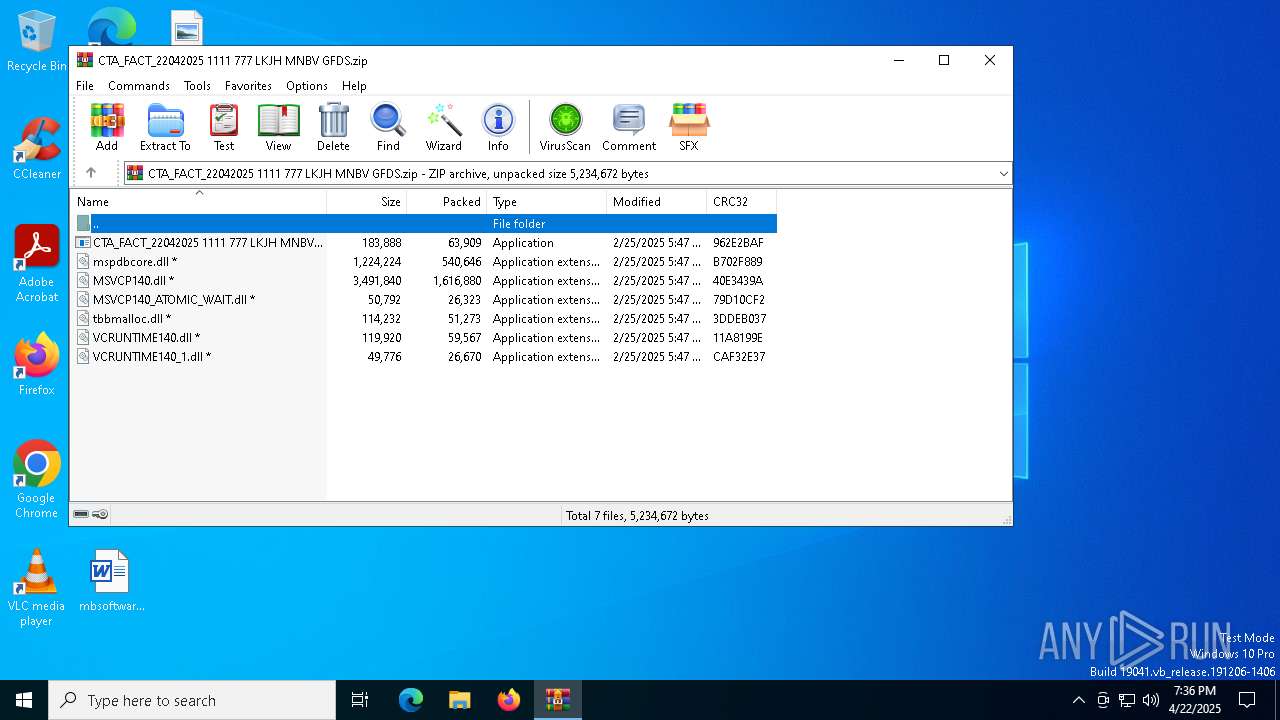
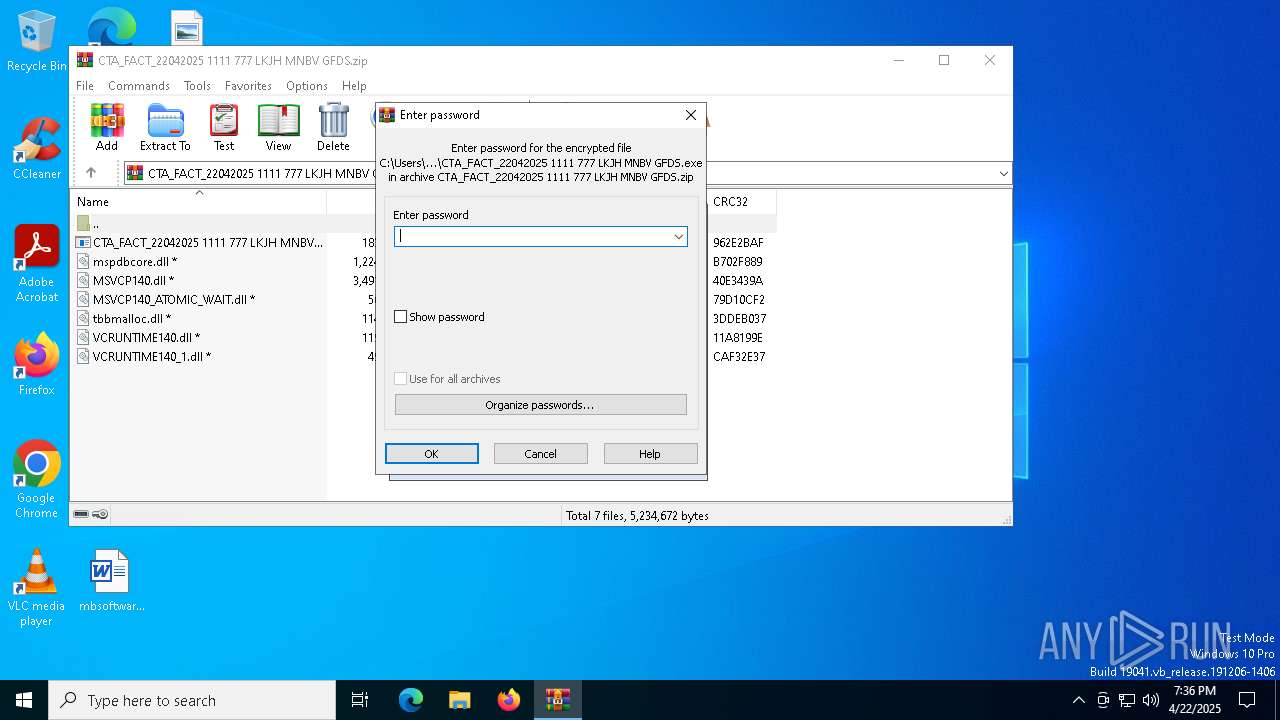
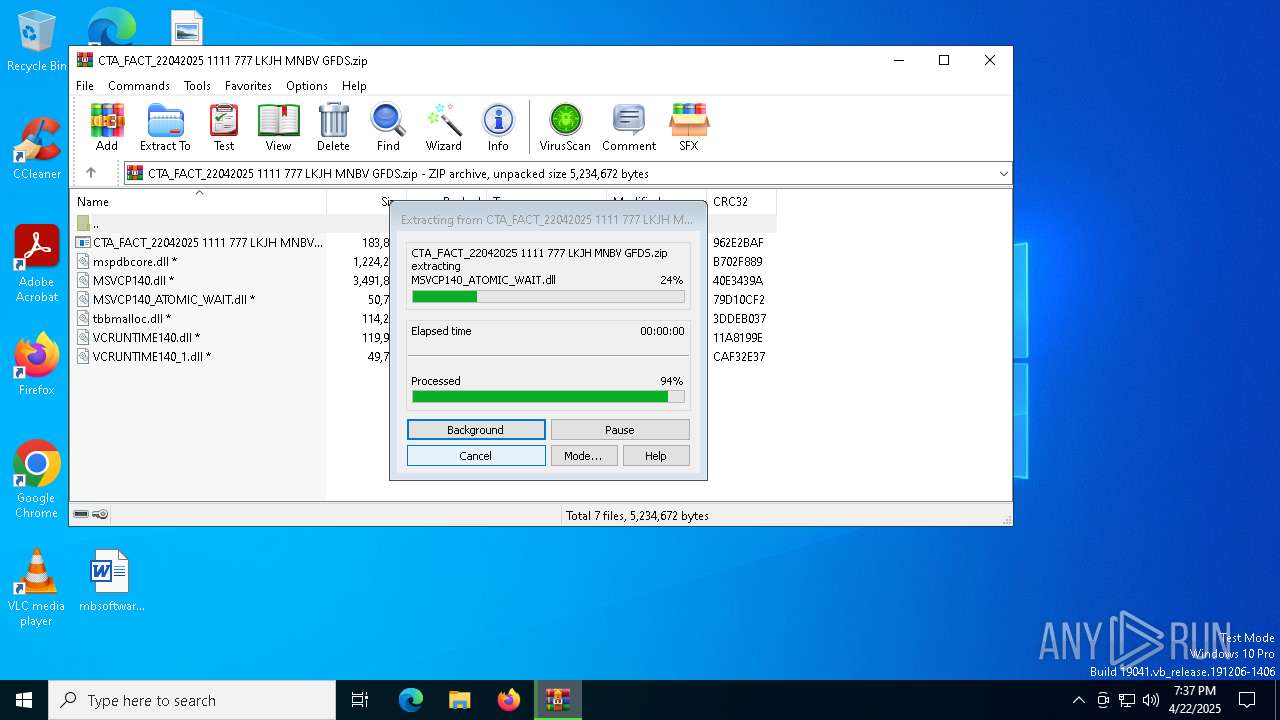
| File name: | CTA_FACT_22042025 1111 777 LKJH MNBV GFDS.zip |
| Full analysis: | https://app.any.run/tasks/4c8cfe1a-ad99-4fe2-a23d-2171ba1f51fc |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | April 22, 2025, 19:36:36 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | CA8B9D54345A5BBC67BE28947556BBA8 |
| SHA1: | 13827EBDD85FFE286661279EA8FF02AFA9492B49 |
| SHA256: | FD0C2B55AAD059AC0258D41800A8A6A2A9C07B14257A542174B0C1867B126038 |
| SSDEEP: | 98304:xv6OyCdmOwqeGlMd7NMSnhKgyWhHjh4i3u0Ib/RT7ubrAx3Zl0RL/eIhNkZCwG5q:rAuqJS |
MALICIOUS
Changes the autorun value in the registry
- CTA_FACT_22042025 1111 777 LKJH MNBV GFDS.exe (PID: 1184)
DCRAT mutex has been found
- AddInProcess32.exe (PID: 4120)
ASYNCRAT has been detected (SURICATA)
- AddInProcess32.exe (PID: 4120)
ASYNCRAT has been detected (YARA)
- AddInProcess32.exe (PID: 4120)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 4560)
- CTA_FACT_22042025 1111 777 LKJH MNBV GFDS.exe (PID: 1184)
Write to the desktop.ini file (may be used to cloak folders)
- CTA_FACT_22042025 1111 777 LKJH MNBV GFDS.exe (PID: 1184)
Starts a Microsoft application from unusual location
- CTA_FACT_22042025 1111 777 LKJH MNBV GFDS.exe (PID: 1184)
Executable content was dropped or overwritten
- CTA_FACT_22042025 1111 777 LKJH MNBV GFDS.exe (PID: 1184)
The process drops C-runtime libraries
- CTA_FACT_22042025 1111 777 LKJH MNBV GFDS.exe (PID: 1184)
Connects to unusual port
- AddInProcess32.exe (PID: 4120)
Contacting a server suspected of hosting an CnC
- AddInProcess32.exe (PID: 4120)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4560)
Checks supported languages
- CTA_FACT_22042025 1111 777 LKJH MNBV GFDS.exe (PID: 1184)
- AddInProcess32.exe (PID: 4120)
The sample compiled with english language support
- CTA_FACT_22042025 1111 777 LKJH MNBV GFDS.exe (PID: 1184)
- WinRAR.exe (PID: 4560)
Manual execution by a user
- CTA_FACT_22042025 1111 777 LKJH MNBV GFDS.exe (PID: 1184)
Reads the computer name
- AddInProcess32.exe (PID: 4120)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 6040)
- OpenWith.exe (PID: 6592)
- OpenWith.exe (PID: 5328)
Reads the machine GUID from the registry
- AddInProcess32.exe (PID: 4120)
Reads the software policy settings
- AddInProcess32.exe (PID: 4120)
- slui.exe (PID: 5084)
- slui.exe (PID: 2096)
Checks proxy server information
- slui.exe (PID: 5084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(4120) AddInProcess32.exe
C2 (1)176.65.144.19
Ports (1)8848
Version1.0.7
Options
AutoRunfalse
MutexDcRatMutex_qwqdanchun
InstallFolder%AppData%
Certificates
Cert1MIICMDCCAZmgAwIBAgIVAJdJTOcvv+RE0UKkRJdxy6sUSIJ9MA0GCSqGSIb3DQEBDQUAMGQxFTATBgNVBAMMDERjUmF0IFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEcMBoGA1UECgwTRGNSYXQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTI0MDYyNjE0MzcyN1oXDTM1MDQwNTE0MzcyN1owEDEOMAwGA1UEAwwFRGNSYXQwgZ8wDQYJKoZIhvcNAQEBBQADgY0A...
Server_SignatureWx3JA6Bp9lQ8a21ITT2Yf7QtTZhVXQKXKNqdrmnSpJpNWw196WRqSRvXpfHx4gBSz0xQh/uE4uACTMLMbOUbGKDz0F3RU+cVl9U26/MzJauCM4UBDdiDAyVlw7dEoQV4vkxMgAqd0kTMWhYz/3TnSu7mGAIh36l9PisuHty9TXk=
Keys
AES4604c385e80480152eb162e857331ecd057b39947bcce94baed9e2c3458c51b3
SaltDcRatByqwqdanchun
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:02:25 00:47:52 |
| ZipCRC: | 0x962e2baf |
| ZipCompressedSize: | 63909 |
| ZipUncompressedSize: | 183888 |
| ZipFileName: | CTA_FACT_22042025 1111 777 LKJH MNBV GFDS.exe |
Total processes
141
Monitored processes
10
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1184 | "C:\Users\admin\Desktop\CTA_FACT_22042025 1111 777 LKJH MNBV GFDS.exe" | C:\Users\admin\Desktop\CTA_FACT_22042025 1111 777 LKJH MNBV GFDS.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Program Database Exit code: 0 Version: 14.40.33819.0 Modules
| |||||||||||||||
| 1672 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2096 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4120 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe | CTA_FACT_22042025 1111 777 LKJH MNBV GFDS.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: AddInProcess.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
AsyncRat(PID) Process(4120) AddInProcess32.exe C2 (1)176.65.144.19 Ports (1)8848 Version1.0.7 Options AutoRunfalse MutexDcRatMutex_qwqdanchun InstallFolder%AppData% Certificates Cert1MIICMDCCAZmgAwIBAgIVAJdJTOcvv+RE0UKkRJdxy6sUSIJ9MA0GCSqGSIb3DQEBDQUAMGQxFTATBgNVBAMMDERjUmF0IFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEcMBoGA1UECgwTRGNSYXQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTI0MDYyNjE0MzcyN1oXDTM1MDQwNTE0MzcyN1owEDEOMAwGA1UEAwwFRGNSYXQwgZ8wDQYJKoZIhvcNAQEBBQADgY0A... Server_SignatureWx3JA6Bp9lQ8a21ITT2Yf7QtTZhVXQKXKNqdrmnSpJpNWw196WRqSRvXpfHx4gBSz0xQh/uE4uACTMLMbOUbGKDz0F3RU+cVl9U26/MzJauCM4UBDdiDAyVlw7dEoQV4vkxMgAqd0kTMWhYz/3TnSu7mGAIh36l9PisuHty9TXk= Keys AES4604c385e80480152eb162e857331ecd057b39947bcce94baed9e2c3458c51b3 SaltDcRatByqwqdanchun | |||||||||||||||
| 4560 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\CTA_FACT_22042025 1111 777 LKJH MNBV GFDS.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5084 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5328 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6040 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6592 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6816 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | CTA_FACT_22042025 1111 777 LKJH MNBV GFDS.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 124
Read events
8 094
Write events
17
Delete events
13
Modification events
| (PID) Process: | (4560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\CTA_FACT_22042025 1111 777 LKJH MNBV GFDS.zip | |||
| (PID) Process: | (4560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (4560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
14
Suspicious files
3
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4560 | WinRAR.exe | C:\Users\admin\Desktop\tbbmalloc.dll | executable | |
MD5:32EBE3A562D2663F78953A0CFBAA4C58 | SHA256:86415AE0E92DDEB1D4BBC094D7D8A72D047282629DEE982A28D6F89E343CF718 | |||
| 4560 | WinRAR.exe | C:\Users\admin\Desktop\mspdbcore.dll | executable | |
MD5:D4344D28980951AAF07598E59818C805 | SHA256:E4CDD42FF68AC4993D8790BED78206BFEA795F698FA8AF8AA0A18199F2F6ABE6 | |||
| 4560 | WinRAR.exe | C:\Users\admin\Desktop\MSVCP140_ATOMIC_WAIT.dll | executable | |
MD5:9362B9E34890378404FDE12AD8CEAFEC | SHA256:793EADD10CA8AA264A11936FD312558B42966C5A211CCF0AA51A03E0060AF8CE | |||
| 4560 | WinRAR.exe | C:\Users\admin\Desktop\VCRUNTIME140_1.dll | executable | |
MD5:83111A77BD2F4BAC4F19D2ADB751D301 | SHA256:5DB3EA3F9B2196145411995FD4461B670D497043A7E29DF797EAED8020E58588 | |||
| 4560 | WinRAR.exe | C:\Users\admin\Desktop\CTA_FACT_22042025 1111 777 LKJH MNBV GFDS.exe | executable | |
MD5:5CFED6E570F577D9055E4007C94C88AE | SHA256:8FB83BE3FBA9675177176D224328A13C03A40413EB041EEC07004033DE714A5B | |||
| 1184 | CTA_FACT_22042025 1111 777 LKJH MNBV GFDS.exe | C:\Users\admin\SystemRootDoc\statustrying.png | binary | |
MD5:0ED43523BE41F55C53E72F378F2BA985 | SHA256:A3BCC69481A84AA9A9614251E4F9DF1495E8C93CF64640613C1F4F4B8AB6A15D | |||
| 1184 | CTA_FACT_22042025 1111 777 LKJH MNBV GFDS.exe | C:\Users\admin\SystemRootDoc\desktop.ini | text | |
MD5:9E36CC3537EE9EE1E3B10FA4E761045B | SHA256:4B9D687AC625690FD026ED4B236DAD1CAC90EF69E7AD256CC42766A065B50026 | |||
| 1184 | CTA_FACT_22042025 1111 777 LKJH MNBV GFDS.exe | C:\Users\admin\SystemRootDoc\mbsoftware.rtf | text | |
MD5:9E9A8D4BAD7669923A9856A26D3DE1D5 | SHA256:63D923F9F295B93F9B9AFABA266CD3CB96738F54F0BBC169DFAD0472D1AFB569 | |||
| 1184 | CTA_FACT_22042025 1111 777 LKJH MNBV GFDS.exe | C:\Users\admin\SystemRootDoc\dictionaryfew.rtf | text | |
MD5:6ED09276CCFF8334F549B350098EC870 | SHA256:2EDD43A18C85D90C2C3D03EF94C71E6BFC31A725C9F461B58D3BB5C11E8E89E4 | |||
| 1184 | CTA_FACT_22042025 1111 777 LKJH MNBV GFDS.exe | C:\Users\admin\SystemRootDoc\stringcritical.rtf | text | |
MD5:DF0AD3BA7C22C97E0D7535A750310EAA | SHA256:3857E0C17CF10804F57512B857954E959F3E8C3C256B74B85FBE654A4BF160C8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
26
DNS requests
17
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6392 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6392 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4120 | AddInProcess32.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
4120 | AddInProcess32.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 30 |
4120 | AddInProcess32.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (AsyncRAT) |
4120 | AddInProcess32.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |