSBuild.exe (PID: 1200)
Returns hidden items found within a container (POWERSHELL)
- conhost.exe (PID: 3680)
- conhost.exe (PID: 11036)
- conhost.exe (PID: 12116)
- conhost.exe (PID: 1496)
- conhost.exe (PID: 11952)
- conhost.exe (PID: 11920)
- cmd.exe (PID: 11904)
- conhost.exe (PID: 8536)
- conhost.exe (PID: 7488)
- conhost.exe (PID: 6180)
- conhost.exe (PID: 12196)
- conhost.exe (PID: 11320)
- conhost.exe (PID: 6740)
- conhost.exe (PID: 4392)
- conhost.exe (PID: 11224)
- conhost.exe (PID: 2972)
- conhost.exe (PID: 9476)
- conhost.exe (PID: 11312)
- conhost.exe (PID: 8460)
- conhost.exe (PID: 12312)
- conhost.exe (PID: 8980)
- conhost.exe (PID: 12660)
- conhost.exe (PID: 13968)
- powershell.exe (PID: 6792)
- conhost.exe (PID: 5308)
- conhost.exe (PID: 12792)
- conhost.exe (PID: 13828)
- conhost.exe (PID: 14024)
Returns all items recursively from all subfolders (POWERSHELL)
- powershell.exe (PID: 12236)
Checks current location (POWERSHELL)
- powershell.exe (PID: 7236)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 7236)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 7236)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7236)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(5096) rapes.exe
C2176.113.115.6
URLhttp://176.113.115.6/Ni9kiput/index.php
Version5.21
Options
Drop directorybb556cff4a
Drop namerapes.exe
Strings (125)d1
/Plugins/
cred.dll
.jpg
|
%-lu
<d>
lv:
shell32.dll
GetNativeSystemInfo
Content-Disposition: form-data; name="data"; filename="
Powershell.exe
\
Kaspersky Lab
\0000
cred.dll|clip.dll|
kernel32.dll
" && ren
------
rundll32
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
sd:
&&
rb
/Ni9kiput/index.php
VideoID
Content-Type: application/x-www-form-urlencoded
2016
0123456789
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
r=
rapes.exe
CurrentBuild
Doctor Web
ComputerName
\App
0000043f
cmd
DefaultSettings.XResolution
Bitdefender
WinDefender
av:
Content-Type: multipart/form-data; boundary=----
ar:
bb556cff4a
--
2022
Startup
/k
abcdefghijklmnopqrstuvwxyz0123456789-_
=
SYSTEM\ControlSet001\Services\BasicDisplay\Video
00000419
2019
&unit=
" && timeout 1 && del
Main
S-%lu-
shutdown -s -t 0
DefaultSettings.YResolution
GET
"taskkill /f /im "
Norton
exe
dm:
5.21
SOFTWARE\Microsoft\Windows NT\CurrentVersion
-%lu
360TotalSecurity
bi:
random
os:
http://
id:
pc:
dll
wb
zip
<c>
176.113.115.6
AVG
+++
msi
Sophos
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
:::
-unicode-
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
#
ProductName
00000422
ESET
"
Content-Type: application/octet-stream
/quiet
Keyboard Layout\Preload
un:
2025
"
00000423
https://
clip.dll
e3
AVAST Software
Programs
vs:
ps1
Avira
Comodo
og:
&& Exit"
st=s
e1
?scr=1
POST
cmd /C RMDIR /s/q
%USERPROFILE%
------
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
e2
Rem
rundll32.exe
Panda Security
ProgramData\
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
-executionpolicy remotesigned -File "
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:01:13 02:48:24 |
| ZipCRC: | 0x072e96ed |
| ZipCompressedSize: | 403105 |
| ZipUncompressedSize: | 782336 |
| ZipFileName: | 4363463463464363463463463.exe |
Total processes
790
Monitored processes
733
Malicious processes
180
Suspicious processes
97
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 320 | C:\WINDOWS\system32\svchost.exe -k DcomLaunch -p -s LSM | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 376 | C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s WdiSystemHost | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 440 | "C:\Users\admin\Desktop\Files\kp8dnpa9.exe" | C:\Users\admin\Desktop\Files\kp8dnpa9.exe | ._cache_4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 648 | "C:\Users\admin\Desktop\._cache_4363463463464363463463463.exe" | C:\Users\admin\Desktop\._cache_4363463463464363463463463.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 648 | "C:\Users\admin\AppData\Local\Temp\10015790101\MegVlau.exe" | C:\Users\admin\AppData\Local\Temp\10015790101\MegVlau.exe | rapes.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Brought Exit code: 3221226505 Version: 1.0.0.0 Modules
| |||||||||||||||
| 684 | winlogon.exe | C:\Windows\System32\winlogon.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Logon Application Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 760 | C:\WINDOWS\system32\lsass.exe | C:\Windows\System32\lsass.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Security Authority Process Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 772 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s StorSvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 836 | "C:\Users\admin\Desktop\Files\Java.exe" | C:\Users\admin\Desktop\Files\Java.exe | ._cache_4363463463464363463463463.exe | ||||||||||||
User: admin Company: java © Integrity Level: HIGH Description: Java Exit code: 3 Version: 1.2.3.4 Modules
| |||||||||||||||
Total events
491 156
Read events
472 796
Write events
1 662
Delete events
16 698
Modification events
| (PID) Process: | (4712) MoUsoCoreWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsSelfHost\OneSettings |
| Operation: | write | Name: | MinTimeBetweenCallsWhenThrottledInSeconds |
Value: 300 | |||
| (PID) Process: | (4712) MoUsoCoreWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsSelfHost\OneSettings |
| Operation: | write | Name: | CostedConnectionInterval |
Value: 20160 | |||
| (PID) Process: | (4712) MoUsoCoreWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsSelfHost\OneSettings |
| Operation: | write | Name: | TargetingAttributes |
Value: {"Version":396,"SchemaVersion":1,"PartA":["App","AppVer","AttrDataVer"],"Default":["DeviceFamily","f:FlightRing","t:OSVersionFull"],"PartB":{"ACSOVERRIDE":["OSArchitecture","c:IsAlwaysOnAlwaysConnectedCapable"],"APPTARGETEDFEATUREDB":["c:FlightingBranchName","f:FlightRing","t:OSVersionFull","DeviceFamily"],"CASSCLIENT":["OSVersion","c:OSEdition","f:FlightRing","c:OSUILocale","f:FlightingBranchName","r:OEMMode"],"CDM":["ChassisTypeId","r:CurrentBranch","DeviceFamily","f:FlightingBranchName","f:FlightRing","c:InstallLanguage","c:IsDomainJoined","t:IsTestLab","OEMModel","OSArchitecture","OSVersion","t:OSSkuId","c:ProcessorIdentifier","c:TelemetryLevel","t:IsMsftOwned","t:WCOSProductId","c:OSUILocale","c:CommercialId","c:ActivationChannel","c:SCCMClientId","c:IsCloudDomainJoined","r:WebExperience","c:FlightIds","AccountFirstChar","r:WSX_Windows_Settings_Account","r:InstallDate","r:WSX_Runtime","r:DefaultUserRegion","a:GatedFeature_NI22H2","r:WSX_Windows_Shell_Start","a:GatedFeature_CU23H2","r:ExpStates","n:MVVersion","r:CIOptin","c:ProcessorCores","c:TotalPhysicalRAM","r:TestRN","u:UpdateServiceUrl","u:WUfBClientManaged","r:UUSVersion","DL_OSVersion","r:ExpPkgs","u:AllowOptionalContent","n:IsMicrosoftAAD","q:WidgetsAppVer","c:IsDeviceRetailDemo","r:IsFSOverlay","a:SdbVer_NI22H2","r:EdgeStableVersion","r:Migrated_GatedFeature_NI22H2Setup","a:SdbVer_21H2","a:GatedFeature_21H2","r:UtcDataHandlingPolicies","v:SkypeRoomSystem","r:BypassNRO","c:IsVirtualDevice","s:IsA9CapablePC","a:SdbVer_GE24H2"],"CDM_OS":["+CDM","c:FlightIds"],"COMPATLOGGER":["osVer","ring","deviceId"],"CONTENT_DELIVERY_MANAGER":["c:OSEdition","t:OSSkuId","c:OSUILocale","a:UpgEx_CO21H2","a:GStatus_CO21H2","a:DataExpDateEpoch_CO21H2","a:TimestampEpochString_CO21H2","r:AndroidUserOptinValue","f:FlightingBranchName","f:FlightRing","r:CurrentBranch","procm","r:NPUEnabledDevice","MX_FlightIds","r:KnownFoldersBackupStatus","c:IsDomainJoined","iepe","iste","drgng","r:WindowsAccountSyncConsentState","r:WindowsAccountSyncConsentApplicable","r:WindowsAccountSyncConsentPromptAllowed","aipc","ram","prccn","prccs","prcmf","ccr"],"CORTANA_GATEKEEPER":["r:CurrentBranch","f:FlightRing","f:IsRetailOS"],"CORTANAUWP":["c:OSUILocale","t:OSVersionFull","v:CortanaAppVer","r:TestAllowedIDFlags"],"CORTANAUWPTEST":["+CORTANAUWP","v:CortanaAppVerTest"],"CTAC":["+FSS"],"DBUPDATE":["c:FirmwareVersion","c:OEMModelBaseBoard","OSArchitecture","c:FirmwareManufacturer","c:OEMModelNumber","r:BaseBoardManufacturer","c:OEMModelSKU","c:OEMManufacturerName","c:OEMName","c:OEMModelBaseBoardVersion","c:OEMModelSystemFamily","c:OEMModelSystemVersion","c:FirmwareReleaseDate"],"DDC":["+WU_STORE","+_WU_PTI"],"DXDB":["DeviceFamily","f:FlightRing","r:IsHybridOrXGpu","t:OSVersionFull","OSVersion"],"EDGE_SERVICEUI":["t:LocalDeviceID","t:LocalUserID"],"FCON":["+CDM"],"FSS":["r:PreviewBuildsManagerEnabled","f:BranchReadinessLevelRaw","u:BranchReadinessLevelSource","r:BuildFID","t:DeviceFamily","DeviceId","c:EnablePreviewBuilds","f:FlightingPolicyValue","f:IsRetailOS","f:ManagePreviewBuilds","OSVersionFull","t:WCOSProductId","r:SmartActiveHoursState","r:ActiveHoursStart","r:ActiveHoursEnd","r:IsCHCapableBuild","r:FSRing","s:MaxShellVersion","s:MinShellVersion","c:TPMVersion","c:SecureBootCapable","c:ProcessorClockSpeed","c:ProcessorCores","c:TotalPhysicalRAM","t:SMode","c:SystemVolumeTotalCapacity","c:OEMManufacturerName","c:OEMModelNumber","a:ISVM","r:AllowUpgradesWithUnsupportedTPMOrCPU","r:IntelPlatformId","r:IsConfigMgrEnabled","f:IsFlightingEnabled","r:DeviceInfoGatherSuccessful","c:IsVirtualDevice","r:OemPartnerRing","c:FlightingBranchName","a:UpgEx_CO21H2","a:UpgEx_NI22H2","a:UpgEx_GE24H2","sku"],"FXIRISCLIENT":["+IRISCLIENT"],"GS":["t:OSSkuId","t:OSVersionFull","r:CurrentBranch","r:DefaultUserRegion","DeviceFamily","c:FlightIds","f:FlightingBranchName","f:FlightRing","c:IsCloudDomainJoined","t:IsMsftOwned","f:IsRetailOS","c:OSUILocale","c:IsDomainJoined"],"IDSPCA":["f:FlightRing","f:IsFlightingEnabled","f:FlightingBranchName","f:IsRetailOS","c:OSEdition","c:IsDomainJoined","c:OSUILocale","n:IsMicrosoftAAD","r:CurrentBranch","t:IsMsftOwned","t:IsTestLab","t:DeviceFamily","t:LocalDeviceID","t:OSSkuId","t:OSVersionFull","IsVM","OEMModel","OSVersion"],"IRISCLIENT":["+IRISCLIENTBASE","c:FlightIds"],"IRISCLIENTBASE":["DeviceFamily","OSVersion","t:OSSkuId","OSArchitecture","c:TelemetryLevel","f:FlightRing","f:FlightingBranchName","OEMModel","c:OSUILocale","c:OSEdition","r:CurrentBranch","t:WCOSProductId","c:InstallationType","r:InstallDate","c:IsDeviceRetailDemo","f:IsRetailOS","prccs","prccn","prcmf","ram","c:D3DMaxFeatureLevel","c:IsAlwaysOnAlwaysConnectedCapable","t:SMode","t:LocalUserID","r:AndroidUserOptinValue","procm","MX_FlightIds","a:UpgEx_CO21H2","r:KnownFoldersBackupStatus","c:OEMModelSystemFamily","OEMName_Uncleaned","r:IsSpotlightEnabledInOEMTheme","r:IsSpotlightThemeEnabledByOEM","r:WindowsAccountSyncConsentApplicable","r:WindowsAccountSyncConsentState","r:WindowsAccountSyncConsentPromptAllowed","iepe","iste","drgng","aipc","oemname","smbiosdm","ccr"],"IRISCLIENTV2":["+IRISCLIENTBASE","IX_FlightIds"],"MICROSOFT.WINDOWSFEEDBACKHUB_8WEKYB3D8BBWE":["t:OSVersionFull","t:IsTestLab","f:FlightRing"],"MITIGATION":["t:DeviceFamily","f:FlightRing","c:FlightIds","c:IsDomainJoined","t:IsMsftOwned","f:IsRetailOS","t:IsTestLab","IsVM","OEMModel","c:OSEdition","t:OSSkuId","t:OSVersionFull","c:OSUILocale","t:SMode","f:IsFlightingEnabled","c:FirmwareVersion","c:TelemetryLevel","f:FlightingBranchName","r:CurrentBranch","OSVersion","w:FirstStorageSpaceDeviceId","r:IsCldFltSyncRoots","c:OSInstallType","v:IsNotepadExePresent","r:StrictHiveSecurityReg","a:GatedBlockId_21H1","r:UpdateOfferedDays","r:UsoScanMitigation","r:GamingServicesInstalledKey","v:FileExistsMscoreeDll","w:NetFx3State","r:WCFHTTPActivationNotificationState","w:WCFHTTPActivationState","r:WCFNonHTTPActivationNotificationState","w:WCFNonHTTPActivationState","r:DotNetMissingComponentsTroubleshooterSuccess","r:IIS_ASPNET","w:IIS_ASPNET_WMI","r:IIS_NetFxExtensibility","w:IIS_NetFxExtensibility_WMI","r:WAS_NetFxEnvironment","w:WAS_NetFxEnvironment_WMI","v:XamlCbsActivationStore","v:XamlCbsActivationStoreArm64","v:OnnxruntimeVer","w:ElanFingerprintDriverVersion","r:AADBrokerPluginNotRegistered","r:TenantId","r:IppPrinterBadDefaultPdc","r:FlightingOptOutState","r:CloudFilesFilter","r:PSAKyoceraMissingDEH","r:PSATATriumphMissingDEH","r:PSAXeroxMissingDEH","w:PSAKyoceraInstalledName","w:PSATATriumphInstalledName","w:XeroxPsaInstalledName","v:DmdHpControlPackageEnUs","v:DmdHpControlPackageMultiloc","v:DmdHpControlPackageTr","v:WASDK_1_2_ARM","v:WASDK_1_2_ARM64","v:WASDK_1_2_DLL","v:WASDK_1_2_X86"],"MLMOD":["ChassisTypeId","t:DeviceFamily","f:FlightingBranchName","f:FlightRing","f:IsRetailOS","t:OSSkuId","t:OSVersionFull","c:OSUILocale","OSVersion","c:TelemetryLevel","r:CurrentBranch","t:IsTestLab","c:PrimaryDiskType","FX_FlightIds"],"MTP":["+_WU_OS_CORE"],"MUSE":["+_WU_FB","ChassisTypeId","deviceClass","deviceId","c:FlightIds","locale","ms","os","osVer","ring","sampleId","sku","r:DaysSince19H1FUOffer","u:DisableDualScan","u:UpdateServiceUrl","c:CommercialId","f:FlightingBranchName","c:SystemVolumeTotalCapacity","c:IsAlwaysOnAlwaysConnectedCapable","c:ProcessorCores","c:PrimaryDiskType","c:TotalPhysicalRAM","c:ProcessorClockSpeed","c:ProcessorIdentifier","c:ProcessorModel","c:ActivationChannel","c:IsCloudDomainJoined","c:isCommercial","c:IsDomainJoined","c:IsMDMEnrolled","c:SCCMClientID","r:OEMSubModel","c:OEMModelNumber","c:OEMManufacturerName","r:OobeSeeker","r:DefaultUserRegion"],"NARRATORNNV":["+WU_STORE"],"NOISYHAMMER":["+WU_OS"],"PHS":["r:GridZoneName","OEMModel","c:OEMManufacturerName","c:OSUILocale","r:OEMSubModel","DeviceFamily"],"RULESENGINE":["c:OSEdition","t:OSSkuId","c:OSUILocale","a:UpgEx_CO21H2","a:GStatus_CO21H2","a:DataExpDateEpoch_CO21H2","a:TimestampEpochString_CO21H2","r:AndroidUserOptinValue","f:FlightingBranchName","f:FlightRing","r:CurrentBranch","c:ProcessorModel","r:NPUEnabledDevice","MX_FlightIds","r:KnownFoldersBackupStatus","c:IsDomainJoined","r:WindowsAccountSyncConsentApplicable","r:WindowsAccountSyncConsentState","r:WindowsAccountSyncConsentPromptAllowed","c:FlightIds"],"RUXIM":["c:ActivationChannel","f:FlightRing","r:InstallDate","f:IsFlightingEnabled","a:ISVM","OEMModel","OSArchitecture","t:OSSkuId","c:SCCMClientID","r:SetupDisplayedEulaVersion","r:KioskMode","r:OobeSeeker","r:UninstallActive","c:OEMManufacturerName","r:OEMSubModel","c:OSUILocale","f:FlightingBranchName"],"SEDIMENTPACK":["+WU_OS"],"SERVICEEXPERIENCES":["f:FlightingBranchName","f:FlightRing","s:MaxShellVersion","s:MinShellVersion","t:IsTestLab","c:TelemetryLevel","t:OSSkuId","r:CurrentBranch","OSVersion","DeviceFamily","r:WSX_Windows_Settings_Account","c:FlightIds","r:WSX_Runtime","r:WSX_Windows_Shell_Start","r:WSX_Windows_AppSample","r:WSX_Windows_AccountControl"],"SERVICING_CBS":["+WU","osVer"],"SETUP360":["t:OSSkuId","f:FlightRing"],"SMARTOPTOUT":["+CDM"],"STORAGEGROVELER":["a:Free","c:TelemetryLevel","f:FlightRing","f:IsFlightingEnabled","IsVM","t:OSVersionFull"],"UNEXPECTEDCODEPATHLOGGING":["+UTC_STATIC","t:LocalDeviceID","OSVersionFull","OEMModel","OEMName_Uncleaned"],"UTC":["+UTC_STATIC","osVer","locale","ring","f:PilotRing","f:IsRetailOS","ms","expId","t:SMode","f:FlightingBranchName","c:CommercialId","r:IsFeedbackHubSelfhost","c:AzureVMType","t:IsTestLab","c:TelemetryLevel","c:IsVirtualDevice","r:IsProcessorMode","r:UtcDataHandlingPolicies"],"UTC_STATIC":["os","deviceId","sampleId","deviceClass","sku","OEMModel","OEMName_Uncleaned","c:PrimaryDiskType","c:ProcessorModel","c:TotalPhysicalRAM"],"UUS":["OSVersion","f:FlightRing","t:IsTestLab","t:OSVersionFull","f:FlightingBranchName","r:CurrentBranch","f:IsFlightingEnabled"],"WAASASSESSMENT":["+WU_OS"],"WAASMEDIC":["os","osVer","ring","deviceClass","deviceId","locale","sku","c:ActivationChannel","c:CommercialId","r:CurrentBranch","f:FlightingBranchName","c:IsCloudDomainJoined","c:IsDomainJoined","t:IsTestLab","OSVersion","c:SCCMClientID","c:TelemetryLevel","r:FlightingOptOutState"],"WOSC":["t:DeviceFamily","f:FlightRing","f:IsFlightingEnabled","t:IsMsftOwned","t:LocalDeviceID","t:OSSkuId","c:OSUILocale","t:OSVersionFull","c:TelemetryLevel","r:IsHybridOrXGpu","r:PlayFabPartyRelay","OSVersion","n:IsMicrosoftAAD","r:WOSCEndpointsSupported"],"WPSHIFT":["+MTP"],"WU":["+WU_OS","r:DUInternal"],"_WU_AV":["r:AvastReg","r:AvastBlackScreen","v:AvastVer","r:AvgReg","v:AvgVer","r:EsetReg","v:EsetVer","r:KasperskyReg","v:KasperskyVer","v:SymantecVer","r:TencentReg","r:TencentType","r:AhnlabInstalledKey","r:AvastInstalledKey","r:AVGInstalledKey","r:AviraInstalledKey","r:BullguardInstalledKey","r:ESETInstalledKey","r:ESTSecurityInstalledKey","r:FSecureInstalledKey","v:GDataInstalledVer","r:K7InstalledKey","r:KasperskyInstalledKey","r:KingsoftInstalledKey","r:LenovoInstalledKey","r:MalwarebytesInstalledKey","r:McAfeeInstalledKey","r:PandaInstalledKey","r:QuickhealInstalledKey1","r:SophosInstalledKey1","r:SymantecInstalledKey","r:TencentInstalledKey","r:ThreatTrackInstalledKey","r:TrendInstalledKey","r:WebrootInstalledKey","v:K7InstalledVer"],"_WU_COMMON":["r:CurrentBranch","r:DefaultUserRegion","DeviceFamily","r:DriverPartnerRing","r:FlightContent","f:FlightingBranchName","f:FlightRing","HoloLens","c:InstallationType","c:InstallLanguage","f:IsFlightingEnabled","r:IsFlightingEnabled","c:MobileOperatorCommercialized","OEMModel","OEMName_Uncleaned","r:OemPartnerRing","OSArchitecture","OSVersion","t:OSSkuId","c:OSUILocale","c:ProcessorManufacturer","r:ReleaseType","v:SkypeRoomSystem","t:SMode","c:TelemetryLevel","r:WindowsMixedReality","v:WuClientVer","p:DucPublisherId","p:DucDeviceModelId","p:DucOemPartnerRing","p:DucCustomPackageId","p:DesiredOsVersion","p:DesiredSystemManifestVersion","r:TenantId"],"_WU_FB":["u:BranchReadinessLevel","u:DeferQualityUpdatePeriodInDays","u:DeferFeatureUpdatePeriodInDays","r:PausedFeatureStatus","r:PausedQualityStatus","u:TargetReleaseVersion","r:QUDeadline","r:UpdatePreference","r:UpdateOfferedDays","u:TargetProductVersion","DSS_Enrolled","r:NonSecurityUpdate","u:AdminOptedIntoRebootlessUpdates"],"WU_OS":["+_WU_OS_CORE","+_WU_FB"],"_WU_OS_CORE":["+_WU_COMMON","+_WU_AV","r:AhnLabKeyboard","a:Bios","r:BlockFeatureUpdates","c:CommercialId","a:DataVer_RS5","r:DisconnectedStandby","r:DchuNvidiaGrfxExists","r:DchuNvidiaGrfxVen","r:DchuIntelGrfxExists","r:DchuIntelGrfxVen","r:DchuAmdGrfxExists","r:DchuAmdGrfxVen","c:FirmwareVersion","a:Free","a:GStatus_RS3","a:GStatus_RS4","a:GStatus_RS5","r:HidOverGattReg","r:InstallDate","c:IsDeviceRetailDemo","c:IsPortableOperatingSystem","IsVM","c:OEMModelBaseBoard","r:OobeSeeker","r:OSRollbackBuild","r:OSRollbackCount","r:OSRollbackDate","PhoneTargetingName","r:PonchAllow","r:PonchBlock","c:ProcessorIdentifier","r:RecoveredFromBuild","r:RecoveredOnDate","r:Steam","v:TobiiVer","v:TrendMicroVer","r:UninstallActive","l:UpdateManagementGroup","a:UpgEx_RS3","a:UpgEx_RS4","a:UpgEx_RS5","a:Version_RS5","r:DisableWUfBOfferBlock","a:UpgEx_19H1","a:SdbVer_19H1","a:GStatus_19H1","a:GStatus_19H1Setup","a:TimestampEpochString_19H1Setup","a:GenTelRunTimestamp_19H1","a:DataExpDateEpoch_19H1","u:EnableWUfBUpgradeGates","r:GStatusBlockIDs_All","TimestampDelta_19H1Subtract19H1Setup","DataExpDateDelta_19H1Subtract19H1Setup","a:DataExpDateEpoch_19H1Setup","a:TimestampEpochString_19H1","r:IsContainerMgrInstalled","r:IsWDAGEnabled","r:MTPTargetingInfo","r:EKB19H2InstallCount","r:EKB19H2UnInstallCount","r:EKB19H2InstallTimeEpoch","r:EKB19H2UnInstallTimeEpoch","r:BlockEdgeWithChromiumUpdate","r:IsWDATPEnabled","r:IsAutopilotRegistered","r:EdgeWithChromiumInstallVersion","r:EdgeWithChromiumInstallFailureCount","r:IsEdgeWithChromiumInstalled","r:KioskMode","c:IsCloudDomainJoined","c:IsDomainJoined","a:DataExpDateEpoch_20H1","a:DataExpDateEpoch_20H1Setup","a:GStatus_20H1","a:GStatus_20H1Setup","a:SdbVer_20H1","a:TimestampEpochString_20H1","a:TimestampEpochString_20H1Setup","DataExpDateDelta_20H1Subtract20H1Setup","TimestampDelta_20H1Subtract20H1Setup","a:UpgEx_20H1","r:AutopilotUpdateInProgress","r:UHSEnrolled","r:HotPatchEKBInstalled","r:LCUVer","c:isCommercial","c:ActivationChannel","c:IsMDMEnrolled","c:SCCMClientID","r:ChinaTypeApproval_CTA","p:DesiredOcpVersion","r:UpgradeEligible","r:AllowInPlaceUpgrade","r:SH_SIPolicyCleanup","r:FeatureUpdateDeadline","a:DataExpDateEpoch_21H1","a:UpgEx_CO21H2","a:GStatus_21H1","DataExpDateDelta_21H1Subtract20H1Setup","TimestampDelta_21H1Subtract20H1Setup","a:TimestampEpochString_21H1","r:OEMSubModel","c:ProcessorModel","c:TPMVersion","r:StayOnWindows10Timestamp","a:GStatus_CO21H2Setup","TimestampDelta_CO21H2SubtractCO21H2Setup","DataExpDateDelta_CO21H2SubtractCO21H2Setup","a:TimestampEpochString_CO21H2Setup","a:DataExpDateEpoch_CO21H2Setup","a:TimestampEpochString_CO21H2","a:DataExpDateEpoch_CO21H2","a:GStatus_CO21H2","p:SetPolicyDrivenUpdateSourceForFeatureUpdates","r:DchuNvidiaGrfxVenTest","a:DataExpDateDelta_21H2Subtract20H1Setup","a:TimestampEpochString_21H2","a:TimestampDelta_21H2Subtract20H1Setup","a:GStatus_21H2","a:DataExpDateEpoch_21H2","r:DSS_Enrolled_DF","r:UpgradeAccepted","r:SetupDisplayedEulaVersion","c:ProcessorCores","c:ProcessorClockSpeed","c:TotalPhysicalRAM","c:SecureBootCapable","c:PrimaryDiskTotalCapacity","r:BitDefenderInstalledKey","r:BroadcomInstalledKey","v:CrowdStrikeInstalledVer","r:QihooInstalledKey","r:Win11UpgradeAcceptedTimestamp","a:UpgEx_NI22H2","r:OobeNdupAcceptedTarget","r:OobeNdupFU22621CommitChoice","a:DataExpDateEpoch_NI22H2","a:GStatus_NI22H2","a:GStatus_NI22H2Setup","a:TimestampEpochString_NI22H2Setup","TimestampDelta_NI22H2SubtractNI22H2Setup","DataExpDateDelta_NI22H2SubtractNI22H2Setup","a:DataExpDateEpoch_NI22H2Setup","a:TimestampEpochString_NI22H2","r:IsVbsEnabled","r:FODRetryPending","r:UserInPlaceUpgrade","v:HidparseDriversVer","v:HidparseSystem32Ver","v:HidparseSystem32Ver1","r:CIOptin","r:FlightingOptOutState","p:WSUSconfigured_csp","a:UpgEx_NI22H2Setup","a:UpgEx_CO21H2Setup","u:WUfBClientManaged","u:UpdateServiceUrl","u:AllowOptionalContent","FX_FlightIds","DL_OSVersion","r:ExpPkgs","r:UUSVersion","c:FlightIds","r:OobeNdupFUTarget","a:GStatus_NI23H2","a:DataExpDateEpoch_NI23H2","a:TimestampEpochString_NI23H2","DataExpDateDelta_NI23H2SubtractNI22H2Setup","TimestampDelta_NI23H2SubtractNI22H2Setup","r:LaunchUserOOBE","r:RobloxPlayer","r:RobloxStudio","c:VBSState","r:ARCHotpatchAttached_State","r:MDEWSLPluginReleaseRing","r:SystemGuard_Enabled","u:AdminOptedIntoRebootlessUpdates","r:LaunchOobeInEndUserSession","r:MDE4WSLPluginReleaseRing","r:AdminOptedIntoRebootlessUpdates_Server","r:IsRemoteDesktopSessionHost","a:UpgEx_GE24H2","s:IsA9CapablePC","a:UpgEx_GE24H2Setup","r:ProductType","a:DataExpDateEpoch_GE24H2","DataExpDateDelta_GE24H2SubtractGE24H2Setup","a:DataExpDateEpoch_GE24H2Setup","a:GStatus_GE24H2","a:GStatus_GE24H2Setup","a:TimestampEpochString_GE24H2","TimestampDelta_GE24H2SubtractGE24H2Setup","a:TimestampEpochString_GE24H2Setup","q:AIFabricCBSStableVer","c:IsVirtualDevice","a:SdbVer_GE24H2"],"_WU_PTI":["c:FrontFacingCameraResolution","c:RearFacingCameraResolution","c:TotalPhysicalRAM","c:NFCProximity","c:Magnetometer","c:Gyroscope","c:D3DMaxFeatureLevel","c:InternalPrimaryDisplayResolutionHorizontal","c:InternalPrimaryDisplayResolutionVetical"],"WU_STORE":["+_WU_COMMON","r:AppChannels","r:AppRMIDs","u:BranchReadinessLevel"]},"Required":["App","AppVer","AttrDataVer"],"Aliases":{"AccountFirstChar":"c:MSA_Accounts","aipc":"s:IsA9CapablePC","ccr":"r:ChargeCapacityRatio","ChassisTypeId":"c:ChassisType","CX_FlightIds":"c:CX_FlightIds","DataExpDateDelta_19H1Subtract19H1Setup":"a:DataExpDateEpoch_19H1_Subtract_DataExpDateEpoch_19H1Setup","DataExpDateDelta_20H1Subtract20H1Setup":"a:DataExpDateEpoch_20H1_Subtract_DataExpDateEpoch_20H1Setup","DataExpDateDelta_21H1Subtract20H1Setup":"a:DataExpDateEpoch_21H1_Subtract_DataExpDateEpoch_20H1Setup","DataExpDateDelta_CO21H2SubtractCO21H2Setup":"a:DataExpDateEpoch_CO21H2_Subtract_DataExpDateEpoch_CO21H2Setup","DataExpDateDelta_GE24H2SubtractGE24H2Setup":"a:DataExpDateEpoch_GE24H2_Subtract_DataExpDateEpoch_GE24H2Setup","DataExpDateDelta_NI22H2SubtractNI22H2Setup":"a:DataExpDateEpoch_NI22H2_Subtract_DataExpDateEpoch_NI22H2Setup","DataExpDateDelta_NI23H2SubtractNI22H2Setup":"a:DataExpDateEpoch_NI23H2_Subtract_DataExpDateEpoch_NI22H2Setup","deviceClass":"DeviceFamily","deviceId":"t:LocalDeviceID","DeviceId":"t:LocalDeviceID","DL_OSVersion2":"DL_OSVersion","drgng":"r:DurableDeviceRegionGeo","DSS_Enrolled":"r:DSS_Enrolled_State","EdgeStableVersion":"r:EdgeStableVersion","expId":"c:FlightIds","FlightRing":"f:FlightRing","FX_FlightIds":"c:FlightIds","iepe":"g:IsCampaignEdgePromotionEnabled","iste":"g:IsCampaignSegmentTargetingEnabled","IsVM":"a:ISVM","IX_FlightIds":"c:FlightIds","locale":"c:OSUILocale","ms":"t:IsMsftOwned","MX_FlightIds":"c:FlightIds","OEMModel":"c:OEMModelNumber","oemname":"r:SystemManufacturer","OEMName_Uncleaned":"c:OEMManufacturerName","osVer":"t:OSVersionFull","OSVersionFull":"t:OSVersionFull","PhoneTargetingName":"c:OEMModelName","prccn":"c:ProcessorCores","prccs":"c:ProcessorClockSpeed","prcmf":"c:ProcessorManufacturer","procm":"c:ProcessorModel","ram":"c:TotalPhysicalRAM","ring":"f:FlightRing","sampleId":"t:PopVal","sku":"t:OSSkuId","smbiosdm":"r:SystemProductName","TimestampDelta_19H1Subtract19H1Setup":"a:TimestampEpochString_19H1_Subtract_TimestampEpochString_19H1Setup","TimestampDelta_20H1Subtract20H1Setup":"a:TimestampEpochString_20H1_Subtract_TimestampEpochString_20H1Setup","TimestampDelta_21H1Subtract20H1Setup":"a:TimestampEpochString_21H1_Subtract_TimestampEpochString_20H1Setup","TimestampDelta_CO21H2SubtractCO21H2Setup":"a:TimestampEpochString_CO21H2_Subtract_TimestampEpochString_CO21H2Setup","TimestampDelta_GE24H2SubtractGE24H2Setup":"a:TimestampEpochString_GE24H2_Subtract_TimestampEpochString_GE24H2Setup","TimestampDelta_NI22H2SubtractNI22H2Setup":"a:TimestampEpochString_NI22H2_Subtract_TimestampEpochString_NI22H2Setup","TimestampDelta_NI23H2SubtractNI22H2Setup":"a:TimestampEpochString_NI23H2_Subtract_TimestampEpochString_NI22H2Setup"},"Fallback":{"r:AhnlabInstalledKey":"r:AhnlabInstalledWowKey","r:AvastBlackScreen":"r:AvgBlackScreen","r:AvastInstalledKey":"r:AvastInstalledWowKey","r:AVGInstalledKey":"r:AVGInstalledWowKey","r:AviraInstalledKey":"r:AviraInstalledWowKey","a:Bios":"a:Bios_RS3","a:Bios_RS3":"a:Bios_RS4","a:Bios_RS4":"a:Bios_RS5","r:BlockFeatureUpdates":"r:BlockWUUpgrades","r:BlockWUUpgrades":"r:BlockWUUpgradesWow","r:BuildFID":"r:BuildFID_WCOS","r:BuildFID_WCOS":"r:BuildFID_WCOS2","r:BullguardInstalledKey":"v:BullguardInstalledVer","a:DataExpDateEpoch_CO21H2":"r:DataExpDateEpoch_CO21H2RegFb","r:DchuAmdGrfxVen":"r:DchuAmdGrfxVen2","r:DchuAmdGrfxVen2":"r:DchuAmdGrfxDeletePending","r:DchuIntelGrfxDeletePending":"r:DchuIntelGrfxNExists","r:DchuIntelGrfxVen":"r:DchuIntelGrfxVen2","r:DchuIntelGrfxVen2":"r:DchuIntelGrfxDeletePending","r:DchuNvidiaGrfxVen":"r:DchuNvidiaGrfxVen2","r:DchuNvidiaGrfxVen2":"r:DchuNvidiaGrfxDeletePending","DL_OSVersion":"OSVersion","r:DriverPartnerRing":"r:OSDataDriverPartnerRing","r:EdgeStableOPV_Native":"r:EdgeStablePV_Native","r:EdgeStablePV_WOW6432":"r:EdgeStableOPV_Native","r:EdgeStableVersion":"r:EdgeStablePV_WOW6432","r:EdgeWithChromiumInstallFailureCount":"r:EdgeWithChromiumInstallFailureCountWow","r:EdgeWithChromiumInstallVersion":"r:EdgeWithChromiumInstallVersionWow","u:EnableWUfBUpgradeGates":"r:EnableWUfBUpgradeGatesRS5","r:ESETInstalledKey":"r:ESETInstalledWowKey","r:ESTSecurityInstalledKey":"r:ESTSecurityInstalledWowKey","f:FlightingBranchName":"c:FlightingBranchName","a:Free":"a:Free_RS3","a:Free_RS3":"a:Free_RS4","a:Free_RS4":"a:Free_RS5","r:FSecureInstalledKey":"r:FSecureInstalledWowKey","a:GatedFeature_NI22H2":"r:Migrated_GatedFeature_NI22H2Setup","a:GStatus_CO21H2":"r:GStatus_CO21H2RegFb","HoloLens":"r:WindowsMixedReality","r:IsEdgeWithChromiumInstalled":"r:IsEdgeWithChromiumInstalledWow","a:ISVM":"a:ISVM_RS3","a:ISVM_RS3":"a:ISVM_RS4","a:ISVM_RS4":"a:ISVM_RS5","r:K7InstalledKey":"r:K7InstalledWowKey","r:KasperskyInstalledKey":"r:KasperskyInstalledWowKey","r:KingsoftInstalledKey":"r:KingsoftInstalledWowKey","r:LenovoInstalledKey":"r:LenovoInstalledWowKey","r:MalwarebytesInstalledKey":"r:MalwarebytesInstalledWowKey","r:McAfeeInstalledKey":"r:McAfeeInstalledWowKey","r:Migrated_GatedFeature_NI22H2Setup":"r:Migrated_GatedFeature_NI22H2","c:OEMModelBaseBoard":"r:OEMModelBaseBoard","r:PandaInstalledKey":"r:PandaInstalledWowKey","r:PandaInstalledWowKey":"v:PandaInstalledVer","r:PonchAllow":"r:PonchAllowKey","r:PonchAllowKey":"r:PonchAllowWow","r:PonchAllowWow":"r:PonchAllowWowKey","r:QUDeadline":"r:QUDeadlineMDM","r:QuickhealInstalledKey1":"r:QuickhealInstalledKey2","r:SophosInstalledKey1":"r:SophosInstalledKey2","r:SymantecInstalledKey":"r:SymantecInstalledWowKey","v:SymantecVer":"v:SymantecVer64","u:TargetReleaseVersion":"r:TargetReleaseVersionGP","r:TargetReleaseVersionGP":"r:TargetReleaseVersionMDM","r:TencentInstalledKey":"r:TencentInstalledWowKey","r:ThreatTrackInstalledKey":"r:ThreatTrackInstalledWowKey","a:TimestampEpochString_CO21H2":"r:TimestampEpochString_CO21H2RegFb","v:TobiiVer":"v:TobiiVerx86","v:TobiiVerx86":"v:TobiiVer1x86","r:TrendInstalledKey":"r:TrendInstalledWowKey","r:TrendInstalledWowKey":"v:TrendInstalledVer","a:UpgEx_CO21H2":"r:UpgEx_CO21H2RegFb","r:UpgradeAccepted":"r:Win11UpgradeAcceptedWUSeeker","r:WebExperience":"r:WebExperienceWow","r:WebrootInstalledKey":"r:WebrootInstalledWowKey"},"Transform":{"AccountFirstChar":{"SubLength":1},"CX_FlightIds":{"Regex":"CX:[^,]*","RegexDelimiter":","},"FlightingOptOutState":{"Ignore":["0"]},"FX_FlightIds":{"Regex":"FX:[^,]*","RegexDelimiter":","},"IppPrinterBadDefaultPdc":{"Contains":"V4_No_ChangeID_Present"},"aipc":{"Ignore":["0"]},"IsDomainJoined":{"Ignore":["0"]},"IsHybridOrXGpu":{"Ignore":["0"]},"IsMsftOwned":{"Ignore":["0"]},"IsPortableOperatingSystem":{"Ignore":["0"]},"IsRemoteDesktopSessionHost":{"Contains":"ServerRdsh"},"IsTestLab":{"Ignore":["0"]},"IsVM":{"Ignore":["0"]},"IX_FlightIds":{"Regex":"IX:[^,]*","RegexDelimiter":","},"MX_FlightIds":{"Regex":"ME:[^,]*|MD:[^,]*","RegexDelimiter":","},"OEMModel":{"SubLength":100},"OEMName_Uncleaned":{"SubLength":100},"PausedFeatureStatus":{"Ignore":["0"]},"PausedQualityStatus":{"Ignore":["0"]},"PSAKyoceraInstalledName":{"Contains":"A97ECD55.KYOCERAPrintCenter"},"PSATATriumphInstalledName":{"Contains":"TATriumph-AdlerGmbH.TAUTAXPrintCenter"},"SMode":{"Ignore":["0"]},"StayOnWindows10Timestamp":{"SubLength":-3,"Ignore":[""]},"XeroxPsaInstalledName":{"Contains":"XeroxCorp.PrintExperience"}},"Registry":{"AADBrokerPluginNotRegistered":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\WindowsMitigationData\\AADBrokerPluginNotRegistered","IfExists":true},"ActiveHoursEnd":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\WindowsUpdate\\UX\\Settings","ValueName":"ActiveHoursEnd","RegValueType":"REG_DWORD"},"ActiveHoursStart":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\WindowsUpdate\\UX\\Settings","ValueName":"ActiveHoursStart","RegValueType":"REG_DWORD"},"AdminOptedIntoRebootlessUpdates_Server":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\Hotpatch\\Environment","ValueName":"AllowRebootlessUpdates","RegValueType":"REG_DWORD"},"AhnlabInstalledKey":{"FullPath":"SOFTWARE\\Ahnlab","IfExists":true},"AhnlabInstalledWowKey":{"FullPath":"SOFTWARE\\WOW6432Node\\Ahnlab","IfExists":true},"AhnLabKeyboard":{"FullPath":"SYSTEM\\CurrentControlSet\\Services\\Mkd2kfNt","ValueName":"NbTpMsExist"},"AllowInPlaceUpgrade":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\\\Windows\\\\CurrentVersion","ValueName":"AllowInPlaceUpgrade","RegValueType":"REG_DWORD"},"AllowUpgradesWithUnsupportedTPMOrCPU":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SYSTEM\\Setup\\MoSetup","ValueName":"AllowUpgradesWithUnsupportedTPMOrCPU","RegValueType":"REG_DWORD"},"AndroidUserOptinValue":{"HKey":"HKEY_CURRENT_USER","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Mobility\\","ValueName":"OptedIn","RegValueType":"REG_DWORD"},"AppChannels":{"FullPath":"SOFTWARE\\Policies\\Microsoft\\WindowsStore\\Apps\\*","ValueName":"ChannelId","EncodingType":"Json"},"AppRMIDs":{"FullPath":"SOFTWARE\\Policies\\Microsoft\\WindowsStore\\Apps\\*","ValueName":"ReleaseManagementId","EncodingType":"Json"},"ARCHotpatchAttached_State":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Azure Connected Machine Agent\\Windows\\Licenses\\Features\\Hotpatch","ValueName":"Subscription","RegValueType":"REG_DWORD"},"AutopilotUpdateInProgress":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Provisioning\\AutopilotSettings\\VolatileAutopilotUpdate","ValueName":"AutopilotUpdateInProgress","RegValueType":"REG_DWORD"},"AvastBlackScreen":{"FullPath":"SYSTEM\\CurrentControlSet\\Services\\aswVmm\\Parameters","ValueName":"Win10-1803"},"AvastInstalledKey":{"FullPath":"SOFTWARE\\Avast Software\\Avast","IfExists":true},"AvastInstalledWowKey":{"FullPath":"SOFTWARE\\WOW6432Node\\Avast Software\\Avast","IfExists":true},"AvastReg":{"FullPath":"SYSTEM\\CurrentControlSet\\Services\\aswVmm\\Parameters","ValueName":"QualityCompat"},"AvgBlackScreen":{"FullPath":"SYSTEM\\CurrentControlSet\\Services\\avgVmm\\Parameters","ValueName":"Win10-1803"},"AVGInstalledKey":{"FullPath":"SOFTWARE\\AVG\\Antivirus","IfExists":true},"AVGInstalledWowKey":{"FullPath":"SOFTWARE\\WOW6432Node\\AVG\\Antivirus","IfExists":true},"AvgReg":{"FullPath":"SYSTEM\\CurrentControlSet\\Services\\avgVmm\\Parameters","ValueName":"QualityCompat"},"AviraInstalledKey":{"FullPath":"SOFTWARE\\X-AVCSD\\Workstation\\Antivirus","IfExists":true},"AviraInstalledWowKey":{"FullPath":"SOFTWARE\\WOW6432Node\\X-AVCSD\\Workstation\\Antivirus","IfExists":true},"BaseBoardManufacturer":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"HARDWARE\\DESCRIPTION\\System\\BIOS","ValueName":"BaseBoardManufacturer"},"BitDefenderInstalledKey":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"Software\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\{1FCCF41D-5F00-4FE2-9653-162D0486C8B4}","IfExists":true},"BlockEdgeWithChromiumUpdate":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\EdgeUpdate","ValueName":"DoNotUpdateToEdgeWithChromium","RegValueType":"REG_DWORD"},"BlockFeatureUpdates":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\WindowsUpdate\\OSUpgrade","ValueName":"BlockFeatureUpdates","RegValueType":"REG_DWORD"},"BlockWUUpgrades":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows10Upgrader\\Volatile","ValueName":"BlockWUUpgrades","RegValueType":"REG_DWORD"},"BlockWUUpgradesWow":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\WOW6432Node\\Microsoft\\Windows10Upgrader\\Volatile","ValueName":"BlockWUUpgrades","RegValueType":"REG_DWORD"},"BroadcomInstalledKey":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Symantec\\Symantec Endpoint Protection","IfExists":true},"BuildFID":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"Software\\Microsoft\\Windows\\CurrentVersion\\Flighting\\Build","ValueName":"EsdFlightData","RegValueType":"REG_SZ"},"BuildFID_WCOS":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"OSDATA\\Software\\Microsoft\\Windows\\CurrentVersion\\Flighting\\Build","ValueName":"EsdFlightData","RegValueType":"REG_SZ"},"BuildFID_WCOS2":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"OSDATA\\Microsoft\\Windows\\CurrentVersion\\Flighting\\Build","ValueName":"EsdFlightData","RegValueType":"REG_SZ"},"BullguardInstalledKey":{"FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\BullGuard","IfExists":true},"BypassNRO":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\OOBE","ValueName":"BypassNRO","RegValueType":"REG_DWORD"},"ChargeCapacityRatio":{"HKey":"HKEY_CURRENT_USER","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\HealthSignals","ValueName":"ChargeCapacityRatio","RegValueType":"REG_DWORD"},"ChinaTypeApproval_CTA":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\DeviceAccess","ValueName":"ActivePolicyCode","RegValueType":"REG_SZ"},"CIOptin":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\WindowsUpdate\\UX\\Settings","ValueName":"IsContinuousInnovationOptedIn","RegValueType":"REG_DWORD"},"CloudFilesFilter":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SYSTEM\\CurrentControlSet\\Services\\CldFlt\\Instances\\","ValueName":"DefaultInstance","RegValueType":"REG_SZ"},"CurrentBranch":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion","ValueName":"BuildBranch","RegValueType":"REG_SZ"},"DataExpDateEpoch_CO21H2RegFb":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\AppCompatFlags\\TargetVersionUpgradeExperienceIndicators\\CO21H2","ValueName":"DataExpDateEpoch","RegValueType":"REG_SZ"},"DaysSince19H1FUOffer":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\rempl\\irplugin","ValueName":"DaysSinceLastOffer","RegValueType":"REG_QWORD"},"DchuAmdGrfxDeletePending":{"FullPath":"SYSTEM\\CurrentControlSet\\Services\\amdkmdag","ValueName":"DriverDelete"},"DchuAmdGrfxExists":{"FullPath":"SYSTEM\\CurrentControlSet\\Services\\amdkmdag","IfExists":true},"DchuAmdGrfxVen":{"FullPath":"SYSTEM\\CurrentControlSet\\Services\\amdkmdag","ValueName":"DCHUVen"},"DchuAmdGrfxVen2":{"FullPath":"SYSTEM\\CurrentControlSet\\Services\\amdkmdag\\Parameters","ValueName":"DCHUVen"},"DchuIntelGrfxDeletePending":{"FullPath":"SYSTEM\\CurrentControlSet\\Services\\igfx","ValueName":"DriverDelete"},"DchuIntelGrfxExists":{"FullPath":"SYSTEM\\CurrentControlSet\\Services\\igfx","IfExists":true},"DchuIntelGrfxNExists":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SYSTEM\\CurrentControlSet\\Services\\igfxn","IfExists":true},"DchuIntelGrfxVen":{"FullPath":"SYSTEM\\CurrentControlSet\\Services\\igfx","ValueName":"DCHUVen"},"DchuIntelGrfxVen2":{"FullPath":"SYSTEM\\CurrentControlSet\\Services\\igfx\\Parameters","ValueName":"DCHUVen"},"DchuNvidiaGrfxDeletePending":{"FullPath":"SYSTEM\\CurrentControlSet\\Services\\nvlddmkm","ValueName":"DriverDelete"},"DchuNvidiaGrfxExists":{"FullPath":"SYSTEM\\CurrentControlSet\\Services\\nvlddmkm","IfExists":true},"DchuNvidiaGrfxVen":{"FullPath":"SYSTEM\\CurrentControlSet\\Services\\nvlddmkm","ValueName":"DCHUVen"},"DchuNvidiaGrfxVen2":{"FullPath":"SYSTEM\\CurrentControlSet\\Services\\nvlddmkm\\Parameters","ValueName":"DCHUVen"},"DchuNvidiaGrfxVenTest":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SYSTEM\\CurrentControlSet\\Services\\nvlddmkm","ValueName":"DCHUVenTest","RegValueType":"REG_DWORD"},"DefaultUserRegion":{"HKey":"HKEY_USERS","FullPath":".DEFAULT\\Control Panel\\International\\Geo","ValueName":"Nation","RegValueType":"REG_SZ"},"DeviceInfoGatherSuccessful":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Component Based Servicing","ValueName":"DeviceInfoGatherSuccessful","RegValueType":"REG_DWORD"},"DisableWUfBOfferBlock":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\WindowsUpdate\\UpdatePolicy\\Settings","ValueName":"DisableWUfBOfferBlock","RegValueType":"REG_DWORD"},"DisconnectedStandby":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SYSTEM\\CurrentControlSet\\Control\\Power","ValueName":"EnforceDisconnectedStandby","RegValueType":"REG_DWORD"},"DotNetMissingComponentsTroubleshooterSuccess":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\.NETFramework","ValueName":"DotNetMissingComponentsTroubleshooterSuccess","RegValueType":"REG_DWORD"},"DriverPartnerRing":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\DriverFlighting\\Partner","ValueName":"TargetRing","RegValueType":"REG_SZ"},"DSS_Enrolled_DF":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\\\Policies\\\\Microsoft\\\\Windows\\\\WindowsUpdate","ValueName":"WUfBDF","RegValueType":"REG_DWORD"},"DSS_Enrolled_State":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\WufbDS","ValueName":"enrollmenttype","RegValueType":"REG_SZ"},"DUInternal":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SYSTEM\\Setup\\MoSetup","ValueName":"DynamicUpdateInternalTest","RegValueType":"REG_DWORD"},"DurableDeviceRegionGeo":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Control Panel\\DeviceRegion","ValueName":"DeviceRegion","RegValueType":"REG_DWORD"},"EdgeStableOPV_Native":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\EdgeUpdate\\Clients\\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}","ValueName":"opv","RegValueType":"REG_SZ"},"EdgeStablePV_Native":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\EdgeUpdate\\Clients\\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}","ValueName":"pv","RegValueType":"REG_SZ"},"EdgeStablePV_WOW6432":{"FullPath":"SOFTWARE\\Wow6432Node\\Microsoft\\EdgeUpdate\\Clients\\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}","ValueName":"pv","RegValueType":"REG_SZ"},"EdgeStableVersion":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Wow6432Node\\Microsoft\\EdgeUpdate\\Clients\\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}","ValueName":"opv","RegValueType":"REG_SZ"},"EdgeWithChromiumInstallFailureCount":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\EdgeUpdate","ValueName":"WindowsUpdateAttempts"},"EdgeWithChromiumInstallFailureCountWow":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Wow6432Node\\Microsoft\\EdgeUpdate","ValueName":"WindowsUpdateAttempts"},"EdgeWithChromiumInstallVersion":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\EdgeUpdate","ValueName":"WindowsUpdateVersion"},"EdgeWithChromiumInstallVersionWow":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Wow6432Node\\Microsoft\\EdgeUpdate","ValueName":"WindowsUpdateVersion"},"EKB19H2InstallCount":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SYSTEM\\Setup\\FeatureStaging\\20455539\\2","ValueName":"Count"},"EKB19H2InstallTimeEpoch":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SYSTEM\\Setup\\FeatureStaging\\20455539\\2","ValueName":"Timestamp"},"EKB19H2UnInstallCount":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SYSTEM\\Setup\\FeatureStaging\\20455539\\0","ValueName":"Count"},"EKB19H2UnInstallTimeEpoch":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SYSTEM\\Setup\\FeatureStaging\\20455539\\0","ValueName":"Timestamp"},"EnableWUfBUpgradeGatesRS5":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"Software\\Microsoft\\Windows NT\\CurrentVersion\\502505fe-762c-4e80-911e-0c3fa4c63fb0","ValueName":"DataRequireGatedScanForFeatureUpdates","RegValueType":"REG_DWORD"},"ESETInstalledKey":{"FullPath":"SOFTWARE\\ESET\\ESET Security","IfExists":true},"ESETInstalledWowKey":{"FullPath":"SOFTWARE\\WOW6432Node\\ESET\\ESET Security","IfExists":true},"EsetReg":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SYSTEM\\CurrentControlSet\\Services\\ehdrv\\Parameters","ValueName":"WindowsCompatibilityLevel","RegValueType":"REG_DWORD"},"ESTSecurityInstalledKey":{"FullPath":"SOFTWARE\\ESTsoft","IfExists":true},"ESTSecurityInstalledWowKey":{"FullPath":"SOFTWARE\\WOW6432Node\\ESTsoft","IfExists":true},"ExpPkgs":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\WindowsSelfhost\\Applicability","ValueName":"ExpPkgs","RegValueType":"REG_SZ"},"ExpStates":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\WindowsSelfHost\\FIDs","ValueName":"PreviewConfigs","RegValueType":"REG_SZ"},"FeatureUpdateDeadline":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"Software\\Policies\\Microsoft\\Windows\\WindowsUpdate\\","ValueName":"ConfigureDeadlineForFeatureUpdates","RegValueType":"REG_DWORD"},"FlightContent":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\WindowsSelfHost\\Applicability","ValueName":"ContentType","RegValueType":"REG_SZ"},"FlightingOptOutState":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\WindowsSelfHost\\UI\\Selection","ValueName":"OptOutState","RegValueType":"REG_DWORD"},"FODRetryPending":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Component Based Servicing","ValueName":"FODRetry","RegValueType":"REG_DWORD"},"FSecureInstalledKey":{"FullPath":"SOFTWARE\\F-Secure\\OneClient","IfExists":true},"FSecureInstalledWowKey":{"FullPath":"SOFTWARE\\WOW6432Node\\F-Secure\\OneClient","IfExists":true},"FSRing":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\WindowsSelfhost\\Applicability","ValueName":"FSRing","RegValueType":"REG_SZ"},"GamingServicesInstalledKey":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SYSTEM\\CurrentControlSet\\Services\\GamingServices","IfExists":true},"GridZoneName":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\COAWOS","ValueName":"GridZoneName","RegValueType":"REG_SZ","PersistedSourceId":"COAWOSRoot"},"GStatus_CO21H2RegFb":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\AppCompatFlags\\TargetVersionUpgradeExperienceIndicators\\CO21H2","ValueName":"GStatus","RegValueType":"REG_SZ"},"GStatusBlockIDs_All":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\AppCompatFlags\\Appraiser\\GWX","ValueName":"SdbEntries","RegValueType":"REG_SZ"},"HidOverGattReg":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Setup\\PnpLockdownFiles\\%SystemRoot%/System32/drivers/UMDF/Microsoft.Bluetooth.Profiles.HidOverGatt.dll","ValueName":"Source","RegValueType":"REG_SZ"},"HotPatchEKBInstalled":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Update\\TargetingInfo\\DynamicInstalled\\Hotpatch.amd64","IfExists":true},"IIS_ASPNET":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Component Based Servicing\\Notifications\\OptionalFeatures\\IIS-ASPNET","ValueName":"Selection","RegValueType":"REG_DWORD"},"IIS_NetFxExtensibility":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Component Based Servicing\\Notifications\\OptionalFeatures\\IIS-NetFxExtensibility","ValueName":"Selection","RegValueType":"REG_DWORD"},"InstallDate":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion","ValueName":"InstallDate","RegValueType":"REG_DWORD"},"IntelPlatformId":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"HARDWARE\\DESCRIPTION\\System\\CentralProcessor\\0","ValueName":"Platform Specific Field 1","RegValueType":"REG_DWORD"},"IppPrinterBadDefaultPdc":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Print\\Printers\\*\\PrinterDriverData","ValueName":"V4_PDC_ChangeID","RegValueType":"REG_SZ","EncodingType":"Json"},"IsAutopilotRegistered":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Provisioning\\AutopilotPolicyCache","ValueName":"ProfileAvailable","RegValueType":"REG_DWORD"},"IsFlightingEnabled":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\WindowsSelfHost\\Applicability","ValueName":"IsBuildFlightingEnabled","RegValueType":"REG_DWORD"},"IsCHCapableBuild":{"HKey":"HKEY_CLASSES_ROOT","FullPath":"CLSID\\{2C57C51B-FD43-4E74-B077-551AE6228AD6}","IfExists":true},"IsCldFltSyncRoots":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Explorer\\SyncRootManager\\*","IfExists":true},"IsConfigMgrEnabled":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\WindowsSelfHost\\ClientState","ValueName":"ConfigMgrEnabled","RegValueType":"REG_DWORD"},"IsContainerMgrInstalled":{"FullPath":"SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Containers\\CmService","IfExists":true},"IsEdgeWithChromiumInstalled":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\EdgeUpdate\\Clients\\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}","IfExists":true},"IsEdgeWithChromiumInstalledWow":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Wow6432Node\\Microsoft\\EdgeUpdate\\Clients\\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}","IfExists":true},"IsFeedbackHubSelfhost":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Diagnostics\\DiagTrack\\Partners\\IsFeedbackHubSelfhost","IfExists":true},"IsFSOverlay":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SYSTEM\\CurrentControlSet\\Control\\GlobMerger","ValueName":"IsEnabled","RegValueType":"REG_DWORD"},"IsHybridOrXGpu":{"FullPath":"SOFTWARE\\Microsoft\\DirectX","ValueName":"HybridDeviceApplicableForDxDbGpuPreferences"},"IsProcessorMode":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Diagnostics\\DiagTrack\\RegionalSettings","ValueName":"IsProcessorMode","RegValueType":"REG_QWORD"},"IsRemoteDesktopSessionHost":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion","ValueName":"EditionID","RegValueType":"REG_SZ"},"IsSpotlightEnabledInOEMTheme":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Themes","ValueName":"WindowsSpotlight","RegValueType":"REG_DWORD"},"IsSpotlightThemeEnabledByOEM":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Explorer\\DesktopOptimization","ValueName":"WindowsSpotlightTheme","RegValueType":"REG_DWORD"},"IsVbsEnabled":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SYSTEM\\ControlSet001\\Control\\DeviceGuard","ValueName":"EnableVirtualizationBasedSecurity","RegValueType":"REG_DWORD"},"IsWDAGEnabled":{"FullPath":"SYSTEM\\ControlSet001\\Services\\hvsics","IfExists":true},"IsWDATPEnabled":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows Advanced Threat Protection\\Status","ValueName":"OnboardingState"},"K7InstalledKey":{"FullPath":"SOFTWARE\\K7 Computing","IfExists":true},"K7InstalledWowKey":{"FullPath":"SOFTWARE\\WOW6432Node\\K7 Computing","IfExists":true},"KasperskyInstalledKey":{"FullPath":"SOFTWARE\\KasperskyLab","IfExists":true},"KasperskyInstalledWowKey":{"FullPath":"SOFTWARE\\WOW6432Node\\KasperskyLab","IfExists":true},"KasperskyReg":{"FullPath":"System\\CurrentControlSet\\Services\\klhk\\Parameters","ValueName":"UseVtHardware"},"KingsoftInstalledKey":{"FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\Kingsoft Internet Security","IfExists":true},"KingsoftInstalledWowKey":{"FullPath":"SOFTWARE\\WOW6432Node\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\Kingsoft Internet Security","IfExists":true},"KioskMode":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\AssignedAccessCsp\\AutoLogonAccount","ValueName":"ConfigSource","RegValueType":"REG_DWORD"},"KnownFoldersBackupStatus":{"HKey":"HKEY_CURRENT_USER","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Explorer\\StorageProviderStatus","ValueName":"OneDrive","RegValueType":"REG_SZ"},"LaunchOobeInEndUserSession":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"Software\\Microsoft\\Windows\\CurrentVersion\\OOBE","ValueName":"ContinueOobeInEnduserSession"},"LaunchUserOOBE":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"Software\\Microsoft\\Windows\\CurrentVersion\\OOBE","ValueName":"LaunchUserOOBE","RegValueType":"REG_DWORD"},"LCUVer":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion","ValueName":"LCUVer"},"LenovoInstalledKey":{"FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\{A9861883-31C5-4324-BD9A-DC9527EEB675}_is1","IfExists":true},"LenovoInstalledWowKey":{"FullPath":"SOFTWARE\\WOW6432Node\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\{A9861883-31C5-4324-BD9A-DC9527EEB675}_is1","IfExists":true},"MalwarebytesInstalledKey":{"FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\{35065F43-4BB2-439A-BFF7-0F1014F2E0CD}_is1","IfExists":true},"MalwarebytesInstalledWowKey":{"FullPath":"SOFTWARE\\WOW6432Node\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\{35065F43-4BB2-439A-BFF7-0F1014F2E0CD}_is1","IfExists":true},"McAfeeInstalledKey":{"FullPath":"SOFTWARE\\McAfee\\MSC\\AppInfo\\Substitute\\QueryParams","IfExists":true},"McAfeeInstalledWowKey":{"FullPath":"SOFTWARE\\WOW6432Node\\McAfee\\MSC\\AppInfo\\Substitute\\QueryParams","IfExists":true},"MDE4WSLPluginReleaseRing":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Microsoft Defender for Endpoint plug-in for WSL","ValueName":"ReleaseRing","RegValueType":"REG_SZ"},"MDEWSLPluginReleaseRing":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"Software\\Microsoft\\Windows\\CurrentVersion\\Lxss\\Plugins\\DefenderPlug-in","ValueName":"ReleaseRing","RegValueType":"REG_SZ"},"Migrated_GatedFeature_NI22H2":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\AppCompatFlags\\MigratedMarkers\\TargetVersionUpgradeExperienceIndicators\\NI22H2","ValueName":"GatedFeatureSingleString","RegValueType":"REG_SZ"},"Migrated_GatedFeature_NI22H2Setup":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\AppCompatFlags\\MigratedMarkers\\TargetVersionUpgradeExperienceIndicators\\NI22H2Setup","ValueName":"GatedFeatureSingleString","RegValueType":"REG_SZ"},"MTPTargetingInfo":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SYSTEM\\Platform\\MTPTargetingInfo","ValueName":"TargetRing"},"NonSecurityUpdate":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Policies\\Microsoft\\Windows\\WindowsUpdate","ValueName":"NonSecurityRelease","RegValueType":"REG_DWORD"},"NPUEnabledDevice":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows Media Foundation\\FrameServer\\WindowsCameraEffects","ValueName":"EffectsCameraAvailable","RegValueType":"REG_DWORD"},"OEMMode":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Office\\16.0\\Common\\OEM","ValueName":"OOBEMode","RegValueType":"REG_SZ"},"OEMModelBaseBoard":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"HARDWARE\\DESCRIPTION\\System\\BIOS","ValueName":"BaseBoardProduct","RegValueType":"REG_SZ"},"OemPartnerRing":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SYSTEM\\Platform\\DeviceTargetingInfo","ValueName":"TargetRing","RegValueType":"REG_SZ"},"OEMSubModel":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"HARDWARE\\DESCRIPTION\\System\\BIOS","ValueName":"SystemSKU","RegValueType":"REG_SZ"},"OobeNdupAcceptedTarget":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Setup\\OOBE\\NDUP\\Updates","ValueName":"Target","RegValueType":"REG_SZ"},"OobeNdupFU22621CommitChoice":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\NDUP\\Updates\\FeatureUpdate_22621","ValueName":"CommitChoice","RegValueType":"REG_DWORD"},"OobeNdupFUTarget":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\NDUP\\Updates\\FeatureUpdate_22631","ValueName":"Target","RegValueType":"REG_SZ"},"OobeSeeker":{"FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\OOBE\\Updates","ValueName":"OOBEUpdateStarted"},"OSDataDriverPartnerRing":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"OSData\\SOFTWARE\\Microsoft\\DriverFlighting\\Partner","ValueName":"TargetRing","RegValueType":"REG_SZ"},"OSRollbackBuild":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\WindowsUpdate\\OSUpgrade\\Rollback","ValueName":"BuildString","RegValueType":"REG_SZ"},"OSRollbackCount":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\WindowsUpdate\\OSUpgrade\\Rollback","ValueName":"Count","RegValueType":"REG_DWORD"},"OSRollbackDate":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\WindowsUpdate\\OSUpgrade\\Rollback","ValueName":"DateStamp","RegValueType":"REG_DWORD"},"PandaInstalledKey":{"FullPath":"SOFTWARE\\Panda Software\\Setup","IfExists":true},"PandaInstalledWowKey":{"FullPath":"SOFTWARE\\WOW6432Node\\Panda Software\\Setup","IfExists":true},"PausedFeatureStatus":{"FullPath":"SOFTWARE\\Microsoft\\WindowsUpdate\\UpdatePolicy\\Settings","ValueName":"PausedFeatureStatus"},"PausedQualityStatus":{"FullPath":"SOFTWARE\\Microsoft\\WindowsUpdate\\UpdatePolicy\\Settings","ValueName":"PausedQualityStatus"},"PlayFabPartyRelay":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\PlayFabPartyRelay","IfExists":true},"PonchAllow":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\QualityCompat","ValueName":"cadca5fe-87d3-4b96-b7fb-a231484277cc","RegValueType":"REG_DWORD"},"PonchAllowKey":{"FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\QualityCompat\\cadca5fe-87d3-4b96-b7fb-a231484277cc","IfExists":true},"PonchAllowWow":{"FullPath":"SOFTWARE\\WOW6432Node\\Microsoft\\Windows\\CurrentVersion\\QualityCompat","ValueName":"cadca5fe-87d3-4b96-b7fb-a231484277cc"},"PonchAllowWowKey":{"FullPath":"SOFTWARE\\WOW6432Node\\Microsoft\\Windows\\CurrentVersion\\QualityCompat\\cadca5fe-87d3-4b96-b7fb-a231484277cc","IfExists":true},"PonchBlock":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\QualityCompat","ValueName":"65d75b03-6f4d-46e9-b870-517731e06cf9","RegValueType":"REG_DWORD"},"PreviewBuildsManagerEnabled":{"FullPath":"SOFTWARE\\Microsoft\\WindowsSelfhost\\Manager","ValueName":"ArePreviewBuildsAllowed"},"ProductType":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SYSTEM\\CurrentControlSet\\Control\\ProductOptions","ValueName":"ProductType"},"PSAKyoceraMissingDEH":{"HKey":"HKEY_CLASSES_ROOT","FullPath":"Extensions\\ContractId\\Windows.PrintSupportExtension\\PackageId\\A97ECD55.KYOCERAPrintCenter_4.1.11108.0_x64__kqmhh0ktdt7dg","IfExists":true},"PSATATriumphMissingDEH":{"HKey":"HKEY_CLASSES_ROOT","FullPath":"Extensions\\ContractId\\Windows.PrintSupportExtension\\PackageId\\TATriumph-AdlerGmbH.TAUTAXPrintCenter_4.1.11108.0_x64__h5e8vsnevp54y","IfExists":true},"PSAXeroxMissingDEH":{"HKey":"HKEY_CLASSES_ROOT","FullPath":"Extensions\\ContractId\\Windows.PrintSupportExtension\\PackageId\\XeroxCorp.PrintExperience_8.29.32.0_x64__f7egpvdyrs2a8","IfExists":true},"QihooInstalledKey":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"Software\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\360TotalSecurity","IfExists":true},"QUDeadline":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Policies\\Microsoft\\Windows\\WindowsUpdate","ValueName":"ConfigureDeadlineForQualityUpdates","RegValueType":"REG_DWORD"},"QUDeadlineMDM":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\PolicyManager\\current\\device\\Update","ValueName":"ConfigureDeadlineForQualityUpdates","RegValueType":"REG_DWORD"},"QuickhealInstalledKey1":{"FullPath":"SYSTEM\\CurrentControlSet\\Servicescatflt","IfExists":true},"QuickhealInstalledKey2":{"FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\App Paths\\scanner.exe","IfExists":true},"RecoveredFromBuild":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"Software\\Microsoft\\WindowsSelfHost\\Applicability\\RecoveredFrom","ValueName":"LastBuild","RegValueType":"REG_DWORD"},"RecoveredOnDate":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"Software\\Microsoft\\WindowsSelfHost\\Applicability\\RecoveredFrom","ValueName":"DateStamp","RegValueType":"REG_DWORD"},"ReleaseType":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Update\\TargetingInfo","ValueName":"ReleaseType","RegValueType":"REG_SZ"},"RobloxPlayer":{"HKey":"HKEY_CLASSES_ROOT","FullPath":"roblox-player","RegValueType":"REG_SZ","IfExists":true},"RobloxStudio":{"HKey":"HKEY_CLASSES_ROOT","FullPath":"roblox-studio","RegValueType":"REG_SZ","IfExists":true},"SetupDisplayedEulaVersion":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Setup\\OOBE\\","ValueName":"SetupDisplayedEulaVersion","RegValueType":"REG_DWORD"},"SH_SIPolicyCleanup":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\PPI\\Settings","ValueName":"SIPolicyCleanup","RegValueType":"REG_DWORD"},"SmartActiveHoursState":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\WindowsUpdate\\UX\\Settings","ValueName":"SmartActiveHoursState","RegValueType":"REG_DWORD"},"SophosInstalledKey1":{"FullPath":"SYSTEM\\CurrentControlSet\\Services\\SAVService","IfExists":true},"SophosInstalledKey2":{"FullPath":"SYSTEM\\CurrentControlSet\\Services\\hmpalertsvc","IfExists":true},"StayOnWindows10Timestamp":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\WindowsUpdate\\UX\\Settings","ValueName":"SvOfferDeclined","RegValueType":"REG_QWORD"},"Steam":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Classes\\Steam","ValueName":"","RegValueType":"REG_SZ"},"StrictHiveSecurityReg":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"Software\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\*","ValueName":"StrictHiveSecuritySet"},"SymantecInstalledKey":{"FullPath":"SOFTWARE\\Norton\\{0C55C096-0F1D-4F28-AAA2-85EF591126E7}","IfExists":true},"SymantecInstalledWowKey":{"FullPath":"SOFTWARE\\WOW6432Node\\Norton\\{0C55C096-0F1D-4F28-AAA2-85EF591126E7}","IfExists":true},"SystemGuard_Enabled":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SYSTEM\\CurrentControlSet\\Control\\DeviceGuard\\Scenarios\\SystemGuard","ValueName":"Enabled","RegValueType":"REG_DWORD"},"SystemManufacturer":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SYSTEM\\CurrentControlSet\\Control\\SystemInformation","ValueName":"SystemManufacturer","RegValueType":"REG_SZ"},"SystemProductName":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SYSTEM\\CurrentControlSet\\Control\\SystemInformation","ValueName":"SystemProductName","RegValueType":"REG_SZ"},"TargetReleaseVersionGP":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Policies\\Microsoft\\Windows\\WindowsUpdate","ValueName":"TargetReleaseVersionInfo","RegValueType":"REG_SZ"},"TargetReleaseVersionMDM":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\PolicyManager\\current\\device\\Update","ValueName":"TargetReleaseVersion","RegValueType":"REG_SZ"},"TenantId":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SYSTEM\\CurrentControlSet\\Control\\CloudDomainJoin\\JoinInfo\\*","ValueName":"TenantId"},"TencentInstalledKey":{"FullPath":"SOFTWARE\\Tencent\\QQPCMgr","IfExists":true},"TencentInstalledWowKey":{"FullPath":"SOFTWARE\\WOW6432Node\\Tencent\\QQPCMgr","IfExists":true},"TencentReg":{"FullPath":"SYSTEM\\CurrentControlSet\\services\\TesSafe","ValueName":"LoadStartTime"},"TencentType":{"FullPath":"SYSTEM\\CurrentControlSet\\services\\TesSafe","ValueName":"Type"},"TestAllowedIDFlags":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\OOBE\\TestHooks","ValueName":"TestAllowedIDFlags","RegValueType":"REG_DWORD"},"TestRN":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Wosc\\Client\\Persistent\\ClientState\\FCON","ValueName":"TestRing"},"ThreatTrackInstalledKey":{"FullPath":"SOFTWARE\\SBAMSvc","IfExists":true},"ThreatTrackInstalledWowKey":{"FullPath":"SOFTWARE\\WOW6432Node\\SBAMSvc","IfExists":true},"TimestampEpochString_CO21H2RegFb":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\AppCompatFlags\\TargetVersionUpgradeExperienceIndicators\\CO21H2","ValueName":"TimestampEpochString","RegValueType":"REG_SZ"},"TrendInstalledKey":{"FullPath":"SOFTWARE\\TrendMicro","IfExists":true},"TrendInstalledWowKey":{"FullPath":"SOFTWARE\\WOW6432Node\\TrendMicro","IfExists":true},"UHSEnrolled":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion","ValueName":"UHSEnrolled","RegValueType":"REG_SZ","IfExists":true},"UninstallActive":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"System\\Setup","ValueName":"UninstallActive","RegValueType":"REG_DWORD"},"UpdateOfferedDays":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\WaaSAssessment\\Cache\\","ValueName":"UpToDateDays","RegValueType":"REG_DWORD"},"UpdatePreference":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Policies\\Microsoft\\Windows\\WindowsUpdate","ValueName":"UpdatePreference","RegValueType":"REG_DWORD"},"UpgEx_CO21H2RegFb":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\AppCompatFlags\\TargetVersionUpgradeExperienceIndicators\\CO21H2","ValueName":"UpgEx","RegValueType":"REG_SZ"},"UpgradeAccepted":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\OOBE\\Updates\\","ValueName":"UpgradeAccepted","RegValueType":"REG_DWORD","IfExists":true},"UpgradeEligible":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\\\Microsoft\\\\Windows\\\\CurrentVersion","ValueName":"UpgradeEligible","RegValueType":"REG_DWORD"},"UserInPlaceUpgrade":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\\\Windows\\\\CurrentVersion","ValueName":"UserInPlaceUpgrade","RegValueType":"REG_DWORD"},"UsoScanMitigation":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\WindowsUpdate\\Orchestrator\\Mitigation\\","ValueName":"UsoScanNotStartingMitigationCompleted","RegValueType":"REG_DWORD","IfExists":true},"UtcDataHandlingPolicies":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Diagnostics\\DiagTrack","ValueName":"UtcDataHandlingPolicies","RegValueType":"REG_QWORD"},"UUSVersion":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\WindowsUpdate\\Orchestrator","ValueName":"LastRunVersion","RegValueType":"REG_SZ"},"WAS_NetFxEnvironment":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Component Based Servicing\\Notifications\\OptionalFeatures\\WAS-NetFxEnvironment","ValueName":"Selection","RegValueType":"REG_DWORD"},"WCFHTTPActivationNotificationState":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\\\Microsoft\\\\Windows\\\\CurrentVersion\\\\Component Based Servicing\\\\Notifications\\\\OptionalFeatures\\\\WCF-HTTP-Activation","ValueName":"Selection","RegValueType":"REG_DWORD"},"WCFNonHTTPActivationNotificationState":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\\\Microsoft\\\\Windows\\\\CurrentVersion\\\\Component Based Servicing\\\\Notifications\\\\OptionalFeatures\\\\WCF-NonHTTP-Activation","ValueName":"Selection","RegValueType":"REG_DWORD"},"WebExperience":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\EdgeUpdate\\Clients\\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}","IfExists":true},"WebExperienceWow":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\WOW6432Node\\Microsoft\\EdgeUpdate\\Clients\\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}","IfExists":true},"WebrootInstalledKey":{"FullPath":"SOFTWARE\\WRData","IfExists":true},"WebrootInstalledWowKey":{"FullPath":"SOFTWARE\\WOW6432Node\\WRData","IfExists":true},"Win11UpgradeAcceptedTimestamp":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\WindowsUpdate\\UX\\Settings","ValueName":"SvOfferAccepted","RegValueType":"REG_QWORD"},"Win11UpgradeAcceptedWUSeeker":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\WindowsUpdate\\UX\\Settings","ValueName":"SvOfferAccepted","RegValueType":"REG_QWORD","IfExists":true},"WindowsAccountSyncConsentApplicable":{"HKey":"HKEY_CURRENT_USER","FullPath":"Software\\Microsoft\\Windows\\CurrentVersion\\UnifiedConsent\\DEFAULTACCOUNT\\WINDOWSACCOUNTSYNCCONSENT","ValueName":"isApplicable","RegValueType":"REG_DWORD"},"WindowsAccountSyncConsentPromptAllowed":{"HKey":"HKEY_CURRENT_USER","FullPath":"Software\\Microsoft\\Windows\\CurrentVersion\\UnifiedConsent\\DEFAULTACCOUNT\\WINDOWSACCOUNTSYNCCONSENT","ValueName":"isSystemInitiatedPromptAllowed","RegValueType":"REG_DWORD"},"WindowsAccountSyncConsentState":{"HKey":"HKEY_CURRENT_USER","FullPath":"Software\\Microsoft\\Windows\\CurrentVersion\\UnifiedConsent\\DEFAULTACCOUNT\\WINDOWSACCOUNTSYNCCONSENT\\DATASHARING","ValueName":"isConsentAccepted","RegValueType":"REG_DWORD"},"WindowsMixedReality":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\WUDF\\Services\\HoloLensSensors","ValueName":"WdfMajorVersion","RegValueType":"REG_DWORD"},"WOSCEndpointsSupported":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Wosc\\Client\\Persistent","ValueName":"EndpointsSupported","RegValueType":"REG_SZ"},"WSX_Runtime":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\WSX\\WSXPacks\\CTAC","ValueName":"ExperienceExtensions","RegValueType":"REG_SZ"},"WSX_Windows_AccountControl":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\WSX\\WSXPacks\\CTAC","ValueName":"Windows.AccountControl","RegValueType":"REG_SZ"},"WSX_Windows_AppSample":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\WSX\\WSXPacks\\CTAC","ValueName":"Windows.AppSample","RegValueType":"REG_SZ"},"WSX_Windows_Settings_Account":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\WSX\\WSXPacks\\CTAC","ValueName":"Windows.Settings.Account","RegValueType":"REG_SZ"},"WSX_Windows_Shell_Start":{"HKey":"HKEY_LOCAL_MACHINE","FullPath":"SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\WSX\\WSXPacks\\CTAC","ValueName":"Windows.Shell.StartMenu","RegValueType":"REG_SZ"}},"UpdatePolicy":{"AdminOptedIntoRebootlessUpdates":{"PolicyEnum":59,"Enterprise":true},"AllowOptionalContent":{"PolicyEnum":58,"Enterprise":true},"BranchReadinessLevel":{"PolicyEnum":5,"Enterprise":true},"BranchReadinessLevelSource":{"PolicyEnum":5,"Enterprise":true,"UseSource":true},"DeferFeatureUpdatePeriodInDays":{"PolicyEnum":9,"Enterprise":true},"DeferQualityUpdatePeriodInDays":{"PolicyEnum":7,"Enterprise":true},"DisableDualScan":{"PolicyEnum":42,"Enterprise":true},"EnableWUfBUpgradeGates":{"PolicyEnum":51,"Enterprise":true},"TargetProductVersion":{"PolicyEnum":53,"Enterprise":true},"TargetReleaseVersion":{"PolicyEnum":50,"Enterprise":true},"UpdateServiceUrl":{"PolicyEnum":12},"WUfBClientManaged":{"PolicyEnum":32,"Enterprise":true}},"FileInfo":{"AvastVer":{"Path":"\\system32\\Drivers\\aswVmm.sys","FolderGuid":"{F38BF404-1D43-42F2-9305-67DE0B28FC23}"},"AvgVer":{"Path":"\\system32\\Drivers\\avgVmm.sys","FolderGuid":"{F38BF404-1D43-42F2-9305-67DE0B28FC23}"},"BullguardInstalledVer":{"Path":"\\BullGuard Ltd\\BullGuard\\BullGuard.exe","IfExists":true,"FolderGuid":"{905E63B6-C1BF-494E-B29C-65B732D3D21A}"},"CortanaAppVer":{"Path":"\\WindowsApps\\Microsoft.549981C3F5F10_8wekyb3d8bbwe\\CortanaApp.View.exe","FolderGuid":"{905E63B6-C1BF-494E-B29C-65B732D3D21A}"},"CortanaAppVerTest":{"Path":"\\WindowsApps\\3242f7d9-db60-4380-a379-4205ea768bfc_1.0.0.0_x64__zs4v8rx04ex0m\\UndockingTestApp.exe","FolderGuid":"{905E63B6-C1BF-494E-B29C-65B732D3D21A}"},"CrowdStrikeInstalledVer":{"Path":"drivers\\CrowdStrike\\CSAgent.sys","IfExists":true,"FolderGuid":"{1AC14E77-02E7-4E5D-B744-2EB1AE5198B7}"},"DmdHpControlPackageEnUs":{"Path":"%PROGRAMDATA%\\Microsoft\\Windows\\DeviceMetadataCache\\dmrccache\\en-US\\d3a162c7-a388-4099-b63d-265639514cc0\\PackageInfo.xml","IfExists":true},"DmdHpControlPackageMultiloc":{"Path":"%PROGRAMDATA%\\Microsoft\\Windows\\DeviceMetadataCache\\dmrccache\\multiloc\\d3a162c7-a388-4099-b63d-265639514cc0\\PackageInfo.xml","IfExists":true},"DmdHpControlPackageTr":{"Path":"%PROGRAMDATA%\\Microsoft\\Windows\\DeviceMetadataCache\\dmrccache\\tr\\d3a162c7-a388-4099-b63d-265639514cc0\\PackageInfo.xml","IfExists":true},"EsetVer":{"Path":"\\drivers\\ehdrv.sys","FolderGuid":"{1AC14E77-02E7-4E5D-B744-2EB1AE5198B7}"},"FileExistsMscoreeDll":{"Path":"%windir%\\\\system32\\\\mscoree.dll","IfExists":true},"GDataInstalledVer":{"Path":"\\drivers\\MiniIcpt.sys","IfExists":true,"FolderGuid":"{1AC14E77-02E7-4E5D-B744-2EB1AE5198B7}"},"HidparseDriversVer":{"Path":"%windir%\\system32\\drivers\\hidparse.sys"},"HidparseSystem32Ver":{"Path":"%windir%\\system32"},"HidparseSystem32Ver1":{"Path":"%windir%\\system32\\hidparse.sys"},"IsNotepadExePresent":{"Path":"%windir%\\system32\\notepad.exe","IfExists":true},"K7InstalledVer":{"Path":"\\K7 Computing","IfExists":true,"FolderGuid":"{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}"},"KasperskyVer":{"Path":"\\system32\\Drivers\\klhk.sys","FolderGuid":"{F38BF404-1D43-42F2-9305-67DE0B28FC23}"},"OnnxruntimeVer":{"Path":"%windir%\\\\system32\\\\onnxruntime.dll"},"PandaInstalledVer":{"Path":"\\Panda Security","IfExists":true,"FolderGuid":"{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}"},"SkypeRoomSystem":{"Path":"%systemdrive%\\Recovery\\OEM\\$oem$\\$1\\Rigel\\x64\\Scripts\\Provisioning\\AutoUnattend.xml","IfExists":true},"SymantecVer":{"Path":"\\Symantec\\Shared\\EENGINE\\eeCtrl.sys","FolderGuid":"{DE974D24-D9C6-4D3E-BF91-F4455120B917}"},"SymantecVer64":{"Path":"\\Symantec\\Shared\\EENGINE\\eeCtrl64.sys","FolderGuid":"{DE974D24-D9C6-4D3E-BF91-F4455120B917}"},"TobiiVer":{"Path":"\\Tobii\\Tobii EyeX Interaction\\Tobii.EyeX.Interaction.exe","FolderGuid":"{905E63B6-C1BF-494E-B29C-65B732D3D21A}"},"TobiiVer1x86":{"Path":"\\Tobii\\tobii EyeX Interaction\\Tobii.EyeX.Interaction.exe","FolderGuid":"{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}"},"TobiiVerx86":{"Path":"\\tobii EyeX Interaction\\Tobii.EyeX.Interaction.exe","FolderGuid":"{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}"},"TrendInstalledVer":{"Path":"\\Trend Micro\\Titanium\\plugin\\plugVizor.dll","IfExists":true,"FolderGuid":"{905E63B6-C1BF-494E-B29C-65B732D3D21A}"},"TrendMicroVer":{"Path":"\\drivers\\TMUMH.sys","FolderGuid":"{1AC14E77-02E7-4E5D-B744-2EB1AE5198B7}"},"WASDK_1_2_ARM":{"Path":"%programfiles%\\WindowsApps\\Microsoft.WindowsAppRuntime.1.6_6000.311.13.0_arm__8wekyb3d8bbwe\\WindowsAppRuntime.DeploymentExtensions.OneCore.dll","IfExists":true},"WASDK_1_2_ARM64":{"Path":"%programfiles%\\WindowsApps\\Microsoft.WindowsAppRuntime.1.6_6000.311.13.0_arm64__8wekyb3d8bbwe\\WindowsAppRuntime.DeploymentExtensions.OneCore.dll","IfExists":true},"WASDK_1_2_DLL":{"Path":"%programfiles%\\WindowsApps\\Microsoft.WindowsAppRuntime.1.6_6000.311.13.0_x64__8wekyb3d8bbwe\\WindowsAppRuntime.DeploymentExtensions.OneCore.dll","IfExists":true},"WASDK_1_2_X86":{"Path":"%programfiles%\\WindowsApps\\Microsoft.WindowsAppRuntime.1.6_6000.311.13.0_x86__8wekyb3d8bbwe\\WindowsAppRuntime.DeploymentExtensions.OneCore.dll","IfExists":true},"WuClientVer":{"Path":"\\system32\\wuaueng.dll","FolderGuid":"{F38BF404-1D43-42F2-9305-67DE0B28FC23}"},"XamlCbsActivationStore":{"Path":"%ProgramData%\\\\Microsoft\\\\Windows\\\\AppRepository\\\\Packages\\\\Microsoft.UI.Xaml.CBS_8.2205.4001.0_x64__8wekyb3d8bbwe\\\\ActivationStore.dat","IfExists":true},"XamlCbsActivationStoreArm64":{"Path":"%ProgramData%\\\\Microsoft\\\\Windows\\\\AppRepository\\\\Packages\\\\Microsoft.UI.Xaml.CBS_8.2205.4001.0_arm64__8wekyb3d8bbwe\\\\ActivationStore.dat","IfExists":true}},"Licensing":{"UpdateManagementGroup":{"Name":"UpdatePolicy-UpdateManagementGroup"}},"Policy":{"DesiredOcpVersion":{"LocUri":"./Device/Vendor/MSFT/DeviceUpdateCenter/DesiredUpdates/OcpVersion/"},"DesiredOsVersion":{"LocUri":"./Device/Vendor/MSFT/DeviceUpdateCenter/DesiredUpdates/OsVersion"},"DesiredSystemManifestVersion":{"LocUri":"./Device/Vendor/MSFT/DeviceUpdateCenter/DesiredUpdates/SystemManifestVersion"},"DucCustomPackageId":{"LocUri":"./Device/Vendor/MSFT/DeviceUpdateCenter/Enrollment/CustomPackageId"},"DucDeviceModelId":{"LocUri":"./Device/Vendor/MSFT/DeviceUpdateCenter/Enrollment/DeviceModelId"},"DucOemPartnerRing":{"LocUri":"./Device/Vendor/MSFT/DeviceUpdateCenter/Enrollment/OemPartnerRing"},"DucPublisherId":{"LocUri":"./Device/Vendor/MSFT/DeviceUpdateCenter/Enrollment/PublisherId"},"SetPolicyDrivenUpdateSourceForFeatureUpdates":{"LocUri":"./Device/Vendor/MSFT/Policy/Config/Update/SetPolicyDrivenUpdateSourceForFeatureUpdates"},"WSUSconfigured_csp":{"LocUri":"./Device/Vendor/MSFT/Policy/Config/Update/UpdateServiceUrl"}},"AppInfo":{"AIFabricCBSStableVer":{"Name":"Microsoft.WindowsAppRuntime.CBS.1.6"},"WidgetsAppVer":{"Name":"MicrosoftWindows.Client.WebExperience"}},"WMI":{"ElanFingerprintDriverVersion":{"Query":"SELECT DriverVersion, Manufacturer FROM Win32_PnPSignedDriver WHERE Manufacturer = 'ELAN'","Name":"DriverVersion","Timeout":2000},"FirstStorageSpaceDeviceId":{"Query":"SELECT DeviceID FROM Win32_DiskDrive WHERE Model = 'Microsoft Storage Space Device'","Name":"DeviceID","Timeout":2000},"IIS_ASPNET_WMI":{"Query":"SELECT * FROM Win32_OptionalFeature WHERE name = 'IIS-ASPNET'","Name":"InstallState","Timeout":2000},"IIS_NetFxExtensibility_WMI":{"Query":"SELECT * FROM Win32_OptionalFeature WHERE name = 'IIS-NetFxExtensibility'","Name":"InstallState","Timeout":2000},"NetFx3State":{"Query":"SELECT * FROM Win32_OptionalFeature WHERE name = 'NetFX3'","Name":"InstallState","Timeout":2000},"PSAKyoceraInstalledName":{"Query":"SELECT Name, ProgramId FROM Win32_InstalledStoreProgram WHERE ProgramId = 'A97ECD55.KYOCERAPrintCenter_4.1.11108.0_x64__kqmhh0ktdt7dg'","Name":"Name","Timeout":2000},"PSATATriumphInstalledName":{"Query":"SELECT Name, ProgramId FROM Win32_InstalledStoreProgram WHERE ProgramId = 'TATriumph-AdlerGmbH.TAUTAXPrintCenter_4.1.11108.0_x64__h5e8vsnevp54y'","Name":"Name","Timeout":2000},"WAS_NetFxEnvironment_WMI":{"Query":"SELECT * FROM Win32_OptionalFeature WHERE name = 'WAS-NetFxEnvironment'","Name":"InstallState","Timeout":2000},"WCFHTTPActivationState":{"Query":"SELECT * FROM Win32_OptionalFeature WHERE name = 'WCF-HTTP-Activation'","Name":"InstallState","Timeout":2000},"WCFNonHTTPActivationState":{"Query":"SELECT * FROM Win32_OptionalFeature WHERE name = 'WCF-NonHTTP-Activation'","Name":"InstallState","Timeout":2000},"XeroxPsaInstalledName":{"Query":"SELECT Name, ProgramId FROM Win32_InstalledStoreProgram WHERE ProgramId = 'XeroxCorp.PrintExperience_8.29.32.0_x64__f7egpvdyrs2a8'","Name":"Name","Timeout":2000}},"RegionPolicy":{"IsCampaignEdgePromotionEnabled":{"ForceEvaluate":false,"PolicyGUID":"{2BF706DE-6DBB-4692-B7EF-84D80C47E927}"},"IsCampaignSegmentTargetingEnabled":{"ForceEvaluate":false,"PolicyGUID":"{36996754-E327-483A-902F-523E2BA03239}"}}} | |||
| (PID) Process: | (4712) MoUsoCoreWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsSelfHost\OneSettings |
| Operation: | write | Name: | FlightSettingsServiceUrl |
Value: https://insideruser.microsoft.com/api/FlightSettings | |||
| (PID) Process: | (4712) MoUsoCoreWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsSelfHost\OneSettings |
| Operation: | write | Name: | HonorUTCRestrictions |
Value: 0 | |||
| (PID) Process: | (4712) MoUsoCoreWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsSelfHost\OneSettings |
| Operation: | write | Name: | SyncWNSUri |
Value: 0 | |||
| (PID) Process: | (4712) MoUsoCoreWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsSelfHost\OneSettings |
| Operation: | write | Name: | IsBuildUnsupported |
Value: 0 | |||
| (PID) Process: | (4712) MoUsoCoreWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsSelfHost\OneSettings |
| Operation: | write | Name: | FlightSettingsVersion |
Value: 2 | |||
| (PID) Process: | (4712) MoUsoCoreWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsSelfHost\OneSettings |
| Operation: | write | Name: | UTCApprovedProperties |
Value: deviceType;osUILocale;currentTelemetryLevelInt;defaultDynamicRegistryReads;propertyIgnoreList;testFlags;rs2CapabilitiesPresent;rs3CapabilitiesPresent | |||
| (PID) Process: | (4712) MoUsoCoreWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsSelfHost\OneSettings |
| Operation: | write | Name: | MaxCallsPerDay |
Value: 500 | |||
Executable files
535
Suspicious files
1 197
Text files
345
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1276 | svchost.exe | C:\Windows\System32\Tasks\Microsoft\Windows\UpdateOrchestrator\Schedule Wake To Work | xml | |
MD5:C6086D02F8CE044F5FA07A98303DC7EB | SHA256:8901D9C9AEA465DA4EA7AA874610A90B8CF0A71EBA0E321CF9675FCEEE0B54A0 | |||
| 1276 | svchost.exe | C:\Windows\System32\Tasks\Microsoft\Windows\UpdateOrchestrator\Schedule Work | xml | |
MD5:5FADF13CCFBDCC5DD728380F7A615B28 | SHA256:FF1F73395F6B5B22D5FDA367521FE0DCC31FF252849B7FA85FA346B953A40451 | |||
| 1276 | svchost.exe | C:\Windows\System32\Tasks\Microsoft\Windows\UpdateOrchestrator\Schedule Scan | xml | |
MD5:11954764DE4745B35A42219A7C5E2DCA | SHA256:997FCF971A38394C30D9E5CA0C6B36E782630E83B52D2664C56F1DEFBA54CB6C | |||
| 1768 | svchost.exe | C:\Windows\Prefetch\SVCHOST.EXE-D1174AA4.pf | binary | |
MD5:3FECF660C143EE63BAAFF08AD029F31E | SHA256:096D12B2235B9C95B8C633AA8CF450469F0FCEE932E97A9CD8A274353653D758 | |||
| 1768 | svchost.exe | C:\Windows\Prefetch\UPFC.EXE-BDDF79D6.pf | binary | |
MD5:22BE1B766FA33154B0FA3DD4CB83AAE1 | SHA256:071FF539791E12C77B99BBAF6236A6AEAF625EDAD4FD525437966E160BCD639F | |||
| 760 | lsass.exe | C:\Windows\System32\Microsoft\Protect\S-1-5-18\User\e16931e4-9d2e-4d8e-b087-4d6c884a94a5 | binary | |
MD5:1D6B196C37F95C3DC130328D87D4357A | SHA256:7082244E11DD3AF9FA8912CDC744D2F466B9BE8F630B3D0E741987F991315F84 | |||
| 1768 | svchost.exe | C:\Windows\Prefetch\TASKHOSTW.EXE-3E0B74C8.pf | binary | |
MD5:4D53B6D43B871665BF9BEF17B37CA73B | SHA256:11CB06DFEBD0C3B89539AFF8605A7C1C73AAE5DD27DC8A801FD432ACACE7C58A | |||
| 5164 | dllhost.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WebCache\V01.chk | binary | |
MD5:9628937F1D0F7449C2BB18557D32ABBC | SHA256:B4F5910E457A3718E24C74BC67529F799CE881225673F938E9462A76F90C40C3 | |||
| 1768 | svchost.exe | C:\Windows\Prefetch\HOST.EXE-F5D74C61.pf | binary | |
MD5:ADF8A029AE93A7591F1C30E22763F3A5 | SHA256:8EECCCE3BE5A207EC5A3E07084B357596B3447FC6E7833D0CF84E50567FDE736 | |||
| 1980 | svchost.exe | C:\Windows\ServiceProfiles\LocalService\AppData\Local\FontCache\~FontCache-S-1-5-18.dat | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
358
TCP/UDP connections
6 517
DNS requests
436
Threats
1 851
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2324 | svchost.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2324 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6392 | ._cache_4363463463464363463463463.exe | GET | 200 | 113.31.111.76:80 | http://113.31.111.76/1.exe | unknown | — | — | malicious |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3560 | SIHClient.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6596 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6392 | ._cache_4363463463464363463463463.exe | GET | 200 | 185.215.113.16:80 | http://185.215.113.16/inc/lummetc.exe | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3040 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
2324 | svchost.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
5064 | SearchApp.exe | 2.23.227.221:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
2324 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5064 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6392 | ._cache_4363463463464363463463463.exe | A Network Trojan was detected | ET MALWARE Single char EXE direct download likely trojan (multiple families) |
6392 | ._cache_4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6392 | ._cache_4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
6392 | ._cache_4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
6392 | ._cache_4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
6392 | ._cache_4363463463464363463463463.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 31 |
6392 | ._cache_4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6392 | ._cache_4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
6392 | ._cache_4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
6392 | ._cache_4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
Process | Message |
|---|---|
._cache_4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
cfc53e19dd.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
._cache_4363463463464363463463463.exe | Unable to connect to the remote server
|
bb20675cd6.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
3e3ev3.exe | CLR: Managed code called FailFast without specifying a reason.
|
9580ad453f.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
6246a44bcb.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
CritScript.exe | C:\Users\admin\AppData\Local\Temp\JUSCHED.EXE |
CritScript.exe | C:\Users\admin\AppData\Local\Temp\ZOMBIES.AHK |
34647a8c61.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|