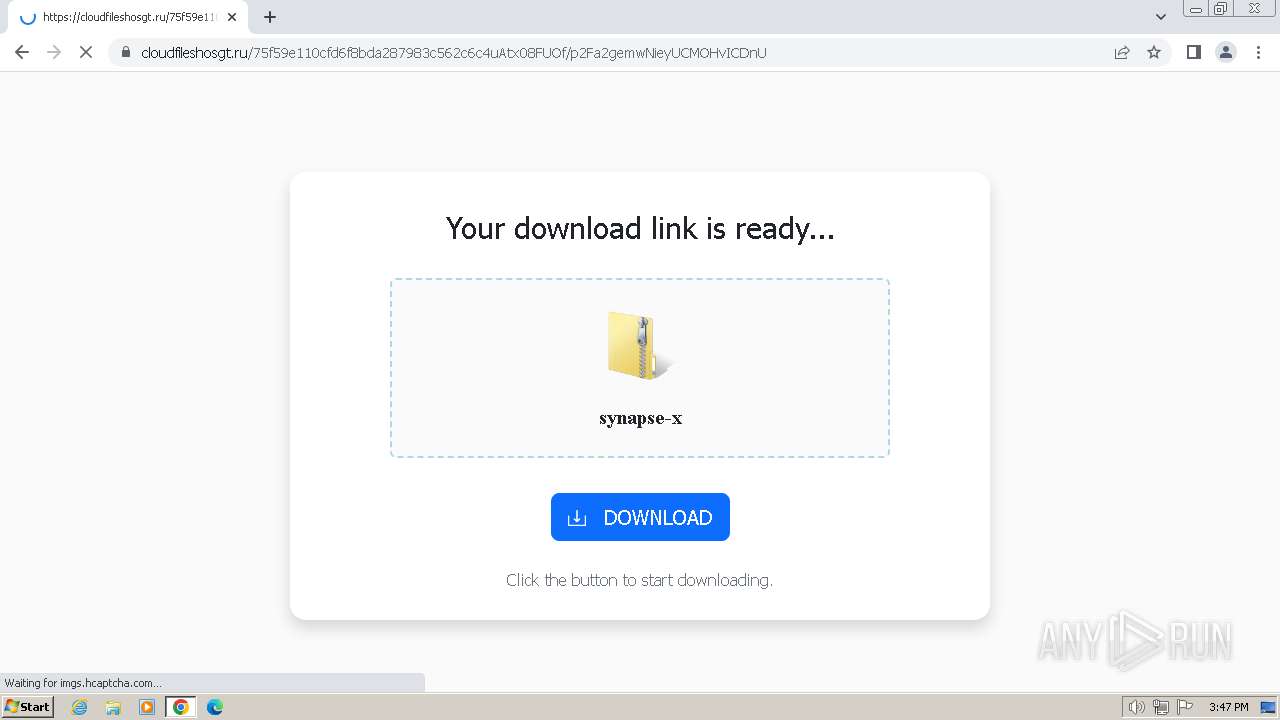
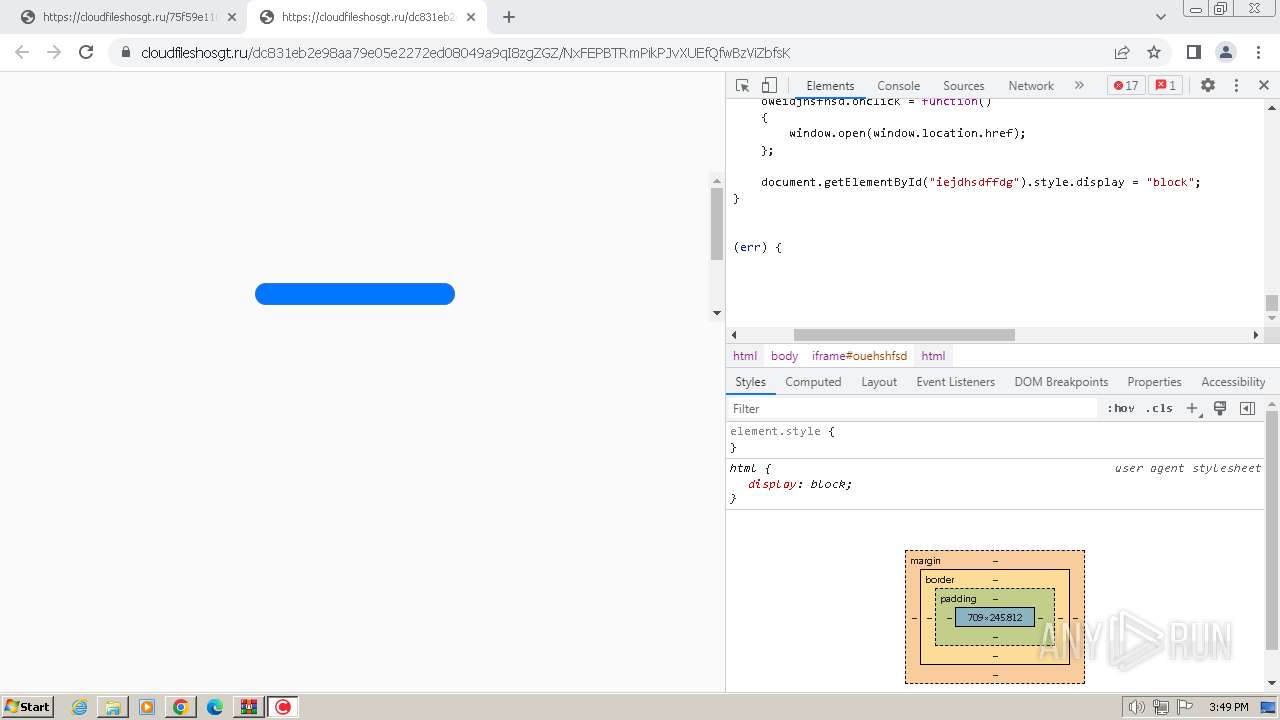
| URL: | http://cloudaxus.com/file/144f150 |
| Full analysis: | https://app.any.run/tasks/70ca5060-beda-452e-996b-d455328a373e |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | March 23, 2024, 15:46:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | FF74554AEF3C8505C66980E419FD4B39 |
| SHA1: | FD3F4D265095A3CC47247C12FB3BC2F5F0B10C22 |
| SHA256: | FD7C1D8EED4541A3FD5EBA632F0758077631086FF321FA3DEF03AE1348000A58 |
| SSDEEP: | 3:N1KdJKQBEdWKzoU4QV:C6gKLV |
MALICIOUS
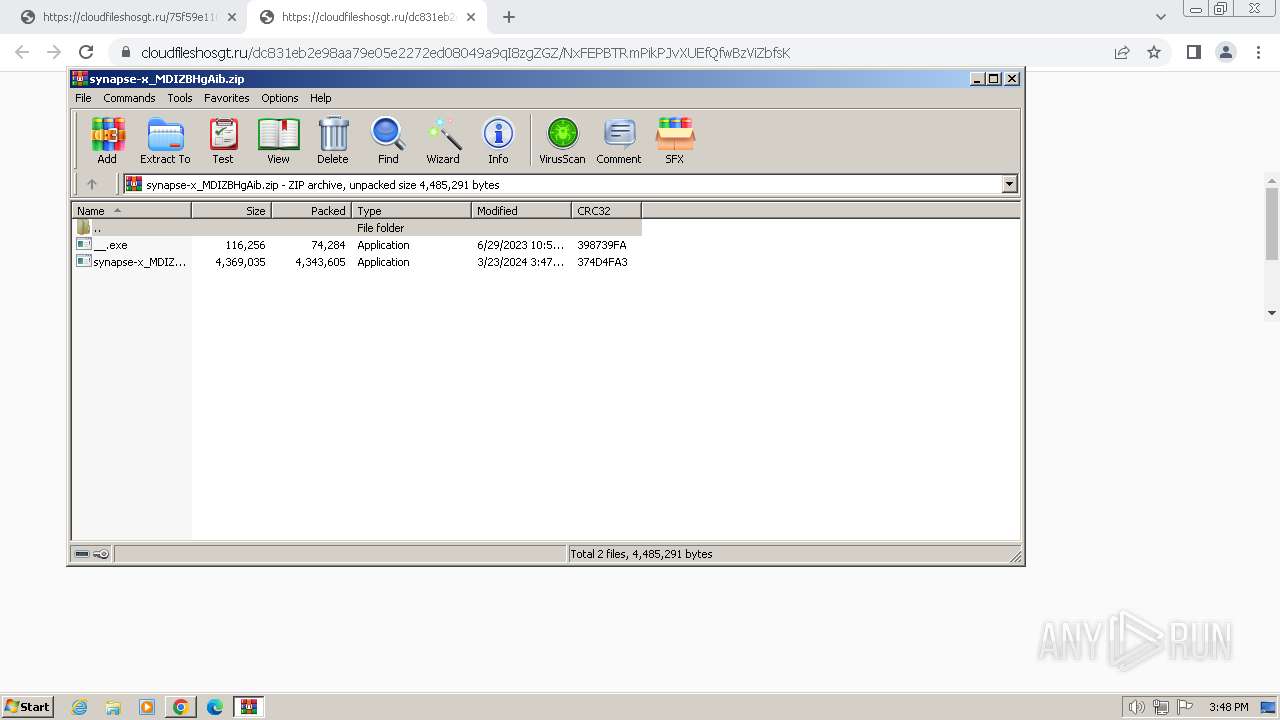
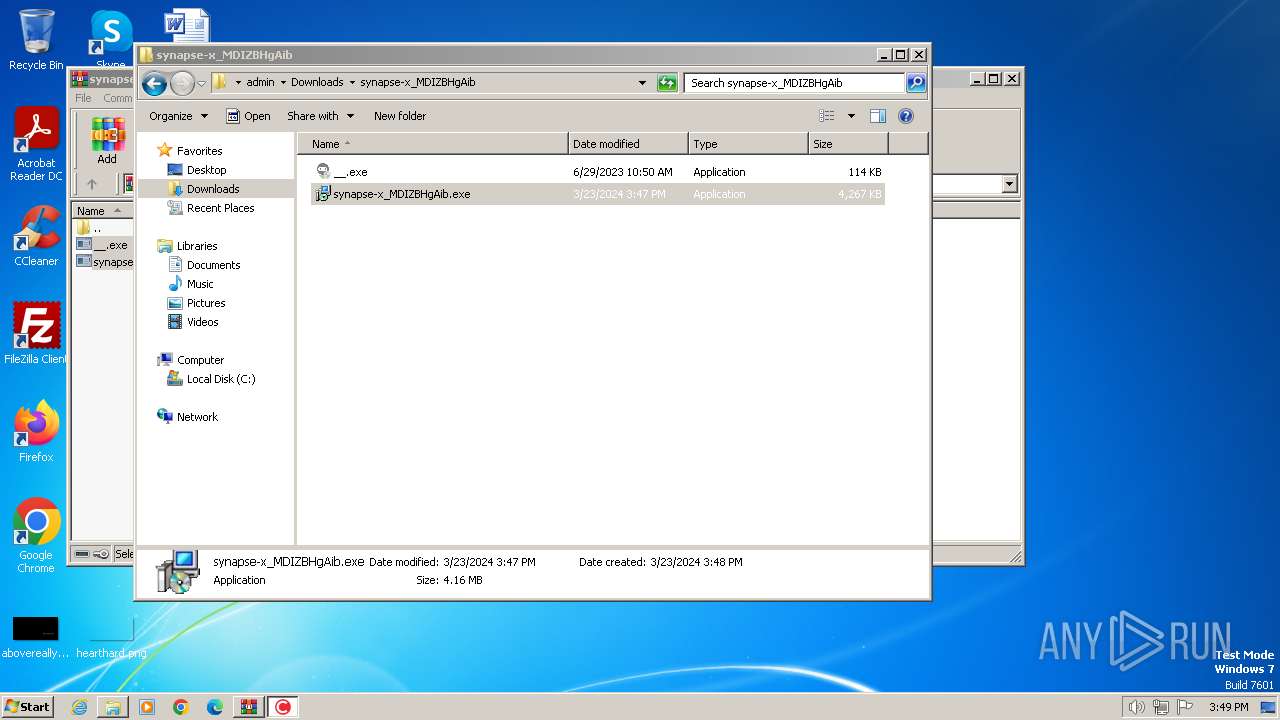
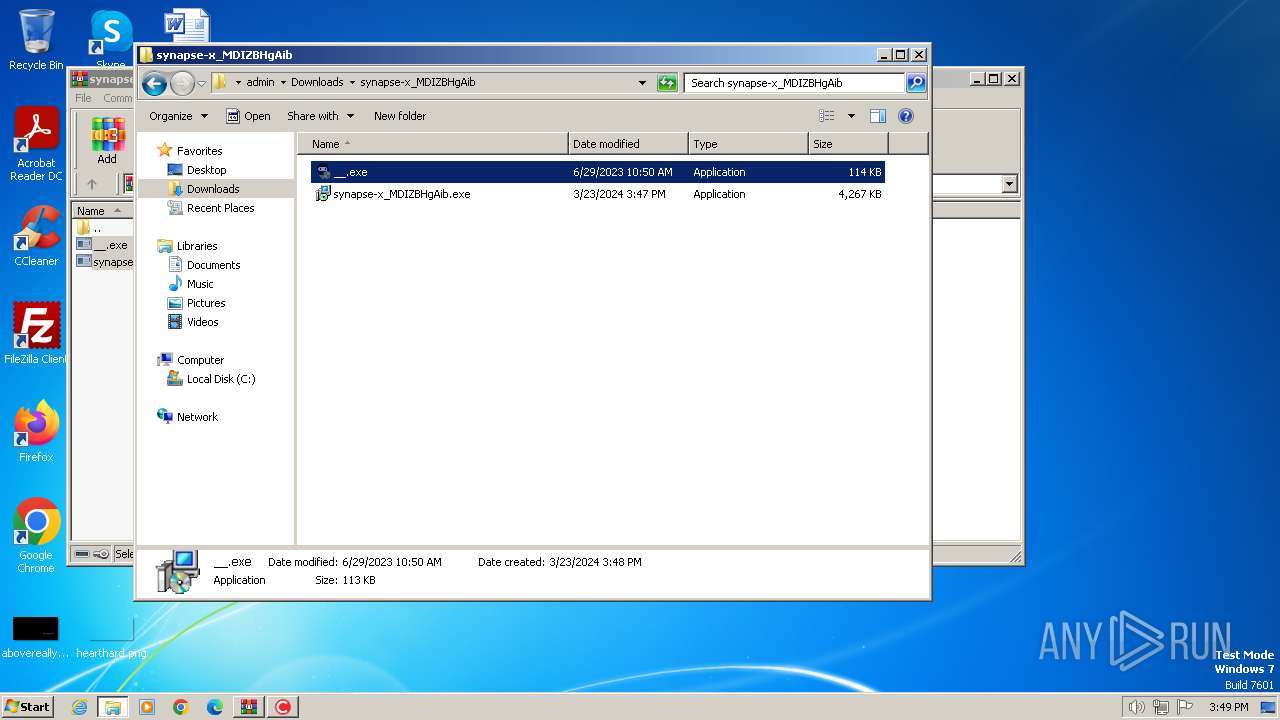
Drops the executable file immediately after the start
- synapse-x_MDIZBHgAib.exe (PID: 1308)
- synapse-x_MDIZBHgAib.exe (PID: 2584)
- synapse-x_MDIZBHgAib.tmp (PID: 1216)
- __.exe (PID: 2356)
- setup.exe (PID: 2016)
- setup.exe (PID: 864)
- installer.exe (PID: 2788)
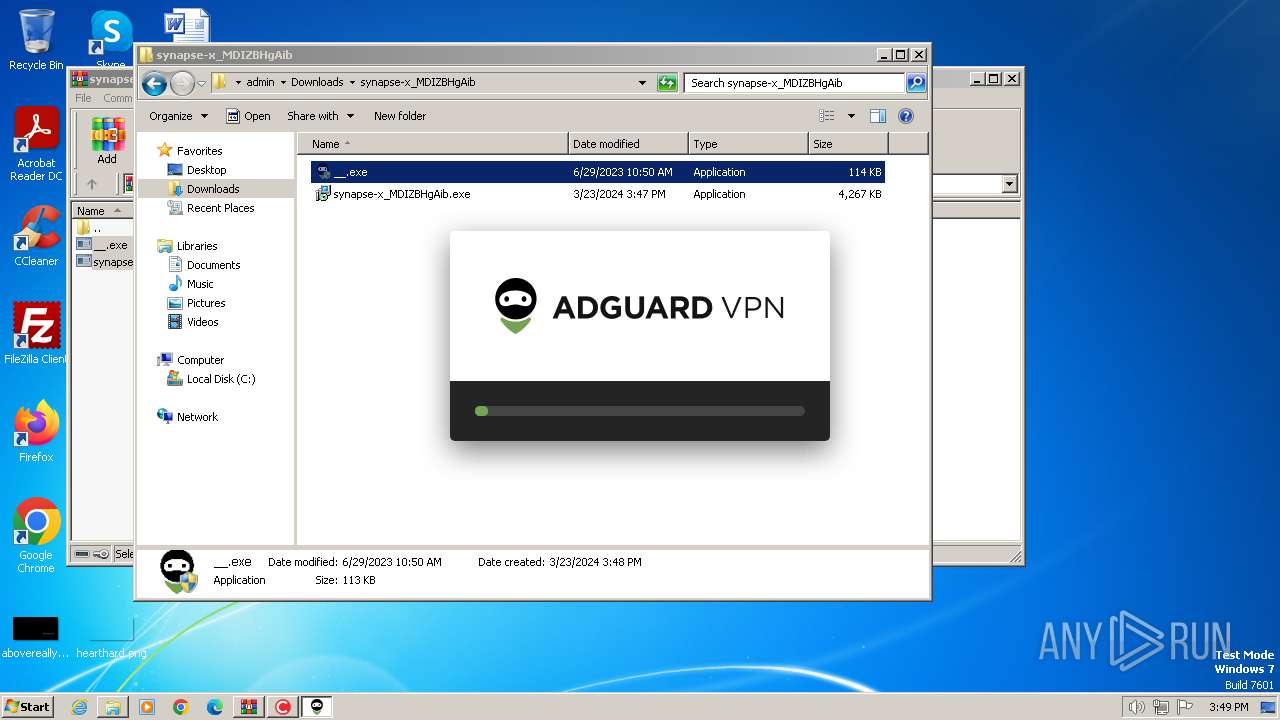
- AdGuardVpnSvc.exe (PID: 2668)
Registers / Runs the DLL via REGSVR32.EXE
- synapse-x_MDIZBHgAib.tmp (PID: 1216)
Changes the autorun value in the registry
- installer.exe (PID: 2788)
- setup.exe (PID: 864)
DOWNLOADASSISTANT has been detected (SURICATA)
- phpdesignerpro.exe (PID: 2760)
[YARA] zgRAT detected by memory dumps
- AdGuardVpn.exe (PID: 2892)
SUSPICIOUS
Executable content was dropped or overwritten
- synapse-x_MDIZBHgAib.exe (PID: 1308)
- synapse-x_MDIZBHgAib.exe (PID: 2584)
- __.exe (PID: 2356)
- setup.exe (PID: 2016)
- setup.exe (PID: 864)
- installer.exe (PID: 2788)
- synapse-x_MDIZBHgAib.tmp (PID: 1216)
- AdGuardVpnSvc.exe (PID: 2668)
Reads the Windows owner or organization settings
- synapse-x_MDIZBHgAib.tmp (PID: 1216)
Process drops legitimate windows executable
- synapse-x_MDIZBHgAib.tmp (PID: 1216)
- setup.exe (PID: 864)
The process drops C-runtime libraries
- synapse-x_MDIZBHgAib.tmp (PID: 1216)
Checks Windows Trust Settings
- __.exe (PID: 2356)
- AdGuardVpnSvc.exe (PID: 2668)
Reads the Internet Settings
- __.exe (PID: 2356)
- setup.exe (PID: 864)
- AdGuardVpn.exe (PID: 2892)
Reads security settings of Internet Explorer
- __.exe (PID: 2356)
- setup.exe (PID: 864)
- AdGuardVpn.exe (PID: 2892)
- AdGuardVpnSvc.exe (PID: 2668)
Adds/modifies Windows certificates
- __.exe (PID: 2356)
- AdGuardVpnSvc.exe (PID: 2668)
The process creates files with name similar to system file names
- setup.exe (PID: 864)
Reads settings of System Certificates
- setup.exe (PID: 864)
- __.exe (PID: 2356)
Process requests binary or script from the Internet
- setup.exe (PID: 864)
Searches for installed software
- setup.exe (PID: 864)
- installer.exe (PID: 2788)
Starts itself from another location
- setup.exe (PID: 864)
Creates a software uninstall entry
- installer.exe (PID: 2788)
Executes as Windows Service
- AdGuardVpnSvc.exe (PID: 2668)
Drops a system driver (possible attempt to evade defenses)
- AdGuardVpnSvc.exe (PID: 2668)
Starts SC.EXE for service management
- setup.exe (PID: 864)
- AdGuardVpnSvc.exe (PID: 2668)
Starts CMD.EXE for commands execution
- AdGuardVpnSvc.exe (PID: 2668)
Process uses IPCONFIG to clear DNS cache
- cmd.exe (PID: 3768)
The process executes via Task Scheduler
- AdGuardVpn.exe (PID: 2892)
INFO
Application launched itself
- chrome.exe (PID: 2124)
Drops the executable file immediately after the start
- chrome.exe (PID: 2080)
- WinRAR.exe (PID: 3356)
Executable content was dropped or overwritten
- chrome.exe (PID: 2080)
- WinRAR.exe (PID: 3356)
Manual execution by a user
- explorer.exe (PID: 3660)
- synapse-x_MDIZBHgAib.exe (PID: 1308)
- __.exe (PID: 2356)
- __.exe (PID: 3728)
Checks supported languages
- synapse-x_MDIZBHgAib.exe (PID: 1308)
- synapse-x_MDIZBHgAib.exe (PID: 2584)
- synapse-x_MDIZBHgAib.tmp (PID: 3912)
- synapse-x_MDIZBHgAib.tmp (PID: 1216)
- phpdesignerpro.exe (PID: 2760)
- __.exe (PID: 2356)
- setup.exe (PID: 864)
- installer.exe (PID: 2788)
- AdGuardVpnSvc.exe (PID: 2668)
- setup.exe (PID: 2016)
- AdGuardVpn.exe (PID: 2892)
The process uses the downloaded file
- chrome.exe (PID: 3156)
- WinRAR.exe (PID: 3356)
Reads the computer name
- synapse-x_MDIZBHgAib.tmp (PID: 3912)
- synapse-x_MDIZBHgAib.tmp (PID: 1216)
- phpdesignerpro.exe (PID: 2760)
- __.exe (PID: 2356)
- setup.exe (PID: 864)
- installer.exe (PID: 2788)
- AdGuardVpnSvc.exe (PID: 2668)
- AdGuardVpn.exe (PID: 2892)
Create files in a temporary directory
- synapse-x_MDIZBHgAib.exe (PID: 2584)
- synapse-x_MDIZBHgAib.tmp (PID: 1216)
- __.exe (PID: 2356)
- setup.exe (PID: 864)
- synapse-x_MDIZBHgAib.exe (PID: 1308)
- installer.exe (PID: 2788)
Creates files or folders in the user directory
- synapse-x_MDIZBHgAib.tmp (PID: 1216)
- __.exe (PID: 2356)
- AdGuardVpn.exe (PID: 2892)
Creates a software uninstall entry
- synapse-x_MDIZBHgAib.tmp (PID: 1216)
Reads the machine GUID from the registry
- phpdesignerpro.exe (PID: 2760)
- __.exe (PID: 2356)
- setup.exe (PID: 864)
- installer.exe (PID: 2788)
- AdGuardVpnSvc.exe (PID: 2668)
- AdGuardVpn.exe (PID: 2892)
Checks proxy server information
- __.exe (PID: 2356)
Reads the software policy settings
- __.exe (PID: 2356)
- setup.exe (PID: 864)
- AdGuardVpnSvc.exe (PID: 2668)
Reads Environment values
- setup.exe (PID: 864)
- AdGuardVpnSvc.exe (PID: 2668)
- AdGuardVpn.exe (PID: 2892)
Creates files in the program directory
- setup.exe (PID: 864)
- installer.exe (PID: 2788)
- AdGuardVpnSvc.exe (PID: 2668)
- AdGuardVpn.exe (PID: 2892)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
122
Monitored processes
51
Malicious processes
11
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 784 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=13 --mojo-platform-channel-handle=3612 --field-trial-handle=1180,i,12250987845429103511,18118916202663290162,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 864 | "C:\Windows\Temp\{7B25C83B-D1EB-4C91-9072-FC77F3BDA082}\.cr\setup.exe" -burn.clean.room="C:\Users\admin\AppData\Local\Temp\adguard\setup.exe" -burn.filehandle.attached=268 -burn.filehandle.self=276 "AID=31220" | C:\Windows\Temp\{7B25C83B-D1EB-4C91-9072-FC77F3BDA082}\.cr\setup.exe | setup.exe | ||||||||||||
User: admin Company: Adguard Software Limited Integrity Level: HIGH Description: AdGuardVPN Exit code: 0 Version: 2.2.1271.0 Modules
| |||||||||||||||
| 952 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3536 --field-trial-handle=1180,i,12250987845429103511,18118916202663290162,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 980 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=23 --mojo-platform-channel-handle=3344 --field-trial-handle=1180,i,12250987845429103511,18118916202663290162,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1216 | "C:\Users\admin\AppData\Local\Temp\is-3B57A.tmp\synapse-x_MDIZBHgAib.tmp" /SL5="$601EC,4085412,56832,C:\Users\admin\Downloads\synapse-x_MDIZBHgAib\synapse-x_MDIZBHgAib.exe" /SPAWNWND=$50238 /NOTIFYWND=$9020C | C:\Users\admin\AppData\Local\Temp\is-3B57A.tmp\synapse-x_MDIZBHgAib.tmp | synapse-x_MDIZBHgAib.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Version: 51.52.0.0 Modules
| |||||||||||||||
| 1308 | "C:\Users\admin\Downloads\synapse-x_MDIZBHgAib\synapse-x_MDIZBHgAib.exe" | C:\Users\admin\Downloads\synapse-x_MDIZBHgAib\synapse-x_MDIZBHgAib.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: PHP Designer Pro Setup Version: Modules
| |||||||||||||||
| 1348 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1360 --field-trial-handle=1180,i,12250987845429103511,18118916202663290162,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1376 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=956 --field-trial-handle=1180,i,12250987845429103511,18118916202663290162,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1584 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=2112 --field-trial-handle=1180,i,12250987845429103511,18118916202663290162,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1732 | schtasks /run /tn f757140c4d1742cfa0d878694bd75de3 | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
38 534
Read events
38 184
Write events
314
Delete events
36
Modification events
| (PID) Process: | (2124) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2124) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2124) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2124) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2124) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2124) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2124) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2124) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2124) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2124) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
110
Suspicious files
136
Text files
109
Unknown types
106
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2124 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF183bdb.TMP | — | |
MD5:— | SHA256:— | |||
| 2124 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2124 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 2124 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:ECD3386BCC950E73B86EB128A5F57622 | SHA256:C9A068EAFBC587EDFC89392F64DDD350EEB96C5CF195CDB030BAB8F6DD33833B | |||
| 2124 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\AutofillStrikeDatabase\LOG.old~RF1851a5.TMP | — | |
MD5:— | SHA256:— | |||
| 2124 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\AutofillStrikeDatabase\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2124 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\metadata\LOG.old | text | |
MD5:4E2B7997F4C3647F8D1ADA88339BBBA5 | SHA256:C33226C460208AA10537A23CB5128FD887DCBAA335C7DC8BFFBE08A607CCFDF5 | |||
| 2124 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF183bfa.TMP | text | |
MD5:05CF4C3C5148DA6355D3561A9EAA5E8A | SHA256:8D720243F6876898E4F197C8867C4CEE69F1C7335C55B8A29C120B1028D93E41 | |||
| 2124 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old~RF18533b.TMP | — | |
MD5:— | SHA256:— | |||
| 2124 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
67
DNS requests
64
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
856 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | binary | 10.3 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | binary | 5.56 Kb | unknown |
856 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYTBmQUFZUHRkSkgtb01uSGNvRHZ2Tm5HQQ/1.0.0.15_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | binary | 7.94 Kb | unknown |
2760 | phpdesignerpro.exe | POST | — | 104.21.74.224:80 | http://soneservice.shop/new/net_api | unknown | — | — | unknown |
856 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad6eob6nunr64xlqs3i7jpbbwlqa_20230923.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230923.567854667.14_all_ENUS500000_ace7f54yxy3vtmc2mjkr5yii7sta.crx3 | unknown | binary | 3.07 Kb | unknown |
856 | svchost.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYTBmQUFZUHRkSkgtb01uSGNvRHZ2Tm5HQQ/1.0.0.15_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | binary | 3.07 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad6eob6nunr64xlqs3i7jpbbwlqa_20230923.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230923.567854667.14_all_ENUS500000_ace7f54yxy3vtmc2mjkr5yii7sta.crx3 | unknown | binary | 75.1 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad6eob6nunr64xlqs3i7jpbbwlqa_20230923.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230923.567854667.14_all_ENUS500000_ace7f54yxy3vtmc2mjkr5yii7sta.crx3 | unknown | binary | 185 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad6eob6nunr64xlqs3i7jpbbwlqa_20230923.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230923.567854667.14_all_ENUS500000_ace7f54yxy3vtmc2mjkr5yii7sta.crx3 | unknown | binary | 1.11 Mb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | unknown |
2124 | chrome.exe | 239.255.255.250:1900 | — | — | — | unknown |
1348 | chrome.exe | 108.177.15.84:443 | accounts.google.com | GOOGLE | US | unknown |
1348 | chrome.exe | 104.21.29.204:443 | cloudaxus.com | CLOUDFLARENET | — | unknown |
1348 | chrome.exe | 172.217.16.196:443 | www.google.com | GOOGLE | US | whitelisted |
2124 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1348 | chrome.exe | 104.16.89.20:443 | cdn.jsdelivr.net | CLOUDFLARENET | — | shared |
1348 | chrome.exe | 88.212.201.204:443 | counter.yadro.ru | United Network LLC | RU | unknown |
1348 | chrome.exe | 172.67.172.237:443 | cloudfileshosgt.ru | CLOUDFLARENET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
cloudaxus.com |
| unknown |
www.google.com |
| whitelisted |
cdn.jsdelivr.net |
| whitelisted |
counter.yadro.ru |
| whitelisted |
cloudfileshosgt.ru |
| unknown |
www.hcaptcha.com |
| whitelisted |
newassets.hcaptcha.com |
| whitelisted |
a.nel.cloudflare.com |
| whitelisted |
content-autofill.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1348 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
1348 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
1348 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
2760 | phpdesignerpro.exe | Misc activity | ADWARE [ANY.RUN] DownloadAssistant |
2240 | rundll32.exe | Misc activity | ET INFO Observed Cloudflare DNS over HTTPS Domain (cloudflare-dns .com in TLS SNI) |
2240 | rundll32.exe | Misc activity | ET INFO Observed Google DNS over HTTPS Domain (dns .google in TLS SNI) |
2240 | rundll32.exe | Misc activity | ET INFO Observed DNS Over HTTPS Domain (dns .alidns .com in TLS SNI) |
2240 | rundll32.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
2668 | AdGuardVpnSvc.exe | Misc activity | ET INFO Observed DNS Over HTTPS Domain (dns .alidns .com in TLS SNI) |
2668 | AdGuardVpnSvc.exe | Misc activity | ET INFO Observed DNS Over HTTPS Domain (dns .alidns .com in TLS SNI) |