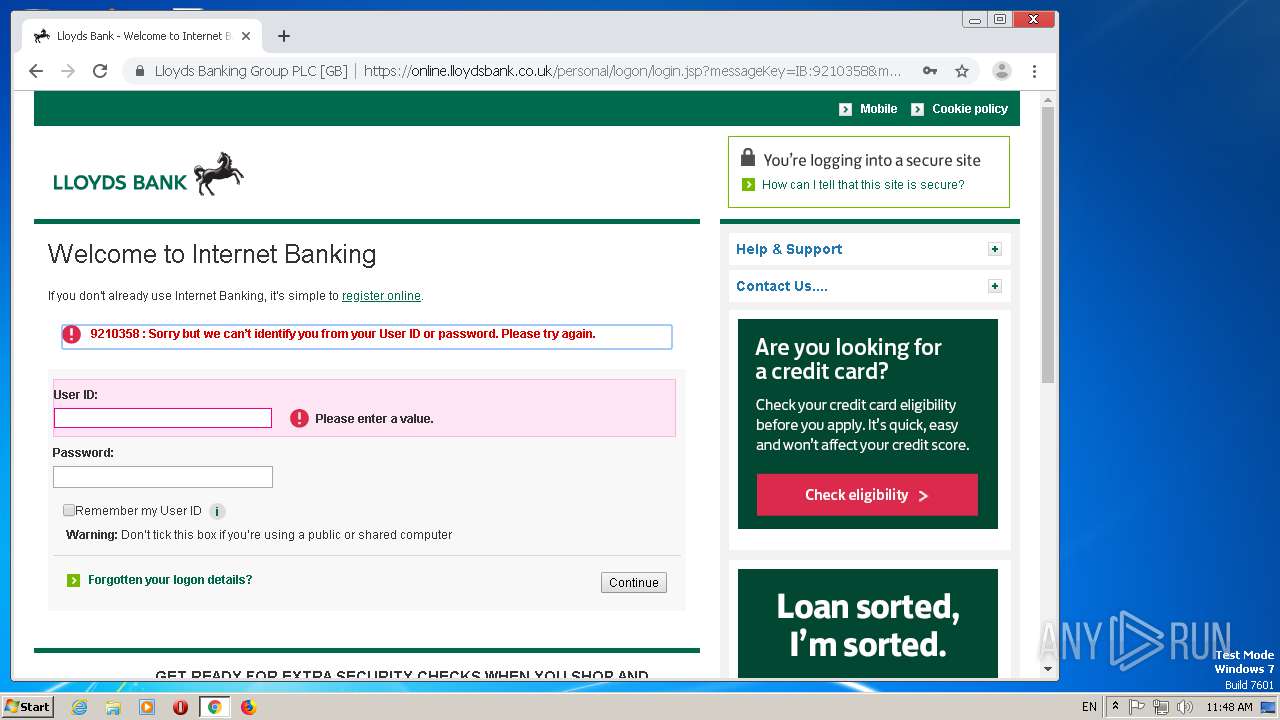
| File name: | Scan-005678207.pdf.exe |
| Full analysis: | https://app.any.run/tasks/738b3e7a-a59c-48cc-9252-425c96efcfea |
| Verdict: | Malicious activity |
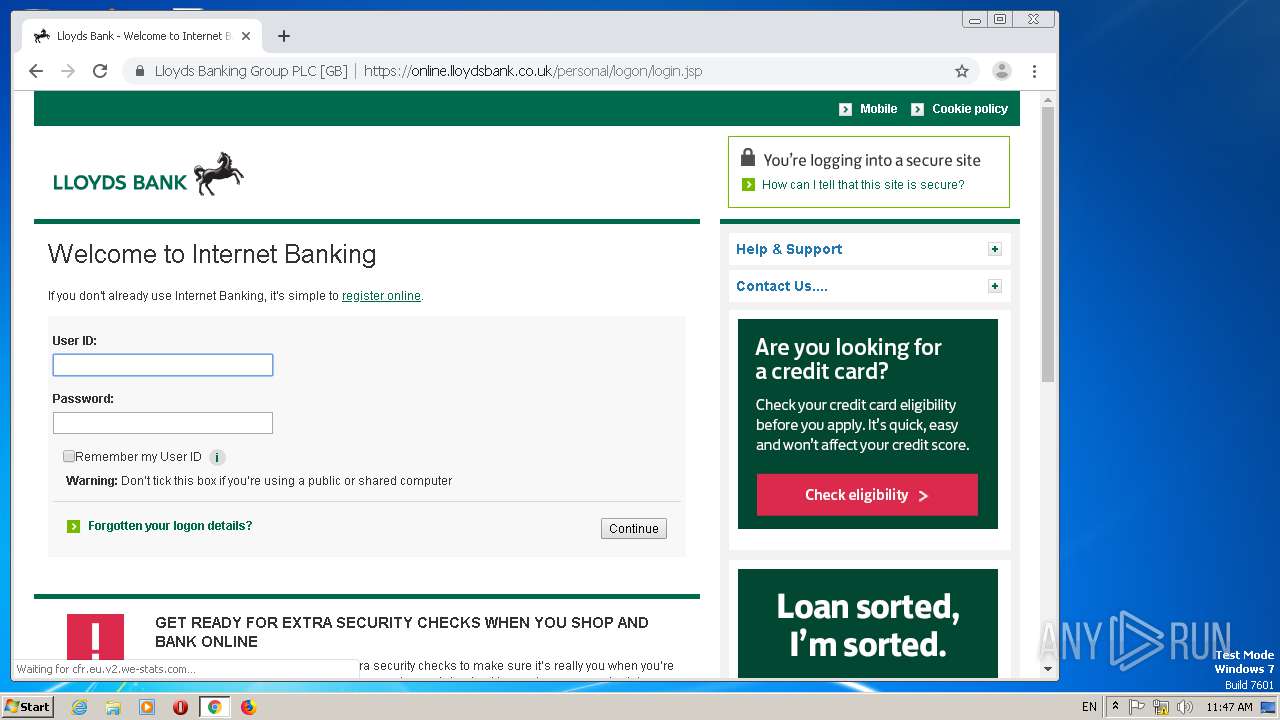
| Threats: | Dridex is a very evasive and technically complex banking trojan. Despite being based on a relatively old malware code, it was substantially updated over the years and became capable of using very effective infiltration techniques that make this malware especially dangerous. |
| Analysis date: | September 19, 2019, 10:45:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | 38856839FBA47E234EA86F3D8F456F0E |
| SHA1: | 4AC1CA93ABC92E1DBCB447C1A3F4C3D8B70A24C3 |
| SHA256: | FD27A4FD9BFE3675A89FF0CEB77F8738A7661EA4FC4644DED554A8DEB66987C2 |
| SSDEEP: | 6144:5IkjQinemPaRNf/wVNLsD7nDc5rwWElkDZG:KmS3fI5GnDoctkDZG |
MALICIOUS
Changes settings of System certificates
- Scan-005678207.pdf.exe (PID: 668)
SUSPICIOUS
Adds / modifies Windows certificates
- Scan-005678207.pdf.exe (PID: 668)
Connects to unusual port
- Scan-005678207.pdf.exe (PID: 668)
INFO
Application launched itself
- chrome.exe (PID: 1616)
Manual execution by user
- chrome.exe (PID: 1616)
Reads the hosts file
- chrome.exe (PID: 1616)
- chrome.exe (PID: 2476)
Reads the machine GUID from the registry
- chrome.exe (PID: 2476)
- chrome.exe (PID: 1616)
- chrome.exe (PID: 1172)
Reads settings of System Certificates
- chrome.exe (PID: 2476)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2002:09:18 01:43:10+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 15.2 |
| CodeSize: | 12288 |
| InitializedDataSize: | 94208 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3380 |
| OSVersion: | 5 |
| ImageVersion: | 5 |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows command line |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_CUI |
| Compilation Date: | 17-Sep-2002 23:43:10 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000C8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 7 |
| Time date stamp: | 17-Sep-2002 23:43:10 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00002CC8 | 0x00003000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.45366 |
.idata | 0x00018000 | 0x000002AA | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.21655 |
.data | 0x00012000 | 0x00005EEA | 0x00006000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 6.30177 |
qeWSV | 0x00019000 | 0x0000F8EB | 0x00010000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.93372 |
qrQym | 0x00029000 | 0x0000042F | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.06365 |
.reloc | 0x0002A000 | 0x000003D8 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 2.11198 |
Imports
KERNEL32.dll |
OLEAUT32.dll |
USER32.dll |
WINSPOOL.DRV |
Total processes
55
Monitored processes
20
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 324 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2096 --on-initialized-event-handle=328 --parent-handle=332 /prefetch:6 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 392 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1000,6558972813084533129,7747103718319202725,131072 --lang=en-US --service-sandbox-type=utility --service-request-channel-token=4366965336803744732 --mojo-platform-channel-handle=3872 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 668 | "C:\Users\admin\Desktop\Scan-005678207.pdf.exe" | C:\Users\admin\Desktop\Scan-005678207.pdf.exe | explorer.exe | ||||||||||||
User: admin Company: Citrix Systems, Inc. Integrity Level: MEDIUM Description: SSOnChecker Exit code: 0 Version: 4.12.0.18016 Modules
| |||||||||||||||
| 1000 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1000,6558972813084533129,7747103718319202725,131072 --lang=en-US --service-sandbox-type=utility --service-request-channel-token=1078919950653692528 --mojo-platform-channel-handle=3612 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1172 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1000,6558972813084533129,7747103718319202725,131072 --lang=en-US --no-sandbox --service-request-channel-token=14285601336163460103 --mojo-platform-channel-handle=924 /prefetch:8 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1580 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1000,6558972813084533129,7747103718319202725,131072 --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7569866685313962988 --renderer-client-id=16 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3936 /prefetch:1 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1616 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1660 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1000,6558972813084533129,7747103718319202725,131072 --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=9769299651948366823 --mojo-platform-channel-handle=1020 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1868 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1000,6558972813084533129,7747103718319202725,131072 --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2200065907145583032 --renderer-client-id=14 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2864 /prefetch:1 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2176 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1000,6558972813084533129,7747103718319202725,131072 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9828579231804156479 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2488 /prefetch:1 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 951
Read events
1 861
Write events
85
Delete events
5
Modification events
| (PID) Process: | (1616) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1616) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1616) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (1616) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1616) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1616) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1616) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (1616) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 1488-13208965925882812 |
Value: 0 | |||
| (PID) Process: | (1616) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (1616) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 1616-13213363654163250 |
Value: 259 | |||
Executable files
0
Suspicious files
87
Text files
100
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1616 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\e87a2380-ed81-4891-b90f-386ccfb7b996.tmp | — | |
MD5:— | SHA256:— | |||
| 1616 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000018.dbtmp | — | |
MD5:— | SHA256:— | |||
| 1616 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1616 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF173066.TMP | text | |
MD5:— | SHA256:— | |||
| 1616 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1616 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1616 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF173066.TMP | text | |
MD5:— | SHA256:— | |||
| 1616 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RF173095.TMP | text | |
MD5:— | SHA256:— | |||
| 1616 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1616 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
51
DNS requests
31
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2476 | chrome.exe | GET | 200 | 35.156.254.208:80 | http://ocsp.quovadisglobal.com/MFUwUzBRME8wTTAJBgUrDgMCGgUABBTyhcKR1A4XhQLFZRt5u%2BT8TDsYdQQUGoRivEhMMyUE1O7Q9gPEGUbRlGsCFHPaWvoj2T%2B6hC4KIPQBydhuJPxd | DE | der | 1.78 Kb | whitelisted |
2476 | chrome.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?cf757251930333ca | US | compressed | 57.0 Kb | whitelisted |
2476 | chrome.exe | GET | 200 | 52.219.73.130:80 | http://trust.quovadisglobal.com/qvrca2.crt | DE | der | 1.43 Kb | shared |
2476 | chrome.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?465c811796dfcbf7 | US | compressed | 6.73 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2476 | chrome.exe | 216.58.207.45:443 | accounts.google.com | Google Inc. | US | whitelisted |
2476 | chrome.exe | 172.217.18.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2476 | chrome.exe | 216.58.205.227:443 | www.google.de | Google Inc. | US | whitelisted |
2476 | chrome.exe | 216.58.207.42:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2476 | chrome.exe | 216.58.206.3:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2476 | chrome.exe | 172.217.18.14:443 | ogs.google.com | Google Inc. | US | whitelisted |
2476 | chrome.exe | 172.217.21.238:443 | apis.google.com | Google Inc. | US | whitelisted |
2476 | chrome.exe | 172.217.21.196:443 | www.google.com | Google Inc. | US | whitelisted |
2476 | chrome.exe | 172.217.16.195:443 | www.google.lt | Google Inc. | US | whitelisted |
2476 | chrome.exe | 172.217.21.227:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.de |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ogs.google.com |
| whitelisted |
www.google.com |
| malicious |
www.google.lt |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
668 | Scan-005678207.pdf.exe | A Network Trojan was detected | ET TROJAN ABUSE.CH SSL Blacklist Malicious SSL certificate detected (Dridex) |
668 | Scan-005678207.pdf.exe | A Network Trojan was detected | MALWARE [PTsecurity] Dridex/Feodo SSL connection |
668 | Scan-005678207.pdf.exe | A Network Trojan was detected | ET TROJAN ABUSE.CH SSL Blacklist Malicious SSL certificate detected (Dridex) |
668 | Scan-005678207.pdf.exe | A Network Trojan was detected | ET TROJAN ABUSE.CH SSL Blacklist Malicious SSL certificate detected (Dridex) |
668 | Scan-005678207.pdf.exe | A Network Trojan was detected | ET TROJAN ABUSE.CH SSL Blacklist Malicious SSL certificate detected (Dridex) |
668 | Scan-005678207.pdf.exe | A Network Trojan was detected | MALWARE [PTsecurity] Dridex/Feodo SSL connection |
Process | Message |
|---|---|
Scan-005678207.pdf.exe | Installing...
|
Scan-005678207.pdf.exe | Installing...
|
Scan-005678207.pdf.exe | Installing...
|
Scan-005678207.pdf.exe | Installing...
|
Scan-005678207.pdf.exe | Installing...
|
Scan-005678207.pdf.exe | Installing...
|
Scan-005678207.pdf.exe | Installing...
|
Scan-005678207.pdf.exe | Installing...
|
Scan-005678207.pdf.exe | Installing...
|
Scan-005678207.pdf.exe | Installing...
|