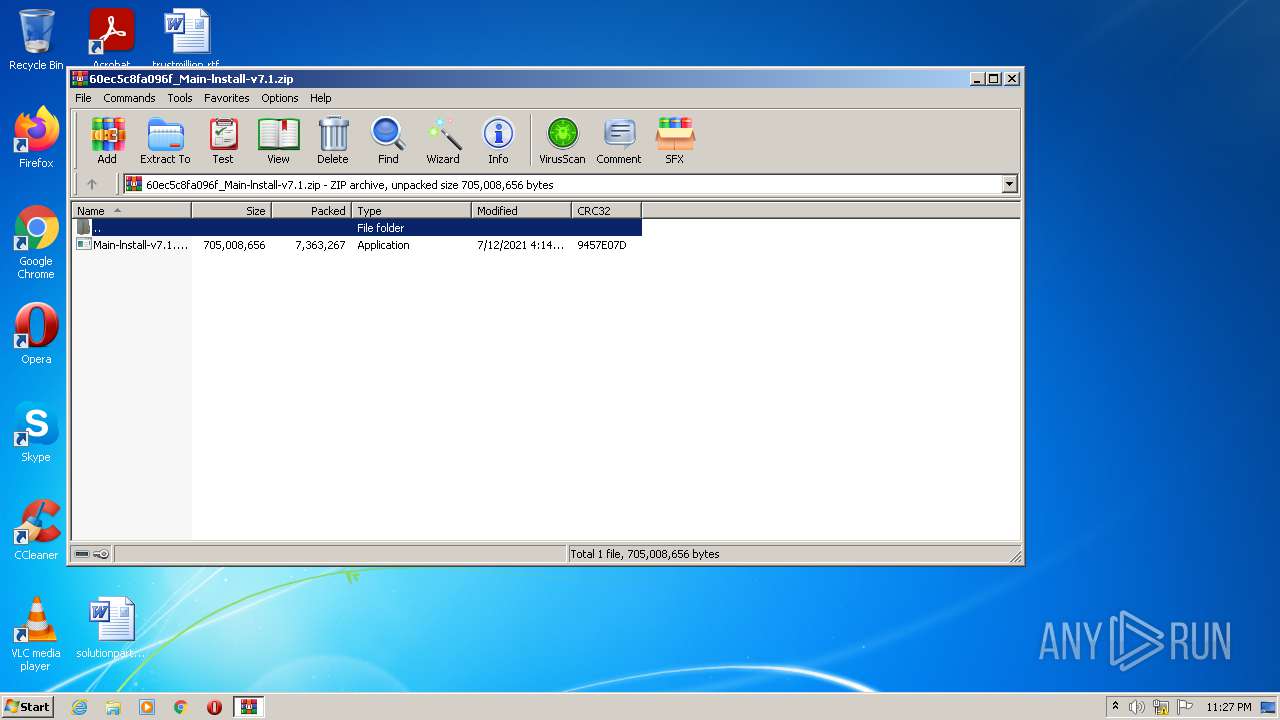
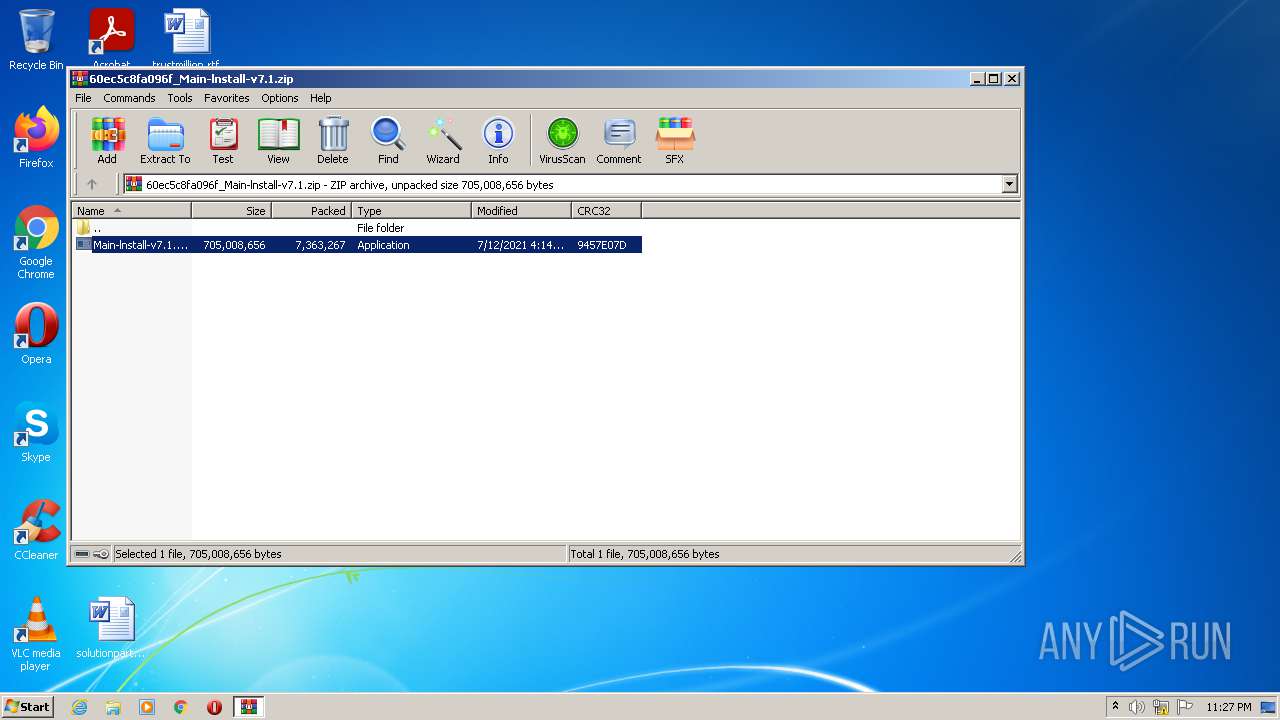
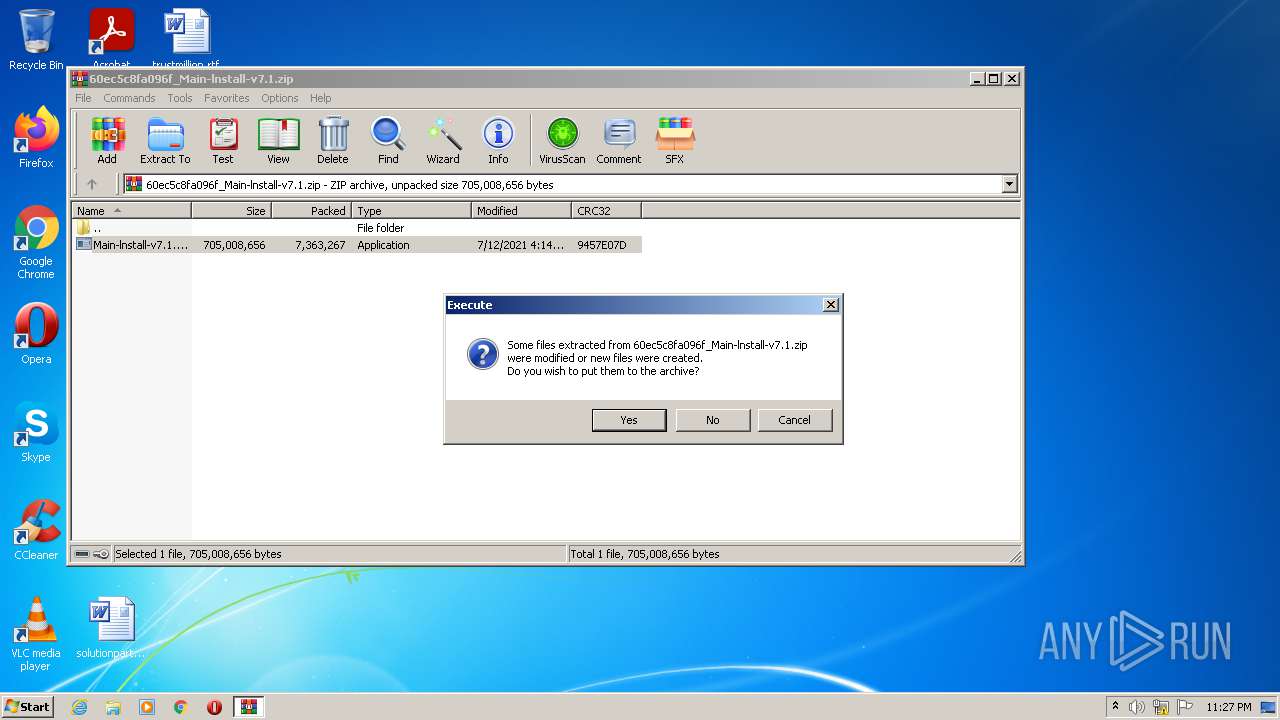
| File name: | 60ec5c8fa096f_Main-lnstall-v7.1.zip |
| Full analysis: | https://app.any.run/tasks/abd17d39-adbe-4d16-b1ce-d58dfc3fe5ba |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | July 13, 2021, 22:26:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 4866A761DDF36B47EBCDAF2094D1F1C5 |
| SHA1: | 24D44E12FAAA781FEF93824C8BF752C532421BCA |
| SHA256: | FD94ADD9F55D6CE4BCF4428A4EA78C6A311D5EF26CF63E98BF39D4CDD4A573A1 |
| SSDEEP: | 196608:Iqkr3+qZVbbFpd+eTrnKXaIX5cDjZmrZN2lmK7I:Iqk3TzFue35o5cDGZNm7I |
MALICIOUS
Actions looks like stealing of personal data
- Main-lnstall-v7.1.exe (PID: 3228)
- Setup.exe (PID: 840)
- svchost.exe (PID: 5604)
- Tritiation.exe (PID: 5276)
- NANbrowser.exe (PID: 4248)
- w_Xrc6UqsJdXOyGPQsMWdR0b.exe (PID: 4040)
- 8pthOztIBVLYt6kFLMuKjjvo.exe (PID: 5384)
- Updater.exe (PID: 5684)
- Newouttab02.exe (PID: 2192)
- ZA_Q3L8vS0E4GccBjGfJVJLe.exe (PID: 4496)
- 3QHjZx8dt0t26AfH9CRQRJBm.exe (PID: 5640)
- 5RrDYWMxQIYVWAyYwWHPHLBn.exe (PID: 2536)
- oXzrQf21IDNLKfJlC5lhX4Jv.exe (PID: 4164)
- Tu_oVga04bBd7yyUotWPAALW.exe (PID: 5040)
- 10680835434.exe (PID: 8252)
- HpF8gAIYSEJ1ugDsKShf2kv1.exe (PID: 3784)
- F30KJxMk0hUsZoEPkpTkTDh_.exe (PID: 3680)
- mGFTWeXoYYdP5IqOlAWoOOLT.exe (PID: 5924)
- X8BrG24DU0bF6vlhsqhngg76.exe (PID: 2612)
Executes PowerShell scripts
- cmd.exe (PID: 3140)
- cmd.exe (PID: 2676)
- cmd.exe (PID: 2288)
- cmd.exe (PID: 3520)
- cmd.exe (PID: 2116)
- cmd.exe (PID: 3892)
- cmd.exe (PID: 3564)
- cmd.exe (PID: 3048)
- cmd.exe (PID: 2640)
- cmd.exe (PID: 3624)
- cmd.exe (PID: 2080)
- cmd.exe (PID: 3524)
- cmd.exe (PID: 424)
- cmd.exe (PID: 1772)
Application was dropped or rewritten from another process
- appsetup.exe (PID: 2060)
- appsetup.exe (PID: 2980)
- IDWCH2.exe (PID: 2408)
- LabPicV2.exe (PID: 3068)
- NANbrowser.exe (PID: 3100)
- SMCh1.exe (PID: 3912)
- gogonami.exe (PID: 3588)
- 7eae3352.exe (PID: 3848)
- BrowzarBrowser_j6.exe (PID: 1992)
- md3_3kvm.exe (PID: 2304)
- Pupdate.exe (PID: 324)
- Xteat12.exe (PID: 3568)
- vguuu.exe (PID: 2352)
- umbr.exe (PID: 2540)
- app.exe (PID: 3736)
- Newouttab02.exe (PID: 2192)
- askinstall50.exe (PID: 3208)
- sfx_123_701.exe (PID: 2396)
- gogonami.exe (PID: 5756)
- NANbrowser.exe (PID: 4248)
- mAp.exe (PID: 3796)
- Browzar.exe (PID: 1272)
- Tritiation.exe (PID: 5276)
- jfiag3g_gg.exe (PID: 2112)
- Tritiation.exe (PID: 360)
- run.exe (PID: 2388)
- aE_nK7vZOFYhFlDLqUQshFxg.exe (PID: 4376)
- 8pthOztIBVLYt6kFLMuKjjvo.exe (PID: 5384)
- jfiag3g_gg.exe (PID: 808)
- 8pthOztIBVLYt6kFLMuKjjvo.exe (PID: 4616)
- w_Xrc6UqsJdXOyGPQsMWdR0b.exe (PID: 4040)
- RG5CP0uxCTKWsDmpT9Ht1oCN.exe (PID: 4808)
- aE_nK7vZOFYhFlDLqUQshFxg.exe (PID: 4560)
- oXzrQf21IDNLKfJlC5lhX4Jv.exe (PID: 4020)
- oXzrQf21IDNLKfJlC5lhX4Jv.exe (PID: 4164)
- SystemMonitor.exe (PID: 5416)
- 3QHjZx8dt0t26AfH9CRQRJBm.exe (PID: 5640)
- Fepolicaeta.exe (PID: 2460)
- prolab.exe (PID: 5856)
- Ma07pX6h4JcViSzSUhgFN8RZ.exe (PID: 1260)
- SAtbVCDzYYWFTBTA_Oea8a1N.exe (PID: 6028)
- SAtbVCDzYYWFTBTA_Oea8a1N.exe (PID: 5412)
- IDownload.exe (PID: 5060)
- Jisyraeloru.exe (PID: 3688)
- Ficocefyqa.exe (PID: 1280)
- wXBwx1IVBV0oj3c7ksEBCECJ.exe (PID: 4836)
- ZA_Q3L8vS0E4GccBjGfJVJLe.exe (PID: 4496)
- Vecamelyky.exe (PID: 3380)
- Gylaevoluta.exe (PID: 2608)
- F30KJxMk0hUsZoEPkpTkTDh_.exe (PID: 3680)
- Mekymutavi.exe (PID: 544)
- dkkoyQhUoZBWUs4Rp_cJIa5o.exe (PID: 5924)
- run.exe (PID: 4488)
- run.exe (PID: 1136)
- run.exe (PID: 3544)
- run.exe (PID: 1892)
- run.exe (PID: 4996)
- run.exe (PID: 3344)
- run.exe (PID: 1804)
- run.exe (PID: 3968)
- run.exe (PID: 5168)
- run.exe (PID: 4988)
- run.exe (PID: 2568)
- run.exe (PID: 5692)
- run.exe (PID: 3152)
- run.exe (PID: 1088)
- run.exe (PID: 5600)
- run.exe (PID: 4200)
- 5RrDYWMxQIYVWAyYwWHPHLBn.exe (PID: 2536)
- X8BrG24DU0bF6vlhsqhngg76.exe (PID: 2612)
- run.exe (PID: 5208)
- run.exe (PID: 1596)
- Tu_oVga04bBd7yyUotWPAALW.exe (PID: 5040)
- run.exe (PID: 5112)
- run.exe (PID: 5864)
- run.exe (PID: 1544)
- run.exe (PID: 3428)
- run.exe (PID: 5104)
- run.exe (PID: 424)
- run.exe (PID: 3288)
- x9yRVY4KGRfHuTqOEPAuH4XU.exe (PID: 4196)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 3524)
- HpF8gAIYSEJ1ugDsKShf2kv1.exe (PID: 3784)
- run.exe (PID: 4880)
- run.exe (PID: 1032)
- run.exe (PID: 364)
- run.exe (PID: 1104)
- run.exe (PID: 4032)
- run.exe (PID: 3676)
- run.exe (PID: 4780)
- mGFTWeXoYYdP5IqOlAWoOOLT.exe (PID: 5644)
- mGFTWeXoYYdP5IqOlAWoOOLT.exe (PID: 5924)
- run.exe (PID: 5960)
- run.exe (PID: 5120)
- run.exe (PID: 2056)
- run.exe (PID: 4428)
- run.exe (PID: 5288)
- run.exe (PID: 5136)
- run.exe (PID: 4260)
- run.exe (PID: 4960)
- run.exe (PID: 3596)
- run.exe (PID: 4304)
- run.exe (PID: 4528)
- run.exe (PID: 1332)
- run.exe (PID: 2452)
- run.exe (PID: 4608)
- run.exe (PID: 5972)
- run.exe (PID: 3348)
- run.exe (PID: 3140)
- run.exe (PID: 4588)
- run.exe (PID: 2240)
- run.exe (PID: 4072)
- run.exe (PID: 1144)
- run.exe (PID: 4672)
- run.exe (PID: 648)
- run.exe (PID: 4420)
- run.exe (PID: 4192)
- run.exe (PID: 5944)
- jfiag3g_gg.exe (PID: 5444)
- run.exe (PID: 4820)
- run.exe (PID: 1364)
- run.exe (PID: 5736)
- run.exe (PID: 4252)
- run.exe (PID: 580)
- run.exe (PID: 5468)
- run.exe (PID: 4300)
- run.exe (PID: 2524)
- run.exe (PID: 868)
- run.exe (PID: 5852)
- run.exe (PID: 504)
- run.exe (PID: 3820)
- run.exe (PID: 1240)
- run.exe (PID: 5064)
- run.exe (PID: 5444)
- run.exe (PID: 4532)
- run.exe (PID: 3876)
- run.exe (PID: 4748)
- run.exe (PID: 2408)
- run.exe (PID: 4824)
- run.exe (PID: 4316)
- run.exe (PID: 2696)
- run.exe (PID: 472)
- run.exe (PID: 2236)
- run.exe (PID: 584)
- run.exe (PID: 2764)
- run.exe (PID: 6468)
- run.exe (PID: 6320)
- run.exe (PID: 6368)
- run.exe (PID: 6348)
- run.exe (PID: 3056)
- run.exe (PID: 6300)
- run.exe (PID: 6508)
- run.exe (PID: 6536)
- run.exe (PID: 6580)
- run.exe (PID: 6608)
- run.exe (PID: 6652)
- run.exe (PID: 6840)
- run.exe (PID: 6768)
- run.exe (PID: 6976)
- run.exe (PID: 6864)
- run.exe (PID: 6552)
- run.exe (PID: 7528)
- run.exe (PID: 7316)
- run.exe (PID: 7632)
- run.exe (PID: 7792)
- run.exe (PID: 7832)
- run.exe (PID: 7900)
- run.exe (PID: 7960)
- run.exe (PID: 8012)
- run.exe (PID: 4312)
- run.exe (PID: 6264)
- run.exe (PID: 6492)
- run.exe (PID: 6576)
- run.exe (PID: 6912)
- run.exe (PID: 7244)
- run.exe (PID: 7144)
- run.exe (PID: 7376)
- run.exe (PID: 7252)
- run.exe (PID: 7444)
- md6_6ydj.exe (PID: 6604)
- run.exe (PID: 7308)
- run.exe (PID: 7616)
- run.exe (PID: 7948)
- run.exe (PID: 6428)
- run.exe (PID: 6516)
- ufgaa.exe (PID: 6444)
- run.exe (PID: 6896)
- run.exe (PID: 6292)
- run.exe (PID: 6560)
- cc0qFqDkZv04whX9rGENHSJM.exe (PID: 4632)
- run.exe (PID: 7196)
- run.exe (PID: 5644)
- run.exe (PID: 7360)
- run.exe (PID: 6952)
- run.exe (PID: 7080)
- run.exe (PID: 7652)
- run.exe (PID: 7800)
- run.exe (PID: 7860)
- run.exe (PID: 7780)
- run.exe (PID: 5272)
- jfiag3g_gg.exe (PID: 7944)
- run.exe (PID: 6504)
- run.exe (PID: 6564)
- run.exe (PID: 6956)
- run.exe (PID: 7396)
- run.exe (PID: 7464)
- run.exe (PID: 7048)
- run.exe (PID: 7500)
- run.exe (PID: 7844)
- run.exe (PID: 2972)
- run.exe (PID: 7980)
- run.exe (PID: 6220)
- run.exe (PID: 8136)
- run.exe (PID: 6248)
- run.exe (PID: 6176)
- run.exe (PID: 6452)
- run.exe (PID: 7868)
- run.exe (PID: 4628)
- run.exe (PID: 6784)
- run.exe (PID: 6876)
- run.exe (PID: 6664)
- jfiag3g_gg.exe (PID: 6544)
- run.exe (PID: 7224)
- run.exe (PID: 7420)
- run.exe (PID: 6800)
- run.exe (PID: 7184)
- run.exe (PID: 6252)
- run.exe (PID: 6736)
- run.exe (PID: 6648)
- 16854848995.exe (PID: 7280)
- ufgaa.exe (PID: 7296)
- run.exe (PID: 3316)
- run.exe (PID: 3976)
- run.exe (PID: 6364)
- run.exe (PID: 7032)
- run.exe (PID: 7660)
- run.exe (PID: 7944)
- run.exe (PID: 5268)
- run.exe (PID: 7992)
- run.exe (PID: 6832)
- run.exe (PID: 8160)
- run.exe (PID: 7712)
- run.exe (PID: 5440)
- run.exe (PID: 7124)
- run.exe (PID: 3872)
- run.exe (PID: 2496)
- run.exe (PID: 5568)
- run.exe (PID: 7744)
- run.exe (PID: 5412)
- run.exe (PID: 6708)
- run.exe (PID: 6688)
- run.exe (PID: 2116)
- run.exe (PID: 6148)
- run.exe (PID: 7276)
- run.exe (PID: 336)
- run.exe (PID: 6732)
- run.exe (PID: 6080)
- run.exe (PID: 5196)
- run.exe (PID: 4688)
- google-game.exe (PID: 7784)
- run.exe (PID: 6436)
- run.exe (PID: 2004)
- run.exe (PID: 6828)
- run.exe (PID: 7012)
- run.exe (PID: 1452)
- run.exe (PID: 5868)
- run.exe (PID: 7596)
- run.exe (PID: 8048)
- run.exe (PID: 1368)
- run.exe (PID: 1020)
- run.exe (PID: 7704)
- run.exe (PID: 7840)
- run.exe (PID: 7384)
- run.exe (PID: 5980)
- run.exe (PID: 2032)
- run.exe (PID: 6208)
- run.exe (PID: 6312)
- run.exe (PID: 1192)
- run.exe (PID: 7772)
- google-game.exe (PID: 3228)
- run.exe (PID: 7424)
- run.exe (PID: 6392)
- run.exe (PID: 7232)
- run.exe (PID: 6192)
- run.exe (PID: 6684)
- run.exe (PID: 3536)
- p3-signed.exe (PID: 5128)
- run.exe (PID: 7096)
- run.exe (PID: 6848)
- run.exe (PID: 6960)
- run.exe (PID: 7684)
- run.exe (PID: 7488)
- run.exe (PID: 1496)
- run.exe (PID: 6948)
- run.exe (PID: 8152)
- run.exe (PID: 4132)
- run.exe (PID: 7264)
- run.exe (PID: 6928)
- run.exe (PID: 4920)
- run.exe (PID: 7452)
- run.exe (PID: 7076)
- run.exe (PID: 8124)
- run.exe (PID: 7524)
- run.exe (PID: 7352)
- run.exe (PID: 6592)
- run.exe (PID: 3704)
- run.exe (PID: 1412)
- run.exe (PID: 4876)
- run.exe (PID: 6340)
- run.exe (PID: 6924)
- run.exe (PID: 6680)
- run.exe (PID: 8104)
- run.exe (PID: 5688)
- run.exe (PID: 4356)
- run.exe (PID: 6812)
- run.exe (PID: 7736)
- run.exe (PID: 6184)
- run.exe (PID: 7300)
- run.exe (PID: 1040)
- run.exe (PID: 8164)
- run.exe (PID: 4016)
- run.exe (PID: 2448)
- run.exe (PID: 7112)
- run.exe (PID: 8020)
- run.exe (PID: 6216)
- run.exe (PID: 8216)
- run.exe (PID: 8244)
- run.exe (PID: 8272)
- run.exe (PID: 8340)
- run.exe (PID: 8364)
- jfiag3g_gg.exe (PID: 8444)
- run.exe (PID: 8800)
- run.exe (PID: 8884)
- run.exe (PID: 8896)
- run.exe (PID: 9044)
- run.exe (PID: 9112)
- run.exe (PID: 9152)
- run.exe (PID: 9184)
- run.exe (PID: 9324)
- run.exe (PID: 9388)
- run.exe (PID: 9524)
- run.exe (PID: 9368)
- google-game.exe (PID: 8484)
- run.exe (PID: 9052)
- run.exe (PID: 9080)
- run.exe (PID: 8920)
- run.exe (PID: 9272)
- run.exe (PID: 9344)
- run.exe (PID: 8992)
- run.exe (PID: 8444)
- run.exe (PID: 9436)
- run.exe (PID: 9552)
- run.exe (PID: 9672)
- run.exe (PID: 9720)
- run.exe (PID: 9880)
- run.exe (PID: 9828)
- google-game.exe (PID: 9424)
- run.exe (PID: 9412)
- run.exe (PID: 9964)
- run.exe (PID: 10232)
- run.exe (PID: 1676)
- run.exe (PID: 4424)
- run.exe (PID: 9848)
- run.exe (PID: 8408)
- run.exe (PID: 8648)
- run.exe (PID: 8672)
- run.exe (PID: 9488)
- run.exe (PID: 5252)
- run.exe (PID: 8872)
- run.exe (PID: 8616)
- run.exe (PID: 8948)
- run.exe (PID: 9300)
- run.exe (PID: 9624)
- run.exe (PID: 9584)
- run.exe (PID: 9744)
- run.exe (PID: 9804)
- run.exe (PID: 9124)
- run.exe (PID: 10028)
- run.exe (PID: 9960)
- run.exe (PID: 3060)
- run.exe (PID: 4692)
- run.exe (PID: 7448)
- run.exe (PID: 4376)
- run.exe (PID: 8312)
- run.exe (PID: 4460)
- run.exe (PID: 8460)
- run.exe (PID: 8552)
- run.exe (PID: 8740)
- run.exe (PID: 8848)
- run.exe (PID: 4364)
- run.exe (PID: 9712)
- run.exe (PID: 8596)
- run.exe (PID: 9196)
- run.exe (PID: 8936)
- run.exe (PID: 8492)
- run.exe (PID: 8608)
- run.exe (PID: 9548)
- run.exe (PID: 8788)
- run.exe (PID: 9360)
- run.exe (PID: 9588)
- run.exe (PID: 9688)
- run.exe (PID: 9656)
- run.exe (PID: 9856)
- run.exe (PID: 10020)
- run.exe (PID: 9692)
- run.exe (PID: 10192)
- run.exe (PID: 9904)
- run.exe (PID: 6632)
- run.exe (PID: 10120)
- run.exe (PID: 964)
- run.exe (PID: 1900)
- run.exe (PID: 7748)
- run.exe (PID: 7536)
- run.exe (PID: 8600)
- run.exe (PID: 10208)
- run.exe (PID: 8228)
- run.exe (PID: 7492)
- run.exe (PID: 8516)
- run.exe (PID: 8584)
- run.exe (PID: 8684)
- run.exe (PID: 9736)
- run.exe (PID: 8480)
- run.exe (PID: 10104)
- run.exe (PID: 316)
- run.exe (PID: 2948)
- run.exe (PID: 9316)
- run.exe (PID: 9792)
- run.exe (PID: 9148)
- run.exe (PID: 10196)
- 10680835434.exe (PID: 8252)
- run.exe (PID: 8668)
- run.exe (PID: 9000)
- toolspab1.exe (PID: 8764)
- jfiag3g_gg.exe (PID: 9236)
- jfiag3g_gg.exe (PID: 8856)
- run.exe (PID: 7728)
- run.exe (PID: 10168)
- run.exe (PID: 5664)
- run.exe (PID: 9308)
- run.exe (PID: 7544)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9568)
- fa041e8b.exe (PID: 8700)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8916)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9452)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9596)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9800)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10024)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9796)
- toolspab1.exe (PID: 10140)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9812)
- ufgaa.exe (PID: 6756)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 7720)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8784)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8756)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8820)
- run.exe (PID: 9312)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9428)
- run.exe (PID: 8332)
- run.exe (PID: 10128)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9064)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9840)
- run.exe (PID: 8960)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9192)
- run.exe (PID: 9708)
- run.exe (PID: 9864)
- run.exe (PID: 8468)
- run.exe (PID: 10164)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 3340)
- run.exe (PID: 9664)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 7156)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9012)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 3920)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 7220)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9376)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9356)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9868)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8976)
- run.exe (PID: 8376)
- run.exe (PID: 280)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9352)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8892)
- run.exe (PID: 9248)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9068)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8448)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8764)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10184)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9244)
- run.exe (PID: 10148)
- run.exe (PID: 10152)
- run.exe (PID: 9888)
- run.exe (PID: 9768)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9516)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9836)
- run.exe (PID: 10052)
- run.exe (PID: 9872)
- run.exe (PID: 9820)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9204)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 5388)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 6336)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9576)
- run.exe (PID: 8404)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8140)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8844)
- run.exe (PID: 9924)
- run.exe (PID: 8400)
- run.exe (PID: 9464)
- run.exe (PID: 6168)
- run.exe (PID: 8260)
- run.exe (PID: 5356)
- run.exe (PID: 9172)
- run.exe (PID: 9896)
- run.exe (PID: 10112)
- run.exe (PID: 8476)
- run.exe (PID: 9140)
- run.exe (PID: 8196)
- run.exe (PID: 6432)
- jfiag3g_gg.exe (PID: 9784)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10580)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10620)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10600)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10644)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10712)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10216)
- 50921261244.exe (PID: 10804)
- run.exe (PID: 10852)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10728)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11300)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11500)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11288)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11336)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11316)
- run.exe (PID: 11020)
- run.exe (PID: 10884)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10900)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11000)
- run.exe (PID: 10968)
- run.exe (PID: 10864)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11708)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11808)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11844)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11828)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11856)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11924)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11956)
- toolspab1.exe (PID: 11984)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12020)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12116)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12104)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12136)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12156)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12248)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12208)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12192)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11880)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12044)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10404)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10532)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 6228)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9108)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10608)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9120)
- run.exe (PID: 10684)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10420)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10664)
- run.exe (PID: 10616)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10756)
- run.exe (PID: 7784)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10768)
- run.exe (PID: 10780)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12268)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9952)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 7972)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10552)
- run.exe (PID: 11604)
- run.exe (PID: 10944)
- run.exe (PID: 11572)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11072)
- run.exe (PID: 10508)
- run.exe (PID: 11484)
- run.exe (PID: 9280)
- run.exe (PID: 11740)
- run.exe (PID: 11780)
- run.exe (PID: 11992)
- run.exe (PID: 11836)
- run.exe (PID: 12008)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10908)
- run.exe (PID: 10820)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10848)
- run.exe (PID: 12172)
- run.exe (PID: 10632)
- run.exe (PID: 10252)
- run.exe (PID: 10436)
- run.exe (PID: 10312)
- run.exe (PID: 10376)
- run.exe (PID: 10464)
- run.exe (PID: 10548)
- run.exe (PID: 10588)
- run.exe (PID: 10812)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10788)
- run.exe (PID: 2232)
- run.exe (PID: 11976)
- run.exe (PID: 12080)
- run.exe (PID: 9164)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10724)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10656)
- run.exe (PID: 10956)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11272)
- run.exe (PID: 10364)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11528)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11632)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11776)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9468)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11796)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12164)
- toolspab1.exe (PID: 11876)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10100)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10836)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11652)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12128)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11244)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10392)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8440)
- run.exe (PID: 8968)
- run.exe (PID: 11376)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10896)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11508)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11540)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10964)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8780)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11568)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10568)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 7148)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9832)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8544)
- run.exe (PID: 11888)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11584)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11028)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11112)
- run.exe (PID: 12244)
- run.exe (PID: 11100)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11128)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11408)
- run.exe (PID: 11424)
- run.exe (PID: 11280)
- run.exe (PID: 10976)
- run.exe (PID: 11552)
- run.exe (PID: 11172)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11896)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 3264)
- run.exe (PID: 11148)
- run.exe (PID: 8760)
- run.exe (PID: 11988)
- run.exe (PID: 4952)
- run.exe (PID: 9652)
- run.exe (PID: 10940)
- run.exe (PID: 11312)
- app.exe (PID: 10660)
- run.exe (PID: 10576)
- run.exe (PID: 11684)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11696)
- run.exe (PID: 11188)
- google-game.exe (PID: 5792)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11192)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11768)
- run.exe (PID: 10336)
- run.exe (PID: 8336)
- run.exe (PID: 9628)
- run.exe (PID: 11332)
- run.exe (PID: 10340)
- run.exe (PID: 8432)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8832)
- run.exe (PID: 9228)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11136)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11680)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11800)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8644)
- run.exe (PID: 9604)
- run.exe (PID: 11420)
- run.exe (PID: 9784)
- run.exe (PID: 11580)
- run.exe (PID: 12112)
- run.exe (PID: 10260)
- run.exe (PID: 11944)
- run.exe (PID: 11052)
- run.exe (PID: 10332)
- run.exe (PID: 10012)
- run.exe (PID: 8352)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11396)
- run.exe (PID: 11132)
- run.exe (PID: 11600)
- run.exe (PID: 11140)
- run.exe (PID: 10628)
- run.exe (PID: 11368)
- run.exe (PID: 9644)
- run.exe (PID: 9028)
- run.exe (PID: 2628)
- run.exe (PID: 11732)
- run.exe (PID: 12056)
- run.exe (PID: 10136)
- run.exe (PID: 12312)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12300)
- run.exe (PID: 12500)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12516)
- google-game.exe (PID: 11496)
- run.exe (PID: 11168)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12616)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12680)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12700)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12716)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12800)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12784)
- run.exe (PID: 12884)
- run.exe (PID: 12932)
- run.exe (PID: 12840)
- run.exe (PID: 12908)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13304)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13324)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12536)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12556)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12736)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12756)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13352)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13416)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13444)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13468)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13484)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13536)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13560)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13588)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13616)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13632)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13652)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13692)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13668)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13800)
- run.exe (PID: 13336)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13876)
- run.exe (PID: 13920)
- run.exe (PID: 14036)
- run.exe (PID: 14160)
- run.exe (PID: 14188)
- run.exe (PID: 14224)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14276)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14236)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12264)
- run.exe (PID: 12280)
- run.exe (PID: 11296)
- run.exe (PID: 5424)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13788)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13844)
- run.exe (PID: 14208)
- run.exe (PID: 12420)
- run.exe (PID: 11760)
- run.exe (PID: 11360)
- run.exe (PID: 12596)
- run.exe (PID: 12588)
- run.exe (PID: 12728)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12772)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10692)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14020)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14048)
- run.exe (PID: 12296)
- run.exe (PID: 10688)
- run.exe (PID: 10708)
- run.exe (PID: 14304)
- run.exe (PID: 14060)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12364)
- IcKhsjetUPnYsC.exe (PID: 13456)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14328)
- run.exe (PID: 14316)
- 94JHTAHA8VoOyufj3gFnsmhz.exe (PID: 10320)
- run.exe (PID: 12448)
- run.exe (PID: 12548)
- run.exe (PID: 12624)
- run.exe (PID: 8060)
- run.exe (PID: 9252)
- run.exe (PID: 12636)
- run.exe (PID: 12744)
- run.exe (PID: 12904)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10484)
- run.exe (PID: 14204)
- run.exe (PID: 13312)
- run.exe (PID: 13012)
- edspolishpp.exe (PID: 13088)
- run.exe (PID: 12672)
- run.exe (PID: 12360)
- run.exe (PID: 12512)
- jfiag3g_gg.exe (PID: 14128)
- run.exe (PID: 12764)
- run.exe (PID: 13252)
- run.exe (PID: 13276)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14220)
- run.exe (PID: 12984)
- run.exe (PID: 12836)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10416)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11380)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12100)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13704)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12472)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12464)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8696)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12488)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12340)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8252)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13432)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13176)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13224)
- run.exe (PID: 14052)
- run.exe (PID: 14268)
- toolspab1.exe (PID: 12408)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13440)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13544)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13584)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11048)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11560)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10672)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14124)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11748)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11236)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8636)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11008)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9520)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8564)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12900)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13048)
- run.exe (PID: 13372)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 5976)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10680)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13436)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11744)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14080)
- run.exe (PID: 13996)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14092)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14112)
- run.exe (PID: 14004)
- run.exe (PID: 13240)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12652)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8904)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11980)
- run.exe (PID: 12924)
- run.exe (PID: 12996)
- run.exe (PID: 13148)
- run.exe (PID: 13100)
- run.exe (PID: 13272)
- toolspab1.exe (PID: 13116)
- run.exe (PID: 11496)
- run.exe (PID: 13784)
- run.exe (PID: 13944)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11824)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13860)
- run.exe (PID: 14300)
- SmartClock.exe (PID: 13900)
- run.exe (PID: 11840)
- run.exe (PID: 13044)
- run.exe (PID: 13424)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11660)
- run.exe (PID: 8548)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8956)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10432)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10804)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14116)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13972)
- run.exe (PID: 13712)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11940)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14068)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13248)
- run.exe (PID: 14248)
- run.exe (PID: 10516)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11352)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13196)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14216)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12692)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12976)
- run.exe (PID: 11444)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13000)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10880)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13744)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14088)
- run.exe (PID: 12412)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11772)
- run.exe (PID: 13212)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9492)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12972)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12872)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13040)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11724)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11816)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13300)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13344)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14132)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13080)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13104)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12644)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11764)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13120)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13680)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13184)
- run.exe (PID: 10476)
- run.exe (PID: 13960)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14136)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10288)
- run.exe (PID: 13188)
- run.exe (PID: 7940)
- run.exe (PID: 7312)
- run.exe (PID: 12896)
- run.exe (PID: 13024)
- run.exe (PID: 5792)
- run.exe (PID: 11392)
- run.exe (PID: 14352)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14464)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13600)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13388)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14532)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14596)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14748)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14616)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14692)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14708)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14780)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14808)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14820)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14840)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14852)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14920)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14868)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14952)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14496)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14480)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14512)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14552)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14672)
- run.exe (PID: 15136)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15164)
- run.exe (PID: 15244)
- run.exe (PID: 15280)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15300)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15344)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15364)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15424)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15444)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15568)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15516)
- run.exe (PID: 15688)
- run.exe (PID: 15088)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15176)
- run.exe (PID: 15208)
- run.exe (PID: 16172)
- run.exe (PID: 16240)
- run.exe (PID: 9816)
- run.exe (PID: 12648)
- run.exe (PID: 11220)
- run.exe (PID: 14492)
- run.exe (PID: 16080)
- run.exe (PID: 14796)
- run.exe (PID: 14848)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12640)
- run.exe (PID: 15108)
- run.exe (PID: 14980)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15020)
- run.exe (PID: 15008)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15820)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15640)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15656)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15868)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15856)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15872)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15920)
- run.exe (PID: 15912)
- run.exe (PID: 14876)
- run.exe (PID: 14816)
- run.exe (PID: 14768)
- run.exe (PID: 14384)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 16040)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9220)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13524)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15504)
- run.exe (PID: 13612)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14416)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8852)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12428)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14588)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14440)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14472)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14264)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14576)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15944)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13392)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10524)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14804)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14992)
- run.exe (PID: 14732)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15752)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14960)
- run.exe (PID: 15224)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15196)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13856)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15460)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15380)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 16012)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14084)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15452)
- run.exe (PID: 14636)
- run.exe (PID: 14720)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14832)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13396)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15672)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 16188)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 16216)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 16336)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 16368)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13768)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14344)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 16024)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10352)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14628)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12608)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14644)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14632)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15144)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 16136)
- run.exe (PID: 13552)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9208)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15636)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13836)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15880)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15968)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13644)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 16036)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11756)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15252)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11892)
- run.exe (PID: 13020)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15264)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15952)
- run.exe (PID: 15760)
- run.exe (PID: 13112)
- run.exe (PID: 11068)
- run.exe (PID: 14788)
- run.exe (PID: 15812)
- run.exe (PID: 14996)
- run.exe (PID: 14736)
- run.exe (PID: 15416)
- run.exe (PID: 13404)
- run.exe (PID: 15964)
- run.exe (PID: 15592)
- run.exe (PID: 16300)
- run.exe (PID: 13740)
- run.exe (PID: 11588)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11252)
- run.exe (PID: 12284)
- run.exe (PID: 13516)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10800)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 16284)
- run.exe (PID: 14716)
- run.exe (PID: 11324)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10808)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15796)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10572)
- run.exe (PID: 12092)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8624)
- run.exe (PID: 9480)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15316)
- run.exe (PID: 13776)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14668)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12144)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15360)
- run.exe (PID: 15980)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15556)
- run.exe (PID: 12292)
- run.exe (PID: 15728)
- run.exe (PID: 15256)
- run.exe (PID: 12752)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8528)
- run.exe (PID: 16072)
- run.exe (PID: 15044)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14196)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 16312)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15472)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 16000)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14396)
- run.exe (PID: 14388)
- run.exe (PID: 13056)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12860)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10916)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15588)
- run.exe (PID: 1256)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 840)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 6124)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15184)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15124)
- run.exe (PID: 10560)
- run.exe (PID: 15204)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11212)
- run.exe (PID: 13820)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14252)
- run.exe (PID: 15816)
- run.exe (PID: 13464)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12920)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11412)
- run.exe (PID: 15240)
- run.exe (PID: 13192)
- run.exe (PID: 12432)
- run.exe (PID: 11144)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15972)
- run.exe (PID: 15160)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11820)
- run.exe (PID: 13512)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15220)
- run.exe (PID: 12308)
- run.exe (PID: 15436)
- run.exe (PID: 16004)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 16296)
- run.exe (PID: 16276)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15032)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11152)
- run.exe (PID: 14100)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15288)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15576)
- run.exe (PID: 12820)
- run.exe (PID: 15312)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14108)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 4084)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 2744)
- run.exe (PID: 12580)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 2312)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14152)
- run.exe (PID: 15232)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12992)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12456)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15120)
- run.exe (PID: 13608)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12828)
- run.exe (PID: 15036)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10980)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 16152)
- run.exe (PID: 12876)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13380)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10996)
- run.exe (PID: 8836)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15652)
- run.exe (PID: 13204)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15420)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9900)
- run.exe (PID: 6232)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 2860)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10068)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14604)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13752)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11468)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11200)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 4784)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13520)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13492)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 16148)
- run.exe (PID: 8944)
- run.exe (PID: 15604)
- run.exe (PID: 14612)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8816)
Changes the autorun value in the registry
- appsetup.exe (PID: 2060)
- Setup.exe (PID: 3004)
- vguuu.exe (PID: 2352)
- 1061149_flats_fon.exe (PID: 1516)
- 12(((((.exe (PID: 752)
- 1844707_pineapple_ood_icon((.exe (PID: 4416)
- 8068626.exe (PID: 7260)
Drops executable file immediately after starts
- LabPicV2.exe (PID: 3068)
- IDWCH2.exe (PID: 2408)
- SMCh1.exe (PID: 3912)
- cmd.exe (PID: 3504)
Changes settings of System certificates
- Xteat12.exe (PID: 3568)
- askinstall50.exe (PID: 3208)
Disables Windows Defender
- Xteat12.exe (PID: 3568)
Loads dropped or rewritten executable
- 7eae3352.exe (PID: 3848)
- powershell.exe (PID: 1604)
- gogonami.exe (PID: 5756)
- conhost.exe (PID: 1440)
- WerFault.exe (PID: 5116)
- conhost.exe (PID: 280)
- cmd.exe (PID: 2080)
- DllHost.exe (PID: 5408)
- mshta.exe (PID: 900)
- prun.exe (PID: 2684)
- svchost.exe (PID: 492)
- Tritiation.exe (PID: 360)
- jfiag3g_gg.exe (PID: 2112)
- cmd.exe (PID: 1772)
- cmd.exe (PID: 2640)
- taskkill.exe (PID: 4552)
- powershell.exe (PID: 3064)
- mAp.exe (PID: 3796)
- Main-lnstall-v7.1.exe (PID: 3228)
- mshta.exe (PID: 1060)
- conhost.exe (PID: 2460)
- conhost.exe (PID: 2520)
- cmd.exe (PID: 3624)
- conhost.exe (PID: 3896)
- NANbrowser.exe (PID: 3100)
- prun.exe (PID: 2284)
- vguuu.exe (PID: 2352)
- conhost.exe (PID: 4032)
- conhost.exe (PID: 324)
- appsetup.exe (PID: 2980)
- WerFault.exe (PID: 1164)
- powershell.exe (PID: 4020)
- powershell.exe (PID: 3716)
- powershell.exe (PID: 3540)
- cmd.exe (PID: 3564)
- conhost.exe (PID: 2432)
- conhost.exe (PID: 3816)
- md3_3kvm.exe (PID: 2304)
- BrowzarBrowser_j6.exe (PID: 1992)
- wmiprvse.exe (PID: 5836)
- cmd.exe (PID: 3048)
- gogonami.exe (PID: 3588)
- conhost.exe (PID: 5832)
- Xteat12.exe (PID: 3568)
- Setup.exe (PID: 3004)
- conhost.exe (PID: 4128)
- conhost.exe (PID: 3832)
- umbr.exe (PID: 2540)
- cmd.exe (PID: 2288)
- cmd.exe (PID: 424)
- conhost.exe (PID: 3164)
- LabPicV2.exe (PID: 3068)
- sfx_123_701.exe (PID: 2396)
- conhost.exe (PID: 3724)
- cmd.exe (PID: 2676)
- cmd.exe (PID: 3524)
- Browzar.exe (PID: 1272)
- app.exe (PID: 3736)
- appsetup.exe (PID: 2060)
- powershell.exe (PID: 2444)
- DllHost.exe (PID: 2312)
- conhost.exe (PID: 3664)
- conhost.exe (PID: 3600)
- askinstall50.exe (PID: 3208)
- conhost.exe (PID: 1148)
- powershell.exe (PID: 3316)
- Newouttab02.exe (PID: 2192)
- DllHost.exe (PID: 3404)
- powershell.exe (PID: 1328)
- Setup.exe (PID: 2868)
- consent.exe (PID: 3868)
- powershell.exe (PID: 2740)
- cmd.exe (PID: 2116)
- cmd.exe (PID: 3892)
- cmd.exe (PID: 3140)
- powershell.exe (PID: 2040)
- cmd.exe (PID: 3520)
- Main-lnstall-v7.1.exe (PID: 2752)
- powershell.exe (PID: 3020)
- Setup.exe (PID: 840)
- powershell.exe (PID: 3628)
- WinRAR.exe (PID: 3928)
- IDWCH2.exe (PID: 2408)
- SMCh1.exe (PID: 3912)
- cmd.exe (PID: 3504)
- conhost.exe (PID: 2432)
- powershell.exe (PID: 4012)
- conhost.exe (PID: 5200)
- svchost.exe (PID: 5604)
- run.exe (PID: 2388)
- Tritiation.exe (PID: 5276)
- Pupdate.exe (PID: 324)
- powershell.exe (PID: 2640)
- rUNdlL32.eXe (PID: 2272)
- cmd.exe (PID: 1300)
- NANbrowser.exe (PID: 4248)
- mshta.exe (PID: 5764)
- cmd.exe (PID: 988)
- conhost.exe (PID: 2288)
- cmd.exe (PID: 5208)
- cmd.exe (PID: 4124)
- jfiag3g_gg.exe (PID: 808)
- aE_nK7vZOFYhFlDLqUQshFxg.exe (PID: 4376)
- w_Xrc6UqsJdXOyGPQsMWdR0b.exe (PID: 4040)
- WerFault.exe (PID: 628)
- 8pthOztIBVLYt6kFLMuKjjvo.exe (PID: 4616)
- conhost.exe (PID: 5008)
- RG5CP0uxCTKWsDmpT9Ht1oCN.exe (PID: 4808)
- conhost.exe (PID: 5572)
- cmd.exe (PID: 5584)
- Updater.exe (PID: 5684)
- explorer.exe (PID: 6028)
- Toner-Recover.exe (PID: 3588)
- explorer.exe (PID: 3112)
- aE_nK7vZOFYhFlDLqUQshFxg.exe (PID: 4560)
- DllHost.exe (PID: 4536)
- conhost.exe (PID: 5212)
- regedit.exe (PID: 5088)
- regedit.exe (PID: 5532)
- SystemMonitor.exe (PID: 5416)
- iexplore.exe (PID: 788)
- oXzrQf21IDNLKfJlC5lhX4Jv.exe (PID: 4020)
- iexplore.exe (PID: 3460)
- SystemMonitor.exe (PID: 5756)
- 3QHjZx8dt0t26AfH9CRQRJBm.exe (PID: 5640)
- 8pthOztIBVLYt6kFLMuKjjvo.exe (PID: 5384)
- WISPTIS.EXE (PID: 2124)
- wXBwx1IVBV0oj3c7ksEBCECJ.exe (PID: 4836)
- consent.exe (PID: 884)
- ZA_Q3L8vS0E4GccBjGfJVJLe.exe (PID: 4496)
- Fepolicaeta.exe (PID: 2460)
- DllHost.exe (PID: 2112)
- prolab.exe (PID: 5856)
- regsvr32.exe (PID: 2520)
- oXzrQf21IDNLKfJlC5lhX4Jv.exe (PID: 4164)
- Ma07pX6h4JcViSzSUhgFN8RZ.exe (PID: 1260)
- conhost.exe (PID: 5012)
- SAtbVCDzYYWFTBTA_Oea8a1N.exe (PID: 6028)
- DllHost.exe (PID: 4856)
- F30KJxMk0hUsZoEPkpTkTDh_.exe (PID: 3680)
- SAtbVCDzYYWFTBTA_Oea8a1N.exe (PID: 5412)
- conhost.exe (PID: 4032)
- WISPTIS.EXE (PID: 4000)
- rUNdlL32.eXe (PID: 4456)
- IDownload.exe (PID: 5060)
- Ficocefyqa.exe (PID: 1280)
- Jisyraeloru.exe (PID: 3688)
- IDownload.App.exe (PID: 5000)
- csc.exe (PID: 5536)
- iexplore.exe (PID: 3352)
- cvtres.exe (PID: 4712)
- iexplore.exe (PID: 4888)
- conhost.exe (PID: 4976)
- Vecamelyky.exe (PID: 3380)
- Gylaevoluta.exe (PID: 2608)
- Mekymutavi.exe (PID: 544)
- iexplore.exe (PID: 4816)
- X8BrG24DU0bF6vlhsqhngg76.exe (PID: 2612)
- dkkoyQhUoZBWUs4Rp_cJIa5o.exe (PID: 5924)
- run.exe (PID: 4488)
- run.exe (PID: 3544)
- run.exe (PID: 1136)
- run.exe (PID: 3344)
- run.exe (PID: 1804)
- run.exe (PID: 4996)
- run.exe (PID: 3968)
- run.exe (PID: 1892)
- jooyu.exe (PID: 4204)
- run.exe (PID: 1088)
- x9yRVY4KGRfHuTqOEPAuH4XU.exe (PID: 4196)
- md8_8eus.exe (PID: 2540)
- file4.exe (PID: 5912)
- run.exe (PID: 5168)
- run.exe (PID: 4988)
- jingzhang.exe (PID: 980)
- run.exe (PID: 5692)
- run.exe (PID: 3152)
- run.exe (PID: 5600)
- WerFault.exe (PID: 2772)
- iexplore.exe (PID: 5068)
- conhost.exe (PID: 360)
- cmd.exe (PID: 4108)
- conhost.exe (PID: 3292)
- run.exe (PID: 4200)
- 5RrDYWMxQIYVWAyYwWHPHLBn.exe (PID: 2536)
- iexplore.exe (PID: 4352)
- conhost.exe (PID: 4956)
- cmd.exe (PID: 3452)
- ntvdm.exe (PID: 4236)
- run.exe (PID: 5208)
- run.exe (PID: 1596)
- Tu_oVga04bBd7yyUotWPAALW.exe (PID: 5040)
- ntvdm.exe (PID: 3644)
- run.exe (PID: 5864)
- run.exe (PID: 1544)
- conhost.exe (PID: 2384)
- cmd.exe (PID: 6028)
- run.exe (PID: 5104)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 3524)
- WerFault.exe (PID: 4792)
- run.exe (PID: 5112)
- cmd.exe (PID: 4132)
- HpF8gAIYSEJ1ugDsKShf2kv1.exe (PID: 3784)
- cmd.exe (PID: 2396)
- WerFault.exe (PID: 2912)
- conhost.exe (PID: 316)
- taskkill.exe (PID: 4828)
- run.exe (PID: 424)
- run.exe (PID: 3428)
- run.exe (PID: 1032)
- run.exe (PID: 4880)
- cmd.exe (PID: 4140)
- conhost.exe (PID: 4764)
- conhost.exe (PID: 964)
- run.exe (PID: 364)
- JoSetp.exe (PID: 5988)
- WerFault.exe (PID: 1336)
- run.exe (PID: 4780)
- ntvdm.exe (PID: 2100)
- run.exe (PID: 3676)
- run.exe (PID: 3288)
- ntvdm.exe (PID: 3664)
- run.exe (PID: 4032)
- mGFTWeXoYYdP5IqOlAWoOOLT.exe (PID: 5644)
- run.exe (PID: 1104)
- conhost.exe (PID: 3644)
- run.exe (PID: 5960)
- cmd.exe (PID: 5664)
- run.exe (PID: 4428)
- conhost.exe (PID: 2528)
- run.exe (PID: 5120)
- run.exe (PID: 5288)
- run.exe (PID: 1332)
- run.exe (PID: 3596)
- run.exe (PID: 4960)
- run.exe (PID: 5136)
- run.exe (PID: 4260)
- run.exe (PID: 4304)
- run.exe (PID: 4588)
- run.exe (PID: 4528)
- run.exe (PID: 2452)
- run.exe (PID: 5972)
- run.exe (PID: 2056)
- taskkill.exe (PID: 336)
- rUNdlL32.eXe (PID: 2492)
- run.exe (PID: 3348)
- run.exe (PID: 4192)
- run.exe (PID: 1144)
- run.exe (PID: 2240)
- run.exe (PID: 4672)
- run.exe (PID: 4608)
- run.exe (PID: 3140)
- run.exe (PID: 4072)
- run.exe (PID: 648)
- run.exe (PID: 4420)
- iexplore.exe (PID: 3312)
- jfiag3g_gg.exe (PID: 5444)
- run.exe (PID: 580)
- run.exe (PID: 4252)
- run.exe (PID: 1364)
- run.exe (PID: 4820)
- run.exe (PID: 5736)
- run.exe (PID: 5468)
- run.exe (PID: 5444)
- run.exe (PID: 4300)
- run.exe (PID: 2524)
- run.exe (PID: 868)
- run.exe (PID: 504)
- run.exe (PID: 5852)
- run.exe (PID: 3820)
- run.exe (PID: 1240)
- run.exe (PID: 5064)
- run.exe (PID: 4316)
- run.exe (PID: 3876)
- timeout.exe (PID: 5928)
- run.exe (PID: 2408)
- run.exe (PID: 4532)
- run.exe (PID: 4824)
- run.exe (PID: 2696)
- run.exe (PID: 472)
- run.exe (PID: 2764)
- run.exe (PID: 584)
- DllHost.exe (PID: 240)
- run.exe (PID: 4748)
- run.exe (PID: 6300)
- run.exe (PID: 6320)
- run.exe (PID: 3056)
- run.exe (PID: 2236)
- run.exe (PID: 6508)
- run.exe (PID: 6348)
- cc0qFqDkZv04whX9rGENHSJM.exe (PID: 4632)
- run.exe (PID: 6368)
- run.exe (PID: 6468)
- run.exe (PID: 6536)
- run.exe (PID: 6580)
- run.exe (PID: 6608)
- run.exe (PID: 6652)
- run.exe (PID: 6552)
- run.exe (PID: 6768)
- run.exe (PID: 6840)
- mGFTWeXoYYdP5IqOlAWoOOLT.exe (PID: 5924)
- run.exe (PID: 6976)
- iexplore.exe (PID: 6900)
- run.exe (PID: 6864)
- cmd.exe (PID: 7644)
- conhost.exe (PID: 7696)
- run.exe (PID: 7316)
- run.exe (PID: 7632)
- run.exe (PID: 7832)
- run.exe (PID: 7900)
- SearchProtocolHost.exe (PID: 6804)
- run.exe (PID: 7528)
- run.exe (PID: 7792)
- run.exe (PID: 7960)
- run.exe (PID: 8012)
- timeout.exe (PID: 6188)
- run.exe (PID: 4312)
- run.exe (PID: 6264)
- md6_6ydj.exe (PID: 6604)
- run.exe (PID: 6492)
- run.exe (PID: 7244)
- cmd.exe (PID: 3944)
- run.exe (PID: 6576)
- conhost.exe (PID: 6820)
- firefox.exe (PID: 2660)
- run.exe (PID: 7144)
- run.exe (PID: 7376)
- run.exe (PID: 7252)
- run.exe (PID: 6912)
- run.exe (PID: 7444)
- run.exe (PID: 7616)
- run.exe (PID: 7308)
- WerFault.exe (PID: 7932)
- ufgaa.exe (PID: 6444)
- run.exe (PID: 7948)
- run.exe (PID: 6428)
- run.exe (PID: 6516)
- run.exe (PID: 6896)
- run.exe (PID: 6292)
- run.exe (PID: 5644)
- run.exe (PID: 7196)
- run.exe (PID: 7360)
- run.exe (PID: 6952)
- run.exe (PID: 6560)
- run.exe (PID: 7080)
- run.exe (PID: 7652)
- run.exe (PID: 7800)
- run.exe (PID: 7780)
- jfiag3g_gg.exe (PID: 7944)
- run.exe (PID: 5272)
- 3270203.exe (PID: 8076)
- run.exe (PID: 6504)
- run.exe (PID: 6564)
- run.exe (PID: 7860)
- run.exe (PID: 2972)
- conhost.exe (PID: 7148)
- cmd.exe (PID: 6988)
- run.exe (PID: 6956)
- run.exe (PID: 7396)
- run.exe (PID: 7048)
- run.exe (PID: 7464)
- run.exe (PID: 7500)
- run.exe (PID: 7844)
- run.exe (PID: 7868)
- cmd.exe (PID: 7720)
- conhost.exe (PID: 7020)
- run.exe (PID: 7980)
- run.exe (PID: 8136)
- run.exe (PID: 6220)
- run.exe (PID: 6248)
- timeout.exe (PID: 6432)
- run.exe (PID: 6452)
- run.exe (PID: 6800)
- run.exe (PID: 4628)
- run.exe (PID: 6784)
- run.exe (PID: 6876)
- run.exe (PID: 7224)
- run.exe (PID: 6176)
- run.exe (PID: 7420)
- run.exe (PID: 6664)
- 8068626.exe (PID: 7260)
- run.exe (PID: 6252)
- run.exe (PID: 6736)
- run.exe (PID: 6648)
- 16854848995.exe (PID: 7280)
- jfiag3g_gg.exe (PID: 6544)
- conhost.exe (PID: 7808)
- ufgaa.exe (PID: 7296)
- run.exe (PID: 6364)
- run.exe (PID: 7184)
- cmd.exe (PID: 6940)
- run.exe (PID: 3976)
- p3-signed.exe (PID: 5128)
- run.exe (PID: 3316)
- run.exe (PID: 7032)
- run.exe (PID: 7660)
- conhost.exe (PID: 2476)
- run.exe (PID: 7944)
- WinHoster.exe (PID: 6156)
- cmd.exe (PID: 6460)
- run.exe (PID: 7992)
- run.exe (PID: 7712)
- cmd.exe (PID: 8184)
- run.exe (PID: 8160)
- run.exe (PID: 5268)
- run.exe (PID: 2496)
- run.exe (PID: 5440)
- findstr.exe (PID: 7216)
- run.exe (PID: 5412)
- run.exe (PID: 7744)
- run.exe (PID: 5568)
- run.exe (PID: 7276)
- run.exe (PID: 3872)
- run.exe (PID: 6832)
- Scolpire.exe.com (PID: 7588)
- run.exe (PID: 6708)
- run.exe (PID: 6688)
- run.exe (PID: 2116)
- run.exe (PID: 6148)
- PING.EXE (PID: 7708)
- cmd.exe (PID: 7220)
- conhost.exe (PID: 7088)
- run.exe (PID: 5196)
- run.exe (PID: 336)
- run.exe (PID: 6732)
- run.exe (PID: 6080)
- run.exe (PID: 6436)
- run.exe (PID: 4688)
- run.exe (PID: 7012)
- Scolpire.exe.com (PID: 6780)
- run.exe (PID: 2004)
- google-game.exe (PID: 7784)
- run.exe (PID: 1452)
- run.exe (PID: 6828)
- run.exe (PID: 7596)
- run.exe (PID: 8048)
- run.exe (PID: 7384)
- run.exe (PID: 1368)
- run.exe (PID: 1020)
- run.exe (PID: 5868)
- run.exe (PID: 5980)
- run.exe (PID: 7840)
- run.exe (PID: 6208)
- run.exe (PID: 2032)
- google-game.exe (PID: 3228)
- run.exe (PID: 6312)
- run.exe (PID: 7704)
- run.exe (PID: 6392)
- run.exe (PID: 1192)
- conhost.exe (PID: 7536)
- run.exe (PID: 7424)
- run.exe (PID: 7232)
- run.exe (PID: 6192)
- run.exe (PID: 6684)
- run.exe (PID: 6960)
- run.exe (PID: 3536)
- run.exe (PID: 7772)
- run.exe (PID: 7684)
- run.exe (PID: 7096)
- run.exe (PID: 6848)
- run.exe (PID: 1496)
- run.exe (PID: 8152)
- run.exe (PID: 6928)
- run.exe (PID: 4132)
- run.exe (PID: 6948)
- 6262959.exe (PID: 6636)
- run.exe (PID: 7264)
- run.exe (PID: 7488)
- run.exe (PID: 7452)
- run.exe (PID: 8124)
- run.exe (PID: 1412)
- run.exe (PID: 3704)
- run.exe (PID: 7076)
- run.exe (PID: 7524)
- run.exe (PID: 4920)
- run.exe (PID: 7352)
- cmd.exe (PID: 7544)
- conhost.exe (PID: 7100)
- ntvdm.exe (PID: 6884)
- run.exe (PID: 6340)
- run.exe (PID: 4876)
- run.exe (PID: 6924)
- run.exe (PID: 6680)
- run.exe (PID: 6592)
- run.exe (PID: 5688)
- run.exe (PID: 2448)
- run.exe (PID: 4356)
- run.exe (PID: 7736)
- run.exe (PID: 7300)
- run.exe (PID: 8104)
- WerFault.exe (PID: 7720)
- run.exe (PID: 6812)
- run.exe (PID: 8164)
- run.exe (PID: 6184)
- cmd.exe (PID: 6752)
- run.exe (PID: 7112)
- run.exe (PID: 8020)
- conhost.exe (PID: 7120)
- run.exe (PID: 8216)
- run.exe (PID: 8244)
- run.exe (PID: 6216)
- run.exe (PID: 1040)
- jfiag3g_gg.exe (PID: 8444)
- cmd.exe (PID: 8392)
- run.exe (PID: 8340)
- run.exe (PID: 8364)
- findstr.exe (PID: 8608)
- run.exe (PID: 8272)
- conhost.exe (PID: 8956)
- cmd.exe (PID: 8564)
- run.exe (PID: 8896)
- run.exe (PID: 9112)
- run.exe (PID: 9044)
- taskkill.exe (PID: 9164)
- run.exe (PID: 9152)
- run.exe (PID: 8800)
- run.exe (PID: 8884)
- run.exe (PID: 9324)
- run.exe (PID: 9184)
- run.exe (PID: 9368)
- Altrove.exe.com (PID: 9604)
- run.exe (PID: 9388)
- PING.EXE (PID: 9616)
- cmd.exe (PID: 6996)
- rUNdlL32.eXe (PID: 9872)
- conhost.exe (PID: 8256)
- Altrove.exe.com (PID: 10084)
- google-game.exe (PID: 8484)
- run.exe (PID: 9524)
- run.exe (PID: 8444)
- run.exe (PID: 9052)
- run.exe (PID: 9080)
- run.exe (PID: 8920)
- run.exe (PID: 8992)
- run.exe (PID: 9272)
- run.exe (PID: 9412)
- run.exe (PID: 9344)
- run.exe (PID: 9552)
- conhost.exe (PID: 9444)
- cmd.exe (PID: 9396)
- google-game.exe (PID: 9424)
- run.exe (PID: 9672)
- run.exe (PID: 9720)
- run.exe (PID: 9880)
- conhost.exe (PID: 9704)
- run.exe (PID: 9436)
- run.exe (PID: 9828)
- ntvdm.exe (PID: 9992)
- run.exe (PID: 10232)
- run.exe (PID: 9848)
- run.exe (PID: 1676)
- WerFault.exe (PID: 7468)
- run.exe (PID: 9964)
- run.exe (PID: 8408)
- run.exe (PID: 8648)
- run.exe (PID: 8616)
- run.exe (PID: 8672)
- run.exe (PID: 5252)
- run.exe (PID: 9488)
- run.exe (PID: 4424)
- run.exe (PID: 8872)
- cmd.exe (PID: 8832)
- cmd.exe (PID: 8984)
- run.exe (PID: 9124)
- run.exe (PID: 8948)
- conhost.exe (PID: 9220)
- run.exe (PID: 9300)
- run.exe (PID: 9624)
- ntvdm.exe (PID: 9772)
- run.exe (PID: 9744)
- run.exe (PID: 9804)
- WerFault.exe (PID: 10172)
- run.exe (PID: 9584)
- run.exe (PID: 9960)
- run.exe (PID: 4692)
- ntvdm.exe (PID: 8068)
- run.exe (PID: 10028)
- run.exe (PID: 8312)
- run.exe (PID: 3060)
- run.exe (PID: 4376)
- run.exe (PID: 8596)
- run.exe (PID: 8552)
- run.exe (PID: 4460)
- run.exe (PID: 8848)
- run.exe (PID: 8460)
- run.exe (PID: 8936)
- run.exe (PID: 9712)
- WerFault.exe (PID: 8760)
- run.exe (PID: 8492)
- run.exe (PID: 9548)
- run.exe (PID: 8608)
- run.exe (PID: 9196)
- run.exe (PID: 8740)
- run.exe (PID: 4364)
- run.exe (PID: 9688)
- run.exe (PID: 8788)
- run.exe (PID: 9656)
- run.exe (PID: 9360)
- run.exe (PID: 9588)
- run.exe (PID: 9856)
- run.exe (PID: 10020)
- run.exe (PID: 9692)
- run.exe (PID: 10192)
- run.exe (PID: 10208)
- run.exe (PID: 9904)
- run.exe (PID: 8228)
- run.exe (PID: 10120)
- run.exe (PID: 7748)
- run.exe (PID: 964)
- run.exe (PID: 1900)
- run.exe (PID: 6632)
- run.exe (PID: 7492)
- run.exe (PID: 7536)
- run.exe (PID: 8600)
- run.exe (PID: 8516)
- cmd.exe (PID: 8560)
- run.exe (PID: 8584)
- run.exe (PID: 10104)
- run.exe (PID: 8684)
- run.exe (PID: 316)
- run.exe (PID: 8480)
- cmd.exe (PID: 9208)
- conhost.exe (PID: 8356)
- run.exe (PID: 9736)
- toolspab1.exe (PID: 8764)
- run.exe (PID: 2948)
- run.exe (PID: 9316)
- run.exe (PID: 9792)
- run.exe (PID: 9148)
- conhost.exe (PID: 1252)
- 10680835434.exe (PID: 8252)
- run.exe (PID: 10196)
- run.exe (PID: 7728)
- run.exe (PID: 8668)
- rUNdlL32.eXe (PID: 8500)
- run.exe (PID: 9000)
- jfiag3g_gg.exe (PID: 8856)
- jfiag3g_gg.exe (PID: 9236)
- run.exe (PID: 7544)
- run.exe (PID: 10168)
- conhost.exe (PID: 4348)
- run.exe (PID: 5664)
- cmd.exe (PID: 9512)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9568)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8916)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9452)
- cmd.exe (PID: 9336)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9596)
- conhost.exe (PID: 9136)
- fa041e8b.exe (PID: 8700)
- conhost.exe (PID: 9180)
- toolspab1.exe (PID: 10140)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9796)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9800)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9812)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8784)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10024)
- ufgaa.exe (PID: 6756)
- run.exe (PID: 8332)
- run.exe (PID: 9308)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8756)
- run.exe (PID: 9312)
- run.exe (PID: 8468)
- run.exe (PID: 8960)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8820)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 7720)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9064)
- run.exe (PID: 10128)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9428)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9840)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9192)
- run.exe (PID: 9864)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 9868)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 3920)
- run.exe (PID: 9708)
- cmd.exe (PID: 10100)
- conhost.exe (PID: 3264)
- jfiag3g_gg.exe (PID: 9784)
- timeout.exe (PID: 8636)
- 50921261244.exe (PID: 10804)
- DllHost.exe (PID: 10816)
- cmd.exe (PID: 8284)
- google-game.exe (PID: 11496)
- rUNdlL32.eXe (PID: 9608)
- WerFault.exe (PID: 10036)
- toolspab1.exe (PID: 11876)
- edspolishpp.exe (PID: 13088)
- app.exe (PID: 10660)
- conhost.exe (PID: 11868)
- chrome.exe (PID: 13260)
- run.exe (PID: 15416)
- SearchFilterHost.exe (PID: 16196)
- 94JHTAHA8VoOyufj3gFnsmhz.exe (PID: 10320)
- chrome.exe (PID: 15536)
- run.exe (PID: 14788)
- run.exe (PID: 14736)
- SmartClock.exe (PID: 13900)
- run.exe (PID: 15760)
- run.exe (PID: 13740)
- run.exe (PID: 11068)
- run.exe (PID: 15812)
- run.exe (PID: 14996)
- run.exe (PID: 11588)
- chrome.exe (PID: 15712)
- chrome.exe (PID: 13296)
- DllHost.exe (PID: 14312)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11252)
- run.exe (PID: 15964)
- run.exe (PID: 13112)
- toolspab1.exe (PID: 13116)
- run.exe (PID: 13516)
- chrome.exe (PID: 15116)
- run.exe (PID: 14716)
- run.exe (PID: 13404)
- run.exe (PID: 15592)
- run.exe (PID: 12284)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15796)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10808)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10572)
- run.exe (PID: 13776)
- chrome.exe (PID: 13136)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10800)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 16284)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14668)
- chrome.exe (PID: 11096)
- run.exe (PID: 9480)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8624)
- run.exe (PID: 12092)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12144)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15316)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15556)
- run.exe (PID: 12292)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 8528)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15360)
- run.exe (PID: 15256)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14196)
- run.exe (PID: 15980)
- run.exe (PID: 16072)
- run.exe (PID: 15728)
- run.exe (PID: 12752)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14396)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 16000)
- run.exe (PID: 14388)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15184)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12860)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15472)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10916)
- chrome.exe (PID: 13364)
- run.exe (PID: 15044)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 16312)
- run.exe (PID: 15240)
- run.exe (PID: 1256)
- run.exe (PID: 15204)
- run.exe (PID: 10560)
- chrome.exe (PID: 14764)
- run.exe (PID: 13056)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15124)
- run.exe (PID: 13820)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11212)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15588)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 840)
- run.exe (PID: 13192)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14252)
- run.exe (PID: 15816)
- run.exe (PID: 12432)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12920)
- run.exe (PID: 13464)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11412)
- run.exe (PID: 13512)
- run.exe (PID: 12308)
- run.exe (PID: 15160)
- run.exe (PID: 11144)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11820)
- run.exe (PID: 15436)
- run.exe (PID: 16004)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 16296)
- run.exe (PID: 16276)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15032)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15972)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15288)
- run.exe (PID: 14100)
- run.exe (PID: 15232)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14108)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15576)
- run.exe (PID: 12820)
- run.exe (PID: 15312)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 2744)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 11152)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12992)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 2312)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 14152)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12828)
- run.exe (PID: 13608)
- run.exe (PID: 15036)
- run.exe (PID: 12580)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 12456)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 15120)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 4084)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 16152)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10996)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 10980)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 13380)
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 988)
Stealing of credential data
- svchost.exe (PID: 5604)
- w_Xrc6UqsJdXOyGPQsMWdR0b.exe (PID: 4040)
- Tritiation.exe (PID: 5276)
- NANbrowser.exe (PID: 4248)
- 8pthOztIBVLYt6kFLMuKjjvo.exe (PID: 5384)
- Newouttab02.exe (PID: 2192)
- ZA_Q3L8vS0E4GccBjGfJVJLe.exe (PID: 4496)
- oXzrQf21IDNLKfJlC5lhX4Jv.exe (PID: 4164)
- X8BrG24DU0bF6vlhsqhngg76.exe (PID: 2612)
- Updater.exe (PID: 5684)
- Tu_oVga04bBd7yyUotWPAALW.exe (PID: 5040)
- 3QHjZx8dt0t26AfH9CRQRJBm.exe (PID: 5640)
- Pupdate.exe (PID: 324)
Steals credentials from Web Browsers
- svchost.exe (PID: 5604)
- Newouttab02.exe (PID: 2192)
- ZA_Q3L8vS0E4GccBjGfJVJLe.exe (PID: 4496)
- w_Xrc6UqsJdXOyGPQsMWdR0b.exe (PID: 4040)
- 5RrDYWMxQIYVWAyYwWHPHLBn.exe (PID: 2536)
- 10680835434.exe (PID: 8252)
Starts Visual C# compiler
- IDownload.App.exe (PID: 5000)
VIDAR was detected
- Newouttab02.exe (PID: 2192)
- ZA_Q3L8vS0E4GccBjGfJVJLe.exe (PID: 4496)
- 5RrDYWMxQIYVWAyYwWHPHLBn.exe (PID: 2536)
REDLINE was detected
- Tritiation.exe (PID: 5276)
- NANbrowser.exe (PID: 4248)
- Updater.exe (PID: 5684)
- 8pthOztIBVLYt6kFLMuKjjvo.exe (PID: 5384)
- oXzrQf21IDNLKfJlC5lhX4Jv.exe (PID: 4164)
- 3QHjZx8dt0t26AfH9CRQRJBm.exe (PID: 5640)
- X8BrG24DU0bF6vlhsqhngg76.exe (PID: 2612)
- Tu_oVga04bBd7yyUotWPAALW.exe (PID: 5040)
- HpF8gAIYSEJ1ugDsKShf2kv1.exe (PID: 3784)
- mGFTWeXoYYdP5IqOlAWoOOLT.exe (PID: 5924)
- Pupdate.exe (PID: 324)
- edspolishpp.exe (PID: 13088)
- 6262959.exe (PID: 6636)
- cc0qFqDkZv04whX9rGENHSJM.exe (PID: 4632)
RACCOON was detected
- w_Xrc6UqsJdXOyGPQsMWdR0b.exe (PID: 4040)
Connects to CnC server
- w_Xrc6UqsJdXOyGPQsMWdR0b.exe (PID: 4040)
- vguuu.exe (PID: 2352)
- jooyu.exe (PID: 4204)
- ufgaa.exe (PID: 7296)
- ufgaa.exe (PID: 6444)
- ufgaa.exe (PID: 6756)
- x9yRVY4KGRfHuTqOEPAuH4XU.exe (PID: 4196)
Runs app for hidden code execution
- cmd.exe (PID: 6460)
- cmd.exe (PID: 6752)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 8184)
- cmd.exe (PID: 8392)
Writes to a start menu file
- Scolpire.exe.com (PID: 6780)
- IcKhsjetUPnYsC.exe (PID: 13456)
Loads the Task Scheduler COM API
- IcKhsjetUPnYsC.exe (PID: 13456)
Modifies hosts file to block updates
- F30KJxMk0hUsZoEPkpTkTDh_.exe (PID: 3680)
Writes to the hosts file
- F30KJxMk0hUsZoEPkpTkTDh_.exe (PID: 3680)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 3928)
- Main-lnstall-v7.1.exe (PID: 2752)
- Main-lnstall-v7.1.exe (PID: 3228)
- Setup.exe (PID: 840)
- Setup.exe (PID: 3004)
- powershell.exe (PID: 3316)
- powershell.exe (PID: 2444)
- powershell.exe (PID: 1328)
- powershell.exe (PID: 2040)
- powershell.exe (PID: 2640)
- powershell.exe (PID: 3716)
- powershell.exe (PID: 4012)
- powershell.exe (PID: 2740)
- powershell.exe (PID: 3064)
- appsetup.exe (PID: 2060)
- powershell.exe (PID: 1604)
- appsetup.exe (PID: 2980)
- powershell.exe (PID: 4020)
- prun.exe (PID: 2284)
- powershell.exe (PID: 3628)
- powershell.exe (PID: 3020)
- Xteat12.exe (PID: 3568)
- gogonami.exe (PID: 3588)
- BrowzarBrowser_j6.exe (PID: 1992)
- askinstall50.exe (PID: 3208)
- sfx_123_701.exe (PID: 2396)
- powershell.exe (PID: 3540)
- umbr.exe (PID: 2540)
- NANbrowser.exe (PID: 3100)
- vguuu.exe (PID: 2352)
- LabPicV2.tmp (PID: 3664)
- SMCh1.tmp (PID: 4504)
- IDWCH2.tmp (PID: 496)
- gogonami.exe (PID: 5756)
- mshta.exe (PID: 900)
- Browzar.exe (PID: 1272)
- Tritiation.exe (PID: 360)
- wmiprvse.exe (PID: 5836)
- Pupdate.exe (PID: 324)
- jfiag3g_gg.exe (PID: 2112)
- mAp.exe (PID: 3796)
- Newouttab02.exe (PID: 2192)
- mshta.exe (PID: 1060)
- run.exe (PID: 2388)
- 1844707_pineapple_ood_icon((.exe (PID: 4416)
- 1061149_flats_fon.exe (PID: 1516)
- Tritiation.exe (PID: 5276)
- app.exe (PID: 3736)
- NANbrowser.exe (PID: 4248)
- mshta.exe (PID: 5764)
- 12(((((.exe (PID: 752)
- 8pthOztIBVLYt6kFLMuKjjvo.exe (PID: 4616)
- RG5CP0uxCTKWsDmpT9Ht1oCN.exe (PID: 4808)
- Toner-Recover.exe (PID: 3588)
- oXzrQf21IDNLKfJlC5lhX4Jv.exe (PID: 4020)
- SystemMonitor.tmp (PID: 520)
- w_Xrc6UqsJdXOyGPQsMWdR0b.exe (PID: 4040)
- Updater.exe (PID: 5684)
- SystemMonitor.exe (PID: 5756)
- 8pthOztIBVLYt6kFLMuKjjvo.exe (PID: 5384)
- wXBwx1IVBV0oj3c7ksEBCECJ.exe (PID: 4836)
- oXzrQf21IDNLKfJlC5lhX4Jv.exe (PID: 4164)
- Fepolicaeta.exe (PID: 2460)
- Ma07pX6h4JcViSzSUhgFN8RZ.exe (PID: 1260)
- prolab.tmp (PID: 3596)
- 3QHjZx8dt0t26AfH9CRQRJBm.exe (PID: 5640)
- SAtbVCDzYYWFTBTA_Oea8a1N.exe (PID: 6028)
- SAtbVCDzYYWFTBTA_Oea8a1N.exe (PID: 5412)
- Ficocefyqa.exe (PID: 1280)
- ZA_Q3L8vS0E4GccBjGfJVJLe.exe (PID: 4496)
- IDownload.tmp (PID: 5936)
- Jisyraeloru.exe (PID: 3688)
- IDownload.App.exe (PID: 5000)
- Vecamelyky.exe (PID: 3380)
- Gylaevoluta.exe (PID: 2608)
- Mekymutavi.exe (PID: 544)
- X8BrG24DU0bF6vlhsqhngg76.exe (PID: 2612)
- dkkoyQhUoZBWUs4Rp_cJIa5o.exe (PID: 5924)
- jooyu.exe (PID: 4204)
- jingzhang.exe (PID: 980)
- Tu_oVga04bBd7yyUotWPAALW.exe (PID: 5040)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 3524)
- HpF8gAIYSEJ1ugDsKShf2kv1.exe (PID: 3784)
- JoSetp.exe (PID: 5988)
- mGFTWeXoYYdP5IqOlAWoOOLT.exe (PID: 5644)
- x9yRVY4KGRfHuTqOEPAuH4XU.exe (PID: 4196)
- F30KJxMk0hUsZoEPkpTkTDh_.exe (PID: 3680)
- jfiag3g_gg.exe (PID: 5444)
- 5RrDYWMxQIYVWAyYwWHPHLBn.exe (PID: 2536)
- mGFTWeXoYYdP5IqOlAWoOOLT.exe (PID: 5924)
- cc0qFqDkZv04whX9rGENHSJM.exe (PID: 4632)
- ufgaa.exe (PID: 6444)
- jfiag3g_gg.exe (PID: 7944)
- 3270203.exe (PID: 8076)
- 8068626.exe (PID: 7260)
- ufgaa.exe (PID: 7296)
- WinHoster.exe (PID: 6156)
- 16854848995.exe (PID: 7280)
- google-game.exe (PID: 7784)
- google-game.exe (PID: 3228)
- 6262959.exe (PID: 6636)
- p3-signed.exe (PID: 5128)
- jfiag3g_gg.exe (PID: 8444)
- Altrove.exe.com (PID: 10084)
- google-game.exe (PID: 8484)
- google-game.exe (PID: 9424)
- Scolpire.exe.com (PID: 6780)
- ufgaa.exe (PID: 6756)
- 10680835434.exe (PID: 8252)
- 50921261244.exe (PID: 10804)
- google-game.exe (PID: 5792)
- google-game.exe (PID: 11496)
- IcKhsjetUPnYsC.exe (PID: 13456)
- edspolishpp.exe (PID: 13088)
- app.exe (PID: 10660)
Checks supported languages
- Main-lnstall-v7.1.exe (PID: 2752)
- WinRAR.exe (PID: 3928)
- Main-lnstall-v7.1.exe (PID: 3228)
- Setup.exe (PID: 840)
- Setup.exe (PID: 3004)
- conhost.exe (PID: 3164)
- cmd.exe (PID: 3140)
- conhost.exe (PID: 3724)
- cmd.exe (PID: 2676)
- powershell.exe (PID: 2444)
- cmd.exe (PID: 2288)
- conhost.exe (PID: 280)
- powershell.exe (PID: 1328)
- conhost.exe (PID: 3896)
- powershell.exe (PID: 3716)
- conhost.exe (PID: 3816)
- cmd.exe (PID: 3520)
- cmd.exe (PID: 2116)
- conhost.exe (PID: 2432)
- cmd.exe (PID: 3892)
- powershell.exe (PID: 2040)
- powershell.exe (PID: 2640)
- conhost.exe (PID: 3664)
- cmd.exe (PID: 3564)
- powershell.exe (PID: 4012)
- powershell.exe (PID: 3316)
- conhost.exe (PID: 324)
- cmd.exe (PID: 3048)
- powershell.exe (PID: 2740)
- cmd.exe (PID: 2640)
- conhost.exe (PID: 2432)
- conhost.exe (PID: 4032)
- cmd.exe (PID: 3624)
- appsetup.exe (PID: 2060)
- powershell.exe (PID: 3064)
- powershell.exe (PID: 1604)
- cmd.exe (PID: 2080)
- appsetup.exe (PID: 2980)
- prun.exe (PID: 2684)
- conhost.exe (PID: 1440)
- powershell.exe (PID: 4020)
- conhost.exe (PID: 3832)
- conhost.exe (PID: 3600)
- prun.exe (PID: 2284)
- cmd.exe (PID: 3524)
- powershell.exe (PID: 3628)
- cmd.exe (PID: 424)
- conhost.exe (PID: 1148)
- cmd.exe (PID: 1772)
- conhost.exe (PID: 2520)
- 7eae3352.exe (PID: 3848)
- IDWCH2.exe (PID: 2408)
- powershell.exe (PID: 3020)
- LabPicV2.exe (PID: 3068)
- NANbrowser.exe (PID: 3100)
- BrowzarBrowser_j6.exe (PID: 1992)
- SMCh1.exe (PID: 3912)
- Newouttab02.exe (PID: 2192)
- Pupdate.exe (PID: 324)
- vguuu.exe (PID: 2352)
- Xteat12.exe (PID: 3568)
- md3_3kvm.exe (PID: 2304)
- gogonami.exe (PID: 3588)
- askinstall50.exe (PID: 3208)
- LabPicV2.tmp (PID: 3664)
- app.exe (PID: 3736)
- sfx_123_701.exe (PID: 2396)
- umbr.exe (PID: 2540)
- IDWCH2.tmp (PID: 496)
- SMCh1.tmp (PID: 4504)
- powershell.exe (PID: 3540)
- conhost.exe (PID: 5832)
- gogonami.exe (PID: 5756)
- mshta.exe (PID: 900)
- Browzar.exe (PID: 1272)
- conhost.exe (PID: 2460)
- Tritiation.exe (PID: 360)
- wmiprvse.exe (PID: 5836)
- jfiag3g_gg.exe (PID: 2112)
- conhost.exe (PID: 4128)
- cmd.exe (PID: 3504)
- mAp.exe (PID: 3796)
- mshta.exe (PID: 1060)
- conhost.exe (PID: 5200)
- cmd.exe (PID: 1300)
- 1061149_flats_fon.exe (PID: 1516)
- run.exe (PID: 2388)
- 1844707_pineapple_ood_icon((.exe (PID: 4416)
- 12(((((.exe (PID: 752)
- Tritiation.exe (PID: 5276)
- NANbrowser.exe (PID: 4248)
- mshta.exe (PID: 5764)
- conhost.exe (PID: 2288)
- cmd.exe (PID: 988)
- cmd.exe (PID: 5208)
- jfiag3g_gg.exe (PID: 808)
- cmd.exe (PID: 4124)
- aE_nK7vZOFYhFlDLqUQshFxg.exe (PID: 4376)
- w_Xrc6UqsJdXOyGPQsMWdR0b.exe (PID: 4040)
- conhost.exe (PID: 5008)
- 8pthOztIBVLYt6kFLMuKjjvo.exe (PID: 4616)
- RG5CP0uxCTKWsDmpT9Ht1oCN.exe (PID: 4808)
- conhost.exe (PID: 5572)
- cmd.exe (PID: 5584)
- Updater.exe (PID: 5684)
- aE_nK7vZOFYhFlDLqUQshFxg.exe (PID: 4560)
- Toner-Recover.exe (PID: 3588)
- conhost.exe (PID: 5212)
- oXzrQf21IDNLKfJlC5lhX4Jv.exe (PID: 4020)
- SystemMonitor.exe (PID: 5416)
- SystemMonitor.tmp (PID: 520)
- wXBwx1IVBV0oj3c7ksEBCECJ.exe (PID: 4836)
- SystemMonitor.exe (PID: 5756)
- 3QHjZx8dt0t26AfH9CRQRJBm.exe (PID: 5640)
- 8pthOztIBVLYt6kFLMuKjjvo.exe (PID: 5384)
- ZA_Q3L8vS0E4GccBjGfJVJLe.exe (PID: 4496)
- Fepolicaeta.exe (PID: 2460)
- oXzrQf21IDNLKfJlC5lhX4Jv.exe (PID: 4164)
- Ma07pX6h4JcViSzSUhgFN8RZ.exe (PID: 1260)
- prolab.tmp (PID: 3596)
- prolab.exe (PID: 5856)
- conhost.exe (PID: 5012)
- SAtbVCDzYYWFTBTA_Oea8a1N.exe (PID: 6028)
- F30KJxMk0hUsZoEPkpTkTDh_.exe (PID: 3680)
- conhost.exe (PID: 4032)
- SAtbVCDzYYWFTBTA_Oea8a1N.exe (PID: 5412)
- IDownload.exe (PID: 5060)
- Ficocefyqa.exe (PID: 1280)
- Jisyraeloru.exe (PID: 3688)
- IDownload.tmp (PID: 5936)
- IDownload.App.exe (PID: 5000)
- conhost.exe (PID: 4976)
- csc.exe (PID: 5536)
- cvtres.exe (PID: 4712)
- Vecamelyky.exe (PID: 3380)
- Gylaevoluta.exe (PID: 2608)
- Mekymutavi.exe (PID: 544)
- X8BrG24DU0bF6vlhsqhngg76.exe (PID: 2612)
- dkkoyQhUoZBWUs4Rp_cJIa5o.exe (PID: 5924)
- file4.exe (PID: 5912)
- jooyu.exe (PID: 4204)
- x9yRVY4KGRfHuTqOEPAuH4XU.exe (PID: 4196)
- md8_8eus.exe (PID: 2540)
- conhost.exe (PID: 360)
- 5RrDYWMxQIYVWAyYwWHPHLBn.exe (PID: 2536)
- Tu_oVga04bBd7yyUotWPAALW.exe (PID: 5040)
- conhost.exe (PID: 4956)
- cmd.exe (PID: 4108)
- jingzhang.exe (PID: 980)
- conhost.exe (PID: 3292)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 3524)
- cmd.exe (PID: 3452)
- conhost.exe (PID: 2384)
- HpF8gAIYSEJ1ugDsKShf2kv1.exe (PID: 3784)
- cmd.exe (PID: 6028)
- conhost.exe (PID: 316)
- cmd.exe (PID: 2396)
- conhost.exe (PID: 4764)
- conhost.exe (PID: 964)
- cmd.exe (PID: 4140)
- JoSetp.exe (PID: 5988)
- cmd.exe (PID: 4132)
- conhost.exe (PID: 3644)
- mGFTWeXoYYdP5IqOlAWoOOLT.exe (PID: 5644)
- conhost.exe (PID: 2528)
- cmd.exe (PID: 5664)
- jfiag3g_gg.exe (PID: 5444)
- cc0qFqDkZv04whX9rGENHSJM.exe (PID: 4632)
- mGFTWeXoYYdP5IqOlAWoOOLT.exe (PID: 5924)
- conhost.exe (PID: 7696)
- cmd.exe (PID: 7644)
- conhost.exe (PID: 6820)
- md6_6ydj.exe (PID: 6604)
- cmd.exe (PID: 3944)
- ufgaa.exe (PID: 6444)
- jfiag3g_gg.exe (PID: 7944)
- 3270203.exe (PID: 8076)
- conhost.exe (PID: 7148)
- conhost.exe (PID: 7020)
- cmd.exe (PID: 6988)
- 8068626.exe (PID: 7260)
- 16854848995.exe (PID: 7280)
- jfiag3g_gg.exe (PID: 6544)
- cmd.exe (PID: 7720)
- conhost.exe (PID: 7808)
- ufgaa.exe (PID: 7296)
- cmd.exe (PID: 6940)
- p3-signed.exe (PID: 5128)
- WinHoster.exe (PID: 6156)
- conhost.exe (PID: 2476)
- cmd.exe (PID: 6460)
- cmd.exe (PID: 8184)
- Scolpire.exe.com (PID: 7588)
- conhost.exe (PID: 7088)
- cmd.exe (PID: 7220)
- Scolpire.exe.com (PID: 6780)
- google-game.exe (PID: 7784)
- google-game.exe (PID: 3228)
- conhost.exe (PID: 7536)
- 6262959.exe (PID: 6636)
- conhost.exe (PID: 7100)
- cmd.exe (PID: 7544)
- conhost.exe (PID: 7120)
- cmd.exe (PID: 6752)
- cmd.exe (PID: 8392)
- jfiag3g_gg.exe (PID: 8444)
- conhost.exe (PID: 8956)
- cmd.exe (PID: 8564)
- Altrove.exe.com (PID: 9604)
- Altrove.exe.com (PID: 10084)
- conhost.exe (PID: 8256)
- cmd.exe (PID: 6996)
- google-game.exe (PID: 8484)
- conhost.exe (PID: 9444)
- conhost.exe (PID: 9704)
- cmd.exe (PID: 9396)
- google-game.exe (PID: 9424)
- conhost.exe (PID: 9180)
- conhost.exe (PID: 9220)
- cmd.exe (PID: 8984)
- cmd.exe (PID: 8832)
- cmd.exe (PID: 8560)
- conhost.exe (PID: 8356)
- toolspab1.exe (PID: 8764)
- conhost.exe (PID: 1252)
- cmd.exe (PID: 9208)
- 10680835434.exe (PID: 8252)
- conhost.exe (PID: 4348)
- cmd.exe (PID: 9512)
- fa041e8b.exe (PID: 8700)
- jfiag3g_gg.exe (PID: 9236)
- jfiag3g_gg.exe (PID: 8856)
- conhost.exe (PID: 9136)
- toolspab1.exe (PID: 10140)
- cmd.exe (PID: 9336)
- ufgaa.exe (PID: 6756)
- conhost.exe (PID: 3264)
- cmd.exe (PID: 10100)
- jfiag3g_gg.exe (PID: 9784)
- cmd.exe (PID: 9364)
- 50921261244.exe (PID: 10804)
- cmd.exe (PID: 10492)
- toolspab1.exe (PID: 11984)
- cmd.exe (PID: 10396)
- toolspab1.exe (PID: 11876)
- cmd.exe (PID: 8284)
- conhost.exe (PID: 11868)
- cmd.exe (PID: 11268)
- google-game.exe (PID: 5792)
- app.exe (PID: 10660)
- google-game.exe (PID: 11496)
- cmd.exe (PID: 13728)
- 94JHTAHA8VoOyufj3gFnsmhz.exe (PID: 10320)
- IcKhsjetUPnYsC.exe (PID: 13456)
- 94JHTAHA8VoOyufj3gFnsmhz.tmp (PID: 14008)
- edspolishpp.exe (PID: 13088)
- cmd.exe (PID: 13076)
- toolspab1.exe (PID: 12408)
- jfiag3g_gg.exe (PID: 14128)
- toolspab1.exe (PID: 13116)
- SmartClock.exe (PID: 13900)
- cmd.exe (PID: 15312)
- cmd.exe (PID: 15412)
Application launched itself
- Main-lnstall-v7.1.exe (PID: 2752)
- Setup.exe (PID: 840)
- prun.exe (PID: 2684)
- gogonami.exe (PID: 3588)
- Tritiation.exe (PID: 360)
- NANbrowser.exe (PID: 3100)
- cmd.exe (PID: 988)
- 8pthOztIBVLYt6kFLMuKjjvo.exe (PID: 4616)
- aE_nK7vZOFYhFlDLqUQshFxg.exe (PID: 4376)
- oXzrQf21IDNLKfJlC5lhX4Jv.exe (PID: 4020)
- SAtbVCDzYYWFTBTA_Oea8a1N.exe (PID: 6028)
- run.exe (PID: 2388)
- mGFTWeXoYYdP5IqOlAWoOOLT.exe (PID: 5644)
- cmd.exe (PID: 6460)
- Scolpire.exe.com (PID: 7588)
- google-game.exe (PID: 7784)
- cmd.exe (PID: 6752)
- Altrove.exe.com (PID: 9604)
- google-game.exe (PID: 8484)
- toolspab1.exe (PID: 8764)
- VAh4p2QmgqFRE9DJAL6BXcA9.exe (PID: 3524)
- toolspab1.exe (PID: 11984)
- google-game.exe (PID: 5792)
- toolspab1.exe (PID: 12408)
Creates files in the user directory
- powershell.exe (PID: 3316)
- powershell.exe (PID: 2444)
- powershell.exe (PID: 1328)
- powershell.exe (PID: 2640)
- powershell.exe (PID: 3716)
- powershell.exe (PID: 2040)
- powershell.exe (PID: 4012)
- powershell.exe (PID: 2740)
- powershell.exe (PID: 1604)
- powershell.exe (PID: 3064)
- powershell.exe (PID: 4020)
- powershell.exe (PID: 3628)
- powershell.exe (PID: 3020)
- powershell.exe (PID: 3540)
- Browzar.exe (PID: 1272)
- Xteat12.exe (PID: 3568)
- svchost.exe (PID: 5604)
- JoSetp.exe (PID: 5988)
- 8068626.exe (PID: 7260)
- Scolpire.exe.com (PID: 6780)
- 50921261244.exe (PID: 10804)
- IcKhsjetUPnYsC.exe (PID: 13456)
Reads the date of Windows installation
- powershell.exe (PID: 2444)
- powershell.exe (PID: 3316)
- powershell.exe (PID: 1328)
- powershell.exe (PID: 3716)
- powershell.exe (PID: 2040)
- powershell.exe (PID: 2640)
- powershell.exe (PID: 4012)
- powershell.exe (PID: 2740)
- powershell.exe (PID: 3064)
- powershell.exe (PID: 1604)
- powershell.exe (PID: 4020)
- powershell.exe (PID: 3628)
- powershell.exe (PID: 3020)
- powershell.exe (PID: 3540)
- wmiprvse.exe (PID: 5836)
- jingzhang.exe (PID: 980)
Drops a file with too old compile date
- Setup.exe (PID: 3004)
- LabPicV2.exe (PID: 3068)
- IDWCH2.exe (PID: 2408)
- SMCh1.exe (PID: 3912)
- BrowzarBrowser_j6.exe (PID: 1992)
- LabPicV2.tmp (PID: 3664)
- SMCh1.tmp (PID: 4504)
- IDWCH2.tmp (PID: 496)
- Xteat12.exe (PID: 3568)
- 1061149_flats_fon.exe (PID: 1516)
- 12(((((.exe (PID: 752)
- 1844707_pineapple_ood_icon((.exe (PID: 4416)
- w_Xrc6UqsJdXOyGPQsMWdR0b.exe (PID: 4040)
Drops a file that was compiled in debug mode
- Setup.exe (PID: 3004)
- LabPicV2.tmp (PID: 3664)
- SMCh1.tmp (PID: 4504)
- IDWCH2.tmp (PID: 496)
- gogonami.exe (PID: 5756)
- 7eae3352.exe (PID: 3848)
- cmd.exe (PID: 3504)
- Xteat12.exe (PID: 3568)
- Newouttab02.exe (PID: 2192)
- w_Xrc6UqsJdXOyGPQsMWdR0b.exe (PID: 4040)
- ZA_Q3L8vS0E4GccBjGfJVJLe.exe (PID: 4496)
- Jisyraeloru.exe (PID: 3688)
- Gylaevoluta.exe (PID: 2608)
- Mekymutavi.exe (PID: 544)
Executable content was dropped or overwritten
- Setup.exe (PID: 3004)
- LabPicV2.exe (PID: 3068)
- IDWCH2.exe (PID: 2408)
- SMCh1.exe (PID: 3912)
- BrowzarBrowser_j6.exe (PID: 1992)
- vguuu.exe (PID: 2352)
- LabPicV2.tmp (PID: 3664)
- SMCh1.tmp (PID: 4504)
- IDWCH2.tmp (PID: 496)
- gogonami.exe (PID: 5756)
- 7eae3352.exe (PID: 3848)
- cmd.exe (PID: 3504)
- umbr.exe (PID: 2540)
- Xteat12.exe (PID: 3568)
- 1061149_flats_fon.exe (PID: 1516)
- Newouttab02.exe (PID: 2192)
- 1844707_pineapple_ood_icon((.exe (PID: 4416)
- 12(((((.exe (PID: 752)
- w_Xrc6UqsJdXOyGPQsMWdR0b.exe (PID: 4040)
- ZA_Q3L8vS0E4GccBjGfJVJLe.exe (PID: 4496)
- Main-lnstall-v7.1.exe (PID: 3228)
- Jisyraeloru.exe (PID: 3688)
- Gylaevoluta.exe (PID: 2608)
- Mekymutavi.exe (PID: 544)
Creates files in the Windows directory
- Setup.exe (PID: 3004)
- appsetup.exe (PID: 2980)
Starts CMD.EXE for commands execution
- Setup.exe (PID: 3004)
- mshta.exe (PID: 900)
- mshta.exe (PID: 1060)
- mshta.exe (PID: 5764)
- cmd.exe (PID: 988)
- RG5CP0uxCTKWsDmpT9Ht1oCN.exe (PID: 4808)
- Jisyraeloru.exe (PID: 3688)
- Gylaevoluta.exe (PID: 2608)
- Newouttab02.exe (PID: 2192)
- ZA_Q3L8vS0E4GccBjGfJVJLe.exe (PID: 4496)
- w_Xrc6UqsJdXOyGPQsMWdR0b.exe (PID: 4040)
- x9yRVY4KGRfHuTqOEPAuH4XU.exe (PID: 4196)
- 16854848995.exe (PID: 7280)
- cmd.exe (PID: 6460)
- p3-signed.exe (PID: 5128)
- cmd.exe (PID: 6752)
- 5RrDYWMxQIYVWAyYwWHPHLBn.exe (PID: 2536)
- Mekymutavi.exe (PID: 544)
- F30KJxMk0hUsZoEPkpTkTDh_.exe (PID: 3680)
Executed as Windows Service
- appsetup.exe (PID: 2980)
Drops a file with a compile date too recent
- Setup.exe (PID: 3004)
- gogonami.exe (PID: 5756)
- umbr.exe (PID: 2540)
- 1061149_flats_fon.exe (PID: 1516)
- Xteat12.exe (PID: 3568)
- 12(((((.exe (PID: 752)
- 1844707_pineapple_ood_icon((.exe (PID: 4416)
- w_Xrc6UqsJdXOyGPQsMWdR0b.exe (PID: 4040)
- Jisyraeloru.exe (PID: 3688)
- Gylaevoluta.exe (PID: 2608)
- Mekymutavi.exe (PID: 544)
Creates a directory in Program Files
- BrowzarBrowser_j6.exe (PID: 1992)
- 1844707_pineapple_ood_icon((.exe (PID: 4416)
- 12(((((.exe (PID: 752)
- 1061149_flats_fon.exe (PID: 1516)
- RG5CP0uxCTKWsDmpT9Ht1oCN.exe (PID: 4808)
- SystemMonitor.tmp (PID: 520)
- prolab.tmp (PID: 3596)
- IDownload.tmp (PID: 5936)
- dkkoyQhUoZBWUs4Rp_cJIa5o.exe (PID: 5924)
Creates files in the program directory
- BrowzarBrowser_j6.exe (PID: 1992)
- RG5CP0uxCTKWsDmpT9Ht1oCN.exe (PID: 4808)
- Newouttab02.exe (PID: 2192)
- ZA_Q3L8vS0E4GccBjGfJVJLe.exe (PID: 4496)
- dkkoyQhUoZBWUs4Rp_cJIa5o.exe (PID: 5924)
- F30KJxMk0hUsZoEPkpTkTDh_.exe (PID: 3680)
- 5RrDYWMxQIYVWAyYwWHPHLBn.exe (PID: 2536)
- 3270203.exe (PID: 8076)
Reads mouse settings
- umbr.exe (PID: 2540)
- Scolpire.exe.com (PID: 7588)
- Scolpire.exe.com (PID: 6780)
- Altrove.exe.com (PID: 9604)
- Altrove.exe.com (PID: 10084)
Reads the Windows organization settings
- LabPicV2.tmp (PID: 3664)
- SMCh1.tmp (PID: 4504)
- IDWCH2.tmp (PID: 496)
- wmiprvse.exe (PID: 5836)
- SystemMonitor.tmp (PID: 520)
- prolab.tmp (PID: 3596)
- IDownload.tmp (PID: 5936)
Reads Windows owner or organization settings
- LabPicV2.tmp (PID: 3664)
- SMCh1.tmp (PID: 4504)
- IDWCH2.tmp (PID: 496)
- wmiprvse.exe (PID: 5836)
- SystemMonitor.tmp (PID: 520)
- prolab.tmp (PID: 3596)
- IDownload.tmp (PID: 5936)
Starts MSHTA.EXE for opening HTA or HTMLS files
- sfx_123_701.exe (PID: 2396)
- mAp.exe (PID: 3796)
Reads Microsoft Outlook installation path
- mshta.exe (PID: 900)
- Browzar.exe (PID: 1272)
- mshta.exe (PID: 1060)
- mshta.exe (PID: 5764)
- iexplore.exe (PID: 3460)
- iexplore.exe (PID: 4888)
- iexplore.exe (PID: 5068)
- iexplore.exe (PID: 3312)
- iexplore.exe (PID: 6900)
Creates a software uninstall entry
- BrowzarBrowser_j6.exe (PID: 1992)
- RG5CP0uxCTKWsDmpT9Ht1oCN.exe (PID: 4808)
- dkkoyQhUoZBWUs4Rp_cJIa5o.exe (PID: 5924)
Adds / modifies Windows certificates
- Xteat12.exe (PID: 3568)
- askinstall50.exe (PID: 3208)
Reads the cookies of Google Chrome
- jfiag3g_gg.exe (PID: 2112)
Checks for external IP
- Xteat12.exe (PID: 3568)
- vguuu.exe (PID: 2352)
- svchost.exe (PID: 5604)
- ufgaa.exe (PID: 6444)
- jooyu.exe (PID: 4204)
- ufgaa.exe (PID: 7296)
- ufgaa.exe (PID: 6756)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3504)
- cmd.exe (PID: 6028)
- cmd.exe (PID: 5664)
- cmd.exe (PID: 8564)
- cmd.exe (PID: 10396)
- cmd.exe (PID: 15312)
- cmd.exe (PID: 15412)
Executed via WMI
- rUNdlL32.eXe (PID: 2272)
Uses RUNDLL32.EXE to load library
- wmiprvse.exe (PID: 5836)
- jingzhang.exe (PID: 980)
Reads internet explorer settings
- Browzar.exe (PID: 1272)
Reads Environment values
- 1061149_flats_fon.exe (PID: 1516)
- 1844707_pineapple_ood_icon((.exe (PID: 4416)
- 12(((((.exe (PID: 752)
- Pupdate.exe (PID: 324)
- Tritiation.exe (PID: 5276)
- SystemMonitor.exe (PID: 5756)
- NANbrowser.exe (PID: 4248)
- Fepolicaeta.exe (PID: 2460)
- Updater.exe (PID: 5684)
- Ficocefyqa.exe (PID: 1280)
- 8pthOztIBVLYt6kFLMuKjjvo.exe (PID: 5384)
- Jisyraeloru.exe (PID: 3688)
- oXzrQf21IDNLKfJlC5lhX4Jv.exe (PID: 4164)
- 3QHjZx8dt0t26AfH9CRQRJBm.exe (PID: 5640)
- Vecamelyky.exe (PID: 3380)
- Gylaevoluta.exe (PID: 2608)
- Newouttab02.exe (PID: 2192)
- Mekymutavi.exe (PID: 544)
- ZA_Q3L8vS0E4GccBjGfJVJLe.exe (PID: 4496)
- JoSetp.exe (PID: 5988)
- X8BrG24DU0bF6vlhsqhngg76.exe (PID: 2612)
- Tu_oVga04bBd7yyUotWPAALW.exe (PID: 5040)
- w_Xrc6UqsJdXOyGPQsMWdR0b.exe (PID: 4040)
- HpF8gAIYSEJ1ugDsKShf2kv1.exe (PID: 3784)
- 5RrDYWMxQIYVWAyYwWHPHLBn.exe (PID: 2536)
- 3270203.exe (PID: 8076)
- mGFTWeXoYYdP5IqOlAWoOOLT.exe (PID: 5924)
- cc0qFqDkZv04whX9rGENHSJM.exe (PID: 4632)
- 6262959.exe (PID: 6636)
- 10680835434.exe (PID: 8252)
- 50921261244.exe (PID: 10804)
- F30KJxMk0hUsZoEPkpTkTDh_.exe (PID: 3680)
- edspolishpp.exe (PID: 13088)
Reads Windows Product ID
- wmiprvse.exe (PID: 5836)
Reads CPU info
- wmiprvse.exe (PID: 5836)
- Newouttab02.exe (PID: 2192)
- ZA_Q3L8vS0E4GccBjGfJVJLe.exe (PID: 4496)
- 5RrDYWMxQIYVWAyYwWHPHLBn.exe (PID: 2536)
- 10680835434.exe (PID: 8252)
- 50921261244.exe (PID: 10804)
Executed via COM
- explorer.exe (PID: 3112)
Starts Internet Explorer
- explorer.exe (PID: 3112)
- Fepolicaeta.exe (PID: 2460)
- Ficocefyqa.exe (PID: 1280)
- Vecamelyky.exe (PID: 3380)
Searches for installed software
- svchost.exe (PID: 5604)
- Tritiation.exe (PID: 5276)
- NANbrowser.exe (PID: 4248)
- Updater.exe (PID: 5684)
- oXzrQf21IDNLKfJlC5lhX4Jv.exe (PID: 4164)
- Newouttab02.exe (PID: 2192)
- ZA_Q3L8vS0E4GccBjGfJVJLe.exe (PID: 4496)
- w_Xrc6UqsJdXOyGPQsMWdR0b.exe (PID: 4040)
- 8pthOztIBVLYt6kFLMuKjjvo.exe (PID: 5384)
- X8BrG24DU0bF6vlhsqhngg76.exe (PID: 2612)
- 5RrDYWMxQIYVWAyYwWHPHLBn.exe (PID: 2536)
- Tu_oVga04bBd7yyUotWPAALW.exe (PID: 5040)
- 10680835434.exe (PID: 8252)
- mGFTWeXoYYdP5IqOlAWoOOLT.exe (PID: 5924)
- 3QHjZx8dt0t26AfH9CRQRJBm.exe (PID: 5640)
- HpF8gAIYSEJ1ugDsKShf2kv1.exe (PID: 3784)
Reads the cookies of Mozilla Firefox
- svchost.exe (PID: 5604)
Executes application which crashes
- cmd.exe (PID: 4108)
- cmd.exe (PID: 3452)
- cmd.exe (PID: 4140)
- cmd.exe (PID: 4132)
- cmd.exe (PID: 7544)
- cmd.exe (PID: 9396)
- cmd.exe (PID: 8984)
- cmd.exe (PID: 8832)
- cmd.exe (PID: 10100)
- cmd.exe (PID: 13728)
Starts CMD.EXE for self-deleting
- Newouttab02.exe (PID: 2192)
- ZA_Q3L8vS0E4GccBjGfJVJLe.exe (PID: 4496)
- w_Xrc6UqsJdXOyGPQsMWdR0b.exe (PID: 4040)
- 5RrDYWMxQIYVWAyYwWHPHLBn.exe (PID: 2536)
Starts itself from another location
- 8068626.exe (PID: 7260)
- IcKhsjetUPnYsC.exe (PID: 13456)
Starts application with an unusual extension
- cmd.exe (PID: 8184)
- Scolpire.exe.com (PID: 7588)
- cmd.exe (PID: 8392)
- Altrove.exe.com (PID: 9604)
INFO
Reads the computer name
- consent.exe (PID: 3868)
- DllHost.exe (PID: 2312)
- DllHost.exe (PID: 3404)
- svchost.exe (PID: 492)
- WerFault.exe (PID: 1164)
- WerFault.exe (PID: 5116)
- DllHost.exe (PID: 5408)
- taskkill.exe (PID: 4552)
- rUNdlL32.eXe (PID: 2272)
- svchost.exe (PID: 5604)
- WerFault.exe (PID: 628)
- explorer.exe (PID: 6028)
- explorer.exe (PID: 3112)
- DllHost.exe (PID: 4536)
- iexplore.exe (PID: 788)
- iexplore.exe (PID: 3460)
- DllHost.exe (PID: 2112)
- consent.exe (PID: 884)
- DllHost.exe (PID: 4856)
- WISPTIS.EXE (PID: 4000)
- rUNdlL32.eXe (PID: 4456)
- iexplore.exe (PID: 3352)
- iexplore.exe (PID: 4888)
- iexplore.exe (PID: 4816)
- iexplore.exe (PID: 5068)
- WerFault.exe (PID: 2772)
- iexplore.exe (PID: 4352)
- WerFault.exe (PID: 4792)
- taskkill.exe (PID: 4828)
- WerFault.exe (PID: 1336)
- taskkill.exe (PID: 336)
- rUNdlL32.eXe (PID: 2492)
- iexplore.exe (PID: 3312)
- DllHost.exe (PID: 240)
- iexplore.exe (PID: 6900)
- SearchProtocolHost.exe (PID: 6804)
- WerFault.exe (PID: 7932)
- firefox.exe (PID: 2660)
- PING.EXE (PID: 7708)
- taskkill.exe (PID: 9164)
- PING.EXE (PID: 9616)
- rUNdlL32.eXe (PID: 9872)
- WerFault.exe (PID: 7468)
- WerFault.exe (PID: 10172)
- rUNdlL32.eXe (PID: 8500)
- taskkill.exe (PID: 11756)
- DllHost.exe (PID: 10816)
- WerFault.exe (PID: 10036)
- rUNdlL32.eXe (PID: 9608)
- chrome.exe (PID: 13260)
- DllHost.exe (PID: 14312)
- taskkill.exe (PID: 16052)
- taskkill.exe (PID: 16152)
- SearchFilterHost.exe (PID: 16196)
- chrome.exe (PID: 15712)
- chrome.exe (PID: 15536)
Checks supported languages
- consent.exe (PID: 3868)
- DllHost.exe (PID: 2312)
- DllHost.exe (PID: 3404)
- svchost.exe (PID: 492)
- WerFault.exe (PID: 1164)
- WerFault.exe (PID: 5116)
- DllHost.exe (PID: 5408)
- taskkill.exe (PID: 4552)
- rUNdlL32.eXe (PID: 2272)
- svchost.exe (PID: 5604)
- WerFault.exe (PID: 628)
- explorer.exe (PID: 6028)
- explorer.exe (PID: 3112)
- DllHost.exe (PID: 4536)
- iexplore.exe (PID: 788)
- regedit.exe (PID: 5088)
- regedit.exe (PID: 5532)
- iexplore.exe (PID: 3460)
- DllHost.exe (PID: 2112)
- consent.exe (PID: 884)
- regsvr32.exe (PID: 2520)
- DllHost.exe (PID: 4856)
- WISPTIS.EXE (PID: 4000)
- rUNdlL32.eXe (PID: 4456)
- iexplore.exe (PID: 3352)
- iexplore.exe (PID: 4888)
- iexplore.exe (PID: 4816)
- WerFault.exe (PID: 2772)
- iexplore.exe (PID: 5068)
- iexplore.exe (PID: 4352)
- ntvdm.exe (PID: 4236)
- WerFault.exe (PID: 4792)
- ntvdm.exe (PID: 3644)
- WerFault.exe (PID: 2912)
- taskkill.exe (PID: 4828)
- WerFault.exe (PID: 1336)
- ntvdm.exe (PID: 3664)
- ntvdm.exe (PID: 2100)
- taskkill.exe (PID: 336)
- rUNdlL32.eXe (PID: 2492)
- iexplore.exe (PID: 3312)
- timeout.exe (PID: 5928)
- DllHost.exe (PID: 240)
- iexplore.exe (PID: 6900)
- SearchProtocolHost.exe (PID: 6804)
- timeout.exe (PID: 6188)
- firefox.exe (PID: 2660)
- WerFault.exe (PID: 7932)
- timeout.exe (PID: 6432)
- findstr.exe (PID: 7216)
- PING.EXE (PID: 7708)
- ntvdm.exe (PID: 6884)
- WerFault.exe (PID: 7720)
- findstr.exe (PID: 8608)
- PING.EXE (PID: 9616)
- rUNdlL32.eXe (PID: 9872)
- taskkill.exe (PID: 9164)
- ntvdm.exe (PID: 9992)
- WerFault.exe (PID: 7468)
- ntvdm.exe (PID: 9772)
- WerFault.exe (PID: 10172)
- ntvdm.exe (PID: 8068)
- WerFault.exe (PID: 8760)
- rUNdlL32.eXe (PID: 8500)
- ntvdm.exe (PID: 9228)
- timeout.exe (PID: 8636)
- WerFault.exe (PID: 10628)
- taskkill.exe (PID: 11756)
- DllHost.exe (PID: 10816)
- WerFault.exe (PID: 10036)
- ntvdm.exe (PID: 12440)
- WerFault.exe (PID: 13192)
- rUNdlL32.eXe (PID: 9608)
- chrome.exe (PID: 13260)
- DllHost.exe (PID: 14312)
- chrome.exe (PID: 13296)
- taskkill.exe (PID: 16052)
- taskkill.exe (PID: 16152)
- SearchFilterHost.exe (PID: 16196)
- chrome.exe (PID: 15712)
- chrome.exe (PID: 15536)
- chrome.exe (PID: 15116)
- chrome.exe (PID: 13136)
- chrome.exe (PID: 11096)
- chrome.exe (PID: 13364)
- chrome.exe (PID: 14764)
Checks Windows Trust Settings
- consent.exe (PID: 3868)
- askinstall50.exe (PID: 3208)
- Newouttab02.exe (PID: 2192)
- Xteat12.exe (PID: 3568)
- consent.exe (PID: 884)
- iexplore.exe (PID: 3460)
- iexplore.exe (PID: 788)
- ZA_Q3L8vS0E4GccBjGfJVJLe.exe (PID: 4496)
- iexplore.exe (PID: 4888)
- iexplore.exe (PID: 5068)
- iexplore.exe (PID: 3312)
- 5RrDYWMxQIYVWAyYwWHPHLBn.exe (PID: 2536)
- iexplore.exe (PID: 6900)
- iexplore.exe (PID: 3352)
- iexplore.exe (PID: 4816)
Reads settings of System Certificates
- Xteat12.exe (PID: 3568)
- askinstall50.exe (PID: 3208)
- Newouttab02.exe (PID: 2192)
- vguuu.exe (PID: 2352)
- 1061149_flats_fon.exe (PID: 1516)
- 1844707_pineapple_ood_icon((.exe (PID: 4416)
- 12(((((.exe (PID: 752)
- w_Xrc6UqsJdXOyGPQsMWdR0b.exe (PID: 4040)
- NANbrowser.exe (PID: 4248)
- Tritiation.exe (PID: 5276)
- consent.exe (PID: 884)
- iexplore.exe (PID: 3460)
- Fepolicaeta.exe (PID: 2460)
- ZA_Q3L8vS0E4GccBjGfJVJLe.exe (PID: 4496)
- iexplore.exe (PID: 788)
- Updater.exe (PID: 5684)
- 8pthOztIBVLYt6kFLMuKjjvo.exe (PID: 5384)
- Jisyraeloru.exe (PID: 3688)
- Ficocefyqa.exe (PID: 1280)
- iexplore.exe (PID: 4888)
- oXzrQf21IDNLKfJlC5lhX4Jv.exe (PID: 4164)
- Gylaevoluta.exe (PID: 2608)
- Vecamelyky.exe (PID: 3380)
- 3QHjZx8dt0t26AfH9CRQRJBm.exe (PID: 5640)
- appsetup.exe (PID: 2980)
- iexplore.exe (PID: 5068)
- Mekymutavi.exe (PID: 544)
- iexplore.exe (PID: 3312)
- 5RrDYWMxQIYVWAyYwWHPHLBn.exe (PID: 2536)
- jooyu.exe (PID: 4204)
- JoSetp.exe (PID: 5988)
- X8BrG24DU0bF6vlhsqhngg76.exe (PID: 2612)
- HpF8gAIYSEJ1ugDsKShf2kv1.exe (PID: 3784)
- iexplore.exe (PID: 6900)
- ufgaa.exe (PID: 6444)
- 3270203.exe (PID: 8076)
- iexplore.exe (PID: 3352)
- mGFTWeXoYYdP5IqOlAWoOOLT.exe (PID: 5924)
- Tu_oVga04bBd7yyUotWPAALW.exe (PID: 5040)
- ufgaa.exe (PID: 7296)
- x9yRVY4KGRfHuTqOEPAuH4XU.exe (PID: 4196)
- 50921261244.exe (PID: 10804)
- ufgaa.exe (PID: 6756)
- iexplore.exe (PID: 4816)
- F30KJxMk0hUsZoEPkpTkTDh_.exe (PID: 3680)
- edspolishpp.exe (PID: 13088)
- chrome.exe (PID: 15712)
Reads internet explorer settings
- mshta.exe (PID: 900)
- mshta.exe (PID: 1060)
- mshta.exe (PID: 5764)
- iexplore.exe (PID: 3460)
- iexplore.exe (PID: 4888)
- iexplore.exe (PID: 3312)
- iexplore.exe (PID: 5068)
- iexplore.exe (PID: 6900)
Loads dropped or rewritten executable
- SMCh1.tmp (PID: 4504)
- LabPicV2.tmp (PID: 3664)
- IDWCH2.tmp (PID: 496)
- 1061149_flats_fon.exe (PID: 1516)
- 1844707_pineapple_ood_icon((.exe (PID: 4416)
- 12(((((.exe (PID: 752)
- SystemMonitor.tmp (PID: 520)
- prolab.tmp (PID: 3596)
- IDownload.tmp (PID: 5936)
- 94JHTAHA8VoOyufj3gFnsmhz.tmp (PID: 14008)
Application was dropped or rewritten from another process
- IDWCH2.tmp (PID: 496)
- SMCh1.tmp (PID: 4504)
- LabPicV2.tmp (PID: 3664)
- 1061149_flats_fon.exe (PID: 1516)
- 12(((((.exe (PID: 752)
- 1844707_pineapple_ood_icon((.exe (PID: 4416)
Reads CPU info
- svchost.exe (PID: 5604)
Creates files in the program directory
- 1061149_flats_fon.exe (PID: 1516)
- SystemMonitor.tmp (PID: 520)
- 12(((((.exe (PID: 752)
- prolab.tmp (PID: 3596)
- 1844707_pineapple_ood_icon((.exe (PID: 4416)
- IDownload.tmp (PID: 5936)
Changes internet zones settings
- iexplore.exe (PID: 788)
- iexplore.exe (PID: 3352)
- iexplore.exe (PID: 4816)
Application launched itself
- iexplore.exe (PID: 788)
- iexplore.exe (PID: 3352)
- iexplore.exe (PID: 4816)
- chrome.exe (PID: 13260)
Creates a software uninstall entry
- SystemMonitor.tmp (PID: 520)
- prolab.tmp (PID: 3596)
- IDownload.tmp (PID: 5936)
Creates files in the user directory
- iexplore.exe (PID: 3460)
- iexplore.exe (PID: 4888)
Dropped object may contain Bitcoin addresses
- Xteat12.exe (PID: 3568)
Reads the hosts file
- chrome.exe (PID: 13260)
- chrome.exe (PID: 15712)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | Main-lnstall-v7.1.exe |
|---|---|
| ZipUncompressedSize: | 705008656 |
| ZipCompressedSize: | 7363267 |
| ZipCRC: | 0x9457e07d |
| ZipModifyDate: | 2021:07:12 15:14:23 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0001 |
| ZipRequiredVersion: | 788 |
Total processes
1 457
Monitored processes
1 416
Malicious processes
981
Suspicious processes
209
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | C:\Windows\system32\DllHost.exe /Processid:{F9717507-6651-4EDB-BFF7-AE615179BCCF} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 280 | \??\C:\Windows\system32\conhost.exe "-1440799351228553031-1748615682-1514047465-1166498968-616591428-12104245102129099103" | \??\C:\Windows\system32\conhost.exe | — | csrss.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 280 | C:\Users\Public\run.exe | C:\Users\Public\run.exe | — | run.exe | |||||||||||
User: admin Company: EdmRelationshipNavigationPropertyAttribute Corporation. Integrity Level: HIGH Description: ListenActivity Application App Exit code: 0 Version: 449.466.103.491 Modules
| |||||||||||||||
| 316 | \??\C:\Windows\system32\conhost.exe "2042275696-39882532196777256820368848913885349621737105098-2090374072-1377877967" | \??\C:\Windows\system32\conhost.exe | — | csrss.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 316 | C:\Users\Public\run.exe | C:\Users\Public\run.exe | — | run.exe | |||||||||||
User: admin Company: EdmRelationshipNavigationPropertyAttribute Corporation. Integrity Level: HIGH Description: ListenActivity Application App Exit code: 0 Version: 449.466.103.491 Modules
| |||||||||||||||
| 324 | \??\C:\Windows\system32\conhost.exe "1807618700935668893320359107127984848-745097267-6483708401196815589637883028" | \??\C:\Windows\system32\conhost.exe | — | csrss.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 324 | C:\Users\admin\AppData\Local\Temp\Pupdate.exe | C:\Users\admin\AppData\Local\Temp\Pupdate.exe | Setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 336 | taskkill /im ZA_Q3L8vS0E4GccBjGfJVJLe.exe /f | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 336 | C:\Users\Public\run.exe | C:\Users\Public\run.exe | — | run.exe | |||||||||||
User: admin Company: EdmRelationshipNavigationPropertyAttribute Corporation. Integrity Level: HIGH Description: ListenActivity Application App Exit code: 0 Version: 449.466.103.491 Modules
| |||||||||||||||
| 360 | "C:\Program Files\Browzar\Tritiation.exe" | C:\Program Files\Browzar\Tritiation.exe | — | BrowzarBrowser_j6.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
Total events
260 136
Read events
256 858
Write events
3 243
Delete events
35
Modification events
| (PID) Process: | (3928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3928) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\60ec5c8fa096f_Main-lnstall-v7.1.zip | |||
| (PID) Process: | (3928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
Executable files
178
Suspicious files
93
Text files
78
Unknown types
272
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3928.7135\Main-lnstall-v7.1.exe | — | |
MD5:— | SHA256:— | |||
| 3228 | Main-lnstall-v7.1.exe | C:\Users\admin\AppData\Local\Temp\Setup.exe | — | |
MD5:— | SHA256:— | |||
| 3316 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 3316 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\T2TAY8JE9BG8F9CLZ4MB.temp | binary | |
MD5:— | SHA256:— | |||
| 2444 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF374829.TMP | binary | |
MD5:— | SHA256:— | |||
| 1328 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ILVD12NQIAFK8O2V1KD0.temp | binary | |
MD5:— | SHA256:— | |||
| 3004 | Setup.exe | C:\Windows\PublicGaming\prun.exe | — | |
MD5:— | SHA256:— | |||
| 2444 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 1328 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF374a2c.TMP | binary | |
MD5:— | SHA256:— | |||
| 1328 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
962
TCP/UDP connections
931
DNS requests
145
Threats
4 544
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
496 | IDWCH2.tmp | HEAD | 200 | 63.250.33.126:80 | http://requested404.com/C_Pirlo/IDownload.exe | US | — | — | suspicious |
4504 | SMCh1.tmp | HEAD | 200 | 63.250.33.126:80 | http://requested404.com/C_Pirlo/sysMonitor.exe | US | — | — | suspicious |
496 | IDWCH2.tmp | GET | 200 | 63.250.33.126:80 | http://requested404.com/C_Pirlo/IDownload.exe | US | executable | 622 Kb | suspicious |
996 | lsass.exe | GET | 200 | 104.117.200.9:80 | http://x1.c.lencr.org/ | US | der | 717 b | whitelisted |
4504 | SMCh1.tmp | GET | 200 | 63.250.33.126:80 | http://requested404.com/C_Pirlo/sysMonitor.exe | US | executable | 282 Kb | suspicious |
996 | lsass.exe | GET | 200 | 195.138.255.17:80 | http://crl.identrust.com/DSTROOTCAX3CRL.crl | DE | der | 1.16 Kb | whitelisted |
2352 | vguuu.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | text | 255 b | malicious |
996 | lsass.exe | GET | 200 | 195.138.255.16:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgS8tNLAQkZB74GlzskVxiDiZQ%3D%3D | DE | der | 503 b | shared |
3568 | Xteat12.exe | GET | 200 | 2.56.59.245:80 | http://2.56.59.245/server.txt | unknown | text | 18 b | suspicious |
3208 | askinstall50.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
996 | lsass.exe | 67.26.75.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
996 | lsass.exe | 195.138.255.17:80 | crl.identrust.com | AS33891 Netzbetrieb GmbH | DE | whitelisted |
996 | lsass.exe | 104.117.200.9:80 | x1.c.lencr.org | TPG Telecom Limited | US | unknown |
3004 | Setup.exe | 195.181.169.68:443 | echo.bluewavecdn.com | — | GB | suspicious |
996 | lsass.exe | 195.138.255.16:80 | r3.o.lencr.org | AS33891 Netzbetrieb GmbH | DE | suspicious |
2980 | appsetup.exe | 195.181.164.195:443 | green.cablesparking.net | Datacamp Limited | GB | malicious |
2284 | prun.exe | 195.181.169.68:443 | echo.bluewavecdn.com | — | GB | suspicious |
3568 | Xteat12.exe | 34.117.59.81:443 | ipinfo.io | — | US | whitelisted |
3568 | Xteat12.exe | 2.56.59.245:80 | — | — | — | suspicious |
2352 | vguuu.exe | 208.95.112.1:80 | ip-api.com | IBURST | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
spark.lightburst.xyz |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
crl.identrust.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
echo.bluewavecdn.com |
| suspicious |
green.cablesparking.net |
| unknown |
server.sproutfrost.com |
| whitelisted |
cdn.coinchargery.com |
| whitelisted |
bucket.swiftlaunchx.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3004 | Setup.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
3568 | Xteat12.exe | A Network Trojan was detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
3568 | Xteat12.exe | Potential Corporate Privacy Violation | ET POLICY Possible External IP Lookup SSL Cert Observed (ipinfo.io) |
2540 | umbr.exe | Potential Corporate Privacy Violation | ET POLICY Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
2540 | umbr.exe | A Network Trojan was detected | ET INFO AutoIt User-Agent Downloading ZIP |
2352 | vguuu.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
2352 | vguuu.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
4504 | SMCh1.tmp | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
496 | IDWCH2.tmp | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1272 | Browzar.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
321 ETPRO signatures available at the full report
Process | Message |
|---|---|
WerFault.exe | Error - |
WerFault.exe | ReadProcessMemory failed while trying to read PebBaseAddress |
WerFault.exe | |
WerFault.exe | Error - |
WerFault.exe | Failed to read the peb from the process |
WerFault.exe | |
WerFault.exe | Error - |
WerFault.exe | ReadProcessMemory failed while trying to read PebBaseAddress |
WerFault.exe | |
WerFault.exe | Error - |