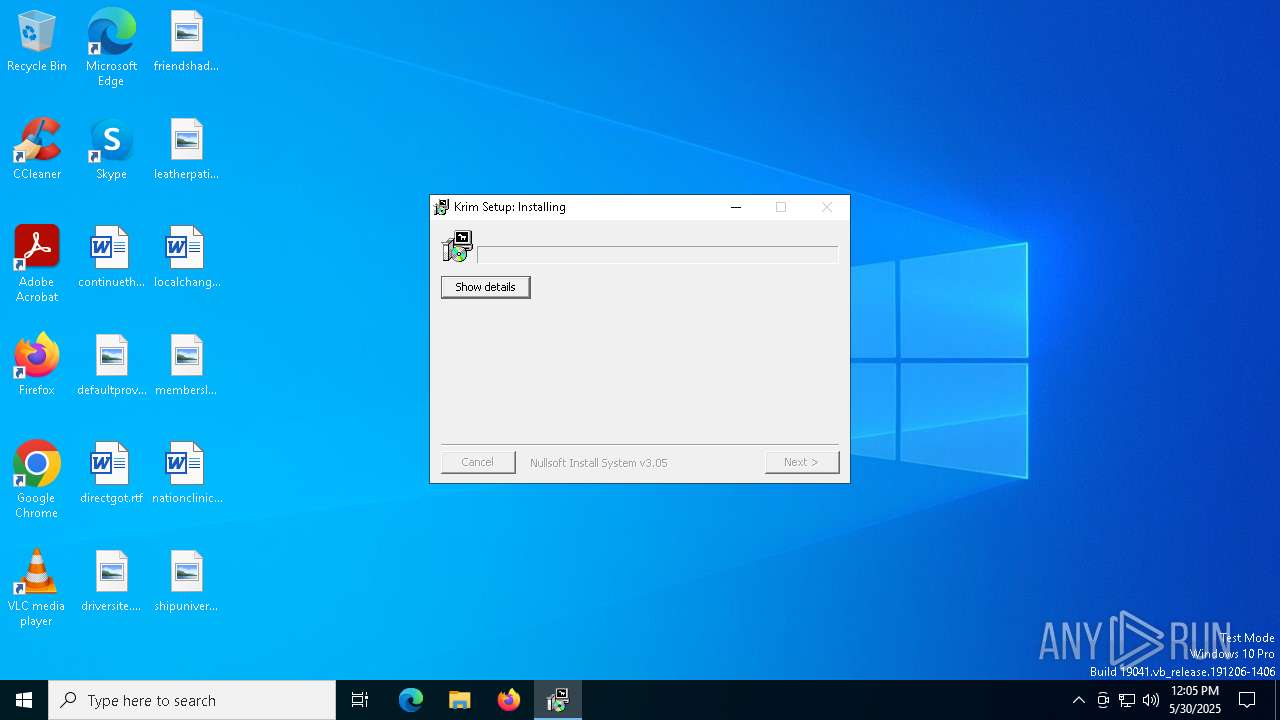
| File name: | Nueva Orden.pdf.exe |
| Full analysis: | https://app.any.run/tasks/66ec24c8-dcea-4c18-aa7e-d28cce947896 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | May 30, 2025, 12:05:28 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | CED90111BDA23A4F34DC779EBE398270 |
| SHA1: | 32DF60B92B59D615D2EDC9E5A666635D89062D64 |
| SHA256: | FB9CBF72507888127F62E5E1EABB1671493419738FDCBEBA0EE74D6B2F3217B4 |
| SSDEEP: | 24576:lwirwlYQCobqCDA0Eci4FIqBOt2tnPTTDIQ5b7Cdf1ktdpyRC:lwirwlVCobqCDA0EF4FIqBOt2tnPTTDL |
MALICIOUS
Steals credentials from Web Browsers
- Nueva Orden.pdf.exe (PID: 7968)
Actions looks like stealing of personal data
- Nueva Orden.pdf.exe (PID: 7968)
AGENTTESLA has been detected (YARA)
- Nueva Orden.pdf.exe (PID: 7968)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- Nueva Orden.pdf.exe (PID: 7444)
Executable content was dropped or overwritten
- Nueva Orden.pdf.exe (PID: 7444)
There is functionality for taking screenshot (YARA)
- Nueva Orden.pdf.exe (PID: 7444)
- Nueva Orden.pdf.exe (PID: 7968)
Application launched itself
- Nueva Orden.pdf.exe (PID: 7444)
The process creates files with name similar to system file names
- Nueva Orden.pdf.exe (PID: 7444)
Reads security settings of Internet Explorer
- Nueva Orden.pdf.exe (PID: 7968)
Connects to the server without a host name
- Nueva Orden.pdf.exe (PID: 7968)
Checks for external IP
- svchost.exe (PID: 2196)
- Nueva Orden.pdf.exe (PID: 7968)
Connects to FTP
- Nueva Orden.pdf.exe (PID: 7968)
INFO
The sample compiled with english language support
- Nueva Orden.pdf.exe (PID: 7444)
Checks supported languages
- Nueva Orden.pdf.exe (PID: 7444)
- Nueva Orden.pdf.exe (PID: 7968)
Reads the computer name
- Nueva Orden.pdf.exe (PID: 7444)
- Nueva Orden.pdf.exe (PID: 7968)
Create files in a temporary directory
- Nueva Orden.pdf.exe (PID: 7444)
Checks proxy server information
- Nueva Orden.pdf.exe (PID: 7968)
- slui.exe (PID: 7288)
Reads the machine GUID from the registry
- Nueva Orden.pdf.exe (PID: 7968)
Disables trace logs
- Nueva Orden.pdf.exe (PID: 7968)
Reads the software policy settings
- slui.exe (PID: 7288)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:12:16 00:50:33+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26112 |
| InitializedDataSize: | 3805696 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x33d7 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.4.0.0 |
| ProductVersionNumber: | 2.4.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | solomonical latrant |
| FileDescription: | mordella appelinstanserne |
| FileVersion: | 2.4.0.0 |
| InternalName: | misconjugation prrafaelit.exe |
| LegalCopyright: | smdenavnes anmasselsens dikterer |
| OriginalFileName: | misconjugation prrafaelit.exe |
| ProductName: | dampkogningen craftier legemshjders |
Total processes
135
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7288 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7444 | "C:\Users\admin\AppData\Local\Temp\Nueva Orden.pdf.exe" | C:\Users\admin\AppData\Local\Temp\Nueva Orden.pdf.exe | explorer.exe | ||||||||||||
User: admin Company: solomonical latrant Integrity Level: MEDIUM Description: mordella appelinstanserne Exit code: 0 Version: 2.4.0.0 Modules
| |||||||||||||||
| 7520 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7552 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7968 | "C:\Users\admin\AppData\Local\Temp\Nueva Orden.pdf.exe" | C:\Users\admin\AppData\Local\Temp\Nueva Orden.pdf.exe | Nueva Orden.pdf.exe | ||||||||||||
User: admin Company: solomonical latrant Integrity Level: MEDIUM Description: mordella appelinstanserne Version: 2.4.0.0 Modules
| |||||||||||||||
Total events
2 386
Read events
2 146
Write events
240
Delete events
0
Modification events
| (PID) Process: | (7444) Nueva Orden.pdf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: u | |||
| (PID) Process: | (7444) Nueva Orden.pdf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: us | |||
| (PID) Process: | (7444) Nueva Orden.pdf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: use | |||
| (PID) Process: | (7444) Nueva Orden.pdf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: user | |||
| (PID) Process: | (7444) Nueva Orden.pdf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: user3 | |||
| (PID) Process: | (7444) Nueva Orden.pdf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: user32 | |||
| (PID) Process: | (7444) Nueva Orden.pdf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: user32: | |||
| (PID) Process: | (7444) Nueva Orden.pdf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: user32:: | |||
| (PID) Process: | (7444) Nueva Orden.pdf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: user32::S | |||
| (PID) Process: | (7444) Nueva Orden.pdf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: user32::Sh | |||
Executable files
1
Suspicious files
4
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7444 | Nueva Orden.pdf.exe | C:\Users\admin\metacarpus\cineast\Drikkens.kon | binary | |
MD5:718F70F0A87C63F78DEB9370893B4B9A | SHA256:EFE325FE3B2636E51963C6D83397BE70BE739ED42A307F8248986B5240C77F61 | |||
| 7444 | Nueva Orden.pdf.exe | C:\Users\admin\metacarpus\cineast\Maskeprogrammerede\leucobryaceae.jpg | image | |
MD5:A47C71B73CEB9F7064990CDC9C23CAB7 | SHA256:A95CE84F1853345671304EA0C6277D9D7D4904E20436C650F40D04A394892E27 | |||
| 7444 | Nueva Orden.pdf.exe | C:\Users\admin\AppData\Local\Temp\Settings.ini | text | |
MD5:A6216EF9FBE57B11DEEB1B1FD840C392 | SHA256:EDF6C9DA71DAF3B3DA2E89A1BC6B9F4B812F18FC133CF4706A3AE983E4040946 | |||
| 7444 | Nueva Orden.pdf.exe | C:\Users\admin\metacarpus\cineast\Maskeprogrammerede\gelatinisers.eve | binary | |
MD5:31DB1AFB06D59B827AB3DD99D3C98348 | SHA256:B254580BE0172029A798A201B1D394E236187D8A0E132F4F99E1EBC8412B99E7 | |||
| 7444 | Nueva Orden.pdf.exe | C:\Users\admin\metacarpus\cineast\Maskeprogrammerede\propellants.rea | binary | |
MD5:8CE33852FB6E9CC3F8A866FAD32D073B | SHA256:FEDEA8597BE2B93742204EE5F09F53976C9BD010E2671C6139EEEAB8A77E3A90 | |||
| 7444 | Nueva Orden.pdf.exe | C:\Users\admin\AppData\Local\Temp\nsrBA5B.tmp\System.dll | executable | |
MD5:8CF2AC271D7679B1D68EEFC1AE0C5618 | SHA256:6950991102462D84FDC0E3B0AE30C95AF8C192F77CE3D78E8D54E6B22F7C09BA | |||
| 7444 | Nueva Orden.pdf.exe | C:\Users\admin\metacarpus\cineast\Maskeprogrammerede\ratafees.txt | text | |
MD5:090CDD675D9BC566C8DF8017DBB19C9A | SHA256:4FD3A0E269F29F2A98EC00BCC04CEF69ED0FB9B48ACF180323045AAE6A0C7A4A | |||
| 7444 | Nueva Orden.pdf.exe | C:\Users\admin\metacarpus\cineast\Incremating.Cab | binary | |
MD5:1C4C3337876005E41E4ACD90DE9B1BCA | SHA256:F884C8858CC79B612FBE333A9B129293B3096EFBBB6653C155E85C9A92B3BC71 | |||
| 7444 | Nueva Orden.pdf.exe | C:\Users\admin\metacarpus\cineast\Maskeprogrammerede\nobelpristagerens.txt | text | |
MD5:BDFD3CF1BD98C89C83C4DE6047C7805A | SHA256:EE0AC63B496AA0A5249289CC0847E38BF3FFFC986B8BB8D7574139D61A922286 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
28
DNS requests
21
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7968 | Nueva Orden.pdf.exe | GET | 200 | 107.175.243.148:80 | http://107.175.243.148/aDgWB192.bin | unknown | — | — | unknown |
4880 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7968 | Nueva Orden.pdf.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
4880 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5740 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7968 | Nueva Orden.pdf.exe | 107.175.243.148:80 | — | AS-COLOCROSSING | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ip-api.com |
| whitelisted |
ftp.horeca-bucuresti.ro |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7968 | Nueva Orden.pdf.exe | Potentially Bad Traffic | ET HUNTING Generic .bin download from Dotted Quad |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
7968 | Nueva Orden.pdf.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
7968 | Nueva Orden.pdf.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |