| File name: | trojan3.exe |
| Full analysis: | https://app.any.run/tasks/ce74d18d-e042-45c1-af64-c4270c075a04 |
| Verdict: | Malicious activity |
| Threats: | Arkei is a stealer type malware capable of collecting passwords, autosaved forms, cryptocurrency wallet credentials, and files. |
| Analysis date: | January 22, 2019, 23:59:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | A0D69C1B3F868D7030231D564E059FB1 |
| SHA1: | 9090167034C7CE3D61F6E73401C48CCD78F85351 |
| SHA256: | FBE0A158C362405D480D40676E5BDA3A9B97047F61661B9F72FF7AFA30F1697D |
| SSDEEP: | 49152:PoMUcFI5eqRRDVsv4HHB150jqVg7HkpHMse9aglouPDAIRdPsP+fL9LQhq6/wvo/:PTUaI9OMzejqikpYbAI7XLyhq6IvorA+ |
MALICIOUS
Writes to a start menu file
- DOC001.exe (PID: 2612)
- DOC001.exe (PID: 4044)
Changes the autorun value in the registry
- DOC001.exe (PID: 2612)
- DOC001.exe (PID: 4044)
Loads dropped or rewritten executable
- DOC001.exe (PID: 2612)
- DOC001.exe (PID: 4044)
- jar2.exe (PID: 2680)
- jar2.exe (PID: 2684)
Application was dropped or rewritten from another process
- java.exe (PID: 2864)
- java1.exe (PID: 3712)
- nsB65B.tmp (PID: 3444)
- nsB502.tmp (PID: 4092)
- DOC001.exe (PID: 4044)
- java.exe (PID: 3552)
- dhelper.exe (PID: 2560)
- jar2.exe (PID: 2684)
- nsB3A9.tmp (PID: 2812)
- java12.exe (PID: 2172)
- jar2.exe (PID: 2680)
- nsC7CD.tmp (PID: 2920)
- nsC8C8.tmp (PID: 2400)
- lsm.exe (PID: 3656)
- nsCA31.tmp (PID: 2760)
- dhelper.exe (PID: 2356)
Downloads executable files from the Internet
- DOC001.exe (PID: 2612)
- DOC001.exe (PID: 4044)
Changes the login/logoff helper path in the registry
- jar2.exe (PID: 2684)
- jar2.exe (PID: 2680)
Uses Task Scheduler to run other applications
- java12.exe (PID: 2172)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2340)
ARKEI was detected
- java12.exe (PID: 2172)
SUSPICIOUS
Creates files in the user directory
- trojan3.exe (PID: 3056)
- java1.exe (PID: 3712)
- DOC001.exe (PID: 2612)
- cmd.exe (PID: 3512)
- DOC001.exe (PID: 4044)
- cmd.exe (PID: 2892)
Executable content was dropped or overwritten
- trojan3.exe (PID: 3056)
- java.exe (PID: 2864)
- DOC001.exe (PID: 2612)
- java1.exe (PID: 3712)
- jar2.exe (PID: 2684)
- cmd.exe (PID: 2892)
- DOC001.exe (PID: 4044)
- java12.exe (PID: 2172)
- jar2.exe (PID: 2680)
Starts itself from another location
- trojan3.exe (PID: 3056)
- java1.exe (PID: 3712)
Dropped object may contain URLs of mainers pools
- DOC001.exe (PID: 2612)
- DOC001.exe (PID: 4044)
Starts application with an unusual extension
- jar2.exe (PID: 2684)
- jar2.exe (PID: 2680)
Starts CMD.EXE for commands execution
- nsB3A9.tmp (PID: 2812)
- nsB502.tmp (PID: 4092)
- nsB65B.tmp (PID: 3444)
- nsC7CD.tmp (PID: 2920)
- nsC8C8.tmp (PID: 2400)
- nsCA31.tmp (PID: 2760)
- java12.exe (PID: 2172)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 684)
- cmd.exe (PID: 296)
Creates files in the program directory
- java12.exe (PID: 2172)
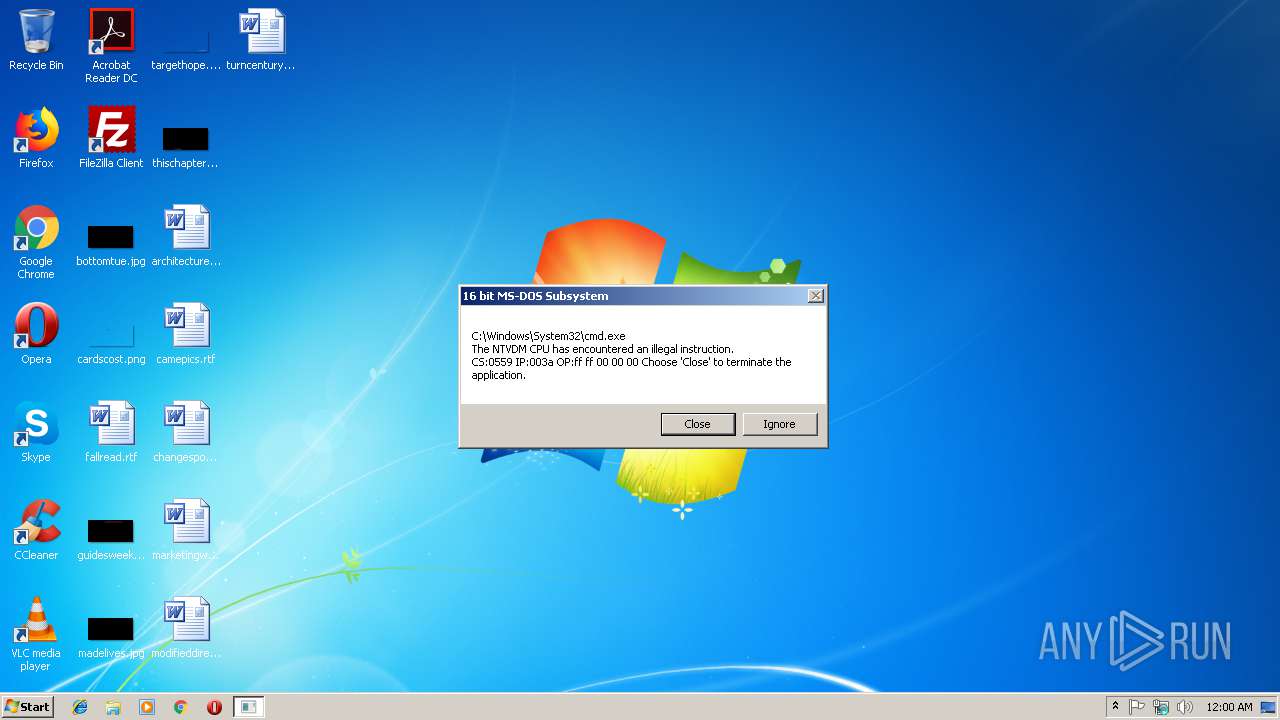
Executes application which crashes
- cmd.exe (PID: 3508)
INFO
Drop XMRig executable file
- DOC001.exe (PID: 4044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (94.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.5) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:12:05 23:52:12+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 24064 |
| InitializedDataSize: | 308224 |
| UninitializedDataSize: | 8192 |
| EntryPoint: | 0x30fa |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 05-Dec-2009 22:52:12 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 05-Dec-2009 22:52:12 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00005C4C | 0x00005E00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.4388 |
.rdata | 0x00007000 | 0x0000129C | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.04684 |
.data | 0x00009000 | 0x00048C58 | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.79628 |
.ndata | 0x00052000 | 0x00040000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x00092000 | 0x0000F160 | 0x0000F200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.88476 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.20956 | 716 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 3.95465 | 9640 | UNKNOWN | English - United States | RT_ICON |
3 | 4.44806 | 4264 | UNKNOWN | English - United States | RT_ICON |
4 | 4.74717 | 3752 | UNKNOWN | English - United States | RT_ICON |
5 | 5.41664 | 2216 | UNKNOWN | English - United States | RT_ICON |
6 | 2.9738 | 1640 | UNKNOWN | English - United States | RT_ICON |
7 | 3.83015 | 1384 | UNKNOWN | English - United States | RT_ICON |
8 | 5.32149 | 1128 | UNKNOWN | English - United States | RT_ICON |
9 | 3.26704 | 744 | UNKNOWN | English - United States | RT_ICON |
10 | 3.05995 | 296 | UNKNOWN | English - United States | RT_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
VERSION.dll |
ole32.dll |
Total processes
68
Monitored processes
29
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 296 | cmd /C taskkill /f /im dhelper.exe & start C:\Users\admin\AppData\Roaming\dhelper.exe | C:\Windows\system32\cmd.exe | — | nsCA31.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 684 | cmd /C taskkill /f /im dhelper.exe & start C:\Users\admin\AppData\Roaming\dhelper.exe | C:\Windows\system32\cmd.exe | — | nsB65B.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 884 | "C:\Windows\system32\ntvdm.exe" | C:\Windows\system32\ntvdm.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2172 | "C:\Users\admin\AppData\Local\Temp\java12.exe" -pJavajre_set8z | C:\Users\admin\AppData\Local\Temp\java12.exe | DOC001.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2340 | "C:\Windows\System32\schtasks.exe" /create /sc minute /f /tn "Microsoft LocalManager[Windows 7 Professional]" /tr "C:\ProgramData\{98304143-9830-9830-983041437365}\lsm.exe" | C:\Windows\System32\schtasks.exe | — | java12.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2356 | C:\Users\admin\AppData\Roaming\dhelper.exe | C:\Users\admin\AppData\Roaming\dhelper.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2400 | "C:\Users\admin\AppData\Local\Temp\nszC7BD.tmp\nsC8C8.tmp" cmd /C copy /b %temp%\Javatemp\jare.7z1 + %temp%\Javatemp\temps.7z1 C:\Users\admin\AppData\Roaming\dhelper.exe | C:\Users\admin\AppData\Local\Temp\nszC7BD.tmp\nsC8C8.tmp | — | jar2.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 2488 | taskkill /f /im dhelper.exe | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2560 | C:\Users\admin\AppData\Roaming\dhelper.exe | C:\Users\admin\AppData\Roaming\dhelper.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 2612 | "C:\Users\admin\AppData\Roaming\Temp\DOC001.exe" | C:\Users\admin\AppData\Roaming\Temp\DOC001.exe | trojan3.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
3 017
Read events
2 921
Write events
96
Delete events
0
Modification events
| (PID) Process: | (3056) trojan3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3056) trojan3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2612) DOC001.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | |
Value: | |||
| (PID) Process: | (2612) DOC001.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DOC001_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2612) DOC001.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DOC001_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2612) DOC001.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DOC001_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2612) DOC001.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DOC001_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2612) DOC001.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DOC001_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2612) DOC001.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DOC001_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2612) DOC001.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DOC001_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
25
Suspicious files
1
Text files
2
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2864 | java.exe | C:\Users\admin\AppData\Local\Temp\Javatemp\ini.jwd | — | |
MD5:— | SHA256:— | |||
| 2684 | jar2.exe | C:\Users\admin\AppData\Local\Temp\nsrB398.tmp | — | |
MD5:— | SHA256:— | |||
| 2612 | DOC001.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\explorer.lnk | lnk | |
MD5:— | SHA256:— | |||
| 2612 | DOC001.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\java[1].dat | executable | |
MD5:— | SHA256:— | |||
| 2612 | DOC001.exe | C:\Users\admin\AppData\Local\Temp\java.exe | executable | |
MD5:— | SHA256:— | |||
| 3056 | trojan3.exe | C:\Users\admin\AppData\Roaming\Temp\DOC001.exe | executable | |
MD5:— | SHA256:— | |||
| 2612 | DOC001.exe | C:\Users\admin\AppData\Local\Temp\nsbA63A.tmp\inetc.dll | executable | |
MD5:D7A3FA6A6C738B4A3C40D5602AF20B08 | SHA256:67EFF17C53A78C8EC9A28F392B9BB93DF3E74F96F6ECD87A333A482C36546B3E | |||
| 2612 | DOC001.exe | C:\Users\admin\AppData\Roaming\Temp\NsCpuCNMiner64.exe | executable | |
MD5:EEDB9D86AE8ABC65FA7AC7C6323D4E8F | SHA256:D0326F0DDCE4C00F93682E3A6F55A3125F6387E959E9ED6C5E5584E78E737078 | |||
| 2684 | jar2.exe | C:\Users\admin\AppData\Local\Temp\nsgB3A8.tmp\nsB502.tmp | executable | |
MD5:— | SHA256:— | |||
| 2684 | jar2.exe | C:\Users\admin\AppData\Local\Temp\nsgB3A8.tmp\nsB3A9.tmp | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
9
DNS requests
15
Threats
29
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2560 | dhelper.exe | GET | — | 208.100.26.251:80 | http://ce893c41a8.pw/index.php?a=1&h=0b76&b=1&p=d1&i=0401758B8503A6D9AF73594421B467F7 | US | — | — | malicious |
2356 | dhelper.exe | GET | — | 208.100.26.251:80 | http://ce893c41a8.pw/index.php?a=1&h=0b76&b=1&p=d1&i=8ECE0ECD731C0F598247F2D34163159D | US | — | — | malicious |
2356 | dhelper.exe | GET | — | 208.100.26.251:80 | http://6ae79845b2.pw/index.php?a=1&h=4f2f&b=1&p=d1&i=8ECE0ECD731C0F598247F2D34163159D | US | — | — | malicious |
4044 | DOC001.exe | GET | 200 | 195.208.1.107:80 | http://kriso.ru/java12.dat | RU | executable | 200 Kb | malicious |
2612 | DOC001.exe | GET | 200 | 195.208.1.107:80 | http://rucop.ru/java.dat | RU | executable | 2.04 Mb | malicious |
2172 | java12.exe | POST | 405 | 195.208.1.107:80 | http://ioad.pw/ioad.exe | RU | html | 182 b | malicious |
2172 | java12.exe | POST | 301 | 88.99.66.31:80 | http://2no.co/1ajz97 | DE | html | 178 b | whitelisted |
2612 | DOC001.exe | GET | 200 | 195.208.1.107:80 | http://kriso.ru/java1.dat | RU | executable | 1009 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2612 | DOC001.exe | 195.208.1.107:80 | rucop.ru | Autonomous Non-commercial Organization Regional Network Information Center | RU | suspicious |
4044 | DOC001.exe | 195.208.1.107:80 | rucop.ru | Autonomous Non-commercial Organization Regional Network Information Center | RU | suspicious |
2172 | java12.exe | 88.99.66.31:80 | 2no.co | Hetzner Online GmbH | DE | malicious |
2560 | dhelper.exe | 208.100.26.251:80 | ce893c41a8.pw | Steadfast | US | suspicious |
2172 | java12.exe | 88.99.66.31:443 | 2no.co | Hetzner Online GmbH | DE | malicious |
2356 | dhelper.exe | 208.100.26.251:80 | ce893c41a8.pw | Steadfast | US | suspicious |
2172 | java12.exe | 195.208.1.107:80 | rucop.ru | Autonomous Non-commercial Organization Regional Network Information Center | RU | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
rucop.ru |
| malicious |
kriso.ru |
| malicious |
ce893c41a8.pw |
| malicious |
2no.co |
| whitelisted |
ioad.pw |
| malicious |
6ae79845b2.pw |
| malicious |
fa41b00ded.pw |
| unknown |
cfa7fed9a2.pw |
| unknown |
7bedab72f1.pw |
| unknown |
fe32f3c117.pw |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2612 | DOC001.exe | A Network Trojan was detected | ET POLICY User-Agent (NSIS_Inetc (Mozilla)) - Sometimes used by hostile installers |
2612 | DOC001.exe | Misc activity | SUSPICIOUS [PTsecurity] Suspicious HTTP header - Sometimes used by hostile installer |
2612 | DOC001.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2612 | DOC001.exe | A Network Trojan was detected | ET POLICY User-Agent (NSIS_Inetc (Mozilla)) - Sometimes used by hostile installers |
2612 | DOC001.exe | Misc activity | SUSPICIOUS [PTsecurity] Suspicious HTTP header - Sometimes used by hostile installer |
2612 | DOC001.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
4044 | DOC001.exe | A Network Trojan was detected | ET POLICY User-Agent (NSIS_Inetc (Mozilla)) - Sometimes used by hostile installers |
4044 | DOC001.exe | Misc activity | SUSPICIOUS [PTsecurity] Suspicious HTTP header - Sometimes used by hostile installer |
4044 | DOC001.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1056 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
2 ETPRO signatures available at the full report