| File name: | setup.exe |
| Full analysis: | https://app.any.run/tasks/ede70688-f57a-4bcf-bd23-54a08ba57a47 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | April 01, 2023, 01:29:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 3B9C6A8C6DD4A1B0DD359AD37EEE5EE1 |
| SHA1: | B0F89579235F8CFBE3614B972BC73971146A7996 |
| SHA256: | FCBB0A893857EF1A65ED50F65D9D21505AEEC595AAB6695B417BB3665E1797ED |
| SSDEEP: | 3072:GDpyyC9KAnpNhz6Qcba2Hv9U5wTOF/9Oej5gFFch:vJKYhzQlP956Doa |
MALICIOUS
Application was injected by another process
- explorer.exe (PID: 1960)
Runs injected code in another process
- setup.exe (PID: 2484)
SMOKE was detected
- explorer.exe (PID: 1960)
Connects to the CnC server
- explorer.exe (PID: 1960)
- nbveek.exe (PID: 2068)
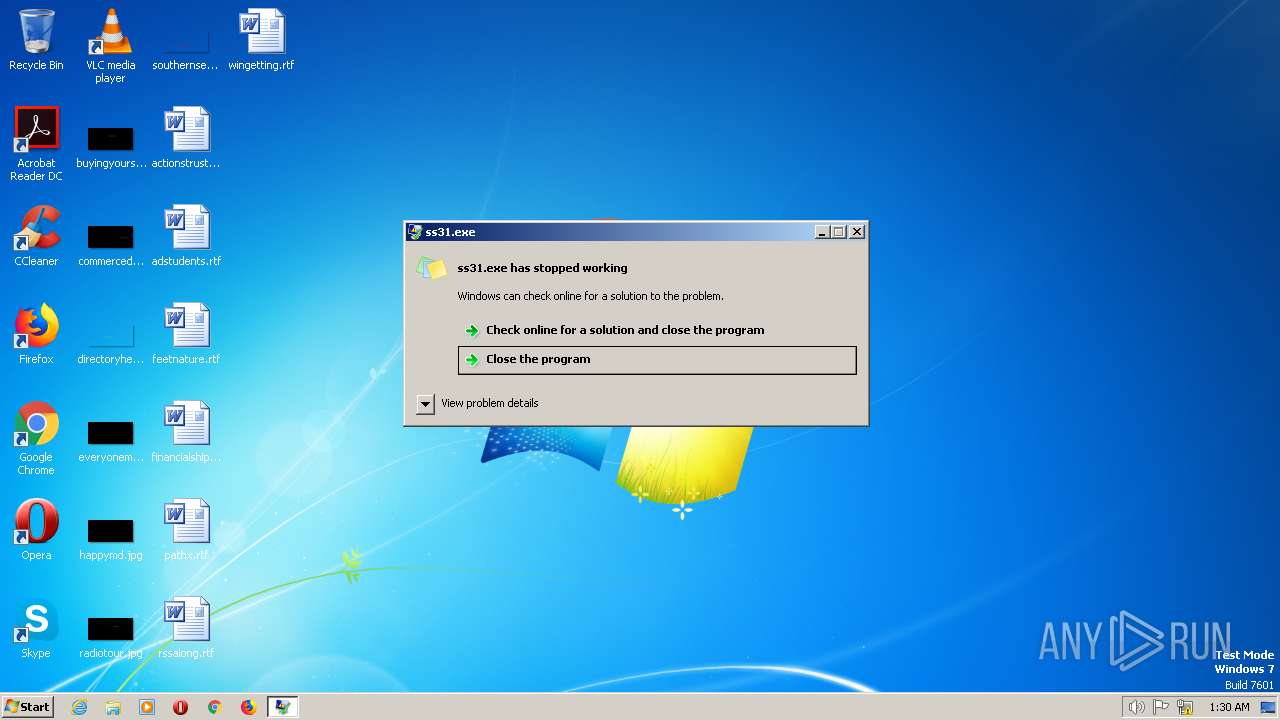
- ss31.exe (PID: 1672)
Application was dropped or rewritten from another process
- nbveek.exe (PID: 2068)
- 5F96.exe (PID: 2088)
- Player3.exe (PID: 2664)
- ss31.exe (PID: 1672)
- XandETC.exe (PID: 2480)
- XandETC.exe (PID: 1928)
- nbveek.exe (PID: 936)
- updater.exe (PID: 2568)
Changes the autorun value in the registry
- nbveek.exe (PID: 2068)
Uses Task Scheduler to run other applications
- nbveek.exe (PID: 2068)
- powershell.exe (PID: 2924)
AMADEY was detected
- nbveek.exe (PID: 2068)
Actions looks like stealing of personal data
- ss31.exe (PID: 1672)
- rundll32.exe (PID: 2276)
AMADEY detected by memory dumps
- nbveek.exe (PID: 2068)
Adds path to the Windows Defender exclusion list
- explorer.exe (PID: 1960)
Uses Task Scheduler to autorun other applications
- powershell.exe (PID: 2468)
- powershell.exe (PID: 2056)
Creates a writable file the system directory
- powershell.exe (PID: 2780)
SUSPICIOUS
Reads the Internet Settings
- 5F96.exe (PID: 2088)
- explorer.exe (PID: 1960)
- Player3.exe (PID: 2664)
- ss31.exe (PID: 1672)
- nbveek.exe (PID: 2068)
- powershell.exe (PID: 2900)
Executable content was dropped or overwritten
- explorer.exe (PID: 1960)
- 5F96.exe (PID: 2088)
- Player3.exe (PID: 2664)
- XandETC.exe (PID: 1928)
- nbveek.exe (PID: 2068)
- updater.exe (PID: 2568)
Starts itself from another location
- Player3.exe (PID: 2664)
Starts CMD.EXE for commands execution
- nbveek.exe (PID: 2068)
- cmd.exe (PID: 2320)
- explorer.exe (PID: 1960)
- updater.exe (PID: 2568)
Application launched itself
- cmd.exe (PID: 2320)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 2320)
Reads settings of System Certificates
- ss31.exe (PID: 1672)
- conhost.exe (PID: 2972)
Connects to the server without a host name
- nbveek.exe (PID: 2068)
Starts POWERSHELL.EXE for commands execution
- explorer.exe (PID: 1960)
- XandETC.exe (PID: 1928)
Uses REG/REGEDIT.EXE to modify register
- cmd.exe (PID: 2572)
- cmd.exe (PID: 2364)
Uses powercfg.exe to modify the power settings
- cmd.exe (PID: 2604)
- cmd.exe (PID: 1764)
Starts SC.EXE for service management
- cmd.exe (PID: 2572)
- cmd.exe (PID: 2364)
The process checks if current user has admin rights
- explorer.exe (PID: 1960)
- XandETC.exe (PID: 1928)
The process executes via Task Scheduler
- updater.exe (PID: 2568)
- nbveek.exe (PID: 936)
Process requests binary or script from the Internet
- nbveek.exe (PID: 2068)
Uses RUNDLL32.EXE to load library
- rundll32.exe (PID: 2216)
Loads DLL from Mozilla Firefox
- rundll32.exe (PID: 2276)
Drops a system driver (possible attempt to evade defenses)
- updater.exe (PID: 2568)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 548)
Unusual connection from system programs
- powershell.exe (PID: 2780)
Connects to unusual port
- conhost.exe (PID: 2972)
INFO
Checks supported languages
- setup.exe (PID: 2484)
- 5F96.exe (PID: 2088)
- ss31.exe (PID: 1672)
- Player3.exe (PID: 2664)
- nbveek.exe (PID: 2068)
- XandETC.exe (PID: 1928)
- updater.exe (PID: 2568)
- nbveek.exe (PID: 936)
Creates files or folders in the user directory
- explorer.exe (PID: 1960)
- ss31.exe (PID: 1672)
- nbveek.exe (PID: 2068)
The process checks LSA protection
- explorer.exe (PID: 1960)
- 5F96.exe (PID: 2088)
- Player3.exe (PID: 2664)
- ss31.exe (PID: 1672)
- nbveek.exe (PID: 2068)
- powershell.exe (PID: 2900)
- powershell.exe (PID: 2468)
- powershell.exe (PID: 2924)
- powershell.exe (PID: 2780)
- powershell.exe (PID: 2056)
- WMIC.exe (PID: 3056)
- conhost.exe (PID: 2972)
Create files in a temporary directory
- explorer.exe (PID: 1960)
- Player3.exe (PID: 2664)
- 5F96.exe (PID: 2088)
- nbveek.exe (PID: 2068)
- powershell.exe (PID: 2900)
- powershell.exe (PID: 2468)
- powershell.exe (PID: 2924)
Reads the computer name
- 5F96.exe (PID: 2088)
- ss31.exe (PID: 1672)
- Player3.exe (PID: 2664)
- nbveek.exe (PID: 2068)
Checks proxy server information
- ss31.exe (PID: 1672)
- nbveek.exe (PID: 2068)
Reads the machine GUID from the registry
- ss31.exe (PID: 1672)
- nbveek.exe (PID: 2068)
Reads settings of System Certificates
- powershell.exe (PID: 2900)
- powershell.exe (PID: 2780)
Reads security settings of Internet Explorer
- powershell.exe (PID: 2468)
- powershell.exe (PID: 2924)
- powershell.exe (PID: 2900)
Creates files in the program directory
- XandETC.exe (PID: 1928)
- updater.exe (PID: 2568)
- cmd.exe (PID: 548)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(2068) nbveek.exe
C2 (1)http://77.73.134.27
Version3.65
Options
Drop directory16de06bfb4
Drop namenbveek.exe
Strings (116)SCHTASKS
/Create /SC MINUTE /MO 1 /TN
/TR "
" /F
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
Startup
Rem
cmd /C RMDIR /s/q
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
rundll32
/Delete /TN "
Programs
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
%USERPROFILE%
\App
POST
GET
id=
&vs=
&sd=
&os=
&bi=
&ar=
&pc=
&un=
&dm=
&av=
&lv=
&og=
cred.dll|clip.dll|
d1
e1
e0
Main
http://
https://
exe
dll
cmd
ps1
<c>
<d>
Plugins/
+++
#
|
&unit=
=
shell32.dll
kernel32.dll
GetNativeSystemInfo
ProgramData\
AVAST Software
Avira
Kaspersky Lab
ESET
Panda Security
Doctor Web
AVG
360TotalSecurity
Bitdefender
Norton
Sophos
Comodo
WinDefender
0123456789
rb
wb
Content-Type: multipart/form-data; boundary=----
------
Content-Disposition: form-data; name="data"; filename="
"
Content-Type: application/octet-stream
------
--
?scr=1
.jpg
Content-Type: application/x-www-form-urlencoded
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
ComputerName
abcdefghijklmnopqrstuvwxyz0123456789-_
-unicode-
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
SYSTEM\ControlSet001\Services\BasicDisplay\Video
VideoID
\0000
DefaultSettings.XResolution
DefaultSettings.YResolution
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
2019
2022
2016
CurrentBuild
&&
echo Y|CACLS "
" /P "
:N"
CACLS "
" /P "
:R" /E
:F" /E
&&Exit
..\
\
:::
rundll32.exe
/k
"taskkill /f /im "
" && timeout 1 && del
&& Exit"
" && ren
&&
Powershell.exe
-executionpolicy remotesigned -File "
"
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| ProductName: | Imba |
|---|---|
| LegalCopyright: | Copyright (C) 2023, shmaer |
| InternalName: | GodGuest |
| FilesVersion: | 19.62.99 |
| CharacterSet: | Unknown (01F2) |
| LanguageCode: | Manipuri |
| FileSubtype: | - |
| ObjectFileType: | Unknown |
| FileOS: | Unknown (0x20461) |
| FileFlags: | (none) |
| FileFlagsMask: | 0x121a |
| ProductVersionNumber: | 26.0.0.0 |
| FileVersionNumber: | 2.0.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 5 |
| ImageVersion: | - |
| OSVersion: | 5 |
| EntryPoint: | 0x6160 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 494592 |
| CodeSize: | 172032 |
| LinkerVersion: | 9 |
| PEType: | PE32 |
| ImageFileCharacteristics: | Executable, 32-bit |
| TimeStamp: | 2022:03:06 15:54:45+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 06-Mar-2022 15:54:45 |
| Detected languages: |
|
| Debug artifacts: |
|
| FilesVersion: | 19.62.99 |
| InternalName: | GodGuest |
| LegalCopyright: | Copyright (C) 2023, shmaer |
| ProductName: | Imba |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 06-Mar-2022 15:54:45 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00029EA2 | 0x0002A000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.53761 |
.data | 0x0002B000 | 0x0006F69C | 0x00003000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.22325 |
.rsrc | 0x0009B000 | 0x000070C8 | 0x00007200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.63378 |
.reloc | 0x000A3000 | 0x00002158 | 0x00002200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 3.89961 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.34304 | 460 | UNKNOWN | UNKNOWN | RT_VERSION |
2 | 4.89752 | 2216 | UNKNOWN | Spanish - Mexico | RT_ICON |
3 | 4.72258 | 1736 | UNKNOWN | Spanish - Mexico | RT_ICON |
4 | 4.26743 | 1384 | UNKNOWN | Spanish - Mexico | RT_ICON |
5 | 3.67549 | 9640 | UNKNOWN | Spanish - Mexico | RT_ICON |
6 | 3.7424 | 4264 | UNKNOWN | Spanish - Mexico | RT_ICON |
7 | 3.79506 | 2440 | UNKNOWN | Spanish - Mexico | RT_ICON |
8 | 3.88036 | 1128 | UNKNOWN | Spanish - Mexico | RT_ICON |
22 | 3.13936 | 412 | UNKNOWN | UNKNOWN | RT_STRING |
23 | 3.22078 | 620 | UNKNOWN | UNKNOWN | RT_STRING |
Imports
ADVAPI32.dll |
GDI32.dll |
KERNEL32.dll |
USER32.dll |
ole32.dll |
Total processes
123
Monitored processes
67
Malicious processes
13
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | CACLS "..\16de06bfb4" /P "admin:N" | C:\Windows\SysWOW64\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Control ACLs Program Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 548 | C:\Windows\System32\cmd.exe /c wmic PATH Win32_VideoController GET Name, VideoProcessor > "C:\Program Files\Google\Libs\g.log" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 564 | reg delete "HKLM\SYSTEM\CurrentControlSet\Services\wuauserv" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 600 | reg delete "HKLM\SYSTEM\CurrentControlSet\Services\bits" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 700 | "C:\Windows\System32\schtasks.exe" /Create /SC MINUTE /MO 1 /TN nbveek.exe /TR "C:\Users\admin\AppData\Local\Temp\16de06bfb4\nbveek.exe" /F | C:\Windows\SysWOW64\schtasks.exe | — | nbveek.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 936 | C:\Users\admin\AppData\Local\Temp\16de06bfb4\nbveek.exe | C:\Users\admin\AppData\Local\Temp\16de06bfb4\nbveek.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1032 | powercfg /x -standby-timeout-ac 0 | C:\Windows\System32\powercfg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Power Settings Command-Line Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1252 | "C:\Users\admin\AppData\Local\Temp\setup.exe" | C:\Users\admin\AppData\Local\Temp\setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1332 | sc stop UsoSvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1356 | sc stop dosvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
15 966
Read events
15 720
Write events
232
Delete events
14
Modification events
| (PID) Process: | (1960) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB0100000040131FD0E0B45449B5325CF35709B45A0000000002000000000010660000000100002000000097BA847E5D0827CAFBC4D33F7B8AFE8834428DFEF065FA018D8CAB90C5710B0A000000000E8000000002000020000000703BDF28CF4D9DFCAB7DDC229F11B838657F02A563D675B7BA5A582848A73F4F300000008091631BBFD318C1A67DDE62193EF5F65F823DF6F3FB12C344A857963FC714699639A04F9F66927C69CA8E9AC61E02154000000007CED62AF9113E09870DE72EB5744E2CBFDC316C2CF8607885EA5CBB68D61BE0CFB49EE1C4CAF8F2769692B62252F8AB0F88C1F92875F93F72FE70BCC896EFE4 | |||
| (PID) Process: | (2088) 5F96.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2088) 5F96.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2088) 5F96.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2088) 5F96.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1672) ss31.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1672) ss31.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000008B000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1672) ss31.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1672) ss31.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1672) ss31.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
28
Suspicious files
22
Text files
6
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2088 | 5F96.exe | C:\Users\admin\AppData\Local\Temp\Player3.exe | executable | |
MD5:— | SHA256:— | |||
| 1960 | explorer.exe | C:\Users\admin\AppData\Roaming\jbhtujv | executable | |
MD5:— | SHA256:— | |||
| 2088 | 5F96.exe | C:\Users\admin\AppData\Local\Temp\ss31.exe | executable | |
MD5:— | SHA256:— | |||
| 1960 | explorer.exe | C:\Users\admin\AppData\Local\Temp\5F96.exe | executable | |
MD5:— | SHA256:— | |||
| 2068 | nbveek.exe | C:\Users\admin\AppData\Local\Temp\896776584425 | image | |
MD5:— | SHA256:— | |||
| 2664 | Player3.exe | C:\Users\admin\AppData\Local\Temp\16de06bfb4\nbveek.exe | executable | |
MD5:— | SHA256:— | |||
| 2068 | nbveek.exe | C:\Users\admin\AppData\Roaming\07c6bc37dc5087\clip64.dll | executable | |
MD5:— | SHA256:— | |||
| 2088 | 5F96.exe | C:\Users\admin\AppData\Local\Temp\XandETC.exe | executable | |
MD5:3006B49F3A30A80BB85074C279ACC7DF | SHA256:F283B4C0AD4A902E1CB64201742CA4C5118F275E7B911A7DAFDA1EF01B825280 | |||
| 2468 | powershell.exe | C:\Users\admin\AppData\Local\Temp\4t5o1wug.5e2.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2900 | powershell.exe | C:\Users\admin\AppData\Local\Temp\j4plwoxi.4j2.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
10
DNS requests
8
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2780 | powershell.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?dd6850b0ae03608c | US | — | — | whitelisted |
1960 | explorer.exe | POST | 404 | 188.114.97.3:80 | http://potunulit.org/ | US | binary | 4.37 Mb | malicious |
2068 | nbveek.exe | POST | 200 | 77.73.134.27:80 | http://77.73.134.27/8bmdh3Slb2/index.php?scr=1 | KZ | — | — | malicious |
2068 | nbveek.exe | GET | 200 | 77.73.134.27:80 | http://77.73.134.27/8bmdh3Slb2/Plugins/cred64.dll | KZ | executable | 1.02 Mb | malicious |
— | — | GET | 200 | 154.221.31.191:80 | http://count.iiagjaggg.com/check/safe | HK | text | 96 b | malicious |
2068 | nbveek.exe | GET | 200 | 77.73.134.27:80 | http://77.73.134.27/8bmdh3Slb2/Plugins/clip64.dll | KZ | executable | 89.0 Kb | malicious |
1672 | ss31.exe | GET | 200 | 45.66.158.126:80 | http://bz.bbbeioaag.com/sts/bimage.jpg | US | image | 1.45 Mb | malicious |
2068 | nbveek.exe | POST | 200 | 77.73.134.27:80 | http://77.73.134.27/8bmdh3Slb2/index.php | KZ | text | 6 b | malicious |
1960 | explorer.exe | POST | 404 | 188.114.97.3:80 | http://potunulit.org/ | US | binary | 7 b | malicious |
1960 | explorer.exe | POST | 404 | 188.114.97.3:80 | http://potunulit.org/ | US | html | 401 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1960 | explorer.exe | 188.114.97.3:80 | potunulit.org | CLOUDFLARENET | NL | malicious |
1672 | ss31.exe | 45.66.158.126:80 | bz.bbbeioaag.com | ENZUINC | US | suspicious |
2068 | nbveek.exe | 77.73.134.27:80 | — | Partner LLC | KZ | malicious |
1672 | ss31.exe | 157.240.20.35:443 | www.facebook.com | FACEBOOK | DE | whitelisted |
1672 | ss31.exe | 154.221.31.191:80 | count.iiagjaggg.com | YISU CLOUD LTD | HK | malicious |
2972 | conhost.exe | 172.67.34.170:443 | pastebin.com | CLOUDFLARENET | US | malicious |
2972 | conhost.exe | 51.15.69.136:14433 | xmr-eu1.nanopool.org | Online S.a.s. | NL | malicious |
2780 | powershell.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2972 | conhost.exe | 152.228.216.245:14433 | xmr-eu2.nanopool.org | OVH SAS | FR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
potunulit.org |
| malicious |
bz.bbbeioaag.com |
| malicious |
www.facebook.com |
| whitelisted |
count.iiagjaggg.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
xmr-eu2.nanopool.org |
| unknown |
pastebin.com |
| malicious |
xmr-eu1.nanopool.org |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1960 | explorer.exe | A Network Trojan was detected | ET MALWARE Suspected Smokeloader Activity (POST) |
1960 | explorer.exe | A Network Trojan was detected | ET MALWARE Suspected Smokeloader Activity (POST) |
1960 | explorer.exe | A Network Trojan was detected | ET MALWARE Suspected Smokeloader Activity (POST) |
1672 | ss31.exe | A Network Trojan was detected | AV INFO Suspicious UA HTTPREAD |
2068 | nbveek.exe | A Network Trojan was detected | AV TROJAN Agent.DHOA System Info Exfiltration |
2068 | nbveek.exe | Unknown Classtype | ET MALWARE Amadey CnC Check-In |
2068 | nbveek.exe | A Network Trojan was detected | ET MALWARE Amadey Bot Activity (POST) |
1672 | ss31.exe | Potentially Bad Traffic | ET HUNTING Double User-Agent (User-Agent User-Agent) |
2068 | nbveek.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host DLL Request |
2068 | nbveek.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .dll file with no User-Agent |
3 ETPRO signatures available at the full report