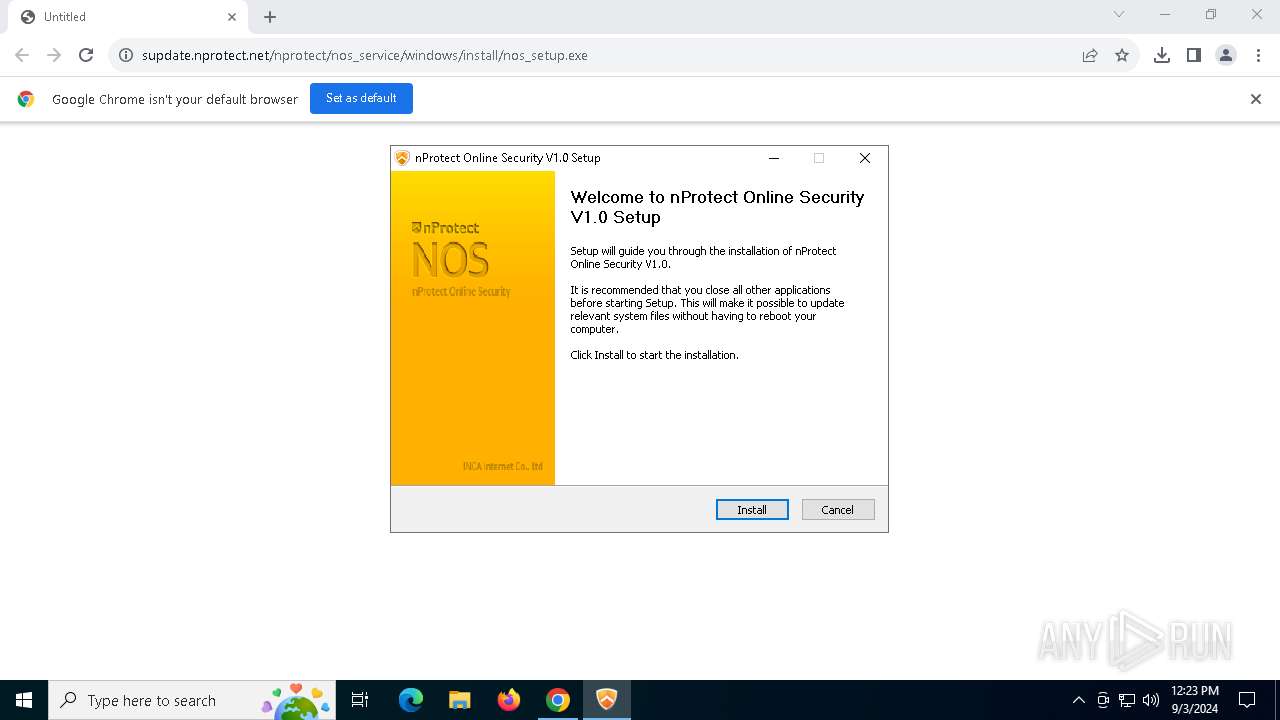
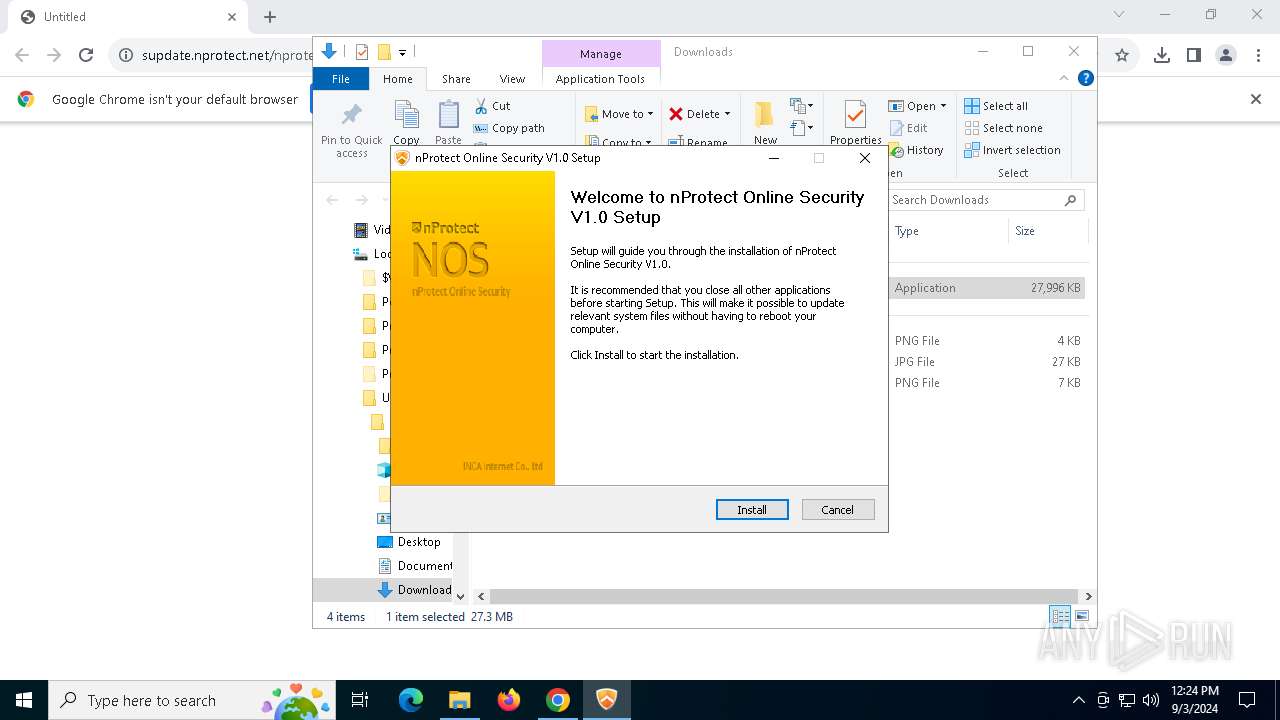
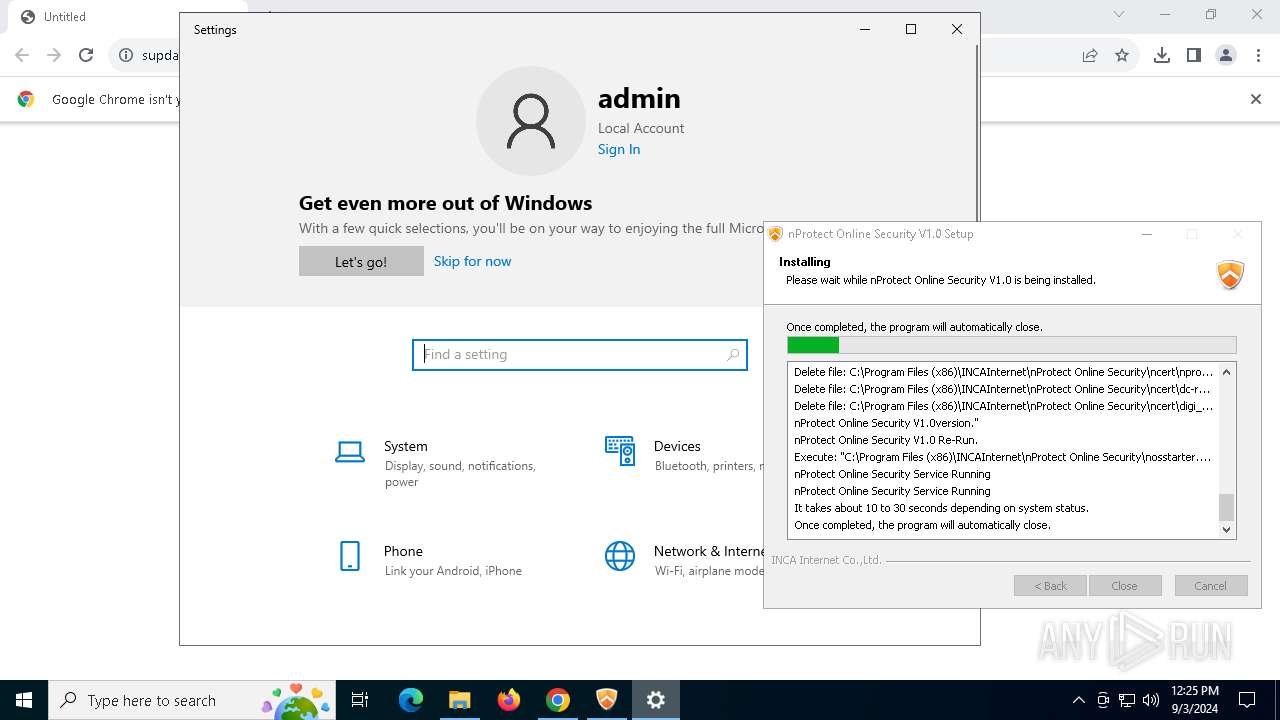
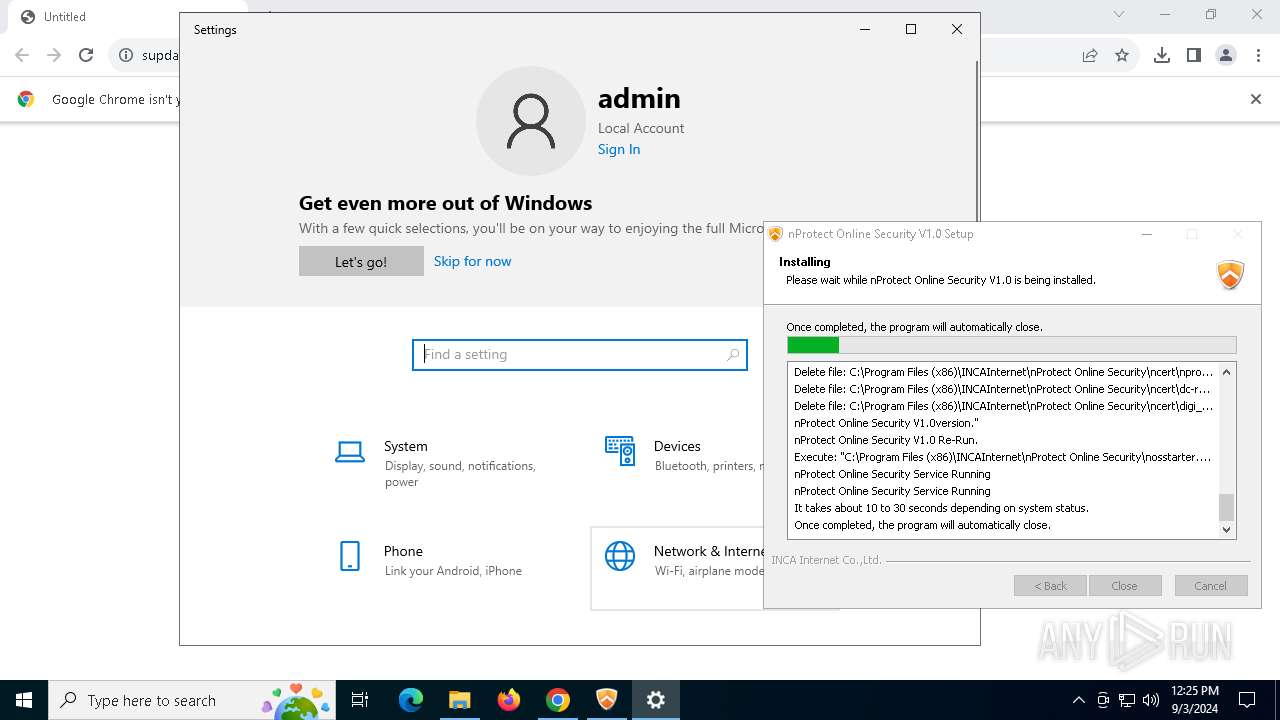
| URL: | https://supdate.nprotect.net/nprotect/nos_service/windows/install/nos_setup.exe |
| Full analysis: | https://app.any.run/tasks/5441c692-95a7-414f-ac25-4928bc88a747 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | September 03, 2024, 12:23:15 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | FB2ADE33FE5251F85C746EEBCE9ED341 |
| SHA1: | FA70A7D3A601B755D2AE8EE1F3D668C5ACED4078 |
| SHA256: | FC455C48E4D180FE2B20BC660B5F67F3517844BF0A8706F912DE75A9BCCE7120 |
| SSDEEP: | 3:N8dQRMGrAtQLyAGKM1KZiqE+9xQh4A:2iWGrgBAGKBZiqEcQh4A |
MALICIOUS
Actions looks like stealing of personal data
- nosstarter.npe (PID: 3140)
- certutil.exe (PID: 1332)
- certutil.exe (PID: 7164)
- certutil.exe (PID: 5044)
- certutil.exe (PID: 6120)
- certutil.exe (PID: 3316)
- certutil.exe (PID: 4528)
- certutil.exe (PID: 6992)
- certutil.exe (PID: 6652)
- nosstarter.npe (PID: 1176)
- certutil.exe (PID: 7700)
- certutil.exe (PID: 6372)
- certutil.exe (PID: 5744)
- certutil.exe (PID: 7020)
- certutil.exe (PID: 3004)
- certutil.exe (PID: 7308)
- certutil.exe (PID: 1700)
- certutil.exe (PID: 7236)
- certutil.exe (PID: 7388)
- certutil.exe (PID: 7464)
- nosstarter.npe (PID: 8140)
- certutil.exe (PID: 4168)
- certutil.exe (PID: 940)
- certutil.exe (PID: 7608)
- certutil.exe (PID: 7684)
- certutil.exe (PID: 8080)
- certutil.exe (PID: 6296)
- certutil.exe (PID: 5656)
- certutil.exe (PID: 8072)
- certutil.exe (PID: 4364)
- certutil.exe (PID: 3980)
ASYNCRAT has been detected (YARA)
- nosstarter.npe (PID: 8140)
MASSLOGGER has been detected (YARA)
- nosstarter.npe (PID: 8140)
STEALERIUM has been detected (YARA)
- nosstarter.npe (PID: 8140)
DCRAT has been detected (YARA)
- nosstarter.npe (PID: 8140)
SUSPICIOUS
Executable content was dropped or overwritten
- nos_setup.exe (PID: 460)
- nos_setup.exe (PID: 8172)
- nos_setup.exe (PID: 7252)
Malware-specific behavior (creating "System.dll" in Temp)
- nos_setup.exe (PID: 460)
- nos_setup.exe (PID: 8172)
- nos_setup.exe (PID: 7252)
The process creates files with name similar to system file names
- nos_setup.exe (PID: 460)
- nos_setup.exe (PID: 8172)
- nos_setup.exe (PID: 7252)
Process drops legitimate windows executable
- nos_setup.exe (PID: 460)
The process drops C-runtime libraries
- nos_setup.exe (PID: 460)
Creates a software uninstall entry
- nos_setup.exe (PID: 460)
Reads security settings of Internet Explorer
- nos_setup.exe (PID: 460)
- nosstarter.npe (PID: 3140)
- nosstarter.npe (PID: 1176)
- nosstarter.npe (PID: 8140)
- nos_launcher.exe (PID: 8012)
Reads the date of Windows installation
- nos_setup.exe (PID: 460)
Drops 7-zip archiver for unpacking
- nos_setup.exe (PID: 460)
Executes as Windows Service
- nossvc.exe (PID: 2724)
- nossvc.exe (PID: 6752)
- nossvc.exe (PID: 7384)
Uses NETSH.EXE to add a firewall rule or allowed programs
- nos_setup.exe (PID: 460)
- nosstarter.npe (PID: 3140)
Creates/Modifies COM task schedule object
- nos_setup.exe (PID: 460)
Reads the BIOS version
- nossvc.exe (PID: 2724)
- nosstarter.npe (PID: 3140)
- nossvc.exe (PID: 6752)
- nosstarter.npe (PID: 1176)
- nosstarter.npe (PID: 8140)
- nossvc.exe (PID: 7384)
- nos_launcher.exe (PID: 8012)
Drops a system driver (possible attempt to evade defenses)
- nos_setup.exe (PID: 460)
Starts application with an unusual extension
- nos_setup.exe (PID: 460)
- nos_setup.exe (PID: 8172)
- nos_setup.exe (PID: 7252)
Checks Windows Trust Settings
- nossvc.exe (PID: 2724)
- nosstarter.npe (PID: 3140)
- nosstarter.npe (PID: 1176)
- nossvc.exe (PID: 6752)
- nosstarter.npe (PID: 8140)
- nossvc.exe (PID: 7384)
- nos_launcher.exe (PID: 8012)
Creates or modifies Windows services
- nossvc.exe (PID: 2724)
- nosstarter.npe (PID: 3140)
- nossvc.exe (PID: 6752)
- nosstarter.npe (PID: 1176)
- nossvc.exe (PID: 7384)
- nosstarter.npe (PID: 8140)
Searches for installed software
- nossvc.exe (PID: 2724)
- nosstarter.npe (PID: 3140)
- nossvc.exe (PID: 6752)
- nosstarter.npe (PID: 1176)
- nossvc.exe (PID: 7384)
- nosstarter.npe (PID: 8140)
Adds/modifies Windows certificates
- nosstarter.npe (PID: 3140)
- nosstarter.npe (PID: 1176)
- nossvc.exe (PID: 6752)
- nosstarter.npe (PID: 8140)
- nos_launcher.exe (PID: 8012)
The process verifies whether the antivirus software is installed
- nosstarter.npe (PID: 3140)
- nossvc.exe (PID: 2724)
- nossvc.exe (PID: 6752)
- nosstarter.npe (PID: 1176)
- nossvc.exe (PID: 7384)
- nosstarter.npe (PID: 8140)
INFO
Application launched itself
- chrome.exe (PID: 6836)
Create files in a temporary directory
- nos_setup.exe (PID: 460)
- nprotect_install.exe (PID: 5944)
- nos_setup.exe (PID: 8172)
- nos_setup.exe (PID: 7252)
Checks supported languages
- nos_setup.exe (PID: 460)
- nprotect_install.exe (PID: 5944)
- nossvc.exe (PID: 2724)
- nosstarter.npe (PID: 3140)
- certutil.exe (PID: 1332)
- noske64.exe (PID: 3040)
- certutil.exe (PID: 7164)
- certutil.exe (PID: 6120)
- certutil.exe (PID: 5044)
- certutil.exe (PID: 4528)
- certutil.exe (PID: 3316)
- certutil.exe (PID: 6992)
- certutil.exe (PID: 6652)
- nos_setup.exe (PID: 8172)
- nossvc.exe (PID: 6752)
- nosstarter.npe (PID: 1176)
- certutil.exe (PID: 7700)
- certutil.exe (PID: 5744)
- certutil.exe (PID: 6372)
- noske64.exe (PID: 5908)
- certutil.exe (PID: 1700)
- certutil.exe (PID: 7236)
- certutil.exe (PID: 7388)
- certutil.exe (PID: 7020)
- certutil.exe (PID: 3004)
- certutil.exe (PID: 7308)
- certutil.exe (PID: 7464)
- nos_setup.exe (PID: 7252)
- nossvc.exe (PID: 7384)
- nosstarter.npe (PID: 8140)
- certutil.exe (PID: 4168)
- certutil.exe (PID: 7608)
- certutil.exe (PID: 940)
- certutil.exe (PID: 7684)
- certutil.exe (PID: 8080)
- certutil.exe (PID: 5656)
- certutil.exe (PID: 3980)
- certutil.exe (PID: 8072)
- certutil.exe (PID: 4364)
- nos_launcher.exe (PID: 8012)
- noske64.exe (PID: 7016)
- certutil.exe (PID: 6296)
Reads the machine GUID from the registry
- nos_setup.exe (PID: 460)
- nosstarter.npe (PID: 3140)
- nossvc.exe (PID: 2724)
- nos_setup.exe (PID: 8172)
- nossvc.exe (PID: 6752)
- nosstarter.npe (PID: 1176)
- nos_setup.exe (PID: 7252)
- nossvc.exe (PID: 7384)
- nosstarter.npe (PID: 8140)
- nos_launcher.exe (PID: 8012)
Reads Environment values
- nos_setup.exe (PID: 460)
- nossvc.exe (PID: 2724)
- nosstarter.npe (PID: 3140)
- nos_setup.exe (PID: 8172)
- nossvc.exe (PID: 6752)
- nosstarter.npe (PID: 1176)
- nos_setup.exe (PID: 7252)
- nosstarter.npe (PID: 8140)
- nossvc.exe (PID: 7384)
- nos_launcher.exe (PID: 8012)
Creates files in the program directory
- nos_setup.exe (PID: 460)
- nprotect_install.exe (PID: 5944)
- nosstarter.npe (PID: 3140)
- nos_setup.exe (PID: 8172)
- nosstarter.npe (PID: 1176)
- nos_setup.exe (PID: 7252)
- nosstarter.npe (PID: 8140)
Reads product name
- nos_setup.exe (PID: 460)
- nossvc.exe (PID: 2724)
- nosstarter.npe (PID: 3140)
- nos_setup.exe (PID: 8172)
- nossvc.exe (PID: 6752)
- nosstarter.npe (PID: 1176)
- nos_setup.exe (PID: 7252)
- nosstarter.npe (PID: 8140)
- nossvc.exe (PID: 7384)
Reads the computer name
- nos_setup.exe (PID: 460)
- nprotect_install.exe (PID: 5944)
- nossvc.exe (PID: 2724)
- nosstarter.npe (PID: 3140)
- certutil.exe (PID: 1332)
- certutil.exe (PID: 7164)
- certutil.exe (PID: 5044)
- certutil.exe (PID: 6120)
- certutil.exe (PID: 4528)
- certutil.exe (PID: 3316)
- certutil.exe (PID: 6992)
- certutil.exe (PID: 6652)
- nos_setup.exe (PID: 8172)
- nossvc.exe (PID: 6752)
- nosstarter.npe (PID: 1176)
- certutil.exe (PID: 7700)
- certutil.exe (PID: 5744)
- certutil.exe (PID: 6372)
- certutil.exe (PID: 7020)
- certutil.exe (PID: 3004)
- certutil.exe (PID: 1700)
- certutil.exe (PID: 7236)
- certutil.exe (PID: 7388)
- certutil.exe (PID: 7308)
- certutil.exe (PID: 7464)
- nos_setup.exe (PID: 7252)
- nossvc.exe (PID: 7384)
- certutil.exe (PID: 4168)
- nosstarter.npe (PID: 8140)
- certutil.exe (PID: 6296)
- certutil.exe (PID: 940)
- certutil.exe (PID: 7608)
- certutil.exe (PID: 7684)
- certutil.exe (PID: 8080)
- certutil.exe (PID: 5656)
- certutil.exe (PID: 8072)
- certutil.exe (PID: 3980)
- certutil.exe (PID: 4364)
- nos_launcher.exe (PID: 8012)
The process uses the downloaded file
- nos_setup.exe (PID: 460)
- chrome.exe (PID: 4364)
- chrome.exe (PID: 6836)
Process checks computer location settings
- nos_setup.exe (PID: 460)
UPX packer has been detected
- nos_setup.exe (PID: 460)
Reads Microsoft Office registry keys
- chrome.exe (PID: 6836)
Executable content was dropped or overwritten
- chrome.exe (PID: 6836)
- chrome.exe (PID: 8112)
Creates files or folders in the user directory
- nosstarter.npe (PID: 3140)
- certutil.exe (PID: 5044)
- certutil.exe (PID: 3316)
- certutil.exe (PID: 3004)
- certutil.exe (PID: 7308)
- certutil.exe (PID: 7684)
- certutil.exe (PID: 4364)
- nos_launcher.exe (PID: 8012)
Reads the software policy settings
- nosstarter.npe (PID: 3140)
- nossvc.exe (PID: 2724)
- slui.exe (PID: 6204)
- nosstarter.npe (PID: 1176)
- nossvc.exe (PID: 6752)
- nosstarter.npe (PID: 8140)
- nossvc.exe (PID: 7384)
- slui.exe (PID: 7584)
- nos_launcher.exe (PID: 8012)
Checks proxy server information
- nosstarter.npe (PID: 3140)
- nosstarter.npe (PID: 1176)
- nosstarter.npe (PID: 8140)
- slui.exe (PID: 7584)
- nos_launcher.exe (PID: 8012)
Reads CPU info
- nosstarter.npe (PID: 3140)
- nosstarter.npe (PID: 1176)
- nosstarter.npe (PID: 8140)
Themida protector has been detected
- nossvc.exe (PID: 2724)
- nosstarter.npe (PID: 3140)
- nossvc.exe (PID: 6752)
- nosstarter.npe (PID: 1176)
- nossvc.exe (PID: 7384)
- nosstarter.npe (PID: 8140)
Manual execution by a user
- nos_setup.exe (PID: 8172)
- nos_setup.exe (PID: 7212)
- nos_setup.exe (PID: 7252)
- nos_launcher.exe (PID: 8012)
- nos_launcher.exe (PID: 3276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
276
Monitored processes
135
Malicious processes
10
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3080 --field-trial-handle=1924,i,651810124118192768,14176940818464904683,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 376 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | certutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
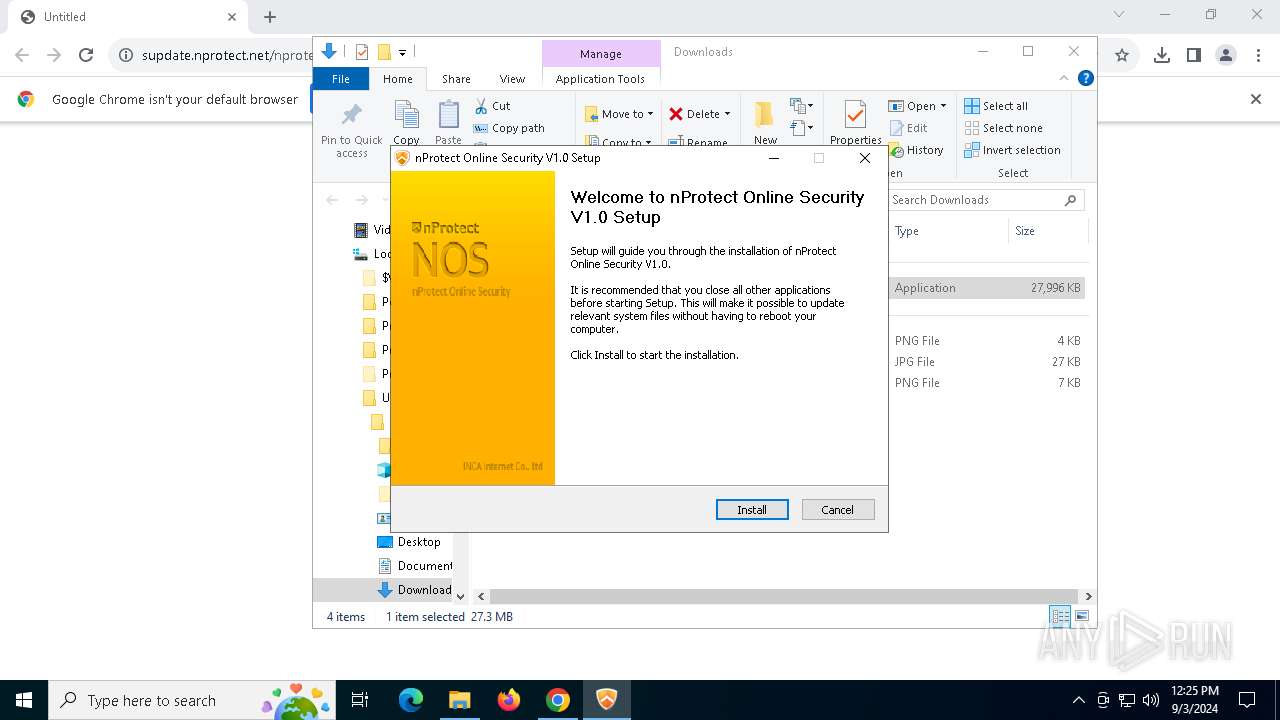
| 460 | "C:\Users\admin\Downloads\nos_setup.exe" | C:\Users\admin\Downloads\nos_setup.exe | chrome.exe | ||||||||||||
User: admin Company: INCA Internet Co.,Ltd. Integrity Level: HIGH Description: nProtect Online Security V1.0 Installer Exit code: 2 Version: 2024.08.28.1 Modules
| |||||||||||||||
| 508 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x21c,0x220,0x224,0x1f8,0x228,0x7fffd56fdc40,0x7fffd56fdc4c,0x7fffd56fdc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 752 | "C:\WINDOWS\system32\sc.exe" create "nossvc" binPath= "\"C:\Program Files (x86)\INCAInternet\nProtect Online Security\nossvc.exe\" /SVC" DisplayName= "nProtect Online Security(PFS)" start= auto | C:\Windows\SysWOW64\sc.exe | — | nos_setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1073 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 936 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4684 --field-trial-handle=1924,i,651810124118192768,14176940818464904683,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 936 | "C:\WINDOWS\system32\sc.exe" create "nossvc" binPath= "\"C:\Program Files (x86)\INCAInternet\nProtect Online Security\nossvc.exe\" /SVC" DisplayName= "nProtect Online Security(PFS)" start= auto | C:\Windows\SysWOW64\sc.exe | — | nos_setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 940 | "C:\Program Files (x86)\INCAInternet\nProtect Online Security\ncert\certutil.exe" -L -d sql:"C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release" | C:\Program Files (x86)\INCAInternet\nProtect Online Security\ncert\certutil.exe | nosstarter.npe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1064 | "C:\WINDOWS\system32\netsh.exe" advfirewall firewall add rule name="nProtect Online Security Starter" program="C:\Program Files (x86)\INCAInternet\nProtect Online Security\nosstarter.npe" description="nProtect Online Security Starter" dir=in action=allow protocol=any enable=yes profile=any | C:\Windows\SysWOW64\netsh.exe | — | nos_setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1148 | "C:\WINDOWS\system32\sc.exe" control nossvc 200 | C:\Windows\SysWOW64\sc.exe | — | nos_setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1062 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
116 568
Read events
116 337
Write events
216
Delete events
15
Modification events
| (PID) Process: | (6836) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6836) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6836) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (6836) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (6836) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6836) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (6836) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6836) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (6836) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6836) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
237
Suspicious files
674
Text files
83
Unknown types
171
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6836 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6836 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6836 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6836 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF12b4c1.TMP | — | |
MD5:— | SHA256:— | |||
| 6836 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6836 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6836 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF12b4d1.TMP | — | |
MD5:— | SHA256:— | |||
| 6836 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6836 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:FCE53E052E5CF7C20819320F374DEA88 | SHA256:CD95DE277E746E92CC2C53D9FC92A8F6F0C3EDFB7F1AD9A4E9259F927065BC89 | |||
| 6836 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:FC81892AC822DCBB09441D3B58B47125 | SHA256:FB077C966296D02D50CCBF7F761D2A3311A206A784A7496F331C2B0D6AD205C8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
58
TCP/UDP connections
94
DNS requests
54
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6488 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2724 | nossvc.exe | GET | 200 | 152.199.19.74:80 | http://ocsp.verisign.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEFIA5aolVvwahu2WydRLM8c%3D | unknown | — | — | whitelisted |
3140 | nosstarter.npe | GET | 200 | 152.199.19.74:80 | http://ocsp.verisign.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEFIA5aolVvwahu2WydRLM8c%3D | unknown | — | — | whitelisted |
3140 | nosstarter.npe | GET | 200 | 192.229.221.95:80 | http://crl.verisign.com/pca3-g5.crl | unknown | — | — | whitelisted |
1780 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6488 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3140 | nosstarter.npe | GET | 200 | 152.199.19.74:80 | http://ocsp.verisign.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEFIA5aolVvwahu2WydRLM8c%3D | unknown | — | — | whitelisted |
3140 | nosstarter.npe | GET | 200 | 152.199.19.74:80 | http://sf.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTSqZMG5M8TA9rdzkbCnNwuMAd5VgQUz5mp6nsm9EvJjo%2FX8AUm7%2BPSp50CEBAl3Oz5Y4DLk%2FbaIuO25fk%3D | unknown | — | — | whitelisted |
3140 | nosstarter.npe | GET | 200 | 152.199.19.74:80 | http://sv.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQe6LNDJdqx%2BJOp7hVgTeaGFJ%2FCQgQUljtT8Hkzl699g%2B8uK8zKt4YecmYCEGVWuysz45rI7F7EXnOwPC0%3D | unknown | — | — | whitelisted |
2724 | nossvc.exe | GET | 200 | 152.199.19.74:80 | http://sv.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQe6LNDJdqx%2BJOp7hVgTeaGFJ%2FCQgQUljtT8Hkzl699g%2B8uK8zKt4YecmYCEGVWuysz45rI7F7EXnOwPC0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | 52.167.17.97:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6876 | svchost.exe | 52.167.17.97:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 52.167.17.97:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6836 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1156 | chrome.exe | 108.177.15.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
1156 | chrome.exe | 61.111.25.113:443 | supdate.nprotect.net | LG DACOM Corporation | KR | whitelisted |
1780 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1780 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
supdate.nprotect.net |
| whitelisted |
accounts.google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.google.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |